| File name: | 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn |
| Full analysis: | https://app.any.run/tasks/603d60c9-5b10-4774-a458-1ae66603cae8 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 16:04:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | C7E8D9358D020015A3E489657A94D761 |
| SHA1: | 63C2B2836057DD99D89584B471C6DD8769FA2BA0 |
| SHA256: | D96F57219BB0E1796D81B9C24B6BA9D08C6259BC3757DD80AF03972504DF46E2 |
| SSDEEP: | 24576:5cPNp94L3wDp74JxCaE/+vbxSxUSJTf9lo1uJbapUHE:5cj947wDp7UxCaE/+vdSxUSJTf9lo1uu |
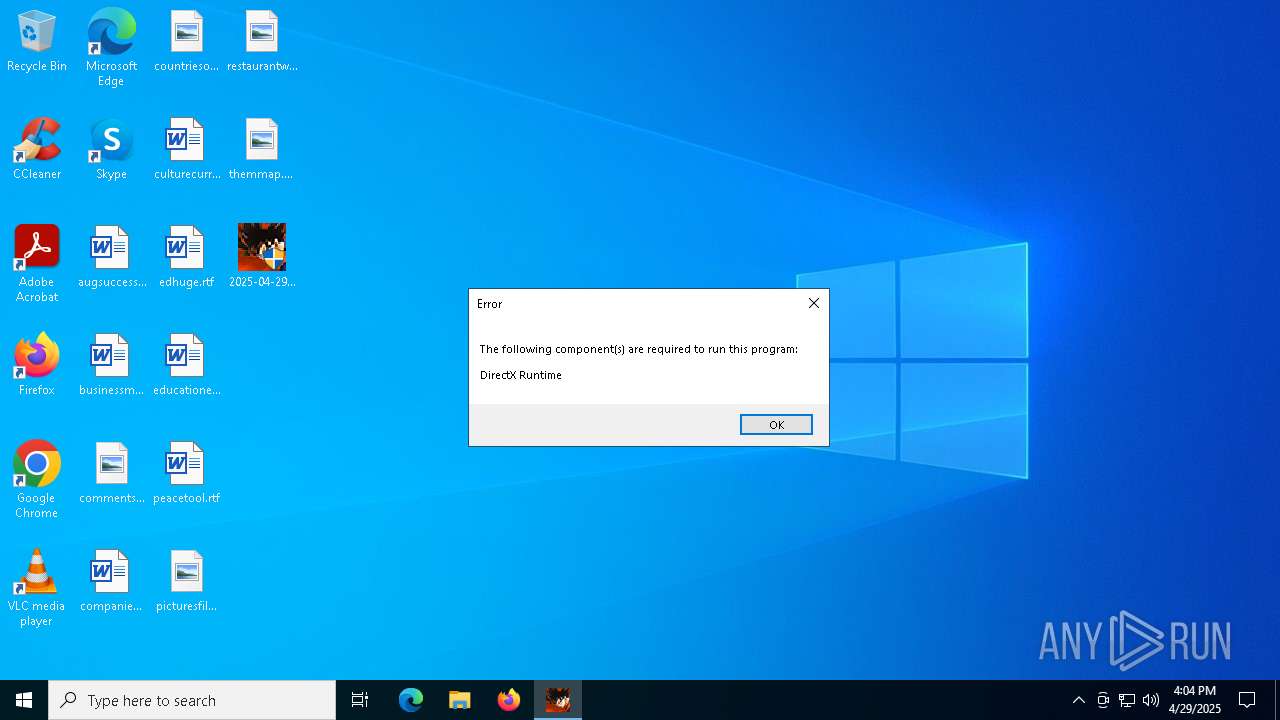
MALICIOUS
JEEFO has been detected
- 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe (PID: 7756)
- icsys.icn.exe (PID: 7820)
- explorer.exe (PID: 7840)
- svchost.exe (PID: 7884)
Changes the autorun value in the registry
- svchost.exe (PID: 7884)
- explorer.exe (PID: 7840)
SUSPICIOUS
Starts application with an unusual extension
- 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe (PID: 7756)
Executable content was dropped or overwritten
- 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe (PID: 7756)
- spoolsv.exe (PID: 7864)
- icsys.icn.exe (PID: 7820)
- explorer.exe (PID: 7840)
Starts itself from another location
- 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe (PID: 7756)
- spoolsv.exe (PID: 7864)
- svchost.exe (PID: 7884)
- icsys.icn.exe (PID: 7820)
- explorer.exe (PID: 7840)
The process creates files with name similar to system file names
- icsys.icn.exe (PID: 7820)
- spoolsv.exe (PID: 7864)
Creates or modifies Windows services
- svchost.exe (PID: 7884)
INFO
Checks supported languages
- 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe (PID: 7756)
- 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe (PID: 7800)
- icsys.icn.exe (PID: 7820)
- spoolsv.exe (PID: 7864)
- svchost.exe (PID: 7884)
- spoolsv.exe (PID: 7908)
- explorer.exe (PID: 7840)
The sample compiled with english language support
- 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe (PID: 7756)
Create files in a temporary directory
- 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe (PID: 7756)
- icsys.icn.exe (PID: 7820)
- spoolsv.exe (PID: 7864)
- svchost.exe (PID: 7884)
- spoolsv.exe (PID: 7908)
- explorer.exe (PID: 7840)
Reads the computer name
- 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe (PID: 7800)
- svchost.exe (PID: 7884)
Auto-launch of the file from Registry key
- svchost.exe (PID: 7884)
- explorer.exe (PID: 7840)
Manual execution by a user
- svchost.exe (PID: 7300)
- explorer.exe (PID: 7288)
Reads the software policy settings
- slui.exe (PID: 6248)
Checks proxy server information
- slui.exe (PID: 6248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
135
Monitored processes
11
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6248 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7288 | c:\windows\resources\themes\explorer.exe RO | C:\Windows\Resources\Themes\explorer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 7300 | c:\windows\resources\svchost.exe RO | C:\Windows\Resources\svchost.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 7652 | "C:\Users\admin\Desktop\2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe" | C:\Users\admin\Desktop\2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 7756 | "C:\Users\admin\Desktop\2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe" | C:\Users\admin\Desktop\2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 7800 | c:\users\admin\desktop\2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe | C:\Users\admin\Desktop\2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe | — | 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe | |||||||||||
User: admin Company: Epic Games, Inc. Integrity Level: HIGH Description: UE4Game Exit code: 9001 Modules
| |||||||||||||||
| 7820 | C:\Windows\Resources\Themes\icsys.icn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 7840 | c:\windows\resources\themes\explorer.exe | C:\Windows\Resources\Themes\explorer.exe | icsys.icn.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 7864 | c:\windows\resources\spoolsv.exe SE | C:\Windows\Resources\spoolsv.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 7884 | c:\windows\resources\svchost.exe | C:\Windows\Resources\svchost.exe | spoolsv.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
Total events
3 758
Read events
3 739
Write events
15
Delete events
4
Modification events
| (PID) Process: | (7756) 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (7820) icsys.icn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (7840) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (7840) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (7840) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (7840) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
| (PID) Process: | (7884) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (7884) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (7884) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (7884) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
Executable files
5
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7840 | explorer.exe | C:\Windows\Resources\spoolsv.exe | executable | |
MD5:5FB65759720A00DD3C6C26D504ABB3BC | SHA256:643C82F76BA506C987F8E8D60FC43120334022CF855A5E6CA3F4B9BF35CCDBD5 | |||
| 7756 | 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:5D805C9D25BD13EA576B7EAF8F20E4A2 | SHA256:930AAB9239E153398A8B6488FB1E4B4F7F340B2F23870E3641796A0F103670EF | |||
| 7756 | 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe | C:\Users\admin\AppData\Local\Temp\~DF589B0044E5715BB1.TMP | binary | |
MD5:8C16223F725A3111F00EA7F4729EE82B | SHA256:9829575B65CC016E6C54755257242D4FDCCF372FF73A1D690BB053D4E39DC88E | |||
| 7864 | spoolsv.exe | C:\Windows\Resources\svchost.exe | executable | |
MD5:0CA1FBD68C38536321F8836108063C4D | SHA256:7A2C00677E925D170865ACF455F45848A3BBEBE883FD0B925D3AD9A7297880DE | |||
| 7908 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF2C4C319604B9D212.TMP | binary | |
MD5:71F3246F1EA067E148A98A31006BCBEF | SHA256:E4D7AEBD7381E8A8743D65B44B5CAEFA37532E6D5FF298100E7302C5DEDA42C4 | |||
| 7820 | icsys.icn.exe | C:\Windows\Resources\Themes\explorer.exe | executable | |
MD5:59247587FDC74BA34C3861F7B40E3BB9 | SHA256:EE353159DAF88715B40A29856296EE3BABB7B3B2BEE918BC993AEAA52697D82C | |||
| 7756 | 2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe | C:\Users\admin\Desktop\2025-04-29_c7e8d9358d020015a3e489657a94d761_black-basta_elex_swisyn.exe | executable | |
MD5:88349710979DC54240C13A9F6A5EBAF3 | SHA256:91B298D5F72C3F9679FD573E3A0E4AD7E994BBC83DBA1E937B1EF2176272A4BD | |||
| 7864 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF715202F8AC942135.TMP | binary | |
MD5:2781CDC6F2671B69EEA2E61348171419 | SHA256:AC07F759BB84FF2F6605E17613F454FB169EA35EC39FC284656DE5837FF02F1B | |||
| 7820 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DF91C7F4CB4F9CD1A2.TMP | binary | |
MD5:5F97108DDF86D8B4FED64C5D6A9C2CB2 | SHA256:19BC2A82666820B75E06344413AA77ACA88D407DEFDD1A6946B6C761467ADADC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
23
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
2104 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7412 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6248 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |