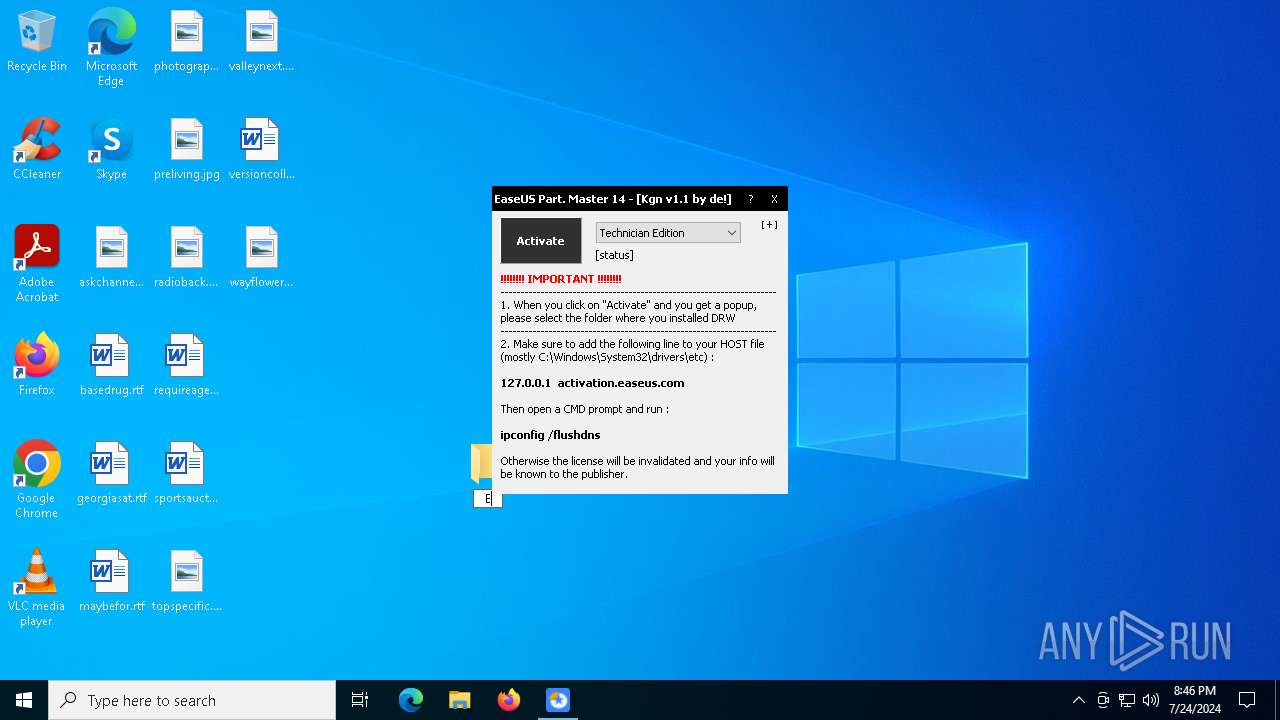
| File name: | EaseUS PM v14.x Activator v1.1.exe |
| Full analysis: | https://app.any.run/tasks/e7fb97db-abd0-4a4b-8dd4-5b5385e3a086 |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 20:45:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9BDFF46961AEF386D4DE5E2B1405DC40 |
| SHA1: | C6EF1ED87C331A8BD1CD1ADAF5AA5D124D677BC3 |
| SHA256: | D8E43DFB7662E0EEB26821F5A6A8D9F8A5B351D1D1E769A516ED65B86144E605 |
| SSDEEP: | 24576:llwhPNBDi2j1/m9+8N5n+Rj4YM7D4OnvHIHeev9Gvxa6uG2g1uv:laNE2Jdm57YMI6voHhKR/71uv |
MALICIOUS
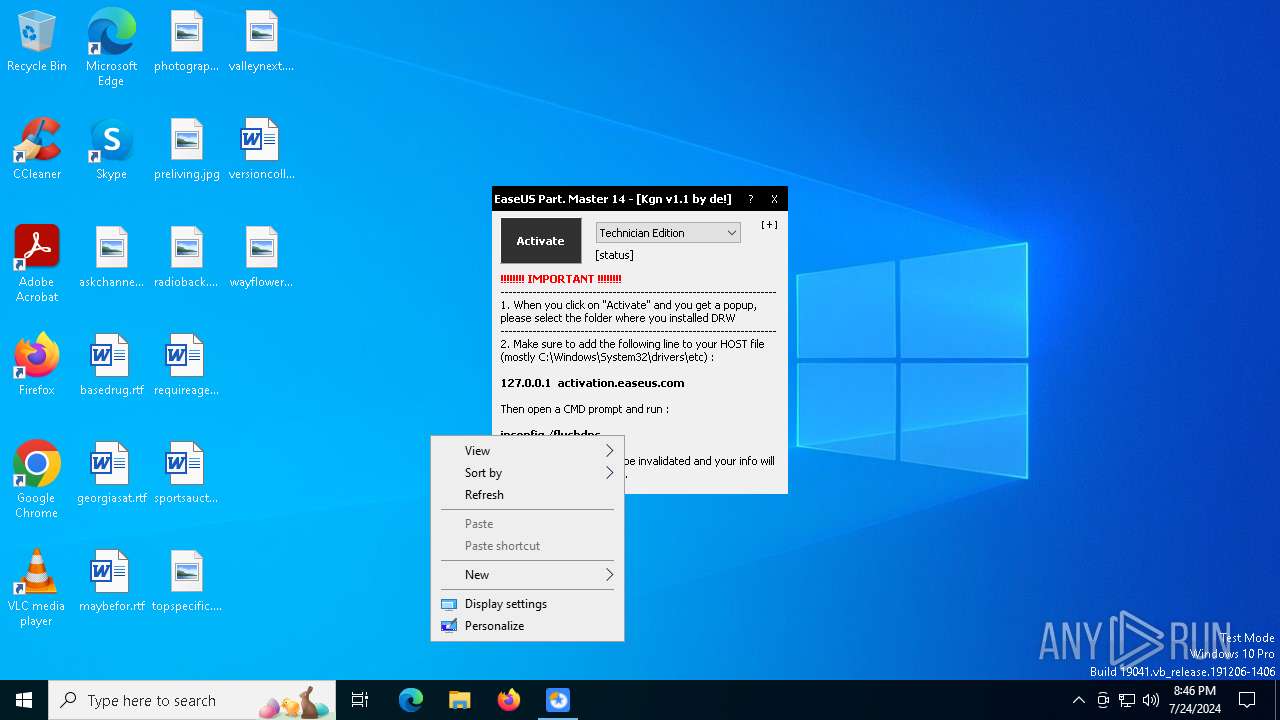
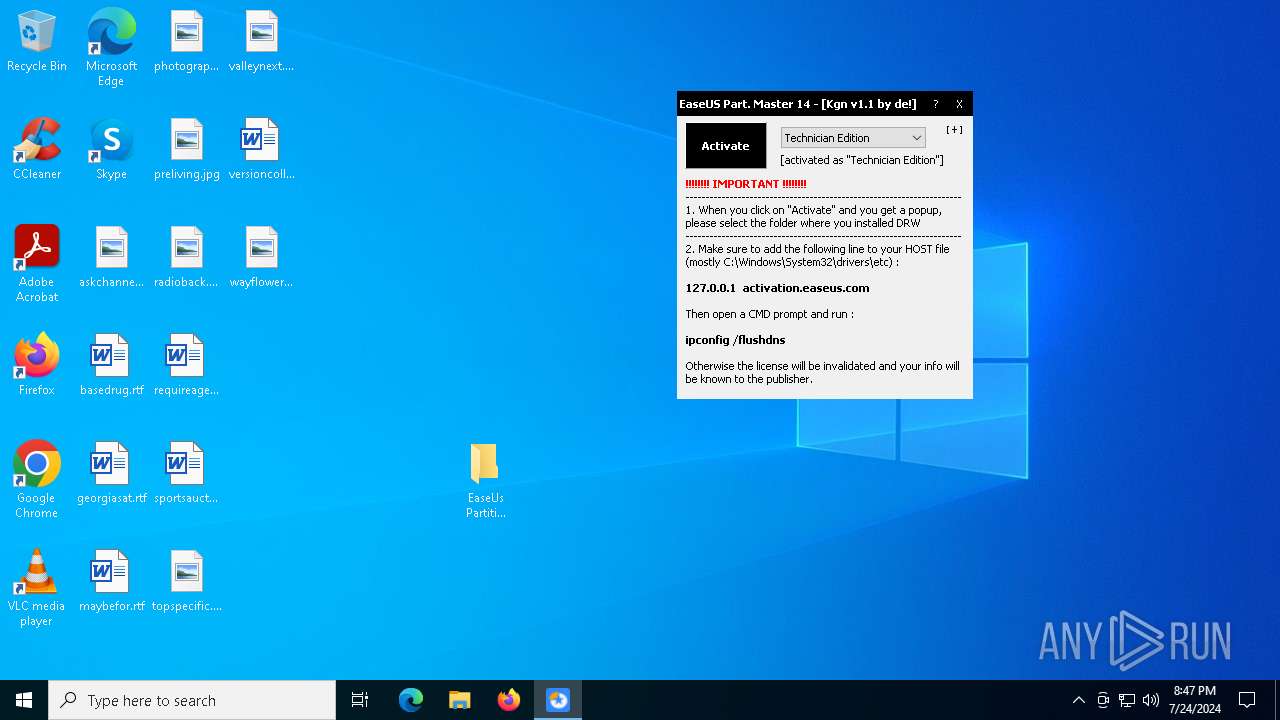
Drops the executable file immediately after the start
- EaseUS PM v14.x Activator v1.1.exe (PID: 3336)
SUSPICIOUS
Searches for installed software
- EaseUS PM v14.x Activator v1.1.exe (PID: 3336)
Reads security settings of Internet Explorer
- EaseUS PM v14.x Activator v1.1.exe (PID: 3336)
INFO
Reads the computer name
- TextInputHost.exe (PID: 1320)
- EaseUS PM v14.x Activator v1.1.exe (PID: 3336)
Checks supported languages
- TextInputHost.exe (PID: 1320)
- EaseUS PM v14.x Activator v1.1.exe (PID: 3336)
Creates files in the program directory
- EaseUS PM v14.x Activator v1.1.exe (PID: 3336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | DOS Executable Generic (100) |
|---|
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:04:28 05:11:45+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 2311168 |
| InitializedDataSize: | 1031168 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3fd000 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 2.0.0.0 |
| ProductVersion: | 1.0.0.0 |
| ProgramID: | com.embarcadero.EaseUS_EPM |
| FileDescription: | EaseUS_EPM |
| ProductName: | EaseUS_EPM |
Total processes
138
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1320 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 3336 | "C:\Users\admin\AppData\Local\Temp\EaseUS PM v14.x Activator v1.1.exe" | C:\Users\admin\AppData\Local\Temp\EaseUS PM v14.x Activator v1.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: EaseUS_EPM Version: 2.0.0.0 Modules
| |||||||||||||||
| 5648 | "C:\Users\admin\AppData\Local\Temp\EaseUS PM v14.x Activator v1.1.exe" | C:\Users\admin\AppData\Local\Temp\EaseUS PM v14.x Activator v1.1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: EaseUS_EPM Exit code: 3221226540 Version: 2.0.0.0 Modules
| |||||||||||||||
| 6680 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 069
Read events
10 869
Write events
191
Delete events
9
Modification events
| (PID) Process: | (3336) EaseUS PM v14.x Activator v1.1.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3336) EaseUS PM v14.x Activator v1.1.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000F0000000E00000003000000000000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (3336) EaseUS PM v14.x Activator v1.1.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (3336) EaseUS PM v14.x Activator v1.1.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (3336) EaseUS PM v14.x Activator v1.1.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files (x86)\Common Files\system\wab32res.dll,-10100 |
Value: Contacts | |||
| (PID) Process: | (3336) EaseUS PM v14.x Activator v1.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3336) EaseUS PM v14.x Activator v1.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3336) EaseUS PM v14.x Activator v1.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3336) EaseUS PM v14.x Activator v1.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3336) EaseUS PM v14.x Activator v1.1.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000400000000000000050000000200000003000000FFFFFFFF | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
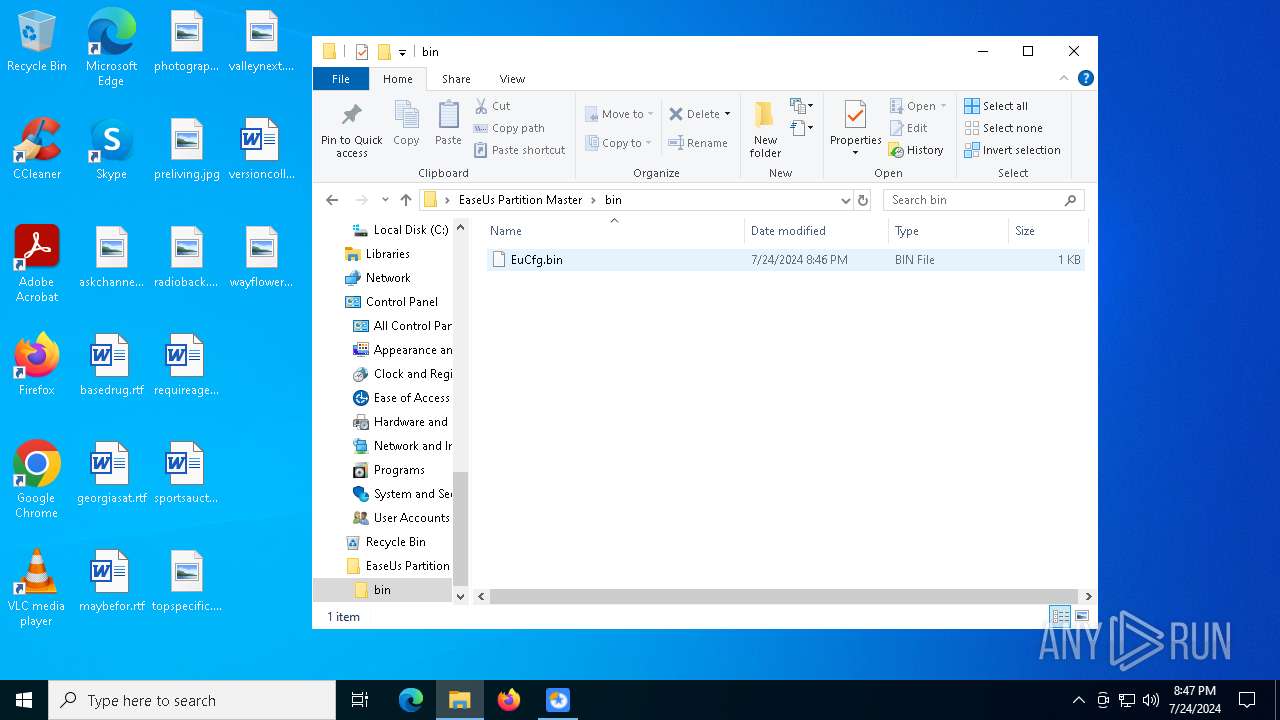
| 3336 | EaseUS PM v14.x Activator v1.1.exe | C:\Users\admin\Desktop\EaseUs Partition Master\bin\EuCfg.bin | binary | |
MD5:91B545B784B3EE34223EEA948F318FD9 | SHA256:6485B587610EC61D14CA0E976E0FD1FCB1CC4EC6322F9E0CA1A7EDEDF65E3269 | |||
| 3336 | EaseUS PM v14.x Activator v1.1.exe | C:\ProgramData\SystemAcCrux\1a530a830cb61980ac.bin | binary | |
MD5:344BEEEA3310AD0FED695538D7BA3A06 | SHA256:00F8920A956E81F1A5BB24E4FBEDA45EF50CC7703E583F5EE63828ABF1A33719 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
47
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6512 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6628 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6012 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4008 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3392 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 104.126.37.160:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4204 | svchost.exe | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5836 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |