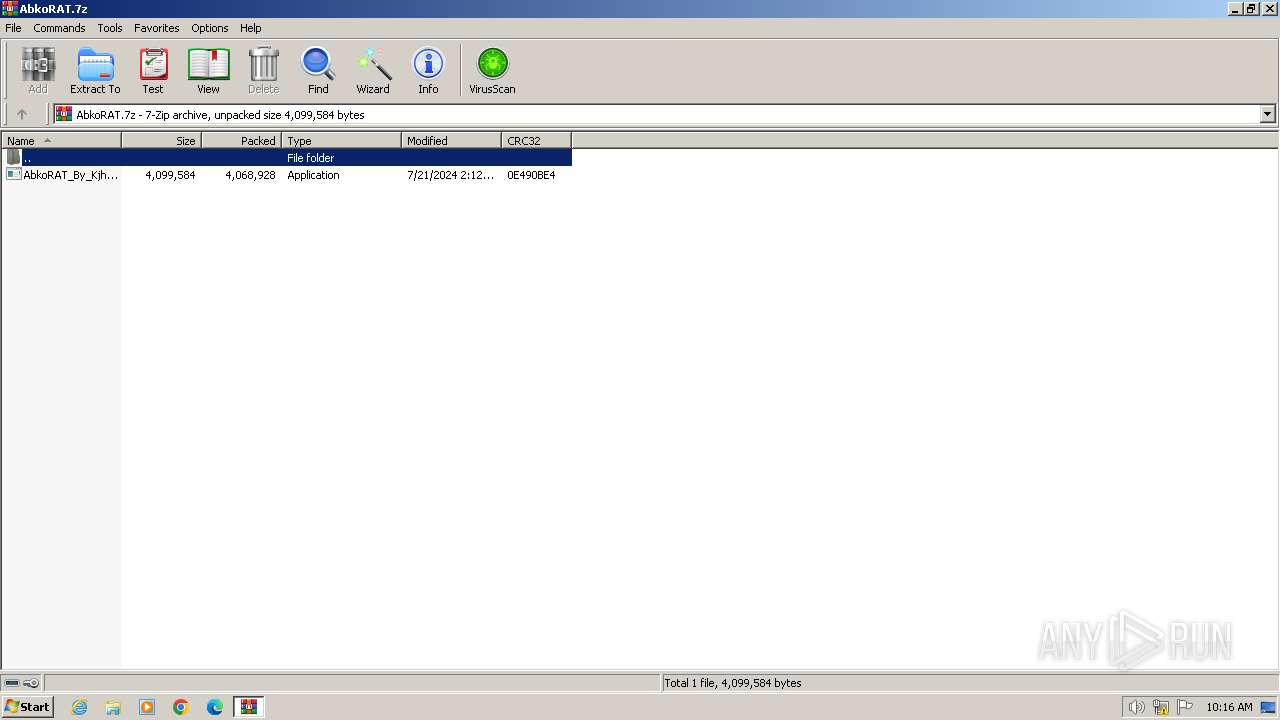
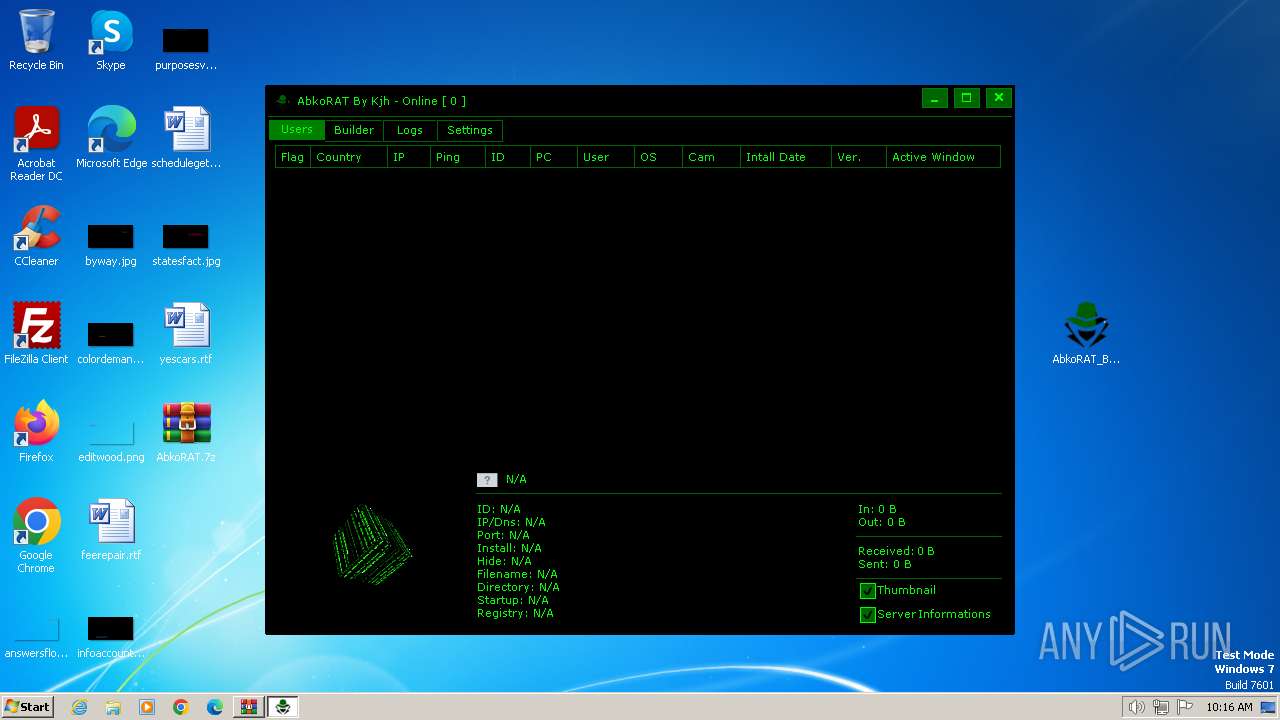
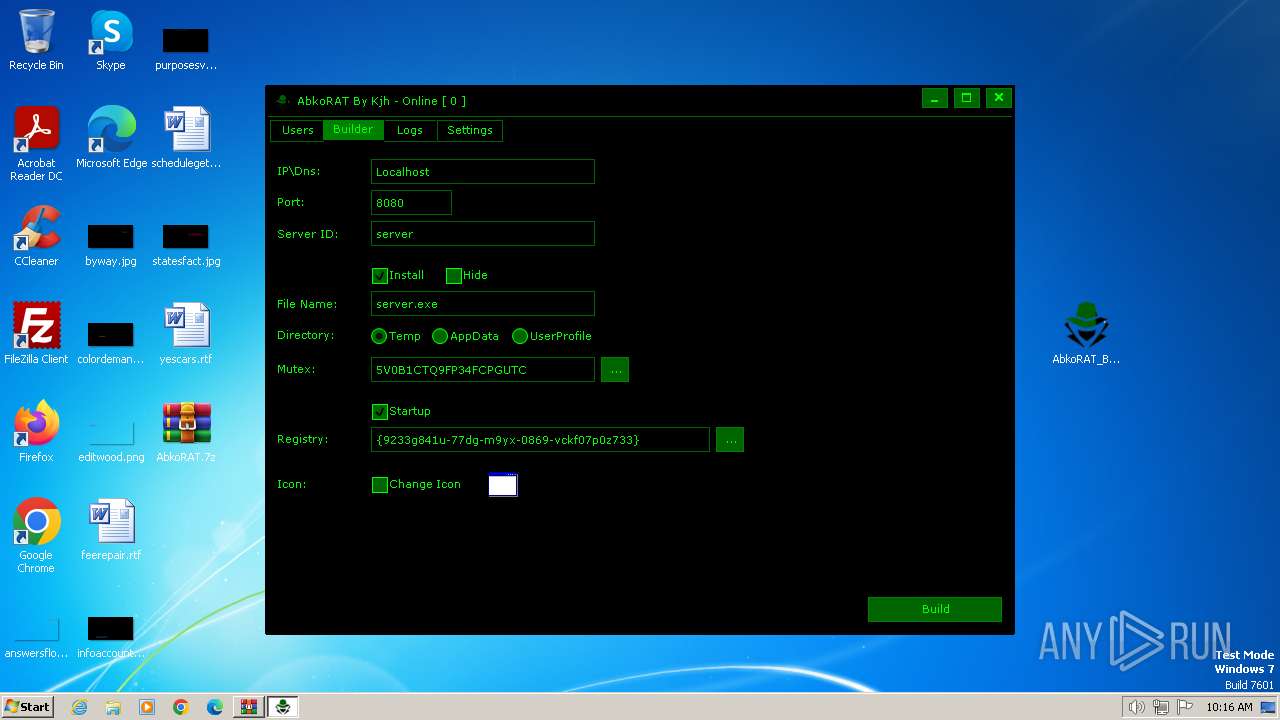
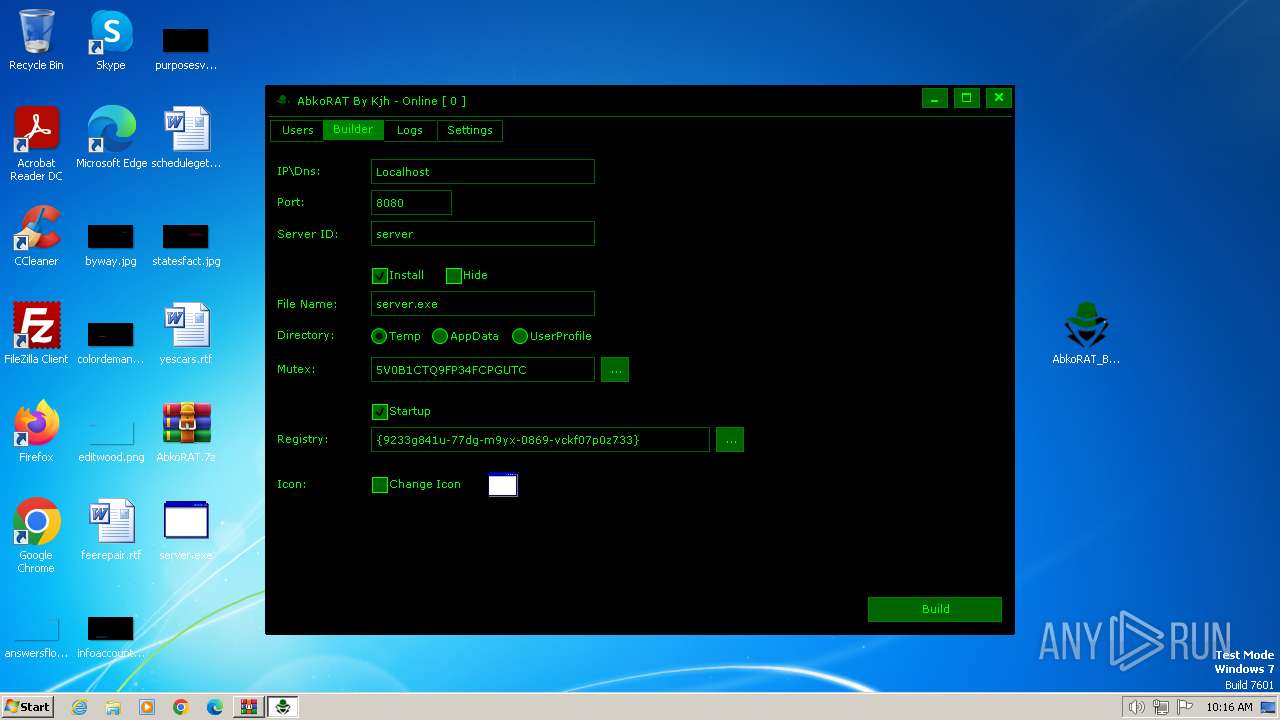
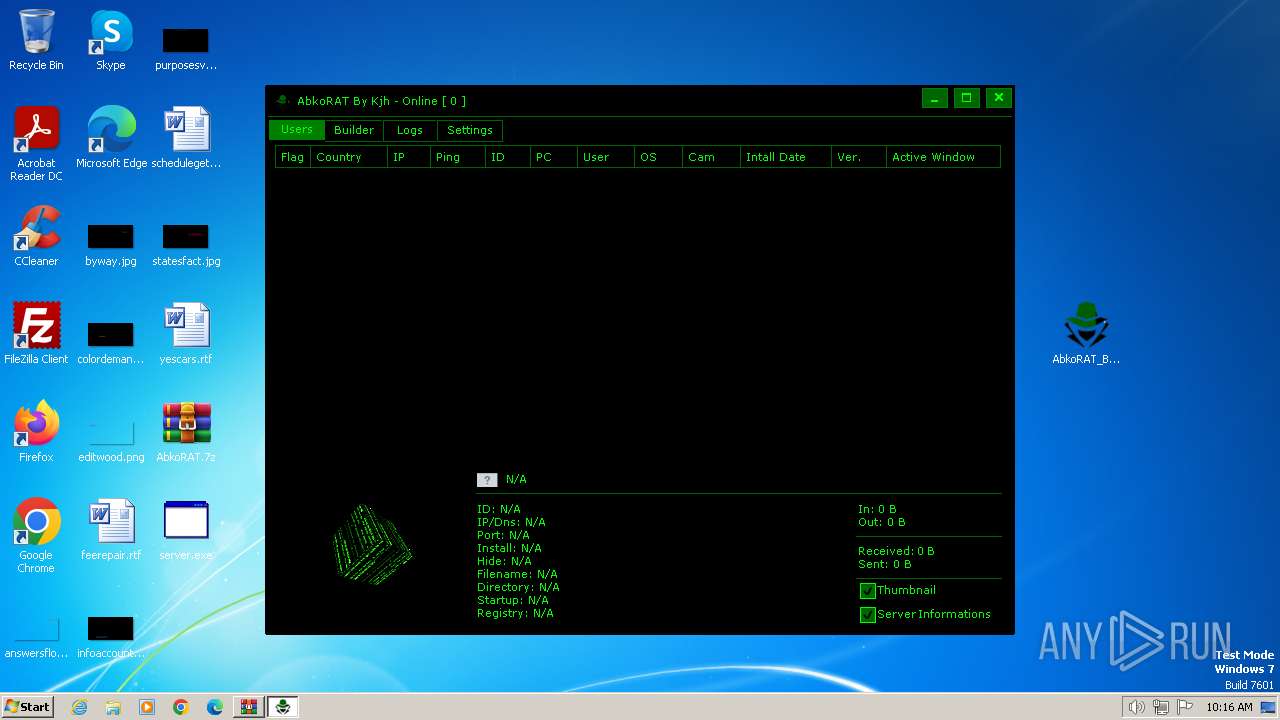
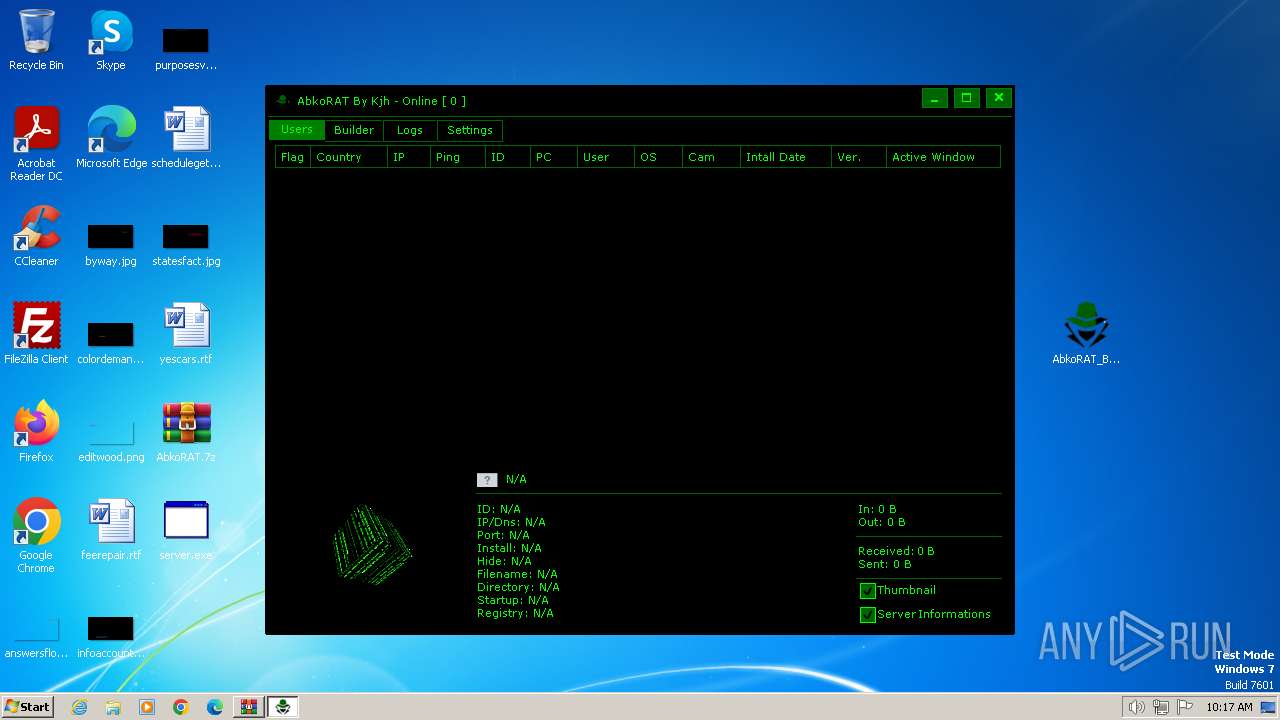
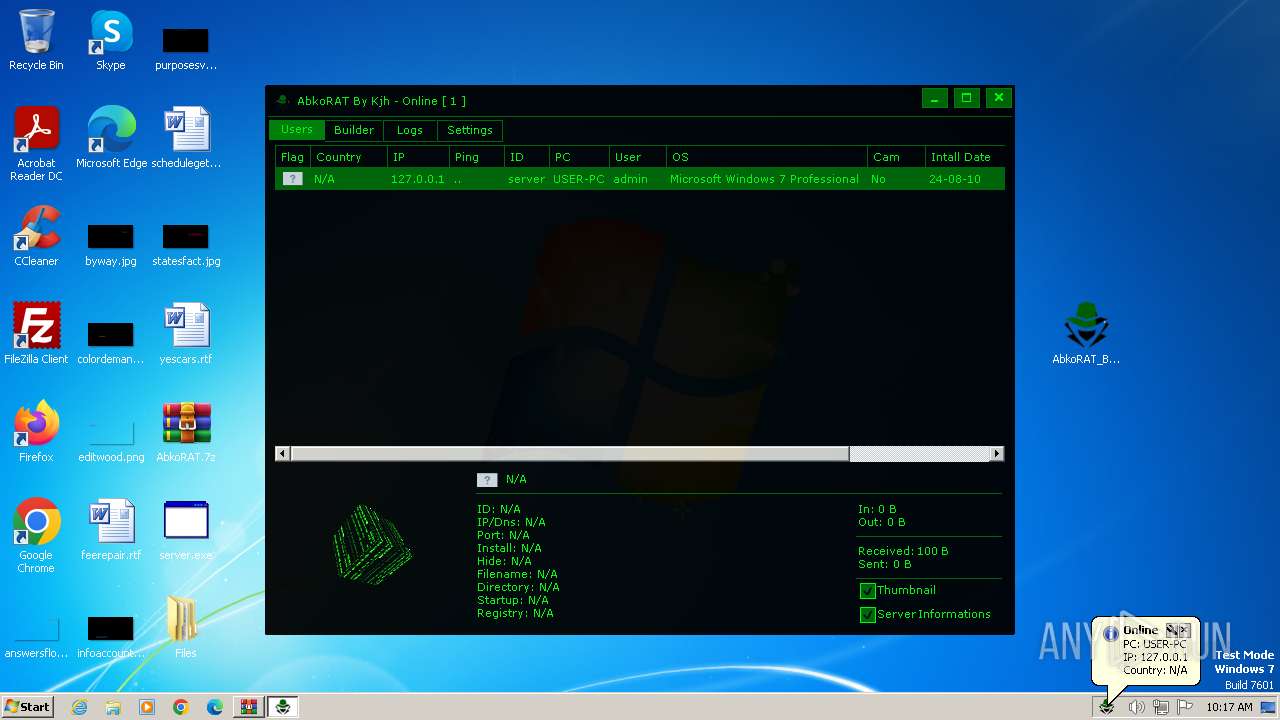
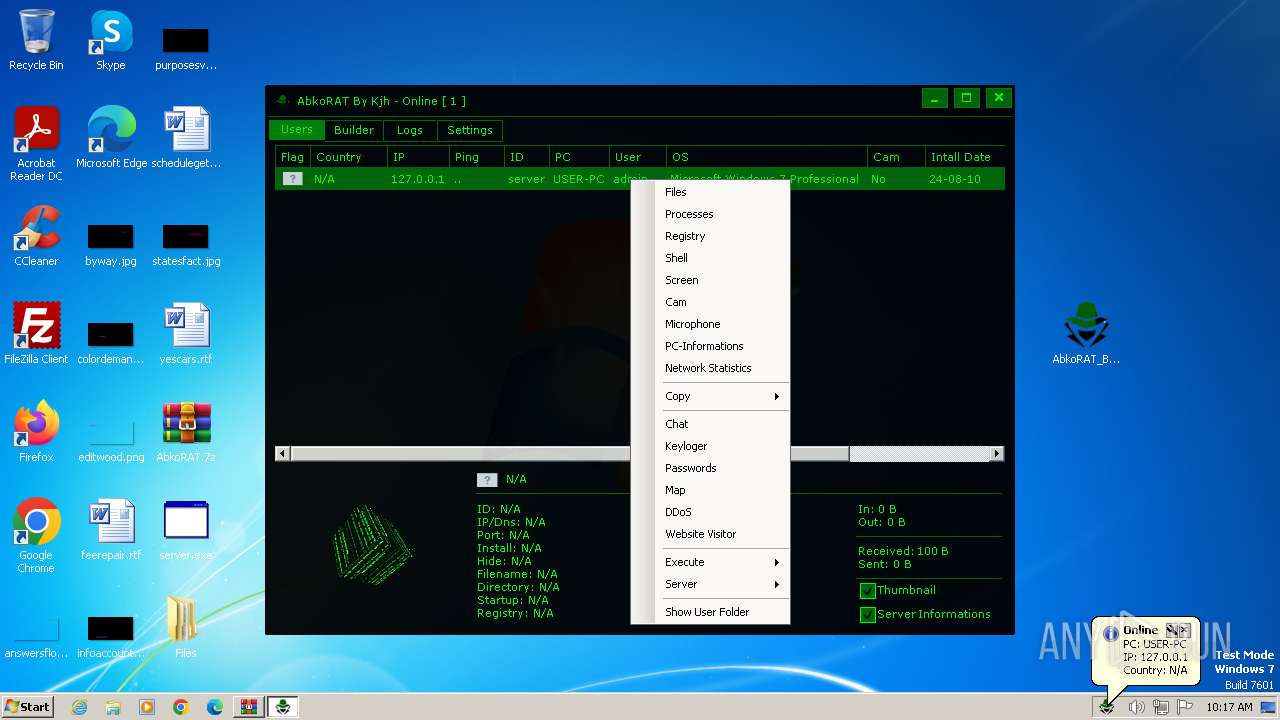
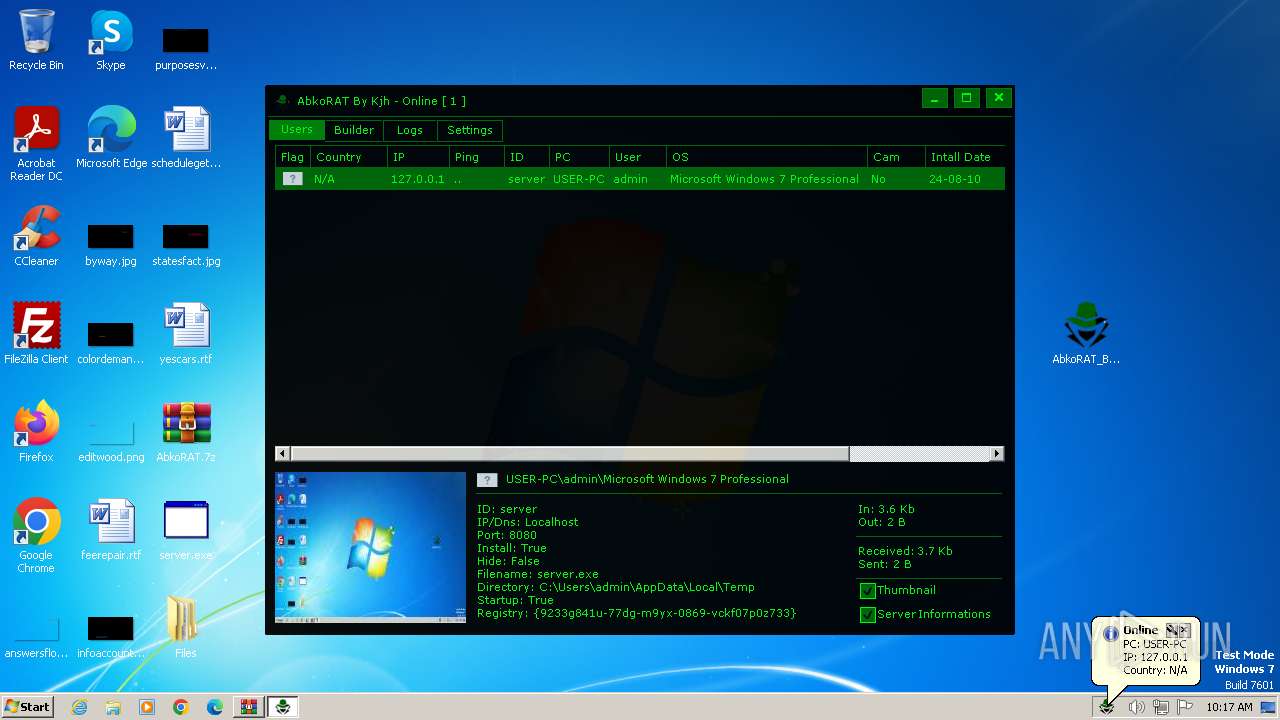
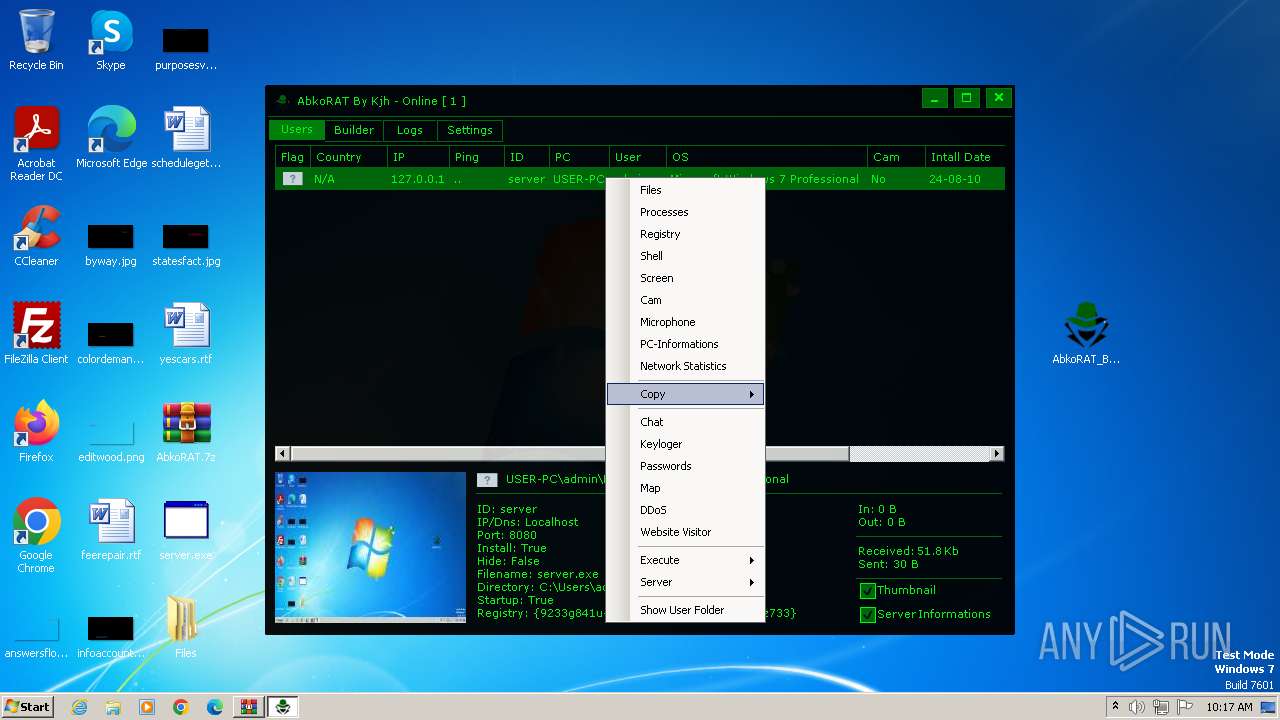
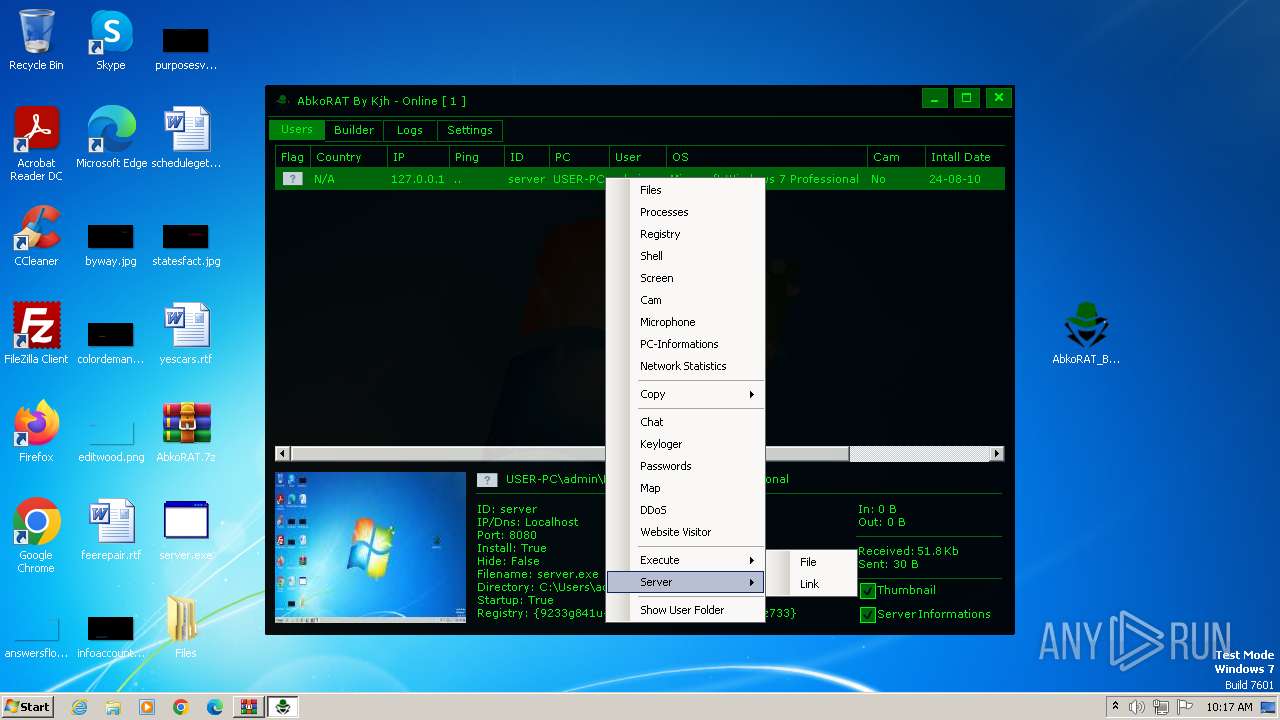
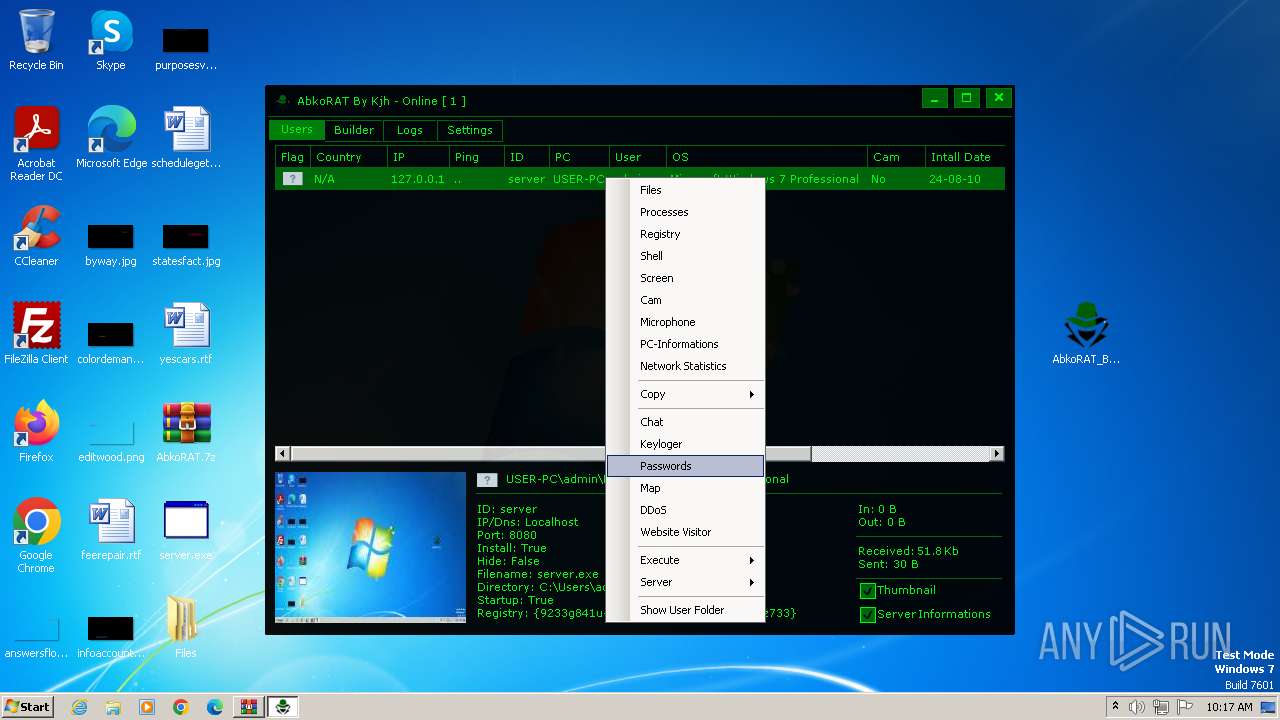
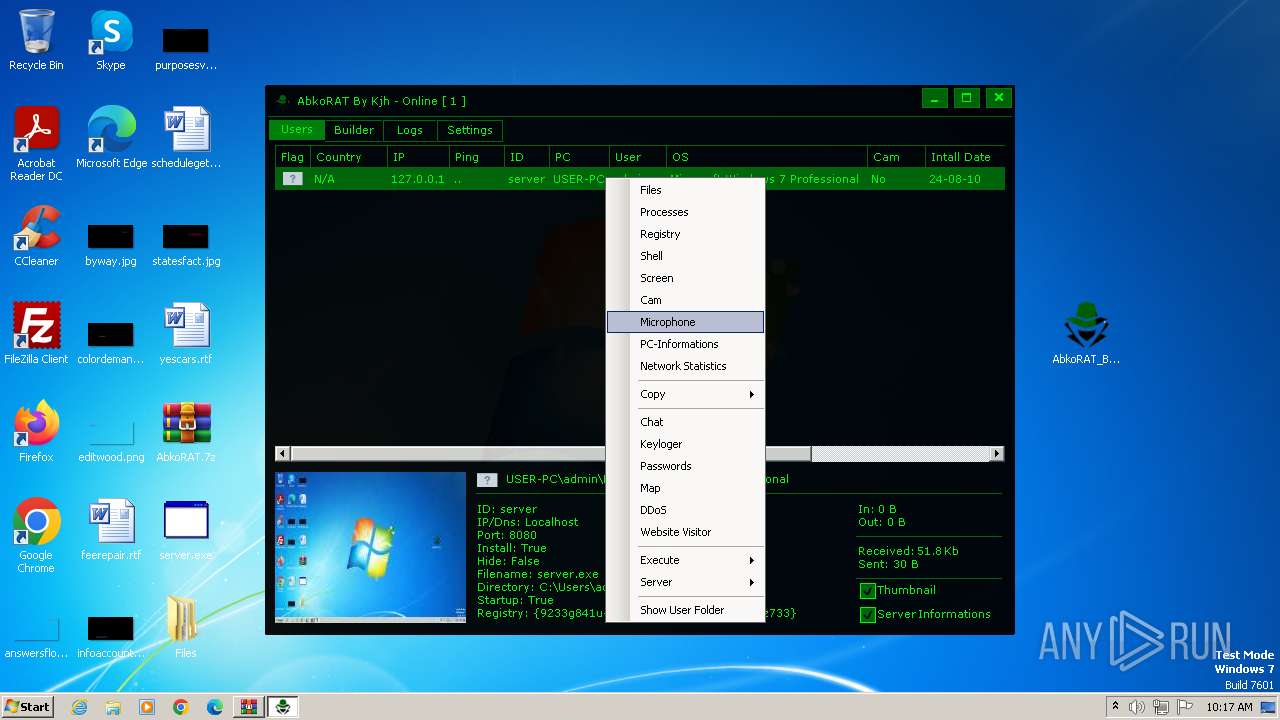
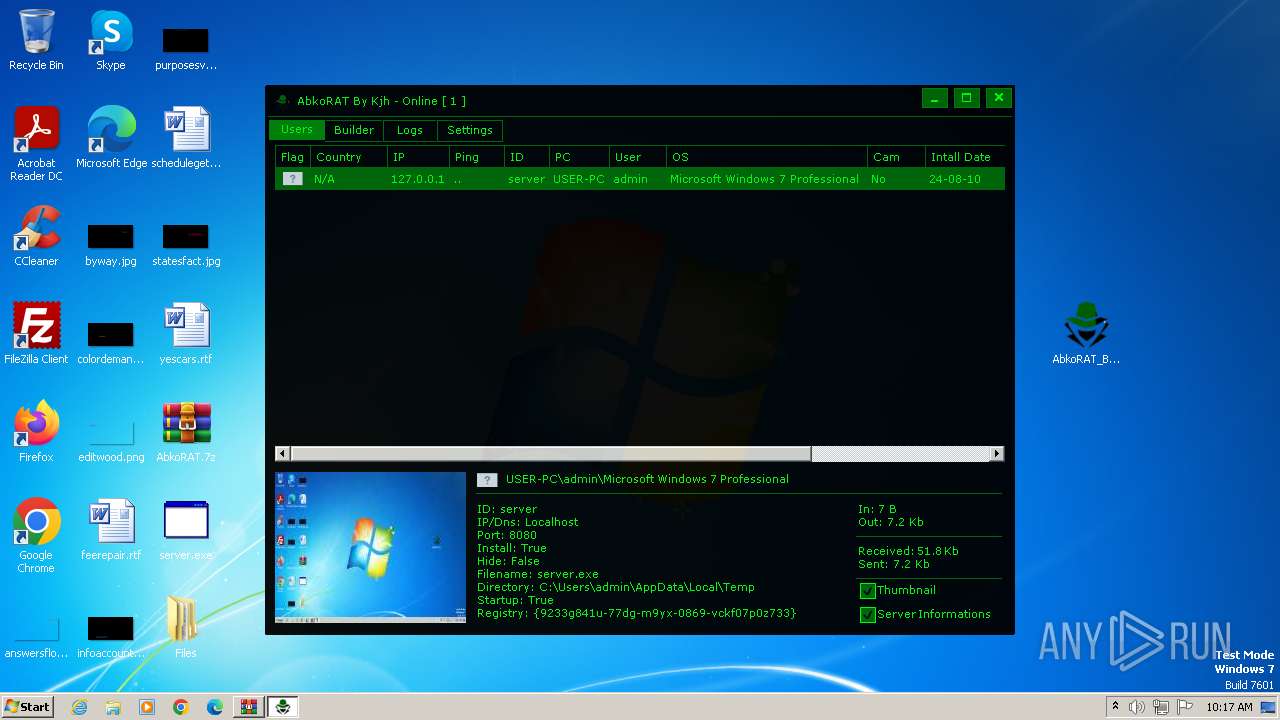
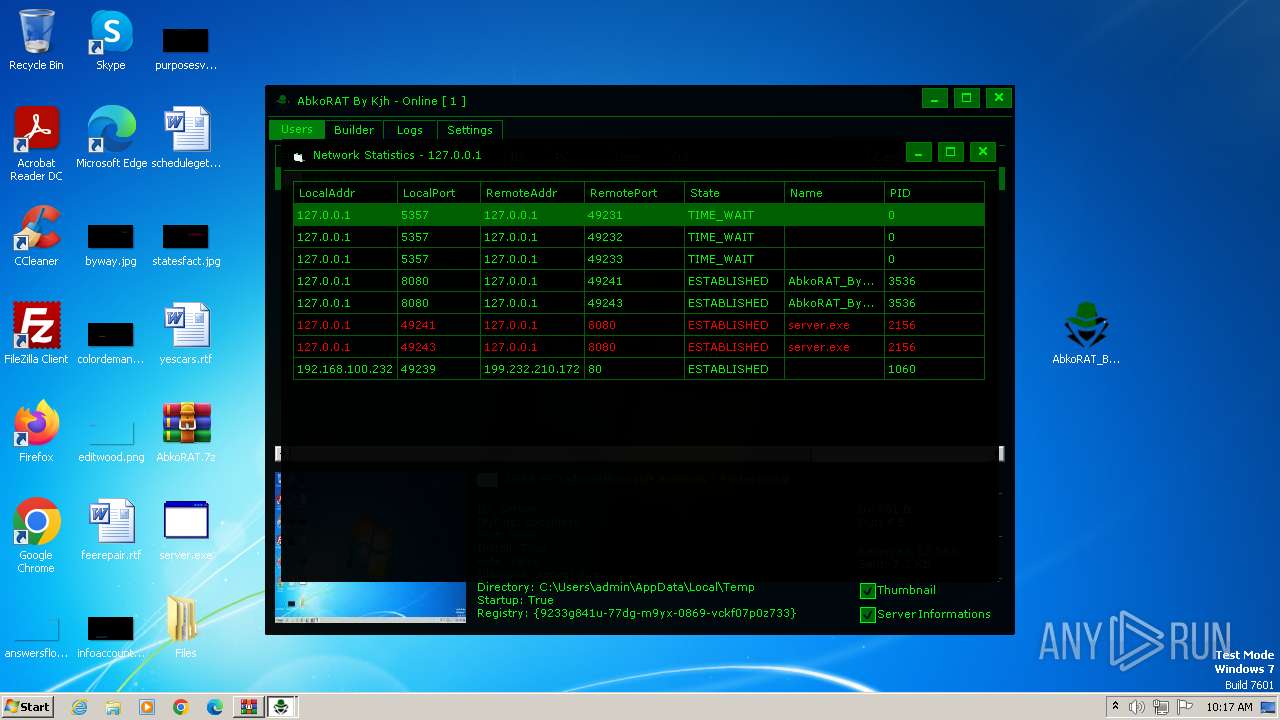
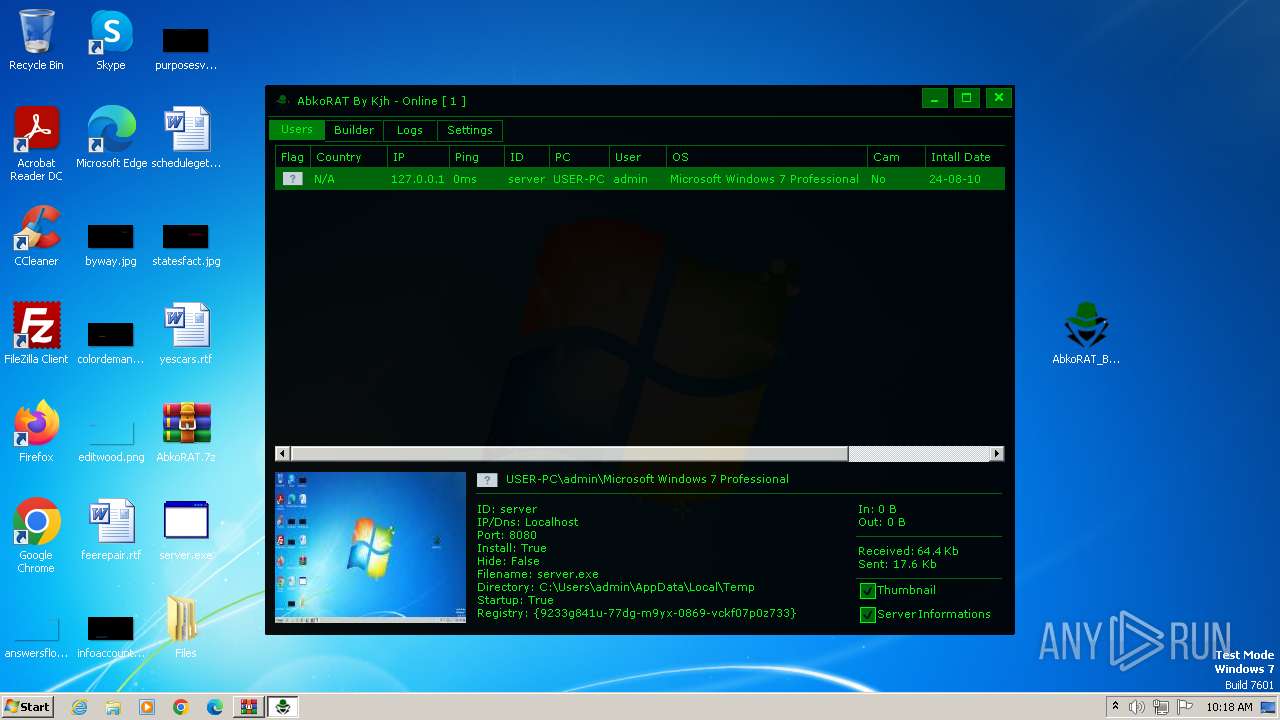
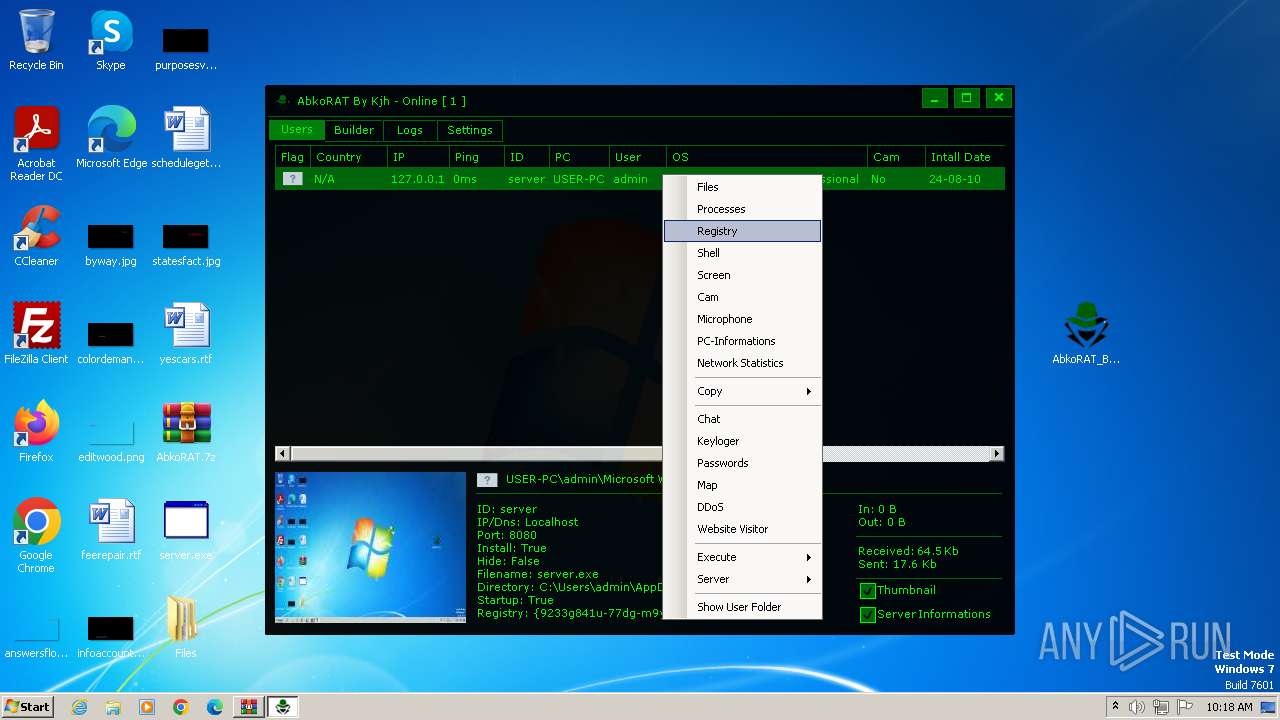
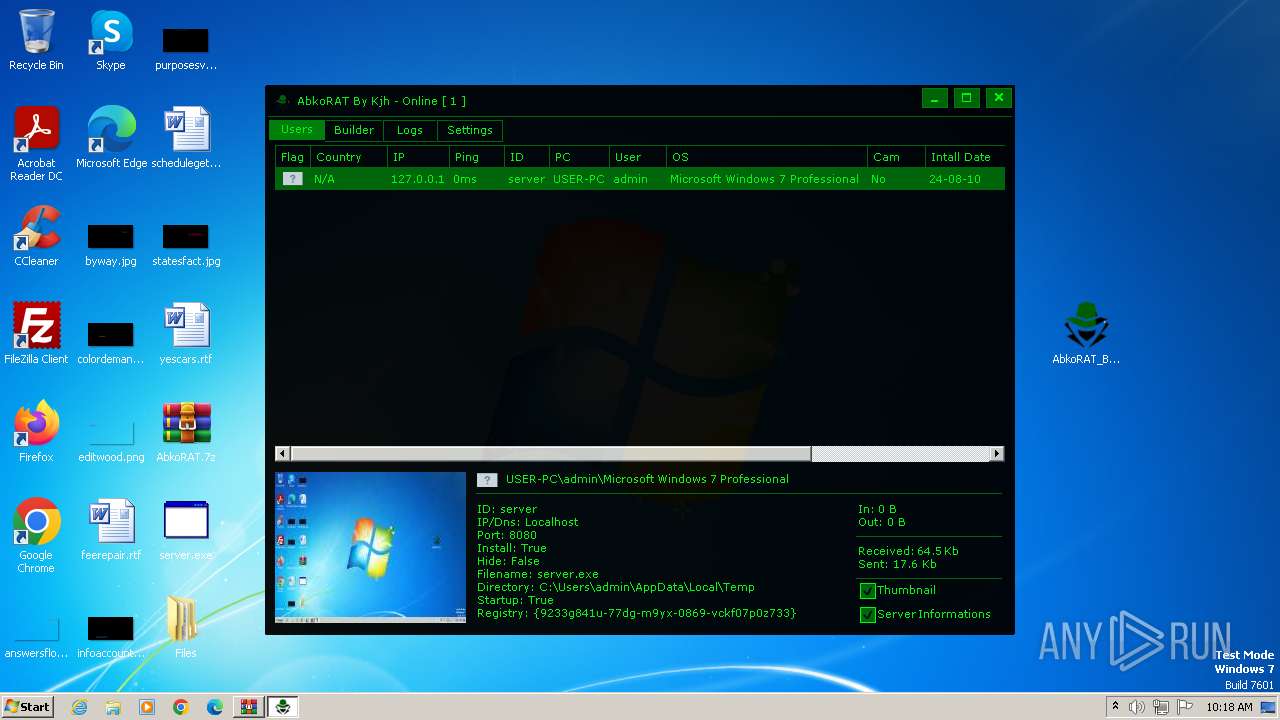
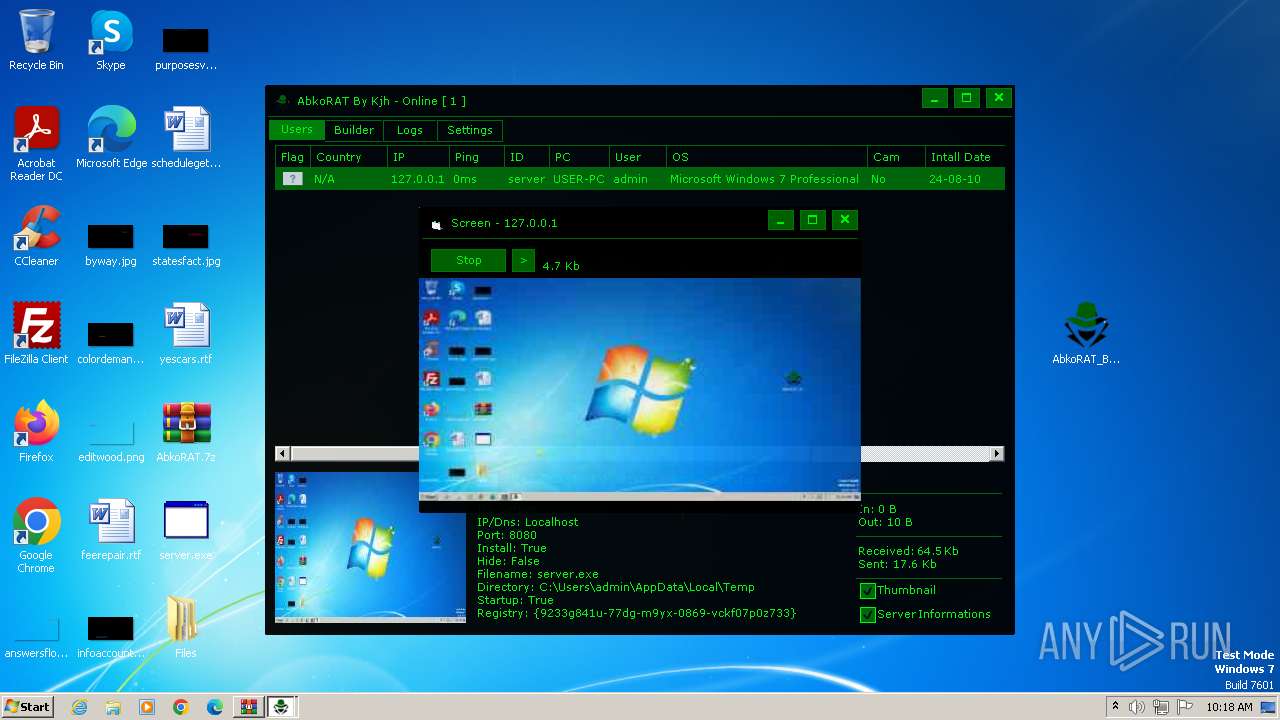
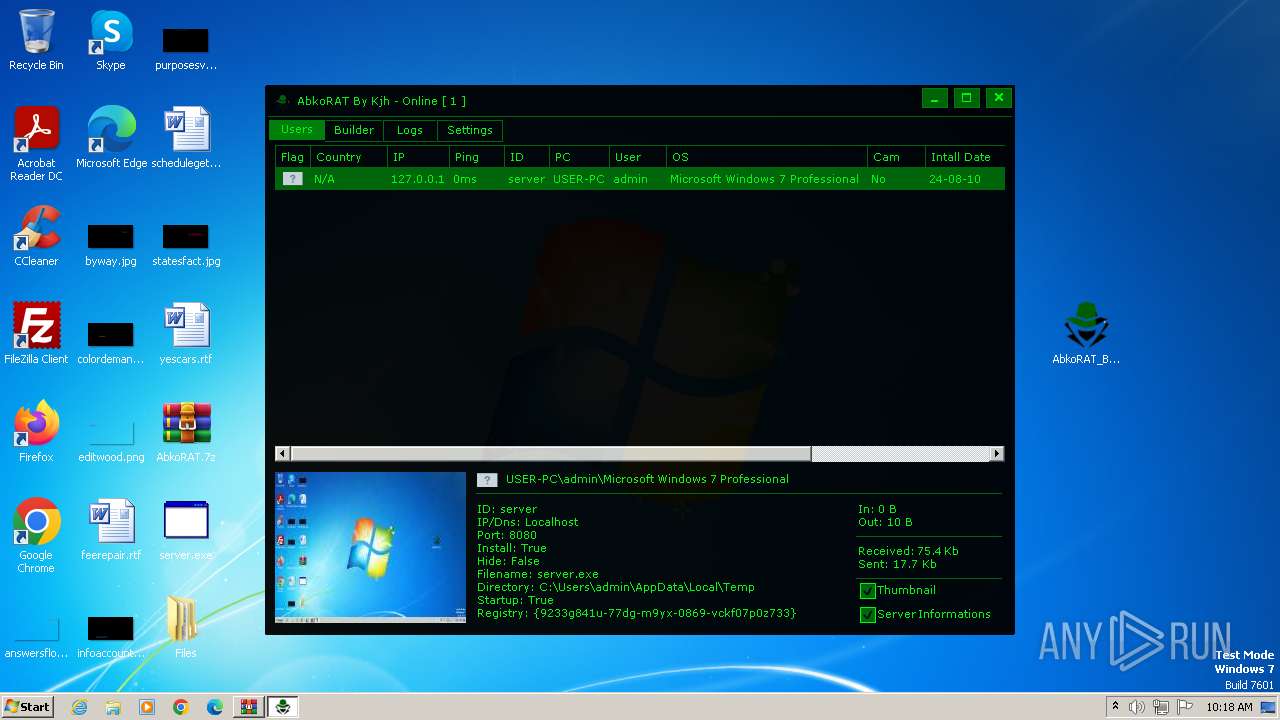
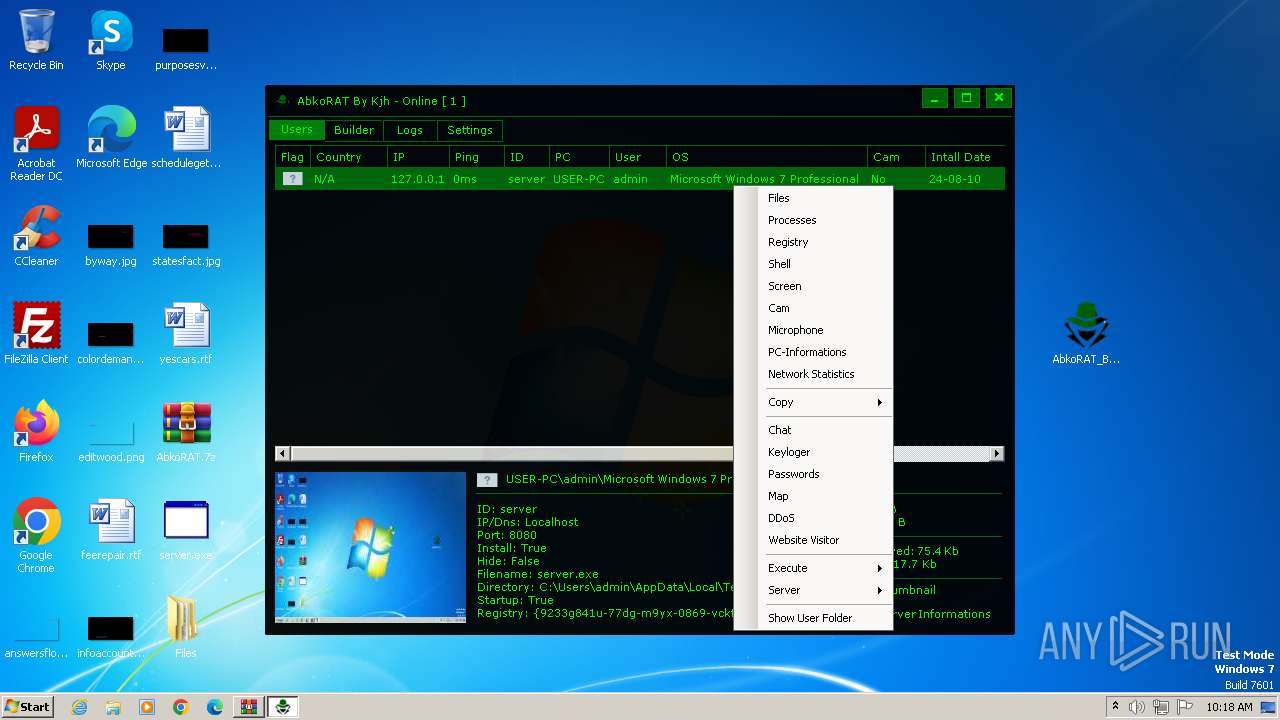
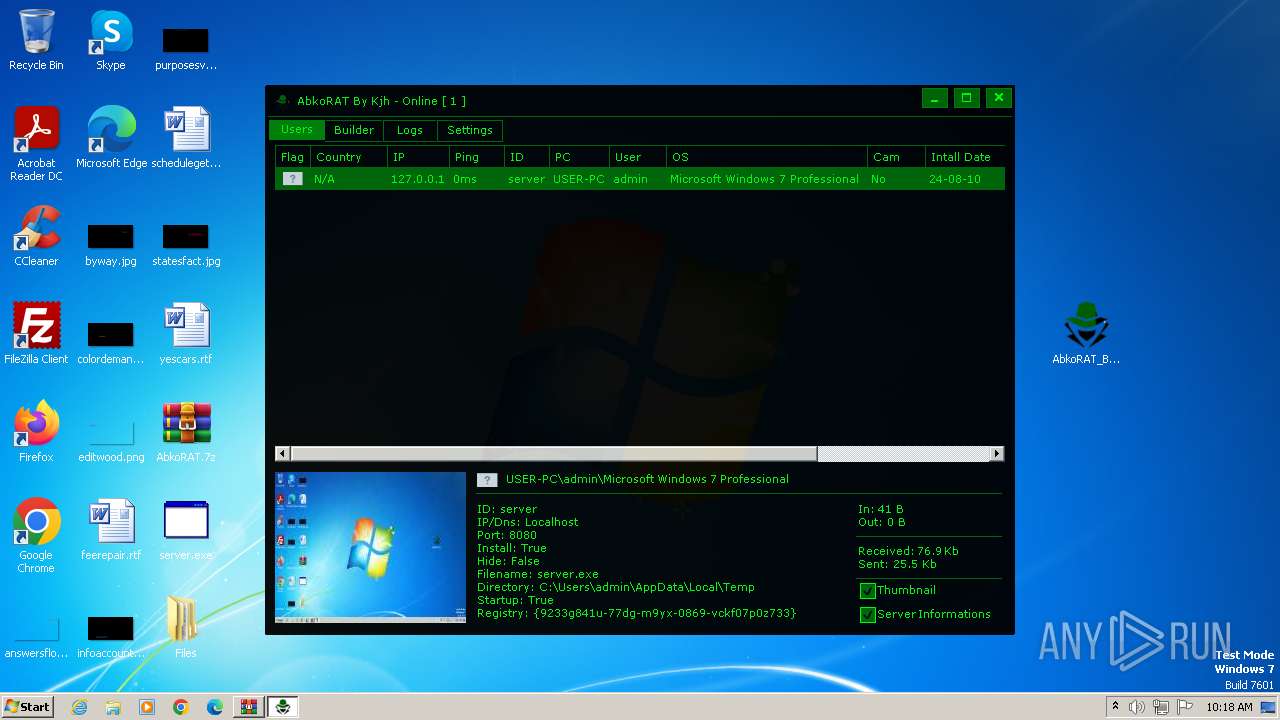
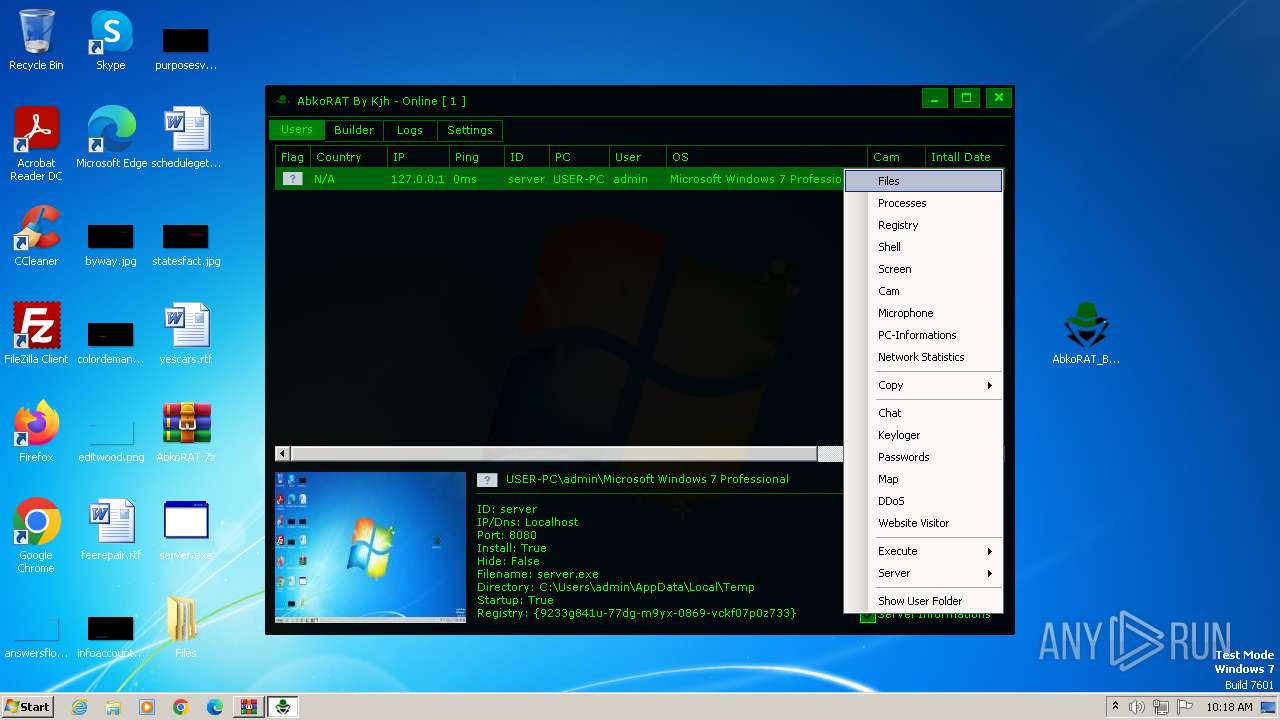
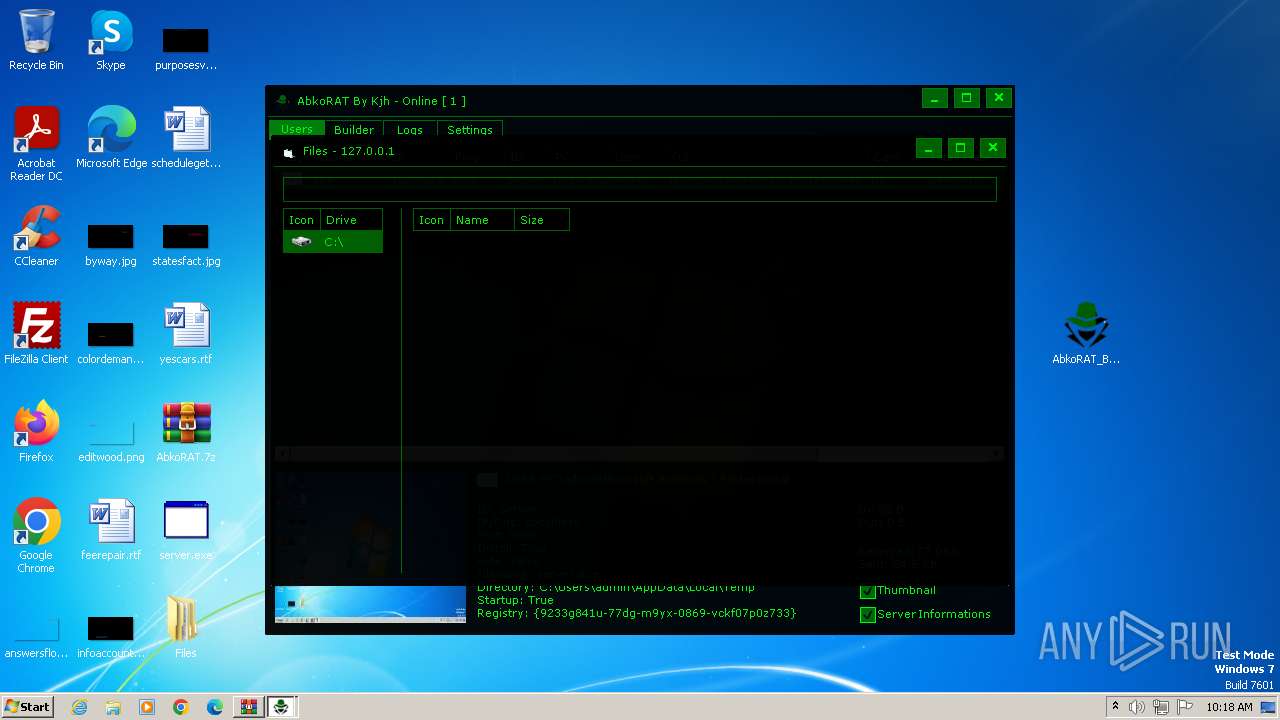
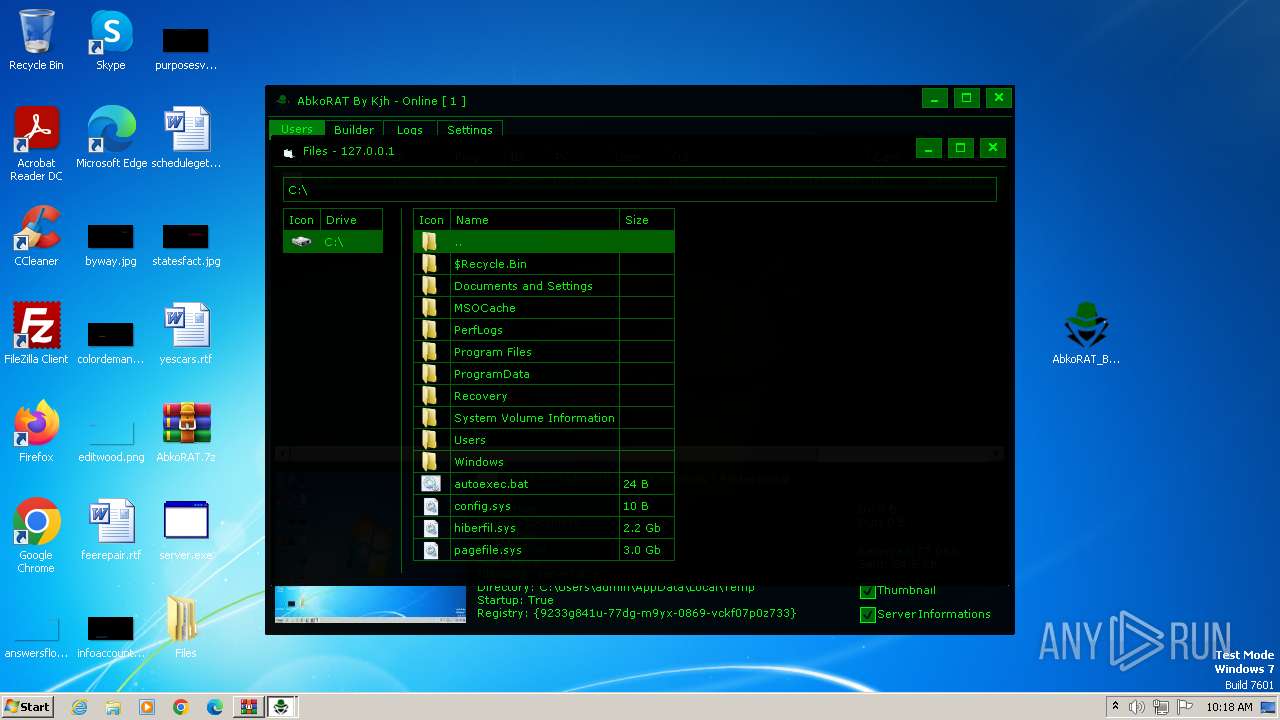
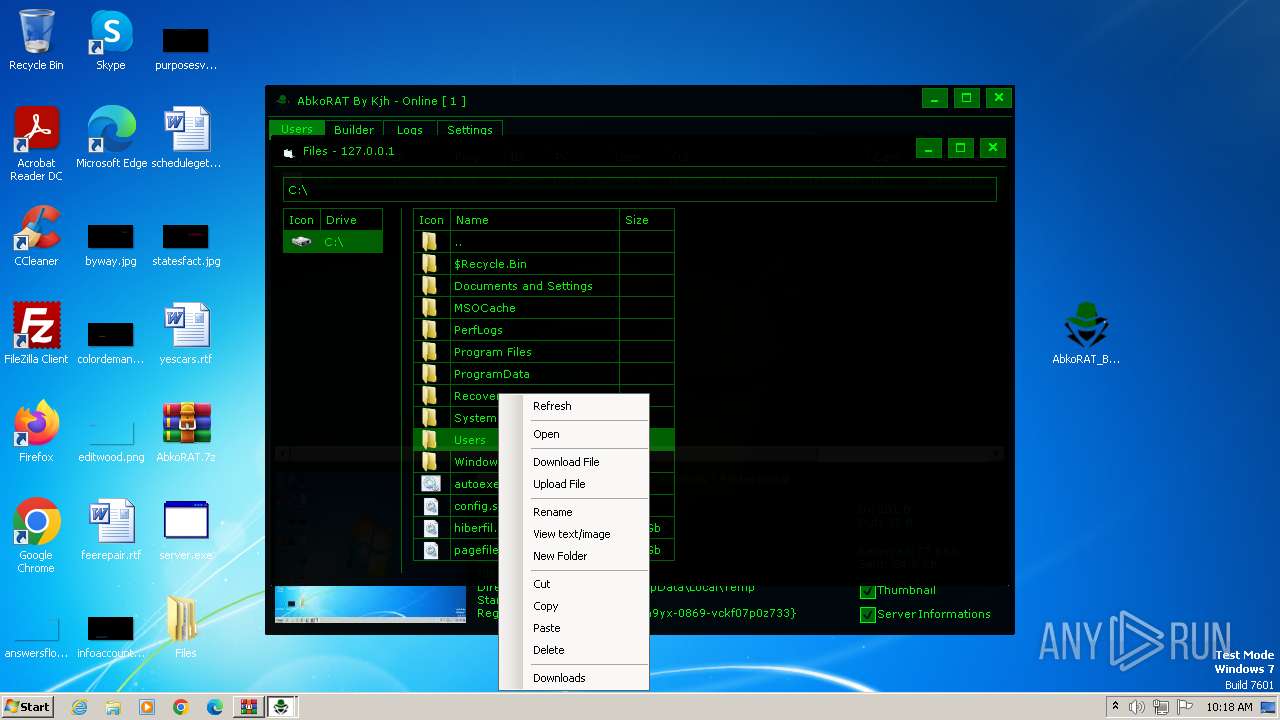
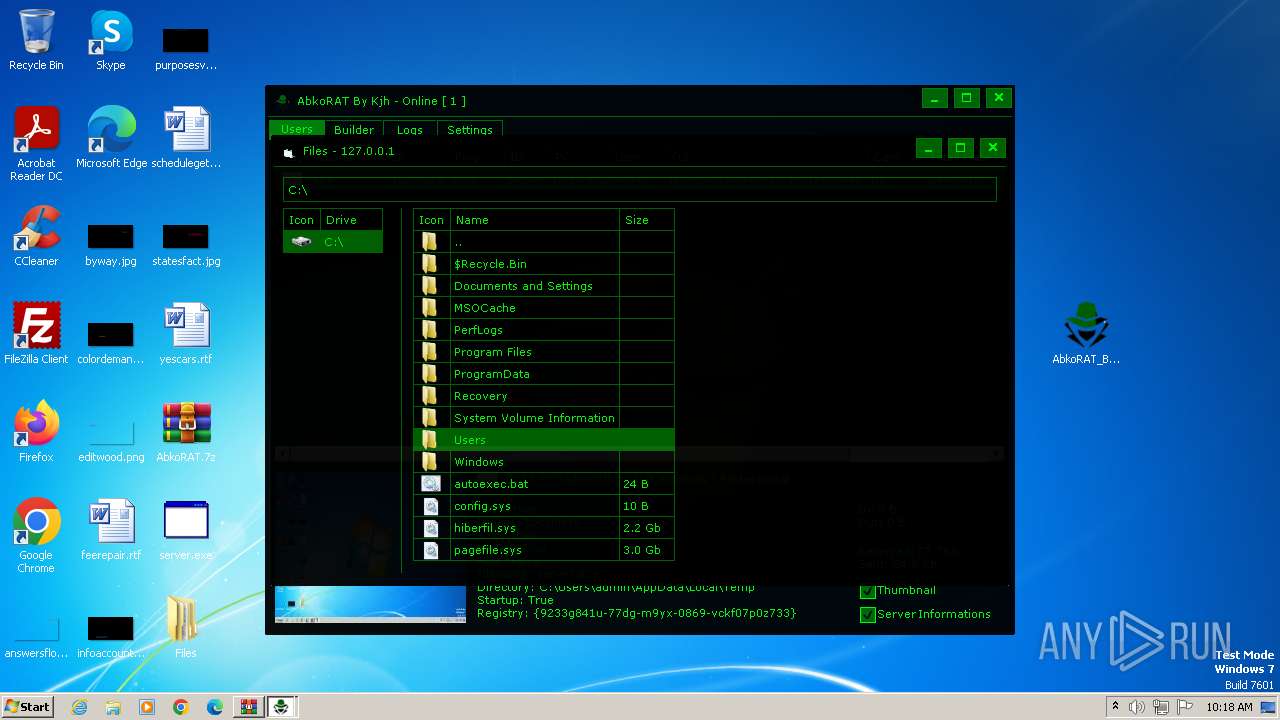
| File name: | AbkoRAT.7z |
| Full analysis: | https://app.any.run/tasks/cbd80a94-6976-4614-940c-8eef5f322158 |
| Verdict: | Malicious activity |
| Analysis date: | August 10, 2024, 09:16:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | B54C66474CDCA7831D21DE571A8CC5B2 |
| SHA1: | A517DC499176F2C10363C1D8D4F9DACA5F75ED4F |
| SHA256: | D87AB4B4B6FAD9A19F62036E1DCDDB5BEAFC51EBB7980A9917C71F7782530A2F |
| SSDEEP: | 98304:m19fdE8KONYCFSxDkEDKHKIWo0jYhWO+0e9lndMITF+7GoMZpzunUzG20UYzYakx:01RwXHHSC |
MALICIOUS
Changes the autorun value in the registry
- server.exe (PID: 2156)
SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2776)
- AbkoRAT_By_Kjh.exe (PID: 3536)
- server.exe (PID: 3724)
Reads the BIOS version
- AbkoRAT_By_Kjh.exe (PID: 3536)
- server.exe (PID: 2156)
Executable content was dropped or overwritten
- AbkoRAT_By_Kjh.exe (PID: 3536)
- server.exe (PID: 3724)
There is functionality for communication dyndns network (YARA)
- AbkoRAT_By_Kjh.exe (PID: 3536)
Starts itself from another location
- server.exe (PID: 3724)
Reads the Internet Settings
- server.exe (PID: 3724)
Reads security settings of Internet Explorer
- server.exe (PID: 3724)
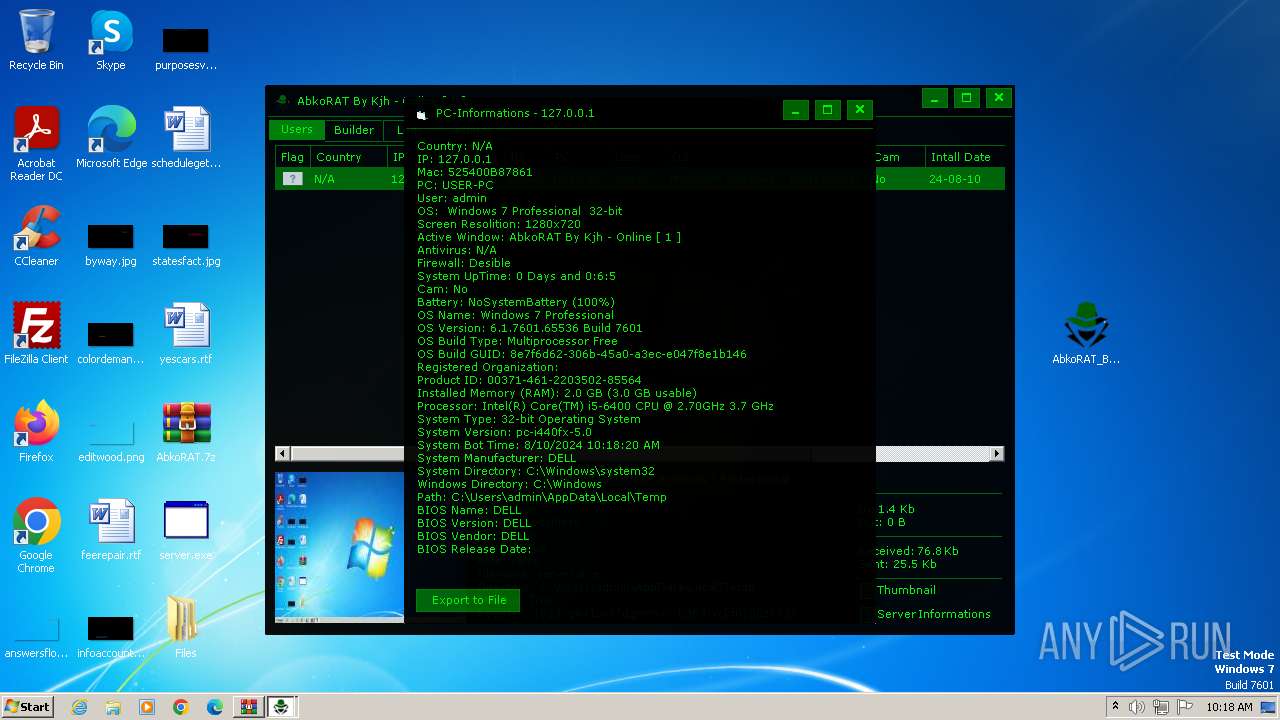
Reads the Windows owner or organization settings
- server.exe (PID: 2156)
Creates file in the systems drive root
- server.exe (PID: 2156)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 3628)
- AbkoRAT_By_Kjh.exe (PID: 3536)
- server.exe (PID: 3724)
- server.exe (PID: 2156)
Manual execution by a user
- AbkoRAT_By_Kjh.exe (PID: 3536)
- wmpnscfg.exe (PID: 3628)
- server.exe (PID: 3724)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2776)
Checks supported languages
- AbkoRAT_By_Kjh.exe (PID: 3536)
- wmpnscfg.exe (PID: 3628)
- server.exe (PID: 3724)
- server.exe (PID: 2156)
Reads the machine GUID from the registry
- AbkoRAT_By_Kjh.exe (PID: 3536)
- server.exe (PID: 2156)
Create files in a temporary directory
- AbkoRAT_By_Kjh.exe (PID: 3536)
- server.exe (PID: 3724)
Reads Environment values
- AbkoRAT_By_Kjh.exe (PID: 3536)
- server.exe (PID: 2156)
.NET Reactor protector has been detected
- AbkoRAT_By_Kjh.exe (PID: 3536)
Themida protector has been detected
- AbkoRAT_By_Kjh.exe (PID: 3536)
Reads CPU info
- server.exe (PID: 2156)
Reads product name
- server.exe (PID: 2156)
Reads Windows Product ID
- server.exe (PID: 2156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
49
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
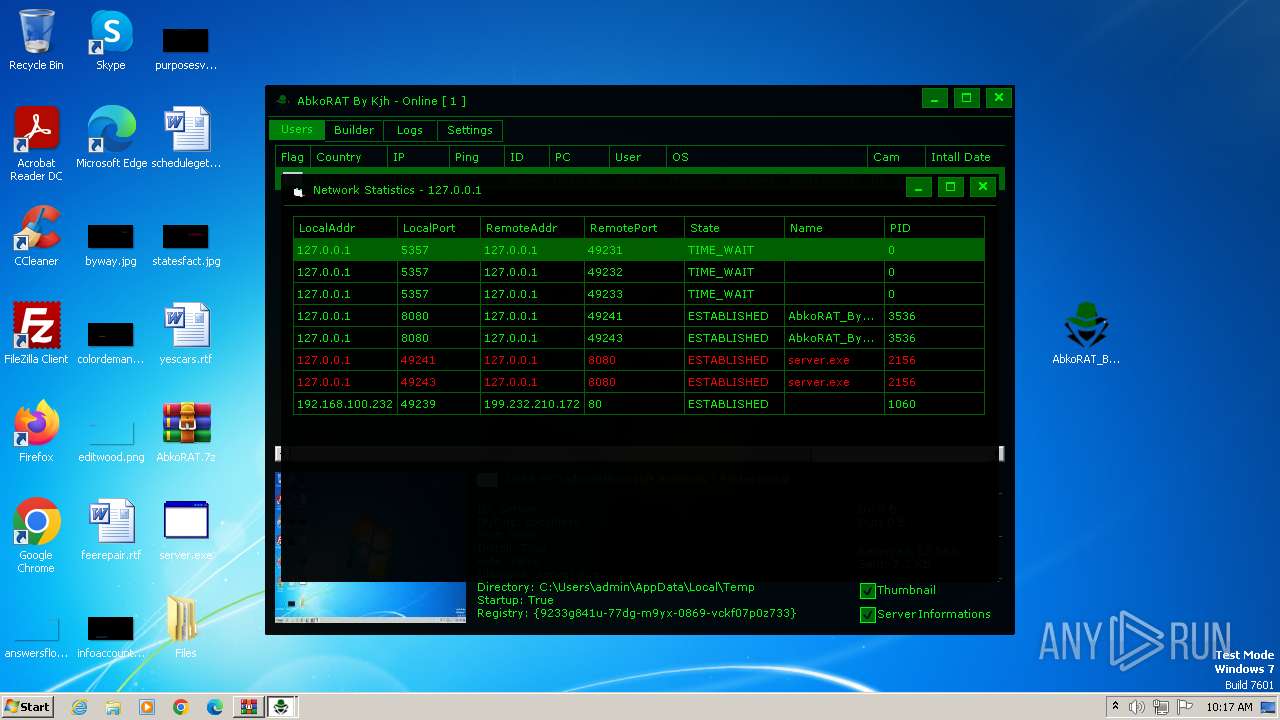
| 2124 | "netstat" -no | C:\Windows\System32\NETSTAT.EXE | — | server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Netstat Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
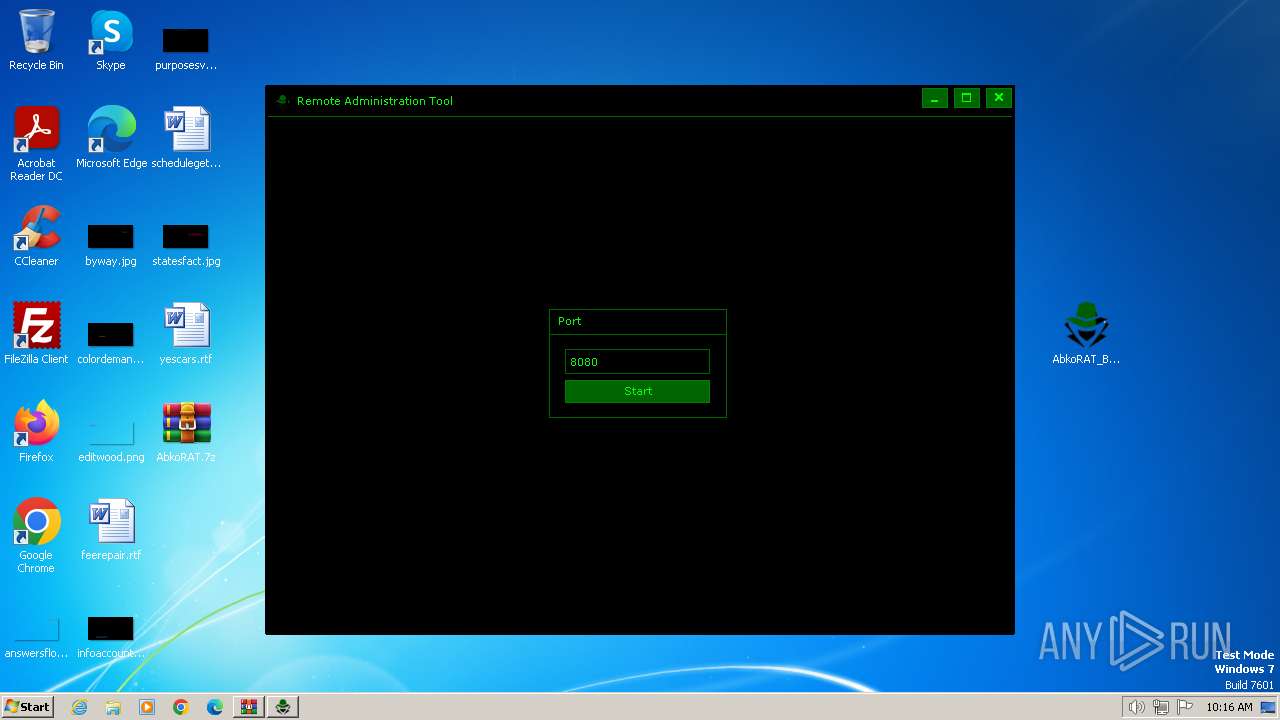
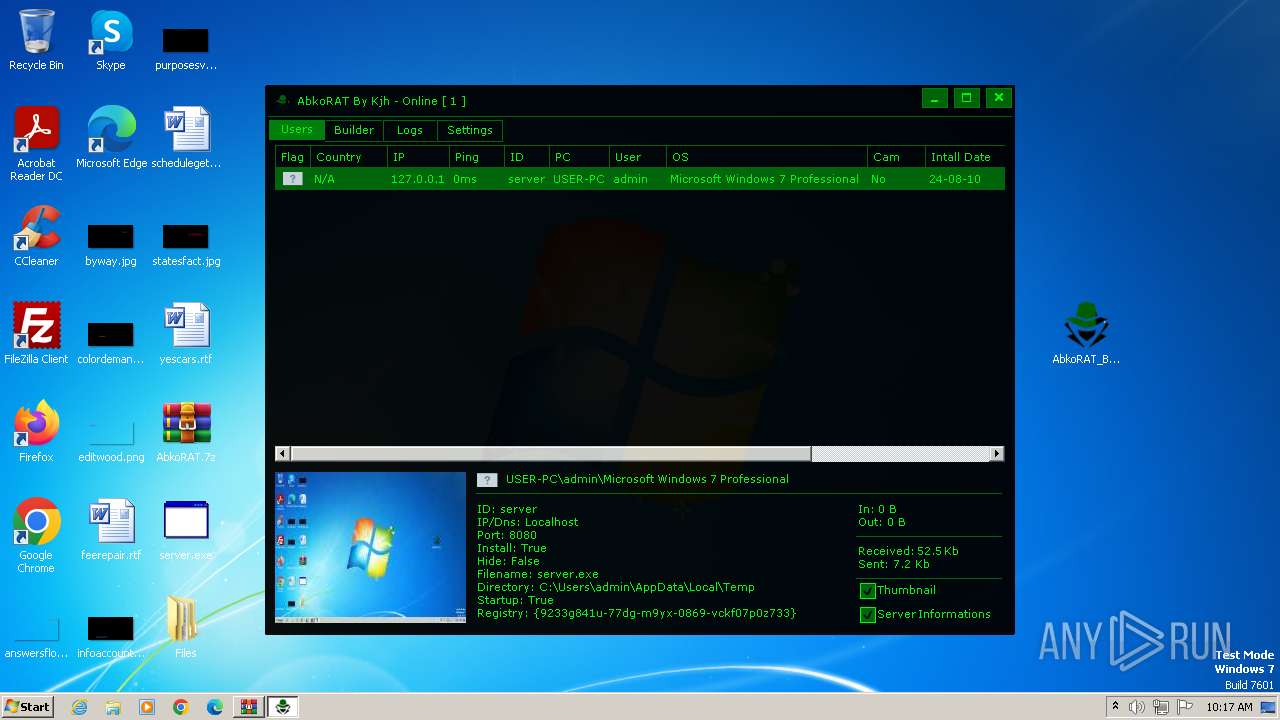
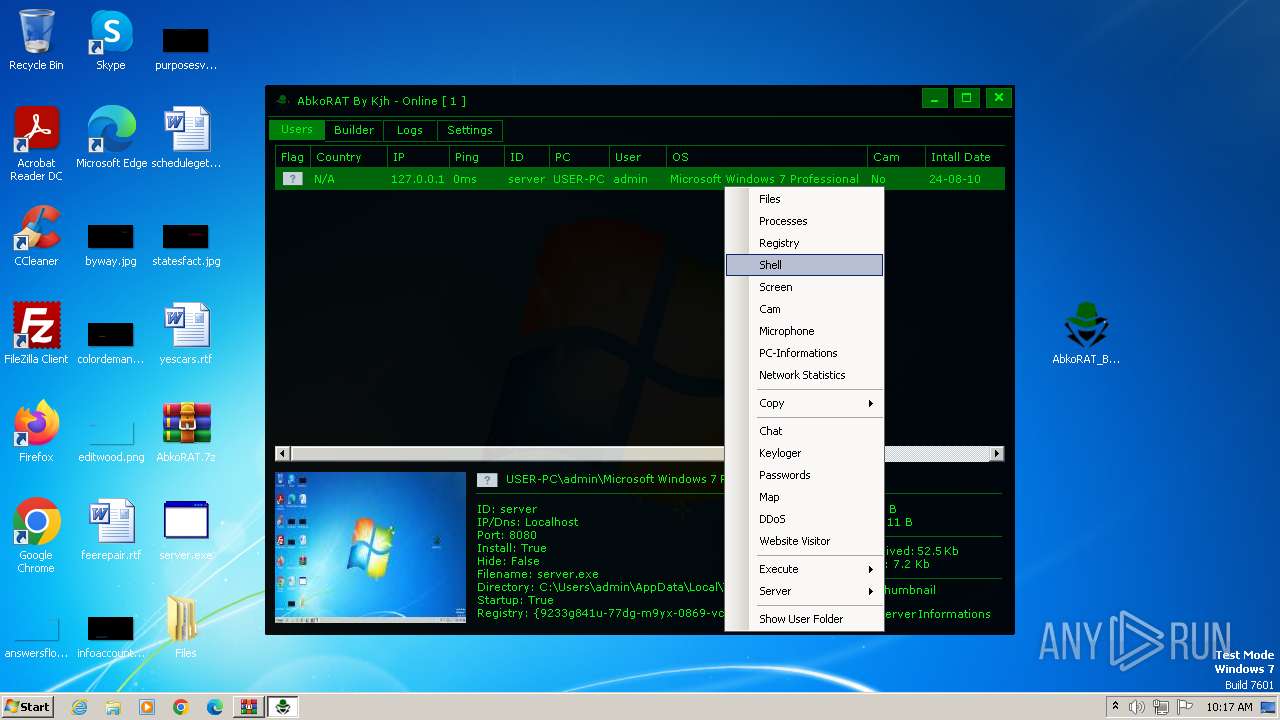
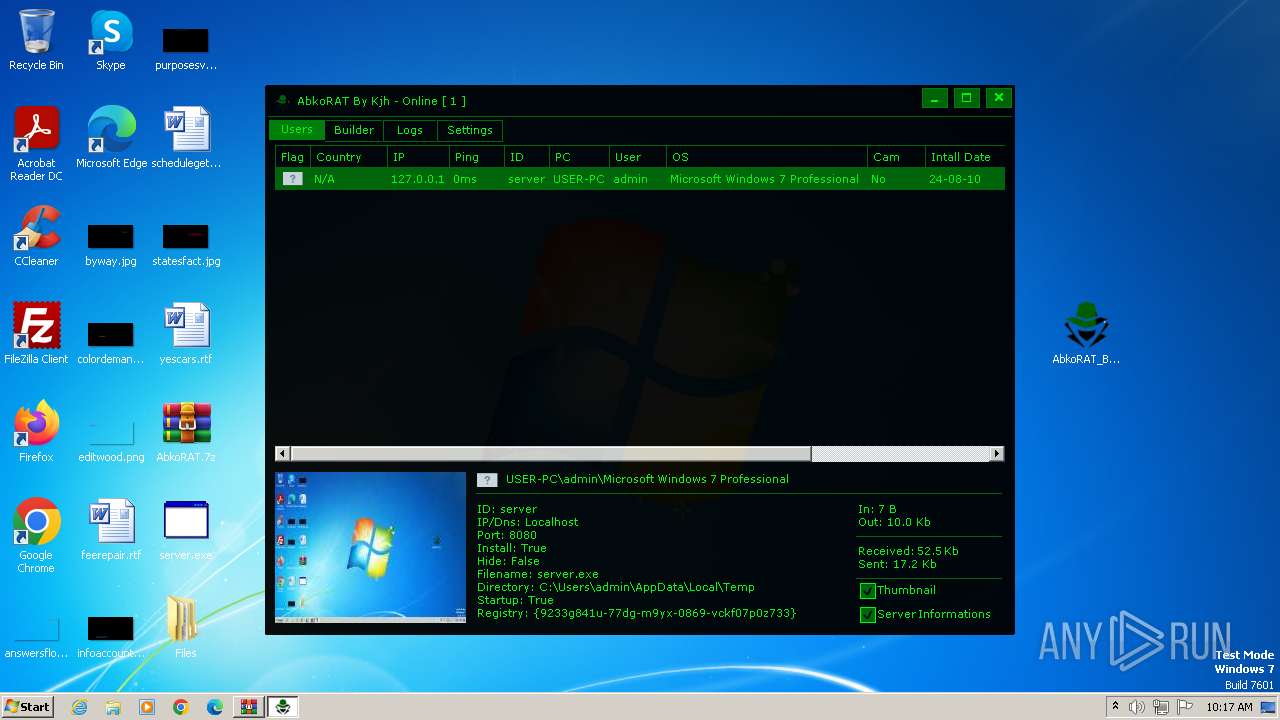
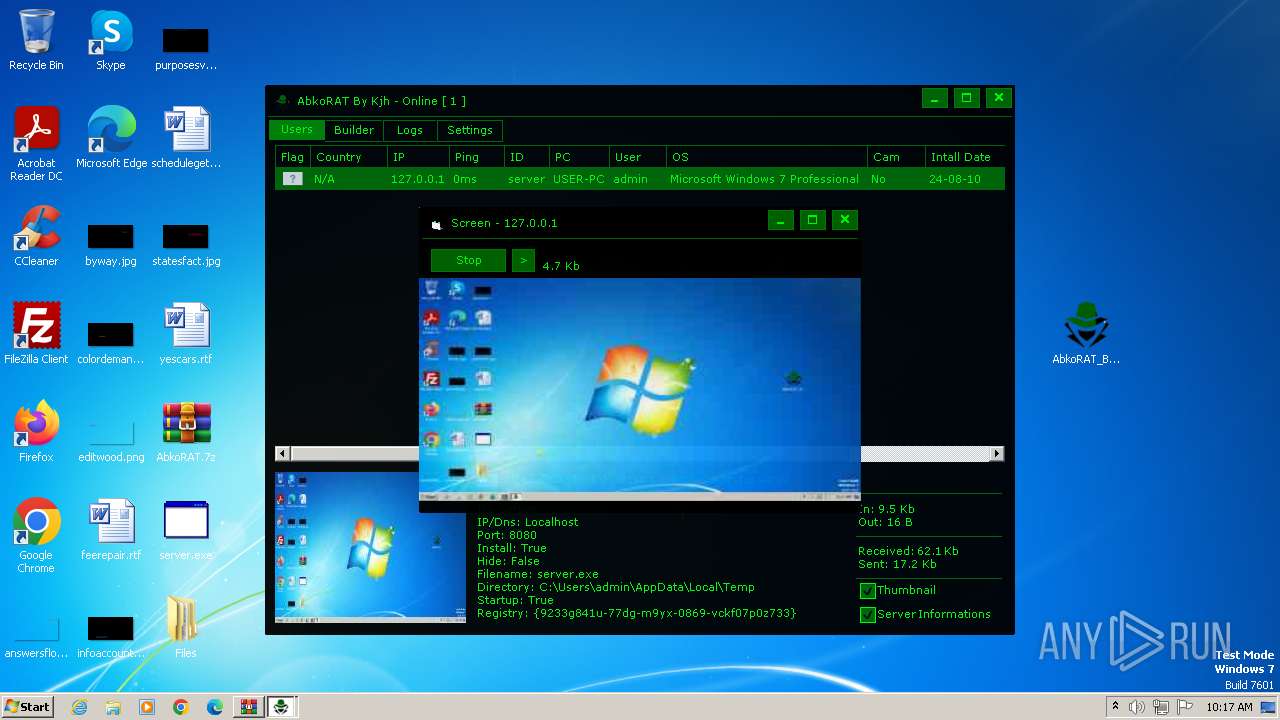
| 2156 | "C:\Users\admin\AppData\Local\Temp\server.exe" | C:\Users\admin\AppData\Local\Temp\server.exe | server.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 1.0.0.0 Modules
| |||||||||||||||
| 2776 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\AbkoRAT.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3536 | "C:\Users\admin\Desktop\AbkoRAT_By_Kjh.exe" | C:\Users\admin\Desktop\AbkoRAT_By_Kjh.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: AbkoRAT Version: 1.0.0.0 Modules
| |||||||||||||||
| 3628 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3724 | "C:\Users\admin\Desktop\server.exe" | C:\Users\admin\Desktop\server.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
8 034
Read events
8 009
Write events
25
Delete events
0
Modification events
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AbkoRAT.7z | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3536 | AbkoRAT_By_Kjh.exe | C:\Users\admin\Desktop\server.exe | executable | |
MD5:99DB29D2F00E82693272C0A3420C5D1B | SHA256:ECDE0AA65A80D4E8C4CF78163D366C325ADF88546B9D85B496B4DD000F49C578 | |||
| 3536 | AbkoRAT_By_Kjh.exe | C:\Users\admin\Desktop\Files\USER-PC_admin_Microsoft Windows 7 Professional\PC-Informations.txt | text | |
MD5:904B512790177D39D31448D15C93C53E | SHA256:A5964F443984B0250844FB01EE85DFD05F822B19E2CAFC009E558BC13F951F9E | |||
| 2776 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2776.19930\AbkoRAT_By_Kjh.exe | executable | |
MD5:BE74505360F04AD9E16A34D13344627F | SHA256:B9F374C7E415C1143AAB8E6D2AC26C682EDC7E5442BE1DB1A9B604DD58A29038 | |||
| 3536 | AbkoRAT_By_Kjh.exe | C:\Users\admin\AppData\Local\Temp\_ght\stub.ght | executable | |
MD5:C28079388C1DD0661FE749AA3F7985F9 | SHA256:ABD99180097530234A1BE4E9433D2A6C34F841C67FAEEAEBAC4B3F118449EE43 | |||
| 3536 | AbkoRAT_By_Kjh.exe | C:\Users\admin\AppData\Local\Temp\_ght\Config.dat | text | |
MD5:B15D8E026F569F11452F731C7D7FF338 | SHA256:A6A464C7ED1CE52BA4C26B656DD0FFBC1B6DAB447906B7F07C9B7D05472C4AA9 | |||
| 3724 | server.exe | C:\Users\admin\AppData\Local\Temp\server.exe | executable | |
MD5:99DB29D2F00E82693272C0A3420C5D1B | SHA256:ECDE0AA65A80D4E8C4CF78163D366C325ADF88546B9D85B496B4DD000F49C578 | |||
| 3536 | AbkoRAT_By_Kjh.exe | C:\Users\admin\AppData\Local\Temp\_ght\GeoIP.dat | binary | |
MD5:1F897B5825CF91799831862620911AFF | SHA256:5F85518CF71E7B53544E0BD0C1874D1F89A0D6DE7A6AD50683517575AAA56301 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f69642324cc87bd | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1060 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
AbkoRAT_By_Kjh.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|