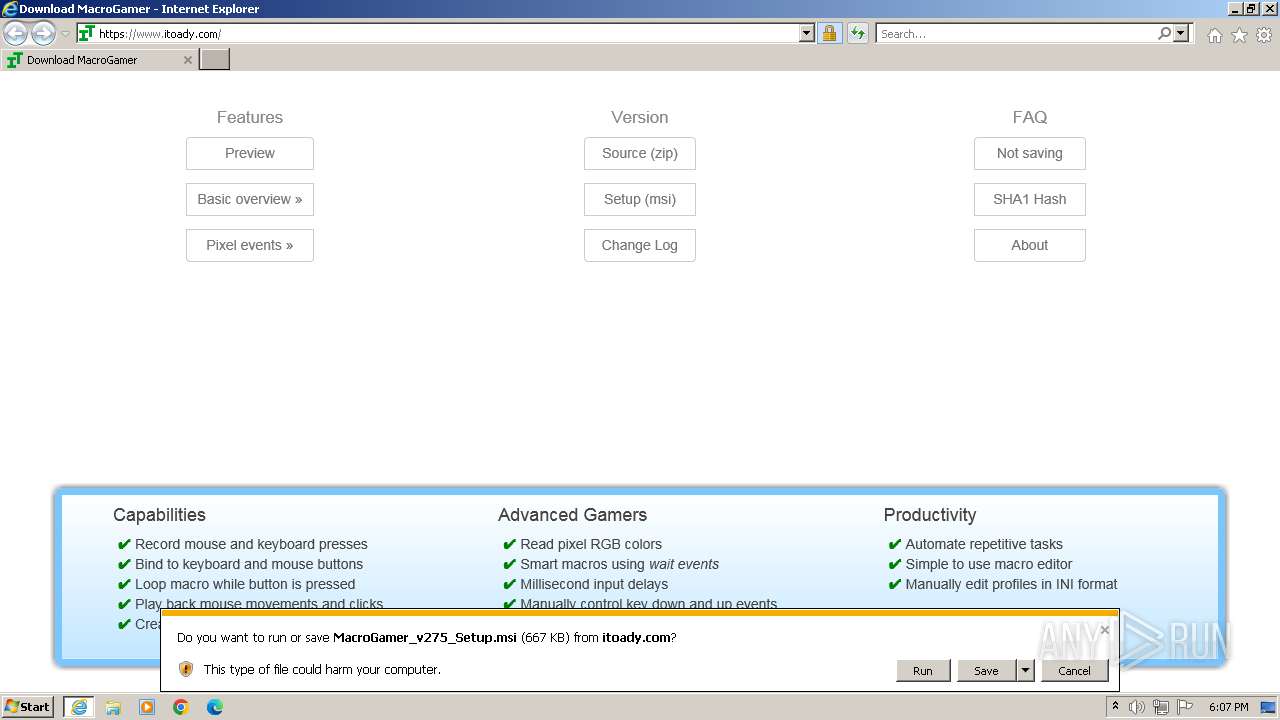
| URL: | https://www.itoady.com/ |
| Full analysis: | https://app.any.run/tasks/082278c0-6dff-4f72-bb1d-39deaec2fafa |
| Verdict: | Malicious activity |
| Analysis date: | November 19, 2023, 18:06:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | AD227854D6E2D00AAB5329204D69D3505919AE5F |
| SHA256: | D87A8E792A99C4B75DE4F7B81CC4814A3B509815AE88052677591A15357ACABE |
| SSDEEP: | 3:N8DSLZyTK:2OLZt |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 4056)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 3676)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3812)
- MacroGamer.exe (PID: 1272)
- msiexec.exe (PID: 4056)
Manual execution by a user
- wmpnscfg.exe (PID: 3812)
- MacroGamer.exe (PID: 1272)
Application launched itself
- iexplore.exe (PID: 3416)
Reads the computer name
- wmpnscfg.exe (PID: 3812)
- msiexec.exe (PID: 4056)
- MacroGamer.exe (PID: 1272)
Creates files or folders in the user directory
- msiexec.exe (PID: 4056)
Create files in a temporary directory
- MacroGamer.exe (PID: 1272)
- msiexec.exe (PID: 4056)
The process uses the downloaded file
- iexplore.exe (PID: 3416)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3812)
- msiexec.exe (PID: 4056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
45
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1272 | "C:\Users\admin\Documents\MacroGamer\MacroGamer.exe" | C:\Users\admin\Documents\MacroGamer\MacroGamer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3, 2, 4, 9 Modules
| |||||||||||||||
| 3308 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3416 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3416 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.itoady.com/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3676 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3812 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
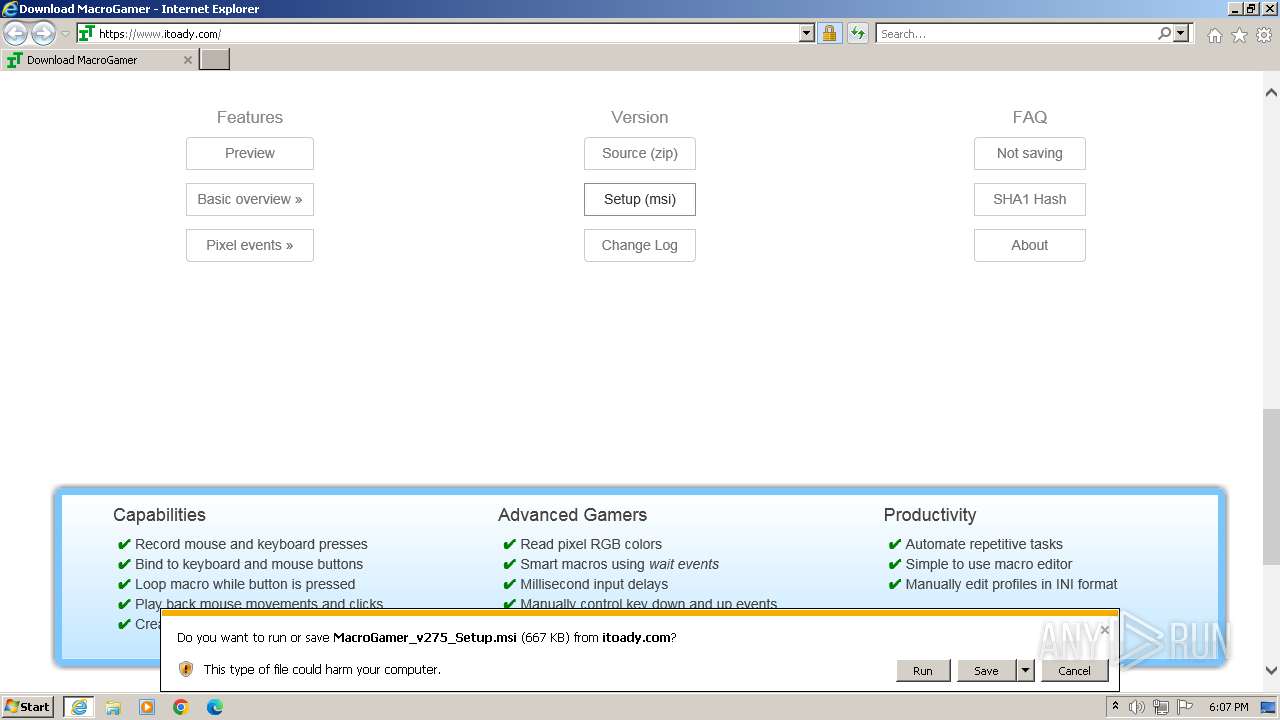
| 3964 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MacroGamer_v275_Setup.msi" | C:\Windows\System32\msiexec.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4056 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
20 943
Read events
20 847
Write events
83
Delete events
13
Modification events
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
6
Suspicious files
55
Text files
83
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:35BED15E3EF373F7D4BBA45E5C0D89E4 | SHA256:925CA1491CE3F9496B132EC78D565464D43082CC83BF9F73066C6A02F60472CE | |||
| 3308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:BE64B7F193EC9317681EFE89B3482799 | SHA256:9C8A363F4B68256BD7A56A2B5B282389A94B10885013C8DBD9775C7FFA7AE80A | |||
| 3308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:C1FC9B1DC67C5C0C7743B919B02F8F9F | SHA256:82A48DE5C9A7835DE925006B1C651F94AC8FB31222FC9C9D639C0BD1C1A8872E | |||
| 3308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:3C94CC624029C43CE7C271D19EE52ABC | SHA256:95363EE5D5C0AC289432379CE7EFB578BE22C85113232670DE6C84F19C6870AE | |||
| 3308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3308 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\LYT0WC1T.txt | text | |
MD5:68C1D1ED2928BB8B596FBB417F67BCA9 | SHA256:A0DE5D557149DDCBF49319EA297C2A1D7502890ADD51B1C17AB0723265A37477 | |||
| 3308 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\mg_preview_1_tran[1].png | image | |
MD5:0662CFA100C827CAF78DCFA62B9A3761 | SHA256:A1F012E2F18659CED6BBDE845D236F63429104F6D205FC945CEF7C7DE1C6FAB1 | |||
| 3308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:0476EC9F054DBC7798505B690F9CBE60 | SHA256:402383D571C6DB35A3A607A2C2D3A341C299CA103AA1CB85C2224E038D9117BE | |||
| 3308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 3308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_9A80F5225FC4BA17E71B590CABC426DB | binary | |
MD5:534EEC0D205001EB05ECEF742ECDC9C7 | SHA256:C262A9967AA509E8DCADEC52892CB3816874E4DD1CF27F672D34DCD51890C7B4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
62
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3308 | iexplore.exe | GET | 200 | 8.253.207.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d6bb2ad0af14907d | unknown | compressed | 4.66 Kb | unknown |
3308 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | unknown | binary | 2.01 Kb | unknown |
3308 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3308 | iexplore.exe | GET | 200 | 8.253.207.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a1f744e7e9e1d6c2 | unknown | compressed | 4.66 Kb | unknown |
3308 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEEYEdcdvM%2B0BEMsDuQBqQWU%3D | unknown | binary | 471 b | unknown |
3308 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCVN9Jf3G%2B1pAqd7QzTt1vx | unknown | binary | 472 b | unknown |
3308 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFYyRZRleaQREjdgJW3R1jM%3D | unknown | binary | 471 b | unknown |
3416 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | der | 471 b | unknown |
3308 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEDBPk217SOCuEsxRjJqpuUQ%3D | unknown | binary | 471 b | unknown |
3308 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCLPpgizFvtXApe3cL6kC3u | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3308 | iexplore.exe | 50.63.8.219:443 | www.itoady.com | GO-DADDY-COM-LLC | US | unknown |
3308 | iexplore.exe | 8.253.207.121:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3308 | iexplore.exe | 192.124.249.24:80 | ocsp.godaddy.com | SUCURI-SEC | US | unknown |
3308 | iexplore.exe | 216.58.212.130:443 | pagead2.googlesyndication.com | GOOGLE | US | whitelisted |
3308 | iexplore.exe | 216.58.206.40:443 | www.googletagmanager.com | GOOGLE | US | unknown |
3308 | iexplore.exe | 142.250.186.78:443 | apis.google.com | GOOGLE | US | whitelisted |
3308 | iexplore.exe | 142.250.185.67:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3308 | iexplore.exe | 142.250.185.110:443 | fundingchoicesmessages.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.itoady.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
partner.googleadservices.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fundingchoicesmessages.google.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |