| File name: | ConsoleApp4.exe |
| Full analysis: | https://app.any.run/tasks/9b370d8b-875e-482e-9147-8b666fcd1986 |
| Verdict: | Malicious activity |
| Analysis date: | November 09, 2024, 09:52:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 9DFD171769BD942E24405BD4A1EE839C |
| SHA1: | 2A5DAA67EE46EFF64C86CCF516DC6416CBF78180 |
| SHA256: | D8CC014A4EDAC8CD90C47D35796A8F7C7687AAAA95E1D94956F8208CA52CF0C9 |
| SSDEEP: | 98304:STIhEIPl7i+/OmeNSq3Ae1XfA09pbID6HdDVJyR5f0CKNIXFida+o8eLO+A84tVN:wK+u/29M5V3Yt |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- ConsoleApp4.exe (PID: 6432)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- ConsoleApp4.exe (PID: 6432)
Checks for external IP
- ConsoleApp4.exe (PID: 6432)
INFO
Creates files or folders in the user directory
- ConsoleApp4.exe (PID: 6432)
Checks supported languages
- ConsoleApp4.exe (PID: 6432)
Reads the computer name
- ConsoleApp4.exe (PID: 6432)
Reads Environment values
- ConsoleApp4.exe (PID: 6432)
Disables trace logs
- ConsoleApp4.exe (PID: 6432)
Reads the machine GUID from the registry
- ConsoleApp4.exe (PID: 6432)
Checks proxy server information
- ConsoleApp4.exe (PID: 6432)
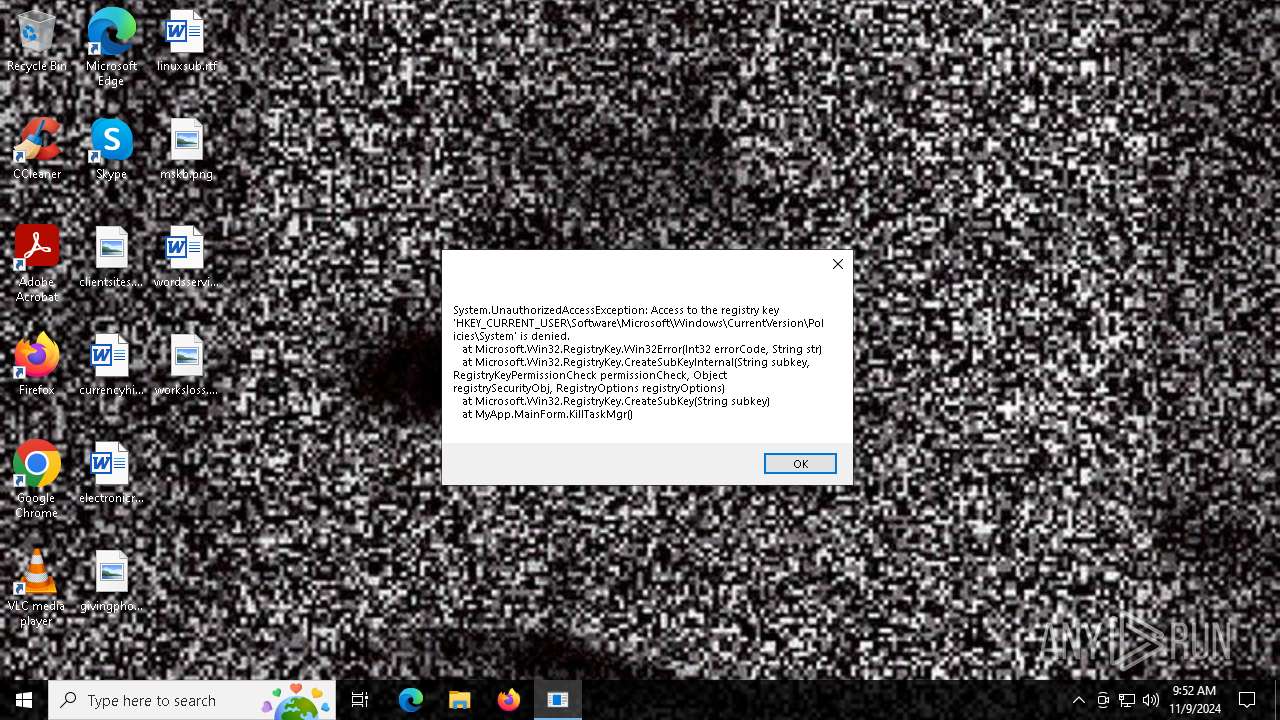
Reads the software policy settings
- ConsoleApp4.exe (PID: 6432)
Create files in a temporary directory
- ConsoleApp4.exe (PID: 6432)
Attempting to use instant messaging service
- ConsoleApp4.exe (PID: 6432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:12:09 18:58:13+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 4096 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2e5e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | ConsoleApp4 |
| FileVersion: | 1.0.0.0 |
| InternalName: | ConsoleApp4.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | ConsoleApp4.exe |
| ProductName: | ConsoleApp4 |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
131
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6432 | "C:\Users\admin\AppData\Local\Temp\ConsoleApp4.exe" | C:\Users\admin\AppData\Local\Temp\ConsoleApp4.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ConsoleApp4 Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 314
Read events
1 277
Write events
35
Delete events
2
Modification events
| (PID) Process: | (6432) ConsoleApp4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | UniqueID |
Value: {86185875-D176-426E-A5B1-1D2947D9AE8B} | |||
| (PID) Process: | (6432) ConsoleApp4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | ComputerName |
Value: DESKTOP-JGLLJLD | |||
| (PID) Process: | (6432) ConsoleApp4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | VolumeSerialNumber |
Value: 649566714 | |||
| (PID) Process: | (6432) ConsoleApp4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Player\Settings |
| Operation: | delete value | Name: | Client ID |
Value: {CECDFD5C-8F08-4FEF-8713-FAA895A422EB} | |||
| (PID) Process: | (6432) ConsoleApp4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | LocalBase |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML | |||
| (PID) Process: | (6432) ConsoleApp4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | DTDFile |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.DTD | |||
| (PID) Process: | (6432) ConsoleApp4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | LocalDelta |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNSD.XML | |||
| (PID) Process: | (6432) ConsoleApp4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | RemoteDelta |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNSR.XML | |||
| (PID) Process: | (6432) ConsoleApp4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences\ProxySettings\HTTP |
| Operation: | write | Name: | ProxyStyle |
Value: 1 | |||
| (PID) Process: | (6432) ConsoleApp4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences\ProxySettings\HTTP |
| Operation: | write | Name: | ProxyName |
Value: | |||
Executable files
0
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6432 | ConsoleApp4.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML | text | |
MD5:5433EAB10C6B5C6D55B7CBD302426A39 | SHA256:23DBF7014E99E93AF5F2760F18EE1370274F06A453145C8D539B66D798DAD131 | |||
| 6432 | ConsoleApp4.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.DTD | xml | |
MD5:90BE2701C8112BEBC6BD58A7DE19846E | SHA256:644FBCDC20086E16D57F31C5BAD98BE68D02B1C061938D2F5F91CBE88C871FBF | |||
| 6432 | ConsoleApp4.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML.bak | text | |
MD5:7050D5AE8ACFBE560FA11073FEF8185D | SHA256:CB87767C4A384C24E4A0F88455F59101B1AE7B4FB8DE8A5ADB4136C5F7EE545B | |||
| 6432 | ConsoleApp4.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNSD.XML | text | |
MD5:A9B5DA9AEC61657B32393D96217165F0 | SHA256:9F4611369CF65B33D886489B2486FCA7B1E83E0DC998D35B15B3AA4C8478A28D | |||
| 6432 | ConsoleApp4.exe | C:\Users\admin\AppData\Local\Temp\image.jpg | image | |
MD5:F2FB6C8C32583042E471D9542212FE51 | SHA256:1DBDF02E198F625E08D14CADC72EFF63992BB3C0C3122F0D2C93E5B998D5FDFD | |||
| 6432 | ConsoleApp4.exe | C:\Users\admin\Documents\zlo.txt | text | |
MD5:A5EA0AD9260B1550A14CC58D2C39B03D | SHA256:F1B2F662800122BED0FF255693DF89C4487FBDCF453D3524A42D4EC20C3D9C04 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
43
DNS requests
21
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7028 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7036 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7036 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6812 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1752 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6432 | ConsoleApp4.exe | 172.67.74.152:443 | api.ipify.org | CLOUDFLARENET | US | shared |
6432 | ConsoleApp4.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | shared |
4360 | SearchApp.exe | 2.23.209.160:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
7028 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
api.ipify.org |
| shared |
api.telegram.org |
| shared |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6432 | ConsoleApp4.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2172 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
2172 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6432 | ConsoleApp4.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
6432 | ConsoleApp4.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |