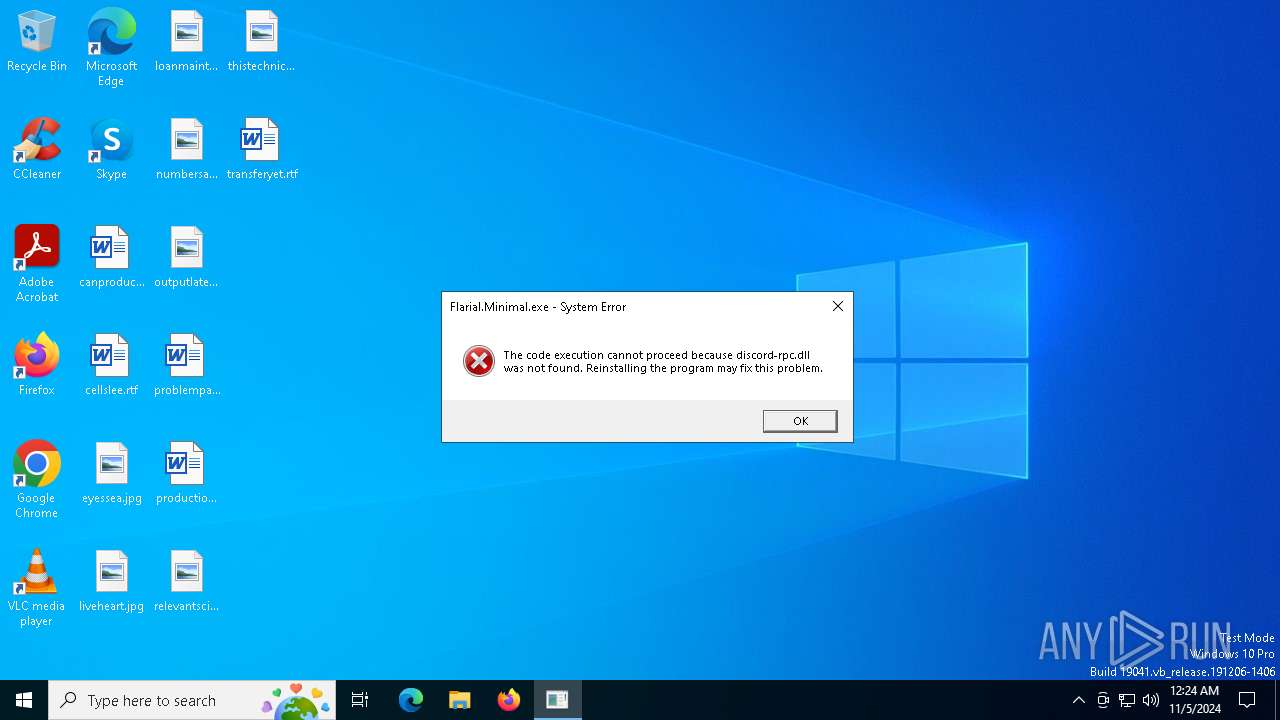
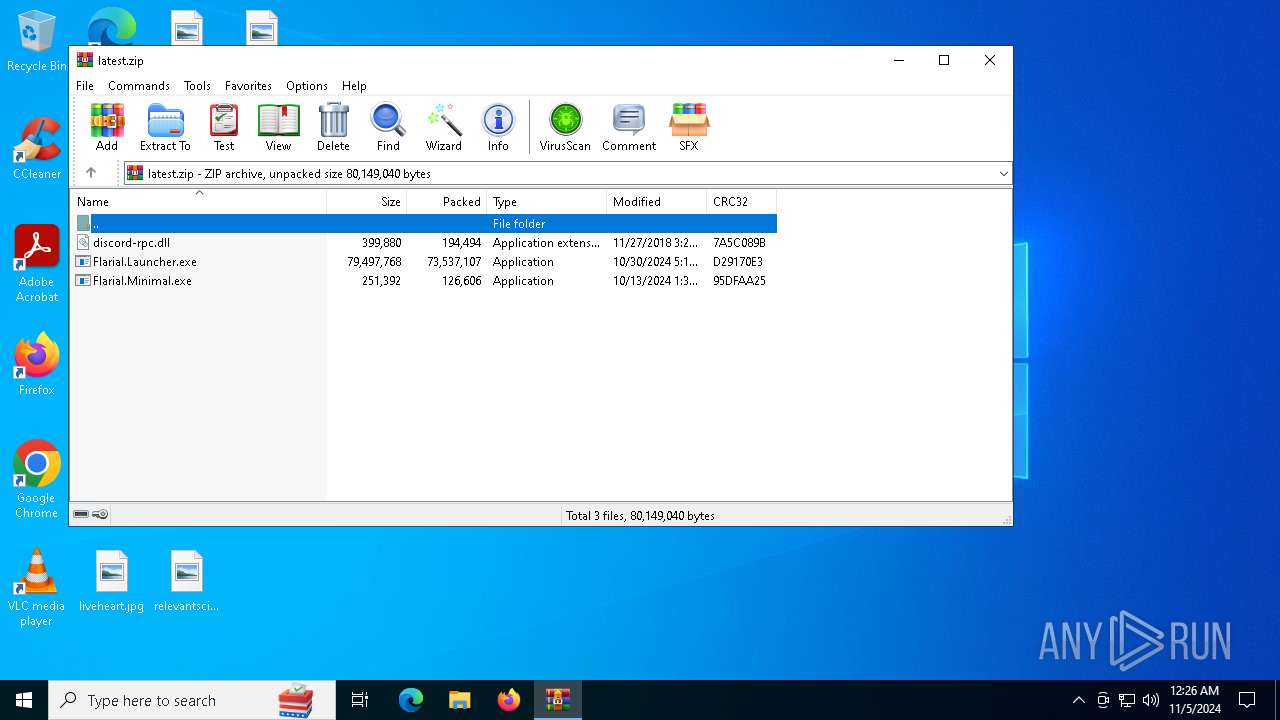
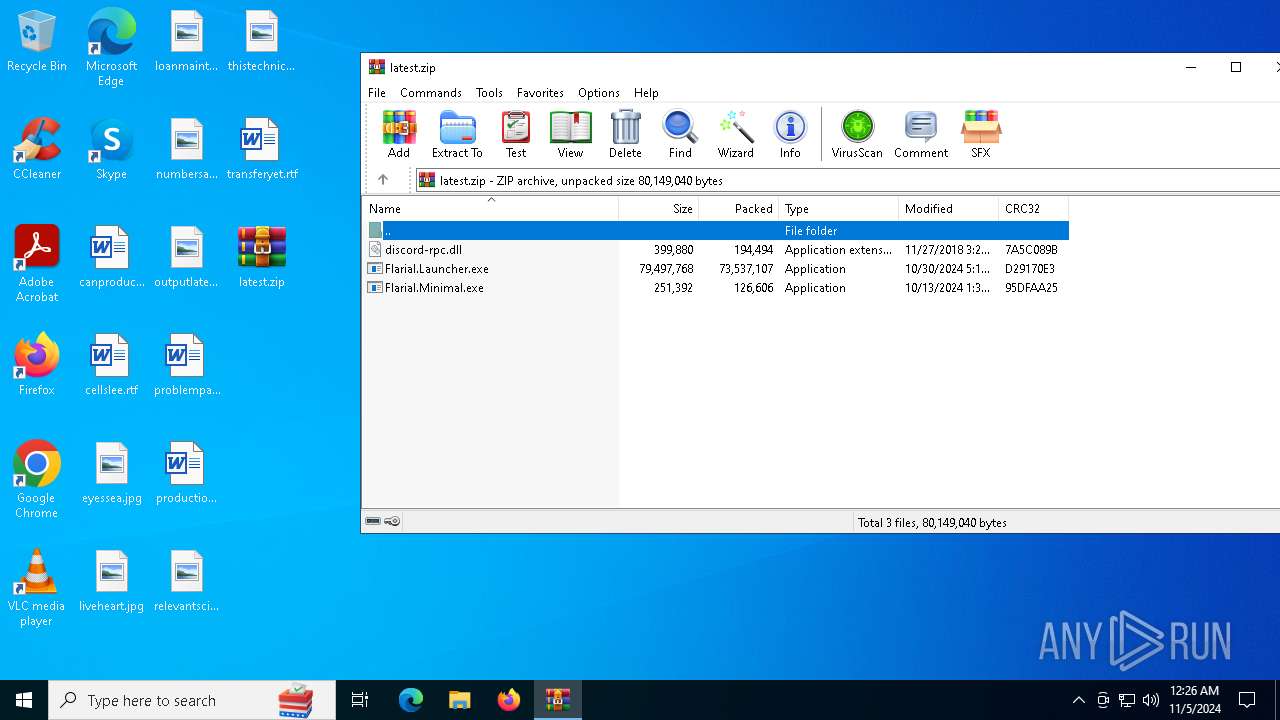
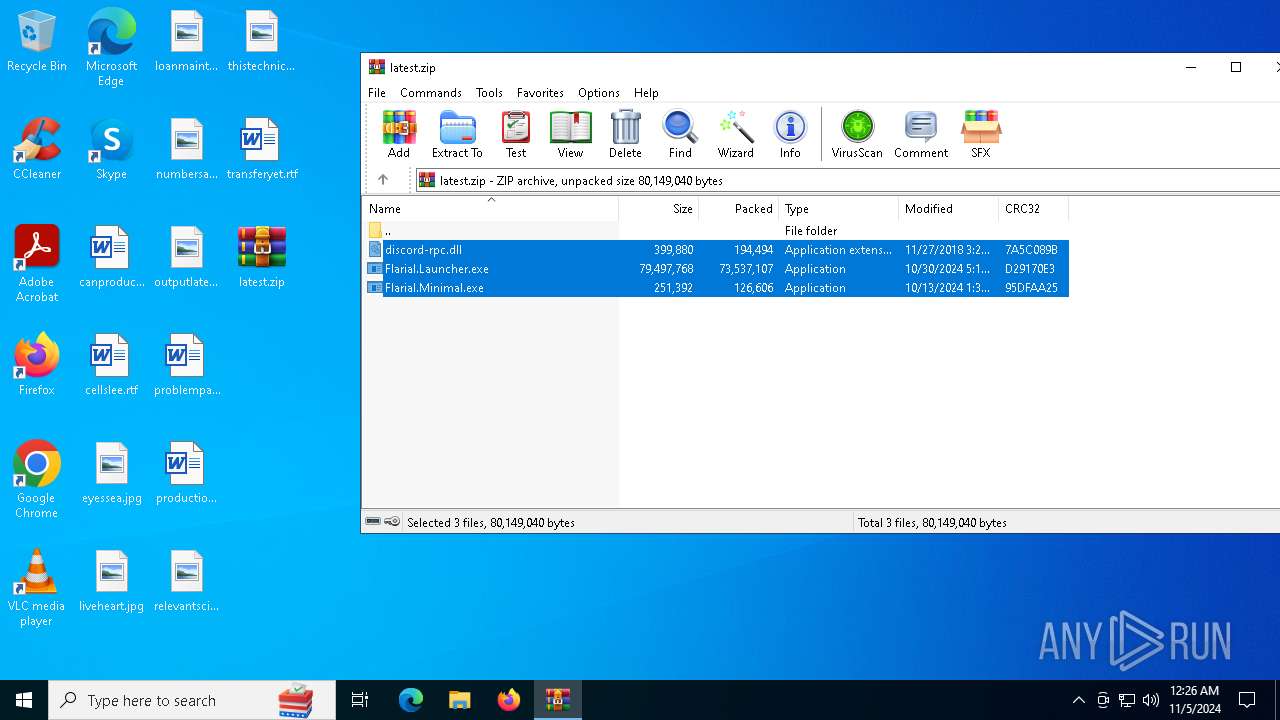
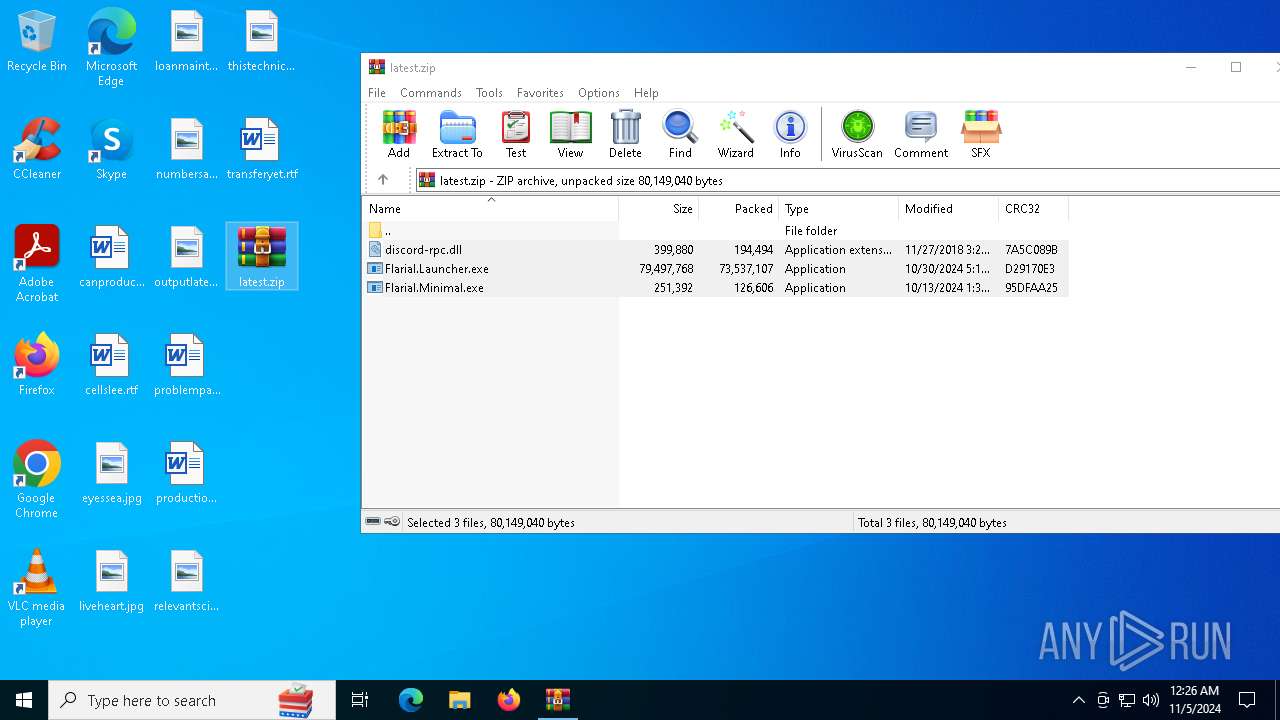
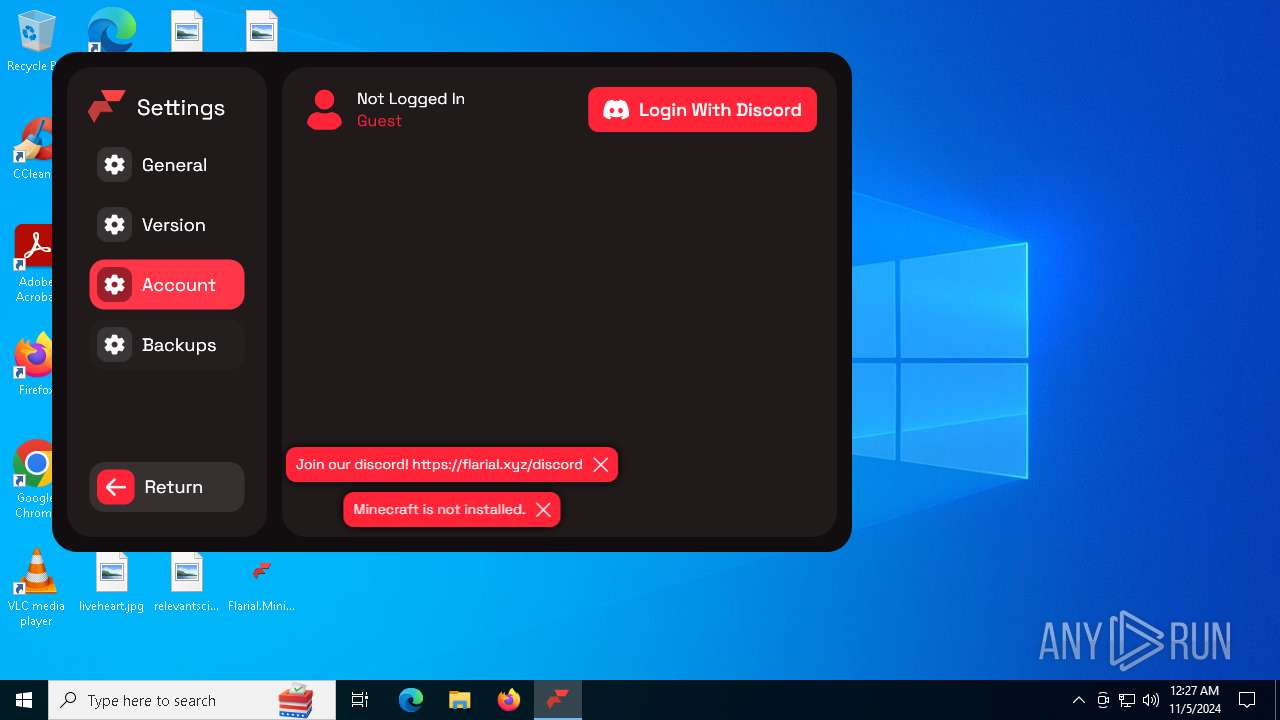
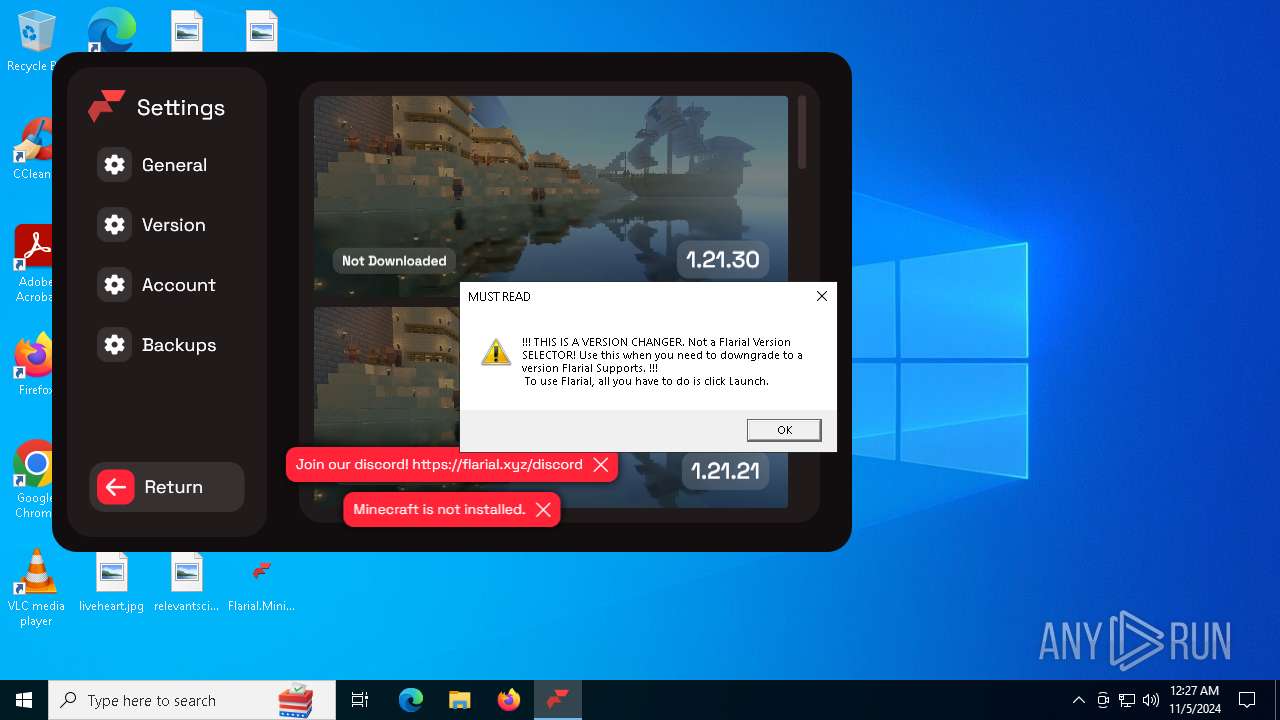
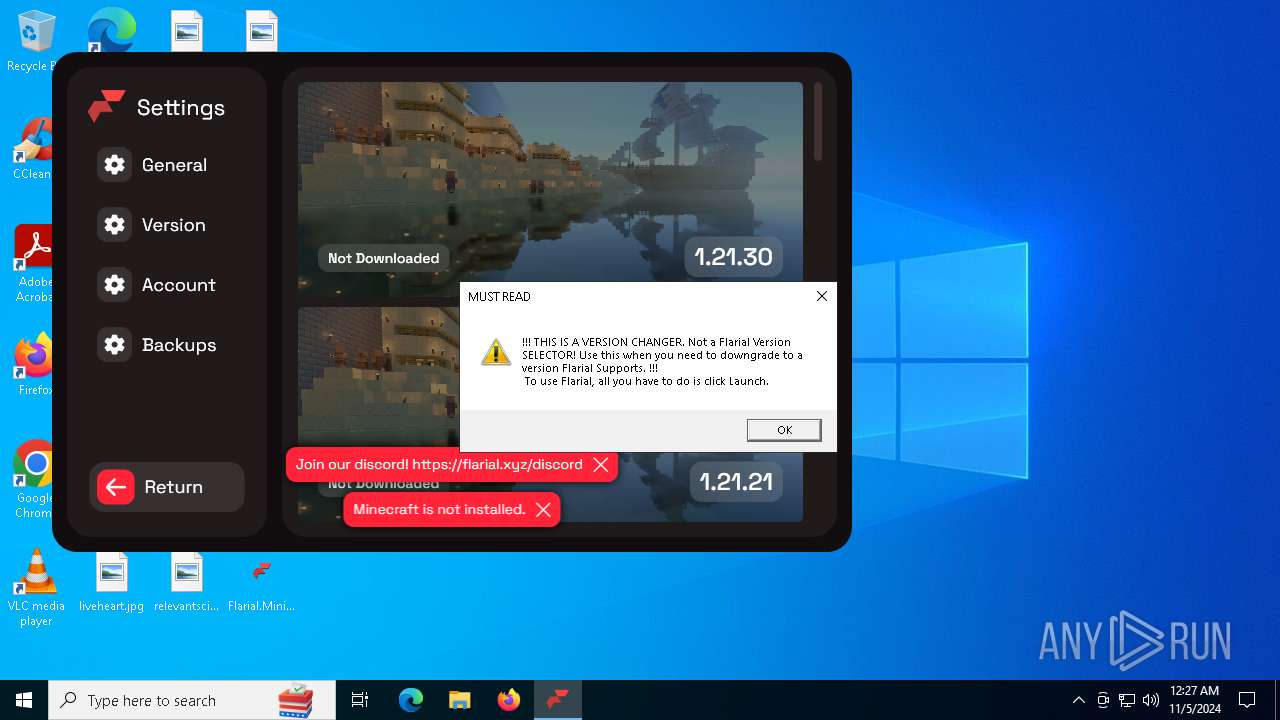
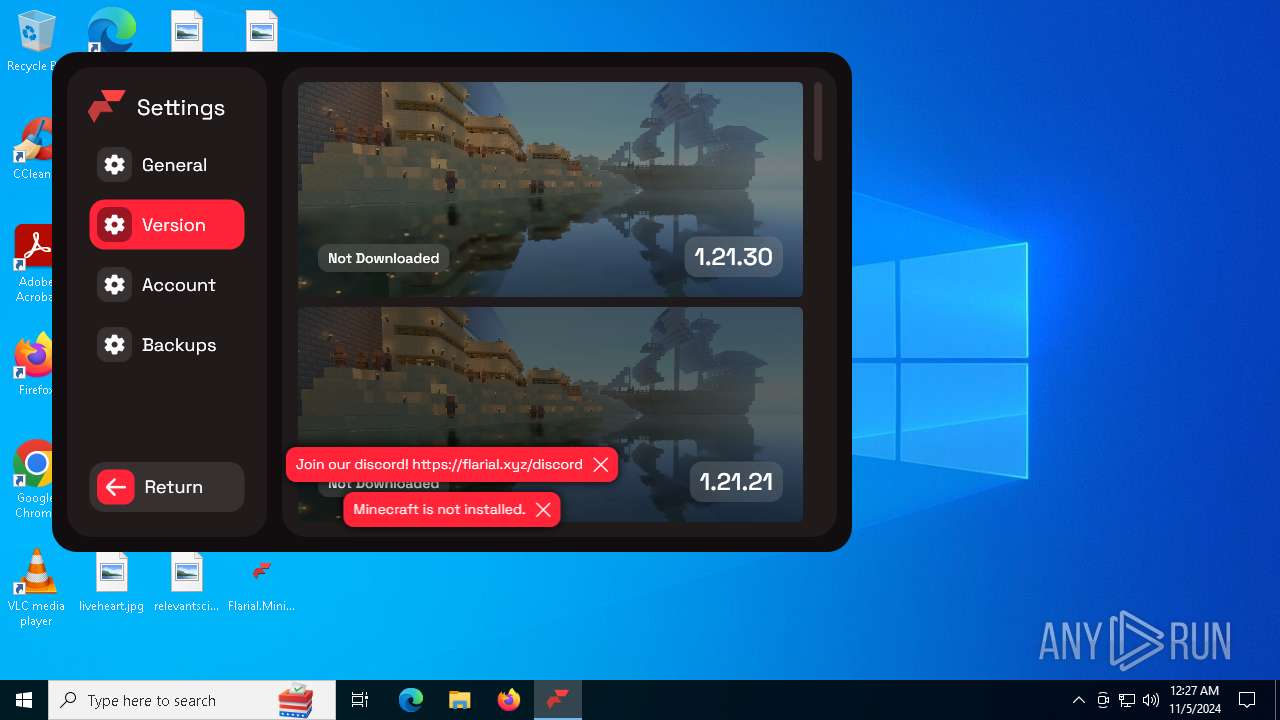
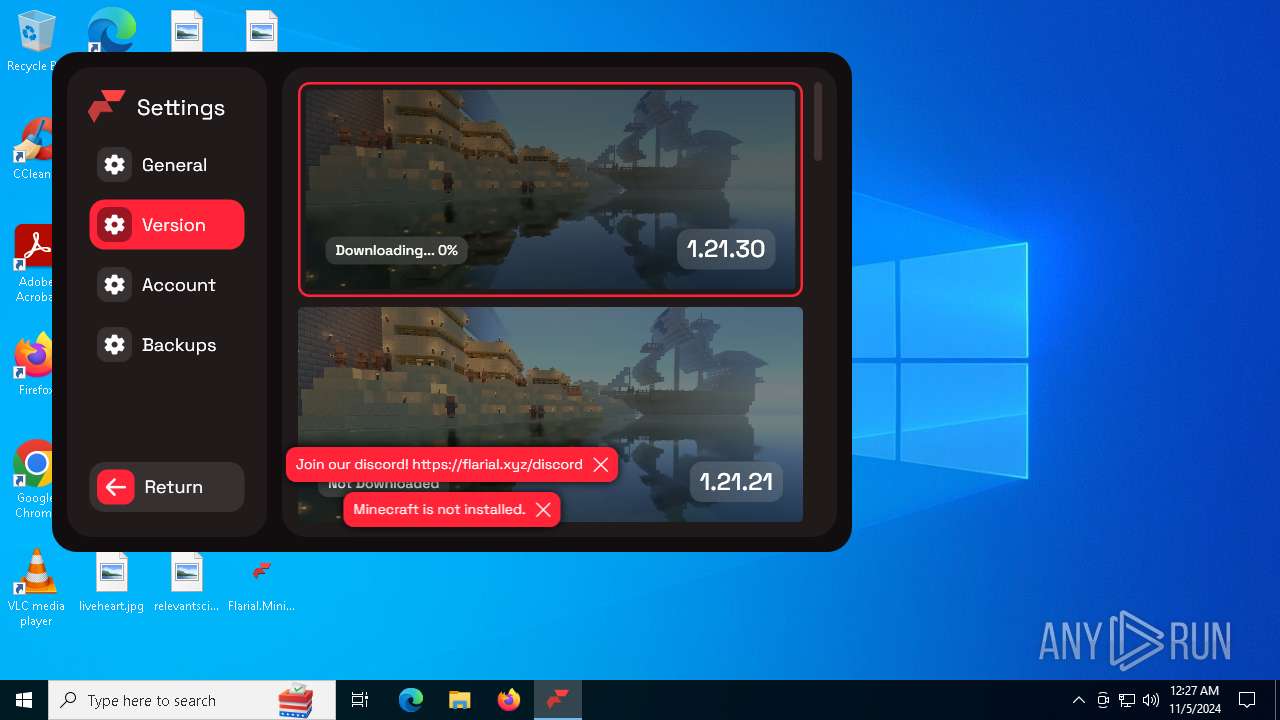
| File name: | Flarial.Minimal.exe |
| Full analysis: | https://app.any.run/tasks/37dd5778-515d-496e-9037-aba121c85be0 |
| Verdict: | Malicious activity |
| Analysis date: | November 05, 2024, 00:23:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 987884E1F9F18E8BA6C184453BB5FD6B |
| SHA1: | 88A5BDC0F92A5E1E6E14FCDEF6C6894E69857EE7 |
| SHA256: | D971208C9B9E1E6F7F08097187F25B34EE5A9C4E351A60C8459444B557B29D17 |
| SSDEEP: | 12288:sYbcJAuHmoqN/TjZ4ubYKKMmUTKfoHwPwGY:sYbQAucXRWoQHY |
MALICIOUS
No malicious indicators.SUSPICIOUS
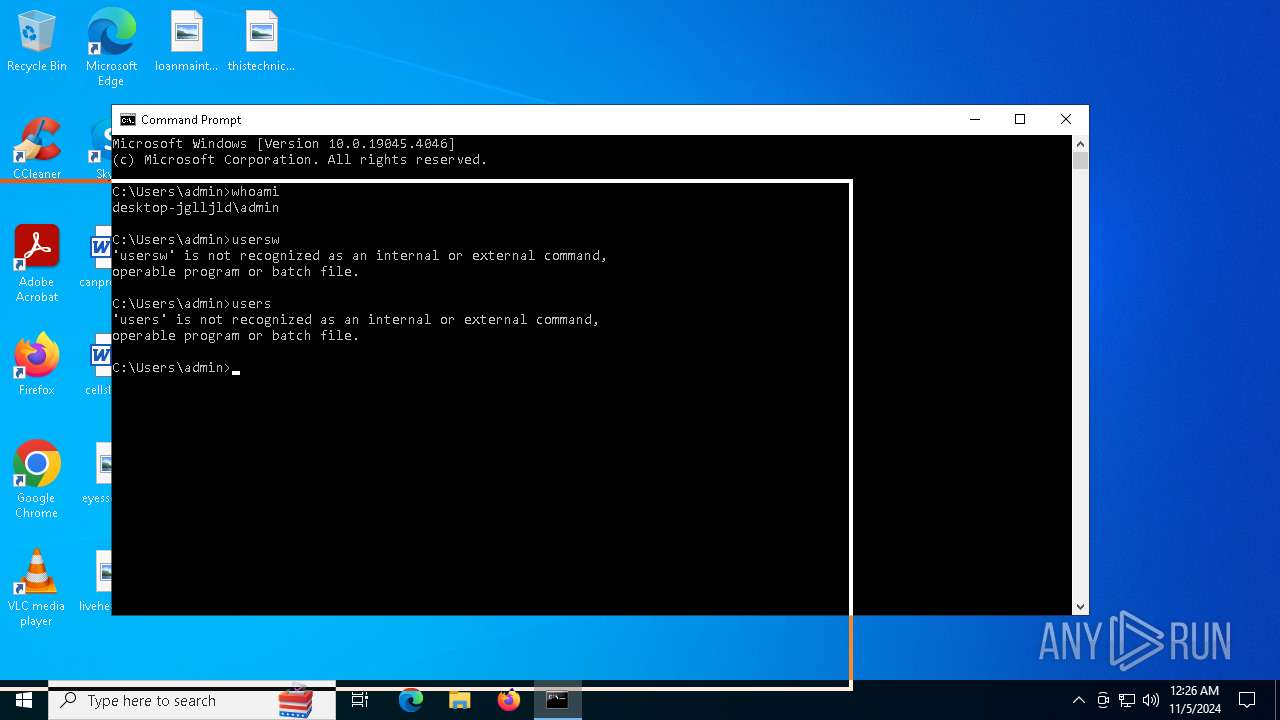
Identifying current user with WHOAMI command
- cmd.exe (PID: 4236)
Executable content was dropped or overwritten
- Flarial.Launcher.exe (PID: 4228)
The process drops C-runtime libraries
- Flarial.Launcher.exe (PID: 4228)
Process drops legitimate windows executable
- Flarial.Launcher.exe (PID: 4228)
INFO
Manual execution by a user
- cmd.exe (PID: 4236)
- WinRAR.exe (PID: 3848)
- Flarial.Launcher.exe (PID: 6492)
- Flarial.Launcher.exe (PID: 4228)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3848)
Attempting to use instant messaging service
- Flarial.Launcher.exe (PID: 6492)
- Flarial.Launcher.exe (PID: 4228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:10:13 13:39:22+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 160768 |
| InitializedDataSize: | 96768 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc0d4 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
139
Monitored processes
7
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 784 | whoami | C:\Windows\System32\whoami.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: whoami - displays logged on user information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\latest.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
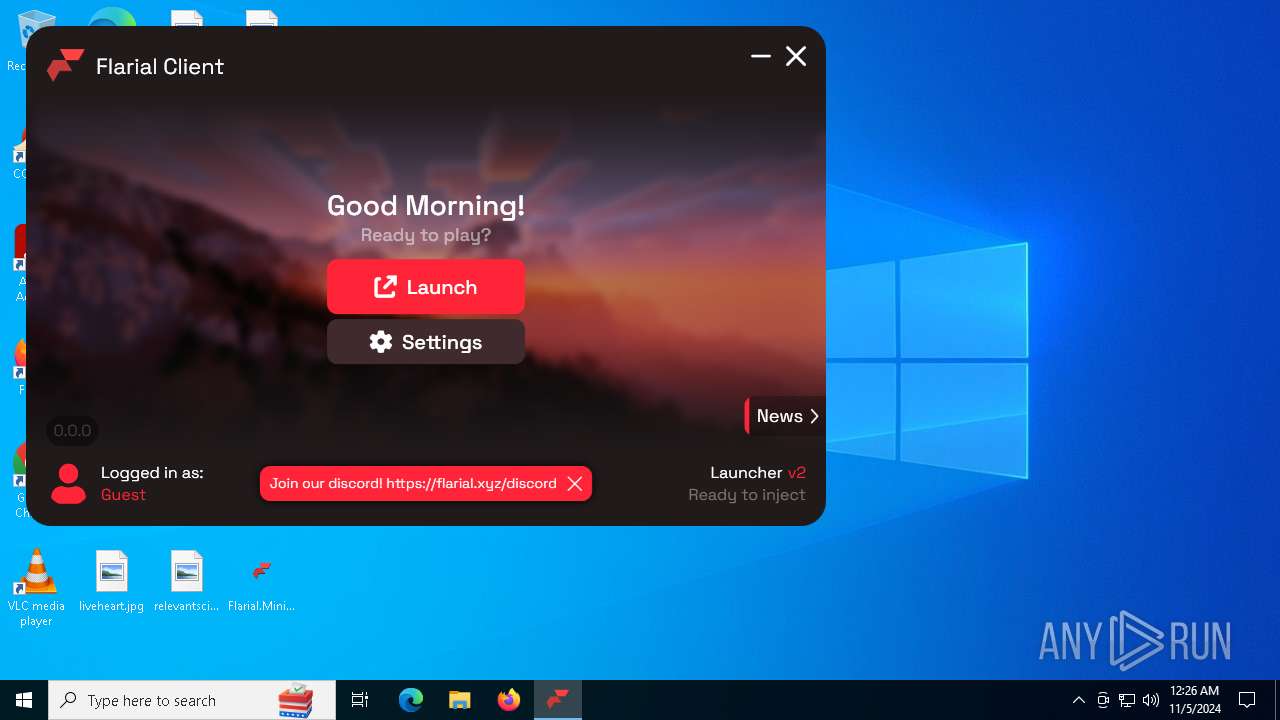
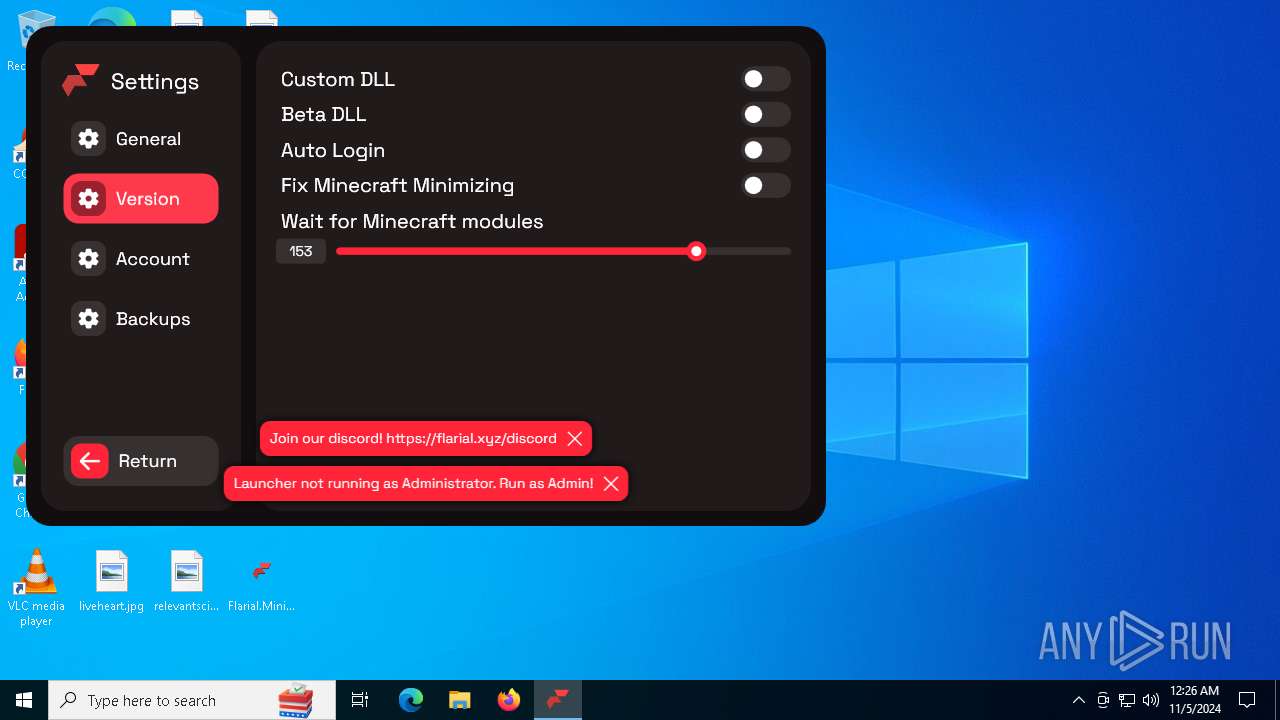
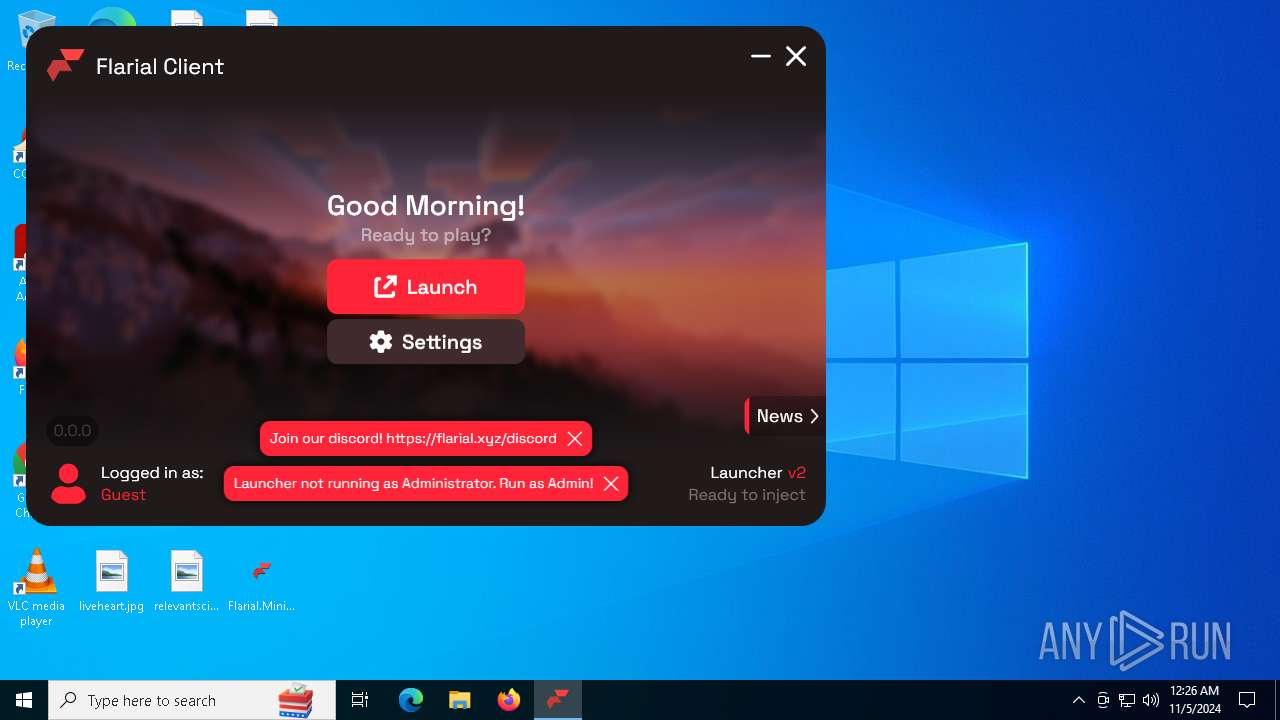
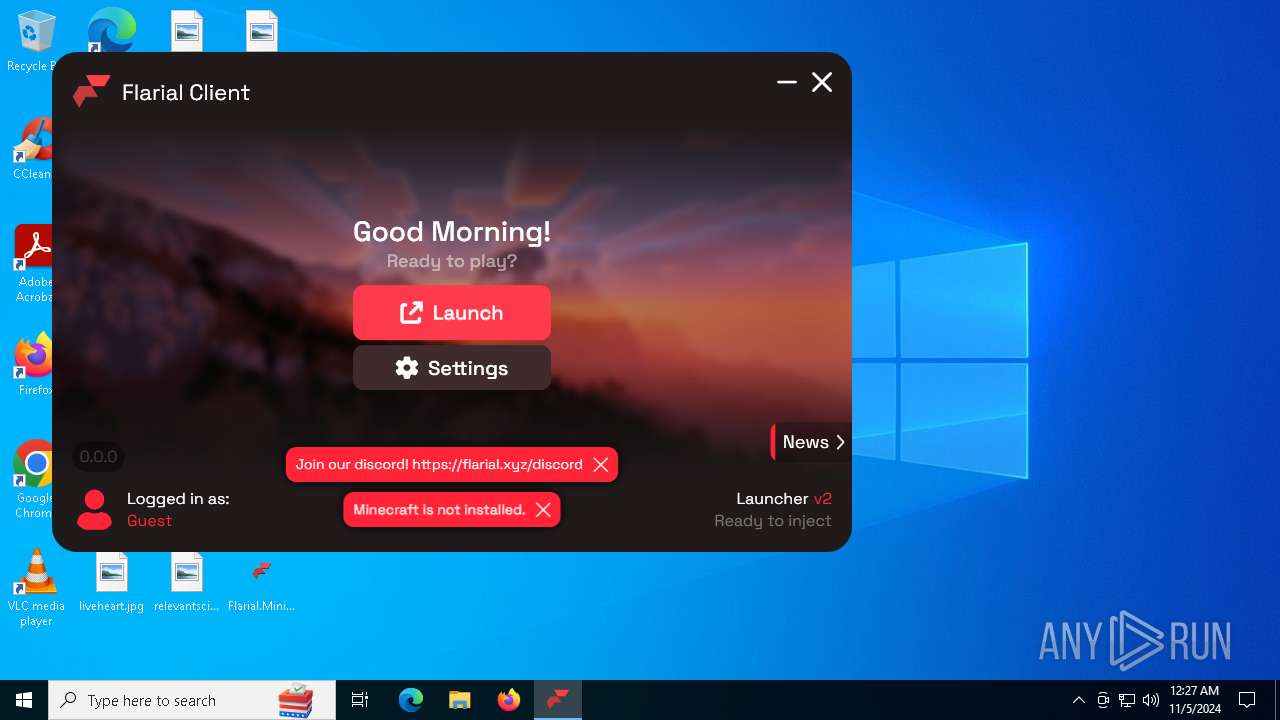
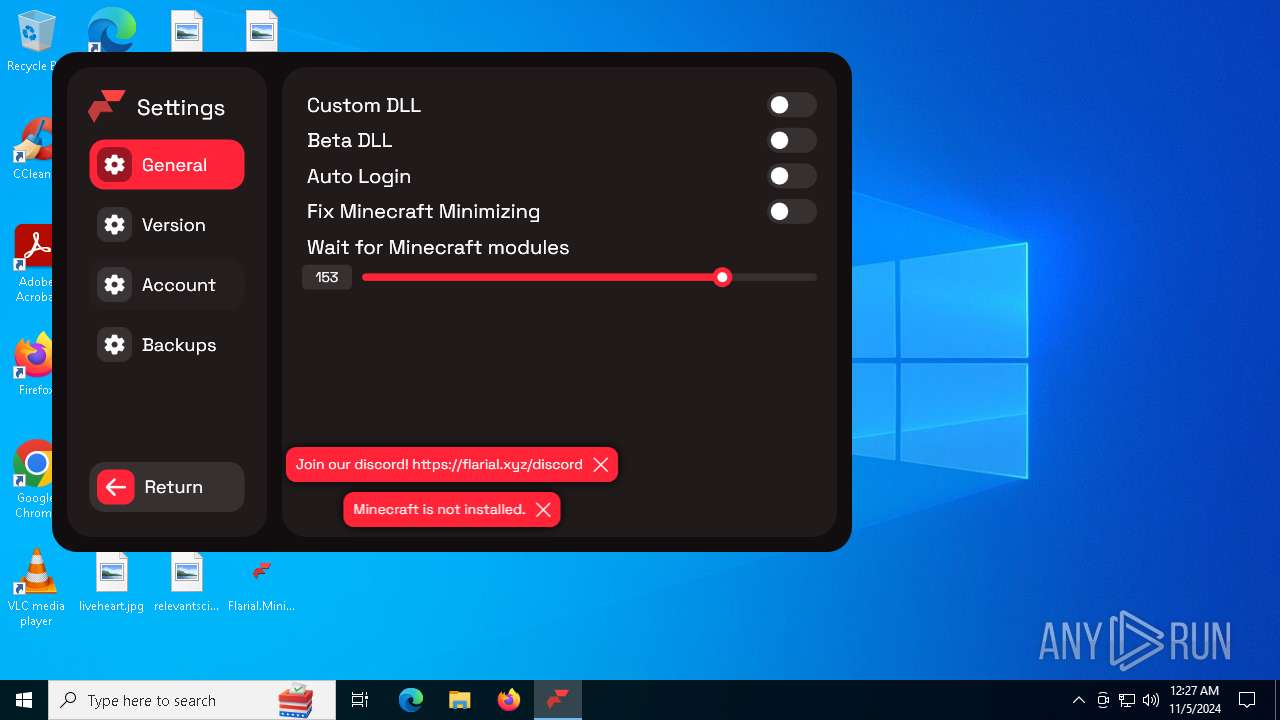
| 4228 | "C:\Users\admin\Desktop\Flarial.Launcher.exe" | C:\Users\admin\Desktop\Flarial.Launcher.exe | explorer.exe | ||||||||||||
User: admin Company: Flarial.Launcher Integrity Level: MEDIUM Description: Flarial.Launcher Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4236 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5496 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6492 | "C:\Users\admin\Desktop\Flarial.Launcher.exe" | C:\Users\admin\Desktop\Flarial.Launcher.exe | explorer.exe | ||||||||||||
User: admin Company: Flarial.Launcher Integrity Level: HIGH Description: Flarial.Launcher Version: 1.0.0.0 Modules
| |||||||||||||||
| 6648 | "C:\Users\admin\AppData\Local\Temp\Flarial.Minimal.exe" | C:\Users\admin\AppData\Local\Temp\Flarial.Minimal.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
Total events
3 269
Read events
3 247
Write events
22
Delete events
0
Modification events
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\latest.zip | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFA3FFFFFF9C0000006303000085020000 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
10
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.21064\Flarial.Launcher.exe | — | |
MD5:— | SHA256:— | |||
| 4228 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Flarial\Launcher\dont.delete | executable | |
MD5:731425E4F8E4F3DBBB129AC24DEFB8E7 | SHA256:5D710C805CC35F40F599224B39092AB7EFB15D0428AF19966F840ADB09F2A386 | |||
| 4228 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Flarial\Launcher\Supported.txt | text | |
MD5:A288E7FF8B6FEDBF6963FF3FC3FB9F46 | SHA256:65462806548E8DE241A5E1C6E282C7DF84FEAA46D9B72B37CF71F5F10DEC70B6 | |||
| 4228 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\WPF4267.tmp | image | |
MD5:7156ECB01EB9980D8A9A9718806D9FD5 | SHA256:41D4B105C63271C89111E8A524FB46F4AAAC487D6173499E72510684CD0C0AD7 | |||
| 4228 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Temp\.net\Flarial.Launcher\1084\runtimes\win-x64\native\WebView2Loader.dll | executable | |
MD5:0AD9319FA14D39C0812583337546CA20 | SHA256:1D963A02D8A7FA3E7EAC2E936DAD5559C4D63327F35B0A09787FFC1D58F9C18D | |||
| 4228 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Temp\.net\Flarial.Launcher\1084\PresentationNative_cor3.dll | executable | |
MD5:7D1615F573257A22895081A4D5C6CC0A | SHA256:DDB6CAA919D51B6CC56E19ED5D064BB04B2FEE9028564B518AD06665AB8B0683 | |||
| 4228 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Temp\.net\Flarial.Launcher\1084\PenImc_cor3.dll | executable | |
MD5:04F9465C06CDDF49E1619739E47C0D75 | SHA256:5C874E2890A36CC3F38D3C1921BC7AC74FB76AEF4D2B25FF30001EF252215650 | |||
| 4228 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\WPF41B8.tmp | image | |
MD5:E88180CAC9ACB9D5A7DA7A62E4238906 | SHA256:4C07398EC37F9B4A5ADAC14DB448C7D749F08A0C15690C44C2F9D99495EE4EB0 | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.21064\Flarial.Minimal.exe | executable | |
MD5:987884E1F9F18E8BA6C184453BB5FD6B | SHA256:D971208C9B9E1E6F7F08097187F25B34EE5A9C4E351A60C8459444B557B29D17 | |||
| 4228 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\WPF4237.tmp | image | |
MD5:49531E0731A2D7F22DB44745B162BA7A | SHA256:E1147DBA3534EFFF1AF27B0E9E66C642C2CEBB0BD2960B6966FA8AD48EECA1DB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
72
DNS requests
31
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.11:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3948 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3824 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6492 | Flarial.Launcher.exe | GET | — | 93.184.221.240:80 | http://tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e3ab54d0-3b0f-406e-a804-c2b45eb6fdf5?P1=1730782369&P2=404&P3=2&P4=IA8zkriwNQJOlljVKSSQZKO6213ZCLPbEQXrPArxzDwhAP4LL%2bxqmB5kGlNQIdjBoI9hUb4KJinfVGOGxEiYqQ%3d%3d | unknown | — | — | whitelisted |
7036 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3824 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4360 | SearchApp.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
3396 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.168.11:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2172 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
4228 | Flarial.Launcher.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
4228 | Flarial.Launcher.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
4228 | Flarial.Launcher.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
6492 | Flarial.Launcher.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
6492 | Flarial.Launcher.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
6492 | Flarial.Launcher.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud infrastructure to build app (vercel .app) |
Process | Message |
|---|---|
Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Flarial
|
Flarial.Launcher.exe | Debug 0 0
|
Flarial.Launcher.exe | Debug 9 27
|
Flarial.Launcher.exe | Debug 1 24
|
Flarial.Launcher.exe | Debug 4 27
|
Flarial.Launcher.exe | Debug 10 27
|
Flarial.Launcher.exe | Debug 8 27
|
Flarial.Launcher.exe | Debug 0.5 21
|
Flarial.Launcher.exe | Debug 7 27
|
Flarial.Launcher.exe | Debug 3 24
|