| URL: | https://www.youtube.com/redirect?event=video_description&redir_token=QUFFLUhqbVFLdVZERlRYejB3cjRUcFp0VjM0MHQtMkxvd3xBQ3Jtc0trMDRtSTY5UDFFbGMyTmNRTlR3YTVlX2xuSDlvOTRNVHRUMHh2Tm80STFrVzIxcm5aQU54MHFxdkc5OFVmWHYxVTIwUnNsaTVRZ0wxeVBaR2F0RDdvTEMxUnppUDdKRGtObS12Q1RyLXMteTJRd3hvVQ&q=https%3A%2F%2Flumennex.live%2F&v=1vct0z6Gakg |
| Full analysis: | https://app.any.run/tasks/09c9686b-d458-4daf-ad35-262e557342fe |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | June 24, 2025, 13:38:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0625DDC72319DE0E41BC57654EB4F2A6 |
| SHA1: | B144AD38D03DD4BB297C8274CCBECE212B75EC4F |
| SHA256: | D88487370C27C6AC7932FE1A1B2DF166FFA19CC99A68A8370B3806A28BD36C49 |
| SSDEEP: | 6:2OLUxGKmKLqZYBVyNA2OI2BuBEA01tl1SUDC3sD7/8X33zUAW/Ty:2jGRf6aAbT0Srl1S8C8D7k3QAF |
MALICIOUS
Executing a file with an untrusted certificate
- Lumen.exe (PID: 892)
RHADAMANTHYS has been detected (YARA)
- OOBE-Maintenance.exe (PID: 1636)
Actions looks like stealing of personal data
- OOBE-Maintenance.exe (PID: 1636)
Starts CMD.EXE for self-deleting
- U54.exe (PID: 7420)
- ]aHS21r2T.exe (PID: 4936)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6736)
- ]aHS21r2T.exe (PID: 4936)
Run PowerShell with an invisible window
- powershell.exe (PID: 7732)
Changes the Windows auto-update feature
- ]aHS21r2T.exe (PID: 4936)
Changes Windows Defender settings
- ]aHS21r2T.exe (PID: 4936)
Adds path to the Windows Defender exclusion list
- ]aHS21r2T.exe (PID: 4936)
Uninstalls Malicious Software Removal Tool (MRT)
- cmd.exe (PID: 8152)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 5436)
Deletes shadow copies
- cmd.exe (PID: 7280)
XORed URL has been found (YARA)
- UserOOBEBroker.exe (PID: 1840)
Vulnerable driver has been detected
- WmiPrvSE.exe (PID: 6404)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 5876)
- U54.exe (PID: 7420)
- ]aHS21r2T.exe (PID: 4936)
Reads security settings of Internet Explorer
- Lumen.exe (PID: 892)
- msedge.exe (PID: 3624)
- WmiPrvSE.exe (PID: 6404)
Starts the AutoIt3 executable file
- cmd.exe (PID: 2764)
Executing commands from a ".bat" file
- Lumen.exe (PID: 892)
Starts CMD.EXE for commands execution
- Lumen.exe (PID: 892)
- ]aHS21r2T.exe (PID: 7180)
- U54.exe (PID: 7420)
- powershell.exe (PID: 7732)
- ]aHS21r2T.exe (PID: 4936)
- UserOOBEBroker.exe (PID: 1840)
- WmiPrvSE.exe (PID: 6404)
The executable file from the user directory is run by the CMD process
- Loose.com (PID: 1832)
- ]aHS21r2T.exe (PID: 4936)
Get information on the list of running processes
- cmd.exe (PID: 2764)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2764)
Starts application with an unusual extension
- cmd.exe (PID: 2764)
The process checks if it is being run in the virtual environment
- OpenWith.exe (PID: 4860)
Connects to unusual port
- OpenWith.exe (PID: 4860)
- OOBE-Maintenance.exe (PID: 1636)
- wmpnscfg.exe (PID: 3480)
- dllhost.exe (PID: 7256)
There is functionality for taking screenshot (YARA)
- Lumen.exe (PID: 892)
Executes application which crashes
- Loose.com (PID: 1832)
- OOBE-Maintenance.exe (PID: 1636)
Reads Mozilla Firefox installation path
- msedge.exe (PID: 3624)
Multiple wallet extension IDs have been found
- OOBE-Maintenance.exe (PID: 1636)
Searches for installed software
- OOBE-Maintenance.exe (PID: 1636)
Loads DLL from Mozilla Firefox
- OOBE-Maintenance.exe (PID: 1636)
Potential Corporate Privacy Violation
- OOBE-Maintenance.exe (PID: 1636)
Reads the BIOS version
- ]aHS21r2T.exe (PID: 7180)
- U54.exe (PID: 7420)
- ]aHS21r2T.exe (PID: 4936)
- UserOOBEBroker.exe (PID: 1840)
- WmiPrvSE.exe (PID: 6404)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 2168)
- net.exe (PID: 2996)
- net.exe (PID: 2180)
- cmd.exe (PID: 6768)
- cmd.exe (PID: 7532)
- net.exe (PID: 5908)
Starts process via Powershell
- powershell.exe (PID: 7732)
Executable content was dropped or overwritten
- OOBE-Maintenance.exe (PID: 1636)
- U54.exe (PID: 7420)
- ]aHS21r2T.exe (PID: 4936)
- WmiPrvSE.exe (PID: 6404)
Connects to the server without a host name
- OOBE-Maintenance.exe (PID: 1636)
Starts POWERSHELL.EXE for commands execution
- ]aHS21r2T.exe (PID: 7180)
- ]aHS21r2T.exe (PID: 4936)
Process requests binary or script from the Internet
- OOBE-Maintenance.exe (PID: 1636)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5504)
- cmd.exe (PID: 8064)
Hides command output
- cmd.exe (PID: 5504)
- cmd.exe (PID: 8064)
Starts SC.EXE for service management
- ]aHS21r2T.exe (PID: 4936)
Stops a currently running service
- sc.exe (PID: 440)
- sc.exe (PID: 7224)
- sc.exe (PID: 5232)
- sc.exe (PID: 4168)
- sc.exe (PID: 7128)
Windows service management via SC.EXE
- sc.exe (PID: 8132)
- sc.exe (PID: 7496)
- sc.exe (PID: 7436)
- sc.exe (PID: 5468)
- sc.exe (PID: 7704)
The process deletes folder without confirmation
- ]aHS21r2T.exe (PID: 4936)
Query Microsoft Defender preferences
- ]aHS21r2T.exe (PID: 4936)
Script adds exclusion path to Windows Defender
- ]aHS21r2T.exe (PID: 4936)
Lists all scheduled tasks
- schtasks.exe (PID: 7920)
The process executes via Task Scheduler
- UserOOBEBroker.exe (PID: 1840)
- WmiPrvSE.exe (PID: 6404)
Process uninstalls Windows update
- wusa.exe (PID: 2668)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 7516)
- cmd.exe (PID: 7508)
- cmd.exe (PID: 7120)
- cmd.exe (PID: 8108)
- cmd.exe (PID: 8092)
- cmd.exe (PID: 7408)
- cmd.exe (PID: 7600)
Executes as Windows Service
- VSSVC.exe (PID: 7856)
Drops a system driver (possible attempt to evade defenses)
- WmiPrvSE.exe (PID: 6404)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5876)
- OOBE-Maintenance.exe (PID: 1636)
- U54.exe (PID: 7420)
- ]aHS21r2T.exe (PID: 4936)
- WmiPrvSE.exe (PID: 6404)
Manual execution by a user
- WinRAR.exe (PID: 5876)
- Lumen.exe (PID: 892)
- OpenWith.exe (PID: 4860)
- OOBE-Maintenance.exe (PID: 1636)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5876)
Reads the computer name
- Lumen.exe (PID: 892)
- extrac32.exe (PID: 2216)
- Loose.com (PID: 1832)
- chrome.exe (PID: 5288)
- chrome.exe (PID: 5552)
- msedge.exe (PID: 3624)
- U54.exe (PID: 7420)
- UserOOBEBroker.exe (PID: 1840)
- WmiPrvSE.exe (PID: 6404)
Create files in a temporary directory
- Lumen.exe (PID: 892)
- extrac32.exe (PID: 2216)
- OOBE-Maintenance.exe (PID: 1636)
- chrome.exe (PID: 5288)
- msedge.exe (PID: 3624)
- chrome.exe (PID: 5552)
Reads mouse settings
- Loose.com (PID: 1832)
Checks supported languages
- Loose.com (PID: 1832)
- Lumen.exe (PID: 892)
- extrac32.exe (PID: 2216)
- chrome.exe (PID: 5288)
- msedge.exe (PID: 3624)
- chrome.exe (PID: 5552)
- ]aHS21r2T.exe (PID: 7180)
- wmpnscfg.exe (PID: 3480)
- U54.exe (PID: 7420)
- ]aHS21r2T.exe (PID: 4936)
- UserOOBEBroker.exe (PID: 1840)
- WmiPrvSE.exe (PID: 6404)
Process checks computer location settings
- Lumen.exe (PID: 892)
- msedge.exe (PID: 3624)
- chrome.exe (PID: 5288)
- chrome.exe (PID: 5552)
Application launched itself
- chrome.exe (PID: 6648)
- chrome.exe (PID: 5288)
- chrome.exe (PID: 5552)
- msedge.exe (PID: 3624)
Reads Environment values
- chrome.exe (PID: 5288)
- msedge.exe (PID: 3624)
- chrome.exe (PID: 5552)
Reads the machine GUID from the registry
- chrome.exe (PID: 5288)
- msedge.exe (PID: 3624)
- chrome.exe (PID: 5552)
- U54.exe (PID: 7420)
- wmpnscfg.exe (PID: 3480)
- UserOOBEBroker.exe (PID: 1840)
- WmiPrvSE.exe (PID: 6404)
Checks proxy server information
- slui.exe (PID: 6404)
- chrome.exe (PID: 5288)
- msedge.exe (PID: 3624)
- chrome.exe (PID: 5552)
- WmiPrvSE.exe (PID: 6404)
Reads the software policy settings
- slui.exe (PID: 6404)
- WmiPrvSE.exe (PID: 6404)
Process checks whether UAC notifications are on
- msedge.exe (PID: 3624)
- ]aHS21r2T.exe (PID: 4936)
- WmiPrvSE.exe (PID: 6404)
Creates files or folders in the user directory
- OOBE-Maintenance.exe (PID: 1636)
Creates files in the program directory
- U54.exe (PID: 7420)
- ]aHS21r2T.exe (PID: 4936)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7856)
- powershell.exe (PID: 1852)
- powershell.exe (PID: 6348)
- powershell.exe (PID: 7544)
- powershell.exe (PID: 7564)
- powershell.exe (PID: 3820)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7544)
- powershell.exe (PID: 6348)
- powershell.exe (PID: 3820)
Themida protector has been detected
- ]aHS21r2T.exe (PID: 4936)
- UserOOBEBroker.exe (PID: 1840)
The sample compiled with japanese language support
- WmiPrvSE.exe (PID: 6404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Rhadamanthys
(PID) Process(1636) OOBE-Maintenance.exe
C2 (1)https://180.178.189.34:8181/gDatFeDway/ujp8k5q9.kbtsk
Total processes
347
Monitored processes
194
Malicious processes
10
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 360 | C:\WINDOWS\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | sc.exe stop wuauserv | C:\Windows\System32\sc.exe | — | ]aHS21r2T.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 480 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgABAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=1944,i,14666786516007935536,15921461696004953453,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=1936 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --field-trial-handle=5388,i,14666786516007935536,15921461696004953453,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5272 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
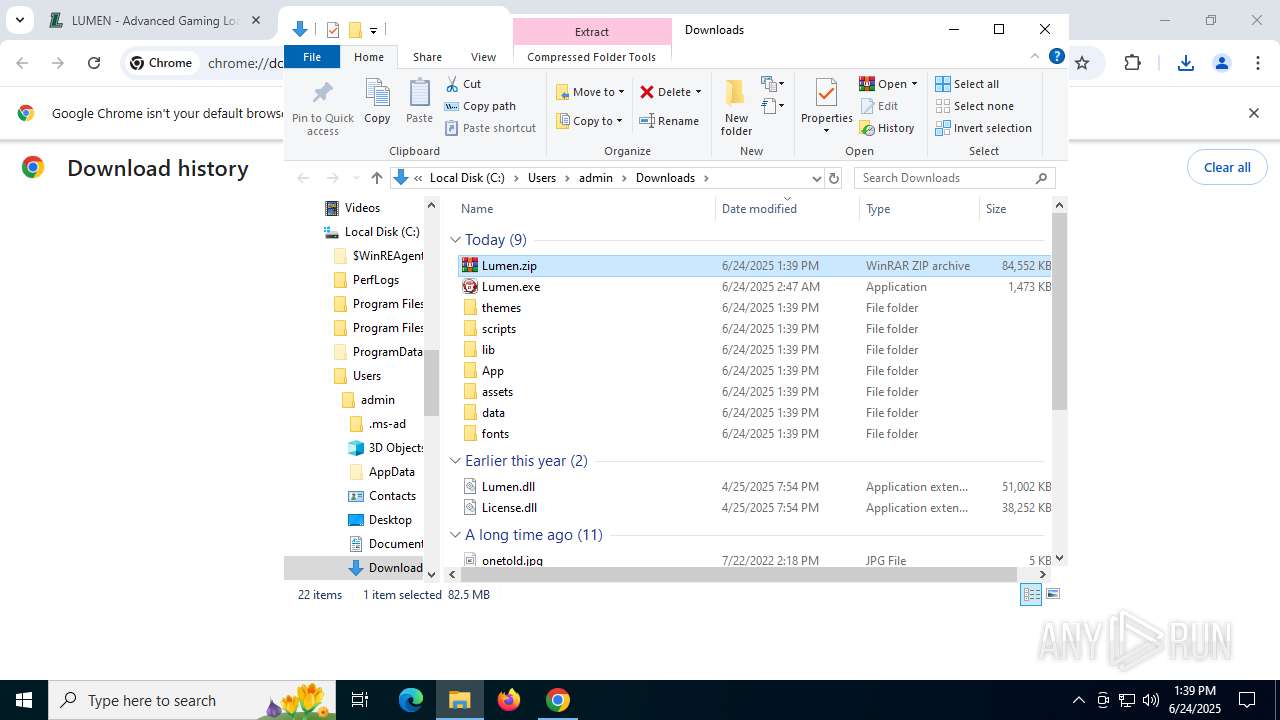
| 892 | "C:\Users\admin\Downloads\Lumen.exe" | C:\Users\admin\Downloads\Lumen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1100 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=3480,i,1699276773408555269,5733375541176221834,262144 --variations-seed-version --mojo-platform-channel-handle=3504 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | OOBE-Maintenance.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
54 305
Read events
54 166
Write events
71
Delete events
68
Modification events
| (PID) Process: | (6648) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6648) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6648) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6648) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6648) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6648) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6648) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6648) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6648) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | ahfgeienlihckogmohjhadlkjgocpleb |
Value: 3B08F722C14555E595AF269F140EE426CE8DEBAD90D03EE9FF33B95CB34233F6 | |||
| (PID) Process: | (6648) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | bjbddleefiddlmdfdfbgodgacjjldihj |
Value: 5CFE6AD362B9AABBD07085580BC6C063CF1C79A0B22ECB6BCBA21EECA68BA07F | |||
Executable files
16
Suspicious files
511
Text files
516
Unknown types
389
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF1756ca.TMP | — | |
MD5:— | SHA256:— | |||
| 6648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF1756da.TMP | — | |
MD5:— | SHA256:— | |||
| 6648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF1756ea.TMP | — | |
MD5:— | SHA256:— | |||
| 6648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1756f9.TMP | — | |
MD5:— | SHA256:— | |||
| 6648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF1756f9.TMP | — | |
MD5:— | SHA256:— | |||
| 6648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF175709.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
106
DNS requests
160
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6368 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2128 | chrome.exe | GET | 200 | 142.250.186.78:80 | http://clients2.google.com/time/1/current?cup2key=8:KQf42q6xPr9DuzkF0JAaYFsMtrdGKQ7nayyPhqdsIRg&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6368 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
6368 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
6368 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
6368 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
6368 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/nbxm2nmgxv67barzilmnhfpntq_9894/hfnkpimlhhgieaddgfemjhofmfblmnib_9894_all_adorneueav22mtzfin2agpv5lavq.crx3 | unknown | — | — | whitelisted |
6368 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/nbxm2nmgxv67barzilmnhfpntq_9894/hfnkpimlhhgieaddgfemjhofmfblmnib_9894_all_adorneueav22mtzfin2agpv5lavq.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2432 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2128 | chrome.exe | 66.102.1.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2128 | chrome.exe | 142.250.181.238:443 | www.youtube.com | GOOGLE | US | whitelisted |
2128 | chrome.exe | 172.217.18.106:443 | clients2.google.com | GOOGLE | US | whitelisted |
2128 | chrome.exe | 142.250.186.78:80 | clients2.google.com | GOOGLE | US | whitelisted |
2128 | chrome.exe | 142.250.185.99:443 | www.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
www.youtube.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
lumennex.live |
| unknown |
fonts.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2128 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2128 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2128 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2128 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2128 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2128 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
4860 | OpenWith.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
1636 | OOBE-Maintenance.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 8 |
1636 | OOBE-Maintenance.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrD2E6.tmp directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrDE61.tmp directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrF48A.tmp directory exists )
|