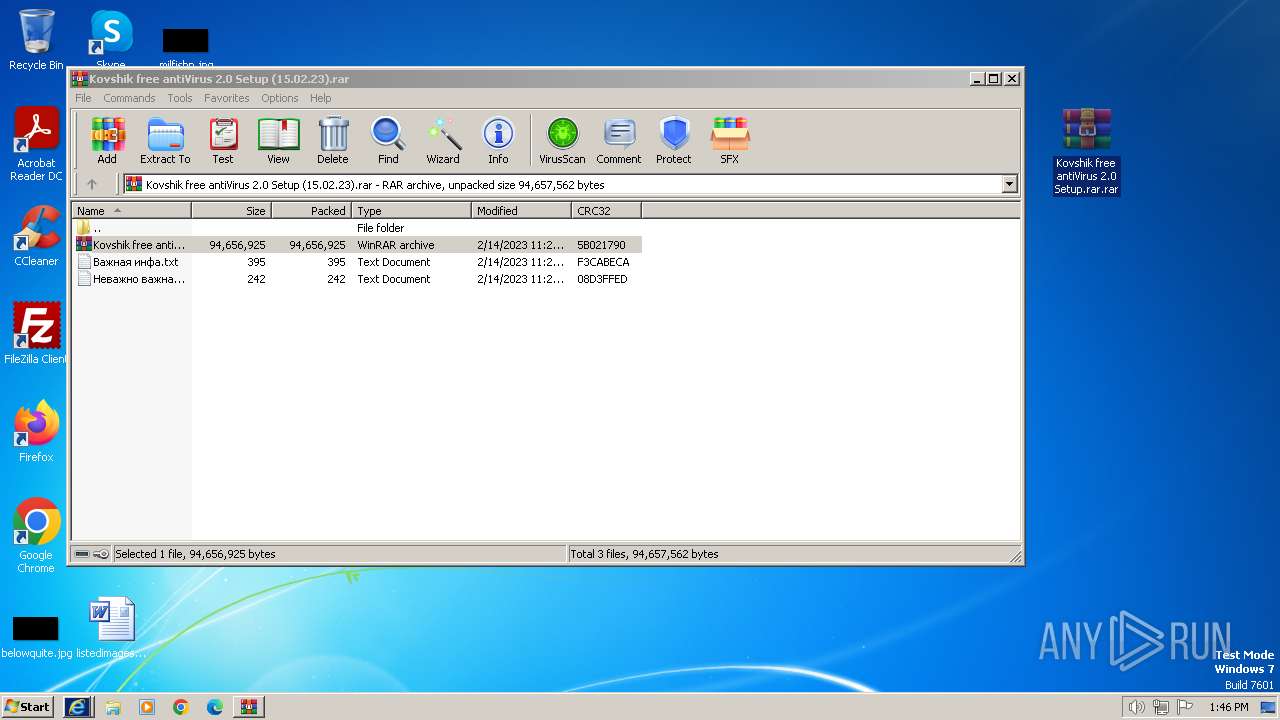
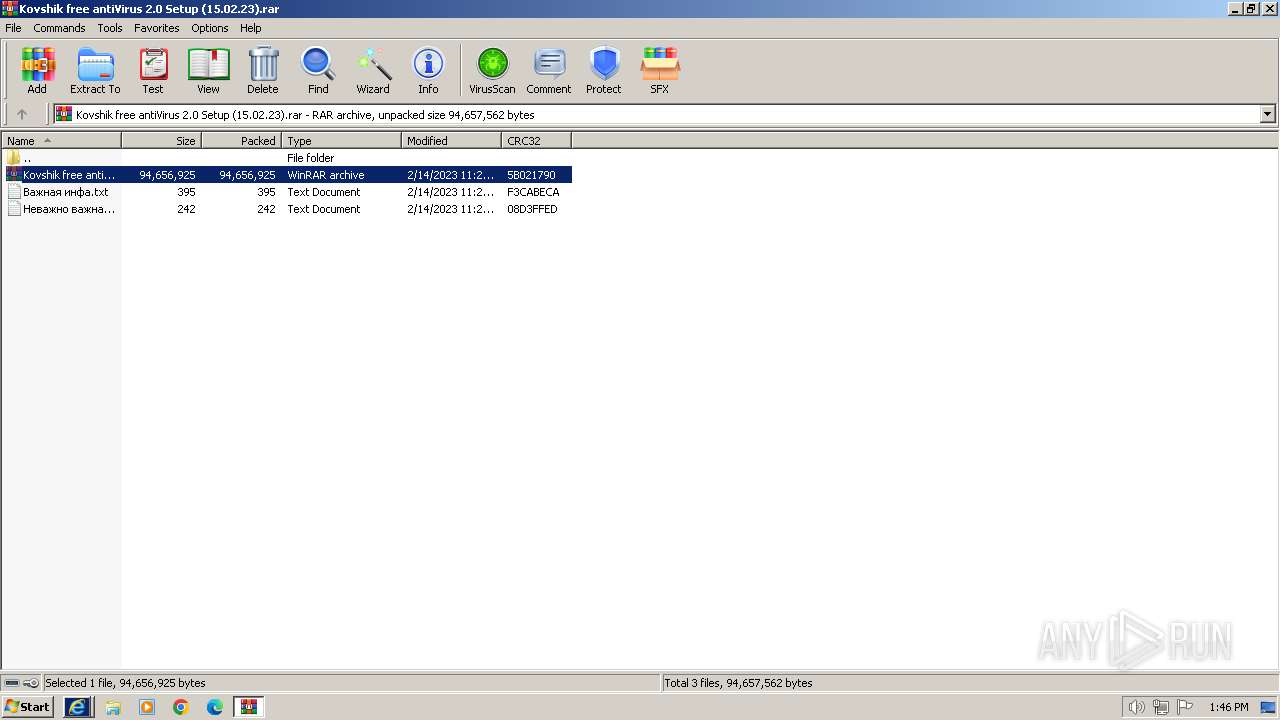
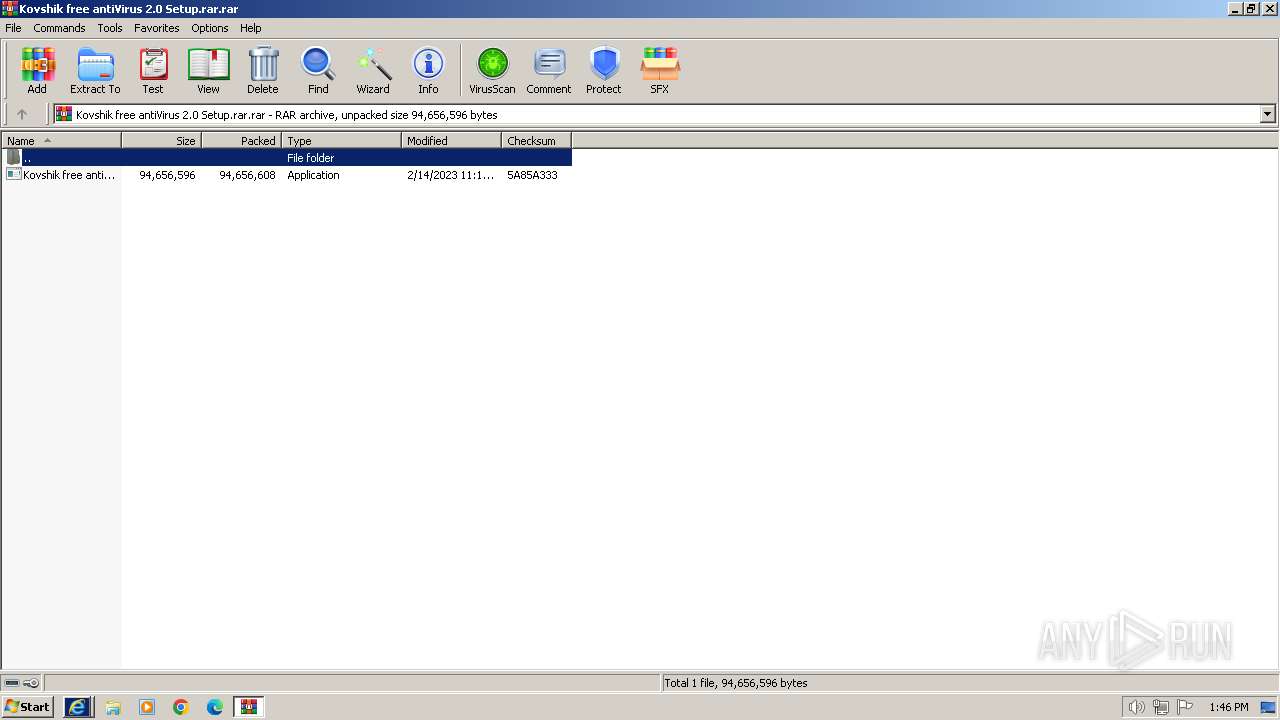
| URL: | https://docviewer.yandex.ru/view/0/?*=ankqa%2BS1jlRovhyvQJEegNW6Mkd7InVybCI6InlhLWRpc2stcHVibGljOi8vYSt1NEhUemkrRWk1eFkrSlVNQTJ1TGIySW0wQlNwNlltY3dDVUE3ME1oM25EWGZHMjFDM2NBLytHUnAxdVJPc3EvSjZicG1SeU9Kb25UM1ZvWG5EYWc9PTovS292c2hpayBmcmVlIGFudGlWaXJ1cyAyLjAgU2V0dXAgKDE1LjAyLjIzKS5yYXIiLCJ0aXRsZSI6IktvdnNoaWsgZnJlZSBhbnRpVmlydXMgMi4wIFNldHVwICgxNS4wMi4yMykucmFyIiwibm9pZnJhbWUiOmZhbHNlLCJ1aWQiOiIwIiwidHMiOjE3MDMzMzg5NjYzNzcsInl1IjoiOTE3OTIzNjI4MTcwMjk5ODU5OSJ9 |
| Full analysis: | https://app.any.run/tasks/02182c8f-3685-42af-805d-72aab2c2bcd9 |
| Verdict: | Malicious activity |
| Analysis date: | December 23, 2023, 13:44:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | FD749A0E66F738C91A5D22B3CF3922AD |
| SHA1: | BDF0EB23ED7BF615119066EB30B8F08AAD9030D5 |
| SHA256: | D9053BB5C91DFADB49CA12357BC906EDB3DD8670B71EA2C2EA036FC3C85ED238 |
| SSDEEP: | 12:2MQ4tJgAKqfu/Rl6MQwkqe8fHhQjsNTgJfyN9MZw:294tu2mnnlo8fBQ+Tg1yN9MZw |
MALICIOUS
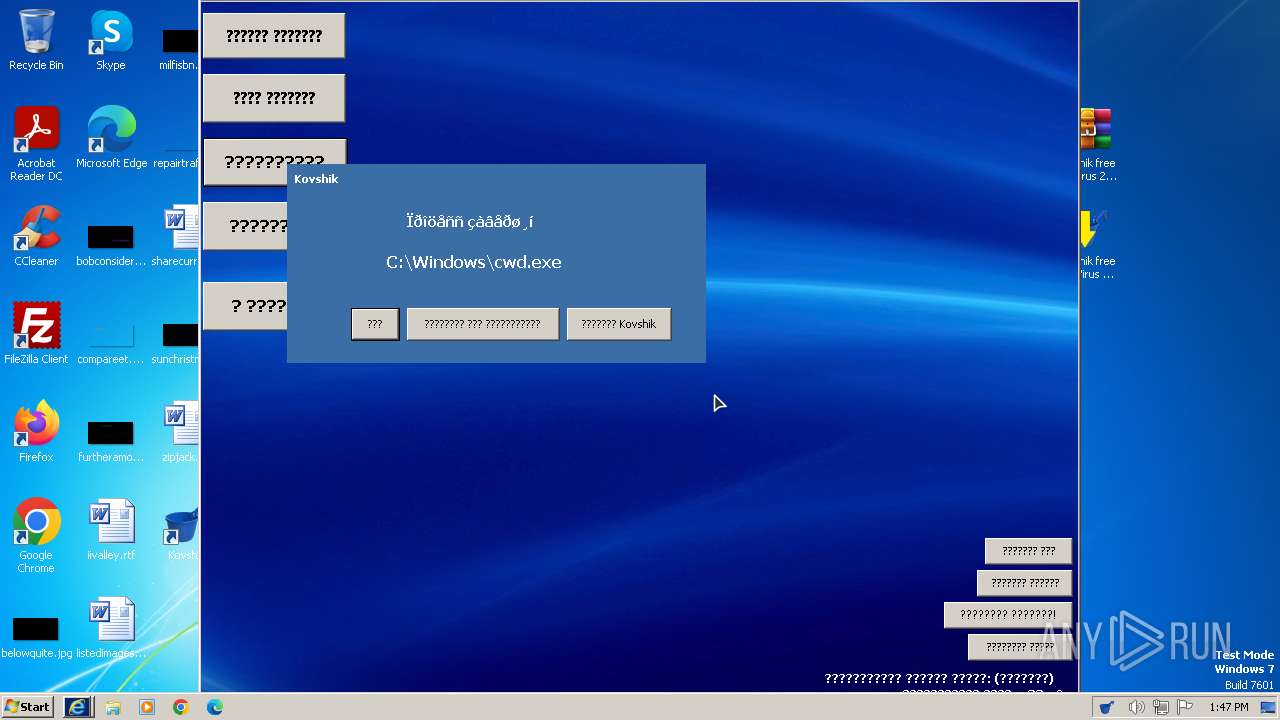
Changes the login/logoff helper path in the registry
- Kovshik_Service.exe (PID: 3116)
Task Manager has been disabled (taskmgr)
- Kovshik_Service.exe (PID: 3116)
UAC/LUA settings modification
- Kovshik_Service.exe (PID: 3116)
Disables the Run the Start menu
- Kovshik_Service.exe (PID: 3116)
Disables the Find the Start menu
- Kovshik_Service.exe (PID: 3116)
Modify registry editing tools (regedit)
- Kovshik_Service.exe (PID: 3116)
SUSPICIOUS
The process creates files with name similar to system file names
- Kovshik free antiVirus 2.0 Setup.exe (PID: 2908)
Reads the Internet Settings
- Kovshik free antiVirus 2.0 Setup.exe (PID: 2908)
- Kovshik_Warning.exe (PID: 1992)
- Kovshik_Tray.exe (PID: 2364)
- Kovshik.exe (PID: 2380)
- Kovshik_Service.exe (PID: 3116)
INFO
Application launched itself
- iexplore.exe (PID: 116)
The process uses the downloaded file
- iexplore.exe (PID: 116)
- WinRAR.exe (PID: 188)
Checks supported languages
- Kovshik free antiVirus 2.0 Setup.exe (PID: 2908)
- Kovshik_Warning.exe (PID: 1992)
- Kovshik_nax.exe (PID: 2512)
- wpnn.exe (PID: 1220)
- K_lnk.exe (PID: 3060)
- Kovshik_Control.exe (PID: 968)
- Kovshik_Service.exe (PID: 3116)
- Kovshik.exe (PID: 2380)
- Kovshik_Tray.exe (PID: 2364)
- Kovshik_dbl.exe (PID: 3196)
- Kov1.exe (PID: 3296)
Reads the computer name
- Kovshik free antiVirus 2.0 Setup.exe (PID: 2908)
- Kovshik_Warning.exe (PID: 1992)
- wpnn.exe (PID: 1220)
- K_lnk.exe (PID: 3060)
- Kovshik_Tray.exe (PID: 2364)
- Kovshik_Service.exe (PID: 3116)
- Kovshik.exe (PID: 2380)
- Kovshik_Control.exe (PID: 968)
- Kov1.exe (PID: 3296)
Manual execution by a user
- WinRAR.exe (PID: 1528)
- Kovshik free antiVirus 2.0 Setup.exe (PID: 2908)
Process drops legitimate windows executable
- Kovshik free antiVirus 2.0 Setup.exe (PID: 2908)
- wpnn.exe (PID: 1220)
Drops the executable file immediately after the start
- Kovshik free antiVirus 2.0 Setup.exe (PID: 2908)
- K_lnk.exe (PID: 3060)
- wpnn.exe (PID: 1220)
The process drops C-runtime libraries
- Kovshik free antiVirus 2.0 Setup.exe (PID: 2908)
- wpnn.exe (PID: 1220)
Reads the machine GUID from the registry
- Kovshik_Warning.exe (PID: 1992)
- Kovshik_Control.exe (PID: 968)
- Kovshik.exe (PID: 2380)
- Kovshik_Service.exe (PID: 3116)
- Kov1.exe (PID: 3296)
Process checks are UAC notifies on
- Kovshik_Service.exe (PID: 3116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
57
Monitored processes
15
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://docviewer.yandex.ru/view/0/?*=ankqa%2BS1jlRovhyvQJEegNW6Mkd7InVybCI6InlhLWRpc2stcHVibGljOi8vYSt1NEhUemkrRWk1eFkrSlVNQTJ1TGIySW0wQlNwNlltY3dDVUE3ME1oM25EWGZHMjFDM2NBLytHUnAxdVJPc3EvSjZicG1SeU9Kb25UM1ZvWG5EYWc9PTovS292c2hpayBmcmVlIGFudGlWaXJ1cyAyLjAgU2V0dXAgKDE1LjAyLjIzKS5yYXIiLCJ0aXRsZSI6IktvdnNoaWsgZnJlZSBhbnRpVmlydXMgMi4wIFNldHVwICgxNS4wMi4yMykucmFyIiwibm9pZnJhbWUiOmZhbHNlLCJ1aWQiOiIwIiwidHMiOjE3MDMzMzg5NjYzNzcsInl1IjoiOTE3OTIzNjI4MTcwMjk5ODU5OSJ9" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 188 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\Kovshik free antiVirus 2.0 Setup (15.02.23).rar" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 968 | "C:\VirusNew17\Kovshik\Kovshik_Control.exe" | C:\VirusNew17\Kovshik\Kovshik_Control.exe | — | Kovshik_Tray.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Kovshik_Control Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1220 | "C:\VirusNew17\Kovshik\wpnn.exe" | C:\VirusNew17\Kovshik\wpnn.exe | — | Kovshik_Warning.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1528 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Kovshik free antiVirus 2.0 Setup.rar.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1992 | "C:\VirusNew17\Kovshik\Kovshik_Warning.exe" | C:\VirusNew17\Kovshik\Kovshik_Warning.exe | — | Kovshik free antiVirus 2.0 Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Kovshik_Warning Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2032 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:116 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2364 | "C:\VirusNew17\Kovshik\Kovshik_Tray.exe" | C:\VirusNew17\Kovshik\Kovshik_Tray.exe | — | Kovshik_Warning.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2380 | "C:\VirusNew17\Kovshik\Kovshik.exe" | C:\VirusNew17\Kovshik\Kovshik.exe | — | Kovshik_Warning.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2512 | "C:\VirusNew17\Kovshik\Kovshik_nax.exe" | C:\VirusNew17\Kovshik\Kovshik_nax.exe | — | Kovshik_Warning.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
39 538
Read events
30 370
Write events
9 164
Delete events
4
Modification events
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
34
Suspicious files
170
Text files
173
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_50D7940D5D3FEDD8634D83074C7A46A3 | binary | |
MD5:61FD814E6143F9F04C707BF86AD408B7 | SHA256:D52354FD9D24913F23AD0F5473484E5BC949744FE17FCE0E8A4A66B872B00D0A | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\ZMJ1NFZA.txt | text | |
MD5:8F5A7E0D3083996F52C7943C30C402E6 | SHA256:46545B507899CDB184BA4E79A598383BDE9E4AC9E6DF90BC9830E22AB17F39ED | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\349D186F1CB5682FA0194D4F3754EF36_24189A5ADBE6F590307BAA21110D145D | binary | |
MD5:DDFCD5D0F972443E5997D49FFB8A2174 | SHA256:86799B93D5F5BAD5FE19B51F34141085610723EC142A1D5D9FB68B5D2995E70C | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\349D186F1CB5682FA0194D4F3754EF36_24189A5ADBE6F590307BAA21110D145D | binary | |
MD5:61BE92D6955364057316BEA23692BCEA | SHA256:5D462B73AA4F40E33B3E9C07484A22128B7F3DA1086532E773BC96C8101331E2 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_4136D3715888E22D65EBE484B233D81B | binary | |
MD5:D097BD67348A18AA6711BBB1E63A287F | SHA256:3E3FA18AA5C705C0E22FA663AEF7880D08ADCE950F95BD854EBB09061944852A | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\DNBG1FNU.txt | text | |
MD5:63862158A8426128E8FB8C69A902EF3B | SHA256:8977D994936202200D18C4DA839ACE15AFD6D97E680CB6E00DD0A18322346EE2 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\0[1].htm | html | |
MD5:4C80A87AB44D61F574115A7A1B94107D | SHA256:AE38441105463042924CC540D06F134C077D42A234AB775E6892CFF40B05E325 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0DA515F703BB9B49479E8697ADB0B955_4136D3715888E22D65EBE484B233D81B | binary | |
MD5:FFA15F21207BF37322C5BE943CD32D61 | SHA256:9A19354DBBFF2D4AA63617ED43588702E863CFA2AC123E971A2F73A18162E4A3 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_50D7940D5D3FEDD8634D83074C7A46A3 | binary | |
MD5:579D551921C3C22C351FD5AC1B508C7A | SHA256:3DF0AACA65160011DE35F00054A08812690CF7D6991FD59127AD85B57D773E4F | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\2C09EEZD.txt | text | |
MD5:E8DF3E1B4A60F8F9FCC24AE6C55ECC5F | SHA256:523B7A6228A1BA2114BC94268347A2F166285B7C0ADDEDDC77E5AA520AC1038D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
36
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2032 | iexplore.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDHlA8lvCmU48FTvWpw%3D%3D | unknown | binary | 1.40 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53bfb7cf8a6cf97e | unknown | compressed | 4.66 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6b21170b0e7a1648 | unknown | compressed | 4.66 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | unknown | binary | 1.41 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 151.101.2.133:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | unknown | binary | 1.40 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDCcZrQuON5%2BRFGXczQ%3D%3D | unknown | binary | 1.40 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/rootr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHUeP1PjGFkz6V8I7O6tApc%3D | unknown | binary | 1.41 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 151.101.2.133:80 | http://ocsp2.globalsign.com/rootr5/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQiD0S5cIHyfrLTJ1fvAkJWflH%2B2QQUPeYpSJvqB8ohREom3m7e0oPQn1kCDQHuXyKVQkkF%2BQGRqNw%3D | unknown | binary | 1.25 Kb | unknown |
116 | iexplore.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?56a48ccbaf965781 | unknown | — | — | unknown |
2032 | iexplore.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/gseccovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSTMjK03nNiYoQYvu4Izyfn9OJNdAQUWHuOdSr%2BYYCqkEABrtboB0ZuP0gCDGR9zAVCqD3GmxxJUg%3D%3D | unknown | binary | 938 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2032 | iexplore.exe | 77.88.21.148:443 | docviewer.yandex.ru | YANDEX LLC | RU | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2032 | iexplore.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2032 | iexplore.exe | 151.101.2.133:80 | ocsp.globalsign.com | FASTLY | US | unknown |
2032 | iexplore.exe | 93.158.134.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
2032 | iexplore.exe | 77.88.21.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
116 | iexplore.exe | 77.88.21.148:443 | docviewer.yandex.ru | YANDEX LLC | RU | unknown |
116 | iexplore.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
docviewer.yandex.ru |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
mc.yandex.ru |
| whitelisted |
mc.yandex.com |
| whitelisted |
yastatic.net |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |