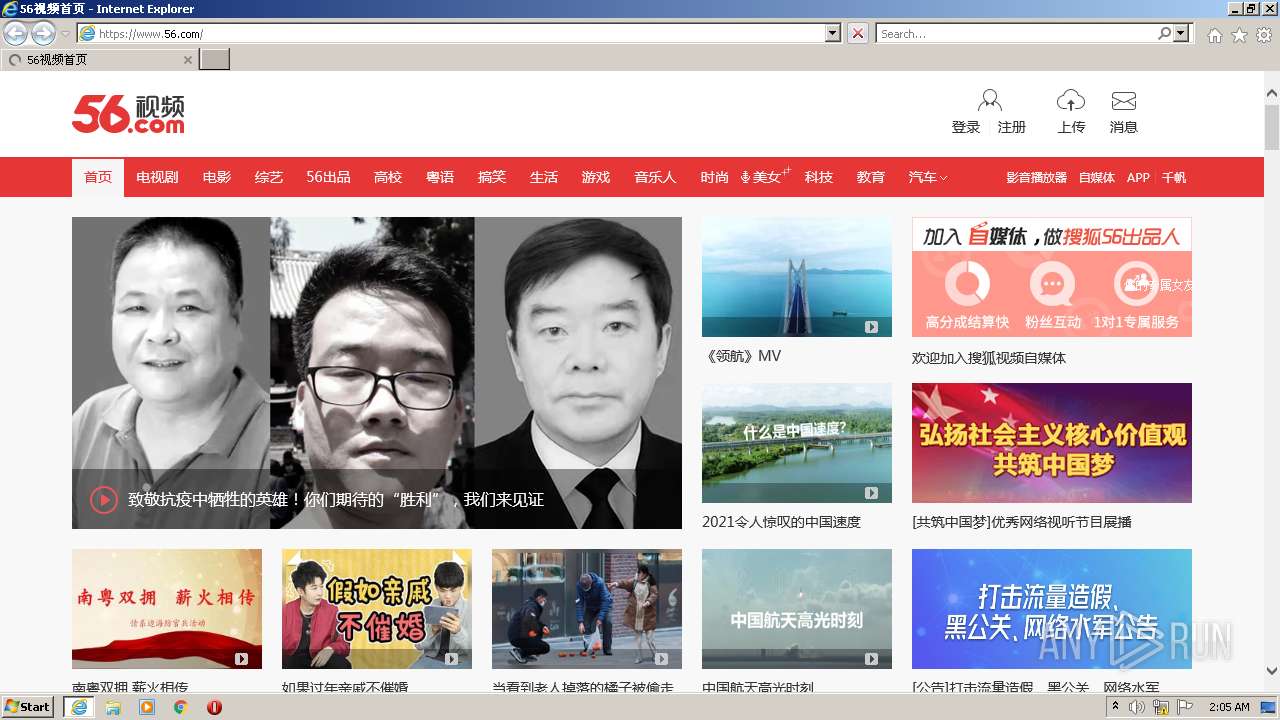
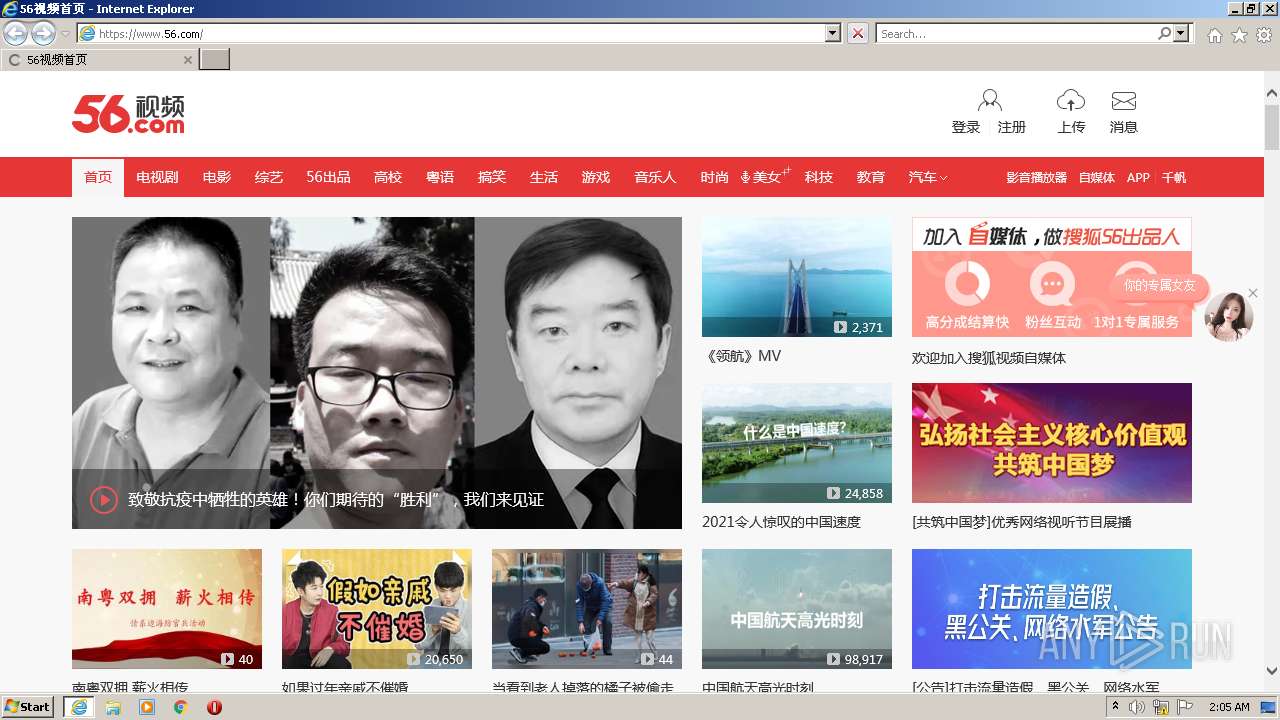
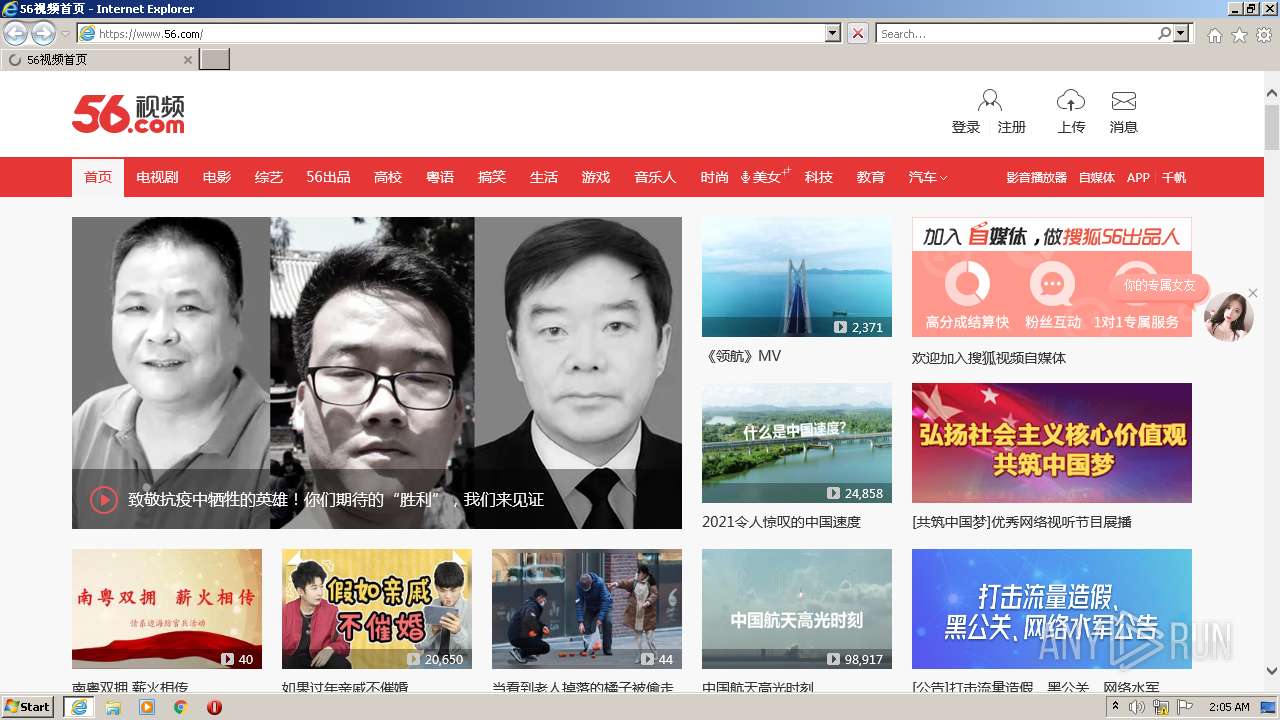
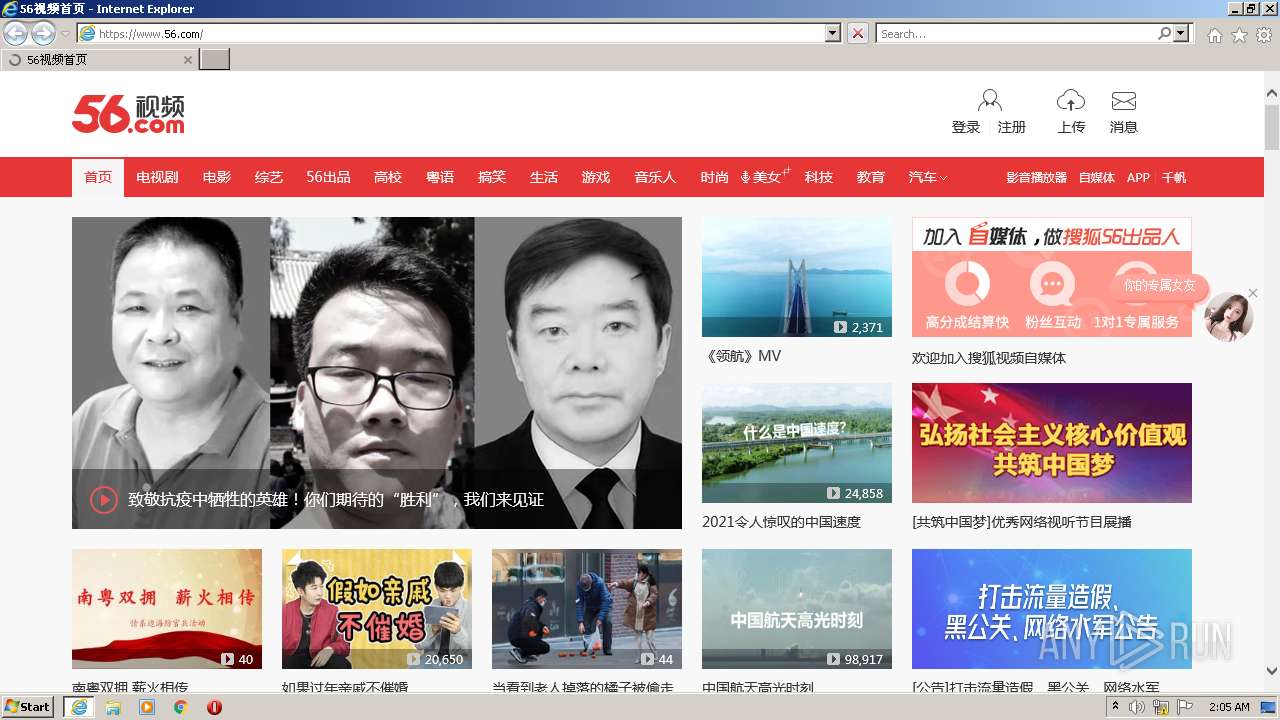
| URL: | https://waaw.to |
| Full analysis: | https://app.any.run/tasks/b343ef18-a565-4683-8028-3bc8d651a1f3 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 02:04:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | BE4607C00158636F3ECAD83A2975FB46 |
| SHA1: | BEC8CE19A16FBD2E892D9D632302174144B0A9E3 |
| SHA256: | D95666F42172762064CA0C2166B84C066041ADE2B9E2D2326007877825E55811 |
| SSDEEP: | 3:N8V7Ls:2Js |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3096)
Executed via COM
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 712)
Checks supported languages
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 712)
Reads the computer name
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 712)
Creates files in the user directory
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 712)
INFO
Reads the computer name
- iexplore.exe (PID: 1536)
- iexplore.exe (PID: 3096)
Checks supported languages
- iexplore.exe (PID: 3096)
- iexplore.exe (PID: 1536)
Application launched itself
- iexplore.exe (PID: 1536)
Changes internet zones settings
- iexplore.exe (PID: 1536)
Reads settings of System Certificates
- iexplore.exe (PID: 1536)
- iexplore.exe (PID: 3096)
Checks Windows Trust Settings
- iexplore.exe (PID: 1536)
- iexplore.exe (PID: 3096)
Reads internet explorer settings
- iexplore.exe (PID: 3096)
Reads CPU info
- iexplore.exe (PID: 3096)
Creates files in the user directory
- iexplore.exe (PID: 3096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 712 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe� Flash� Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
| 1536 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://waaw.to" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3096 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1536 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
22 612
Read events
22 489
Write events
123
Delete events
0
Modification events
| (PID) Process: | (1536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937286 | |||
| (PID) Process: | (1536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937286 | |||
| (PID) Process: | (1536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
22
Text files
466
Unknown types
60
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 1536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_AD319D6DA1A11BC83AC8B4E4D3638231 | binary | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FA0A17BC17FF10008872A7205D0D43E2_608DEF97DFACECDA8E97C6F270153A4F | der | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8F8712BCE78D28F9C5E3E950CD93EADA_94BA1EE559385DB09247581F5A08FD7C | der | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FA0A17BC17FF10008872A7205D0D43E2_608DEF97DFACECDA8E97C6F270153A4F | binary | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\MV1QWARZ.htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
100
TCP/UDP connections
266
DNS requests
71
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3096 | iexplore.exe | GET | 200 | 79.133.177.229:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAoEcNCWvIoSyJCm34Ju7Es%3D | RU | der | 471 b | whitelisted |
3096 | iexplore.exe | GET | 200 | 79.133.177.229:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAxG49zVf%2FDNeB%2F3ST0m558%3D | RU | der | 471 b | whitelisted |
3096 | iexplore.exe | GET | 200 | 79.133.177.229:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAh%2BGPuPqpJ%2B6HYKDYmC9RI%3D | RU | der | 471 b | whitelisted |
3096 | iexplore.exe | GET | 200 | 79.133.177.229:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAa1OdaeBCsLRxbJ177VTqk%3D | RU | der | 471 b | whitelisted |
3096 | iexplore.exe | GET | 200 | 79.133.177.229:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHv1Dj%2BciPJEWH5JNtwL5Y07mRqwQUxBF%2BiECGwkG%2FZfMa4bRTQKOr7H0CEATG1Kc0LXrYXSDbzkAC2zY%3D | RU | der | 471 b | whitelisted |
3096 | iexplore.exe | GET | 200 | 101.33.11.29:80 | http://i0.itc.cn/20151009/348e_0504fee8_c0da_f629_1c13_ae37382441fa_1.jpg | CN | image | 15.9 Kb | suspicious |
3096 | iexplore.exe | GET | 200 | 101.33.11.29:80 | http://i0.itc.cn/20151009/34b0_2c773446_2512_b763_5269_d146d3fb5e2b_1.jpg | CN | image | 33.3 Kb | suspicious |
3096 | iexplore.exe | GET | 200 | 101.33.11.29:80 | http://i0.itc.cn/20150731/34b0_829956b8_c32a_ae36_64bc_c75ac9fe28bd_1.jpg | CN | image | 60.0 Kb | suspicious |
3096 | iexplore.exe | GET | 200 | 79.133.177.218:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTRXf%2BqAIajMnZeiQcx27p1CzET2wQUJG%2BRP4mHhw4ywkAY38VM60%2FISTICEAS%2Ba9HMQvYWOI%2Ff8xOfGl8%3D | RU | der | 471 b | whitelisted |
3096 | iexplore.exe | GET | 200 | 101.33.11.29:80 | http://i0.itc.cn/20151009/34b0_dca9af64_6242_1edd_4d43_ed75804abef5_1.jpg | CN | image | 32.7 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3096 | iexplore.exe | 163.171.129.134:443 | js.tv.itc.cn | — | US | malicious |
— | — | 163.171.129.134:443 | js.tv.itc.cn | — | US | malicious |
— | — | 101.33.11.29:443 | css.tv.itc.cn | — | CN | unknown |
— | — | 101.33.11.29:80 | css.tv.itc.cn | — | CN | unknown |
3096 | iexplore.exe | 172.67.154.15:443 | waaw.to | — | US | suspicious |
1536 | iexplore.exe | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 8.247.210.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | unknown |
— | — | 8.253.208.112:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | unknown |
1536 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3096 | iexplore.exe | 104.21.4.65:443 | waaw.to | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
waaw.to |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.56.com |
| malicious |
ocsp.dcocsp.cn |
| whitelisted |
s2.56img.com |
| whitelisted |
css.tv.itc.cn |
| whitelisted |
js.tv.itc.cn |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
3096 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3096 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed ZeroSSL SSL/TLS Certificate |