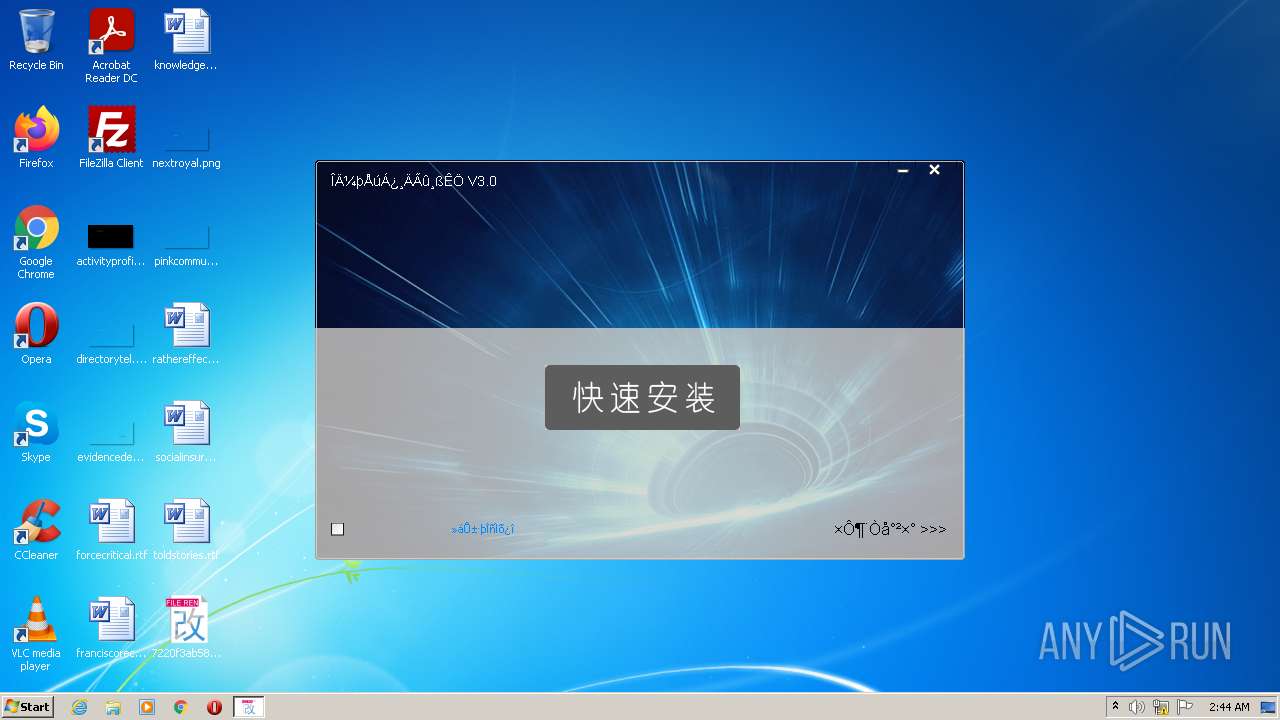
| File name: | 7220f3ab5807fadac06c60d81e60678c.exe.vir |
| Full analysis: | https://app.any.run/tasks/10a08d25-5a4b-42c0-a67b-cc97b7187814 |
| Verdict: | Malicious activity |
| Analysis date: | January 25, 2022, 02:44:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7220F3AB5807FADAC06C60D81E60678C |
| SHA1: | A7F097330C80902EEDC75F6281833FFF33C99BFC |
| SHA256: | D94901376072D9C338260523B55DE650CBA7753E067E35EF8D3A343426C35BA0 |
| SSDEEP: | 98304:TZbhB+wK3lJZOHnISblHZTi+P7SVduApm77Gsj1w63kcdfc:TZbhI3Z65vTiM7IdRFT63Tdfc |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe (PID: 292)
Reads the computer name
- 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe (PID: 292)
Drops a file with a compile date too recent
- 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe (PID: 292)
Checks supported languages
- 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe (PID: 292)
Executable content was dropped or overwritten
- 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe (PID: 292)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (24.4) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.6) |
| .exe | | | UPX compressed Win32 Executable (21.2) |
| .exe | | | Win32 EXE Yoda's Crypter (20.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.1) |
EXIF
EXE
| ProductVersion: | V3.0 |
|---|---|
| ProductName: | 文件批量改名高手 |
| OriginalFileName: | 文件批量改名高手.exe |
| LegalCopyright: | 仙游县灵云软件开发有限公司 www.meimengsoft.com 版权所有 |
| InternalName: | 文件批量改名高手 |
| FileVersion: | 3,0,0,0 |
| FileDescription: | 文件批量改名高手V3.0 软件安装程序 |
| CompanyName: | 仙游县灵云软件开发有限公司 |
| Comments: | 文件批量改名高手的软件安装包 |
| CharacterSet: | Unicode |
| LanguageCode: | Chinese (Simplified) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 0.0.0.0 |
| FileVersionNumber: | 3.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0xe9163 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 1294336 |
| CodeSize: | 1089536 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| TimeStamp: | 2022:01:05 15:36:23+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 05-Jan-2022 14:36:23 |
| Detected languages: |
|
| Comments: | 文件批量改名高手的软件安装包 |
| CompanyName: | 仙游县灵云软件开发有限公司 |
| FileDescription: | 文件批量改名高手V3.0 软件安装程序 |
| FileVersion: | 3,0,0,0 |
| InternalName: | 文件批量改名高手 |
| LegalCopyright: | 仙游县灵云软件开发有限公司 www.meimengsoft.com 版权所有 |
| OriginalFilename: | 文件批量改名高手.exe |
| ProductName: | 文件批量改名高手 |
| ProductVersion: | V3.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 05-Jan-2022 14:36:23 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0010989A | 0x0010A000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.50018 |
.rdata | 0x0010B000 | 0x000F4C14 | 0x000F5000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.65806 |
.data | 0x00200000 | 0x0007A26A | 0x0001D000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.45592 |
.rsrc | 0x0027B000 | 0x00029D3C | 0x0002A000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.99001 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.07695 | 461 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
2 | 2.18858 | 296 | Latin 1 / Western European | Chinese - PRC | RT_ICON |
3 | 7.97213 | 32952 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 2.74274 | 180 | Latin 1 / Western European | Chinese - PRC | RT_CURSOR |
5 | 2.37095 | 308 | Latin 1 / Western European | Chinese - PRC | RT_CURSOR |
6 | 2.42931 | 308 | Latin 1 / Western European | Chinese - PRC | RT_CURSOR |
8 | 3.28608 | 296 | Latin 1 / Western European | UNKNOWN | RT_ICON |
9 | 4.24848 | 1384 | Latin 1 / Western European | UNKNOWN | RT_ICON |
10 | 4.8653 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
11 | 4.63012 | 2440 | Latin 1 / Western European | UNKNOWN | RT_ICON |
Imports
ADVAPI32.dll |
AVIFIL32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
MSVFW32.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
WINMM.dll |
Total processes
36
Monitored processes
1
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Users\admin\Desktop\7220f3ab5807fadac06c60d81e60678c.exe.vir.exe" | C:\Users\admin\Desktop\7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | Explorer.EXE | ||||||||||||
User: admin Company: ????????????? Integrity Level: MEDIUM Description: ????????V3.0 ?????? Exit code: 0 Version: 3,0,0,0 Modules
| |||||||||||||||
Total events
413
Read events
410
Write events
3
Delete events
0
Modification events
| (PID) Process: | (292) 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{53BAD8C1-E718-11CF-893D-00A0C9054228}\TypeLib |
| Operation: | write | Name: | (default) |
Value: {F935DC20-1CF0-11D0-ADB9-00C04FD58A0B} | |||
Executable files
2
Suspicious files
0
Text files
5
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 292 | 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | C:\fileren\-�++-�+�.txt | text | |
MD5:— | SHA256:— | |||
| 292 | 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\�ļ�������������\�ļ�������������.lnk | lnk | |
MD5:— | SHA256:— | |||
| 292 | 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | C:\fileren\data\set.ini | text | |
MD5:— | SHA256:— | |||
| 292 | 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\�ļ�������������\ж�ء��ļ������������֡�.lnk | lnk | |
MD5:— | SHA256:— | |||
| 292 | 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | C:\fileren\data\logo.jpg | image | |
MD5:461E679E627AD01F85CBE3F38A682518 | SHA256:F21E3F03798F4086B6A0377BA8E37E219A8B6CBCBCE425B72BD45924B776BE45 | |||
| 292 | 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | C:\Users\admin\Desktop\�ļ�������������.lnk | lnk | |
MD5:— | SHA256:— | |||
| 292 | 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | C:\fileren\+-+�+�-++-+v+�-+.exe | executable | |
MD5:— | SHA256:— | |||
| 292 | 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | C:\fileren\data\v.ico | image | |
MD5:447418706C992AA4BC97D384F3928A18 | SHA256:21E8FF397F7973A25AD722F192DABE58C4ACCDD9ED1BEB22689DD80CE26F32E2 | |||
| 292 | 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | C:\fileren\uninstall.dat | text | |
MD5:B4AB309E7A954FBED7778068D9C58F7B | SHA256:AC43995B22B0EF8529949CFD5A035C72259355B535CDAE5F6423A6270EB60F54 | |||
| 292 | 7220f3ab5807fadac06c60d81e60678c.exe.vir.exe | C:\fileren\uninstall.exe | executable | |
MD5:460A4E5957F2144BC94E1DFC83E18790 | SHA256:FD0CF68B92646D126F94F321816CC76DC237FB30AA5BB233C7DB24B63EE55AEA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report