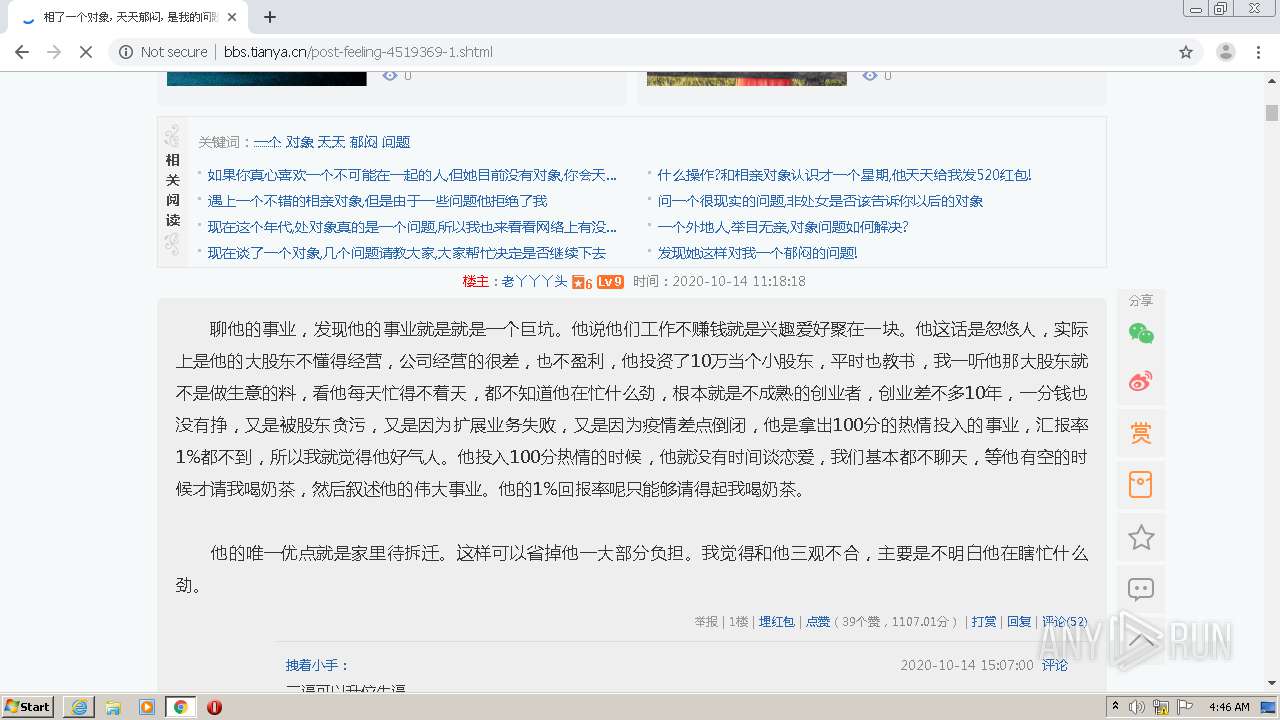
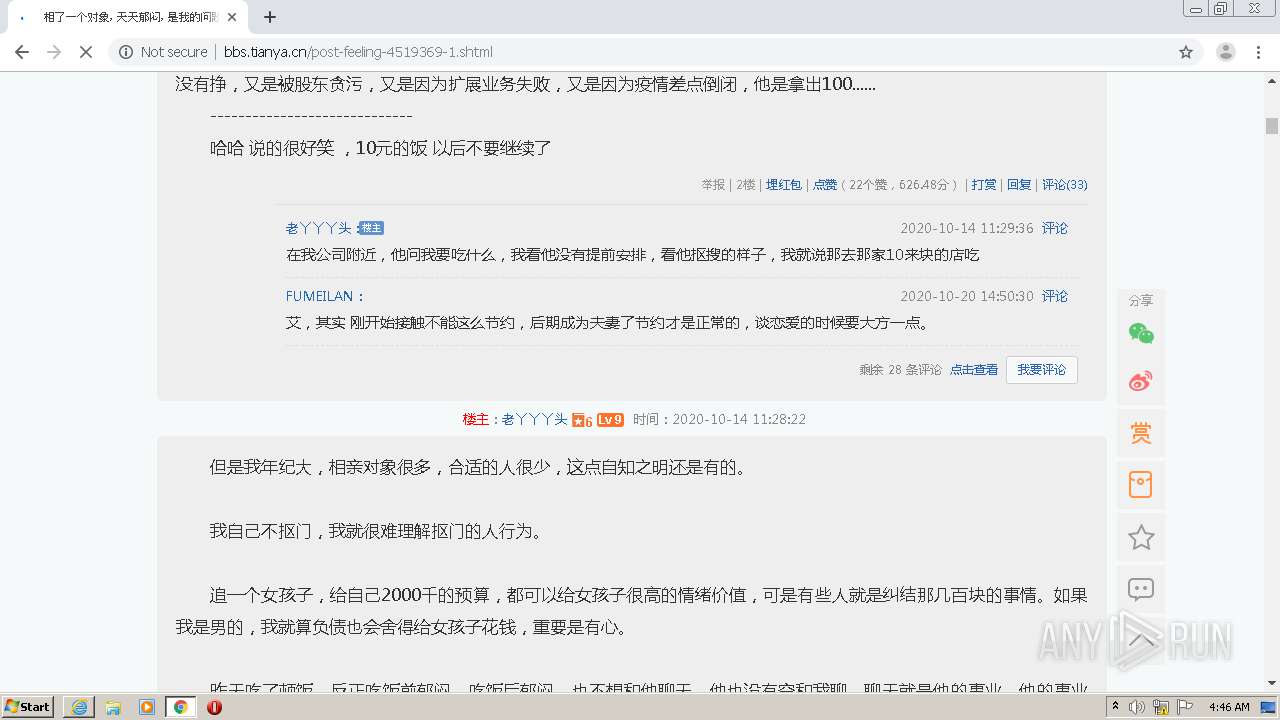
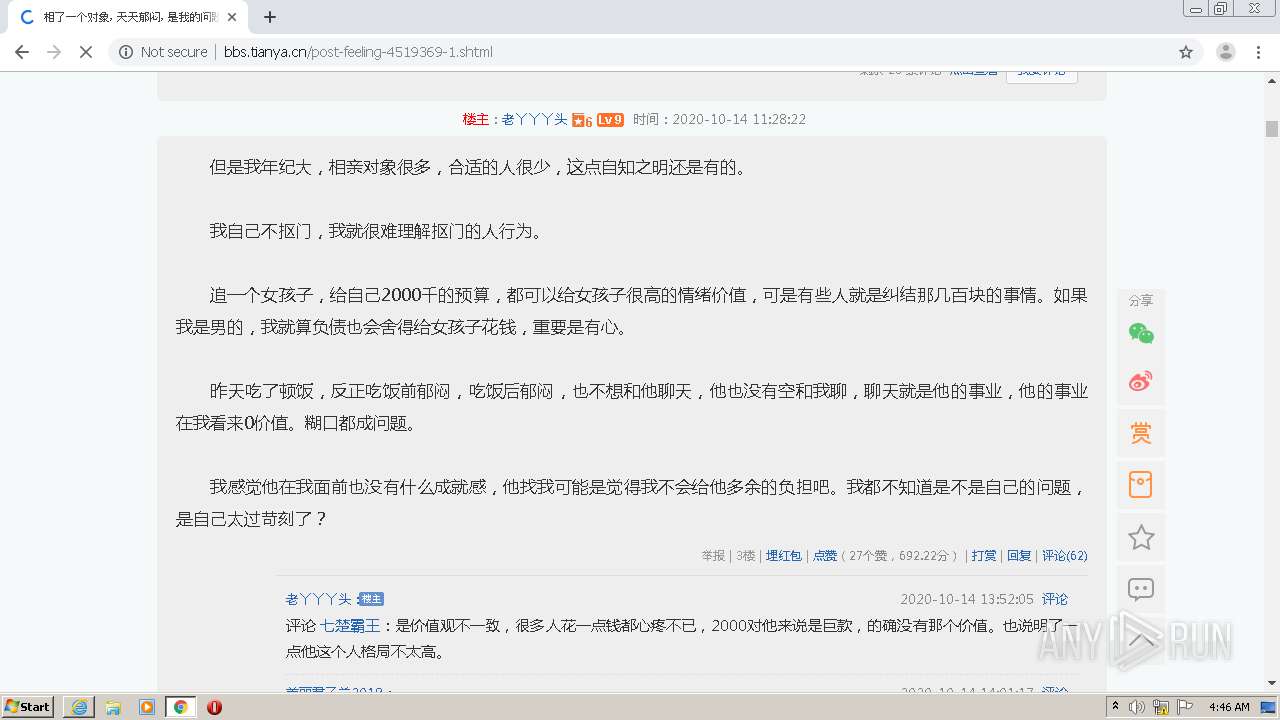
| URL: | http://bbs.tianya.cn/post-feeling-4519369-1.shtml |
| Full analysis: | https://app.any.run/tasks/44222925-d3aa-4529-ba2f-ad5d3e425309 |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2021, 03:44:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4BDD52CEDD551BAE155373E9BD70D7E6 |
| SHA1: | 62B2EB2FFD0469B7C2004E32EB742AA54045FDD3 |
| SHA256: | D90262665B086053A5B5DF8B46DD04CC9CEDBEED165FB8087643BB665E2EDFAD |
| SSDEEP: | 3:N1KcshnVK7A5CIRKMG:CcaVK2KMG |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2700)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1956)
INFO
Application launched itself
- iexplore.exe (PID: 3984)
- chrome.exe (PID: 1956)
Changes internet zones settings
- iexplore.exe (PID: 3984)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3984)
Reads internet explorer settings
- iexplore.exe (PID: 3116)
Creates files in the user directory
- iexplore.exe (PID: 3116)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2700)
- iexplore.exe (PID: 3984)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3116)
- chrome.exe (PID: 692)
- chrome.exe (PID: 1956)
Reads settings of System Certificates
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 3116)
Manual execution by user
- chrome.exe (PID: 1956)
Reads the hosts file
- chrome.exe (PID: 1956)
- chrome.exe (PID: 692)
Changes settings of System certificates
- iexplore.exe (PID: 3984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
72
Monitored processes
38
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,5785773075059191382,4103873915832229870,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=17729727063124088674 --mojo-platform-channel-handle=3660 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,5785773075059191382,4103873915832229870,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11598904950758429334 --mojo-platform-channel-handle=1328 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,5785773075059191382,4103873915832229870,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5409928936674680223 --mojo-platform-channel-handle=2824 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 648 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,5785773075059191382,4103873915832229870,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18185255340954129208 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2464 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 692 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,5785773075059191382,4103873915832229870,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=3497088442685228247 --mojo-platform-channel-handle=1648 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,5785773075059191382,4103873915832229870,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7971606026654126841 --mojo-platform-channel-handle=4152 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,5785773075059191382,4103873915832229870,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6756517902535973662 --mojo-platform-channel-handle=2560 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,5785773075059191382,4103873915832229870,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=307149868612161920 --mojo-platform-channel-handle=4112 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2176 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,5785773075059191382,4103873915832229870,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8803590831766156744 --mojo-platform-channel-handle=4484 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 243
Read events
1 982
Write events
254
Delete events
7
Modification events
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 42464012 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30890228 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
181
Text files
392
Unknown types
58
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3116 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab91DB.tmp | — | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar91DC.tmp | — | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\TY[1].css | text | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\V1VKEH5X.txt | text | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\TY[1].js | text | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\GN6EZBC1.txt | — | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\bbs_article_02a112c[1].css | text | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\bbs_info_ab40358[1].js | html | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\post-feeling-4519369-1[1].htm | html | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\main_a1cbdc9[1].js | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
184
TCP/UDP connections
325
DNS requests
131
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3116 | iexplore.exe | GET | — | 124.225.206.22:80 | http://static.tianyaui.com/global/ty/TY.css | CN | — | — | suspicious |
3116 | iexplore.exe | GET | — | 124.225.206.22:80 | http://static.tianyaui.com/global/bbs/web/static/images/bbs_tyf_fe9c678.png | CN | — | — | suspicious |
3116 | iexplore.exe | GET | 200 | 124.225.206.22:80 | http://static.tianyaui.com/global/ty/TY.js | CN | text | 60.4 Kb | suspicious |
3116 | iexplore.exe | GET | 200 | 124.225.159.113:80 | http://bbs.tianya.cn/post-feeling-4519369-1.shtml | CN | html | 877 Kb | unknown |
3116 | iexplore.exe | GET | 200 | 124.225.206.22:80 | http://static.tianyaui.com/global/bbs/web/static/js/main_a1cbdc9.js | CN | html | 25.6 Kb | suspicious |
3116 | iexplore.exe | GET | 200 | 124.225.206.22:80 | http://static.tianyaui.com/global/bbs/web/static/css/bbs_article_02a112c.css | CN | text | 31.3 Kb | suspicious |
3116 | iexplore.exe | GET | 200 | 23.51.123.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.52 Kb | shared |
3116 | iexplore.exe | GET | 200 | 124.225.206.22:80 | http://static.tianyaui.com/global/bbs/web/static/images/bg_5_4eaca6e.png | CN | image | 222 b | suspicious |
3116 | iexplore.exe | GET | 200 | 124.225.206.22:80 | http://static.tianyaui.com/global/bbs/web/static/js/bbs_info_ab40358.js | CN | html | 45.5 Kb | suspicious |
3116 | iexplore.exe | GET | 200 | 124.225.206.22:80 | http://static.tianyaui.com/img/static/2011/imgloading.gif | CN | image | 2.39 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3116 | iexplore.exe | 124.225.159.113:80 | bbs.tianya.cn | No.31,Jin-rong Street | CN | unknown |
3116 | iexplore.exe | 124.225.206.22:80 | static.tianyaui.com | No.31,Jin-rong Street | CN | suspicious |
3984 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3116 | iexplore.exe | 124.225.206.22:443 | static.tianyaui.com | No.31,Jin-rong Street | CN | suspicious |
3116 | iexplore.exe | 13.225.87.103:443 | d31qbv1cthcecs.cloudfront.net | — | US | unknown |
3116 | iexplore.exe | 34.218.88.199:80 | redirect.prod.experiment.routing.cloudfront.aws.a2z.com | Amazon.com, Inc. | US | unknown |
3116 | iexplore.exe | 23.45.105.185:80 | x1.c.lencr.org | Akamai International B.V. | NL | unknown |
3116 | iexplore.exe | 143.204.98.84:443 | certify.alexametrics.com | — | US | suspicious |
3116 | iexplore.exe | 88.221.223.59:80 | r3.o.lencr.org | Akamai International B.V. | — | suspicious |
3116 | iexplore.exe | 13.32.23.69:80 | ocsp.rootg2.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bbs.tianya.cn |
| unknown |
static.tianyaui.com |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
d31qbv1cthcecs.cloudfront.net |
| shared |
cms.tianyaui.com |
| unknown |
s.symcd.com |
| shared |
ocsp.digicert.com |
| whitelisted |
crl.identrust.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3116 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
3116 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
3116 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |