| File name: | memz_batch_code.bat |
| Full analysis: | https://app.any.run/tasks/4cf7b264-9248-45cf-b365-bfc7b153a44b |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 22:09:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 44FBD58C401A7786DA2E8B6A6291379E |
| SHA1: | 9DBFD08FA557D9DCE79911EB4BBDDB2008D4F53F |
| SHA256: | D8B47727EA05305AD396977B336C3BFC86AE122CDDE01976FA9B0C3A7C2D3F24 |
| SSDEEP: | 192:vOyUySl0UaDz2gWsIzlmj+BxZ3yqueWQx0lZicyC8Sh31xcjBzyxwn7AVhllz3:vVODaDSHMql3yqlxy5L1xcjwrlz3 |
MALICIOUS
Gets a file object corresponding to the file in a specified path (SCRIPT)
- cscript.exe (PID: 1484)
Uses base64 encoding (SCRIPT)
- cscript.exe (PID: 1484)
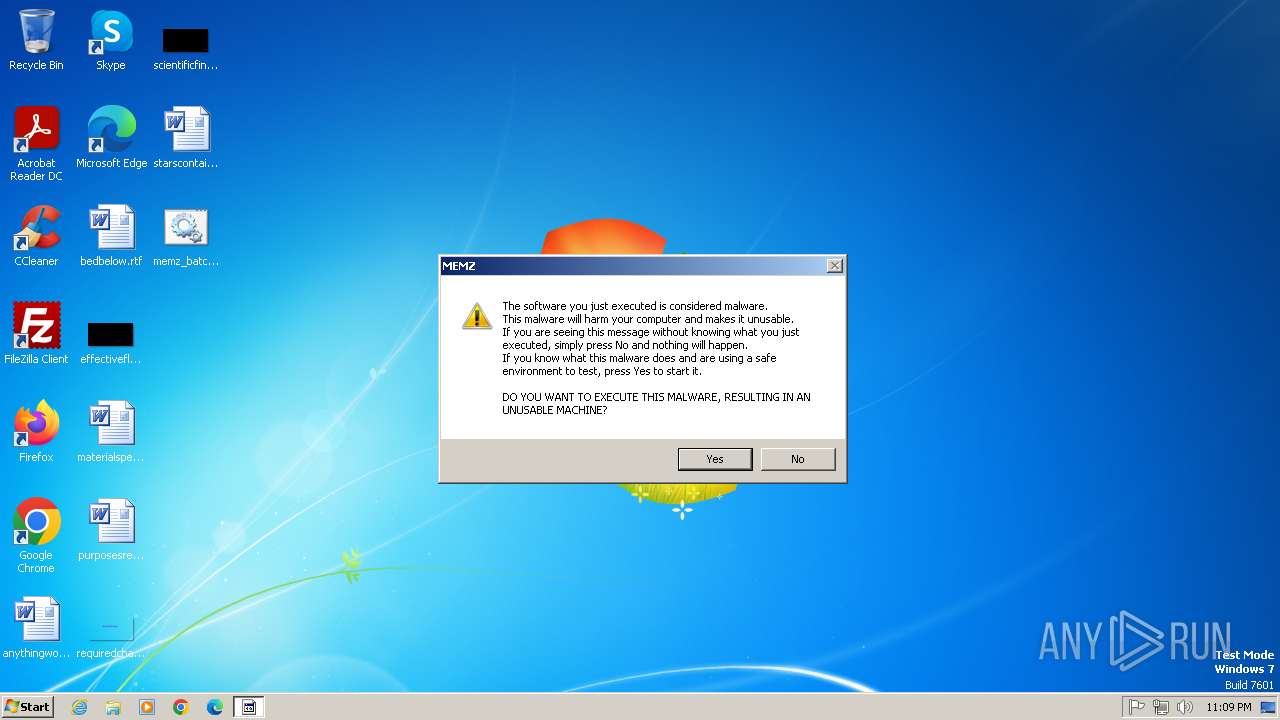
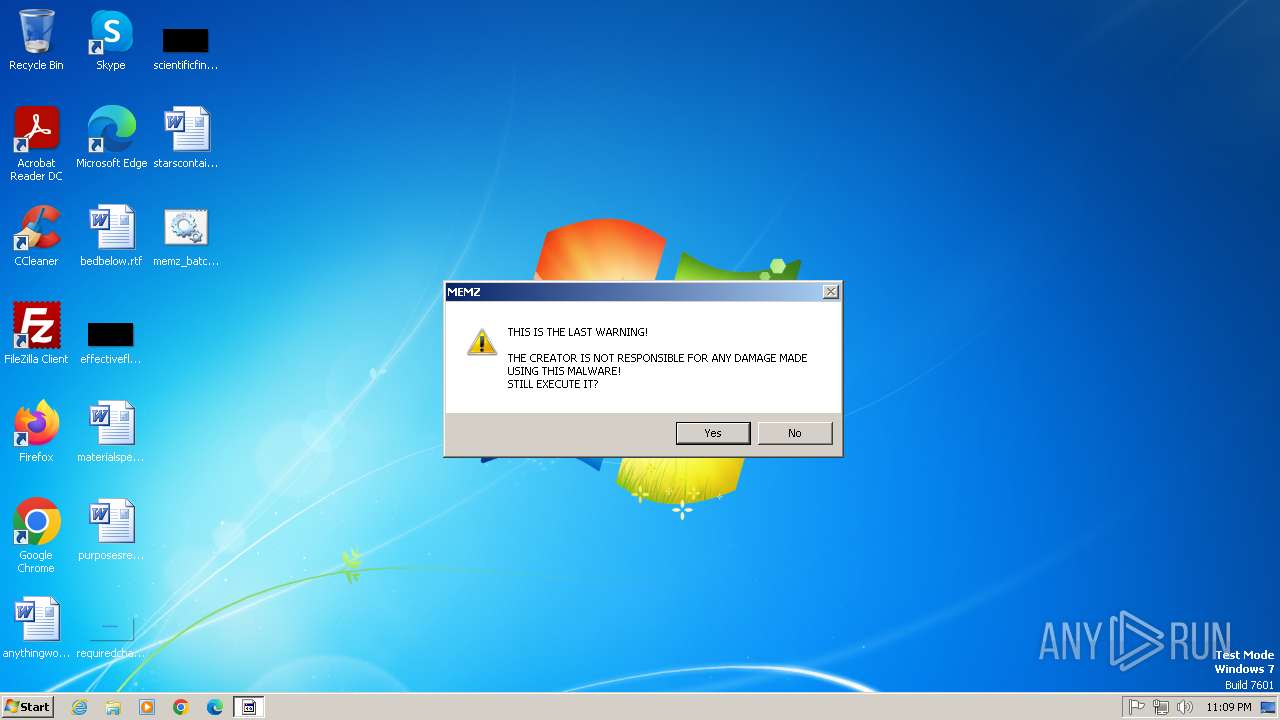
MEMZ has been detected (YARA)
- MEMZ.exe (PID: 3116)
- MEMZ.exe (PID: 2392)
- MEMZ.exe (PID: 2528)
- MEMZ.exe (PID: 2508)
- MEMZ.exe (PID: 2912)
- MEMZ.exe (PID: 892)
- MEMZ.exe (PID: 1500)
SUSPICIOUS
The process executes JS scripts
- cmd.exe (PID: 2812)
Creates XML DOM element (SCRIPT)
- cscript.exe (PID: 1484)
Script creates XML DOM node (SCRIPT)
- cscript.exe (PID: 1484)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 1484)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 1484)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 1484)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 1484)
Saves data to a binary file (SCRIPT)
- cscript.exe (PID: 1484)
Creates a Folder object (SCRIPT)
- cscript.exe (PID: 1484)
Executable content was dropped or overwritten
- cscript.exe (PID: 1484)
Reads the Internet Settings
- cscript.exe (PID: 1484)
- cmd.exe (PID: 2812)
- MEMZ.exe (PID: 3116)
- MEMZ.exe (PID: 1500)
The executable file from the user directory is run by the CMD process
- MEMZ.exe (PID: 1336)
- MEMZ.exe (PID: 1864)
- MEMZ.exe (PID: 3116)
There is functionality for taking screenshot (YARA)
- MEMZ.exe (PID: 3116)
- MEMZ.exe (PID: 2528)
- MEMZ.exe (PID: 2392)
- MEMZ.exe (PID: 2508)
- MEMZ.exe (PID: 892)
- MEMZ.exe (PID: 2912)
- MEMZ.exe (PID: 1500)
Creates file in the systems drive root
- notepad.exe (PID: 3096)
- MEMZ.exe (PID: 1500)
Application launched itself
- MEMZ.exe (PID: 3116)
Reads security settings of Internet Explorer
- MEMZ.exe (PID: 3116)
- MEMZ.exe (PID: 1500)
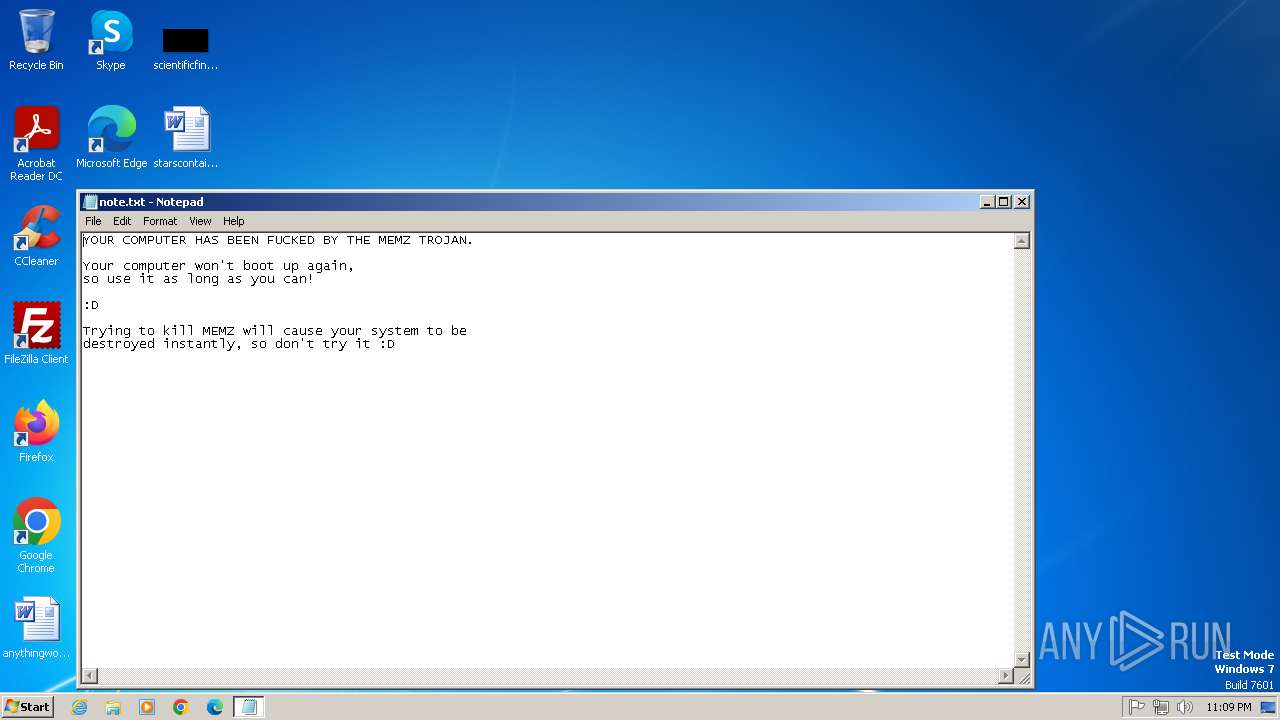
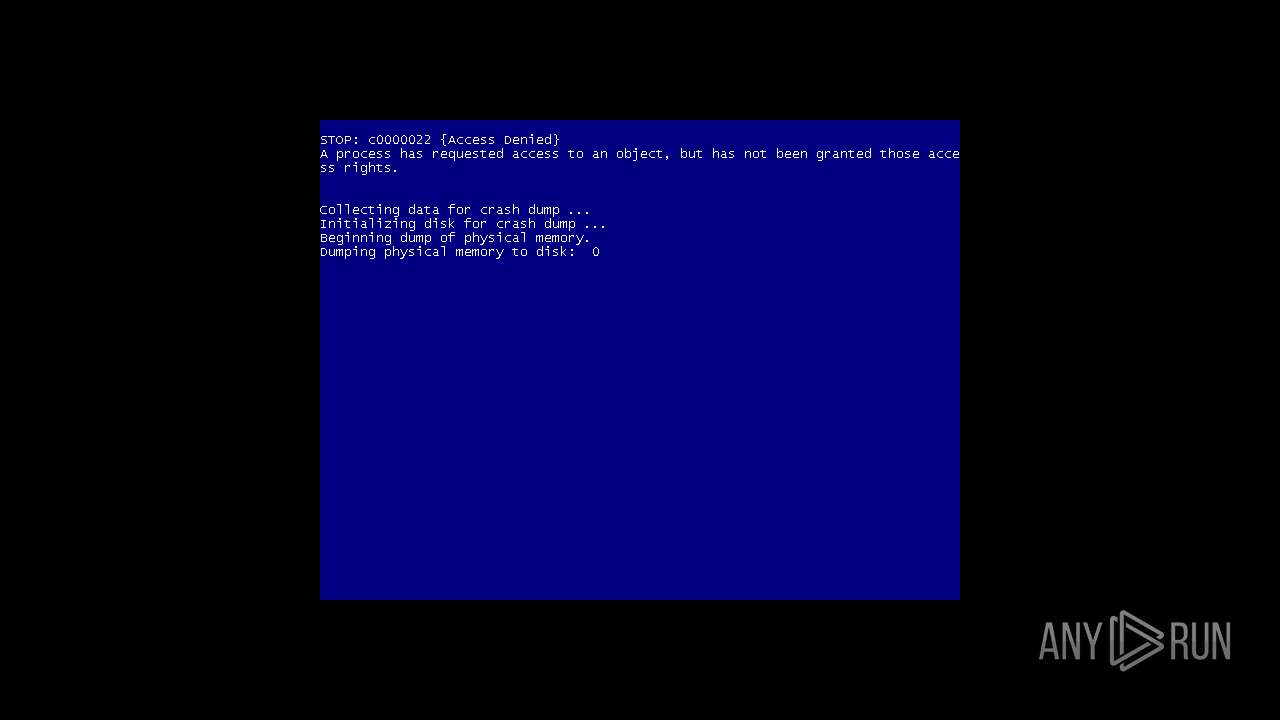
Start notepad (likely ransomware note)
- MEMZ.exe (PID: 1500)
Reads the date of Windows installation
- pwsh.exe (PID: 1548)
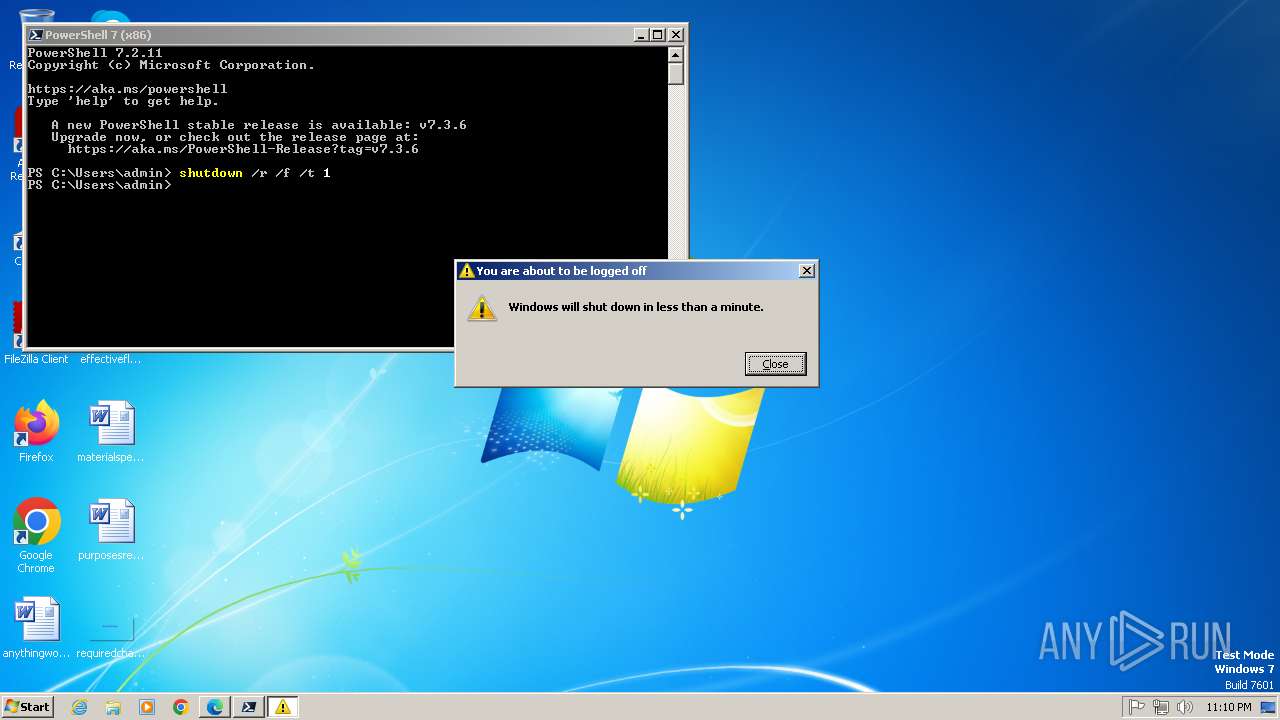
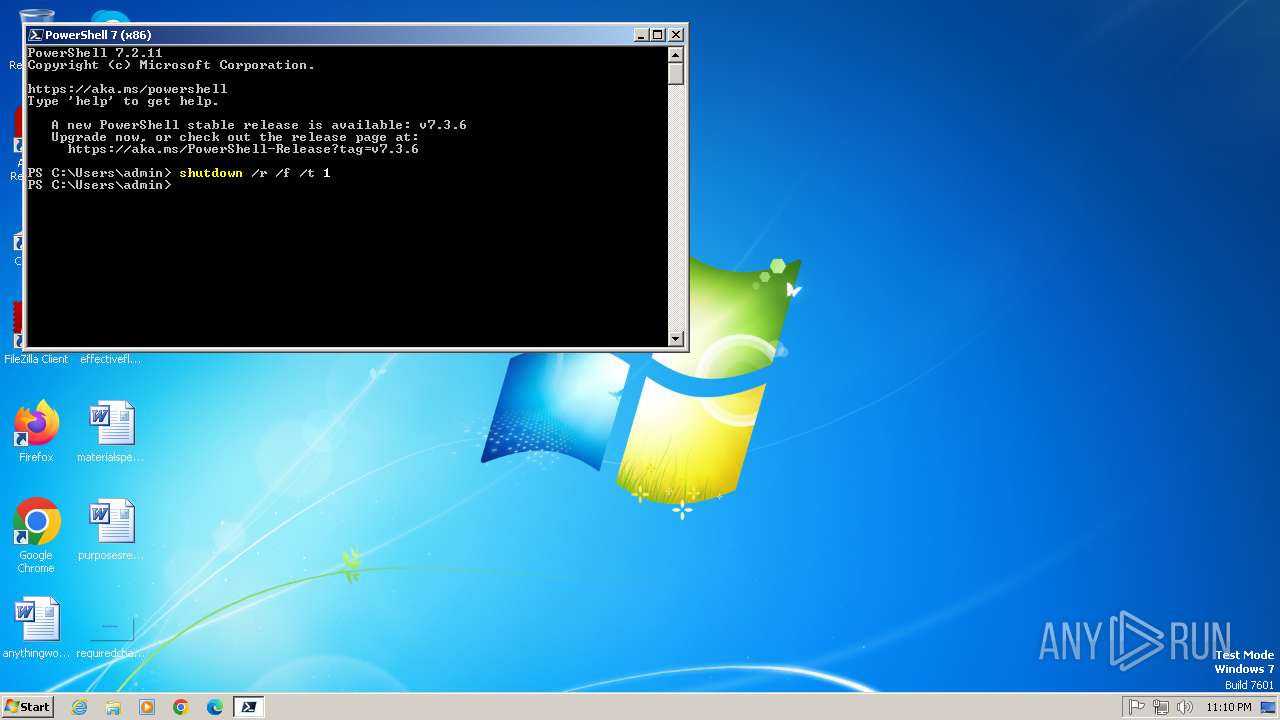
The system shut down or reboot
- pwsh.exe (PID: 1548)
INFO
Creates files or folders in the user directory
- cscript.exe (PID: 1484)
Reads security settings of Internet Explorer
- cscript.exe (PID: 1484)
Checks supported languages
- MEMZ.exe (PID: 3116)
- MEMZ.exe (PID: 2508)
- MEMZ.exe (PID: 2528)
- MEMZ.exe (PID: 2392)
- MEMZ.exe (PID: 892)
- MEMZ.exe (PID: 2912)
- MEMZ.exe (PID: 1500)
- pwsh.exe (PID: 1548)
Reads the computer name
- MEMZ.exe (PID: 3116)
- MEMZ.exe (PID: 1500)
- pwsh.exe (PID: 1548)
Application launched itself
- msedge.exe (PID: 2780)
- msedge.exe (PID: 3344)
Reads the machine GUID from the registry
- MEMZ.exe (PID: 1500)
- MEMZ.exe (PID: 2508)
- MEMZ.exe (PID: 2392)
- MEMZ.exe (PID: 2528)
- MEMZ.exe (PID: 2912)
- MEMZ.exe (PID: 892)
Manual execution by a user
- msedge.exe (PID: 2780)
- pwsh.exe (PID: 1548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
69
Monitored processes
29
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 580 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1536 --field-trial-handle=1276,i,3438986792626234747,13524840622930950653,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 892 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | MEMZ.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2176 --field-trial-handle=1276,i,3438986792626234747,13524840622930950653,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1336 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1484 | cscript x.js | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1500 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /main | C:\Users\admin\AppData\Roaming\MEMZ.exe | MEMZ.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 1548 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\PowerShell\7\pwsh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: pwsh Exit code: 1073807364 Version: 7.2.11.500 Modules
| |||||||||||||||
| 1864 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2392 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | MEMZ.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2508 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | MEMZ.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
12 441
Read events
12 257
Write events
181
Delete events
3
Modification events
| (PID) Process: | (1484) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1484) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1484) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1484) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2812) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2812) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2812) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2812) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3116) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3116) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
1
Suspicious files
40
Text files
33
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1500 | MEMZ.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 1548 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\7.2.11\update1_v7.4.10_2025-05-13 | — | |
MD5:— | SHA256:— | |||
| 1548 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\e1a648060a327b80.customDestinations-ms | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 1500 | MEMZ.exe | C:\note.txt | binary | |
MD5:AFA6955439B8D516721231029FB9CA1B | SHA256:8E9F20F6864C66576536C0B866C6FFDCF11397DB67FE120E972E244C3C022270 | |||
| 1548 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\e1a648060a327b80.customDestinations-ms~RF18755a.TMP | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 3668 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF192fef.TMP | — | |
MD5:— | SHA256:— | |||
| 2780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1548 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_brstizr3.onm.ps1 | text | |
MD5:165F2217002CFB760DEC9365BA18BD3B | SHA256:38CAFD8A846B8BB04096A038AC4E70AA18F661B501BBA0BF6D17B06275582B0D | |||
| 1484 | cscript.exe | C:\Users\admin\AppData\Roaming\MEMZ.exe | executable | |
MD5:19DBEC50735B5F2A72D4199C4E184960 | SHA256:A3D5715A81F2FBEB5F76C88C9C21EEEE87142909716472F911FF6950C790C24D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
17
DNS requests
16
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3152 | msedge.exe | GET | 302 | 142.250.185.132:80 | http://google.co.ck/search?q=best+way+to+kill+yourself | unknown | — | — | whitelisted |
3152 | msedge.exe | GET | — | 142.250.186.163:80 | http://www.google.co.ck/search?q=best+way+to+kill+yourself&google_abuse=GOOGLE_ABUSE_EXEMPTION%3DID%3Dac4ae88301e39f93:TM%3D1747519833:C%3Dj:IP%3D212.30.37.95-:S%3Dtg3MhEHM9ydiVE8eBPPwmw%3B+path%3D/%3B+domain%3Dgoogle.com%3B+expires%3DSun,+18-May-2025+01:10:33+GMT | unknown | — | — | whitelisted |
3152 | msedge.exe | GET | 301 | 142.250.185.132:80 | http://google.co.ck/search?q=best+way+to+kill+yourself&google_abuse=GOOGLE_ABUSE_EXEMPTION%3DID%3Dac4ae88301e39f93:TM%3D1747519833:C%3Dj:IP%3D212.30.37.95-:S%3Dtg3MhEHM9ydiVE8eBPPwmw%3B+path%3D/%3B+domain%3Dgoogle.com%3B+expires%3DSun,+18-May-2025+01:10:33+GMT | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1548 | pwsh.exe | 104.85.2.183:443 | aka.ms | AKAMAI-AS | NL | whitelisted |
1548 | pwsh.exe | 13.107.246.45:443 | powershellinfraartifacts-gkhedzdeaghdezhr.z01.azurefd.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | malicious |
1548 | pwsh.exe | 20.50.88.241:443 | dc.services.visualstudio.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3152 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3152 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3152 | msedge.exe | 142.250.185.132:80 | google.co.ck | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
aka.ms |
| whitelisted |
powershellinfraartifacts-gkhedzdeaghdezhr.z01.azurefd.net |
| unknown |
dc.services.visualstudio.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
google.co.ck |
| whitelisted |
www.google.com |
| whitelisted |
www.google.co.ck |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1548 | pwsh.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
Process | Message |
|---|---|
pwsh.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 1548. Message ID: [0x2509].
|