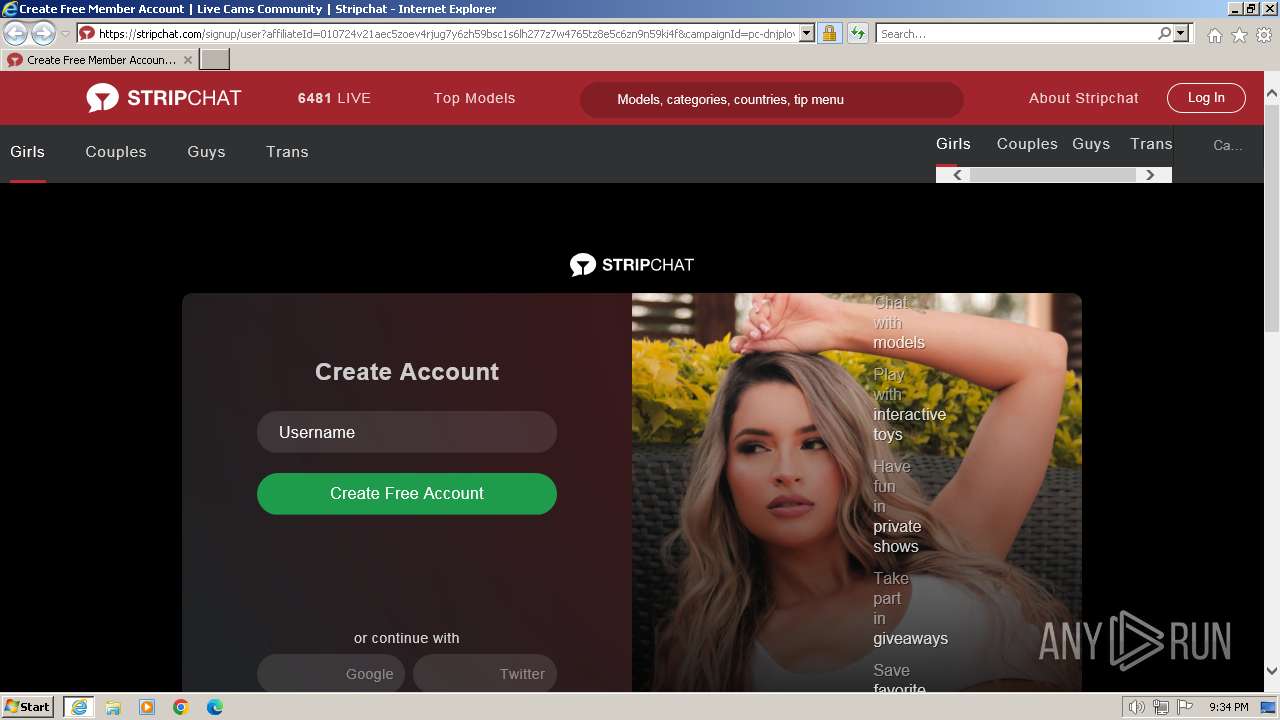
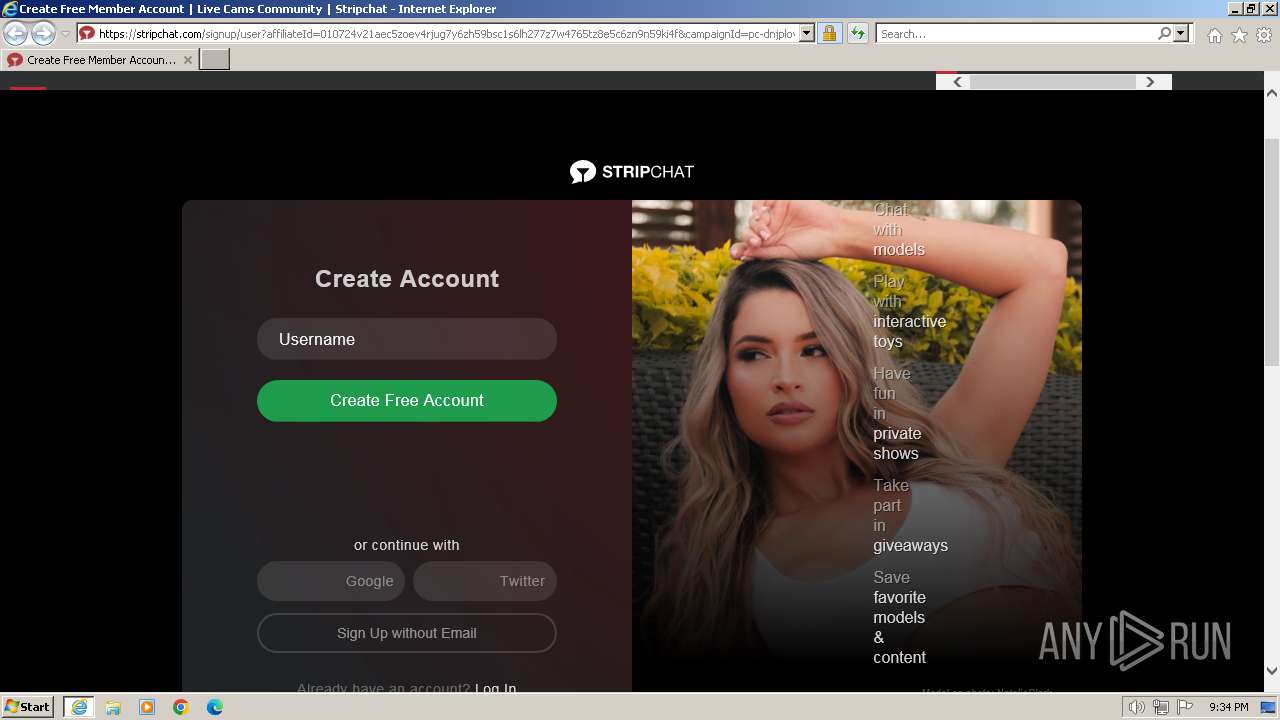
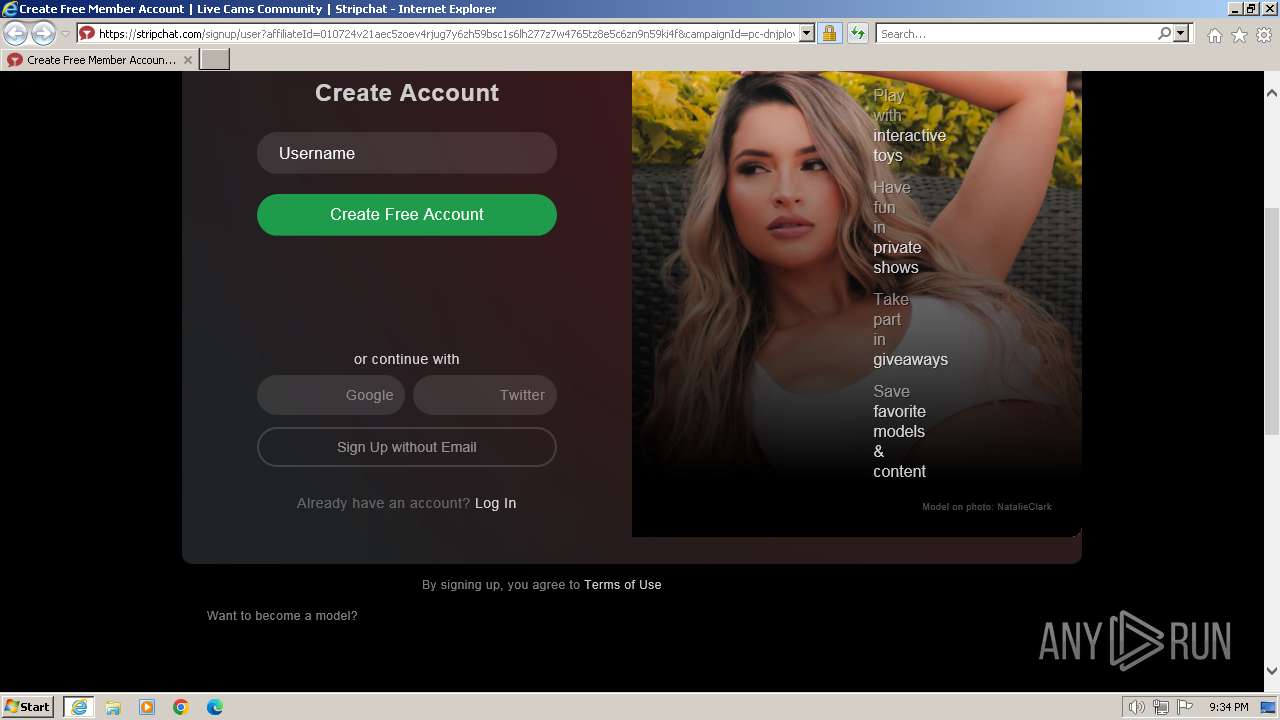
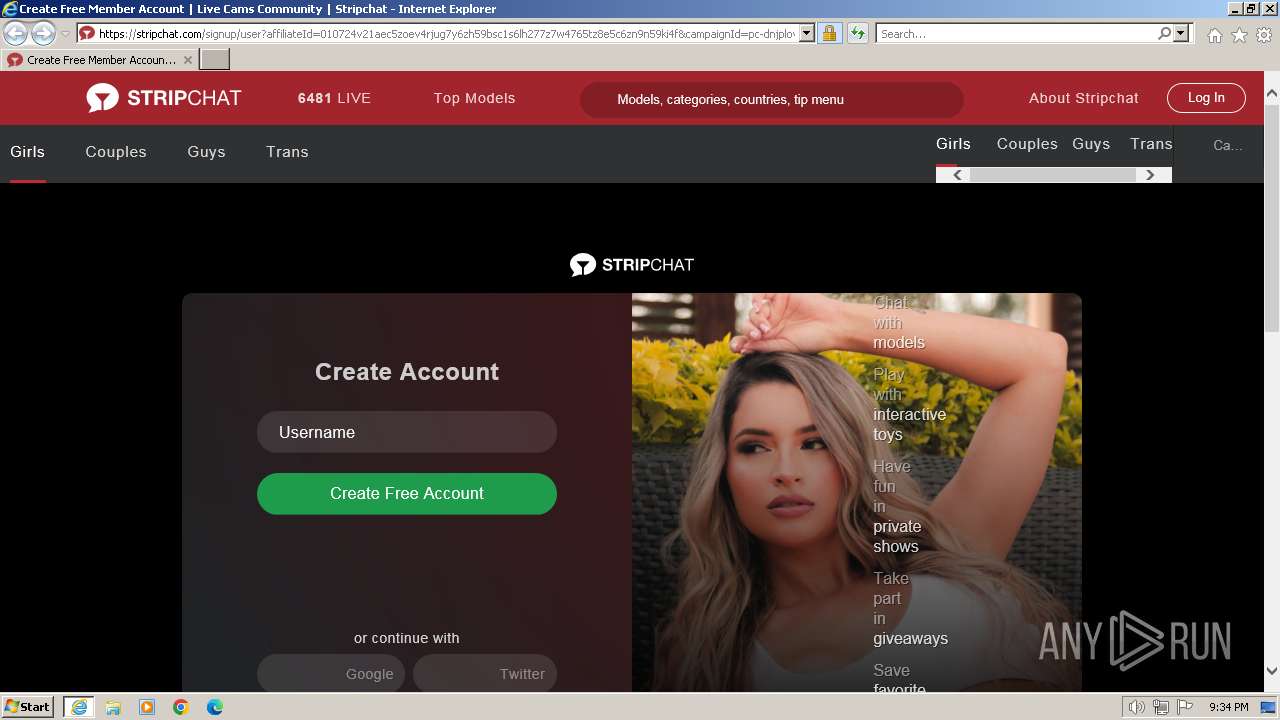
| URL: | p.rapolok.com/go/467596/703813/aHR0cHMlM0EvL3JhcGJlaC5uZXQv?cb=7223329022344520 |
| Full analysis: | https://app.any.run/tasks/c70ae070-f719-4394-9a7f-4e06354073a7 |
| Verdict: | Malicious activity |
| Analysis date: | July 01, 2024, 20:34:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C3D063B5E25909BFC3F6A6E7711C4BD1 |
| SHA1: | 9B0B68BCD2CB403D06B7F5E8FA897F1ACF8DF723 |
| SHA256: | D9987C8A6C7E98F3B1876F838AFB91EA2461D68208CC76F0B37A2E8A4B566164 |
| SSDEEP: | 3:BEVSKkDKV1GtUuvrJPUx/RcV2R2Fn:yV5kAOvdPUx/Nmn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3368 | "C:\Program Files\Internet Explorer\iexplore.exe" "p.rapolok.com/go/467596/703813/aHR0cHMlM0EvL3JhcGJlaC5uZXQv?cb=7223329022344520" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3568 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3368 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
19 772
Read events
19 658
Write events
87
Delete events
27
Modification events
| (PID) Process: | (3368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 336365712 | |||
| (PID) Process: | (3368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31116278 | |||
| (PID) Process: | (3368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 636526962 | |||
| (PID) Process: | (3368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31116278 | |||
| (PID) Process: | (3368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
3
Suspicious files
20
Text files
68
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3568 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\O3PY14QZ.txt | text | |
MD5:E300A93A5B8133BBD76D2EF261F66C6F | SHA256:8F1667B7DE507FE89AECC089D8F058199BBFB9960662026E3D258871BE263FE1 | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:4DAF0AD3F40614A0ED7AF25A7A289EB0 | SHA256:635DEF7DF1D8A3434E0FA5CD411554CF782E38D71DF6D77A329CDE173FF3174B | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:06F676EA4C436E53FED434B7036E4A3C | SHA256:B7A64BB91DE5331FF22F81CF67EB8D8919A62BBA92CE69D098EBD0847802F3A0 | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\IDPDDZ8A.txt | text | |
MD5:52D3FCFCFD9188F3BD0A8515D28245FD | SHA256:EB90644C2D75929018EA057AFF48C4969B5CF758569550E59863BF8F9242F497 | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:3C30E449044FA26449EFFE9B3DDA7E38 | SHA256:608541163DC2A146D06FB609BBB96DFABA1B21B532B33E8A5C7216591A6DDE48 | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\32AWPK2H.txt | text | |
MD5:3CDB5248FD994960BF4AF24A38EE5214 | SHA256:89177048799E863CE11E1DFCF0D9DD853CCDB2A24A5115A9C8D96E263E7930EF | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\HXZXM8LQ.txt | text | |
MD5:DBF1ADA6DA1A862A1314D7D63693E6C6 | SHA256:1FE3E0578B841EF5BC9F9FA04BCEF87CD56D29DA1412567E7BD17E7C394D85B7 | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:2F9BEE936590BC2028C105C3498AAA6F | SHA256:9201749F4881AE2728050486A4A1284D807082158EC8BA6A130F745A9BB6223F | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\SL6ABE4E.txt | text | |
MD5:5F6ED49C1E700A714FDFAEEC4B4B7454 | SHA256:5CEBE95CCCCC1F3DD11CA1E5EC802EFC16C49A595A64D5896937906F93AF4AA5 | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\5P0GSZG3.txt | text | |
