| URL: | https://waaw.to |
| Full analysis: | https://app.any.run/tasks/98533674-3bce-46ee-ac89-b53e26033998 |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2023, 11:40:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | BEC8CE19A16FBD2E892D9D632302174144B0A9E3 |
| SHA256: | D95666F42172762064CA0C2166B84C066041ADE2B9E2D2326007877825E55811 |
| SSDEEP: | 3:N8V7Ls:2Js |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3488)
Checks supported languages
- wmpnscfg.exe (PID: 3488)
Reads the computer name
- wmpnscfg.exe (PID: 3488)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3488)
Application launched itself
- iexplore.exe (PID: 3156)
The process uses the downloaded file
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3156 CREDAT:202020 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 756 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\System32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
| 2928 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3156 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
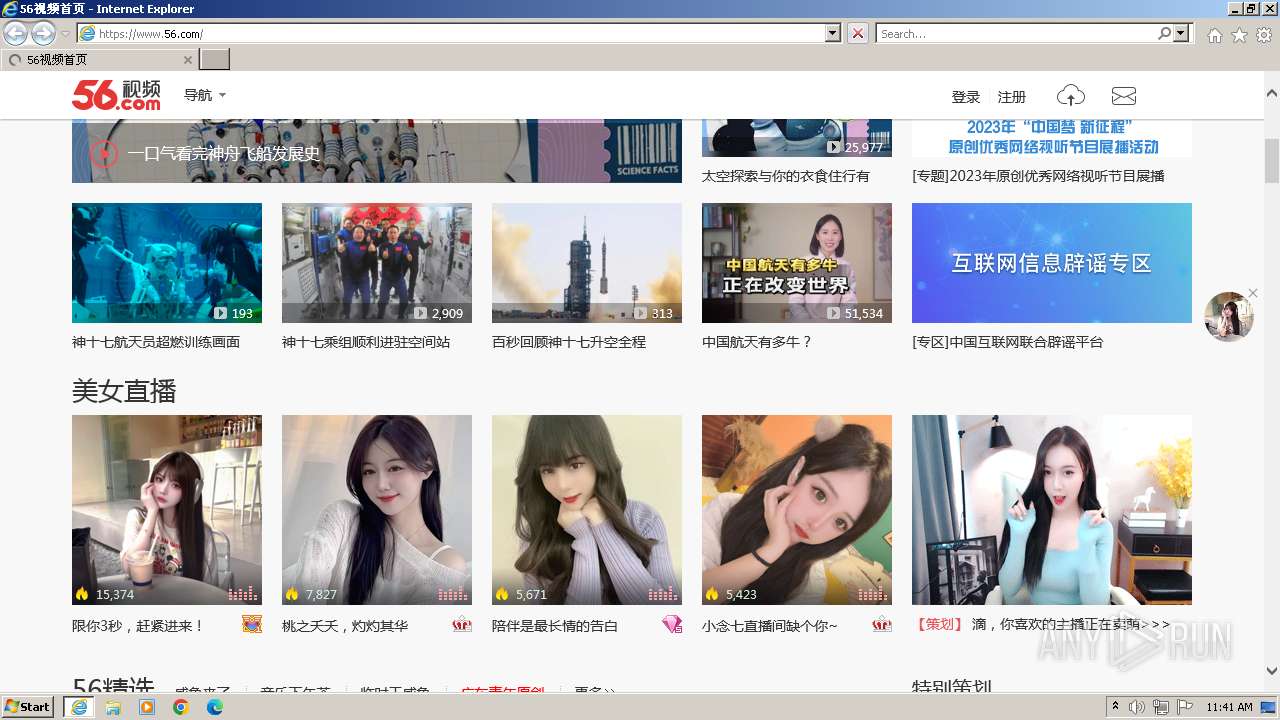
| 3156 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://waaw.to" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3488 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
34 474
Read events
34 378
Write events
89
Delete events
7
Modification events
| (PID) Process: | (3156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000059010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
152
Text files
487
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FA0A17BC17FF10008872A7205D0D43E2_608DEF97DFACECDA8E97C6F270153A4F | binary | |
MD5:F327DCA5DECDFB31BDC8BFE64D3306A9 | SHA256:8B2622183E352C56EFCD06AD90F40650B9187D14B60A6085F92F014F93774C89 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8F8712BCE78D28F9C5E3E950CD93EADA_65D3F18F78AEAA18B0E58242F7706360 | binary | |
MD5:0B16B4409B9AA6A56B9274A25AA1FF0D | SHA256:BDBCB1334AB68A3C30CAA268F2604866E16D8A53102F2EADB302992CAB9DC3D3 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:C162E851B6C89BB1A9E0B5FD865581EC | SHA256:F8A2DE578ECBC7CE4BDC5EF18505AA5519A008E3610F7BE04EAB2695E16981FF | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:FD8683C7BBA5235E41EE9FA3F42FF378 | SHA256:8C73288DB2622DC543FB00067957F49EA762079DFC9534F65B532B5BDB21F3C7 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\MTAwMTE0XzE2OTgyOTA5Mjc2NzM=[1].jpg | image | |
MD5:0E9CD1378C5E7A21AF5B28B80B963416 | SHA256:55BD156AF80B207AD87C49419C6EF27AAE108699648776787B70D3ACDE3E0A83 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FA0A17BC17FF10008872A7205D0D43E2_608DEF97DFACECDA8E97C6F270153A4F | binary | |
MD5:9B75C672F422185DA048D1B9524B6681 | SHA256:D489C51BD58D96F08D68E1929D246813EC6742F4B6520675B83F34344A150497 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\N3VQPIOG.htm | html | |
MD5:955594F8E4773821DB4D311F01BC15F8 | SHA256:AAAEC65CD43BB8F67F7E8D3CF9E7DD2B8196C6CC6152CFC0CFDCA2FE6B5B90B4 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8F8712BCE78D28F9C5E3E950CD93EADA_65D3F18F78AEAA18B0E58242F7706360 | binary | |
MD5:AB6193E433BB802395B76881B6F41F89 | SHA256:E9FD3AEE42B480BCE73D758207D2E26E107AA42B9B672875040C25FEBFAD45E6 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:13478DFB63522ABD5969ADD38A71398A | SHA256:B3F1D6F6D8494598C706676F53B55F05C563937A525B2D2A9A0FE6525E2AF3AC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
110
TCP/UDP connections
245
DNS requests
79
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2928 | iexplore.exe | GET | — | 163.171.130.132:80 | http://i3.itc.cn/20150824/34b0_5d2abeab_e780_9619_9848_f536757fed74_1.jpg | unknown | — | — | unknown |
2928 | iexplore.exe | GET | — | 43.152.44.160:80 | http://i0.itc.cn/20151009/34b0_2c773446_2512_b763_5269_d146d3fb5e2b_1.jpg | unknown | — | — | unknown |
2928 | iexplore.exe | GET | — | 43.152.44.160:80 | http://i0.itc.cn/20151009/34b0_dca9af64_6242_1edd_4d43_ed75804abef5_1.jpg | unknown | — | — | unknown |
2928 | iexplore.exe | GET | — | 43.152.44.160:80 | http://i0.itc.cn/20150731/34b0_829956b8_c32a_ae36_64bc_c75ac9fe28bd_1.jpg | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 200 | 23.53.40.51:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a1f744e7e9e1d6c2 | unknown | compressed | 4.66 Kb | unknown |
2928 | iexplore.exe | GET | 200 | 23.53.40.51:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d6bb2ad0af14907d | unknown | compressed | 4.66 Kb | unknown |
2928 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | binary | 979 b | unknown |
2928 | iexplore.exe | GET | 200 | 163.181.56.209:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAJ%2BYV%2FN5W2THg4NuR8pUi8%3D | unknown | binary | 471 b | unknown |
2928 | iexplore.exe | GET | 200 | 163.181.56.209:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAoEcNCWvIoSyJCm34Ju7Es%3D | unknown | binary | 471 b | unknown |
2928 | iexplore.exe | GET | 200 | 163.181.56.209:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEARG1gQtWCJqly6jHNwHlBA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2928 | iexplore.exe | 190.115.19.71:443 | waaw.to | DDOS-GUARD CORP. | BZ | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2928 | iexplore.exe | 23.53.40.51:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2928 | iexplore.exe | 172.64.149.23:80 | ocsp.usertrust.com | CLOUDFLARENET | US | unknown |
2928 | iexplore.exe | 13.75.75.123:443 | www.56.com | MICROSOFT-CORP-MSN-AS-BLOCK | HK | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2928 | iexplore.exe | 163.181.56.209:80 | ocsp.dcocsp.cn | Zhejiang Taobao Network Co.,Ltd | DE | unknown |
2928 | iexplore.exe | 163.181.92.232:443 | photocdn.tv.sohu.com | Zhejiang Taobao Network Co.,Ltd | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
waaw.to |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
www.56.com |
| unknown |
ocsp.dcocsp.cn |
| whitelisted |
s2.56img.com |
| whitelisted |
css.tv.itc.cn |
| whitelisted |
js.tv.itc.cn |
| unknown |
s1.56img.com |
| whitelisted |
tv.sohu.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |