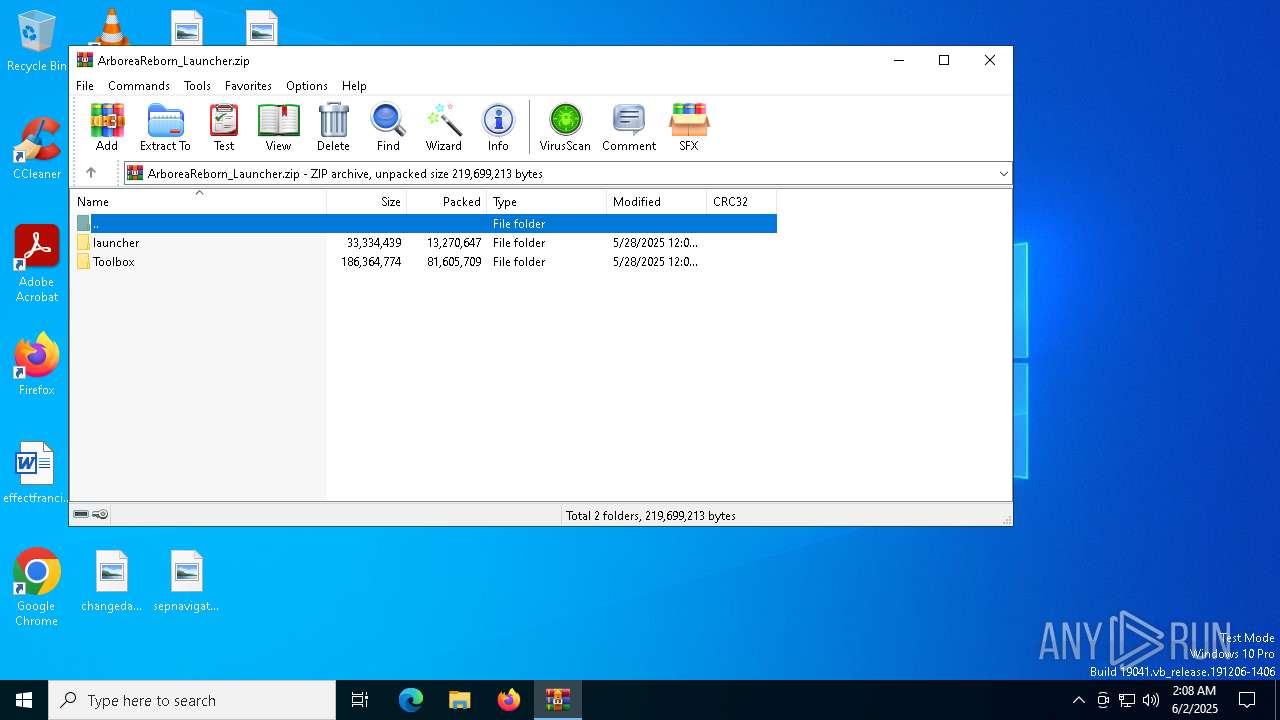
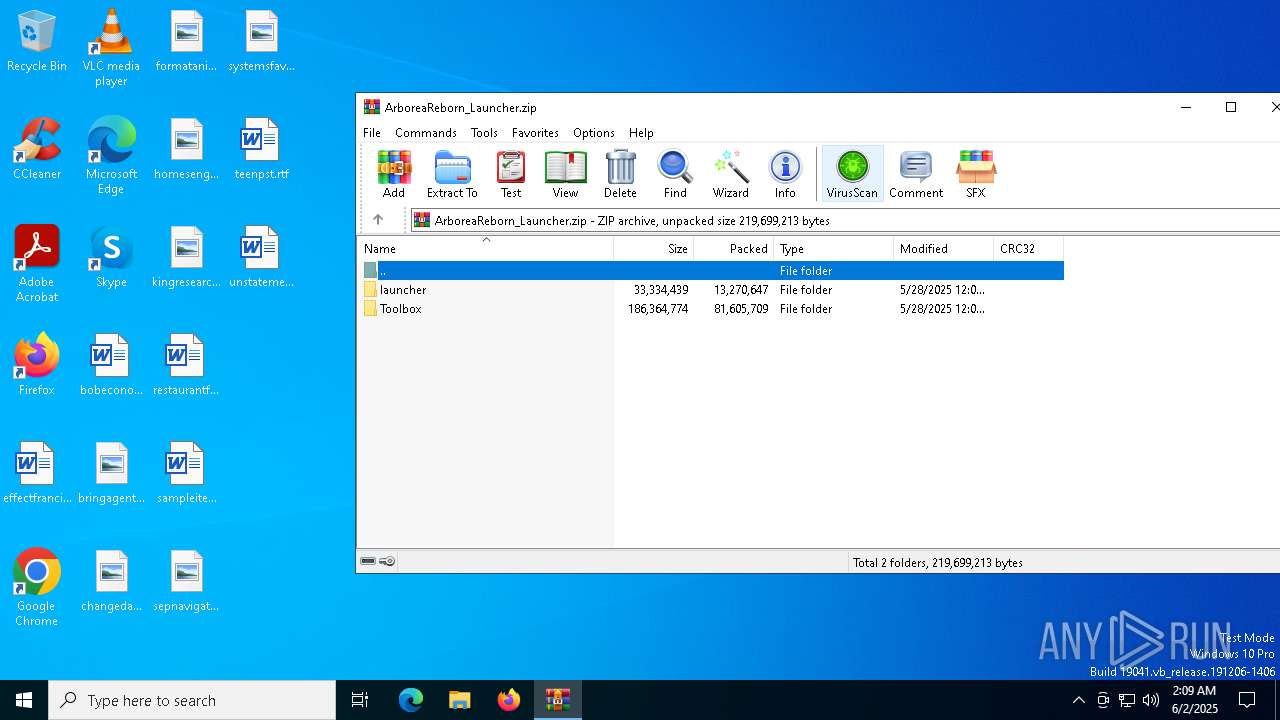
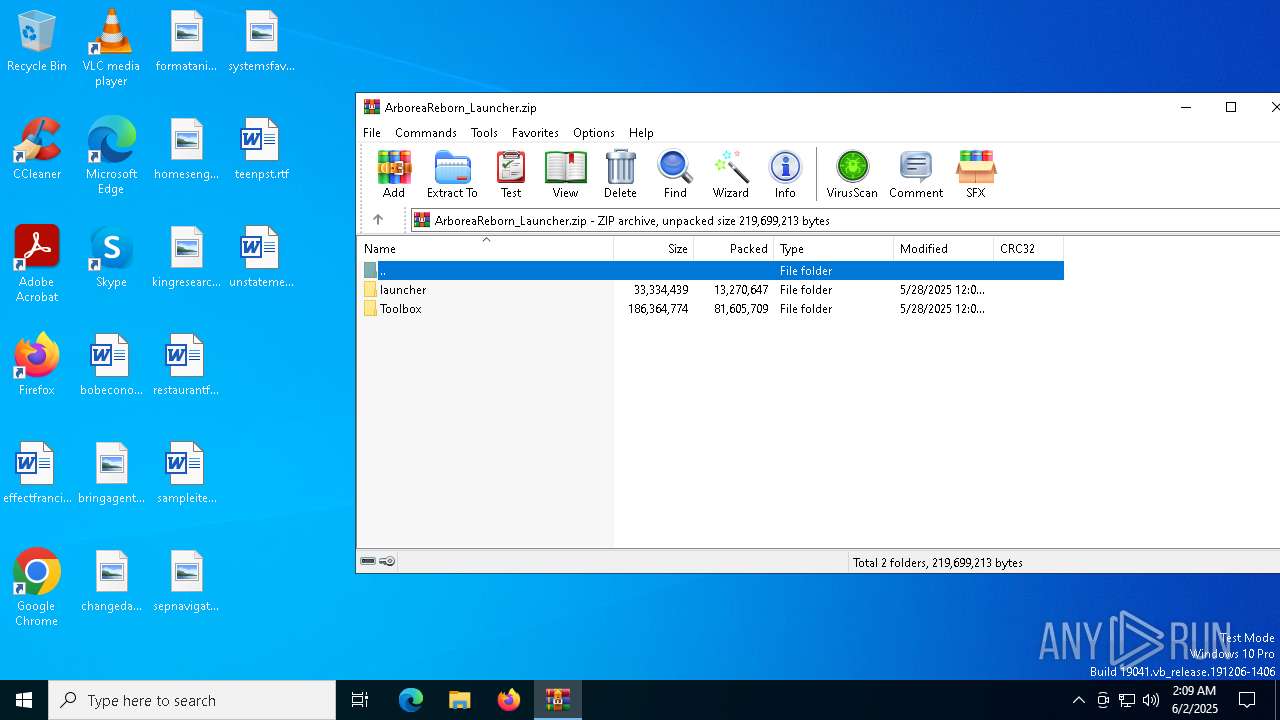
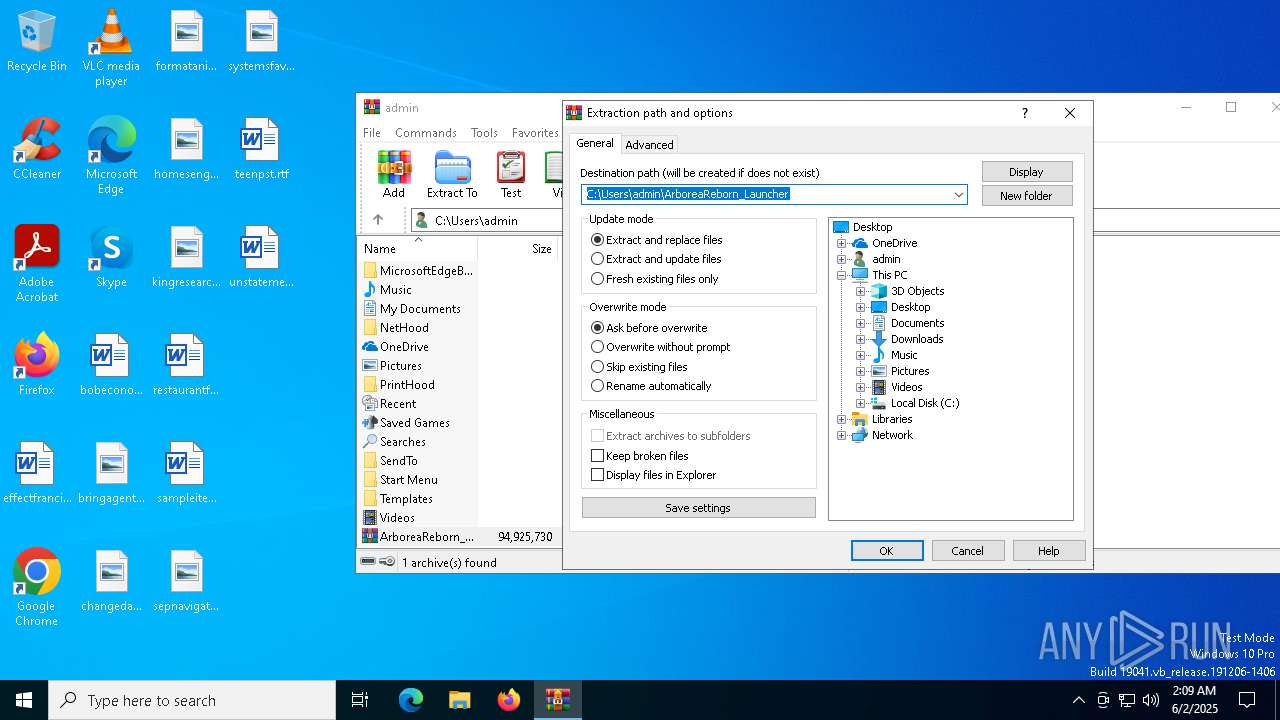
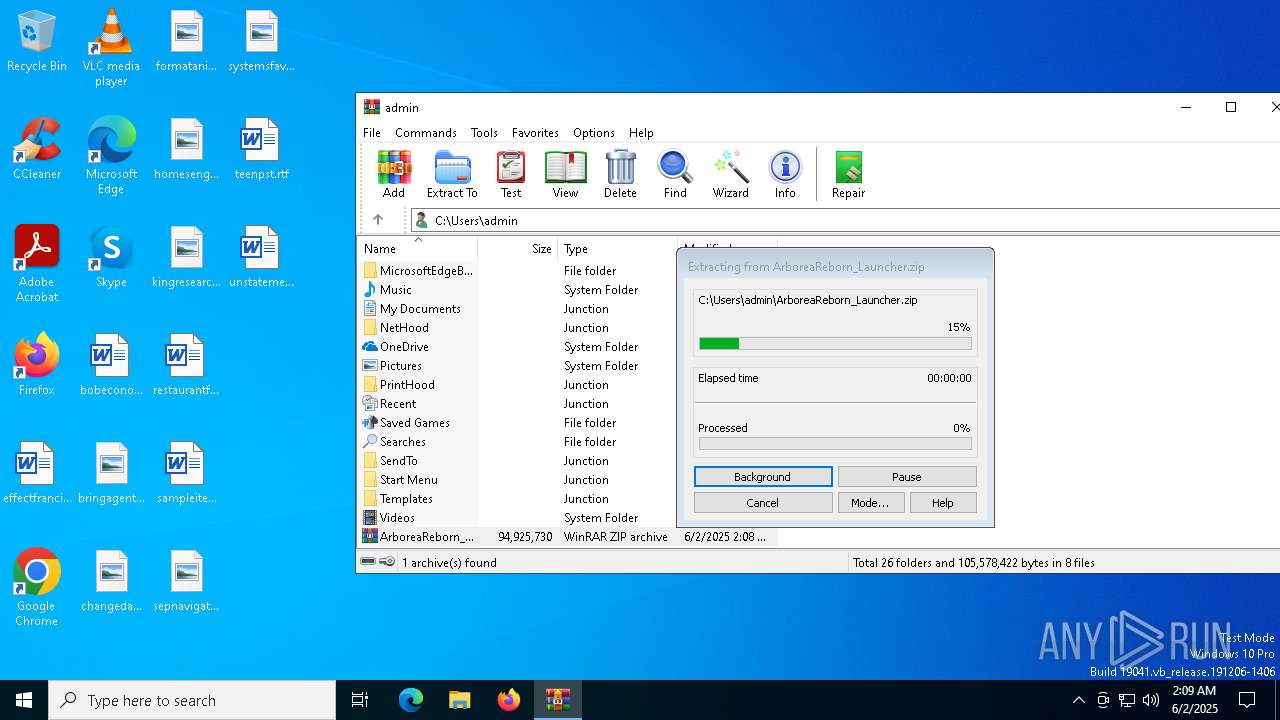
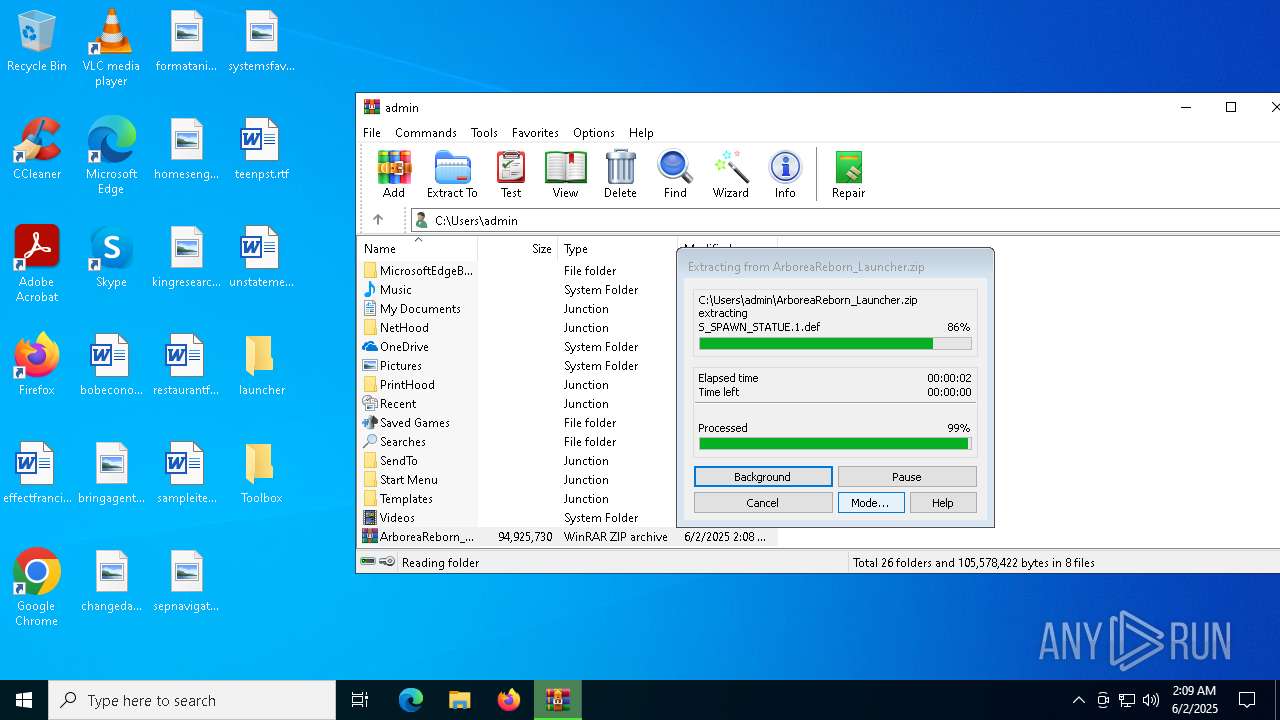
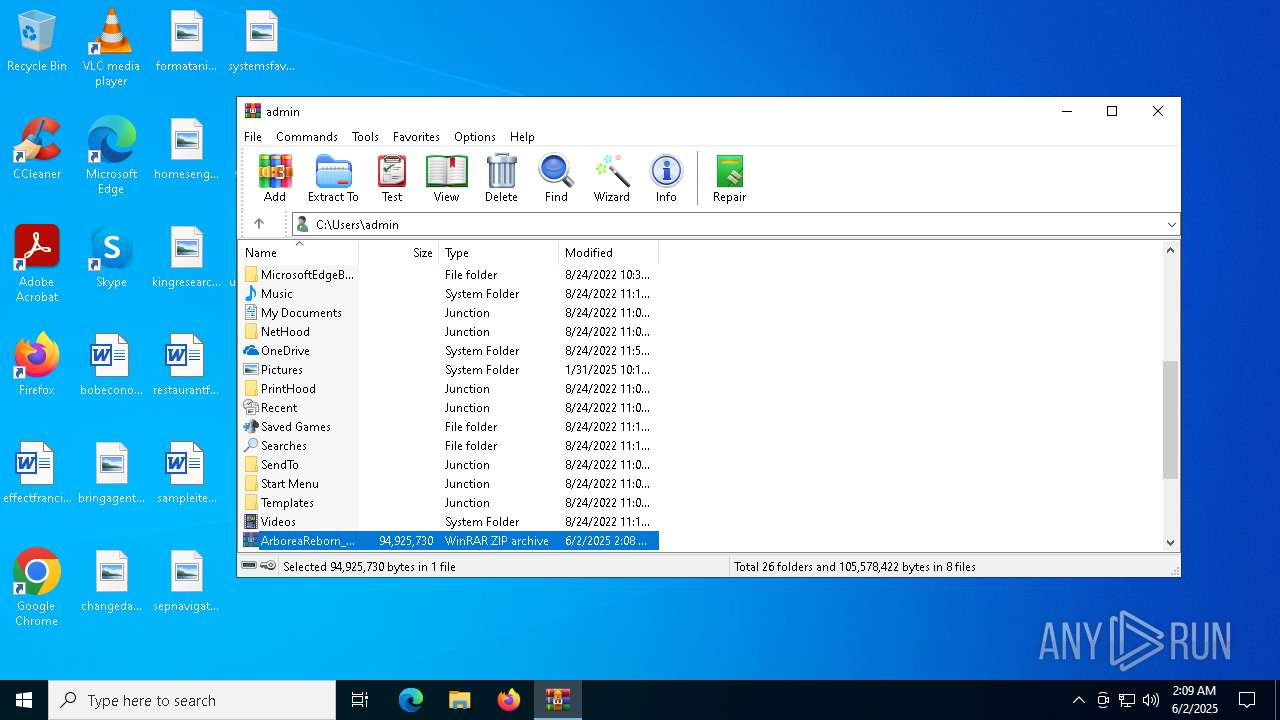
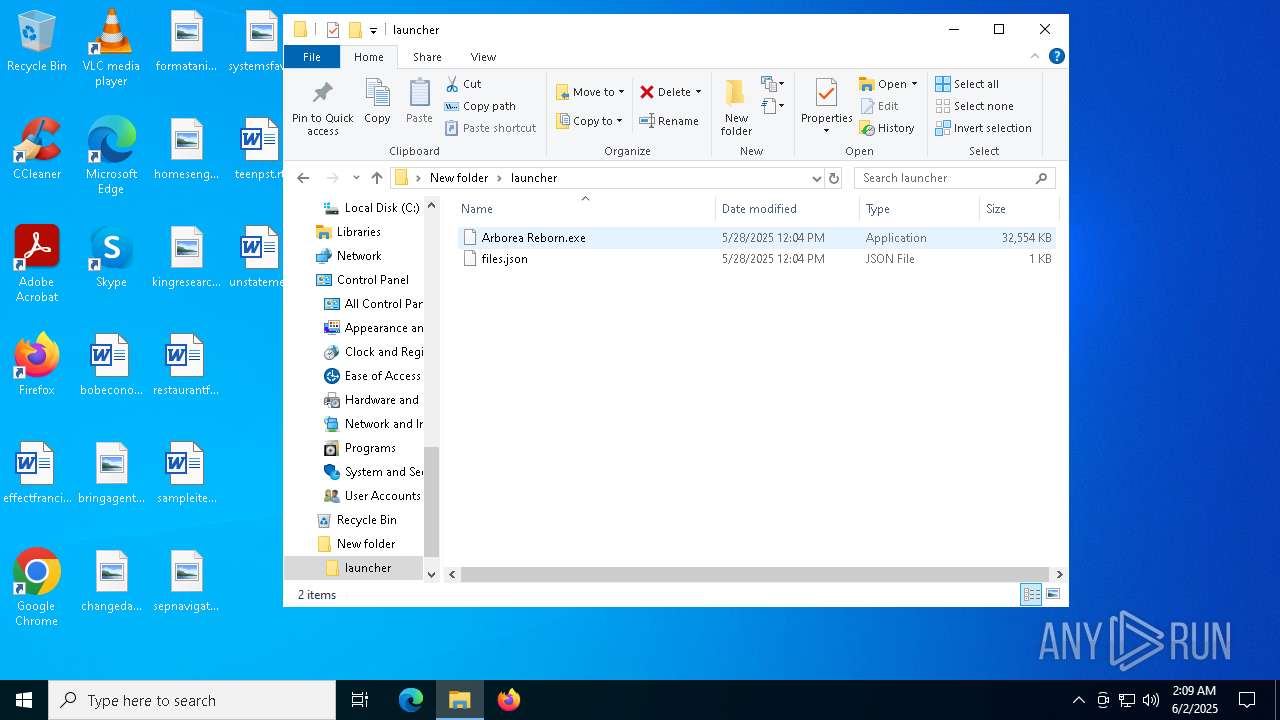
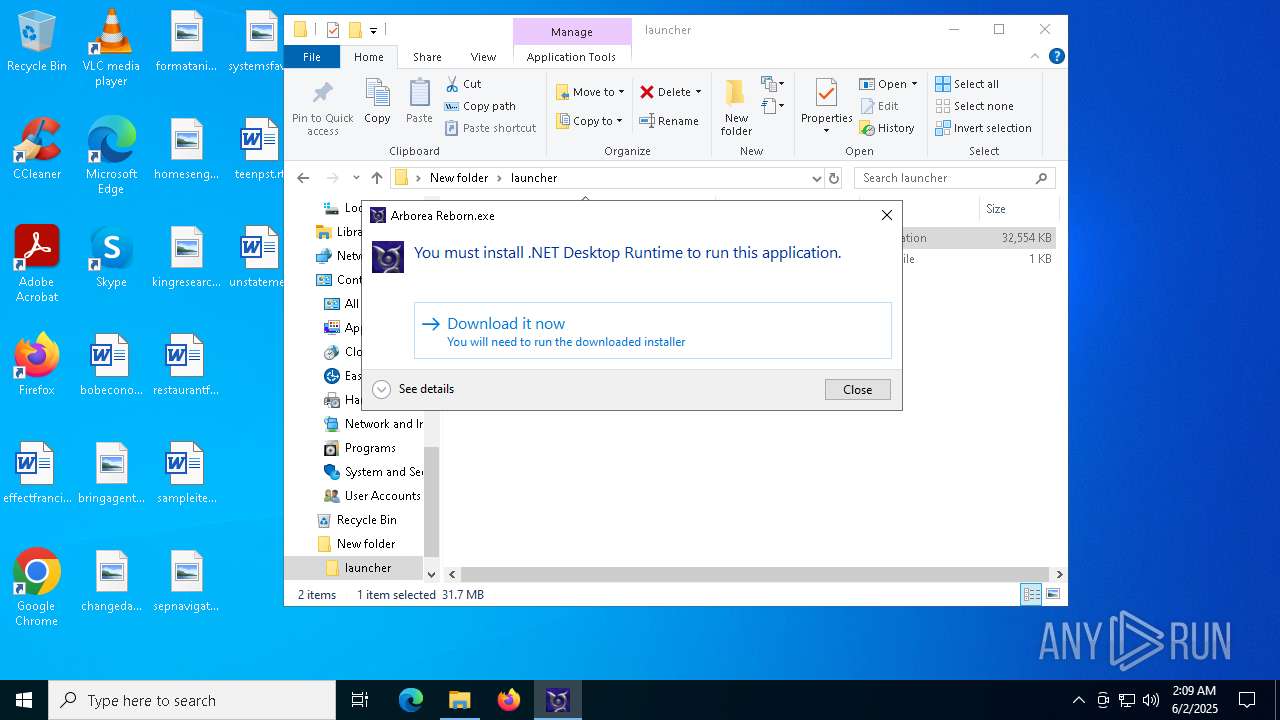
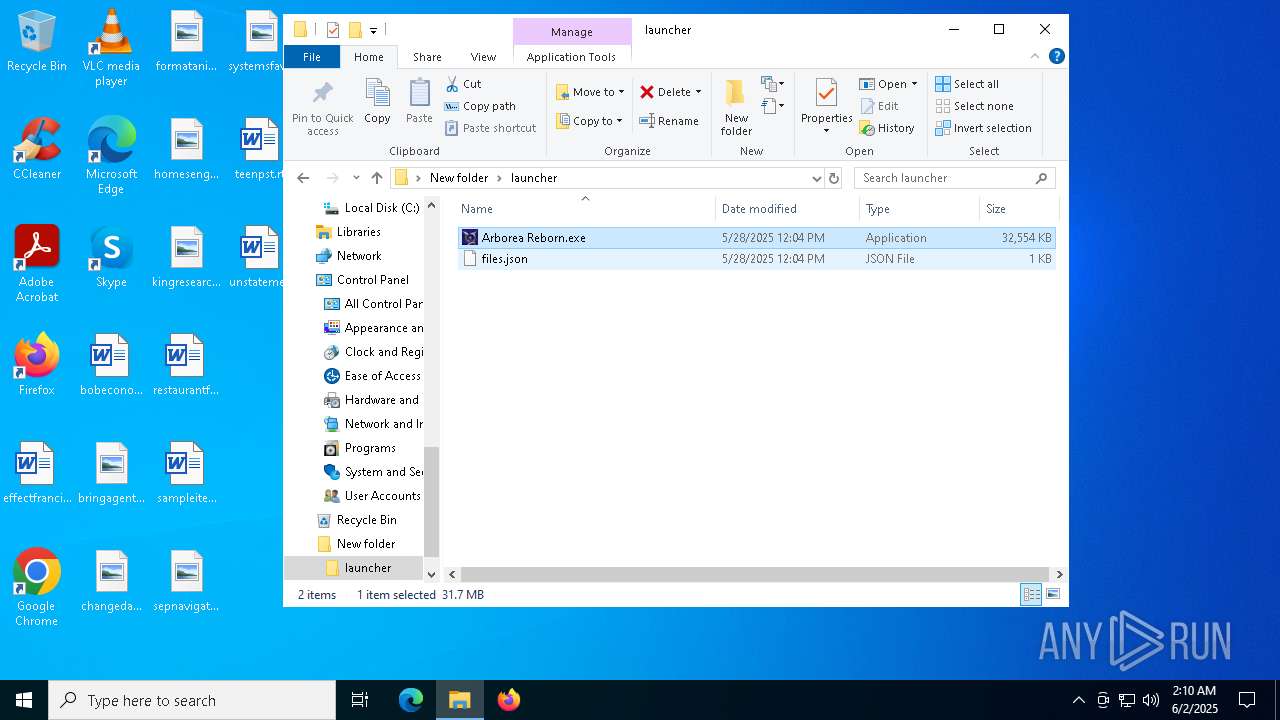
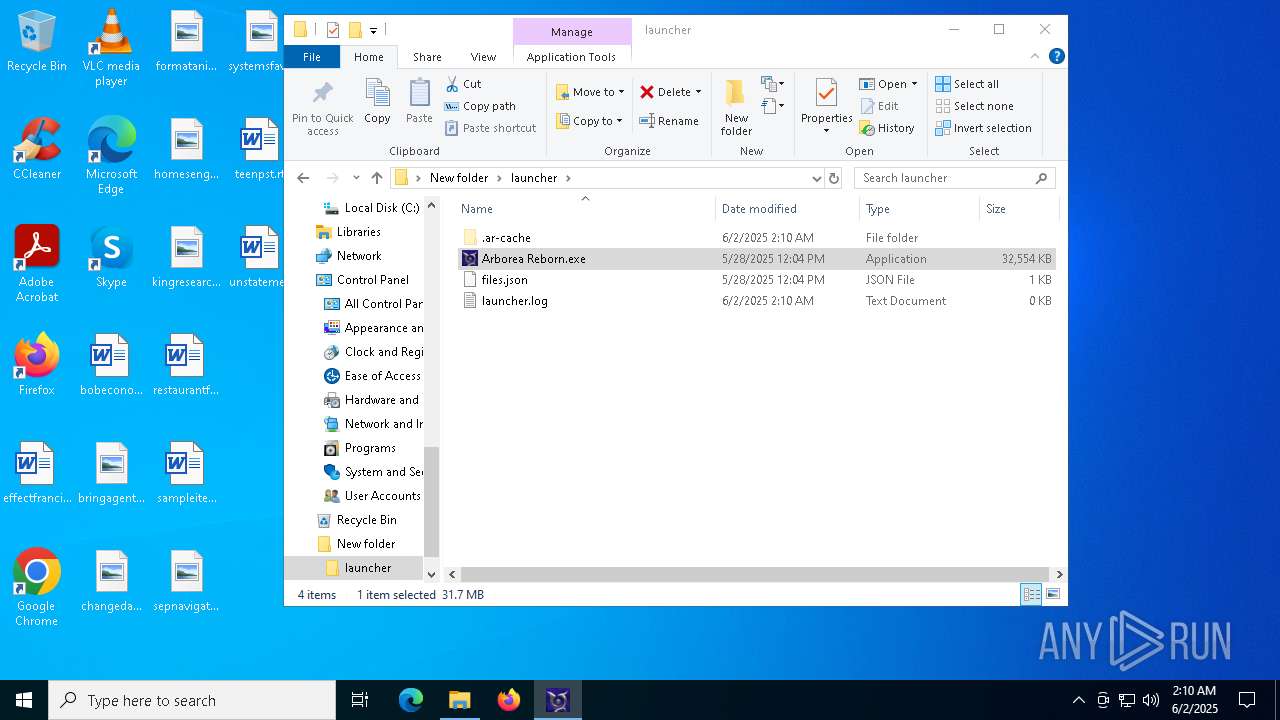
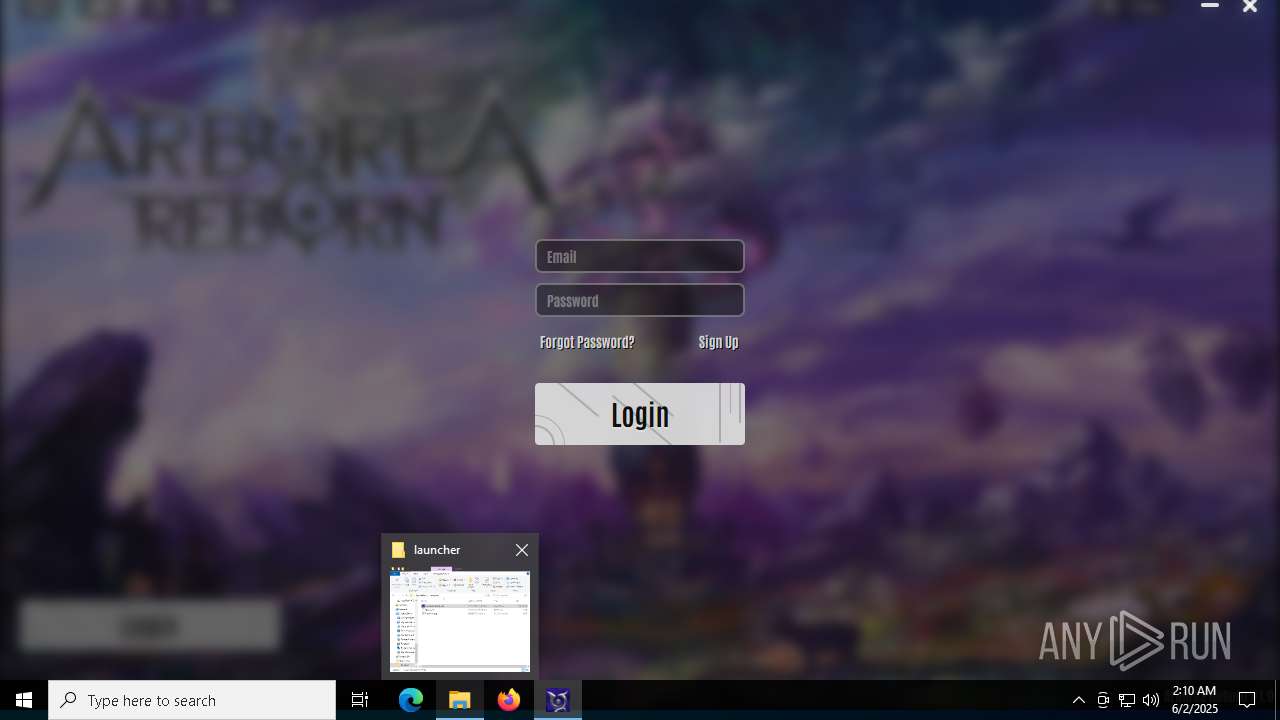
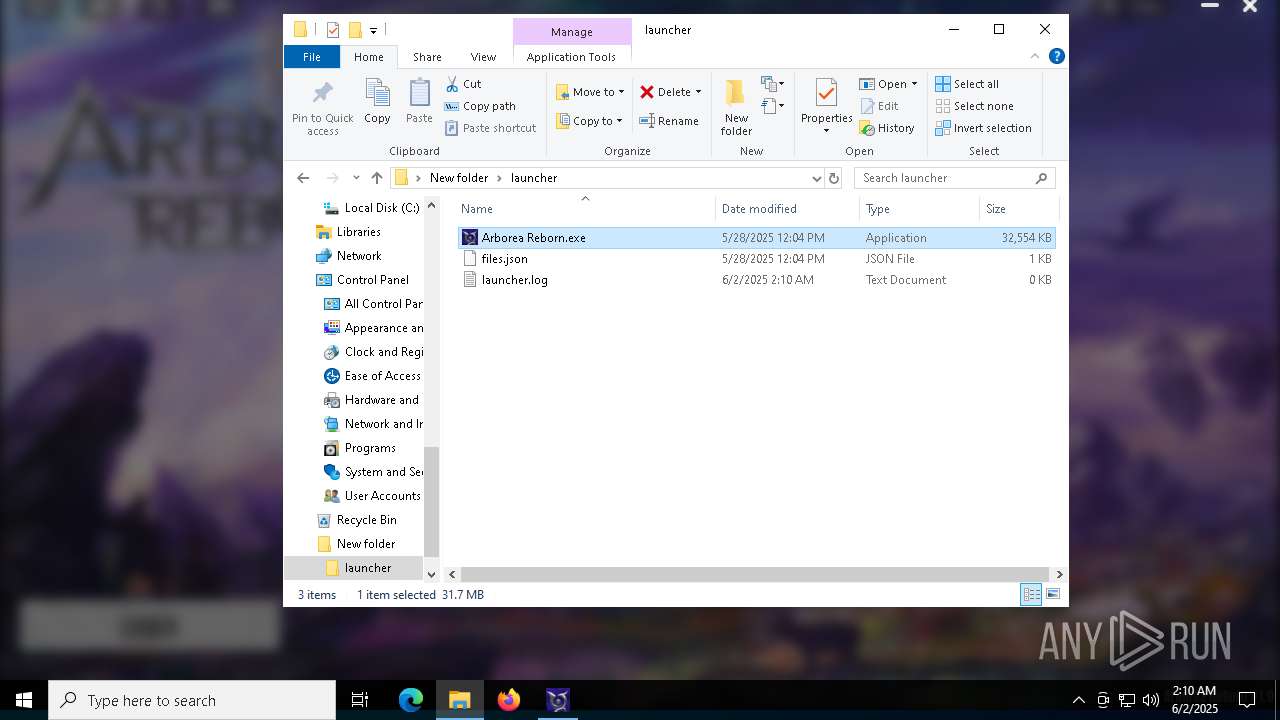
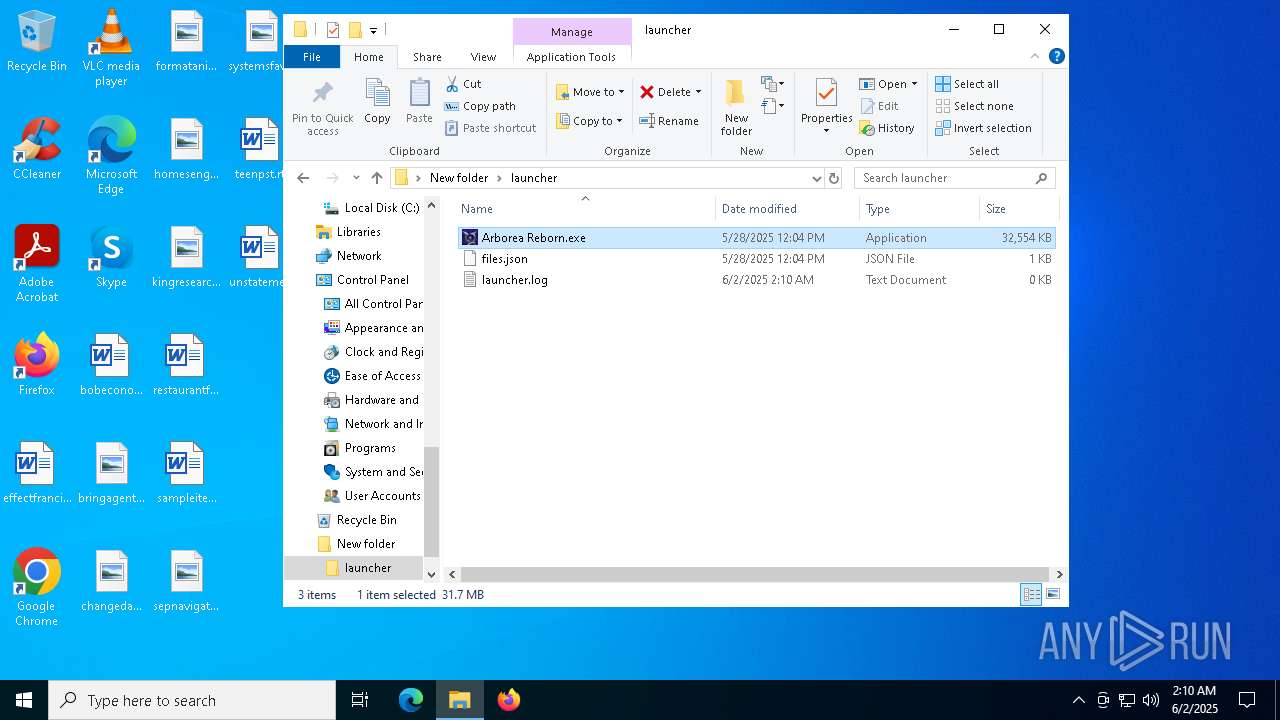
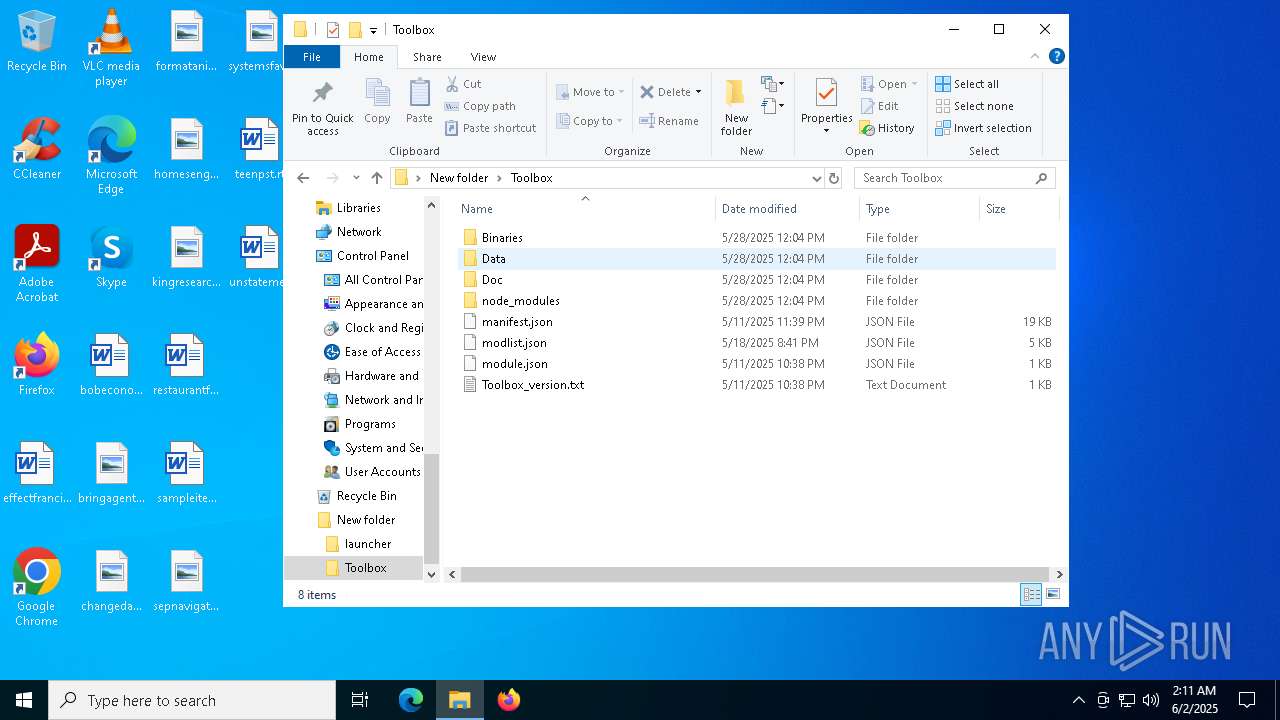
| File name: | ArboreaReborn_Launcher.zip |
| Full analysis: | https://app.any.run/tasks/2011196d-aa2e-4420-8b99-9dc545f65b1e |
| Verdict: | Malicious activity |
| Analysis date: | June 02, 2025, 02:08:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | A8B99CE209A25C0ECED03CAA735E5D20 |
| SHA1: | 9A9D32AC48F1E2CFCA095A66ECEFF25FE13D1C2E |
| SHA256: | D8A7A2F5C0584E5CD5E3C541E4285BE77E6ADBC98297952C8B4C55AEFDCAB4B5 |
| SSDEEP: | 1572864:9EcErwMj/A8YrygMjj1XkJsFYcSiZMyvd92aO0wn:9EcEU6YGgMjj10JsFYcTJvd92Cwn |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2616)
Changes the autorun value in the registry
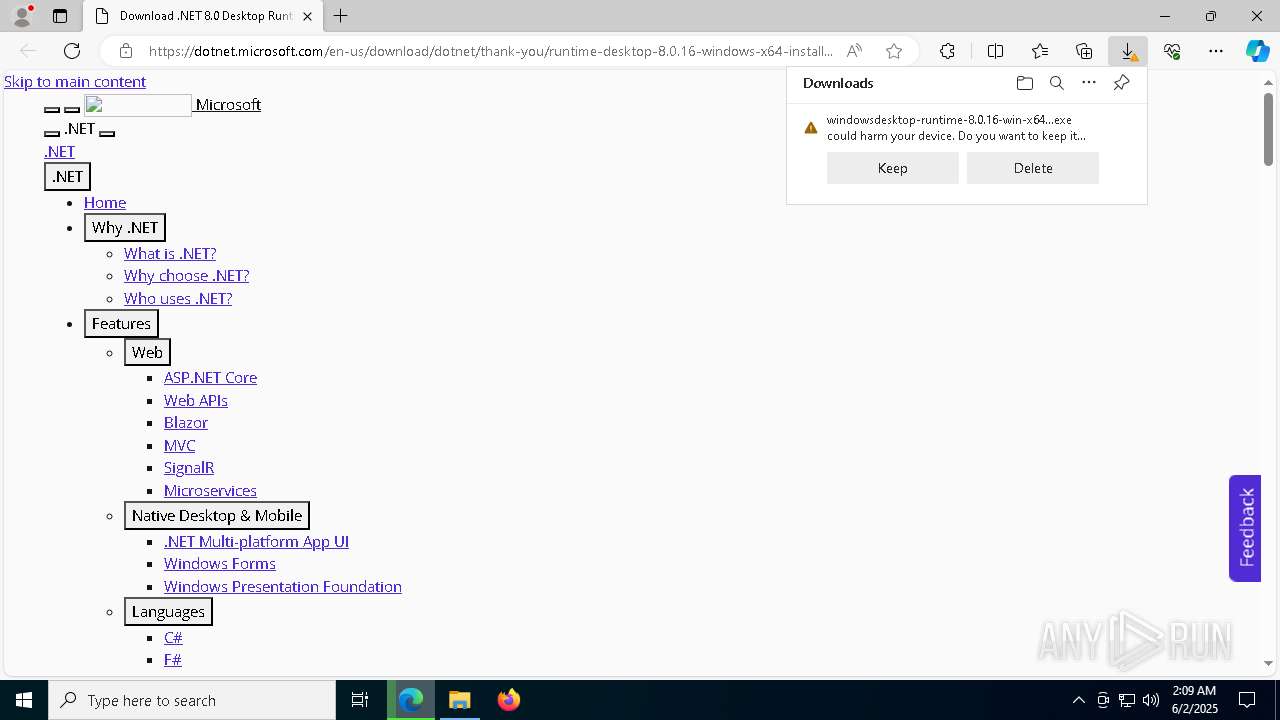
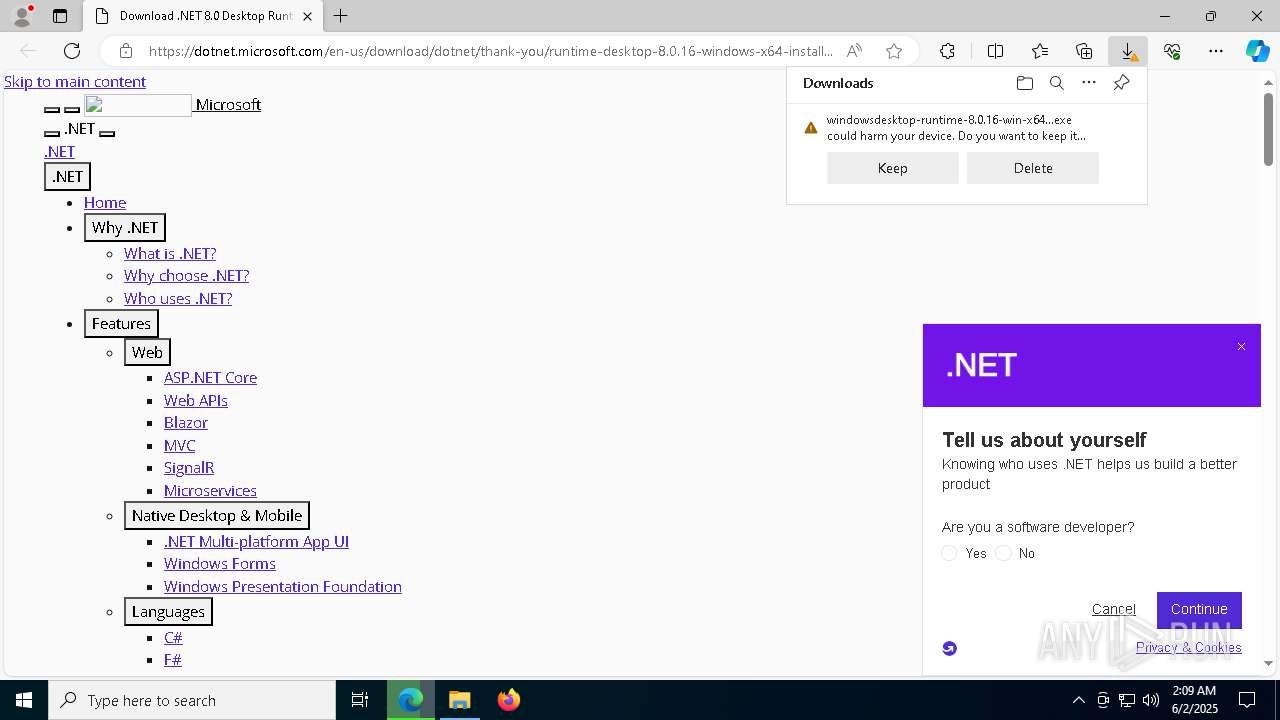
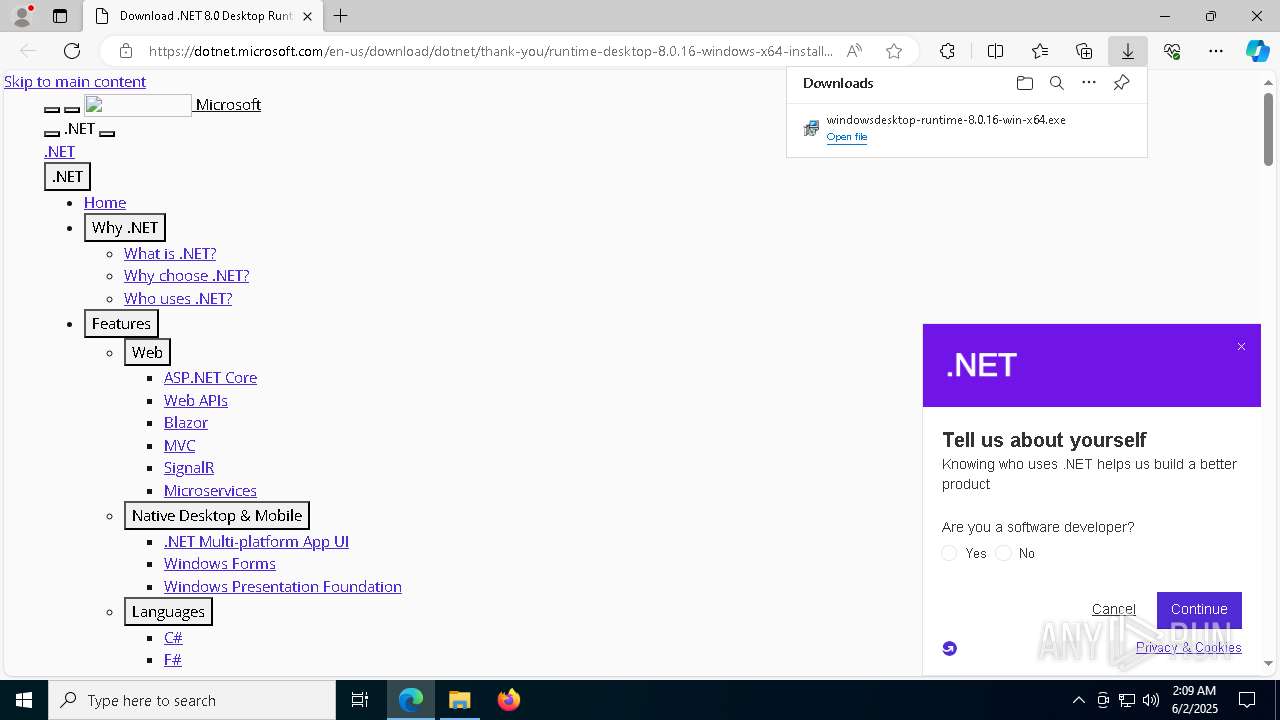
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2616)
- Arborea Reborn.exe (PID: 6840)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 872)
Process drops legitimate windows executable
- WinRAR.exe (PID: 2616)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 872)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7320)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
- msiexec.exe (PID: 6384)
- Arborea Reborn.exe (PID: 872)
Executable content was dropped or overwritten
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 872)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7320)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
- Arborea Reborn.exe (PID: 872)
Searches for installed software
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 872)
Starts a Microsoft application from unusual location
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 872)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6384)
Starts itself from another location
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 872)
Creates a software uninstall entry
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
The process drops C-runtime libraries
- msiexec.exe (PID: 6384)
The process creates files with name similar to system file names
- msiexec.exe (PID: 6384)
Application launched itself
- electron.exe (PID: 8184)
Starts CMD.EXE for commands execution
- electron.exe (PID: 8184)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 2616)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 872)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7320)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
- msiexec.exe (PID: 6384)
- Arborea Reborn.exe (PID: 872)
Reads the computer name
- Arborea Reborn.exe (PID: 6840)
- identity_helper.exe (PID: 6676)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 872)
- msiexec.exe (PID: 6384)
- msiexec.exe (PID: 6060)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
- msiexec.exe (PID: 6644)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2616)
- msedge.exe (PID: 7292)
- msiexec.exe (PID: 6384)
Manual execution by a user
- Arborea Reborn.exe (PID: 6840)
- Arborea Reborn.exe (PID: 872)
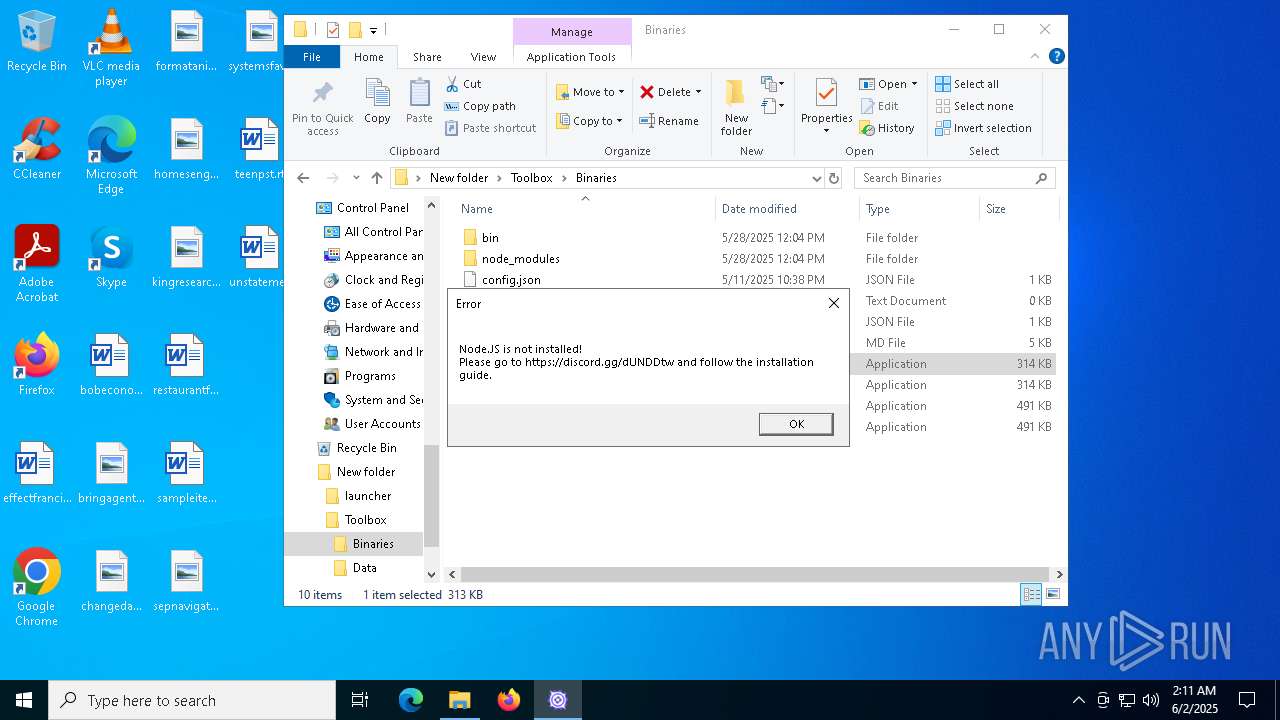
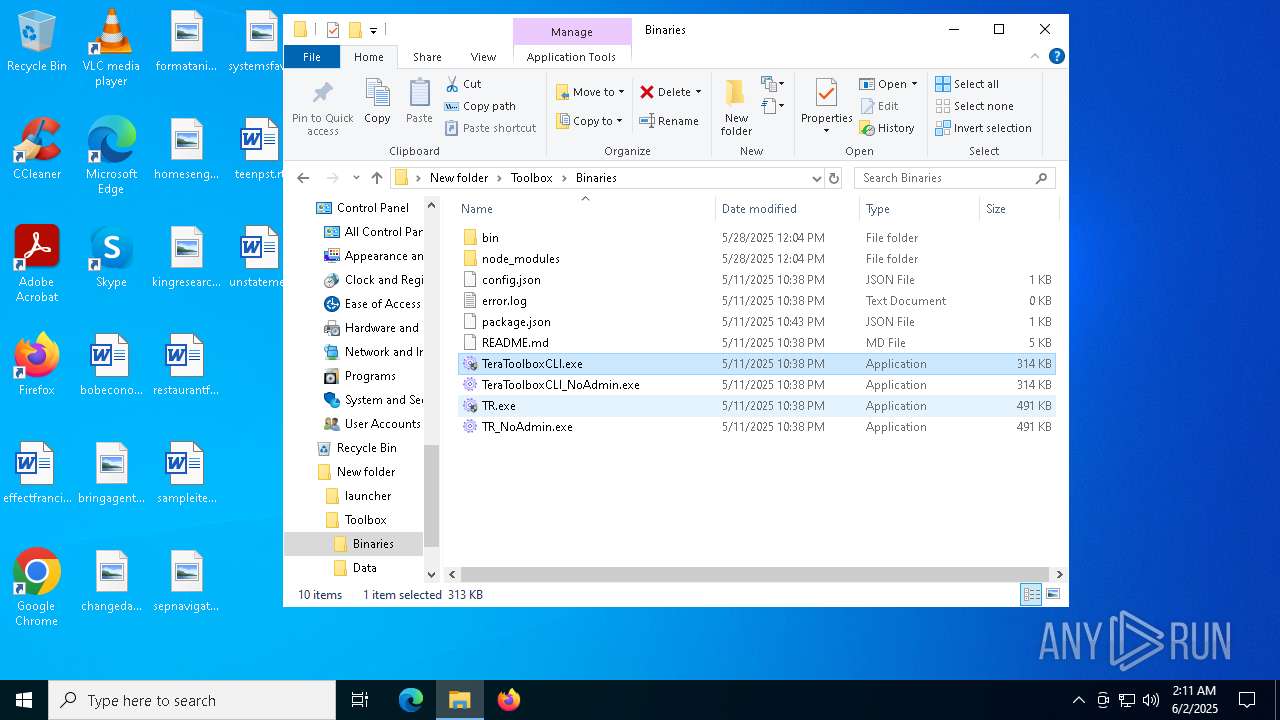
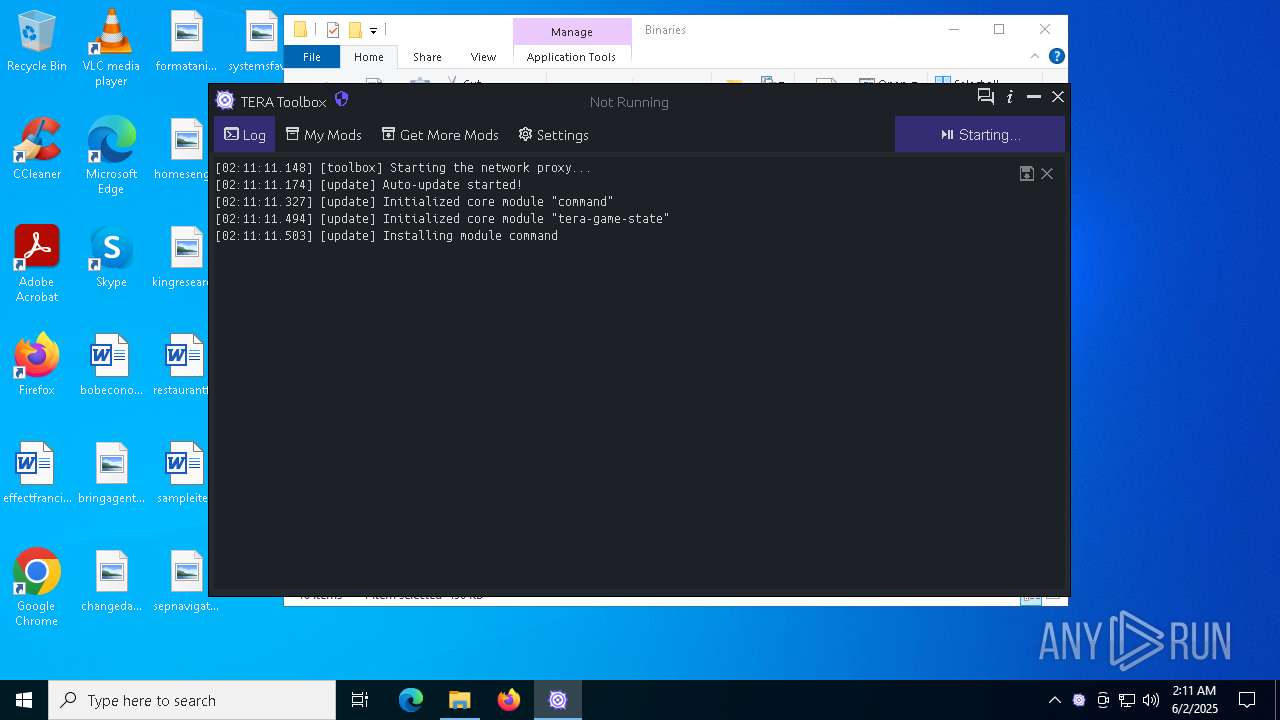
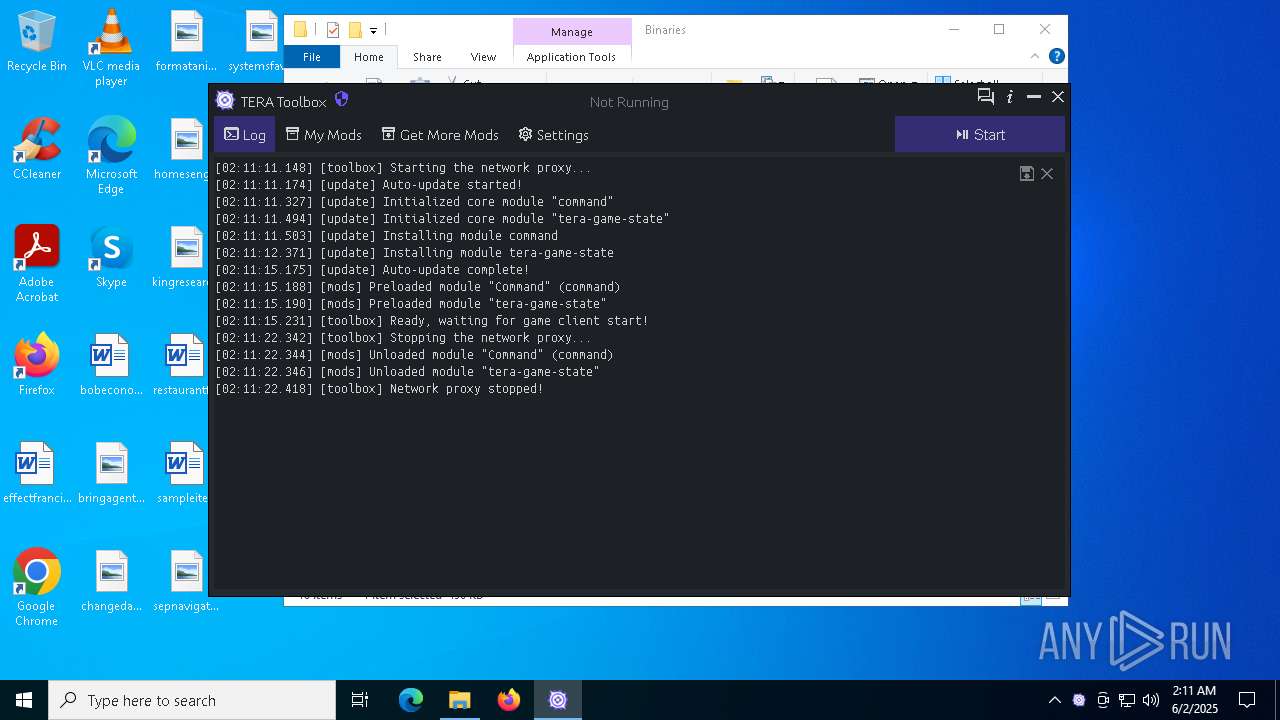
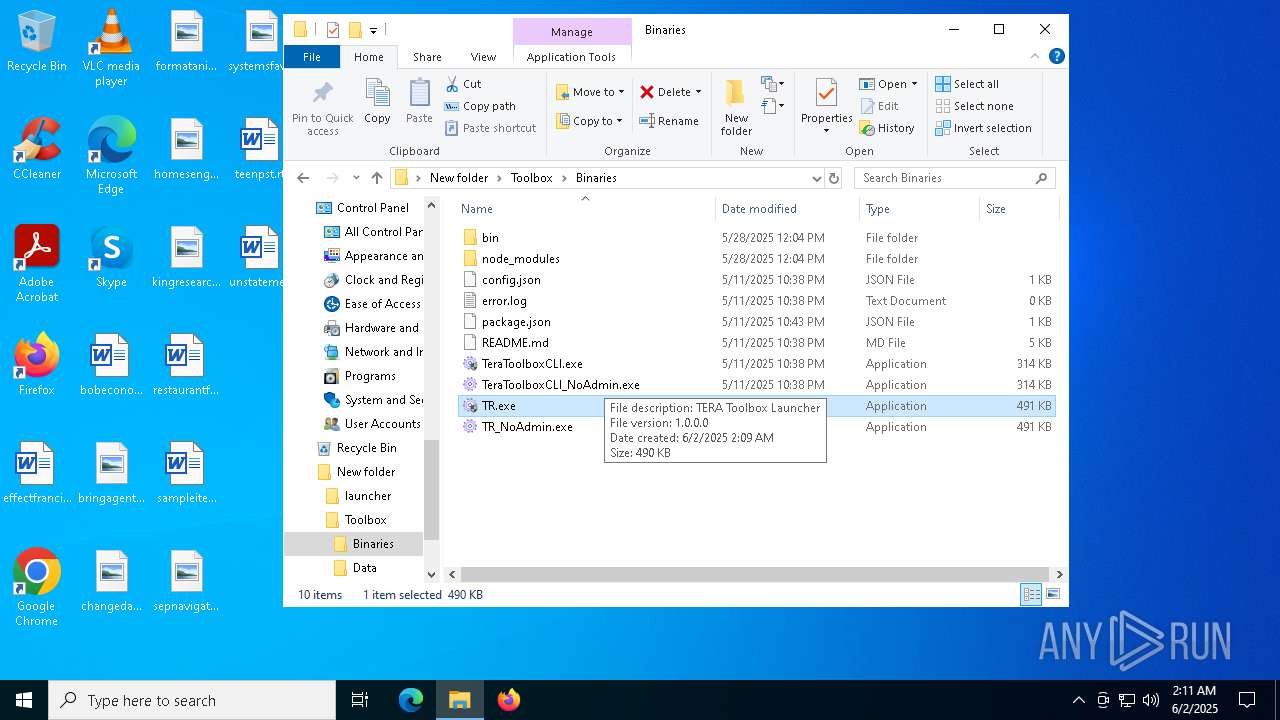
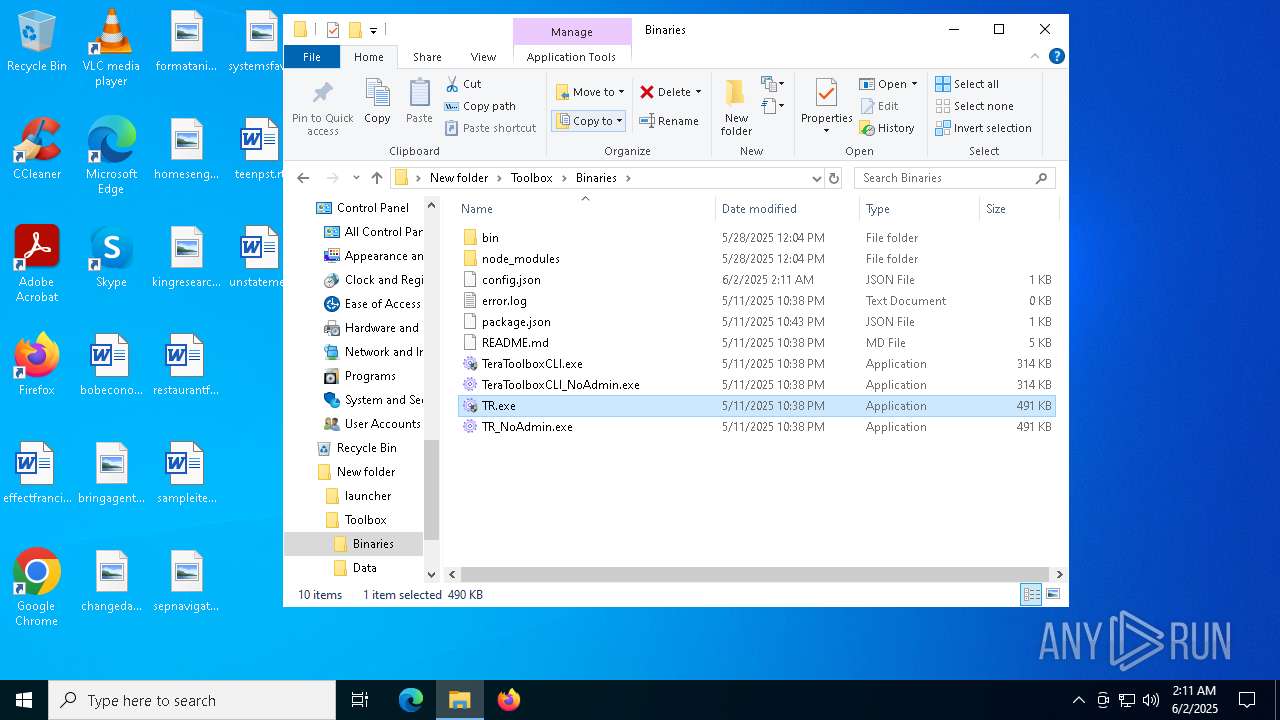
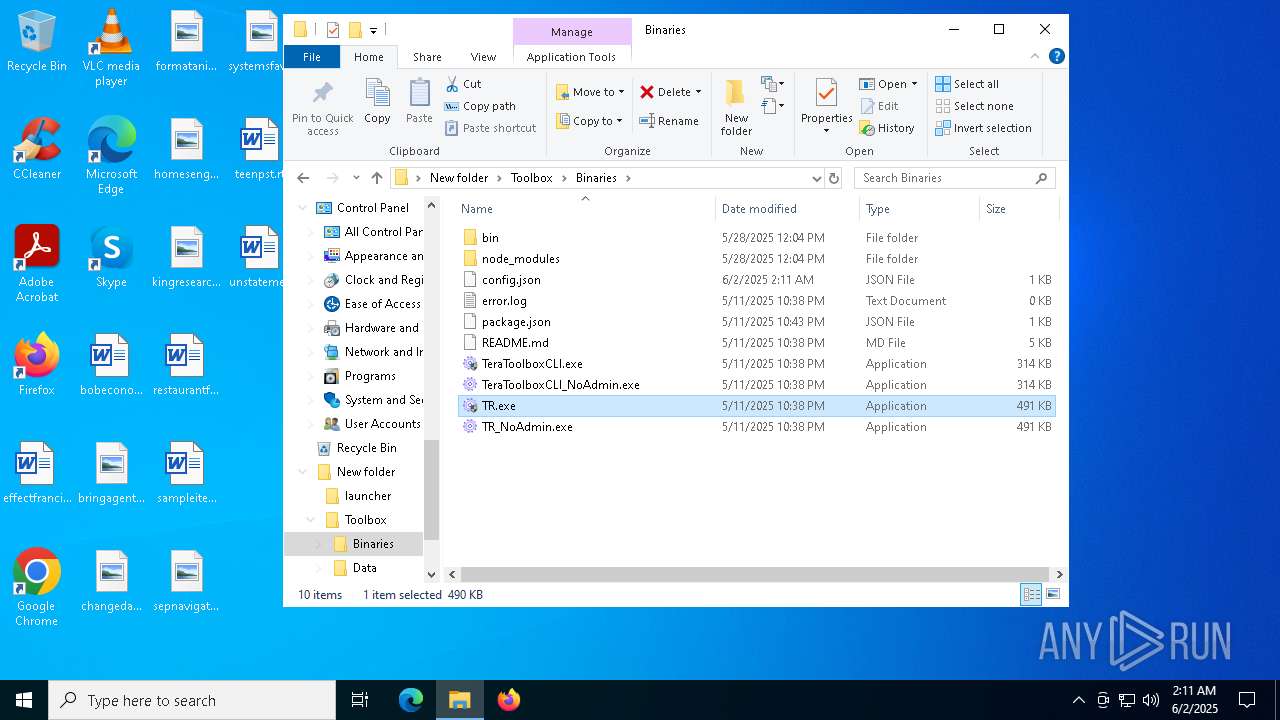
- TeraToolboxCLI.exe (PID: 6300)
- TeraToolboxCLI.exe (PID: 7752)
- TR.exe (PID: 6464)
- TR.exe (PID: 5332)
Checks supported languages
- Arborea Reborn.exe (PID: 6840)
- identity_helper.exe (PID: 6676)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 872)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7320)
- msiexec.exe (PID: 6384)
- msiexec.exe (PID: 6060)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
- msiexec.exe (PID: 6644)
Application launched itself
- msedge.exe (PID: 7292)
- msedge.exe (PID: 5072)
Create files in a temporary directory
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 872)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7320)
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
Process checks computer location settings
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 872)
Reads Environment values
- identity_helper.exe (PID: 6676)
Creates files in the program directory
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
Launch of the file from Registry key
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
Reads the machine GUID from the registry
- windowsdesktop-runtime-8.0.16-win-x64.exe (PID: 7544)
- msiexec.exe (PID: 6384)
Reads the software policy settings
- msiexec.exe (PID: 6384)
Creates a software uninstall entry
- msiexec.exe (PID: 6384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:28 12:04:30 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
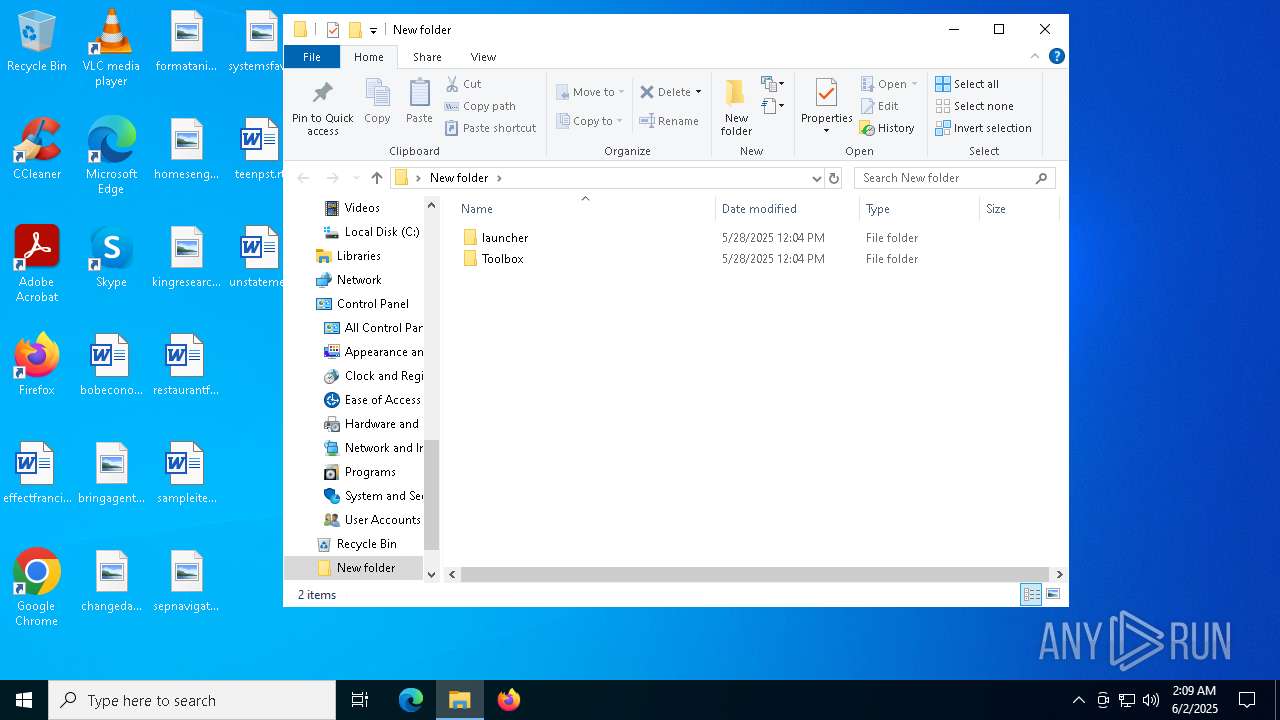
| ZipFileName: | launcher/ |
Total processes
208
Monitored processes
79
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 656 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5788 --field-trial-handle=2336,i,8163630410439165594,339357653131616177,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 872 | "C:\Users\admin\AppData\Local\Temp\{CE22AF7F-6322-474A-A134-9CD98ACF2C5D}\.cr\windowsdesktop-runtime-8.0.16-win-x64.exe" -burn.clean.room="C:\Users\admin\Downloads\windowsdesktop-runtime-8.0.16-win-x64.exe" -burn.filehandle.attached=576 -burn.filehandle.self=584 | C:\Users\admin\AppData\Local\Temp\{CE22AF7F-6322-474A-A134-9CD98ACF2C5D}\.cr\windowsdesktop-runtime-8.0.16-win-x64.exe | windowsdesktop-runtime-8.0.16-win-x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Desktop Runtime - 8.0.16 (x64) Exit code: 0 Version: 8.0.16.34817 Modules
| |||||||||||||||
| 872 | "C:\Users\admin\Desktop\New folder\launcher\Arborea Reborn.exe" | C:\Users\admin\Desktop\New folder\launcher\Arborea Reborn.exe | explorer.exe | ||||||||||||
User: admin Company: Arborea Reborn Integrity Level: MEDIUM Description: Arborea Reborn Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 896 | "C:\Users\admin\Desktop\New folder\Toolbox\Binaries\node_modules\electron\dist\electron.exe" --type=renderer --autoplay-policy=no-user-gesture-required --js-flags=--use-strict --field-trial-handle=1612,4228171128583667842,1449240391158582893,131072 --enable-features=WebComponentsV0Enabled --disable-features=CookiesWithoutSameSiteMustBeSecure,SameSiteByDefaultCookies,SpareRendererForSitePerProcess --disable-gpu-compositing --lang=en-US --app-path="C:\Users\admin\Desktop\New folder\Toolbox\Binaries\bin" --node-integration --no-sandbox --no-zygote --enable-remote-module --background-color=#292F33 --enable-websql --disable-electron-site-instance-overrides --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2336 /prefetch:1 | C:\Users\admin\Desktop\New folder\Toolbox\Binaries\node_modules\electron\dist\electron.exe | — | electron.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: HIGH Description: Electron Exit code: 0 Version: 11.0.5 Modules
| |||||||||||||||
| 1056 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2584 --field-trial-handle=2388,i,11952814265321236773,3677741760789427999,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1072 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=6116 --field-trial-handle=2336,i,8163630410439165594,339357653131616177,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1132 | "C:\Users\admin\Desktop\New folder\Toolbox\Binaries\node_modules\electron\dist\electron.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1612,4228171128583667842,1449240391158582893,131072 --enable-features=WebComponentsV0Enabled --disable-features=CookiesWithoutSameSiteMustBeSecure,SameSiteByDefaultCookies,SpareRendererForSitePerProcess --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=2100 /prefetch:8 | C:\Users\admin\Desktop\New folder\Toolbox\Binaries\node_modules\electron\dist\electron.exe | — | electron.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: HIGH Description: Electron Exit code: 0 Version: 11.0.5 Modules
| |||||||||||||||
| 1324 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5216 --field-trial-handle=2336,i,8163630410439165594,339357653131616177,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1324 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=7148 --field-trial-handle=2336,i,8163630410439165594,339357653131616177,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1532 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5968 --field-trial-handle=2336,i,8163630410439165594,339357653131616177,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
27 580
Read events
26 576
Write events
929
Delete events
75
Modification events
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\ArboreaReborn_Launcher.zip | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
576
Suspicious files
375
Text files
149
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2616 | WinRAR.exe | C:\Users\admin\Desktop\Toolbox\Binaries\node_modules\electron\dist\resources.pak | — | |
MD5:— | SHA256:— | |||
| 2616 | WinRAR.exe | C:\Users\admin\Desktop\launcher\Arborea Reborn.exe | executable | |
MD5:8D1C5071FDBD7D3381AD0BDAA004430A | SHA256:B8CDE0F79ED548789C13632DBEE7DAF98076E5019501C5D46683CC7D8F91B86C | |||
| 2616 | WinRAR.exe | C:\Users\admin\Desktop\Toolbox\manifest.json | binary | |
MD5:16FF1CCA9A97BCE15B33960B67F20AED | SHA256:8720A2F71555573E2727CF1223F86DCB7D7B50A665B8B641B4E5B1F0DCE806B0 | |||
| 2616 | WinRAR.exe | C:\Users\admin\Desktop\Toolbox\Binaries\node_modules\electron\dist\libGLESv2.dll | executable | |
MD5:6F5B040D68C6BC64A0A38C9F4A7C591E | SHA256:AAE63351E5B4C9865748F7BBC59B1B12DA5C1CA764189FC703E69B3F1B19352C | |||
| 2616 | WinRAR.exe | C:\Users\admin\Desktop\Toolbox\Binaries\README.md | text | |
MD5:29A8EE84BE2554E724945AD2307EF1AE | SHA256:1055EF89CFE60ED82DB72CCFF7185929EB1F25173F877FD4B97EC289D18E5AFE | |||
| 2616 | WinRAR.exe | C:\Users\admin\Desktop\Toolbox\Binaries\TeraToolboxCLI_NoAdmin.exe | executable | |
MD5:20EE79A2091657F2FE57D02A37BF9AF8 | SHA256:E4E9306F858B1AFB4A3A21DACDCB38DC0F33F8AE6DCCAAF106F3860FCACA0AC7 | |||
| 2616 | WinRAR.exe | C:\Users\admin\Desktop\Toolbox\Binaries\TeraToolboxCLI.exe | executable | |
MD5:970EBE0C8BDA615F4812F82D36DE6467 | SHA256:AF4DD88CE3913BB595DDA072282CAC98E65075D576C8E68F3A42270C56EF74EB | |||
| 2616 | WinRAR.exe | C:\Users\admin\Desktop\Toolbox\Binaries\package.json | binary | |
MD5:BDEB898781794A54F53AB97E9FFA8C3D | SHA256:8BC2FEE8538908FFC319367E89A321A25D3DEE05A7527042401397DA706B363D | |||
| 2616 | WinRAR.exe | C:\Users\admin\Desktop\Toolbox\Binaries\node_modules\electron\dist\v8_context_snapshot.bin | binary | |
MD5:AE1C494F86526C45DA8F1446159080D9 | SHA256:59170B40E9ACAE9F4A524F6F5E690ADAE82B8AE2F90549D8E3339F8567CFADBC | |||
| 2616 | WinRAR.exe | C:\Users\admin\Desktop\Toolbox\Binaries\node_modules\electron\dist\version | text | |
MD5:87C24A1392D29DCB67BB2BE6A1407878 | SHA256:8A31D3814648C715A8CCE0F8A437D7E9D9FC556E445098FBF78F796E171EEB89 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
67
DNS requests
81
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3192 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3192 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7292 | msedge.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7292 | msedge.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
8076 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5496 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |