| File name: | EPM v14 Activator v1.1 - De!.exe |
| Full analysis: | https://app.any.run/tasks/02f53eb8-c6b1-416c-bd09-68be3bbbf35b |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2024, 17:09:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9BDFF46961AEF386D4DE5E2B1405DC40 |
| SHA1: | C6EF1ED87C331A8BD1CD1ADAF5AA5D124D677BC3 |
| SHA256: | D8E43DFB7662E0EEB26821F5A6A8D9F8A5B351D1D1E769A516ED65B86144E605 |
| SSDEEP: | 24576:llwhPNBDi2j1/m9+8N5n+Rj4YM7D4OnvHIHeev9Gvxa6uG2g1uv:laNE2Jdm57YMI6voHhKR/71uv |
MALICIOUS
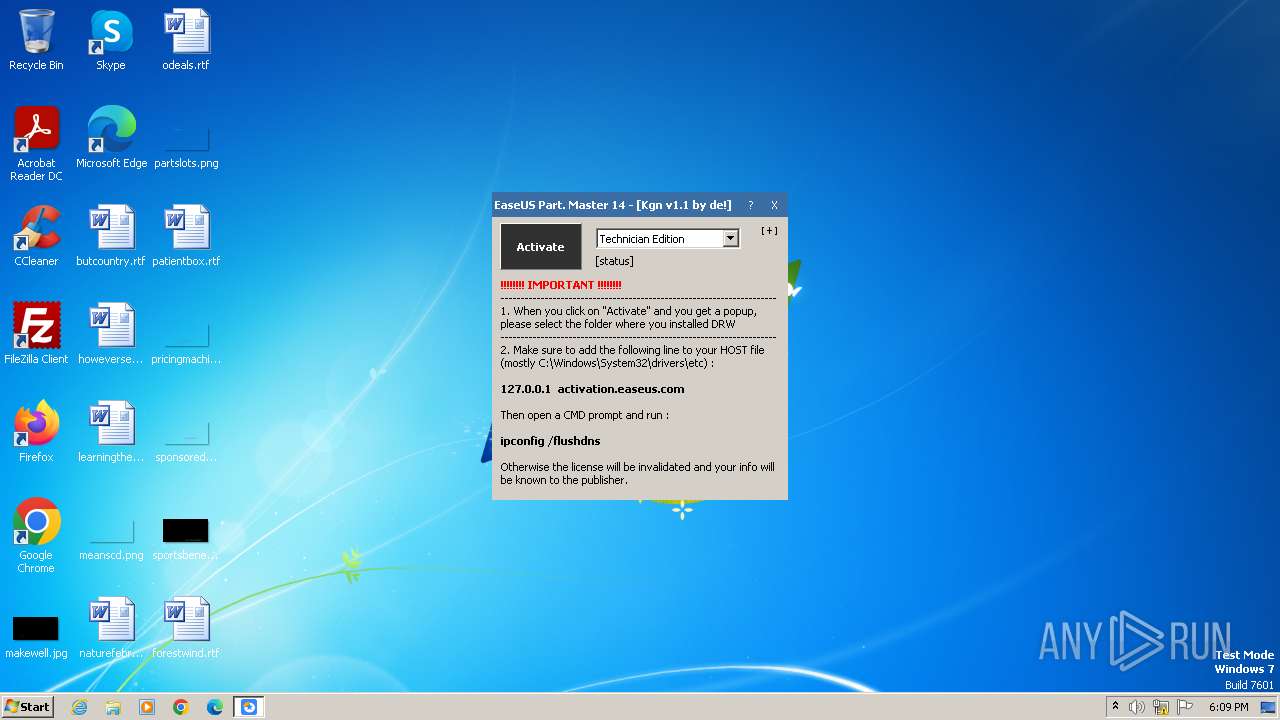
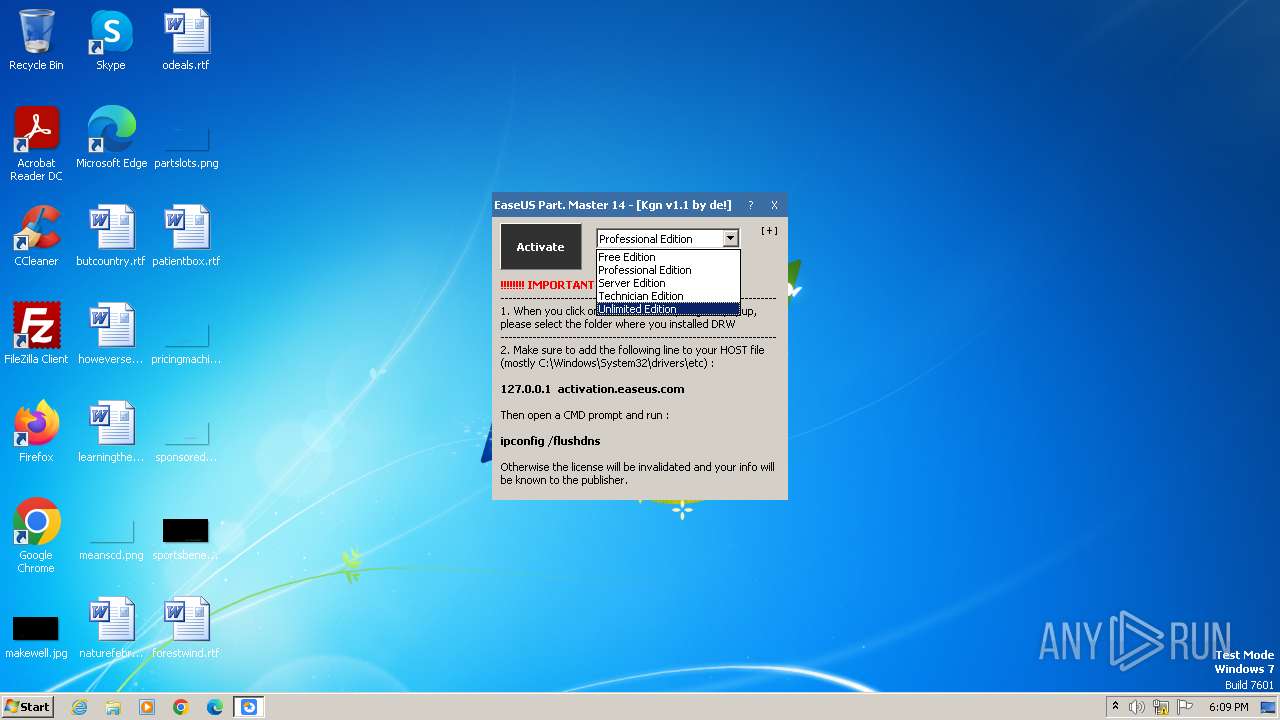
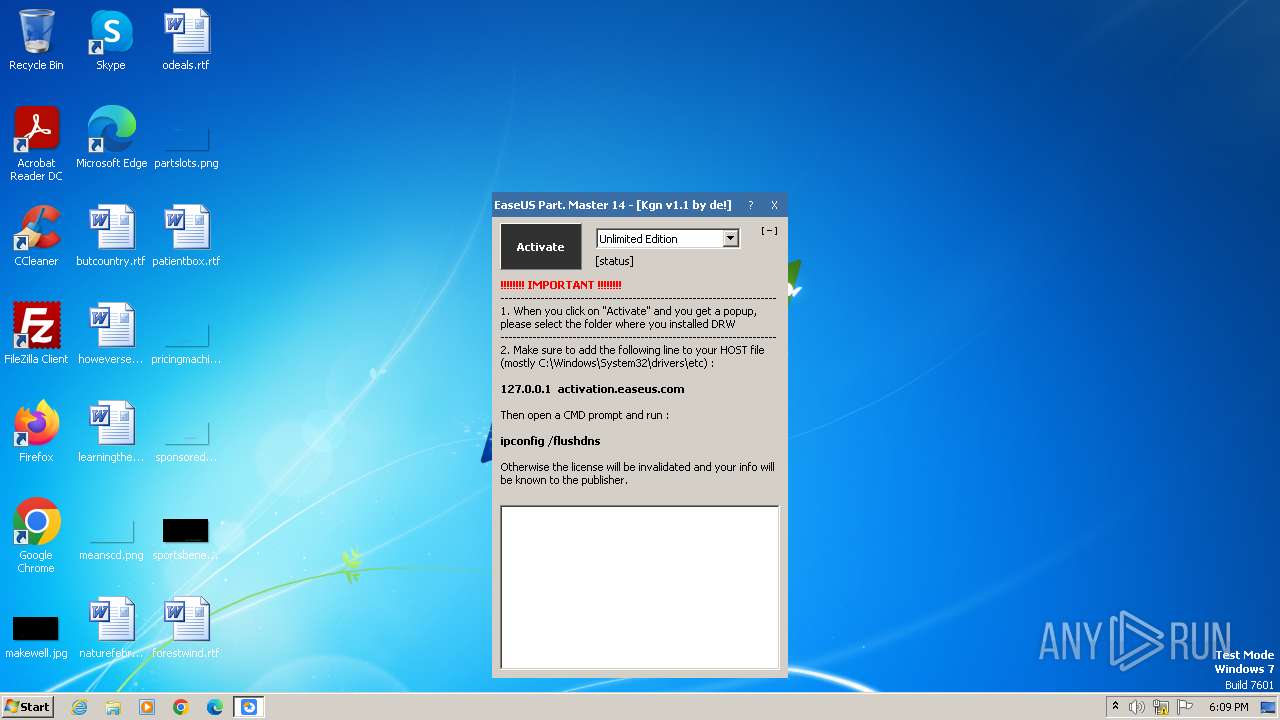
Drops the executable file immediately after the start
- EPM v14 Activator v1.1 - De!.exe (PID: 4076)
SUSPICIOUS
Searches for installed software
- EPM v14 Activator v1.1 - De!.exe (PID: 4076)
INFO
Checks supported languages
- EPM v14 Activator v1.1 - De!.exe (PID: 4076)
Reads the computer name
- EPM v14 Activator v1.1 - De!.exe (PID: 4076)
Reads the machine GUID from the registry
- EPM v14 Activator v1.1 - De!.exe (PID: 4076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | DOS Executable Generic (100) |
|---|
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:04:28 05:11:45+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 2311168 |
| InitializedDataSize: | 1031168 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3fd000 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 2.0.0.0 |
| ProductVersion: | 1.0.0.0 |
| ProgramID: | com.embarcadero.EaseUS_EPM |
| FileDescription: | EaseUS_EPM |
| ProductName: | EaseUS_EPM |
Total processes
36
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3972 | "C:\Users\admin\AppData\Local\Temp\EPM v14 Activator v1.1 - De!.exe" | C:\Users\admin\AppData\Local\Temp\EPM v14 Activator v1.1 - De!.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: EaseUS_EPM Exit code: 3221226540 Version: 2.0.0.0 Modules
| |||||||||||||||
| 4076 | "C:\Users\admin\AppData\Local\Temp\EPM v14 Activator v1.1 - De!.exe" | C:\Users\admin\AppData\Local\Temp\EPM v14 Activator v1.1 - De!.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: EaseUS_EPM Version: 2.0.0.0 Modules
| |||||||||||||||
Total events
6 503
Read events
6 405
Write events
94
Delete events
4
Modification events
| (PID) Process: | (4076) EPM v14 Activator v1.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (4076) EPM v14 Activator v1.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000010000000700000006000000000000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (4076) EPM v14 Activator v1.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (4076) EPM v14 Activator v1.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (4076) EPM v14 Activator v1.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (4076) EPM v14 Activator v1.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4076) EPM v14 Activator v1.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (4076) EPM v14 Activator v1.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (4076) EPM v14 Activator v1.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (4076) EPM v14 Activator v1.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | IconSize |
Value: 16 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |