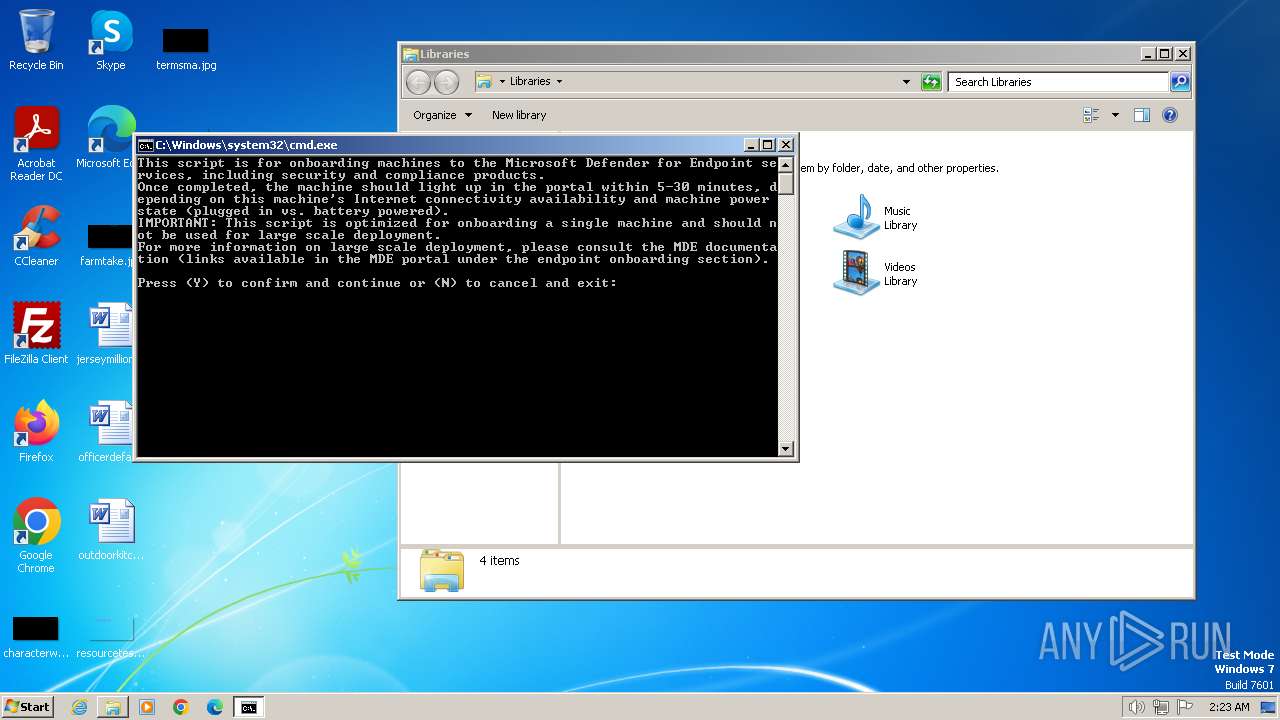
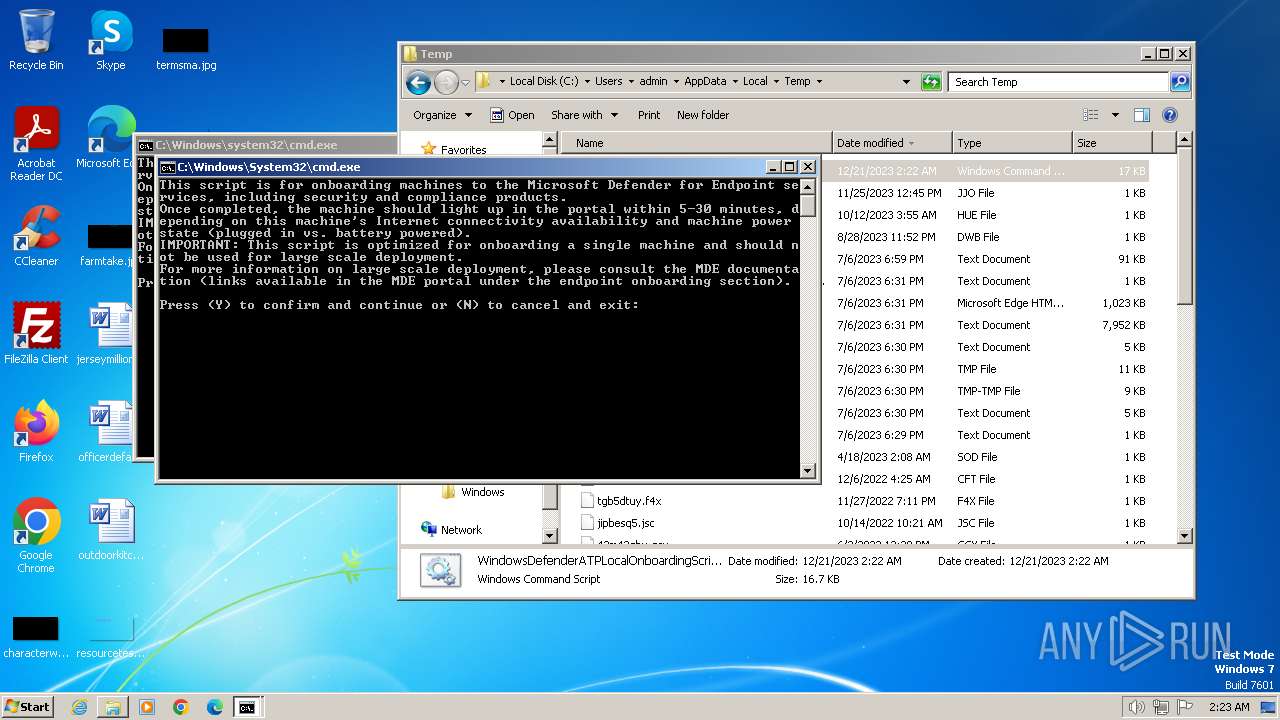
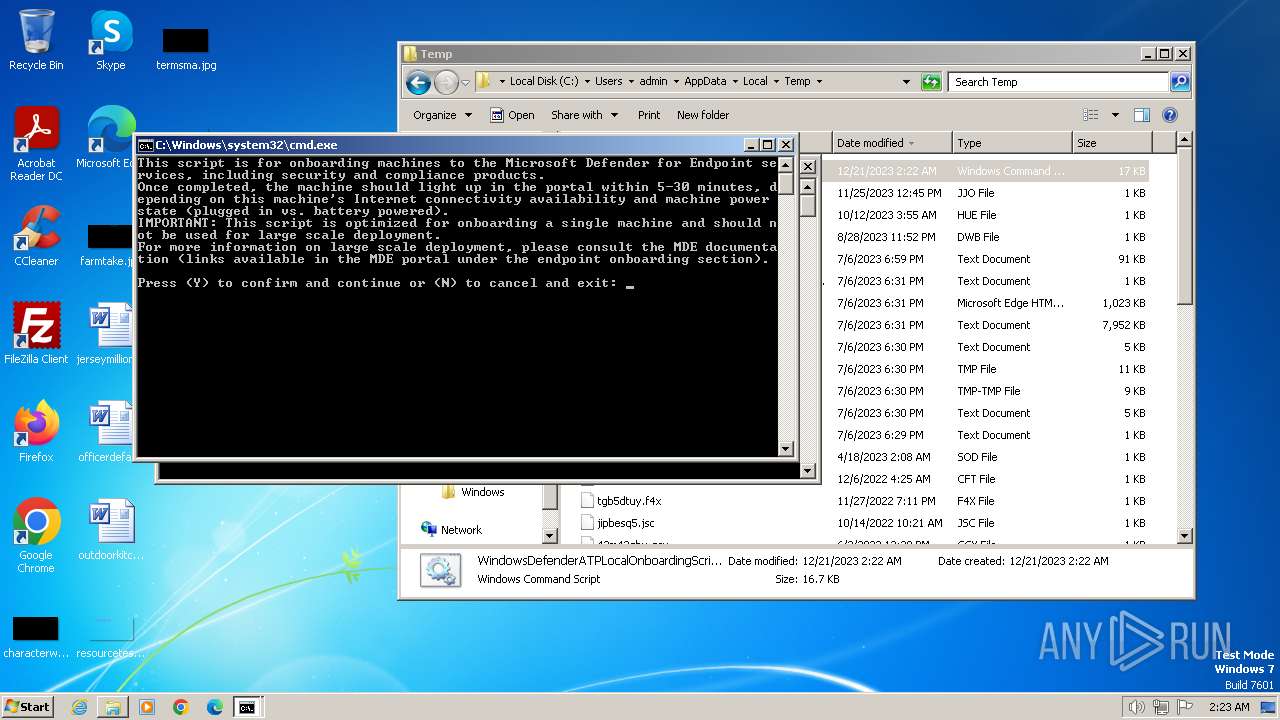
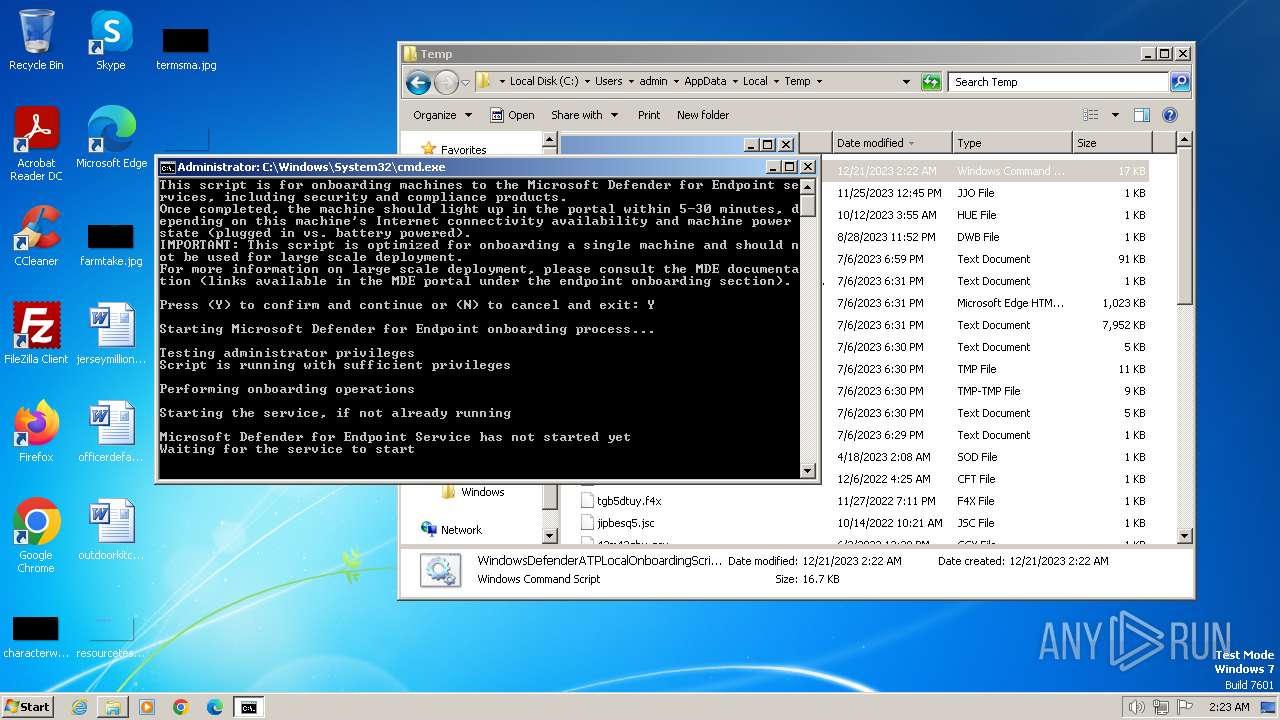
| File name: | WindowsDefenderATPLocalOnboardingScript.cmd |
| Full analysis: | https://app.any.run/tasks/1f304083-0992-424f-9fab-1fa40c0c9a0d |
| Verdict: | Malicious activity |
| Analysis date: | December 21, 2023, 02:22:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines, with CRLF, LF line terminators |
| MD5: | 4175609A64DDD910AA2170302DB56647 |
| SHA1: | 63F8B7DC86E07669D7538F12B55F428835ED0209 |
| SHA256: | D9116F995D9EA521F470D2CB1F00CB2B9BB4BB0C5667A19D05EDF90309959ABE |
| SSDEEP: | 384:UQ7rqhq6uktLekASPSAHJvDZdkaKgHQmAwAHkrfhmOHu:UQ7rUuktLNrvVdkNw8kjhmOO |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 2292)
- powershell.exe (PID: 3012)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 2808)
Starts Visual C# compiler
- powershell.exe (PID: 2292)
- powershell.exe (PID: 3012)
Drops the executable file immediately after the start
- csc.exe (PID: 2884)
- csc.exe (PID: 3236)
Starts NET.EXE for service management
- cmd.exe (PID: 2808)
- net.exe (PID: 2532)
SUSPICIOUS
Uses .NET C# to load dll
- powershell.exe (PID: 2292)
- powershell.exe (PID: 3012)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2808)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2808)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 2808)
Starts SC.EXE for service management
- cmd.exe (PID: 2808)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2808)
INFO
Manual execution by a user
- cmd.exe (PID: 2808)
- explorer.exe (PID: 392)
Reads the machine GUID from the registry
- csc.exe (PID: 2884)
- cvtres.exe (PID: 2816)
- csc.exe (PID: 3236)
- cvtres.exe (PID: 3144)
Checks supported languages
- csc.exe (PID: 2884)
- cvtres.exe (PID: 2816)
- csc.exe (PID: 3236)
- cvtres.exe (PID: 3144)
Create files in a temporary directory
- csc.exe (PID: 2884)
- cvtres.exe (PID: 2816)
- cvtres.exe (PID: 3144)
- csc.exe (PID: 3236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
75
Monitored processes
36
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\WindowsDefenderATPLocalOnboardingScript.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 392 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 880 | C:\Windows\System32\sc.exe query "SENSE" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 884 | C:\Windows\System32\find.exe /i "RUNNING" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | C:\Windows\System32\sc.exe query "SENSE" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | C:\Windows\System32\timeout.exe 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1904 | C:\Windows\System32\reg.exe add "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v latency /t REG_SZ /f /d "Demo" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2240 | C:\Windows\System32\net.exe session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2292 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -ExecutionPolicy Bypass -NoProfile -Command "Add-Type ' using System; using System.IO; using System.Runtime.InteropServices; using Microsoft.Win32.SafeHandles; using System.ComponentModel; public static class Elam{ [DllImport(\"Kernel32\", CharSet=CharSet.Auto, SetLastError=true)] public static extern bool InstallELAMCertificateInfo(SafeFileHandle handle); public static void InstallWdBoot(string path) { Console.Out.WriteLine(\"About to call create file on {0}\", path); var stream = File.Open(path, FileMode.Open, FileAccess.Read, FileShare.Read); var handle = stream.SafeFileHandle; Console.Out.WriteLine(\"About to call InstallELAMCertificateInfo on handle {0}\", handle.DangerousGetHandle()); if (!InstallELAMCertificateInfo(handle)) { Console.Out.WriteLine(\"Call failed.\"); throw new Win32Exception(Marshal.GetLastWin32Error()); } Console.Out.WriteLine(\"Call successful.\"); } } '; $driverPath = $env:SystemRoot + '\System32\Drivers\WdBoot.sys'; [Elam]::InstallWdBoot($driverPath) " | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2320 | C:\Windows\System32\reg.exe add HKLM\SYSTEM\CurrentControlSet\Control\WMI\Security /v cb2ff72d-d4e4-585d-33f9-f3a395c40be7 /t REG_BINARY /d 0100048044000000540000000000000014000000020030000200000000001400FF0F120001010000000000051200000000001400E104120001010000000000050B0000000102000000000005200000002002000001020000000000052000000020020000 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 596
Read events
3 596
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
9
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\2jbtycco.unn.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gz03qznl\gz03qznl.0.cs | text | |
MD5:6FD55E9D12CD585CEFD6D0281E8B1702 | SHA256:A35C0F7E148CFDE26A37CCF1B4EA65107BC175B789AB9174A593EDA8ECE9A59F | |||
| 2292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gz03qznl\gz03qznl.cmdline | text | |
MD5:AA2865FE03F81D2F67C5EE12FDEFD0E7 | SHA256:D2D8CD7F2203CE52DA20E798B288C48EE9168F87BF0CC1836AF47B77F945816A | |||
| 2816 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES7868.tmp | binary | |
MD5:33FF5A8D38FF2A4D6C720487B99EE4AA | SHA256:EF1DCEFE6D5E5985B5ECB30EEE588D705FE16A80EBF91F1E795B52E8D5155955 | |||
| 3012 | powershell.exe | C:\Users\admin\AppData\Local\Temp\w4nl2gb3.cuc.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2884 | csc.exe | C:\Users\admin\AppData\Local\Temp\gz03qznl\gz03qznl.dll | executable | |
MD5:0145965860F59371C45C5635558B8186 | SHA256:3CED9E06C52B72D45A3D77EEB4D8DB03E96CDDD43BB68DE4A1AC89992F6340A2 | |||
| 3012 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ywjto02d\ywjto02d.cmdline | text | |
MD5:25DCA22A634DCE40F3BB2D237ED08749 | SHA256:63F481C8D588588C75899F5913357457B6C1D254D9B22E48AD48EA6EE36EE32E | |||
| 3236 | csc.exe | C:\Users\admin\AppData\Local\Temp\ywjto02d\CSCD1EE280ACE2E4CB5A29D83B76A9FE0BE.TMP | binary | |
MD5:4C5CA6FA62DB64B77A27FD1A87438B95 | SHA256:26E0FEE182658BFA2C5C5F0BBB54884B0AA26B959494789DA3D20ED52B66B664 | |||
| 2292 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 3236 | csc.exe | C:\Users\admin\AppData\Local\Temp\ywjto02d\ywjto02d.dll | executable | |
MD5:ABDF5AFB319DD051AEEB8C336F7DE08D | SHA256:3F2E100CDF1B98A749D8C0944F427513A141218CB325EDF13AE88D26182DA7A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |