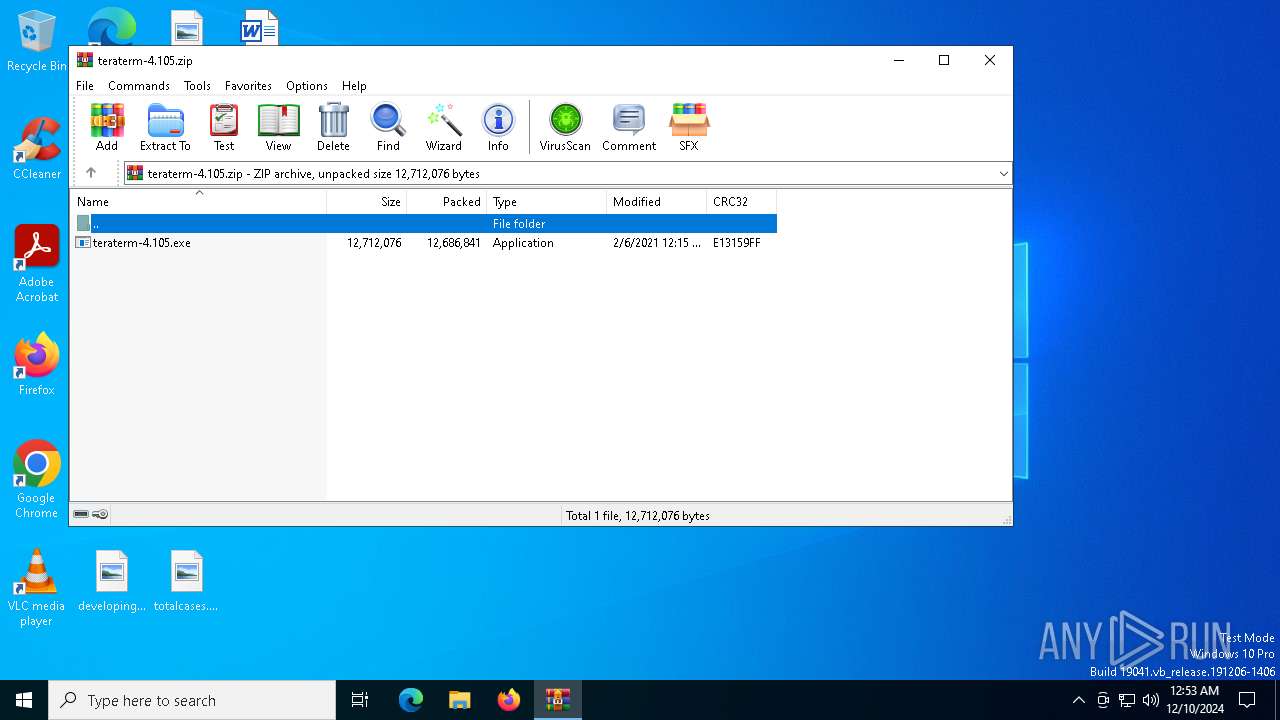
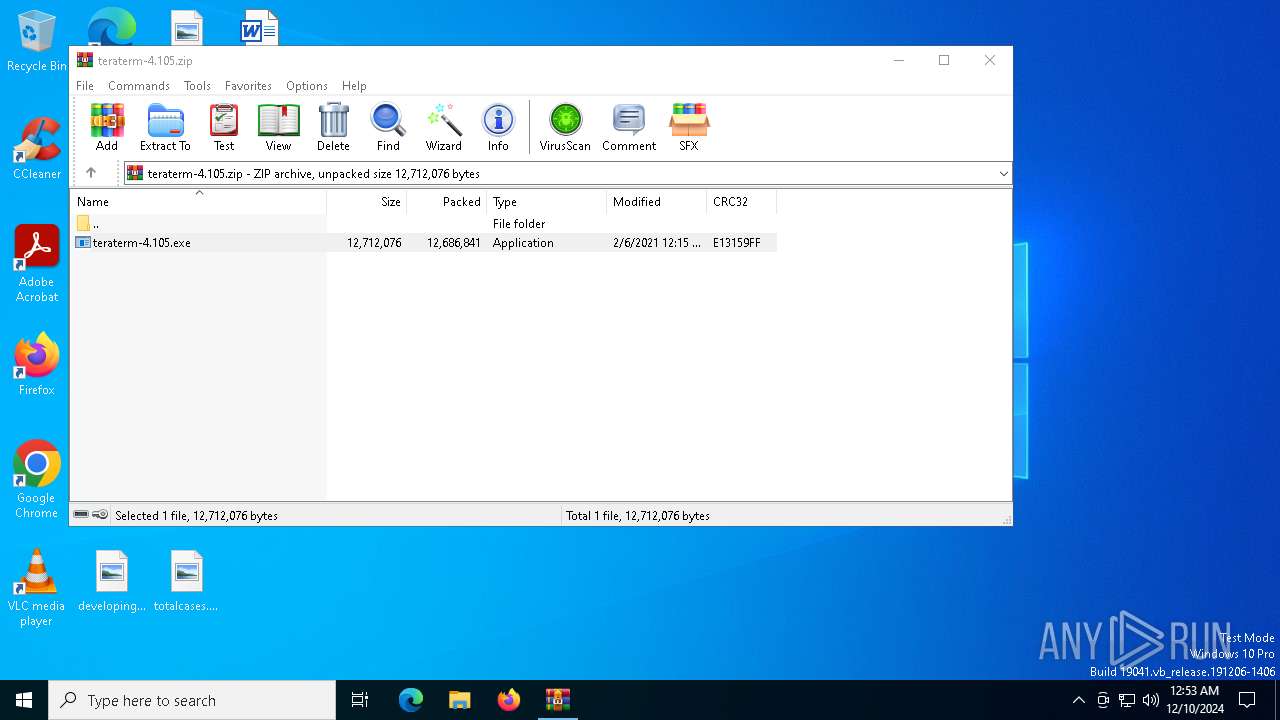
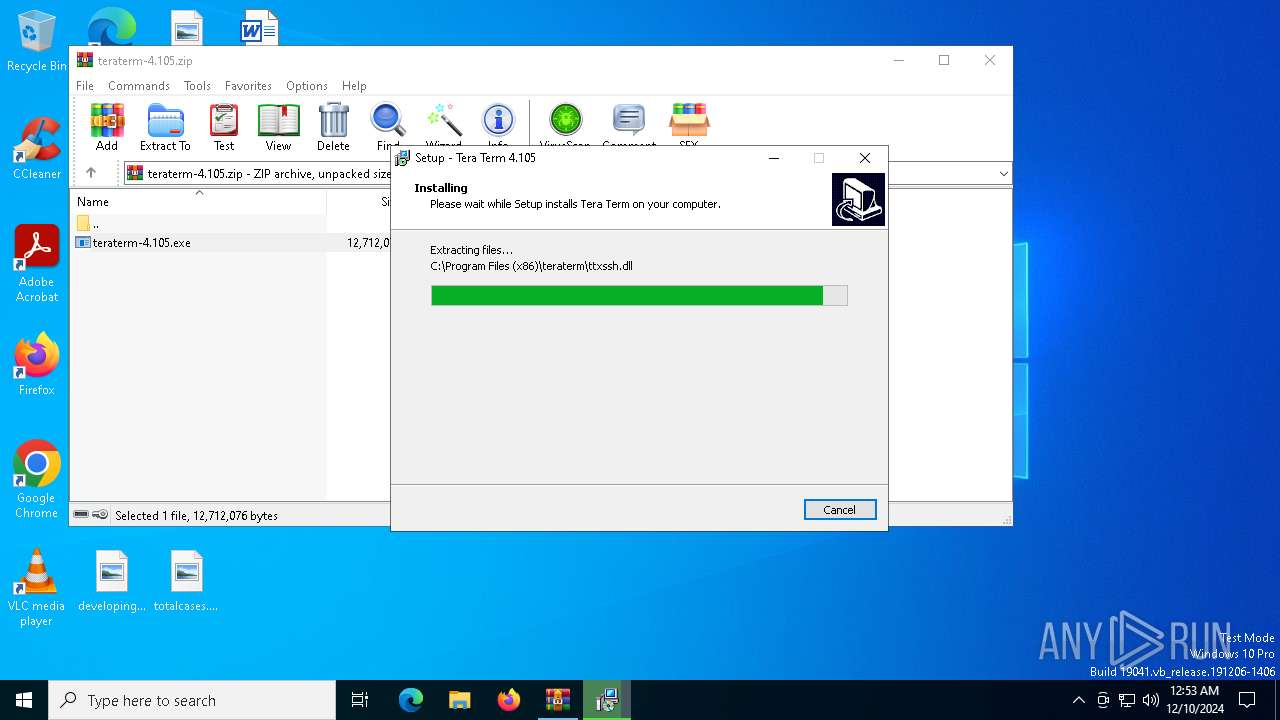
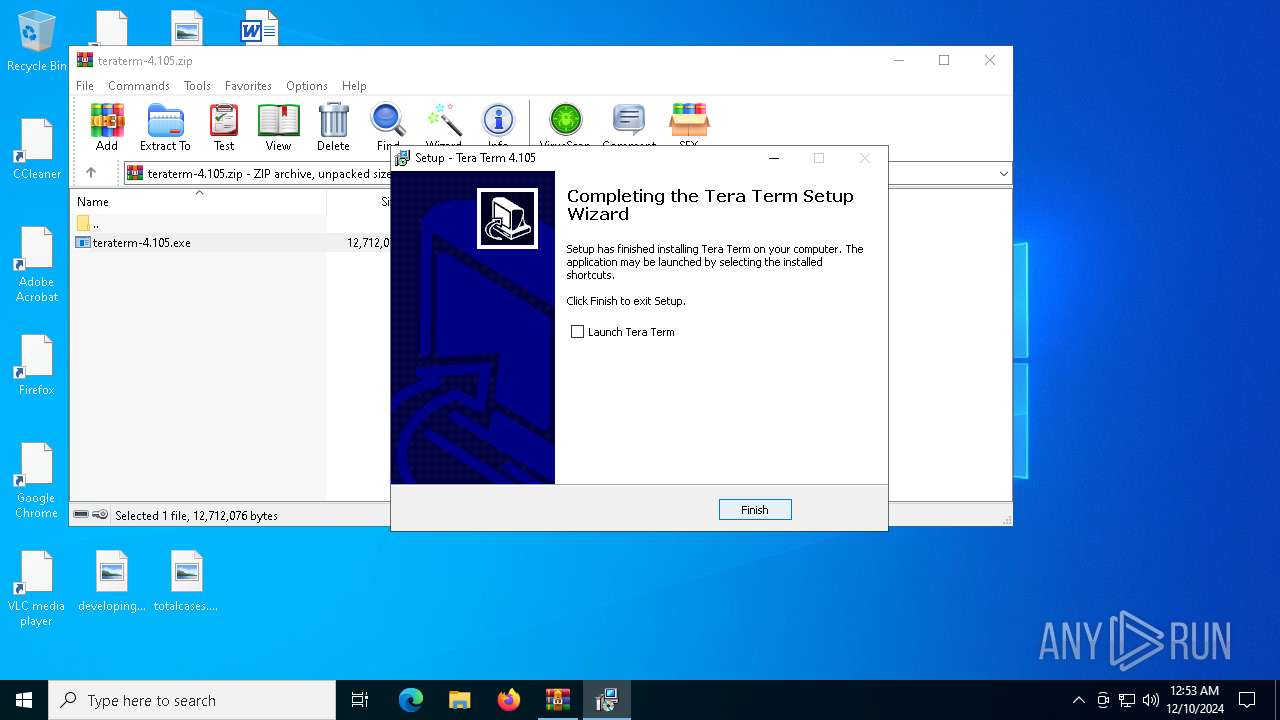
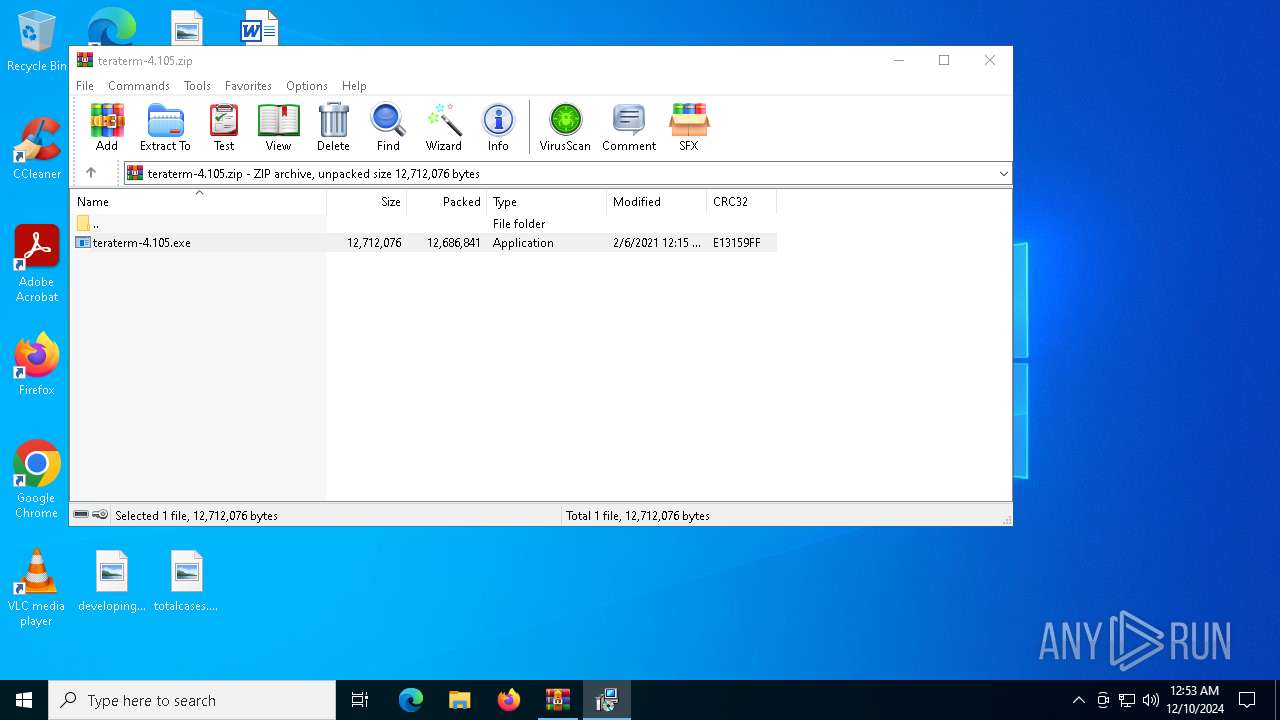
| File name: | teraterm-4.105.zip |
| Full analysis: | https://app.any.run/tasks/021b13fc-6b95-4e0e-b87a-f5a58b58b941 |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2024, 00:52:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | BDA9DD274FB8E4A48B9CE1F65A7D0E94 |
| SHA1: | 1D2B17FD56FBA8D050BAD51F103DA3874ED50DF9 |
| SHA256: | D9A9F6321898F20F032C650476BB533096A092C05CD512FD5E1EF795D11AA791 |
| SSDEEP: | 98304:nG949qJawbav+vr6y6hiQN9b6z9ucRwMq2IWhZ7mP8pk4dDz05OT3ZNP2ihQU7uR:XeNVbX3vGjwBnrjkC0TJejBd+R |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6432)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6432)
- teraterm-4.105.tmp (PID: 7036)
Executable content was dropped or overwritten
- teraterm-4.105.exe (PID: 7016)
- teraterm-4.105.exe (PID: 7116)
- teraterm-4.105.tmp (PID: 7140)
Reads the Windows owner or organization settings
- teraterm-4.105.tmp (PID: 7140)
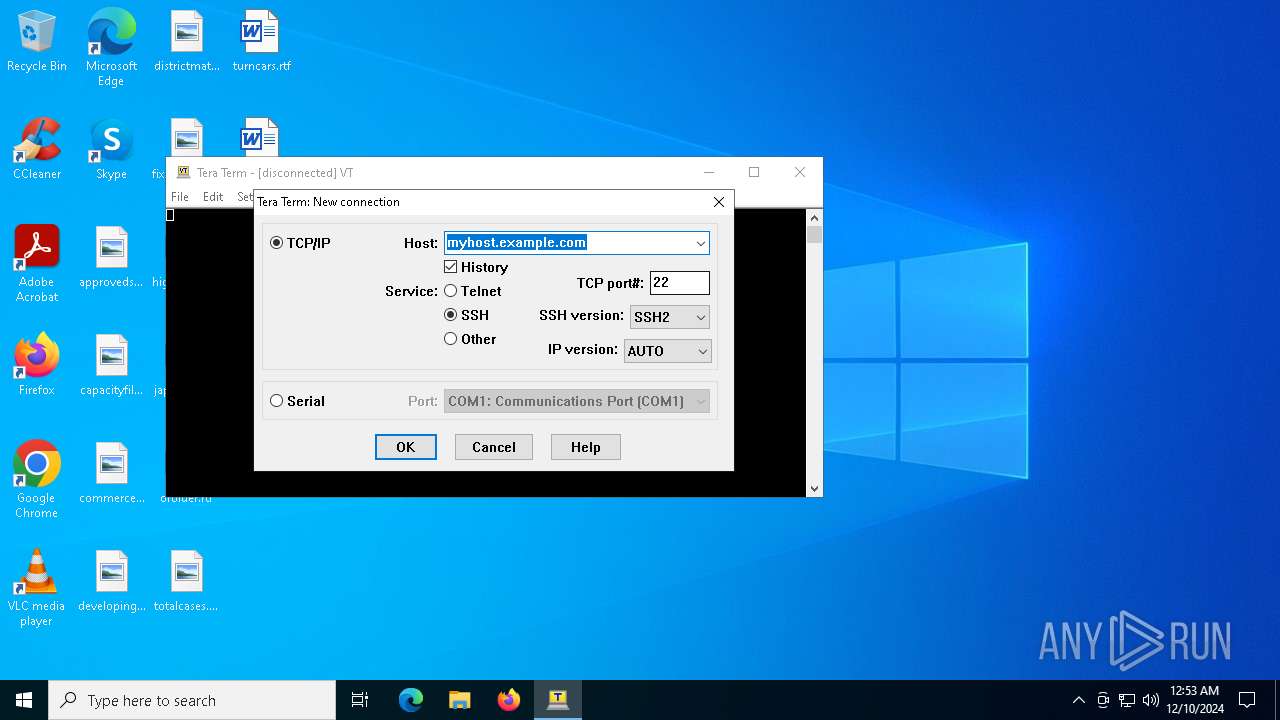
Connects to SSH
- ttermpro.exe (PID: 5572)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6432)
The process uses the downloaded file
- WinRAR.exe (PID: 6432)
Checks supported languages
- teraterm-4.105.exe (PID: 7016)
- teraterm-4.105.tmp (PID: 7036)
- teraterm-4.105.exe (PID: 7116)
- teraterm-4.105.tmp (PID: 7140)
- ttermpro.exe (PID: 5572)
Create files in a temporary directory
- teraterm-4.105.exe (PID: 7016)
- teraterm-4.105.exe (PID: 7116)
- teraterm-4.105.tmp (PID: 7140)
Reads the computer name
- teraterm-4.105.tmp (PID: 7036)
- teraterm-4.105.tmp (PID: 7140)
- ttermpro.exe (PID: 5572)
Process checks computer location settings
- teraterm-4.105.tmp (PID: 7036)
- ttermpro.exe (PID: 5572)
Creates files or folders in the user directory
- teraterm-4.105.tmp (PID: 7140)
Creates a software uninstall entry
- teraterm-4.105.tmp (PID: 7140)
Creates files in the program directory
- teraterm-4.105.tmp (PID: 7140)
Manual execution by a user
- ttermpro.exe (PID: 5572)
Process checks whether UAC notifications are on
- ttermpro.exe (PID: 5572)
Sends debugging messages
- ttermpro.exe (PID: 5572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:02:06 12:15:14 |
| ZipCRC: | 0xe13159ff |
| ZipCompressedSize: | 12686841 |
| ZipUncompressedSize: | 12712076 |
| ZipFileName: | teraterm-4.105.exe |
Total processes
136
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5572 | "C:\Program Files (x86)\teraterm\ttermpro.exe" | C:\Program Files (x86)\teraterm\ttermpro.exe | explorer.exe | ||||||||||||
User: admin Company: T. Teranishi, TeraTerm Project Integrity Level: MEDIUM Description: Tera Term Version: 4, 105, 0, 0 Modules
| |||||||||||||||
| 6432 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\teraterm-4.105.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
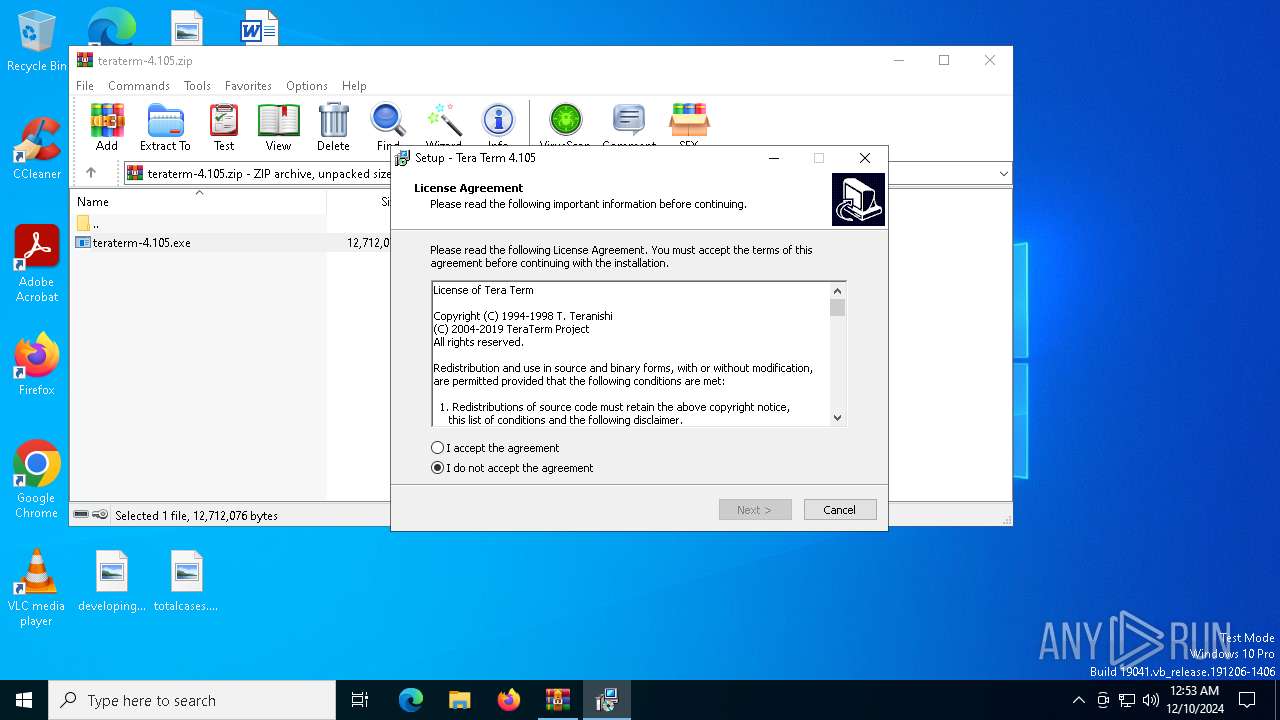
| 7016 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6432.30330\teraterm-4.105.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6432.30330\teraterm-4.105.exe | WinRAR.exe | ||||||||||||
User: admin Company: TeraTerm Project Integrity Level: MEDIUM Description: Tera Term Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 7036 | "C:\Users\admin\AppData\Local\Temp\is-JOP7N.tmp\teraterm-4.105.tmp" /SL5="$902CC,12449558,58368,C:\Users\admin\AppData\Local\Temp\Rar$EXa6432.30330\teraterm-4.105.exe" | C:\Users\admin\AppData\Local\Temp\is-JOP7N.tmp\teraterm-4.105.tmp | — | teraterm-4.105.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 7116 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6432.30330\teraterm-4.105.exe" /SPAWNWND=$702C6 /NOTIFYWND=$902CC | C:\Users\admin\AppData\Local\Temp\Rar$EXa6432.30330\teraterm-4.105.exe | teraterm-4.105.tmp | ||||||||||||
User: admin Company: TeraTerm Project Integrity Level: HIGH Description: Tera Term Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 7140 | "C:\Users\admin\AppData\Local\Temp\is-J2MFM.tmp\teraterm-4.105.tmp" /SL5="$B02B6,12449558,58368,C:\Users\admin\AppData\Local\Temp\Rar$EXa6432.30330\teraterm-4.105.exe" /SPAWNWND=$702C6 /NOTIFYWND=$902CC | C:\Users\admin\AppData\Local\Temp\is-J2MFM.tmp\teraterm-4.105.tmp | teraterm-4.105.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
2 858
Read events
2 812
Write events
46
Delete events
0
Modification events
| (PID) Process: | (6432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\teraterm-4.105.zip | |||
| (PID) Process: | (6432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7140) teraterm-4.105.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Tera Special (TrueType) |
Value: TSPECIAL1.TTF | |||
| (PID) Process: | (7140) teraterm-4.105.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Tera Term_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.6.1 (a) | |||
Executable files
42
Suspicious files
28
Text files
55
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7140 | teraterm-4.105.tmp | C:\Program Files (x86)\teraterm\is-L7SPA.tmp | executable | |
MD5:54A55F85996AAC12C6386877F5E2ED74 | SHA256:F9A5F9FA791D9627EE4E1675C0D0D4C2D8BAEA7981E959DD72DBC3FA417E66C9 | |||
| 7140 | teraterm-4.105.tmp | C:\Windows\Fonts\is-G3973.tmp | binary | |
MD5:2E743CD2B882CA1C1B25922792A2B122 | SHA256:F60767CEAE6383A9CB5A3EB50329440BCA99A27B3BE29D39AB959E8E41B926E8 | |||
| 7140 | teraterm-4.105.tmp | C:\Users\admin\AppData\Local\Temp\is-0H6J2.tmp\cygtool.dll | executable | |
MD5:38B1895BE38F7713474617FFC237D554 | SHA256:E8B4E2437405372F11F0FAAE773563FE10627DBCF2C796DC839F7AC17F409468 | |||
| 7140 | teraterm-4.105.tmp | C:\Program Files (x86)\teraterm\is-TJQJV.tmp | executable | |
MD5:8CCB9EF08FC7797941B3868D32995F27 | SHA256:FADBCCEE54DE35714E651A3F753F243CDAB1C3136F8643B9B67B92E282E47342 | |||
| 7140 | teraterm-4.105.tmp | C:\Program Files (x86)\teraterm\ttermpro.exe | executable | |
MD5:77654DD67441C29472677B15E1EC7760 | SHA256:824CA9775CEE77A62F171C8F1B2597E53573DC8DEB7F506E7780E53FC1FF20C6 | |||
| 7140 | teraterm-4.105.tmp | C:\Program Files (x86)\teraterm\ttpcmn.dll | executable | |
MD5:217C35866ACEBF0EEADC884F40CB9634 | SHA256:B3090E22C2EE1E21E463CD618275AD02AB26693C4983ED20BF65872F7FF01A08 | |||
| 7140 | teraterm-4.105.tmp | C:\Program Files (x86)\teraterm\ttpfile.dll | executable | |
MD5:8CCB9EF08FC7797941B3868D32995F27 | SHA256:FADBCCEE54DE35714E651A3F753F243CDAB1C3136F8643B9B67B92E282E47342 | |||
| 7140 | teraterm-4.105.tmp | C:\Program Files (x86)\teraterm\is-TQV8M.tmp | executable | |
MD5:77654DD67441C29472677B15E1EC7760 | SHA256:824CA9775CEE77A62F171C8F1B2597E53573DC8DEB7F506E7780E53FC1FF20C6 | |||
| 6432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6432.30330\teraterm-4.105.exe | executable | |
MD5:73B752D33E27B75DAEA79BF72FC30885 | SHA256:6EA1B0A64533014ED4CB92F0D496B73F242BF10D2A9A5AF62F3439F9DCB01245 | |||
| 7016 | teraterm-4.105.exe | C:\Users\admin\AppData\Local\Temp\is-JOP7N.tmp\teraterm-4.105.tmp | executable | |
MD5:1AFBD25DB5C9A90FE05309F7C4FBCF09 | SHA256:3BB0EE5569FE5453C6B3FA25AA517B925D4F8D1F7BA3475E58FA09C46290658C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6172 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1556 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1556 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4864 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
ttermpro.exe | google.com
|
ttermpro.exe | Release link failed. (1)
|
ttermpro.exe | myhost.example.com
|
ttermpro.exe | Release link failed. (1)
|
ttermpro.exe | 192.0.2.1
|
ttermpro.exe | Release shell link failed. (1)
|
ttermpro.exe | Release shell link failed. (1)
|
ttermpro.exe | [2001:db8:1:2:8401:2ff:fe03:405]
|
ttermpro.exe | Release shell link failed. (1)
|
ttermpro.exe | Release link failed. (1)
|