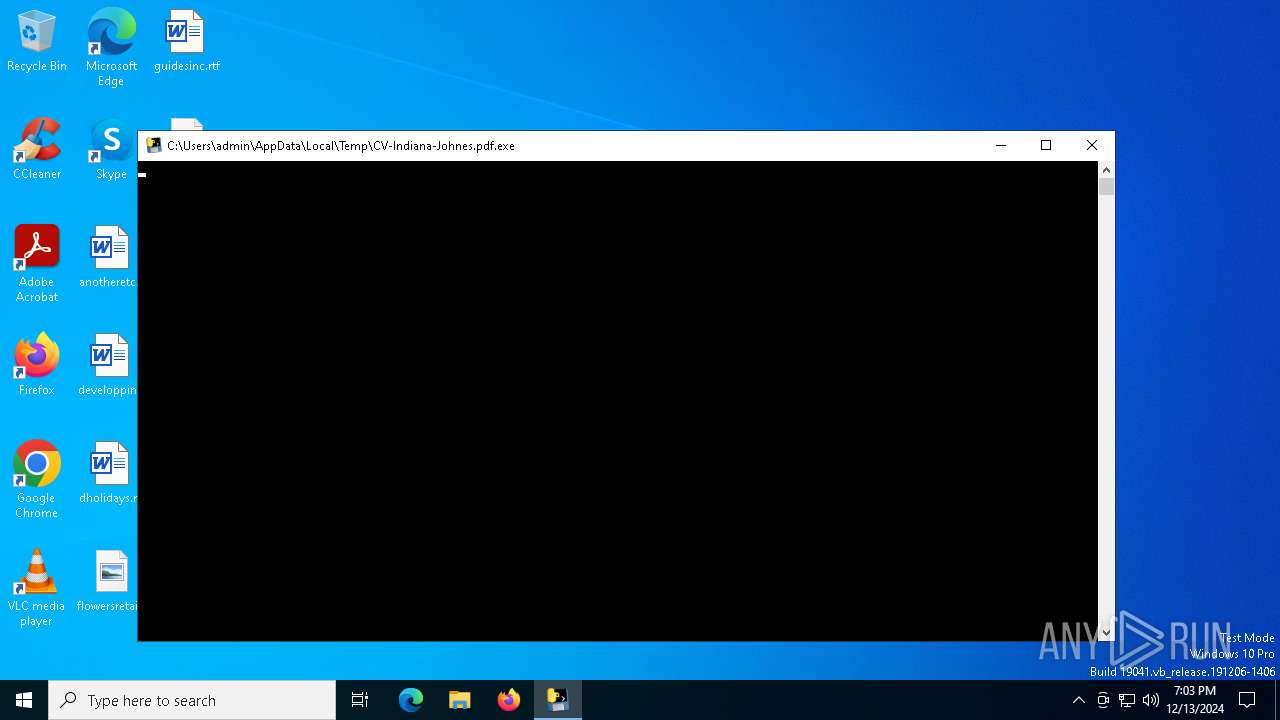
| File name: | CV-Indiana-Johnes.pdf.exe |
| Full analysis: | https://app.any.run/tasks/d9a343d6-4c96-4256-94e4-8dc09cf8c9da |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 19:03:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 3 sections |
| MD5: | 94700D099F55903EDFB286F223D4FE6E |
| SHA1: | 2296679E7FC36C9A44C63E9154DB447B5CD04474 |
| SHA256: | D8E3516C4D65A8D0B35F87D60E1B01F3730E3456658F5A38FDA525E8EACFC009 |
| SSDEEP: | 98304:ZzGouKRBzXqVyqX5ysBfUyRpTe2SnPyTPjW4Uc346MYjH/2xumzy7266tHfktEzd:z8JrbLhXFEEwDoD5T8A |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- CV-Indiana-Johnes.pdf.exe (PID: 6600)
- CV-Indiana-Johnes.pdf.exe (PID: 6684)
Starts CMD.EXE for commands execution
- CV-Indiana-Johnes.pdf.exe (PID: 6684)
- OpenVpnConnect.exe (PID: 6720)
The executable file from the user directory is run by the CMD process
- OpenVpnConnect.exe (PID: 6720)
Process drops python dynamic module
- CV-Indiana-Johnes.pdf.exe (PID: 6600)
Process drops legitimate windows executable
- CV-Indiana-Johnes.pdf.exe (PID: 6600)
The process drops C-runtime libraries
- CV-Indiana-Johnes.pdf.exe (PID: 6600)
Application launched itself
- CV-Indiana-Johnes.pdf.exe (PID: 6600)
Executing commands from a ".bat" file
- OpenVpnConnect.exe (PID: 6720)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6756)
Loads Python modules
- CV-Indiana-Johnes.pdf.exe (PID: 6684)
INFO
Reads the computer name
- OpenVpnConnect.exe (PID: 6720)
- CV-Indiana-Johnes.pdf.exe (PID: 6600)
- CV-Indiana-Johnes.pdf.exe (PID: 6684)
Checks supported languages
- OpenVpnConnect.exe (PID: 6720)
- CV-Indiana-Johnes.pdf.exe (PID: 6600)
- CV-Indiana-Johnes.pdf.exe (PID: 6684)
Create files in a temporary directory
- OpenVpnConnect.exe (PID: 6720)
- CV-Indiana-Johnes.pdf.exe (PID: 6600)
- CV-Indiana-Johnes.pdf.exe (PID: 6684)
The sample compiled with english language support
- CV-Indiana-Johnes.pdf.exe (PID: 6600)
Checks proxy server information
- CV-Indiana-Johnes.pdf.exe (PID: 6684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (47) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (46.1) |
| .exe | | | Generic Win/DOS Executable (3.4) |
| .exe | | | DOS Executable Generic (3.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:12:12 16:25:23+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 135168 |
| InitializedDataSize: | 65536 |
| UninitializedDataSize: | 237568 |
| EntryPoint: | 0x5ad70 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
131
Monitored processes
8
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6600 | "C:\Users\admin\AppData\Local\Temp\CV-Indiana-Johnes.pdf.exe" | C:\Users\admin\AppData\Local\Temp\CV-Indiana-Johnes.pdf.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6608 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | CV-Indiana-Johnes.pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6684 | "C:\Users\admin\AppData\Local\Temp\CV-Indiana-Johnes.pdf.exe" | C:\Users\admin\AppData\Local\Temp\CV-Indiana-Johnes.pdf.exe | CV-Indiana-Johnes.pdf.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6704 | C:\WINDOWS\system32\cmd.exe /c "OpenVpnConnect.exe" | C:\Windows\System32\cmd.exe | — | CV-Indiana-Johnes.pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6720 | OpenVpnConnect.exe | C:\Users\admin\AppData\Local\Temp\OpenVpnConnect.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: sνchost Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6756 | "cmd.exe" /c C:\Users\admin\AppData\Local\Temp\gugugaga.bat C:\Users\admin\AppData\Local\Temp\OpenVpnConnect.exe | C:\Windows\System32\cmd.exe | — | OpenVpnConnect.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6784 | timeout /t 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6816 | cipher /w:"C:\Users" | C:\Windows\System32\cipher.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: File Encryption Utility Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
406
Read events
406
Write events
0
Delete events
0
Modification events
Executable files
64
Suspicious files
1
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6600 | CV-Indiana-Johnes.pdf.exe | C:\Users\admin\AppData\Local\Temp\_MEI66002\MSVCP140.dll | executable | |
MD5:6C3AD90EE8D03A4CE68DBB34B0D72B1E | SHA256:7B8A6F283884E6448559DCF510B00C1A885BFB8E598EA05CD2C290C874657326 | |||
| 6600 | CV-Indiana-Johnes.pdf.exe | C:\Users\admin\AppData\Local\Temp\_MEI66002\_brotli.cp311-win_amd64.pyd | executable | |
MD5:0606E7D1AF5D7420EA2F363A9B22E647 | SHA256:79E60CD8BFD29AD1F7D0BF7A1EEC3D9ABADFCE90587438EA172034074BC174EE | |||
| 6600 | CV-Indiana-Johnes.pdf.exe | C:\Users\admin\AppData\Local\Temp\_MEI66002\_lzma.pyd | executable | |
MD5:B86B9F292AF12006187EBE6C606A377D | SHA256:F5E01B516C2C23035F7703E23569DEC26C5616C05A929B2580AE474A5C6722C5 | |||
| 6600 | CV-Indiana-Johnes.pdf.exe | C:\Users\admin\AppData\Local\Temp\_MEI66002\_socket.pyd | executable | |
MD5:B77017BAA2004833EF3847A3A3141280 | SHA256:A19E3C7C03EF1B5625790B1C9C42594909311AB6DF540FBF43C6AA93300AB166 | |||
| 6600 | CV-Indiana-Johnes.pdf.exe | C:\Users\admin\AppData\Local\Temp\_MEI66002\VCRUNTIME140_1.dll | executable | |
MD5:F8DFA78045620CF8A732E67D1B1EB53D | SHA256:A113F192195F245F17389E6ECBED8005990BCB2476DDAD33F7C4C6C86327AFE5 | |||
| 6600 | CV-Indiana-Johnes.pdf.exe | C:\Users\admin\AppData\Local\Temp\_MEI66002\_queue.pyd | executable | |
MD5:7F52EF40B083F34FD5E723E97B13382F | SHA256:3F8E7E6AA13B417ACC78B63434FB1144E6319A010A9FC376C54D6E69B638FE4C | |||
| 6600 | CV-Indiana-Johnes.pdf.exe | C:\Users\admin\AppData\Local\Temp\_MEI66002\_bz2.pyd | executable | |
MD5:AA1083BDE6D21CABFC630A18F51B1926 | SHA256:00B8CA9A338D2B47285C9E56D6D893DB2A999B47216756F18439997FB80A56E3 | |||
| 6600 | CV-Indiana-Johnes.pdf.exe | C:\Users\admin\AppData\Local\Temp\_MEI66002\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:EB0978A9213E7F6FDD63B2967F02D999 | SHA256:AB25A1FE836FC68BCB199F1FE565C27D26AF0C390A38DA158E0D8815EFE1103E | |||
| 6600 | CV-Indiana-Johnes.pdf.exe | C:\Users\admin\AppData\Local\Temp\_MEI66002\_decimal.pyd | executable | |
MD5:C88282908BA54510EDA3887C488198EB | SHA256:980A63F2B39CF16910F44384398E25F24482346A482ADDB00DE42555B17D4278 | |||
| 6600 | CV-Indiana-Johnes.pdf.exe | C:\Users\admin\AppData\Local\Temp\_MEI66002\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:33BBECE432F8DA57F17BF2E396EBAA58 | SHA256:7CF0944901F7F7E0D0B9AD62753FC2FE380461B1CCE8CDC7E9C9867C980E3B0E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
30
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6884 | SIHClient.exe | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6884 | SIHClient.exe | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
5780 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
244 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 23.212.110.161:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.9.218:80 | www.microsoft.com | AKAMAI-AS | CZ | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |