| File name: | Grand_Theft_Auto_V.exe |
| Full analysis: | https://app.any.run/tasks/68b4c0a3-ff56-4347-96a3-42a6f8b74f1c |
| Verdict: | Malicious activity |
| Analysis date: | April 22, 2024, 20:57:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1B76A21E20BF2D7033E8855983032223 |
| SHA1: | D433C64A2C387E37BB68BC5D6356E4C20E45E52F |
| SHA256: | D98731BBAE8DAB5DE30C091946AD9A80D8EDD1CCD801A8ACCB63E4591E568D4E |
| SSDEEP: | 98304:qsQ44gdhpHKfhTb9EK+2we8ZR9EiYoI+6zfuMaEDnwoAcd1973LqhYArKnwxhtiC:0iDgNPKAD15+9nXMOWb9Xi |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 3664)
Drops the executable file immediately after the start
- Grand_Theft_Auto_V.exe (PID: 3768)
Changes powershell execution policy (Bypass)
- [Grand_Theft_Auto_V - Game PC].exe (PID: 3384)
Run PowerShell with an invisible window
- powershell.exe (PID: 3664)
SUSPICIOUS
Process drops legitimate windows executable
- Grand_Theft_Auto_V.exe (PID: 3768)
Drops 7-zip archiver for unpacking
- Grand_Theft_Auto_V.exe (PID: 3768)
Starts POWERSHELL.EXE for commands execution
- [Grand_Theft_Auto_V - Game PC].exe (PID: 3384)
Reads security settings of Internet Explorer
- Grand_Theft_Auto_V.exe (PID: 3768)
The process creates files with name similar to system file names
- Grand_Theft_Auto_V.exe (PID: 3768)
Reads the Internet Settings
- [Grand_Theft_Auto_V - Game PC].exe (PID: 3384)
- Grand_Theft_Auto_V.exe (PID: 3768)
Executable content was dropped or overwritten
- Grand_Theft_Auto_V.exe (PID: 3768)
INFO
Checks supported languages
- Grand_Theft_Auto_V.exe (PID: 3768)
- [Grand_Theft_Auto_V - Game PC].exe (PID: 3384)
Reads the computer name
- Grand_Theft_Auto_V.exe (PID: 3768)
- [Grand_Theft_Auto_V - Game PC].exe (PID: 3384)
Create files in a temporary directory
- Grand_Theft_Auto_V.exe (PID: 3768)
Reads the machine GUID from the registry
- [Grand_Theft_Auto_V - Game PC].exe (PID: 3384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:16 12:31:25+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 208384 |
| InitializedDataSize: | 262144 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x205e0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
38
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3384 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\[Grand_Theft_Auto_V - Game PC].exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\[Grand_Theft_Auto_V - Game PC].exe | — | Grand_Theft_Auto_V.exe | |||||||||||
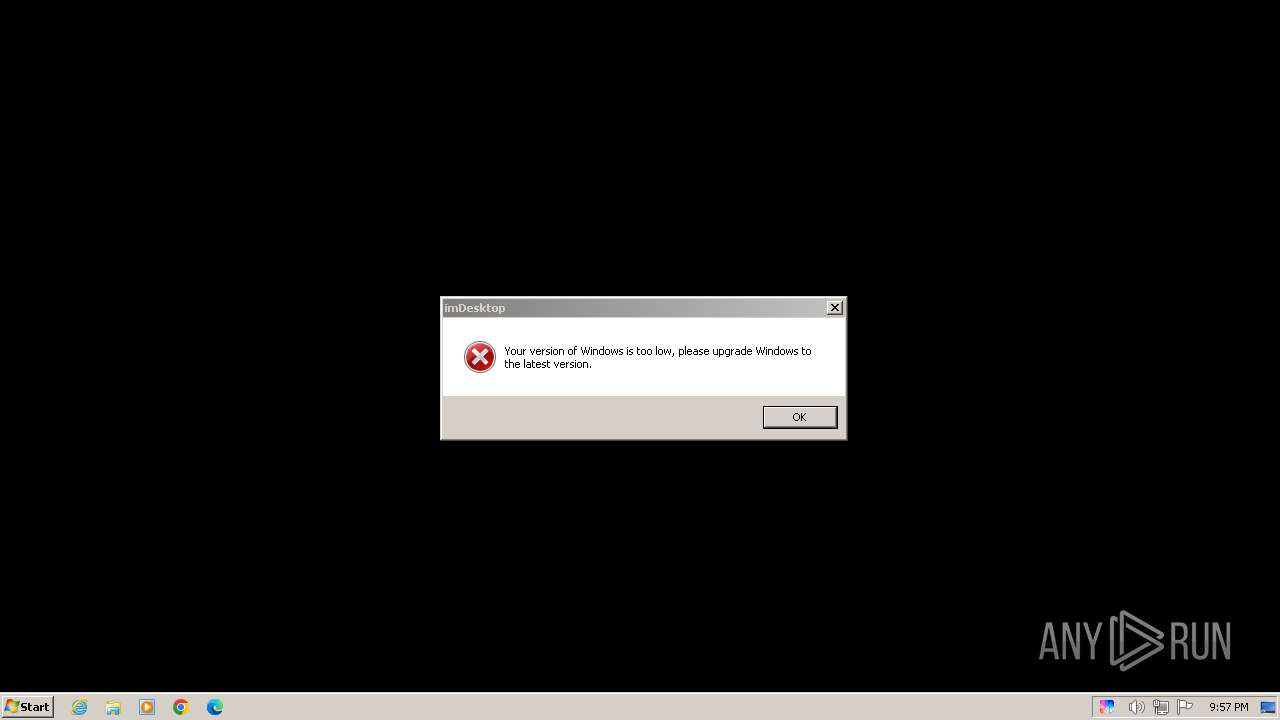
User: admin Company: YL Computing Integrity Level: MEDIUM Description: imDesktop Exit code: 3221225547 Version: 1.3.2.0 Modules
| |||||||||||||||
| 3664 | "powershell.exe" -WindowStyle Hidden -ExecutionPolicy Bypass -Command "(Get-CimInstance -ClassName Win32_VideoController).Caption;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | [Grand_Theft_Auto_V - Game PC].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3768 | "C:\Users\admin\Downloads\Grand_Theft_Auto_V.exe" | C:\Users\admin\Downloads\Grand_Theft_Auto_V.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
6 129
Read events
6 117
Write events
11
Delete events
1
Modification events
| (PID) Process: | (3768) Grand_Theft_Auto_V.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3768) Grand_Theft_Auto_V.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3768) Grand_Theft_Auto_V.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3768) Grand_Theft_Auto_V.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3384) [Grand_Theft_Auto_V - Game PC].exe | Key: | HKEY_CURRENT_USER\Software\imDesktop\Registration |
| Operation: | write | Name: | UsedTimes |
Value: 1 | |||
| (PID) Process: | (3384) [Grand_Theft_Auto_V - Game PC].exe | Key: | HKEY_CURRENT_USER\Software\imDesktop\Registration |
| Operation: | write | Name: | FirstRunTime |
Value: 4/22/2024 9:57:25 PM | |||
| (PID) Process: | (3384) [Grand_Theft_Auto_V - Game PC].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: [Grand_Theft_Auto_V - Game PC].exe | |||
| (PID) Process: | (3384) [Grand_Theft_Auto_V - Game PC].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{C8C9E113-A22C-4E19-B054-75962DF96BBE} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
9
Suspicious files
3
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3768 | Grand_Theft_Auto_V.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\MetroAssets | — | |
MD5:— | SHA256:— | |||
| 3768 | Grand_Theft_Auto_V.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Hardcodet.Wpf.TaskbarNotification.dll | executable | |
MD5:D5D708E9E7625AB2C4AC1C1FAA099350 | SHA256:F6FADF0375D22512B2B3F075362433C0DE173ADFB290B4D8999CDCB7ACEDB0B2 | |||
| 3768 | Grand_Theft_Auto_V.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\ControlzEx.dll | executable | |
MD5:2D5035CB5A3678F2C2F5A889BD384813 | SHA256:424CBE8F24A62C330149DBE0B80E214A984950C3B79B067058671608229FC2ED | |||
| 3768 | Grand_Theft_Auto_V.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Microsoft.WindowsAPICodePack.dll | executable | |
MD5:ACE419174E1E0C792D028F25F60D6E5F | SHA256:90D56B0A1C7E631E5A12985F9B7CC943A1EBC31E40EC53D56DC9149BBA74BA24 | |||
| 3768 | Grand_Theft_Auto_V.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\MahApps.Metro.dll | executable | |
MD5:D0875DF0EFA5AA164ED3A1572CBAD9DC | SHA256:3EA99C14E2B2366DF2EE1281744F18B031E6CB0F7D98EFCCADA8A98D86821D29 | |||
| 3768 | Grand_Theft_Auto_V.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Microsoft.WindowsAPICodePack.Shell.dll | executable | |
MD5:18A46202A1636B985208E2183D756617 | SHA256:513D386FC084AD355D1A8668D8B4E43CC3B21F135AC3EABBC6B96ADEB3EE9E84 | |||
| 3768 | Grand_Theft_Auto_V.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\[Grand_Theft_Auto_V - Game PC].exe | executable | |
MD5:79B862F83A5BFA3FB5011CABF9D47A63 | SHA256:3CA1410D20BFD9CD35C8F9B21D2958C6973E608CAEDD726A01199CDF747B3CD7 | |||
| 3768 | Grand_Theft_Auto_V.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\lang\Chinese(Simplified).png | image | |
MD5:18BD6697BC44BCFAA606AEC883FDF1C4 | SHA256:3705C17E9A6CF982234898D0269B94427FB3B1978BECE5CF4F3A6C3BF518DA70 | |||
| 3768 | Grand_Theft_Auto_V.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\lang\English.png | image | |
MD5:00214D9E4E6155A04E3997D121641C98 | SHA256:1037BB804C8DA171FB1869872BCD24AA1F0C96AD8CE783861DFF91D3174D12A7 | |||
| 3768 | Grand_Theft_Auto_V.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\lang\English.xml | xml | |
MD5:2091E6D656AE235A0E7977B0D5A51CE3 | SHA256:C3CC0E93F9FFF36858CA43188BFD6B67B39EE207B373C8A1601B973B2F07395A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |