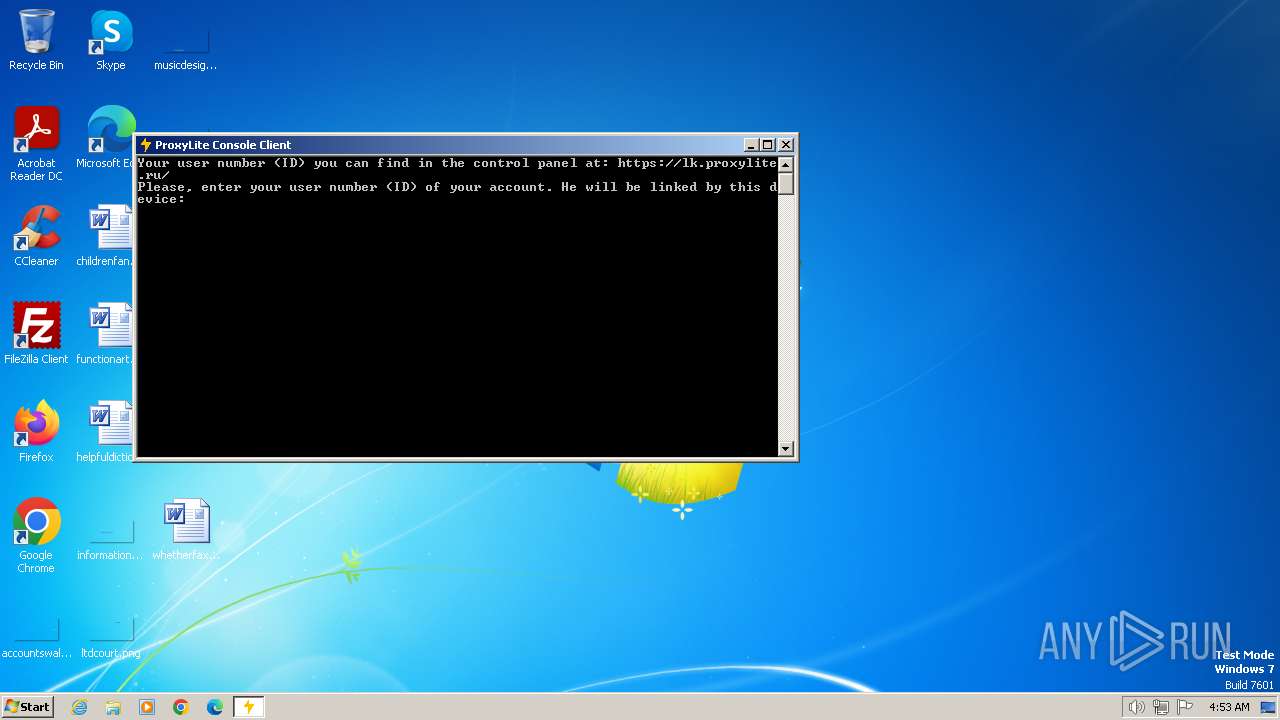
| File name: | ProxyLite.Windows.Console.exe |
| Full analysis: | https://app.any.run/tasks/438bdbcf-ee87-4ead-b002-654af7669ad7 |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2024, 04:53:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | E7D93229D4D58549F0875B5A7A1D564F |
| SHA1: | CE9D39A142F112B787BF9B36AA23EC646A1C975C |
| SHA256: | D99C9862C2C0E2F76074E48281F6C9183B5CD3D9DA0851F56714C860D57A0CBC |
| SSDEEP: | 1536:CxAejq3ZLdCDVLEYkOw/V+iGSD5g5TICWgz9HplKrOLWY76GIZzIZ+U6ciz0UM8h:50Wgz9HPKIWY7ZIZzIZ+U6Rz0Up9xR |
MALICIOUS
Creates a writable file in the system directory
- ProxyService.exe (PID: 2124)
Drops the executable file immediately after the start
- ProxyLite.Windows.Console.exe (PID: 3216)
SUSPICIOUS
Reads the Internet Settings
- ProxyLite.Windows.Console.exe (PID: 3216)
Adds/modifies Windows certificates
- ProxyLite.Windows.Console.exe (PID: 3216)
Executable content was dropped or overwritten
- ProxyLite.Windows.Console.exe (PID: 3216)
Reads settings of System Certificates
- ProxyLite.Windows.Console.exe (PID: 3216)
Connects to unusual port
- ProxyService.exe (PID: 2124)
Executes as Windows Service
- ProxyService.exe (PID: 2124)
INFO
Checks supported languages
- ProxyLite.Windows.Console.exe (PID: 3216)
- ProxyService.exe (PID: 2124)
Reads the software policy settings
- ProxyService.exe (PID: 2124)
- ProxyLite.Windows.Console.exe (PID: 3216)
Reads Environment values
- ProxyLite.Windows.Console.exe (PID: 3216)
- ProxyService.exe (PID: 2124)
Reads the computer name
- ProxyService.exe (PID: 2124)
- ProxyLite.Windows.Console.exe (PID: 3216)
Reads the machine GUID from the registry
- ProxyService.exe (PID: 2124)
- ProxyLite.Windows.Console.exe (PID: 3216)
Creates files or folders in the user directory
- ProxyLite.Windows.Console.exe (PID: 3216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2059:09:25 15:53:08+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 153600 |
| InitializedDataSize: | 74240 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2772e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | ProxyLite Console Client Application |
| CompanyName: | Petrov Ilya Pavlovich IP |
| FileDescription: | ProxyLite Console Client |
| FileVersion: | 1.0.0.0 |
| InternalName: | ProxyLite.Windows.Console.exe |
| LegalCopyright: | - |
| LegalTrademarks: | ProxyLite |
| OriginalFileName: | ProxyLite.Windows.Console.exe |
| ProductName: | ProxyLite Console Client |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
43
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2124 | C:\Users\admin\AppData\Roaming\ProxyLite\ProxyService\ProxyService.exe | C:\Users\admin\AppData\Roaming\ProxyLite\ProxyService\ProxyService.exe | services.exe | ||||||||||||
User: SYSTEM Company: Petrov Ilya Pavlovich IP Integrity Level: SYSTEM Description: ProxyService Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2472 | "C:\Users\admin\AppData\Local\Temp\ProxyLite.Windows.Console.exe" | C:\Users\admin\AppData\Local\Temp\ProxyLite.Windows.Console.exe | — | explorer.exe | |||||||||||
User: admin Company: Petrov Ilya Pavlovich IP Integrity Level: MEDIUM Description: ProxyLite Console Client Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3216 | "C:\Users\admin\AppData\Local\Temp\ProxyLite.Windows.Console.exe" | C:\Users\admin\AppData\Local\Temp\ProxyLite.Windows.Console.exe | explorer.exe | ||||||||||||
User: admin Company: Petrov Ilya Pavlovich IP Integrity Level: HIGH Description: ProxyLite Console Client Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
10 020
Read events
9 956
Write events
59
Delete events
5
Modification events
| (PID) Process: | (3216) ProxyLite.Windows.Console.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ProxyLite_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3216) ProxyLite.Windows.Console.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ProxyLite_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3216) ProxyLite.Windows.Console.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ProxyLite_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3216) ProxyLite.Windows.Console.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ProxyLite_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3216) ProxyLite.Windows.Console.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ProxyLite_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3216) ProxyLite.Windows.Console.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ProxyLite_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3216) ProxyLite.Windows.Console.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ProxyLite_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3216) ProxyLite.Windows.Console.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ProxyLite_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3216) ProxyLite.Windows.Console.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ProxyLite_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3216) ProxyLite.Windows.Console.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ProxyLite_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
1
Suspicious files
5
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2124 | ProxyService.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4C147ED6F106964FDE78B3E86C788386 | binary | |
MD5:65BB290BB406E2DB409854A013CEB08D | SHA256:9924EB5DEEDB062DB9270A2D47895E7F6E1D51180DE2069301C2C6D4FDAC301B | |||
| 2124 | ProxyService.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:BC6331DAAFC2C881AB095A98C5F848C7 | SHA256:192459252A698CA72407ACDCB954DDA257D18E5B91250C7DDEBC57041C5B2799 | |||
| 2124 | ProxyService.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\15488054372351F63F9809E06904943B | binary | |
MD5:0E08BE25C6BF1BC9ABBDE409AC8B833F | SHA256:89227EB808F22C098E3BEA5145DA47FF1A28965C5CB7B6F94F642E2EED42337F | |||
| 2124 | ProxyService.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4C147ED6F106964FDE78B3E86C788386 | binary | |
MD5:C0CC4C46710907F5D724D37876E3221F | SHA256:EC1B654ED50FF44C6DDB363F7A8C0CBE270A8CA413B49582F60C33EDA904F0F6 | |||
| 2124 | ProxyService.exe | C:\Windows\TEMP\Tar4C76.tmp | binary | |
MD5:DD73CEAD4B93366CF3465C8CD32E2796 | SHA256:A6752B7851B591550E4625B832A393AABCC428DE18D83E8593CD540F7D7CAE22 | |||
| 2124 | ProxyService.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 2124 | ProxyService.exe | C:\Windows\TEMP\Cab4C75.tmp | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 2124 | ProxyService.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\15488054372351F63F9809E06904943B | text | |
MD5:4FF7F7A664338FD16C33BDA2A889BF8E | SHA256:F2131FE0E17399D9B19AA9804A7654847BFCE7BA250A6C9022E32388B33326E5 | |||
| 3216 | ProxyLite.Windows.Console.exe | C:\Users\admin\AppData\Roaming\ProxyLite\ProxyService\ProxyService.exe | executable | |
MD5:9E5CB73EA46A0BC10EC45FB237162284 | SHA256:180907224884B5159CD1BC1BB114199A44D0D0463E9EB1FBE863436105E414B3 | |||
| 3216 | ProxyLite.Windows.Console.exe | C:\Users\admin\AppData\Roaming\ProxyLite\ProxyService\userid.ini | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
10
DNS requests
4
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2124 | ProxyService.exe | GET | 200 | 104.21.42.210:80 | http://oscp.cocbuilder.su/Main/CSS.crt | unknown | binary | 1.13 Kb | unknown |
2124 | ProxyService.exe | GET | 200 | 104.21.42.210:80 | http://oscp.cocbuilder.su/Web/1/CWV-New2021.crt | unknown | text | 1.76 Kb | unknown |
2124 | ProxyService.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2b656f2b369344e0 | unknown | compressed | 67.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3216 | ProxyLite.Windows.Console.exe | 185.135.81.106:443 | app.proxylite.ru | Adman LLC | RU | unknown |
2124 | ProxyService.exe | 185.135.81.106:443 | app.proxylite.ru | Adman LLC | RU | unknown |
2124 | ProxyService.exe | 185.135.81.106:51022 | app.proxylite.ru | Adman LLC | RU | unknown |
2124 | ProxyService.exe | 104.21.42.210:80 | oscp.cocbuilder.su | CLOUDFLARENET | — | unknown |
2124 | ProxyService.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2124 | ProxyService.exe | 185.135.81.106:51020 | app.proxylite.ru | Adman LLC | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
app.proxylite.ru |
| unknown |
oscp.cocbuilder.su |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
srv.proxylite.ru |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
2124 | ProxyService.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
2124 | ProxyService.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |