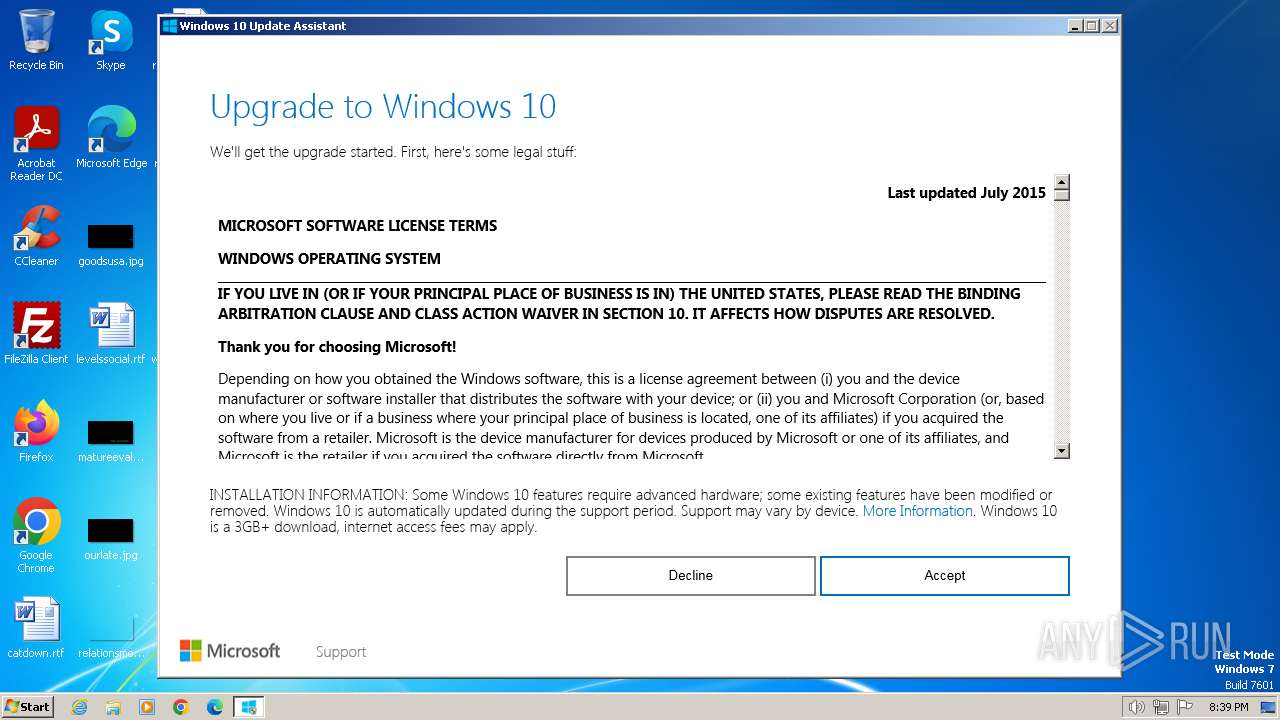
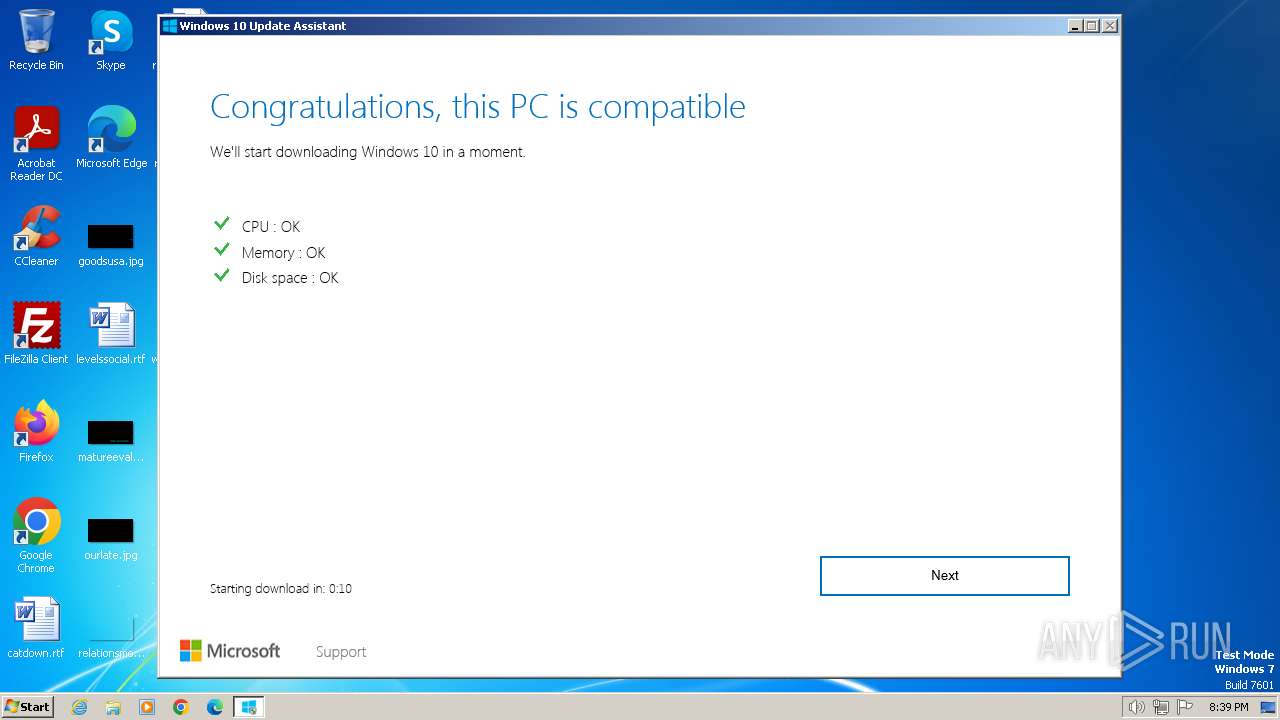
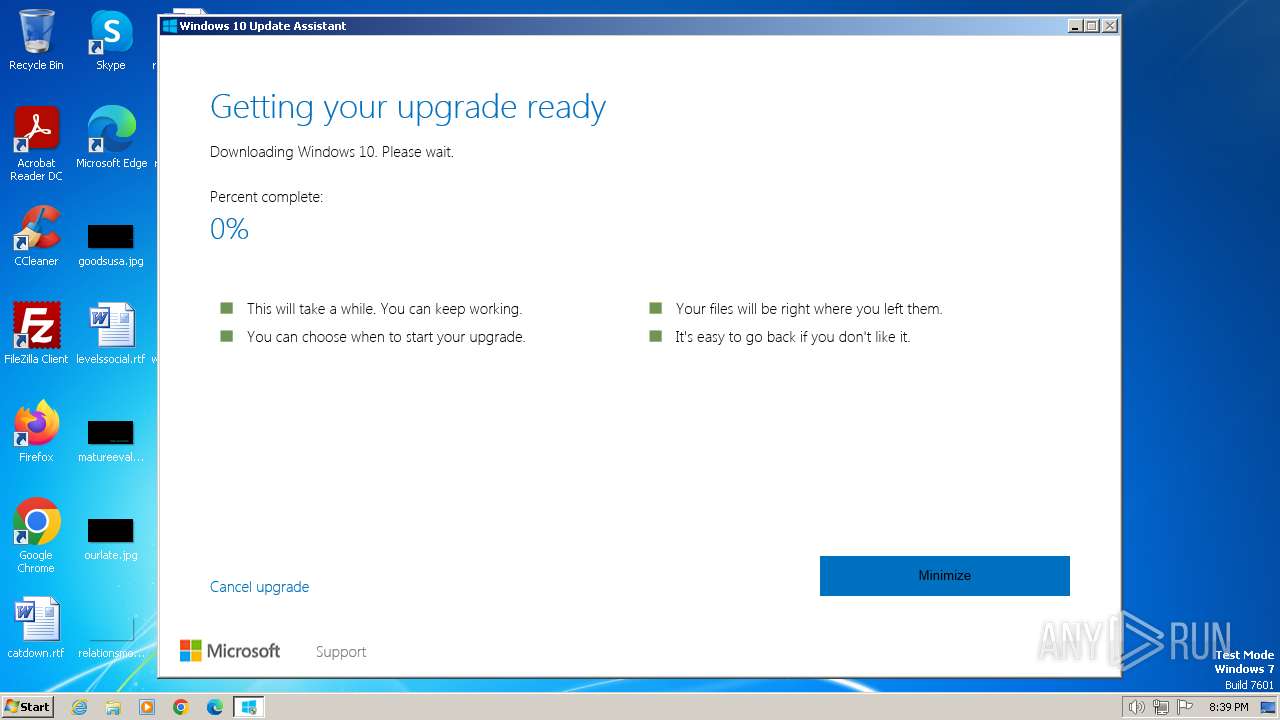
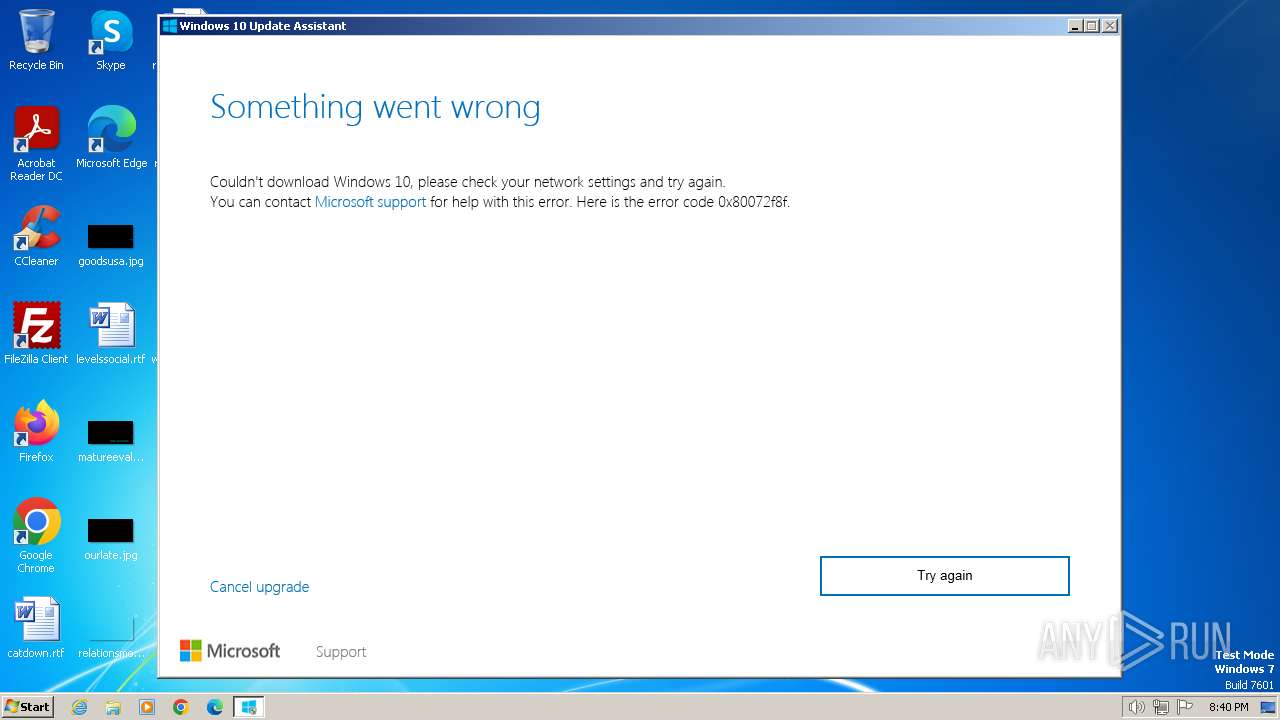
| File name: | windows10 yeah.exe |
| Full analysis: | https://app.any.run/tasks/03e1eaec-1dab-406e-927e-7f65376a0fc4 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2024, 20:37:49 |
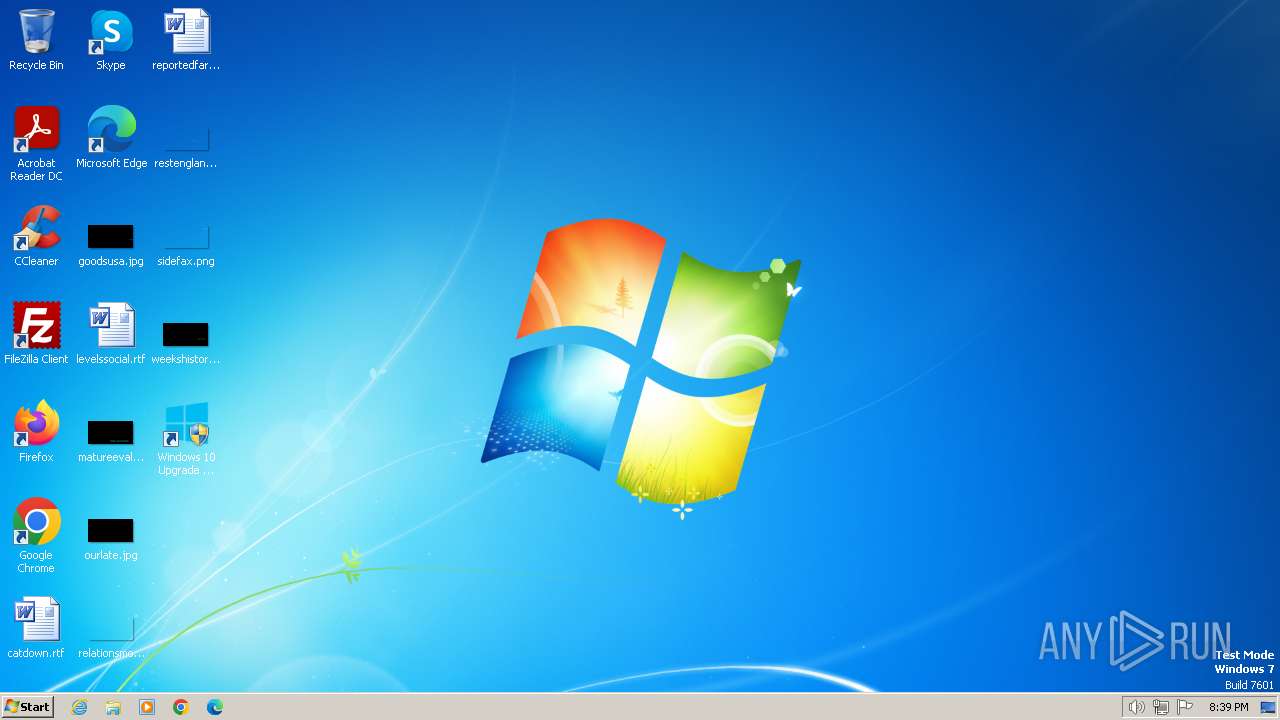
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 59658313B7C7543372B8A40CA8967F58 |
| SHA1: | 2ED1EA40DCBB758FD10D7086642C4FB44EFA6259 |
| SHA256: | D8850528001E6DD8E19E141BB2322C2D144C524759612AEABE2F116A9C49519F |
| SSDEEP: | 98304:o+QF3unYLN996U4Eu0YjO7l03JMjLxUFDz8B3rXoxsFIFQH9OZFj1EAWC5hKCL1F:l1jvn70ggOnTdt/Ag |
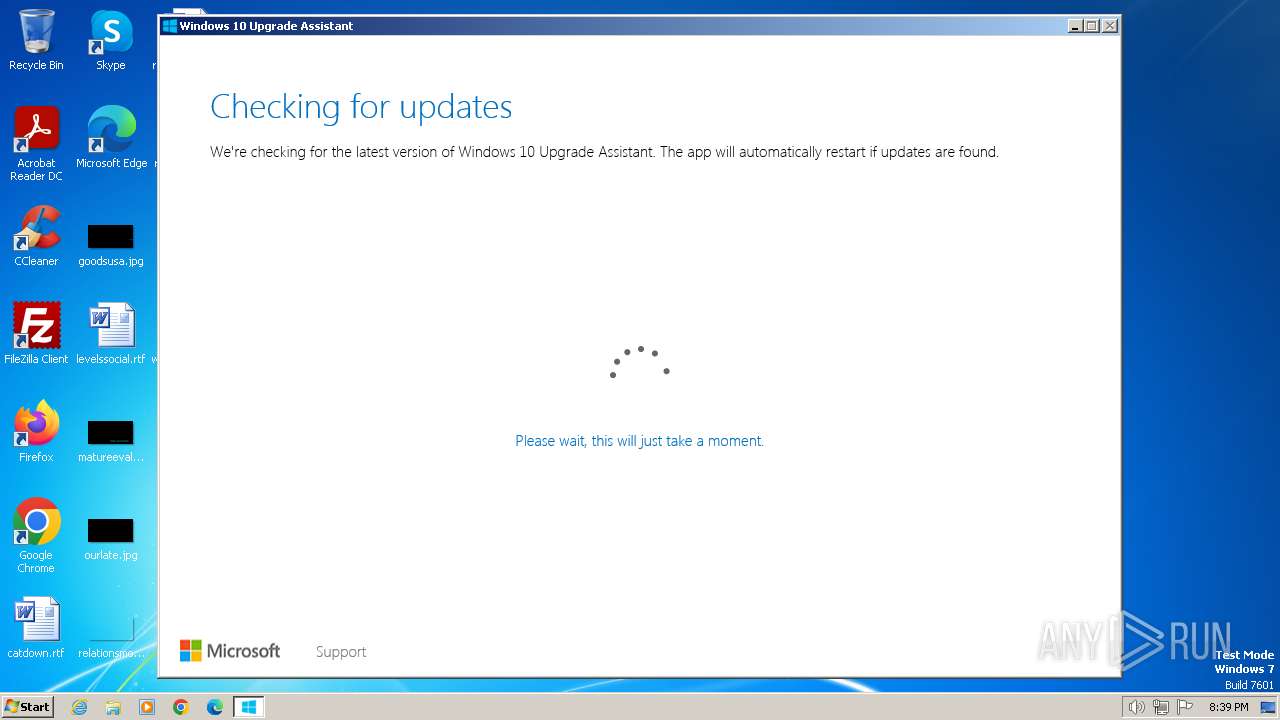
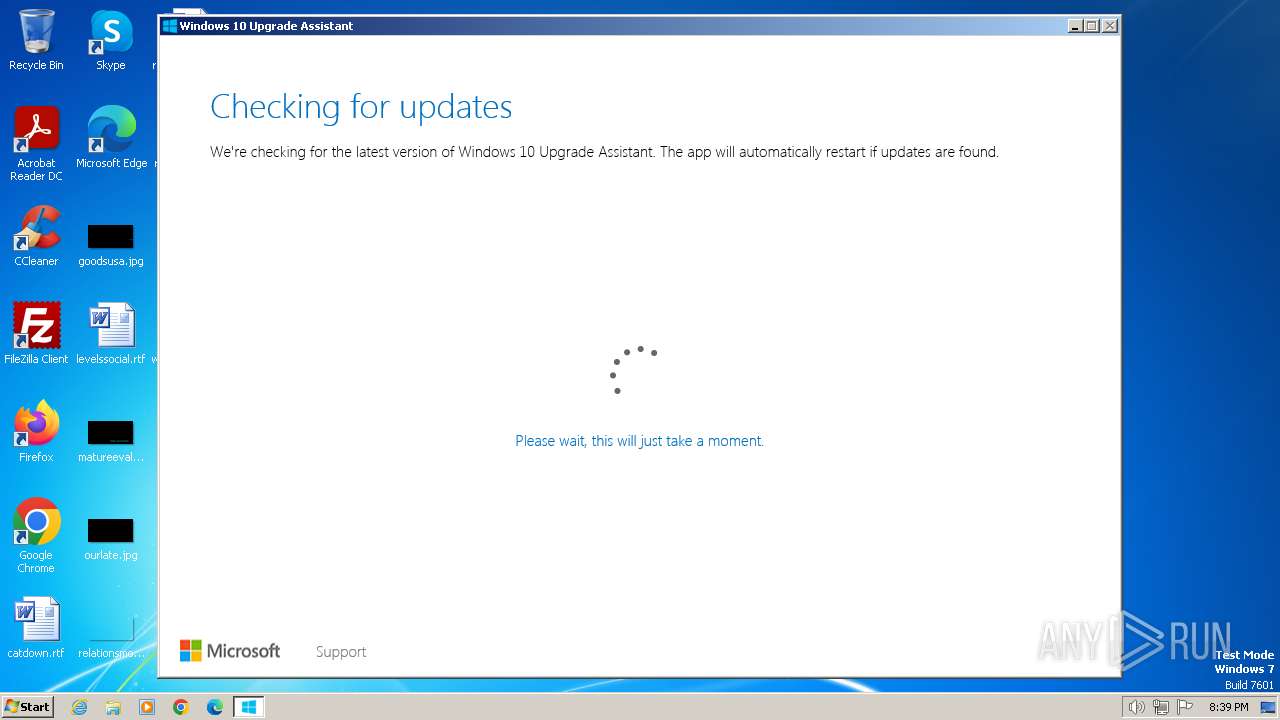
MALICIOUS
Drops the executable file immediately after the start
- windows10 yeah.exe (PID: 2208)
- Windows10UpgraderApp.exe (PID: 2016)
- Windows10Upgrade.exe (PID: 2724)
SUSPICIOUS
Process drops legitimate windows executable
- windows10 yeah.exe (PID: 2208)
- Windows10UpgraderApp.exe (PID: 2016)
- Windows10Upgrade.exe (PID: 2724)
The process creates files with name similar to system file names
- windows10 yeah.exe (PID: 2208)
- Windows10Upgrade.exe (PID: 2724)
Reads the Internet Settings
- windows10 yeah.exe (PID: 2208)
- Windows10UpgraderApp.exe (PID: 2016)
- control.exe (PID: 2712)
- Windows10Upgrade.exe (PID: 2724)
- Windows10UpgraderApp.exe (PID: 2596)
Drops a system driver (possible attempt to evade defenses)
- windows10 yeah.exe (PID: 2208)
- Windows10Upgrade.exe (PID: 2724)
Executable content was dropped or overwritten
- windows10 yeah.exe (PID: 2208)
- Windows10UpgraderApp.exe (PID: 2016)
- Windows10Upgrade.exe (PID: 2724)
Reads Microsoft Outlook installation path
- Windows10UpgraderApp.exe (PID: 2016)
- Windows10UpgraderApp.exe (PID: 2596)
Reads Internet Explorer settings
- Windows10UpgraderApp.exe (PID: 2016)
- Windows10UpgraderApp.exe (PID: 2596)
Reads settings of System Certificates
- Windows10UpgraderApp.exe (PID: 2016)
Reads security settings of Internet Explorer
- Windows10UpgraderApp.exe (PID: 2016)
Checks Windows Trust Settings
- Windows10UpgraderApp.exe (PID: 2016)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 2712)
INFO
Checks supported languages
- windows10 yeah.exe (PID: 2208)
- Windows10UpgraderApp.exe (PID: 2016)
- Windows10Upgrade.exe (PID: 2724)
- Windows10UpgraderApp.exe (PID: 2596)
- HttpHelper.exe (PID: 2836)
- HttpHelper.exe (PID: 3220)
- HttpHelper.exe (PID: 3024)
- HttpHelper.exe (PID: 2752)
- HttpHelper.exe (PID: 2988)
Reads the computer name
- windows10 yeah.exe (PID: 2208)
- Windows10UpgraderApp.exe (PID: 2016)
- Windows10Upgrade.exe (PID: 2724)
- Windows10UpgraderApp.exe (PID: 2596)
- HttpHelper.exe (PID: 2836)
- HttpHelper.exe (PID: 3024)
- HttpHelper.exe (PID: 3220)
- HttpHelper.exe (PID: 2752)
- HttpHelper.exe (PID: 2988)
Create files in a temporary directory
- windows10 yeah.exe (PID: 2208)
- Windows10UpgraderApp.exe (PID: 2016)
- Windows10Upgrade.exe (PID: 2724)
- Windows10UpgraderApp.exe (PID: 2596)
Creates files in the program directory
- windows10 yeah.exe (PID: 2208)
Reads the machine GUID from the registry
- Windows10UpgraderApp.exe (PID: 2016)
- Windows10UpgraderApp.exe (PID: 2596)
Checks proxy server information
- Windows10UpgraderApp.exe (PID: 2016)
- Windows10UpgraderApp.exe (PID: 2596)
Creates files or folders in the user directory
- Windows10UpgraderApp.exe (PID: 2016)
- Windows10UpgraderApp.exe (PID: 2596)
Manual execution by a user
- control.exe (PID: 2712)
Checks transactions between databases Windows and Oracle
- rundll32.exe (PID: 2572)
Reads the time zone
- rundll32.exe (PID: 2572)
Reads Environment values
- Windows10UpgraderApp.exe (PID: 2596)
Reads CPU info
- Windows10UpgraderApp.exe (PID: 2596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:04:14 20:27:56+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10.1 |
| CodeSize: | 423424 |
| InitializedDataSize: | 159744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4cd92 |
| OSVersion: | 6.2 |
| ImageVersion: | 6.2 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.9200.17387 |
| ProductVersionNumber: | 1.4.9200.17387 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Arabic |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | مساعد ترقية Windows 10 |
| InternalName: | Windows10Upgrader.exe |
| LegalCopyright: | Copyright © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | Windows10Upgrader.exe |
| ProductName: | Windows 10 Upgrade Assistant |
| FileVersion: | 1.4.9200.17387 |
| ProductVersion: | 1.4.9200.17387 |
Total processes
64
Monitored processes
13
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2016 | "C:\Windows10Upgrade\Windows10UpgraderApp.exe" | C:\Windows10Upgrade\Windows10UpgraderApp.exe | windows10 yeah.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows 10 Upgrade Assistant Exit code: 0 Version: 1.4.9200.17387 Modules
| |||||||||||||||
| 2184 | "C:\Users\admin\AppData\Local\Temp\windows10 yeah.exe" | C:\Users\admin\AppData\Local\Temp\windows10 yeah.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows 10 Upgrade Assistant Exit code: 3221226540 Version: 1.4.9200.17387 Modules
| |||||||||||||||
| 2208 | "C:\Users\admin\AppData\Local\Temp\windows10 yeah.exe" | C:\Users\admin\AppData\Local\Temp\windows10 yeah.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows 10 Upgrade Assistant Exit code: 0 Version: 1.4.9200.17387 Modules
| |||||||||||||||
| 2396 | C:\Windows\system32\DllHost.exe /Processid:{9DF523B0-A6C0-4EA9-B5F1-F4565C3AC8B8} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2572 | "C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL "C:\Windows\System32\timedate.cpl", | C:\Windows\System32\rundll32.exe | — | control.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2596 | "C:\Windows10Upgrade\Windows10UpgraderApp.exe" /ClientID Win10China:VNL:URL::<1.4.9200.17387>:<1>:{9EBC4F44-4A64-4C9B-B476-D2AF52ECAD92}:[6.1.7601]:[1] /SkipSelfUpdate | C:\Windows10Upgrade\Windows10UpgraderApp.exe | Windows10Upgrade.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows 10 Update Assistant Exit code: 0 Version: 1.4.9200.22391 Modules
| |||||||||||||||
| 2712 | "C:\Windows\System32\control.exe" "C:\Windows\System32\timedate.cpl", | C:\Windows\System32\control.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2724 | C:\Users\admin\AppData\Local\Temp\Windows10Upgrade.exe /Upgrade /InstallationPath C:\Windows10Upgrade /ClientID Win10China:VNL:URL::<1.4.9200.17387>:<1>:{9EBC4F44-4A64-4C9B-B476-D2AF52ECAD92}:[6.1.7601]:[1] /SkipSelfUpdate | C:\Users\admin\AppData\Local\Temp\Windows10Upgrade.exe | Windows10UpgraderApp.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows 10 Update Assistant Exit code: 0 Version: 1.4.9200.22391 Modules
| |||||||||||||||
| 2752 | HttpHelper.exe "g.bing.com" "/gwx/vanilla?ts=1705264788221&SQM=725447e043824fe48f53fe4eddd9a698&GWX=(null)&WU=f43817de583741b48c80b3a0e3cc1efa&WER=3ade2c424ab949b7b142be9aeea69063&CS=12&OSVersion=6.1.7601&STG=win10Vanilla&ER=Completed&LANG=1033&IT=ButtonClicked&IM=Next&CCR=0&RM=(null)&PTN=e52abfc276bb4908883fca581fdd83f9&EC=(null)&SEC=(null)&SUEC=(null)&SI=4f0e87cac0b54a95b102ad1d8ba296d5&CV=(null)&VER=1.4.9200.22391&MD=1&FLT=URL%3A&UPS=CompatSuccessResult&WUAUI=DefaultUi&WDS=Restored&DJR=false&CT=false" | C:\Windows10Upgrade\HttpHelper.exe | Windows10UpgraderApp.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2836 | HttpHelper.exe "g.bing.com" "/gwx/vanilla?ts=1705264784815&SQM=725447e043824fe48f53fe4eddd9a698&GWX=(null)&WU=f43817de583741b48c80b3a0e3cc1efa&WER=3ade2c424ab949b7b142be9aeea69063&CS=12&OSVersion=6.1.7601&STG=win10Vanilla&ER=Completed&LANG=1033&IT=(null)&IM=(null)&CCR=0&RM=(null)&PTN=e52abfc276bb4908883fca581fdd83f9&EC=(null)&SEC=(null)&SUEC=(null)&SI=4f0e87cac0b54a95b102ad1d8ba296d5&CV=(null)&VER=1.4.9200.22391&MD=1&FLT=URL%3A&UPS=CheckingCompat&WUAUI=DefaultUi&WDS=Restored&DJR=false&CT=false" | C:\Windows10Upgrade\HttpHelper.exe | Windows10UpgraderApp.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
7 955
Read events
7 889
Write events
65
Delete events
1
Modification events
| (PID) Process: | (2208) windows10 yeah.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2208) windows10 yeah.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2208) windows10 yeah.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2208) windows10 yeah.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2016) Windows10UpgraderApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2016) Windows10UpgraderApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2016) Windows10UpgraderApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2016) Windows10UpgraderApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2016) Windows10UpgraderApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2016) Windows10UpgraderApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
110
Suspicious files
27
Text files
302
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2208 | windows10 yeah.exe | C:\Users\admin\AppData\Local\Temp\WXUD6.tmp\cosquery.dll | executable | |
MD5:DAA26E8440AF019ED930721B785E6539 | SHA256:9D884B0D38F3863A10D0312872227551E16FDCAE46B396E2D33B61FE32C0C2B6 | |||
| 2208 | windows10 yeah.exe | C:\Users\admin\AppData\Local\Temp\WXUD6.tmp\Windows10UpgraderApp.exe | executable | |
MD5:A18F8C0F6DAFF278EA170790EF533DFC | SHA256:6D6F5428B8C7A837D5C5CEF1D7D063007C0FB3ED65AC1A31A346E6F55442785F | |||
| 2208 | windows10 yeah.exe | C:\Users\admin\AppData\Local\Temp\WXUD6.tmp\DWDCW20.DLL | executable | |
MD5:A1AB4BE6CF197B17A3AEE88232D145B0 | SHA256:2AEF07A30CBEE796561F0E3FFDA1FF5D2B5667C36AC8351221431467227016F3 | |||
| 2208 | windows10 yeah.exe | C:\Users\admin\AppData\Local\Temp\WXUD6.tmp\DW20.EXE | executable | |
MD5:D155E4362FA5991D822FE1C2A14A14F9 | SHA256:713A105C7AFB9BE33249E7C82A23BBDAB89B7F3FCFBD780C123A683B601DBB5B | |||
| 2208 | windows10 yeah.exe | C:\Users\admin\AppData\Local\Temp\WXUD6.tmp\DevInv.dll | executable | |
MD5:5AE30C5CFDCAAEF1B9CDCBA4401DA1A3 | SHA256:BCA5FCA9EE65CBD52BCEB0CAC370FB3E458CC6162782EBA8A56F4DBE30BA9D0F | |||
| 2208 | windows10 yeah.exe | C:\Users\admin\AppData\Local\Temp\WXUD6.tmp\DWTRIG20.EXE | executable | |
MD5:F3BD7AACACC215E643760CEE335697BA | SHA256:182E1488890BEA7914A28A66D1570F676691396AF37B8319A5689545FCC2918A | |||
| 2208 | windows10 yeah.exe | C:\Users\admin\AppData\Local\Temp\WXUD6.tmp\GetCurrentDeploy.dll | executable | |
MD5:DC0D9F26305B0405986121CC742CDE1F | SHA256:20D5E58003B2A145434B5726DD1EF7158E47241105E125A41CF5496ACEF9B862 | |||
| 2208 | windows10 yeah.exe | C:\Users\admin\AppData\Local\Temp\WXUD6.tmp\EnableWiFiTracing.cmd | text | |
MD5:8350DED6D39DF158E51D6CFBE36FB012 | SHA256:AFF2D40828597FBF482753BEC73CC9FC2714484262258875CC23C7D5A7372CEE | |||
| 2208 | windows10 yeah.exe | C:\Users\admin\AppData\Local\Temp\WXUD6.tmp\appraiserxp.dll | executable | |
MD5:74667719A6143F301B35FE1EA835476E | SHA256:D7CCC62B700E96F4AA19EE4DF1B0D2FCBD189932883D0421DEB8875D2D46A1F3 | |||
| 2208 | windows10 yeah.exe | C:\Users\admin\AppData\Local\Temp\WXUD6.tmp\windlp.dll | executable | |
MD5:9C9E2D4EDFFCFDAD28E26E1AB350A635 | SHA256:E5C3E583E9DF016DBA75A3AFCF09250C81B82B682C71DFC501CF9199CDAB83A3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
24
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2016 | Windows10UpgraderApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
2016 | Windows10UpgraderApp.exe | GET | 200 | 2.16.2.89:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6351a6659d3fd473 | unknown | compressed | 4.66 Kb | unknown |
2016 | Windows10UpgraderApp.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/DigiCertGlobalRootG2.crl | unknown | binary | 1.14 Kb | unknown |
2016 | Windows10UpgraderApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | unknown | binary | 471 b | unknown |
2836 | HttpHelper.exe | GET | 204 | 13.107.21.200:80 | http://g.bing.com/gwx/vanilla?ts=1705264784815&SQM=725447e043824fe48f53fe4eddd9a698&GWX=(null)&WU=f43817de583741b48c80b3a0e3cc1efa&WER=3ade2c424ab949b7b142be9aeea69063&CS=12&OSVersion=6.1.7601&STG=win10Vanilla&ER=Completed&LANG=1033&IT=(null)&IM=(null)&CCR=0&RM=(null)&PTN=e52abfc276bb4908883fca581fdd83f9&EC=(null)&SEC=(null)&SUEC=(null)&SI=4f0e87cac0b54a95b102ad1d8ba296d5&CV=(null)&VER=1.4.9200.22391&MD=1&FLT=URL%3A&UPS=CheckingCompat&WUAUI=DefaultUi&WDS=Restored&DJR=false&CT=false | unknown | — | — | unknown |
3024 | HttpHelper.exe | GET | 204 | 13.107.21.200:80 | http://g.bing.com/gwx/vanilla?ts=1705264785502&SQM=725447e043824fe48f53fe4eddd9a698&GWX=(null)&WU=f43817de583741b48c80b3a0e3cc1efa&WER=3ade2c424ab949b7b142be9aeea69063&CS=12&OSVersion=6.1.7601&STG=win10Vanilla&ER=Completed&LANG=1033&IT=(null)&IM=(null)&CCR=0&RM=(null)&PTN=e52abfc276bb4908883fca581fdd83f9&EC=(null)&SEC=(null)&SUEC=(null)&SI=4f0e87cac0b54a95b102ad1d8ba296d5&CV=(null)&VER=1.4.9200.22391&MD=1&FLT=URL%3A&UPS=CompatSuccessResult&WUAUI=DefaultUi&WDS=Restored&DJR=false&CT=false | unknown | — | — | unknown |
3220 | HttpHelper.exe | GET | 204 | 13.107.21.200:80 | http://g.bing.com/gwx/vanilla?ts=1705264788237&SQM=725447e043824fe48f53fe4eddd9a698&GWX=(null)&WU=f43817de583741b48c80b3a0e3cc1efa&WER=3ade2c424ab949b7b142be9aeea69063&CS=12&OSVersion=6.1.7601&STG=win10Vanilla&ER=Completed&LANG=1033&IT=(null)&IM=(null)&CCR=0&RM=(null)&PTN=e52abfc276bb4908883fca581fdd83f9&EC=(null)&SEC=(null)&SUEC=(null)&SI=4f0e87cac0b54a95b102ad1d8ba296d5&CV=(null)&VER=1.4.9200.22391&MD=1&FLT=URL%3A&UPS=Downloading&WUAUI=DefaultUi&WDS=Restored&DJR=false&CT=false | unknown | — | — | unknown |
2752 | HttpHelper.exe | GET | 204 | 13.107.21.200:80 | http://g.bing.com/gwx/vanilla?ts=1705264788221&SQM=725447e043824fe48f53fe4eddd9a698&GWX=(null)&WU=f43817de583741b48c80b3a0e3cc1efa&WER=3ade2c424ab949b7b142be9aeea69063&CS=12&OSVersion=6.1.7601&STG=win10Vanilla&ER=Completed&LANG=1033&IT=ButtonClicked&IM=Next&CCR=0&RM=(null)&PTN=e52abfc276bb4908883fca581fdd83f9&EC=(null)&SEC=(null)&SUEC=(null)&SI=4f0e87cac0b54a95b102ad1d8ba296d5&CV=(null)&VER=1.4.9200.22391&MD=1&FLT=URL%3A&UPS=CompatSuccessResult&WUAUI=DefaultUi&WDS=Restored&DJR=false&CT=false | unknown | — | — | unknown |
— | — | GET | 204 | 13.107.21.200:80 | http://g.bing.com/gwx/vanilla?ts=1705264821799&SQM=725447e043824fe48f53fe4eddd9a698&GWX=(null)&WU=f43817de583741b48c80b3a0e3cc1efa&WER=3ade2c424ab949b7b142be9aeea69063&CS=12&OSVersion=6.1.7601&STG=win10Vanilla&ER=Completed&LANG=1033&IT=(null)&IM=(null)&CCR=0&RM=Failed%20in%20state%20Downloading&PTN=e52abfc276bb4908883fca581fdd83f9&EC=-2147012721&SEC=(null)&SUEC=(null)&SI=4f0e87cac0b54a95b102ad1d8ba296d5&CV=(null)&VER=1.4.9200.22391&MD=1&FLT=URL%3A&UPS=Downloading&WUAUI=DefaultUi&WDS=Restored&DJR=false&CT=false | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2016 | Windows10UpgraderApp.exe | 23.200.162.90:443 | go.microsoft.com | AKAMAI-AS | PL | unknown |
2016 | Windows10UpgraderApp.exe | 2.16.2.89:80 | ctldl.windowsupdate.com | Akamai International B.V. | CZ | whitelisted |
2016 | Windows10UpgraderApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2016 | Windows10UpgraderApp.exe | 104.91.48.252:443 | download.microsoft.com | AKAMAI-AS | PL | unknown |
2836 | HttpHelper.exe | 13.107.21.200:80 | g.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3024 | HttpHelper.exe | 13.107.21.200:80 | g.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2596 | Windows10UpgraderApp.exe | 23.200.162.90:443 | go.microsoft.com | AKAMAI-AS | PL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
download.microsoft.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
g.bing.com |
| whitelisted |