MD5:BB13C70041C60B7D2EB8045F1F041C86 | SHA256:1C8D4C74B13D4547AF7901696AD5C49EABD54AB17FAC26FCDCC8CC7955CB9C6B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
47
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3568 | iexplore.exe | GET | 200 | 54.166.210.213:80 | http://p.rapolok.com/go/467596/703813/aHR0cHMlM0EvL3JhcGJlaC5uZXQv?cb=7223329022344520 | unknown | — | — | unknown |
3368 | iexplore.exe | GET | 404 | 54.166.210.213:80 | http://p.rapolok.com/favicon.ico | unknown | — | — | unknown |
3568 | iexplore.exe | GET | 304 | 23.50.131.213:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?efa5239e04139ffd | unknown | — | — | unknown |
3568 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | unknown |
3568 | iexplore.exe | GET | 304 | 23.50.131.213:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6f6b9a12cba45008 | unknown | — | — | unknown |
3568 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | unknown |
3568 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | — | — | unknown |
3568 | iexplore.exe | GET | 200 | 54.166.210.213:80 | http://p.rapolok.com/ad/ad?p=467596&w=703813&t=6c5d9d8686932c95&r=aHR0cHMlM0EvL3JhcGJlaC5uZXQv&vw=1280&vh=621 | unknown | — | — | unknown |
3568 | iexplore.exe | GET | 200 | 23.50.131.213:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?7fb48b05bef8bbe6 | unknown | — | — | unknown |
3568 | iexplore.exe | GET | 200 | 23.50.131.213:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?676030978224a799 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
3568 | iexplore.exe | 54.166.210.213:80 | p.rapolok.com | AMAZON-AES | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3368 | iexplore.exe | 54.166.210.213:80 | p.rapolok.com | AMAZON-AES | US | unknown |
3568 | iexplore.exe | 188.114.97.3:443 | dreams.ninja | CLOUDFLARENET | NL | unknown |
3568 | iexplore.exe | 23.50.131.213:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3568 | iexplore.exe | 142.250.181.227:80 | c.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
p.rapolok.com |
| unknown |
dreams.ninja |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
c.pki.goog |
| unknown |
go.bbrdbr.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
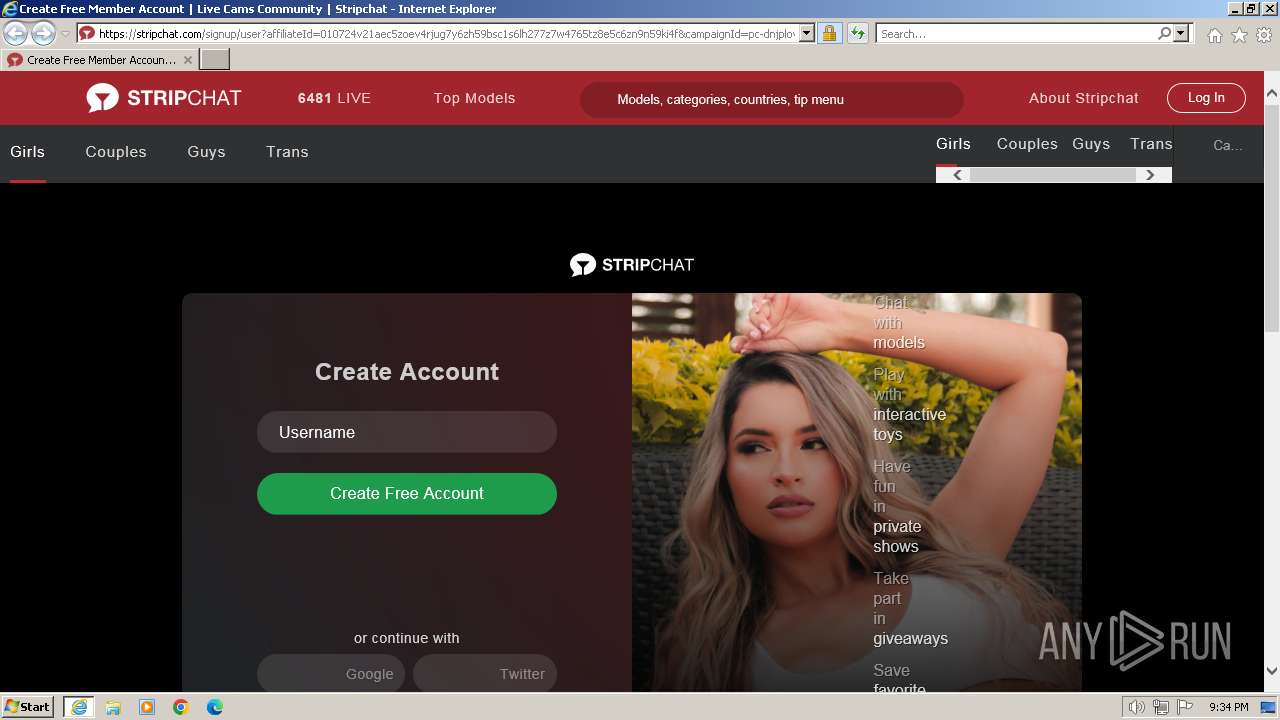
stripchat.com |
| malicious |
assets.strpst.com |
| unknown |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |