| File name: | COEYZ_Donotrunme.bat |
| Full analysis: | https://app.any.run/tasks/9eec0d9a-28b9-4ded-9c0f-cab763f4802d |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 21:54:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | A7C030C2D78CB956A5623F73DD184E96 |
| SHA1: | CC2C72D6C0635707F913DC8E5CBD513AB44F72B5 |
| SHA256: | D8622CE0580A2012AAE4DD6B5446E53D58F72071992240434966F6952F03AB93 |
| SSDEEP: | 48:cfCd0SQq2m821/2uC2X2y4MOmrJ4yFJwAk8li72CaP5pFGIoeJlwaTC29A:cfq0SQC9OS4GSQx5pF/o/ |
MALICIOUS
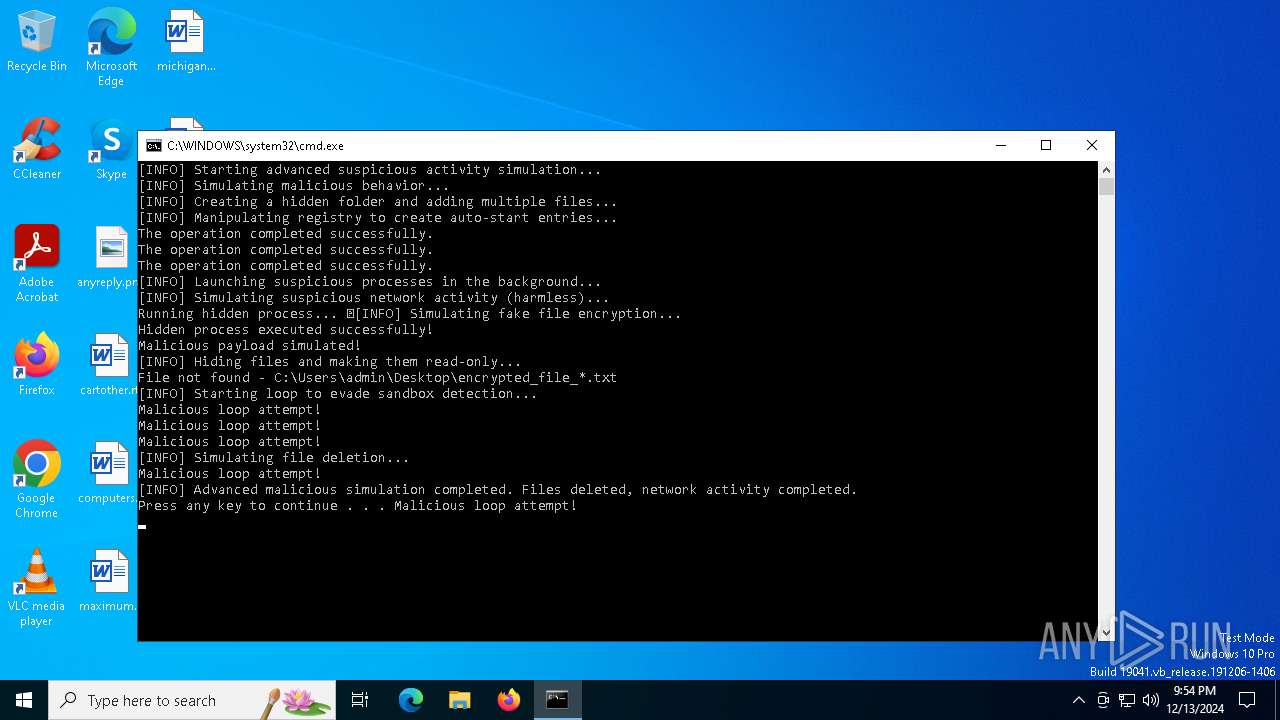
Changes the autorun value in the registry
- reg.exe (PID: 6520)
- reg.exe (PID: 6540)
- reg.exe (PID: 6560)
SUSPICIOUS
Process drops legitimate windows executable
- cmd.exe (PID: 6436)
Application launched itself
- cmd.exe (PID: 6436)
Executable content was dropped or overwritten
- cmd.exe (PID: 6436)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6436)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6436)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6436)
INFO
The sample compiled with english language support
- cmd.exe (PID: 6436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
132
Monitored processes
15
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6436 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\COEYZ_Donotrunme.bat" " | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6496 | attrib +h C:\Users\admin\AppData\Local\HiddenFiles | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6520 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v "SuspiciousApp1" /t REG_SZ /d "C:\Windows\System32\notepad.exe" /f | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6540 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v "SuspiciousApp2" /t REG_SZ /d "C:\Windows\System32\calc.exe" /f | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6560 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v "SuspiciousApp3" /t REG_SZ /d "C:\Windows\System32\mspmsn.exe" /f | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6580 | cmd.exe /c "echo Running hidden process..." | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6588 | cmd.exe /c "echo Hidden process executed successfully!" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6604 | cmd.exe /c "echo Malicious payload simulated!" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6640 | attrib +h +r C:\Users\admin\Desktop\encrypted_file_*.txt | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
162
Read events
159
Write events
3
Delete events
0
Modification events
| (PID) Process: | (6520) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SuspiciousApp1 |
Value: C:\Windows\System32\notepad.exe | |||
| (PID) Process: | (6560) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SuspiciousApp3 |
Value: C:\Windows\System32\mspmsn.exe | |||
| (PID) Process: | (6540) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SuspiciousApp2 |
Value: C:\Windows\System32\calc.exe | |||
Executable files
6
Suspicious files
0
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6436 | cmd.exe | C:\Users\admin\Desktop\encrypted_file_2.exe | executable | |
MD5:5DA8C98136D98DFEC4716EDD79C7145F | SHA256:58189CBD4E6DC0C7D8E66B6A6F75652FC9F4AFC7CE0EBA7D67D8C3FEB0D5381F | |||
| 6436 | cmd.exe | C:\Users\admin\AppData\Local\HiddenFiles\hidden3.txt | text | |
MD5:91D31DC588584AA1F7FAEB4FAC2605EE | SHA256:C147210AB8031C681DBE20A8179180D39F795E937B8F6167F18E307E5B5CF736 | |||
| 6436 | cmd.exe | C:\Users\admin\Desktop\encrypted_file_3.exe | executable | |
MD5:5DA8C98136D98DFEC4716EDD79C7145F | SHA256:58189CBD4E6DC0C7D8E66B6A6F75652FC9F4AFC7CE0EBA7D67D8C3FEB0D5381F | |||
| 6436 | cmd.exe | C:\Users\admin\AppData\Local\HiddenFiles\hidden2.txt | text | |
MD5:12EB3B4649A0ED88266FCFFE30899E14 | SHA256:516874ABD4966B087E5EDC7F9A1F808CD6F63836666D1CB3CF96B532479BE2D1 | |||
| 6436 | cmd.exe | C:\Users\admin\Desktop\locked_2.txt | executable | |
MD5:5DA8C98136D98DFEC4716EDD79C7145F | SHA256:58189CBD4E6DC0C7D8E66B6A6F75652FC9F4AFC7CE0EBA7D67D8C3FEB0D5381F | |||
| 6436 | cmd.exe | C:\Users\admin\AppData\Local\HiddenFiles\hidden1.txt | text | |
MD5:B59918BE6F1EE3DD0EB1471025E8854C | SHA256:02C90A1647F48AD7D0B372B98C934F06DF1E2D94B9120E33C61F12B0C924B325 | |||
| 6436 | cmd.exe | C:\Users\admin\Desktop\locked_1.txt | executable | |
MD5:5DA8C98136D98DFEC4716EDD79C7145F | SHA256:58189CBD4E6DC0C7D8E66B6A6F75652FC9F4AFC7CE0EBA7D67D8C3FEB0D5381F | |||
| 6436 | cmd.exe | C:\Users\admin\Desktop\locked_3.txt | executable | |
MD5:5DA8C98136D98DFEC4716EDD79C7145F | SHA256:58189CBD4E6DC0C7D8E66B6A6F75652FC9F4AFC7CE0EBA7D67D8C3FEB0D5381F | |||
| 6436 | cmd.exe | C:\Users\admin\Desktop\encrypted_file_1.exe | executable | |
MD5:5DA8C98136D98DFEC4716EDD79C7145F | SHA256:58189CBD4E6DC0C7D8E66B6A6F75652FC9F4AFC7CE0EBA7D67D8C3FEB0D5381F | |||
| 6436 | cmd.exe | C:\Users\admin\Desktop\network_activity.txt | text | |
MD5:877A9C2116714DBDA8E7603D49CA276E | SHA256:BF08750870113AB2FCDD62E1F3743130C1009D34396E2F355A5562D054B31C76 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
17
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2356 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2356 | svchost.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2356 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2356 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2356 | svchost.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |