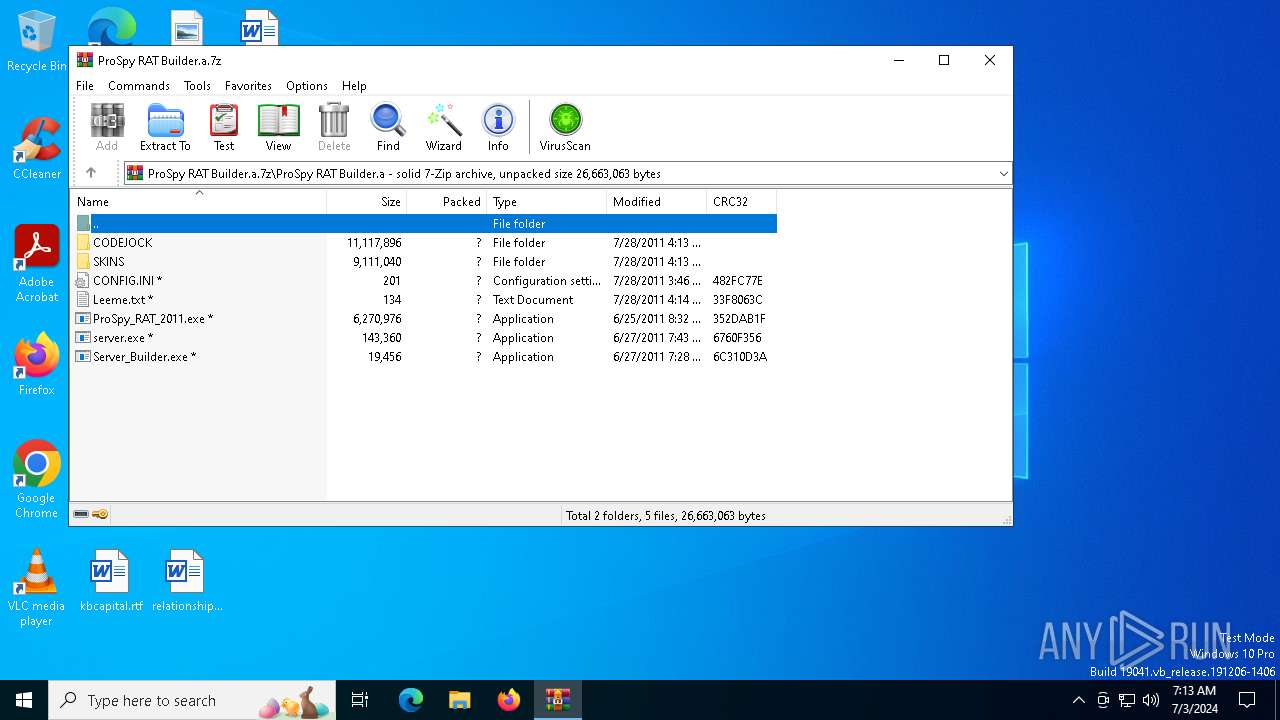
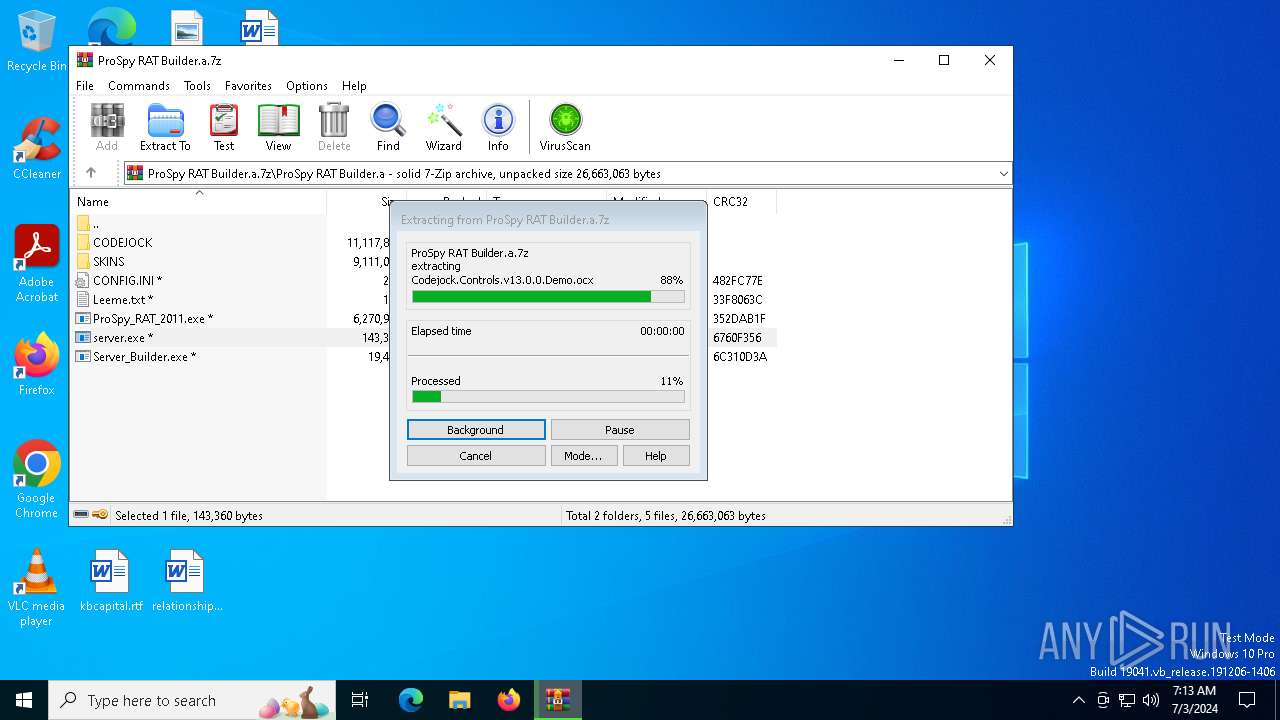
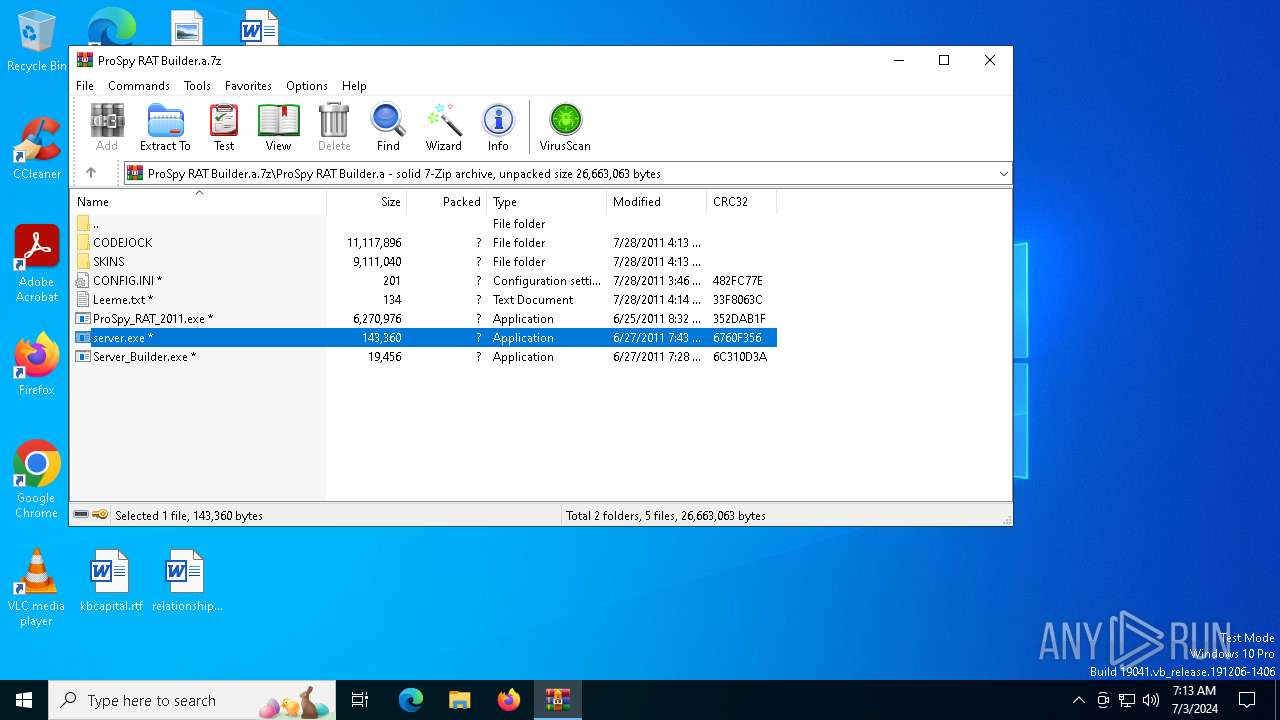
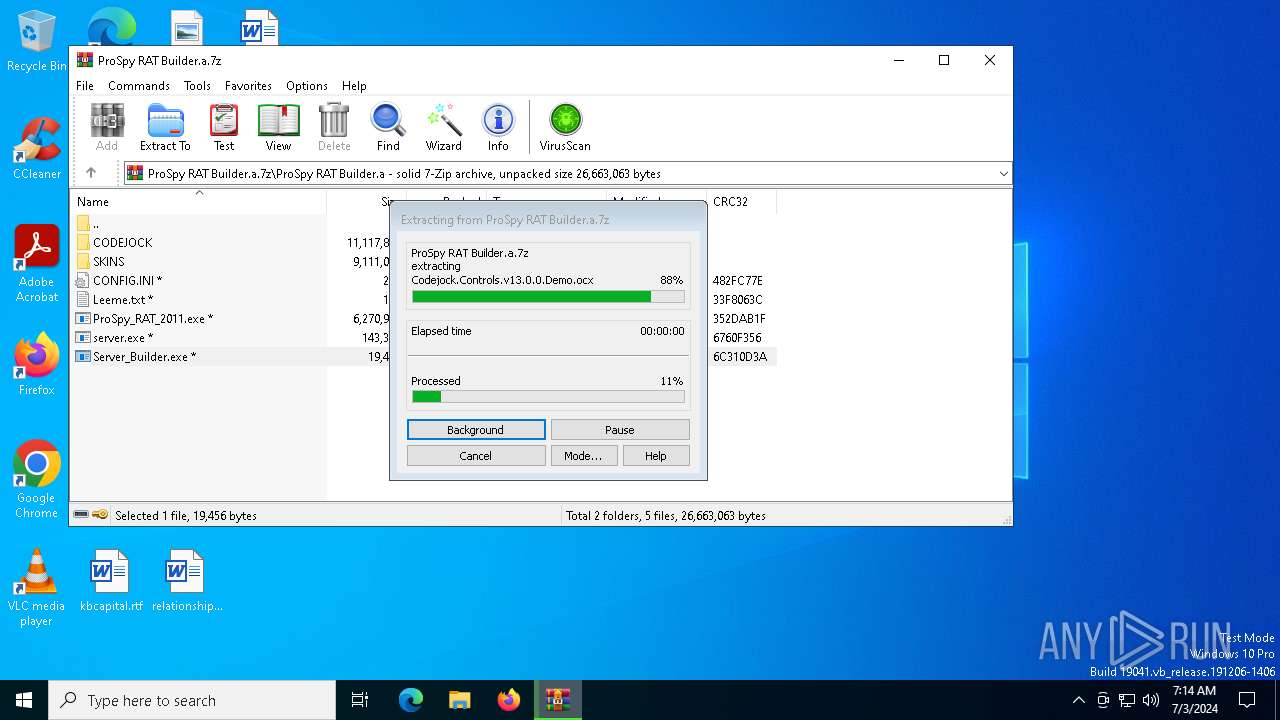
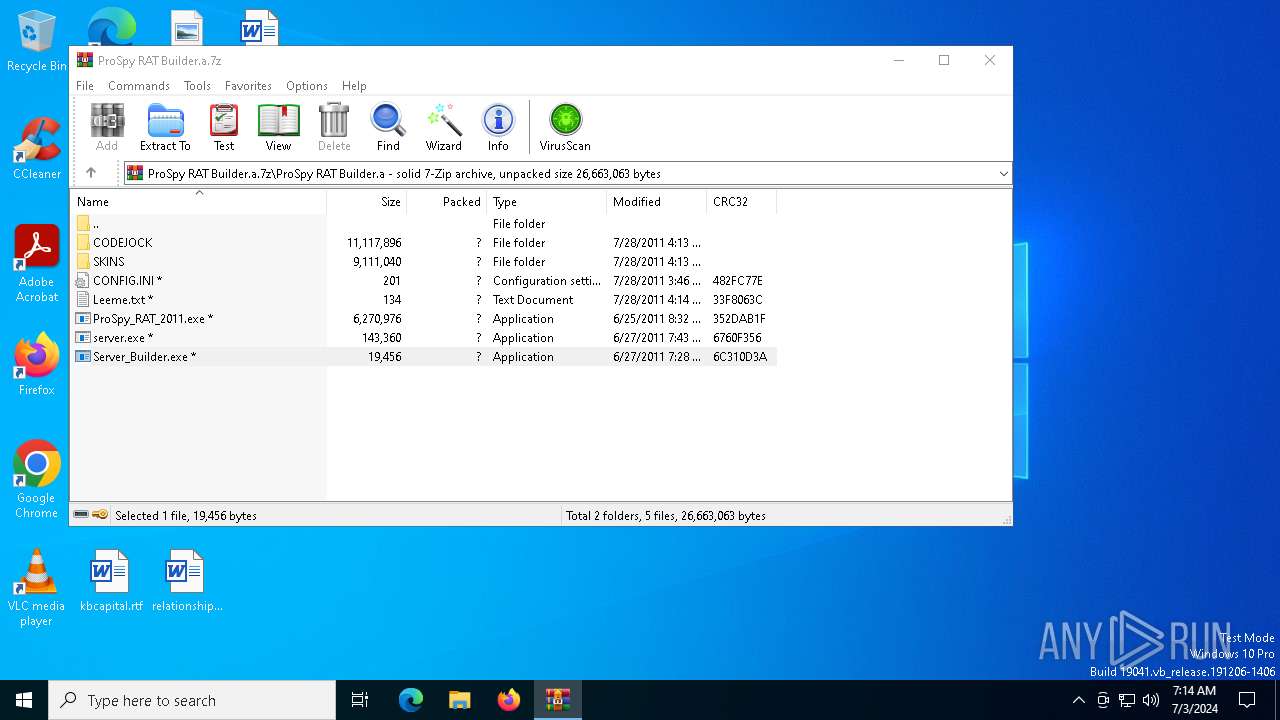
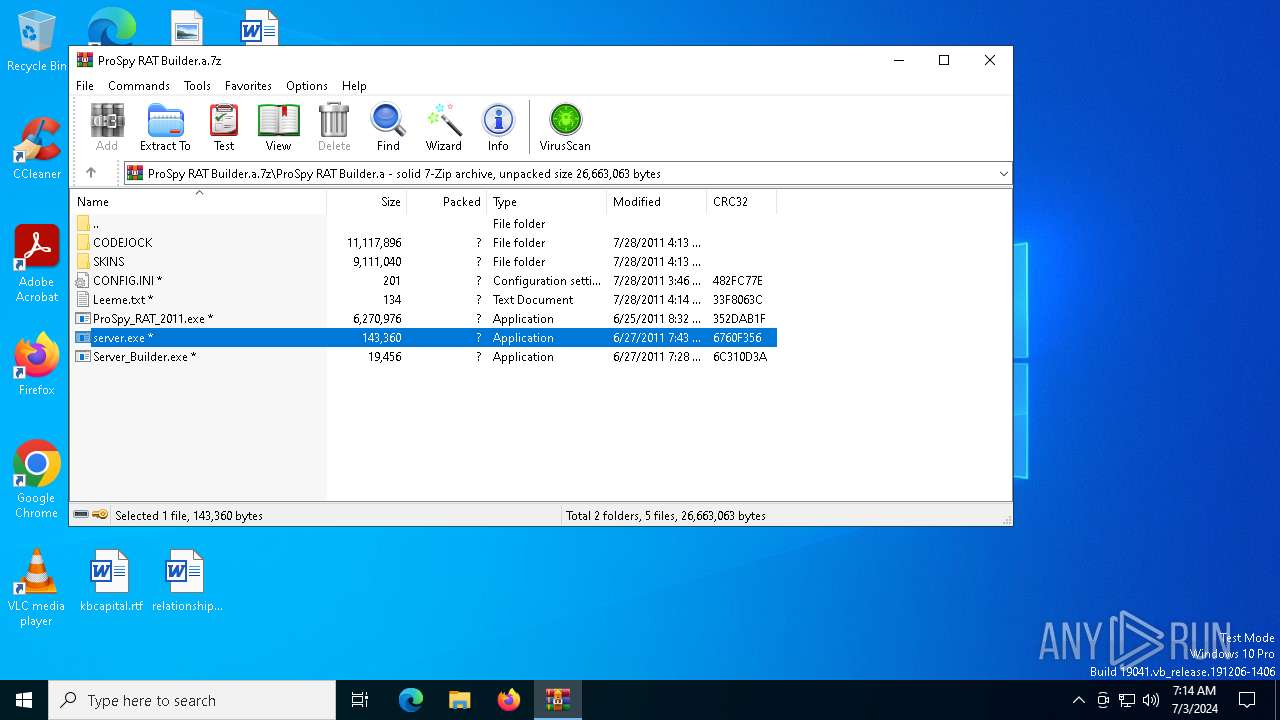
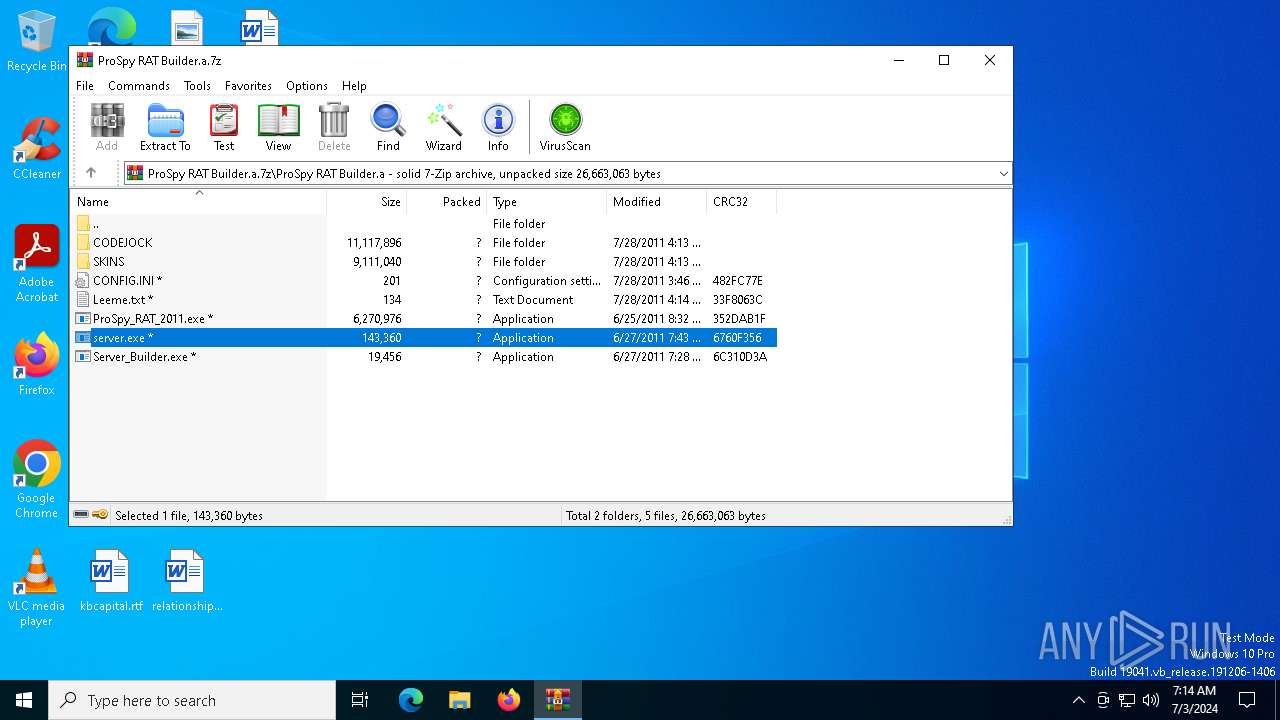
| File name: | ProSpy RAT Builder.a.7z |
| Full analysis: | https://app.any.run/tasks/93b39d07-16b6-49c2-a77d-6929bb14711b |
| Verdict: | Malicious activity |
| Analysis date: | July 03, 2024, 07:13:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 7D608E8AA9E3E5107CD745054047EE8F |
| SHA1: | C2D59DB09486BF649A3951B36AC35442F5564D84 |
| SHA256: | D92614EF8EC35ABDB5E4810E9662E1D05D8B0EAE89018AB3C4D8349D26B046E7 |
| SSDEEP: | 98304:dgSq83gqReijNhVQWVKz2OT275myG+IMi1NlXMs/Cvya8khckHB//eF2h4z39MCf:9NCpuy |
MALICIOUS
Drops the executable file immediately after the start
- server.exe (PID: 452)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2636)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2636)
Starts CMD.EXE for commands execution
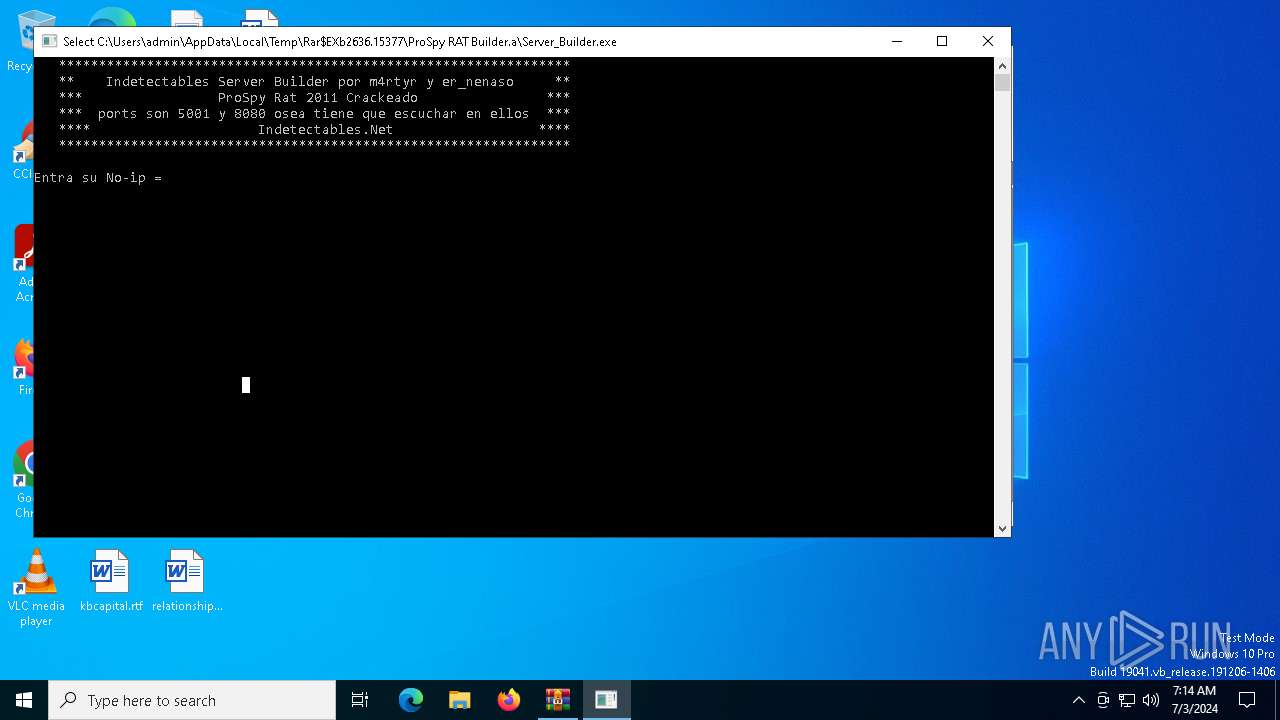
- Server_Builder.exe (PID: 2212)
Executable content was dropped or overwritten
- server.exe (PID: 452)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2636)
Checks supported languages
- server.exe (PID: 452)
- Server_Builder.exe (PID: 2212)
- server.exe (PID: 4424)
Reads the computer name
- server.exe (PID: 452)
Creates files in the program directory
- server.exe (PID: 452)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
136
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 452 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\server.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\server.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Actualizacion de Windows de prioridad maxima Version: 1.00 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2212 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.15377\ProSpy RAT Builder.a\Server_Builder.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.15377\ProSpy RAT Builder.a\Server_Builder.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Server_Builder.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2636 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ProSpy RAT Builder.a.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4424 | C:\WINDOWS\system32\cmd.exe /c pause | C:\Windows\SysWOW64\cmd.exe | — | Server_Builder.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4424 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.16459\ProSpy RAT Builder.a\server.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.16459\ProSpy RAT Builder.a\server.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Actualizacion de Windows de prioridad maxima Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
6 587
Read events
6 568
Write events
19
Delete events
0
Modification events
| (PID) Process: | (2636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ProSpy RAT Builder.a.7z | |||
| (PID) Process: | (2636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
70
Suspicious files
3
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\CODEJOCK\COAABA~1.OCA | executable | |
MD5:3CE9696BAAF1B02079961021DE9D75DB | SHA256:EF01940FC377C06FD1E11FFC7C251957995CF271C4B2D6634599AB1BFF8B04DC | |||
| 2636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\Leeme.txt | text | |
MD5:85D7A901C4F06A3D05A4906FE7C65334 | SHA256:C5A0AE08343AFA7015EA3F237615AE8B93307AC3B1B02DC4E37F31B7003A3C87 | |||
| 2636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\CODEJOCK\CODEJO~2.OCA | executable | |
MD5:AB44CFDE3649E9F50B62B2B0D38046B9 | SHA256:011E3F937179C188D2FCD4426341AB144CF6208FE8A3850525D2DDAF0D9E39EE | |||
| 2636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\CODEJOCK\COD3EF~1.OCA | executable | |
MD5:B39C800840B7F88B3512B77BB95DF86C | SHA256:5E4D50E0BA13AB0845E58C4AE5E00C5F2B337EEA7CFE0F7F6958DBECC23E353F | |||
| 2636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\SKINS\BaltimoreBlack.msstyles | executable | |
MD5:5ACF5097932FC4BC80618912197F6991 | SHA256:F0B80BC0A7E5FFE9C15D4C6DF9E04C75F01625056758CCA73ECF4C6E9B4D97C4 | |||
| 2636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\SKINS\BaltimoreBlue.msstyles | executable | |
MD5:7E987AE8F9DF7299A9AC9CC9EF27AEEF | SHA256:DA5275FA74F1A5C741B7BF8058E3BC7B9F82A56C258E633E03899F281BF84213 | |||
| 2636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\CODEJOCK\CODEJO~3.OCA | executable | |
MD5:C14A418CDE7E767F86D1E5656AA2F76F | SHA256:65F1782049E7907CCC82FA82C70487E64CA6A03A52FB759533E5C539FA7DCFCA | |||
| 2636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\SKINS\Thumbs.db | binary | |
MD5:54F7FB72433440CE5526473FC0E24135 | SHA256:7D2F75473AE20A4C5F966FB4E215909D16C7F5CD65A89917988ED3332AA9E645 | |||
| 2636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\CODEJOCK\COMCTL32.DLL | executable | |
MD5:A77DFB85FAEE49D66C74DA6024EBC69B | SHA256:587FDA8821B611B213ADFEEA7B94E8B3A83870F843D46AF0335584832E9D8644 | |||
| 2636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2636.13573\ProSpy RAT Builder.a\CODEJOCK\COMDLG32.OCX | executable | |
MD5:D76F0EAB36F83A31D411AEAF70DA7396 | SHA256:46F4FDB12C30742FF4607876D2F36CF432CDC7EC3D2C99097011448FC57E997C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
52
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
4820 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.21:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4820 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2912 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4820 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2504 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2624 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3040 | OfficeClickToRun.exe | 52.182.143.208:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3040 | OfficeClickToRun.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4656 | SearchApp.exe | 104.126.37.136:443 | r.bing.com | Akamai International B.V. | DE | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
r.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |