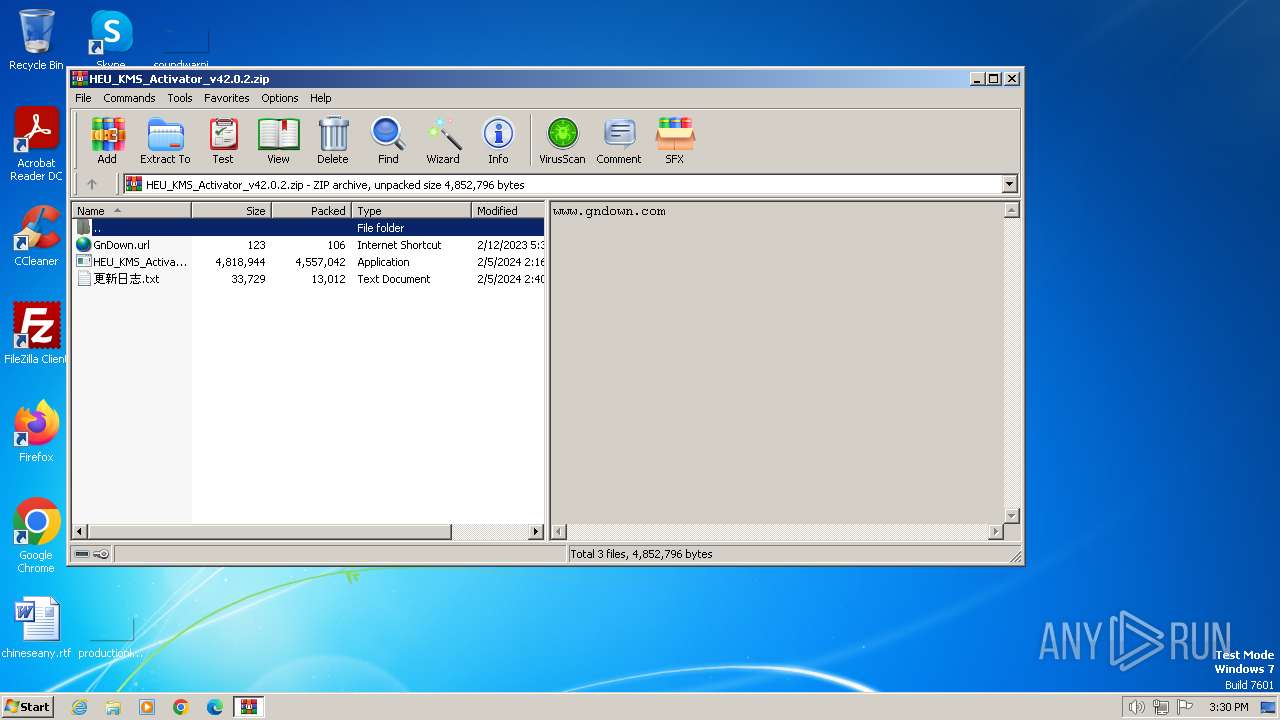
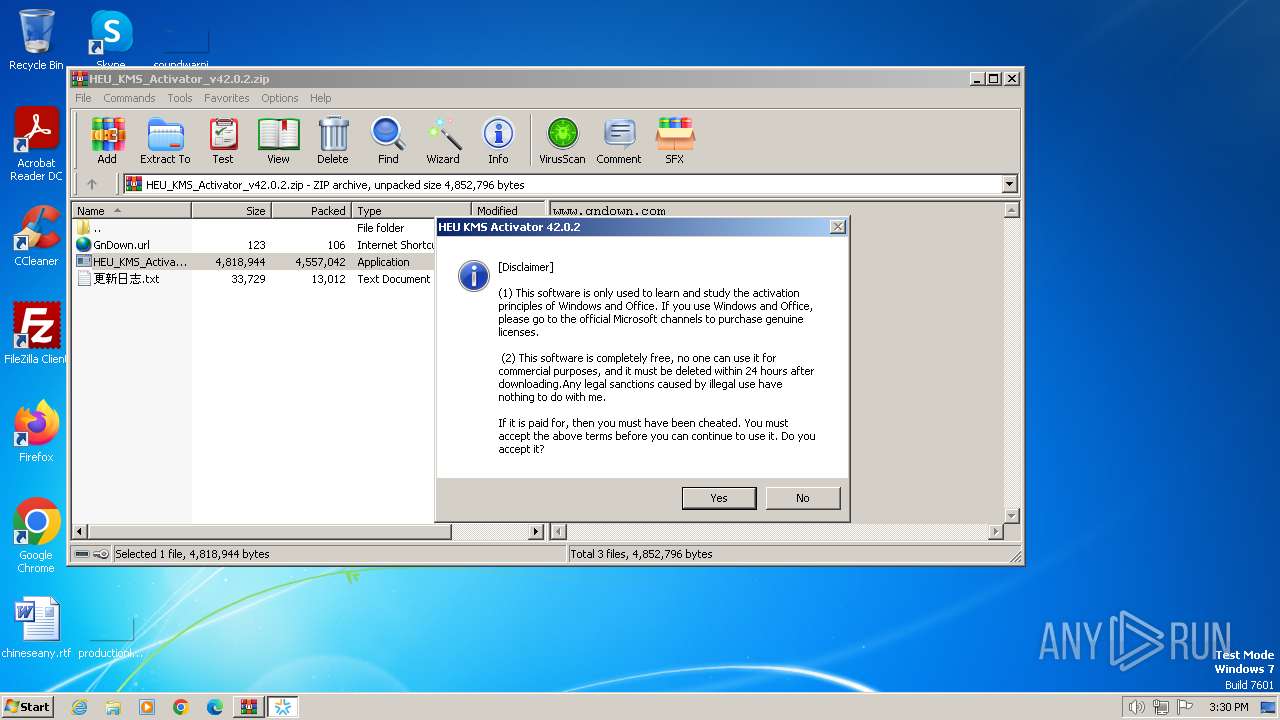
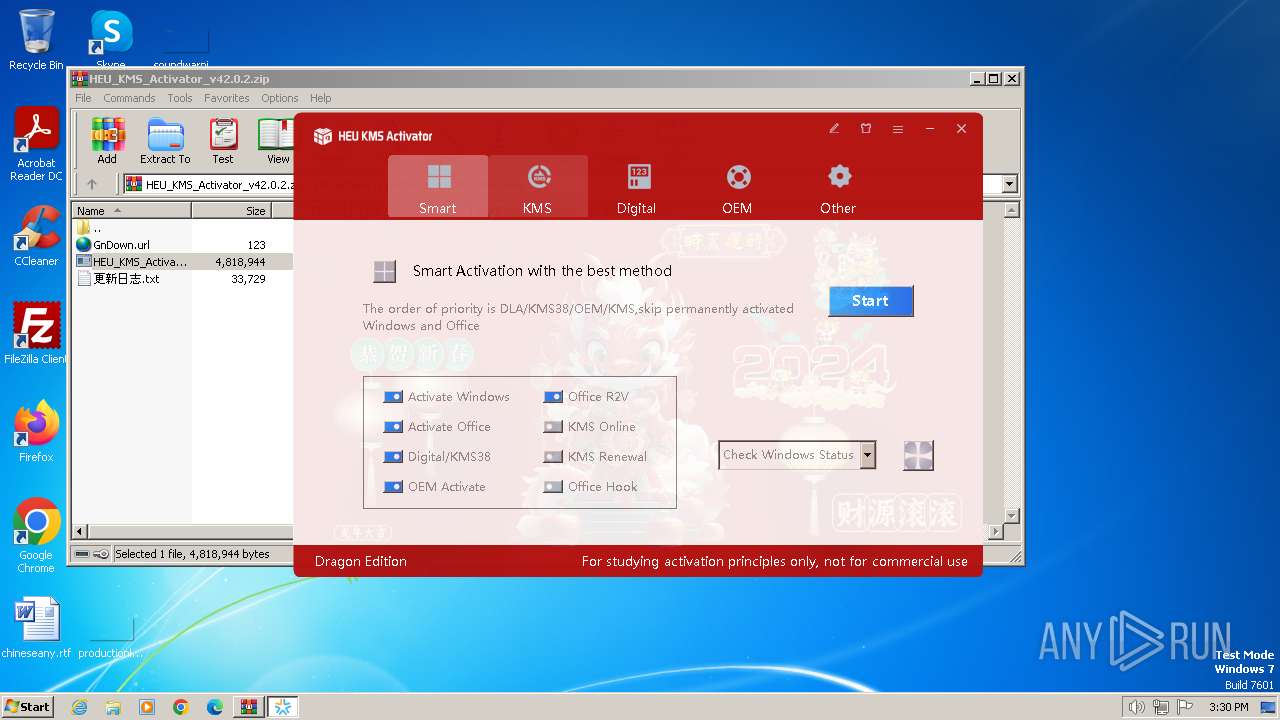
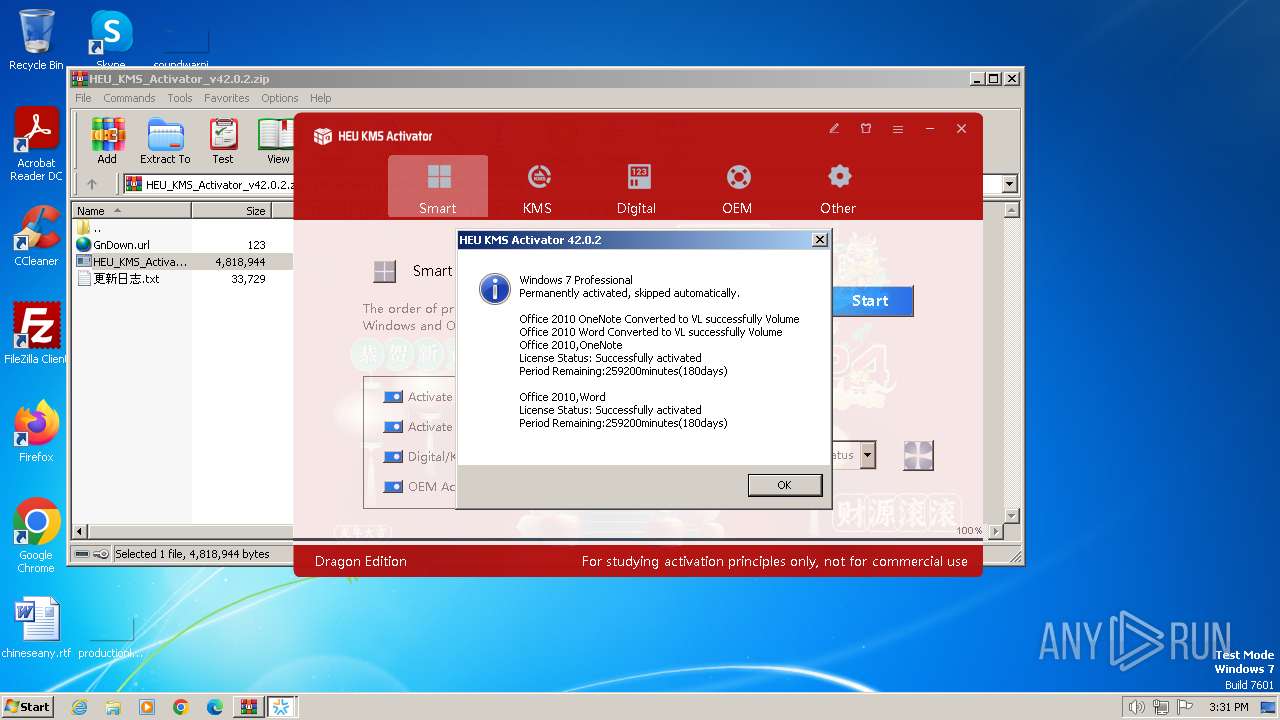
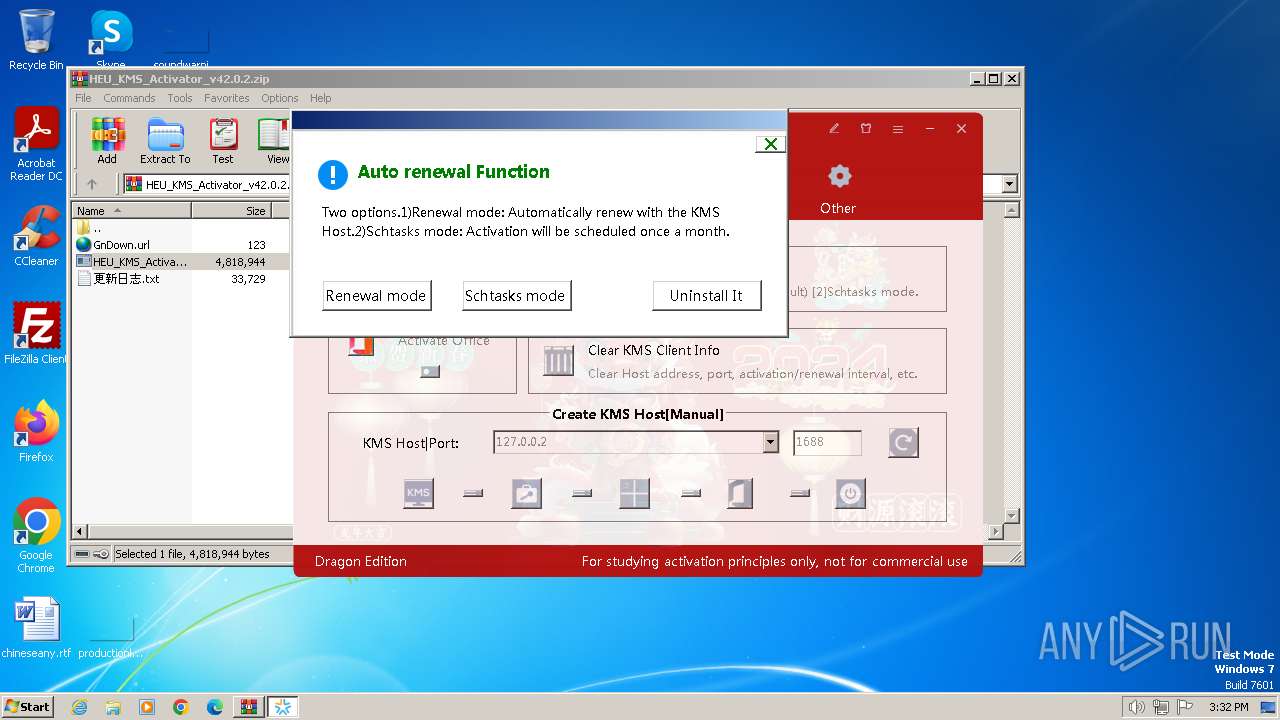
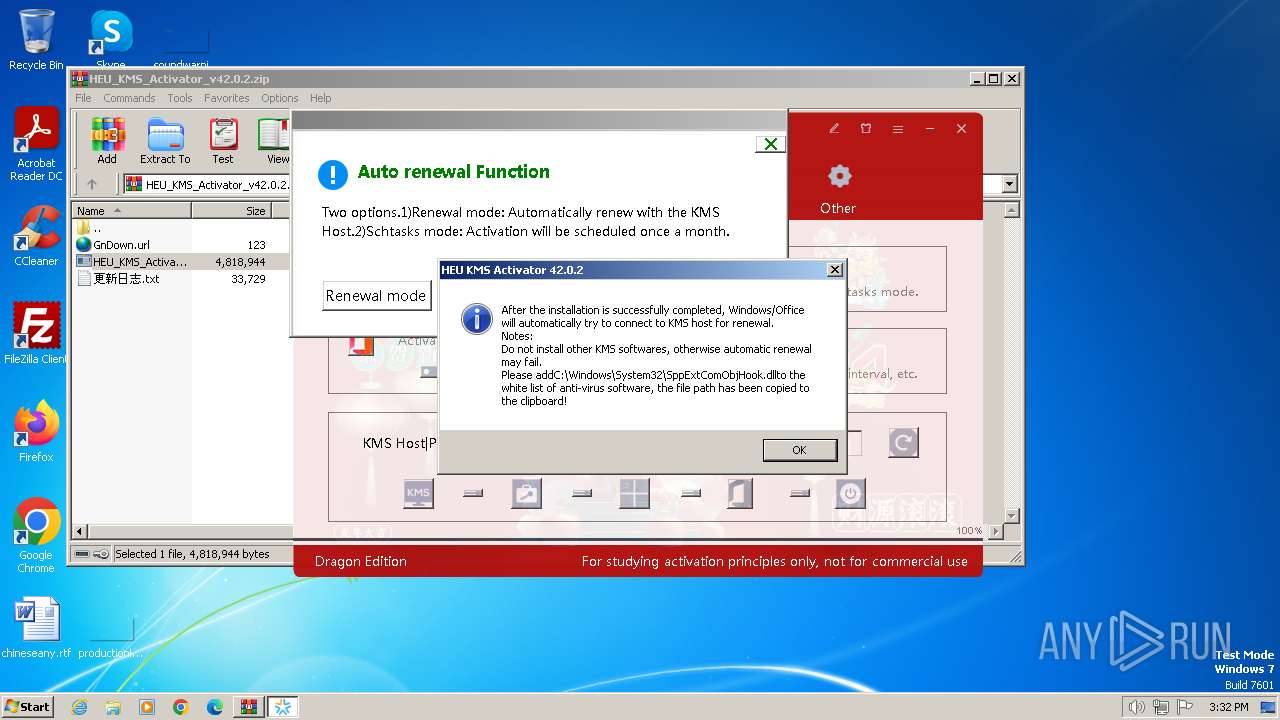
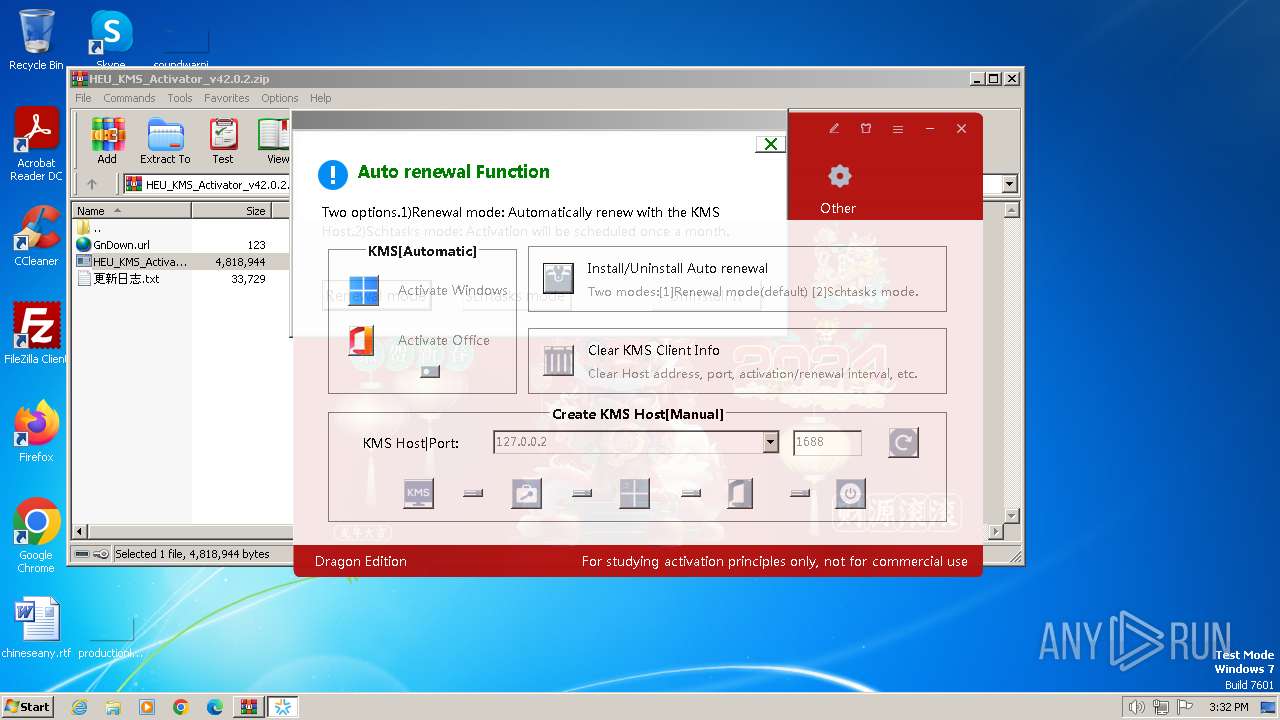
| File name: | HEU_KMS_Activator_v42.0.2.zip |
| Full analysis: | https://app.any.run/tasks/c4c021fe-4a9f-4da5-9a13-99c8fdbe3785 |
| Verdict: | Malicious activity |
| Analysis date: | March 04, 2024, 15:30:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E2E917BF3DFB40E71D1F63E44782549C |
| SHA1: | 5657082B8D9C28F3EEB8149724560E2CC22989CB |
| SHA256: | D975DC64EFD135C46B3335F213B65CE0125A7835BE73C06B6F8EF9815384527C |
| SSDEEP: | 98304:l9zjtP+CrfBy6oDZx3p+2KJ6B5qzxs8O+0+JV3SRo/NKVaYb8xdJbpJCMw9unSZ6:D2YAJjM |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4052)
- HEU_KMS_Activator_Dragon.exe (PID: 3948)
- 7Z.EXE (PID: 3464)
- kms.exe (PID: 864)
Accesses system services(Win32_Service) via WMI (SCRIPT)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Creates a writable file in the system directory
- kms.exe (PID: 864)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4052)
Executable content was dropped or overwritten
- HEU_KMS_Activator_Dragon.exe (PID: 3948)
- 7Z.EXE (PID: 3464)
- kms.exe (PID: 864)
Drops 7-zip archiver for unpacking
- HEU_KMS_Activator_Dragon.exe (PID: 3948)
Detected use of alternative data streams (AltDS)
- kms.exe (PID: 864)
Reads the Internet Settings
- cscript.exe (PID: 3276)
- cscript.exe (PID: 696)
Starts CMD.EXE for commands execution
- kms.exe (PID: 864)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 3276)
- cscript.exe (PID: 696)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 3276)
- cscript.exe (PID: 696)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Starts SC.EXE for service management
- cmd.exe (PID: 3068)
- cmd.exe (PID: 1236)
- cmd.exe (PID: 1864)
- cmd.exe (PID: 2388)
- cmd.exe (PID: 680)
- cmd.exe (PID: 1936)
- cmd.exe (PID: 784)
- cmd.exe (PID: 2088)
- cmd.exe (PID: 2548)
- cmd.exe (PID: 3752)
- cmd.exe (PID: 2948)
- cmd.exe (PID: 1388)
- cmd.exe (PID: 2596)
- cmd.exe (PID: 3936)
Accesses ComputerSystem(Win32_ComputerSystem) via WMI (SCRIPT)
- cscript.exe (PID: 3276)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
The process executes VB scripts
- cmd.exe (PID: 1232)
- cmd.exe (PID: 992)
- cmd.exe (PID: 2640)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 2024)
- cmd.exe (PID: 532)
- cmd.exe (PID: 2492)
- cmd.exe (PID: 1072)
- cmd.exe (PID: 2836)
- cmd.exe (PID: 2928)
- cmd.exe (PID: 1880)
- cmd.exe (PID: 2652)
- cmd.exe (PID: 3216)
- cmd.exe (PID: 116)
- cmd.exe (PID: 796)
- cmd.exe (PID: 1644)
- cmd.exe (PID: 2384)
- cmd.exe (PID: 2804)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2972)
Changes charset (SCRIPT)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 448)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 448)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Reads data from a file (SCRIPT)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Accesses system date via WMI (SCRIPT)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3608)
- cmd.exe (PID: 1404)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 1264)
- cmd.exe (PID: 3716)
- cmd.exe (PID: 2748)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 3988)
- cmd.exe (PID: 3180)
The executable file from the user directory is run by the CMD process
- kms-server.exe (PID: 3732)
- kms-server.exe (PID: 268)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2256)
- cmd.exe (PID: 3068)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4052)
Checks supported languages
- HEU_KMS_Activator_Dragon.exe (PID: 3948)
- 7Z.EXE (PID: 3464)
- kms.exe (PID: 864)
- 7Z.EXE (PID: 1792)
- kms-server.exe (PID: 268)
- kms-server.exe (PID: 668)
- kms-server.exe (PID: 3732)
Reads mouse settings
- HEU_KMS_Activator_Dragon.exe (PID: 3948)
- kms.exe (PID: 864)
Checks Windows language
- HEU_KMS_Activator_Dragon.exe (PID: 3948)
- kms.exe (PID: 864)
Create files in a temporary directory
- HEU_KMS_Activator_Dragon.exe (PID: 3948)
- 7Z.EXE (PID: 3464)
- kms.exe (PID: 864)
- 7Z.EXE (PID: 1792)
Reads the computer name
- 7Z.EXE (PID: 3464)
- kms.exe (PID: 864)
- 7Z.EXE (PID: 1792)
- kms-server.exe (PID: 268)
- kms-server.exe (PID: 668)
- kms-server.exe (PID: 3732)
Reads the machine GUID from the registry
- HEU_KMS_Activator_Dragon.exe (PID: 3948)
- kms.exe (PID: 864)
Reads security settings of Internet Explorer
- cscript.exe (PID: 3276)
- cscript.exe (PID: 696)
- cscript.exe (PID: 448)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 1216)
- cscript.exe (PID: 3312)
- cscript.exe (PID: 4072)
- cscript.exe (PID: 2028)
- cscript.exe (PID: 2080)
- cscript.exe (PID: 3524)
- cscript.exe (PID: 2612)
- cscript.exe (PID: 3104)
- cscript.exe (PID: 3700)
- cscript.exe (PID: 3304)
- cscript.exe (PID: 2848)
- cscript.exe (PID: 2572)
- cscript.exe (PID: 2688)
- cscript.exe (PID: 1900)
- cscript.exe (PID: 2388)
- cscript.exe (PID: 2972)
Reads Environment values
- kms.exe (PID: 864)
Reads product name
- kms.exe (PID: 864)
Reads Microsoft Office registry keys
- kms.exe (PID: 864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:02:05 22:40:36 |
| ZipCRC: | 0x9d648d82 |
| ZipCompressedSize: | 13012 |
| ZipUncompressedSize: | 33729 |
| ZipFileName: | ??????־.txt |
Total processes
187
Monitored processes
97
Malicious processes
41
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Windows\system32\cmd.exe /c set "Path=%SystemRoot%;%SystemRoot%\system32;%SystemRoot%\System32\Wbem;%SystemRoot\System32\WindowsPowerShell\v1.0\" & cscript //nologo "C:\Program Files\Microsoft Office\Office14\ospp.vbs" /inslic:"C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\Licenses\Office2010\Word\Word_KMS_Client_RAC_Pub.xrm-ms" | C:\Windows\System32\cmd.exe | — | kms.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 128 | regedit /s "C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\Licenses\Office2010\Word\VLReg32.reg" | C:\Windows\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\x86\kms-server.exe -S | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\x86\kms-server.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 448 | cscript //nologo "C:\Program Files\Microsoft Office\Office14\ospp.vbs" /inslic:"C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\Licenses\Office2010\OneNote\OneNote_KMS_Client_OOB.xrm-ms" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 532 | C:\Windows\system32\cmd.exe /c set "Path=%SystemRoot%;%SystemRoot%\system32;%SystemRoot%\System32\Wbem;%SystemRoot\System32\WindowsPowerShell\v1.0\" & cscript //nologo "C:\Program Files\Microsoft Office\Office14\ospp.vbs" /inslic:"C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\Licenses\Office2010\OneNote\OneNote_MAK_OOB.xrm-ms" | C:\Windows\System32\cmd.exe | — | kms.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 584 | netsh advfirewall firewall add rule name="heu-kms-mini" dir=in action=allow profile=any program="C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\x86\kms-server.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\x86\kms-server.exe -P 1688 -R 10080 -A 120 -T0 | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\x86\kms-server.exe | — | kms.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 680 | C:\Windows\system32\cmd.exe /c sc query ClickToRunSvc | C:\Windows\System32\cmd.exe | — | kms.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1060 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 696 | C:\Windows\System32\cscript.exe //nologo //Job:WmiQuery "C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\xml\wim.xml?.wsf" SoftwareLicensingService Version | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 784 | C:\Windows\system32\cmd.exe /c sc query osppsvc | C:\Windows\System32\cmd.exe | — | kms.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
14 071
Read events
13 673
Write events
397
Delete events
1
Modification events
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HEU_KMS_Activator_v42.0.2.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
9
Suspicious files
4
Text files
294
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3948 | HEU_KMS_Activator_Dragon.exe | C:\Users\admin\AppData\Local\Temp\aut1642.tmp | binary | |
MD5:A910A59B819F1BFF73FC4D3C5F08EABC | SHA256:DE8761FAB3FB5BA1E8F82E82985F8CC5531C2C19304B826583AF6DA531B35126 | |||
| 3948 | HEU_KMS_Activator_Dragon.exe | C:\Users\admin\AppData\Local\Temp\aut17E9.tmp | compressed | |
MD5:E1981633F4795AD1585958B822736F3F | SHA256:87E34B4F298C6EFB0588E506F74A5FA357CD92BE93B4499B807871CC22E9822F | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4052.20140\HEU_KMS_Activator_Dragon.exe | executable | |
MD5:3B4C7BAFB37601AEBCD4A52FFBA70117 | SHA256:FE55299E52433162845AF063524BD63F77A446541EA64E1FCBC75E3CAA227F7E | |||
| 3948 | HEU_KMS_Activator_Dragon.exe | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\KMSmini.7z | compressed | |
MD5:E1981633F4795AD1585958B822736F3F | SHA256:87E34B4F298C6EFB0588E506F74A5FA357CD92BE93B4499B807871CC22E9822F | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4052.20140\GnDown.url | url | |
MD5:1A237390CE695D9760E2DC0ABDB81D92 | SHA256:0B74409F68F0790962E718C2273A828E4B043554A2674702EA69618404EECADB | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4052.20140\更新日志.txt | text | |
MD5:D6B72E3EF60403D9DBFFA340A4FE9FAD | SHA256:25C59654E2D0D89EC9C0DBE810B9ED75809FEA9A03990A649083362E65A90113 | |||
| 3948 | HEU_KMS_Activator_Dragon.exe | C:\Users\admin\AppData\Local\Temp\ScriptTemp.ini | text | |
MD5:0C6E448946A3B9CE456E7279CF74B573 | SHA256:A74D0FEF19B77DC8BEF04CC4A41139C40FCFF1853272C7B266302A24C595E7A4 | |||
| 3464 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\OtherOfficeOSPP\OSPP.VBS | text | |
MD5:885B4DAE3623B427B8F04A7BC88780B9 | SHA256:6BC8E3991DA8C6527B3588E8F95068665918B685299CBB16BA6CC0C484BFE072 | |||
| 3464 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\Office2010OSPP\OSPP.VBS | text | |
MD5:572E9A87757AC96C7677FD1B1B113C55 | SHA256:008CF05944053116A095AD466561D3FD4BE8A7DE79E5ADA7C5DAAB492F730465 | |||
| 3464 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\pic\12-1.bmp | image | |
MD5:41645B59D0CD2909A8D8105A7C99DC30 | SHA256:9D7C6237E459455D792589C0D2EE7D5F02D0A62E403978D974B4049503EDA4D2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |