| File name: | mimikatz-master.zip |
| Full analysis: | https://app.any.run/tasks/63a58116-15e0-4680-a587-8e03bd76e9e5 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2023, 10:13:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 85061FB539F0E118805729C0D9EFA99E |
| SHA1: | 478BAB67C2525E1B195622E718D1D07FD0D46774 |
| SHA256: | D86E5D2701B548DFBE0419BCFFB2AE82C6CCDEB6DC9612050273C543A6F5215A |
| SSDEEP: | 24576:qwvlkGmFoHjZkvEp/DEyTo+dmH5Q3JR2RZV1GMZH9epNdWR:tviGmateEBBoYmZyR8ZDf9eBWR |
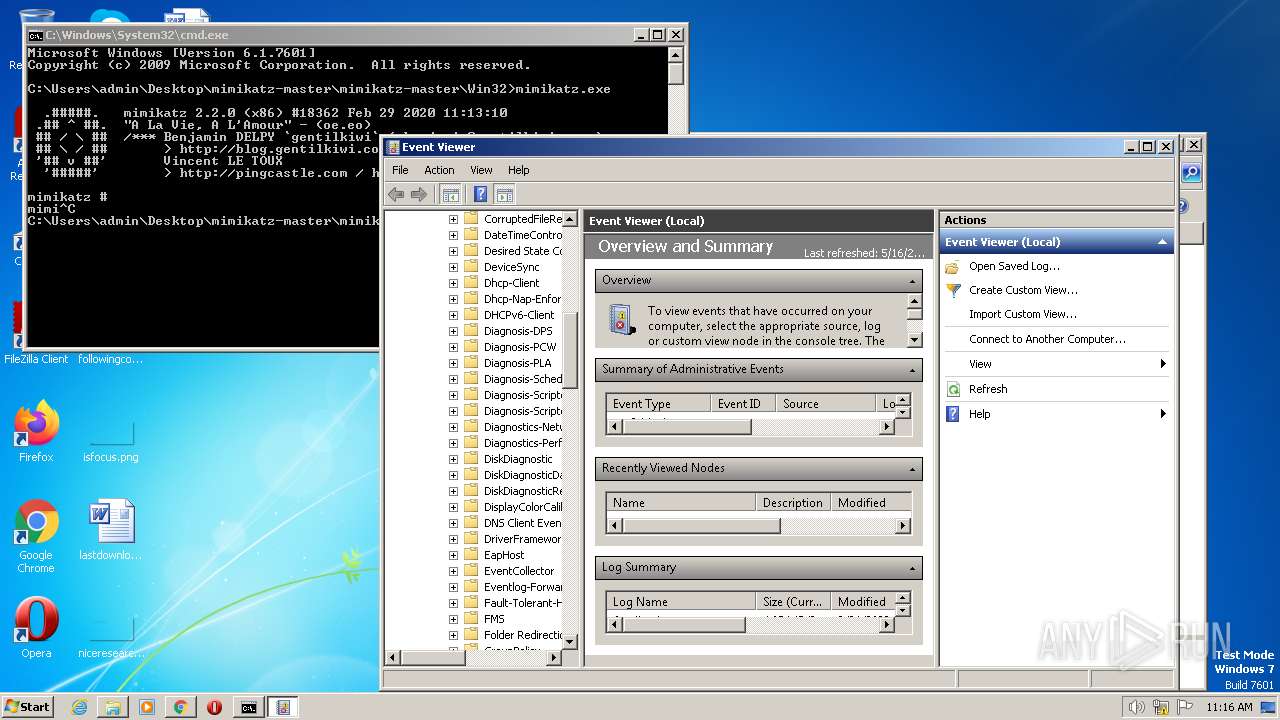
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3064)
Application was dropped or rewritten from another process
- mimikatz.exe (PID: 1756)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 3952)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3952)
Checks supported languages
- mimikatz.exe (PID: 1756)
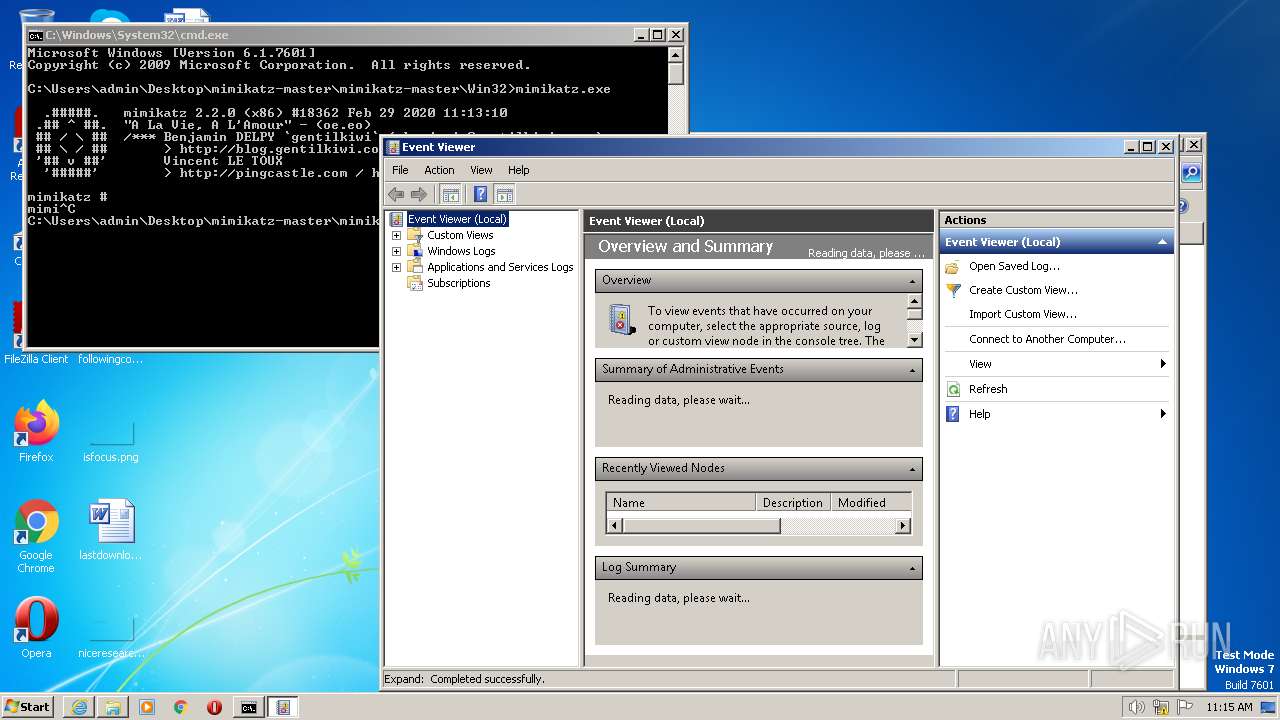
Manual execution by a user
- mmc.exe (PID: 1212)
- cmd.exe (PID: 1712)
- mmc.exe (PID: 3624)
- chrome.exe (PID: 3552)
The process checks LSA protection
- mimikatz.exe (PID: 1756)
- mmc.exe (PID: 1212)
Reads the computer name
- mimikatz.exe (PID: 1756)
Creates files in the program directory
- mmc.exe (PID: 1212)
Application launched itself
- chrome.exe (PID: 3552)
Create files in a temporary directory
- chrome.exe (PID: 3552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | mimikatz-master/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2020:03:02 17:00:44 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
75
Monitored processes
34
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,1366084324531128810,3519214226035930718,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2308 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1048,1366084324531128810,3519214226035930718,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3000 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 656 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1048,1366084324531128810,3519214226035930718,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2720 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1048,1366084324531128810,3519214226035930718,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1672 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1048,1366084324531128810,3519214226035930718,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1256 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1212 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\eventvwr.msc" /s | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6dd7d988,0x6dd7d998,0x6dd7d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,1366084324531128810,3519214226035930718,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3196 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1048,1366084324531128810,3519214226035930718,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1060 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1648 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,1366084324531128810,3519214226035930718,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1948 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
12 104
Read events
11 972
Write events
124
Delete events
8
Modification events
| (PID) Process: | (3952) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
14
Suspicious files
145
Text files
147
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3952 | WinRAR.exe | C:\Users\admin\Desktop\mimikatz-master\mimikatz-master\Win32\mimilib.dll | executable | |
MD5:B89FD300420F7F8AA506177CC230A824 | SHA256:2B202A389838E59A7E19BCB8F1280CF339DE49D23B37C2FF2028DA9924D8ED0D | |||
| 3952 | WinRAR.exe | C:\Users\admin\Desktop\mimikatz-master\mimikatz-master\Win32\mimilove.exe | executable | |
MD5:5B25C78E900658105BC64F0A31B10656 | SHA256:EAC47B3BA3C4A035D4FB8ABE0B5531D7F23F1D803B0C784F25CDF68C27520C77 | |||
| 3952 | WinRAR.exe | C:\Users\admin\Desktop\mimikatz-master\mimikatz-master\debian\dirs | text | |
MD5:B5FE6359B29A35BE2E07F690DDC900E2 | SHA256:AF15BB63F4A5343CE280D4AEC375C0EB593C9740267C48F7C34DA28EA6D534B2 | |||
| 3552 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-646357E4-DE0.pma | — | |
MD5:— | SHA256:— | |||
| 3952 | WinRAR.exe | C:\Users\admin\Desktop\mimikatz-master\mimikatz-master\README.md | text | |
MD5:CD6C6858D2E48DF55978E2006F39B171 | SHA256:56E362B25B365AB16793F15C29F5F05AC6A38A4BFC3D2B38B3A1FCC060B12DEB | |||
| 3952 | WinRAR.exe | C:\Users\admin\Desktop\mimikatz-master\mimikatz-master\Win32\mimikatz.exe | executable | |
MD5:46F366E3EE36C05AB5A7A319319F7C72 | SHA256:2E8092205A2DED4B07E9D10D0EC02EBA0FFCF1D370CAB88C5221A749915F678A | |||
| 3952 | WinRAR.exe | C:\Users\admin\Desktop\mimikatz-master\mimikatz-master\debian\watch | text | |
MD5:A1BF8DCA579F7D169B060A752DD07732 | SHA256:8F74F22608B0F21871352DE72DCF43DF2B89D4787DAB12F153BBD6F371A09FD9 | |||
| 3952 | WinRAR.exe | C:\Users\admin\Desktop\mimikatz-master\mimikatz-master\debian\mimikatz.install | text | |
MD5:B512D3BF8BA6BD36CDA73309F50D2033 | SHA256:2135BC3D34D6FB7AB786E94CAA58E8F8965A7AC8CCB0557CABCC57000F13D084 | |||
| 3952 | WinRAR.exe | C:\Users\admin\Desktop\mimikatz-master\mimikatz-master\debian\compat | text | |
MD5:7C5ABA41F53293B712FD86D08ED5B36E | SHA256:2E6D31A5983A91251BFAE5AEFA1C0A19D8BA3CF601D0E8A706B4CFA9661A6B8A | |||
| 3952 | WinRAR.exe | C:\Users\admin\Desktop\mimikatz-master\mimikatz-master\x64\mimilib.dll | executable | |
MD5:EB05429D25FC57B476428CDB0A134B2F | SHA256:7FFCE7F6D7262F214D78E6B7FD8D07119835CBA4B04CE334260665D7C8FB369A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
45
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvODJiQUFYYVJaZ0k5di1hUFlXS1prX2xDZw/1.0.0.13_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | — | — | whitelisted |
1012 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adboneuub4b4fwlwyx74lytiok3q_2958/jflookgnkcckhobaglndicnbbgbonegd_2958_all_ii2pcs4aybmmcz3egawzik4eom.crx3 | US | binary | 9.36 Kb | whitelisted |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adboneuub4b4fwlwyx74lytiok3q_2958/jflookgnkcckhobaglndicnbbgbonegd_2958_all_ii2pcs4aybmmcz3egawzik4eom.crx3 | US | binary | 4.02 Kb | whitelisted |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/m2zcx4ofgjns4ti4b476evxtiy_7995/hfnkpimlhhgieaddgfemjhofmfblmnib_7995_all_adykk2tbs4yfm5e7pjzpgkgqnrjq.crx3 | US | binary | 40.0 Kb | whitelisted |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/eua6zlfhpj3roq46nymxtbz4zq_2022.10.19.1145/ggkkehgbnfjpeggfpleeakpidbkibbmn_2022.10.19.1145_all_ac7cecrzrmfngskhgmtk6zmhfjoa.crx3 | US | binary | 38.2 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adboneuub4b4fwlwyx74lytiok3q_2958/jflookgnkcckhobaglndicnbbgbonegd_2958_all_ii2pcs4aybmmcz3egawzik4eom.crx3 | US | binary | 38.2 Kb | whitelisted |
852 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/jewvegtcs2qdew3nlzz4kvsjqm_9.44.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.44.0_all_pywouuhjzu3khiqqvvfs2jt53q.crx3 | US | binary | 40.0 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjg0QUFYSnN4MFUtaEQwNDZqVGRkVkFmZw/1.0.6.0_aemomkdncapdnfajjbbcbdebjljbpmpj.crx | US | binary | 4.02 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adboneuub4b4fwlwyx74lytiok3q_2958/jflookgnkcckhobaglndicnbbgbonegd_2958_all_ii2pcs4aybmmcz3egawzik4eom.crx3 | US | binary | 9.59 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3404 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3552 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1012 | chrome.exe | 142.250.187.141:443 | accounts.google.com | GOOGLE | US | unknown |
1012 | chrome.exe | 172.217.17.132:443 | www.google.com | GOOGLE | US | whitelisted |
1012 | chrome.exe | 142.250.185.195:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
1012 | chrome.exe | 142.250.185.78:443 | clients2.google.com | GOOGLE | US | whitelisted |
1012 | chrome.exe | 142.250.186.42:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
1012 | chrome.exe | 216.58.212.129:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
Threats
Process | Message |
|---|---|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|
mmc.exe | Getting next publisher from enum failed-259-No more data is available
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|
mmc.exe | ExpandNode:After EventsNode:InsertChildren CountOfChildren = 5
|
mmc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
mmc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|