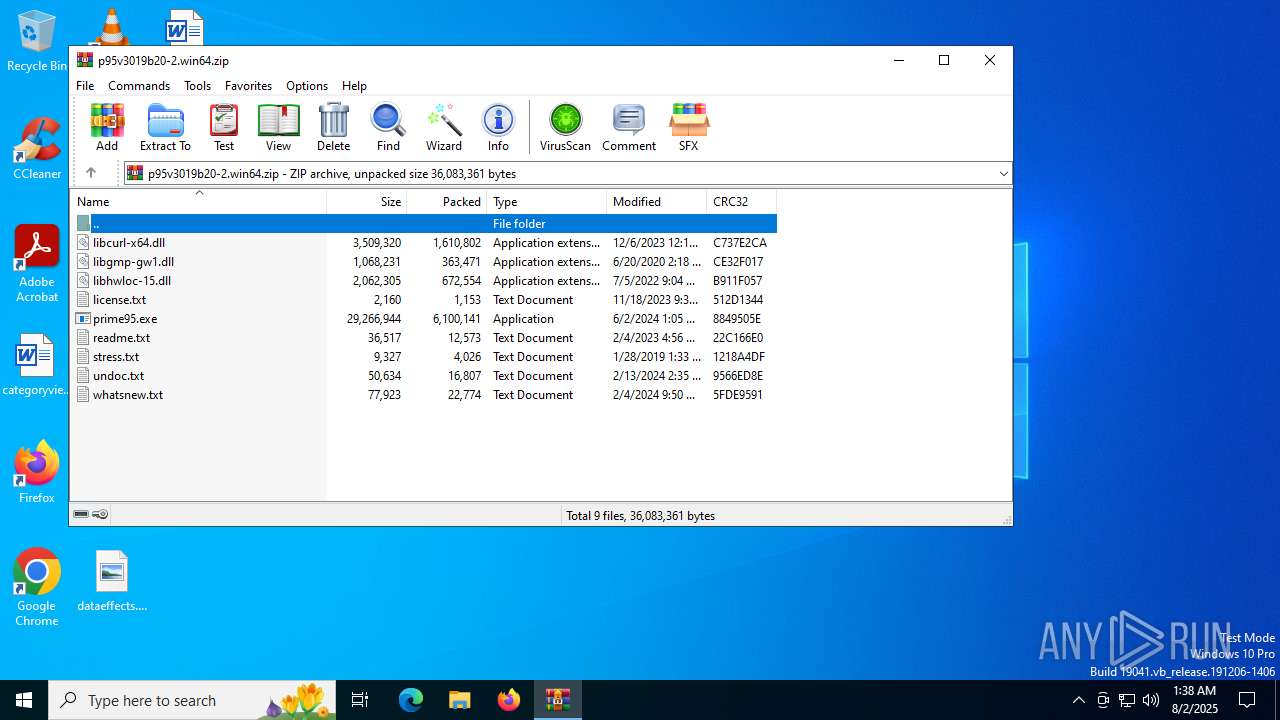
| File name: | p95v3019b20-2.win64.zip |
| Full analysis: | https://app.any.run/tasks/f906d6df-24ef-4243-a769-9c1e675e07c2 |
| Verdict: | Malicious activity |
| Analysis date: | August 02, 2025, 01:37:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 7A4AC1F3FF0045951FE6AD66E36C7929 |
| SHA1: | 51A5849E8652B69909CCE28F1D5F5697D96C1571 |
| SHA256: | D9475F2FF3F4A6A701ABC49A86A66126CB48ABD10BDA6FA87039D98FA8756BCA |
| SSDEEP: | 98304:SWSSz6H/Esh5ilPfNCtaTUEhbY5ngCqNjh/YNWNzvPlQaT211G6+xPrwvWWZ8qgE:1xRHgvNQl19f23 |
MALICIOUS
MIMIKATZ has been detected (YARA)
- prime95.exe (PID: 440)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6360)
There is functionality for taking screenshot (YARA)
- prime95.exe (PID: 440)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6360)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6360)
Reads Windows Product ID
- prime95.exe (PID: 440)
Checks supported languages
- prime95.exe (PID: 440)
Create files in a temporary directory
- prime95.exe (PID: 440)
Reads the computer name
- prime95.exe (PID: 440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:06 08:15:22 |
| ZipCRC: | 0xc737e2ca |
| ZipCompressedSize: | 1610802 |
| ZipUncompressedSize: | 3509320 |
| ZipFileName: | libcurl-x64.dll |
Total processes
138
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\prime95.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\prime95.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: PRIME95 Application Version: 30, 19, 1, 0 Modules
| |||||||||||||||
| 4168 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6360 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\p95v3019b20-2.win64.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
2 621
Read events
2 613
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\p95v3019b20-2.win64.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\libgmp-gw1.dll | executable | |
MD5:4A91F4DEB026574C339C61DF12A81212 | SHA256:817A628A2F8FADC696527D8246D3B1BDE10AA3FC95FD13EBF0F58D9FF68FFDEC | |||
| 440 | prime95.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\prime.txt | text | |
MD5:1688C5FB8E649186101FB6B8BA29C3F1 | SHA256:7AAAF082813D2AC05B84CAFF16919BC515DB01C924AE627A817D92D8B80CCDB9 | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\stress.txt | text | |
MD5:288B408DC7F7A9FC34918AC857591DCF | SHA256:146D5EFDBA4FFB150E23652DF15CB9A70858FB330086BCD4133F0A4300F24D46 | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\license.txt | text | |
MD5:D442FB395F40124EABF62FAE9906FCF0 | SHA256:9D8F6CE09E546117B64FADA383346ADFD0F0C40B3F0E4F8D5C3ED2B2A67DF6D8 | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\libcurl-x64.dll | executable | |
MD5:7B86FEC0ECD59C1393060E1D60DD7AFD | SHA256:CE40AE459704C8C0D7D005C8BE8D280D099E59ACF881DD453C7032323638BDEA | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\libhwloc-15.dll | executable | |
MD5:967AF1CC67142C115695A0821A247616 | SHA256:8DE3DEC1A892D0C4AA5A5985AB2BA7C6346F228D7651E287BEDF3936F0936FB1 | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\whatsnew.txt | text | |
MD5:EBA20A0D9B534BEE3AC48A94B065ED63 | SHA256:5546DBF5539414CF11A3C15CD9ED3DB9D2097504DD6076442A11466B090807E8 | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\readme.txt | text | |
MD5:34A8B96B9A4A49508544D96D51C6855F | SHA256:ED4BF5C3B9D54C0B804E24C4D0EF28E093BA9EAD7B6170335DC1F8A4E1727BC8 | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\undoc.txt | text | |
MD5:8689B8AB5F8BBCA1AC7C0330E0AABA75 | SHA256:DBC7D7FB7CD5615AF7BF51D449000648C7E481C6D6D8061A5E4786C9FBA8A4CB | |||
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.1683\prime95.exe | executable | |
MD5:714D98DD68C4F639A27DE8C836237EBC | SHA256:E28A68AC36DDA0E29CB86D62032D9FFBE37862E926A5E905CD3B20A02CB48289 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2096 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5764 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5764 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3160 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2096 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2096 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |