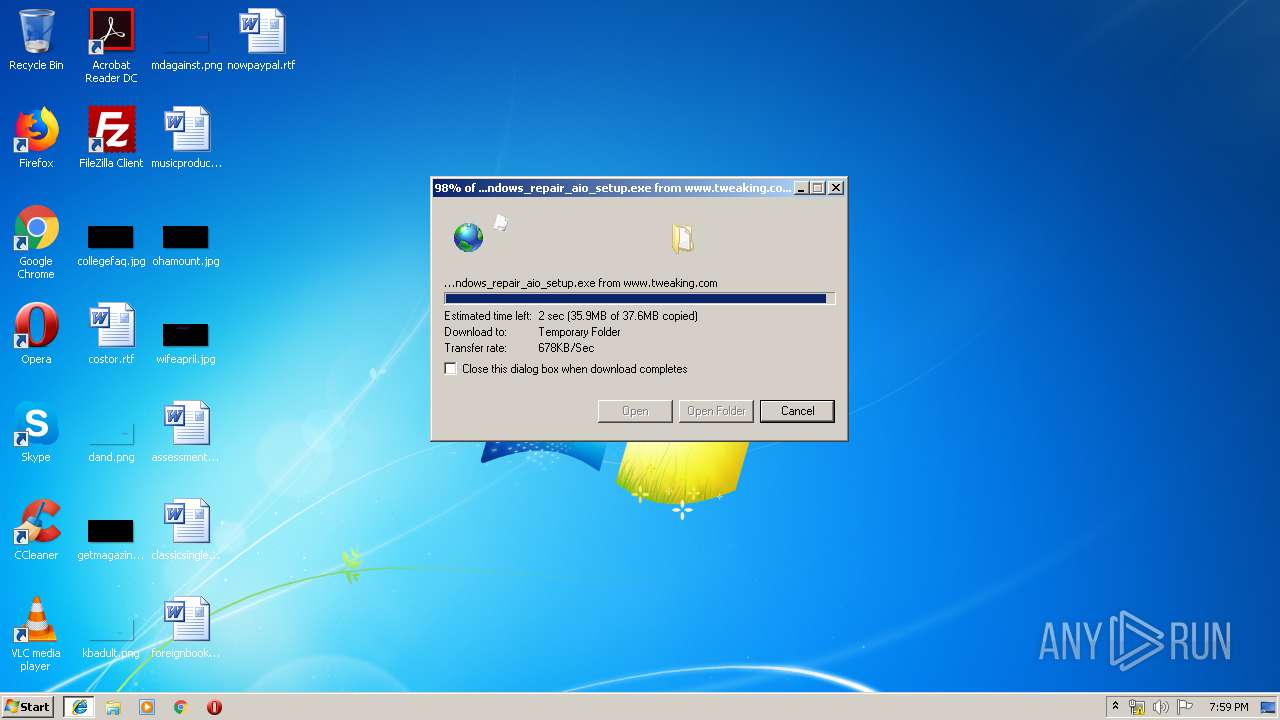
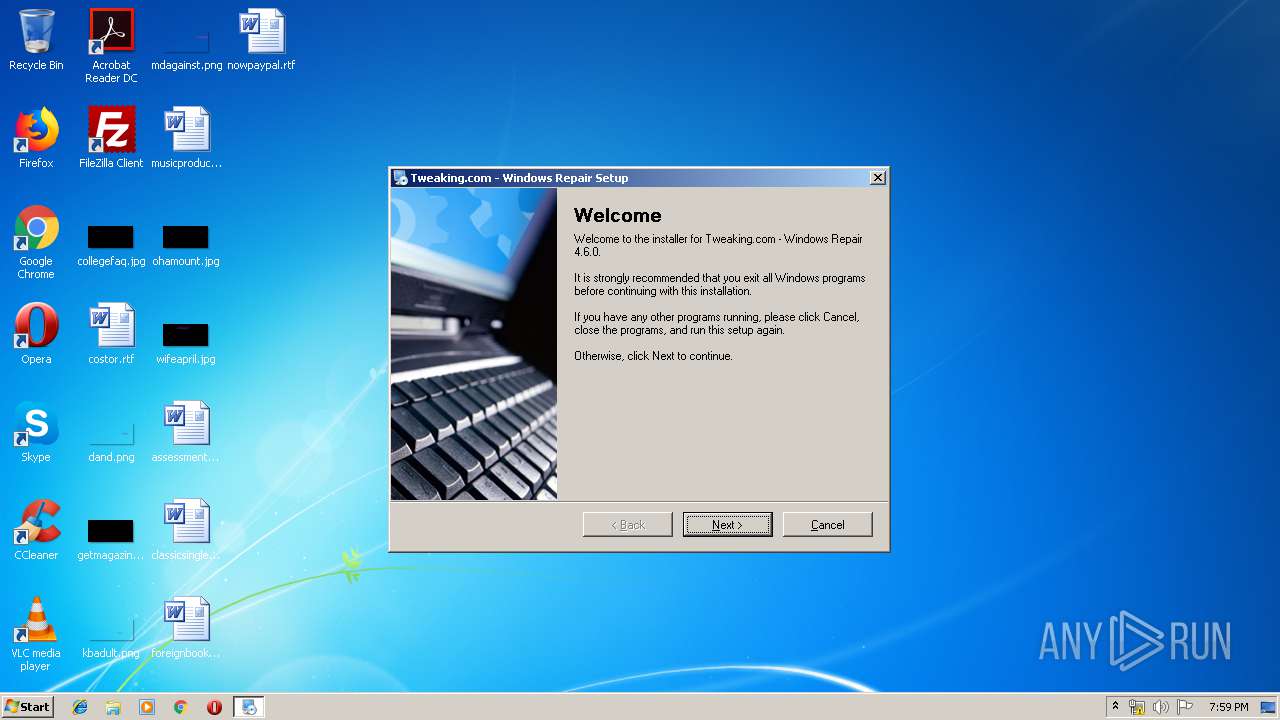
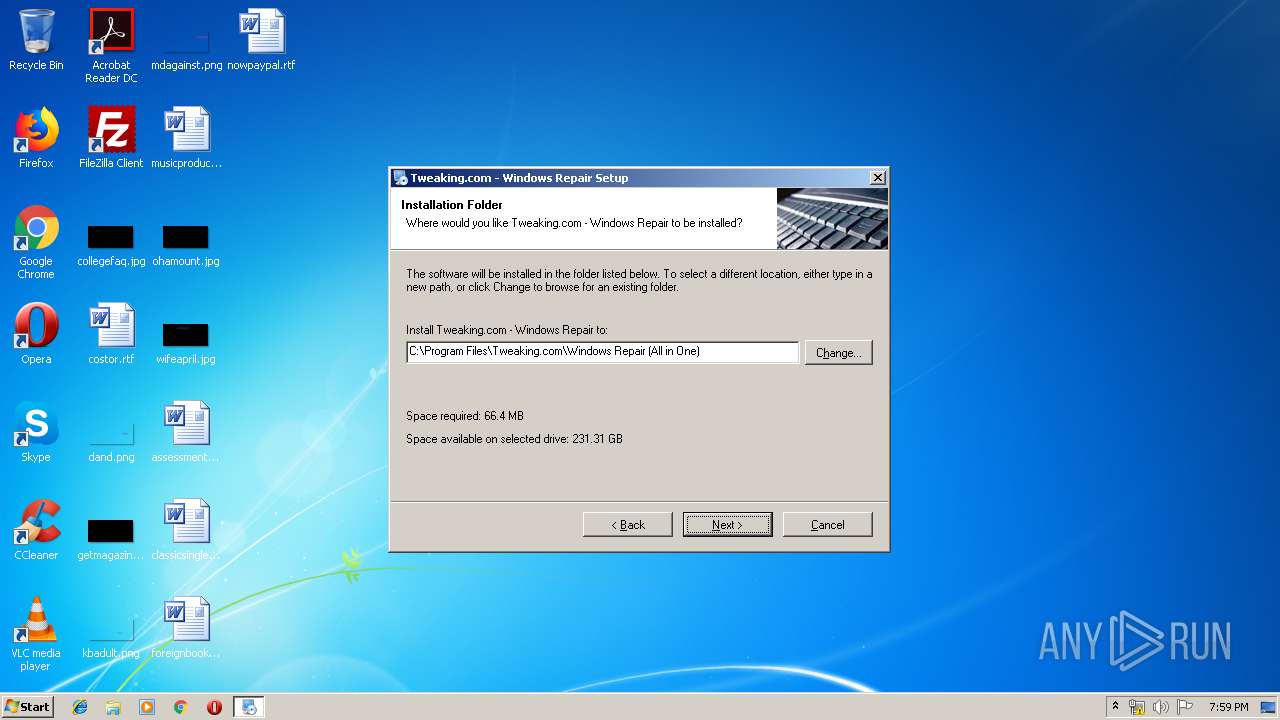
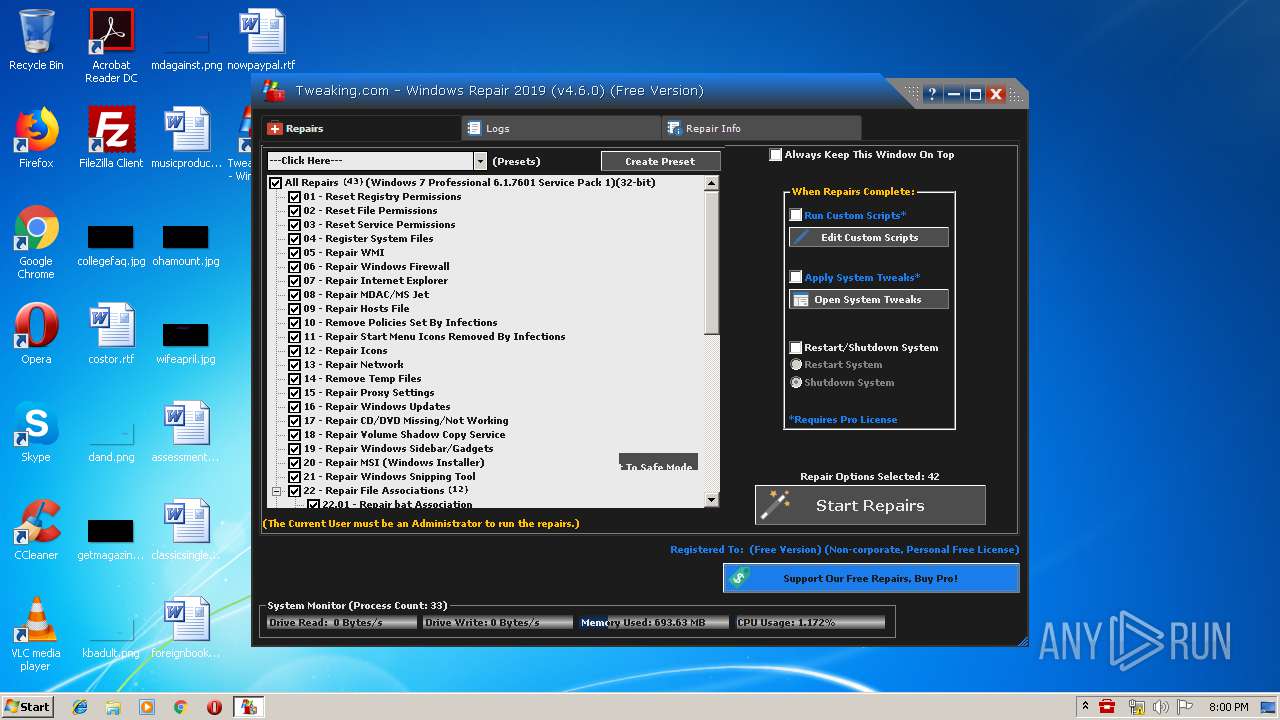
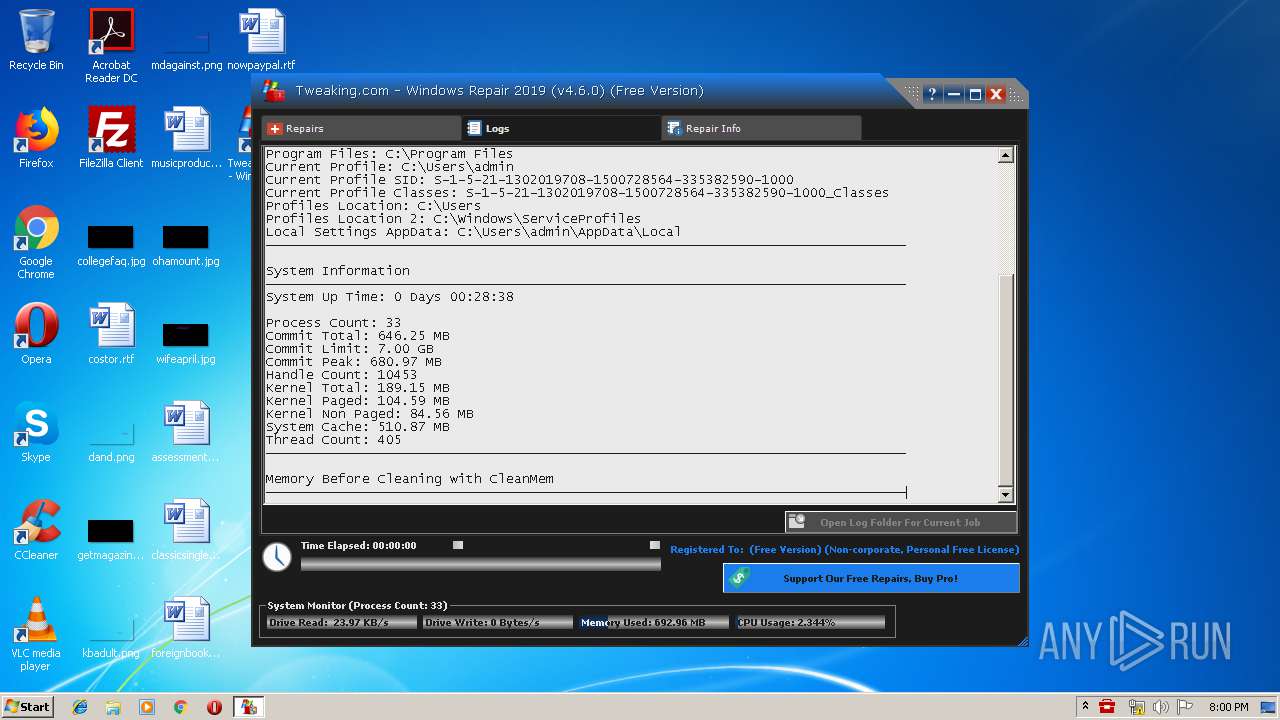
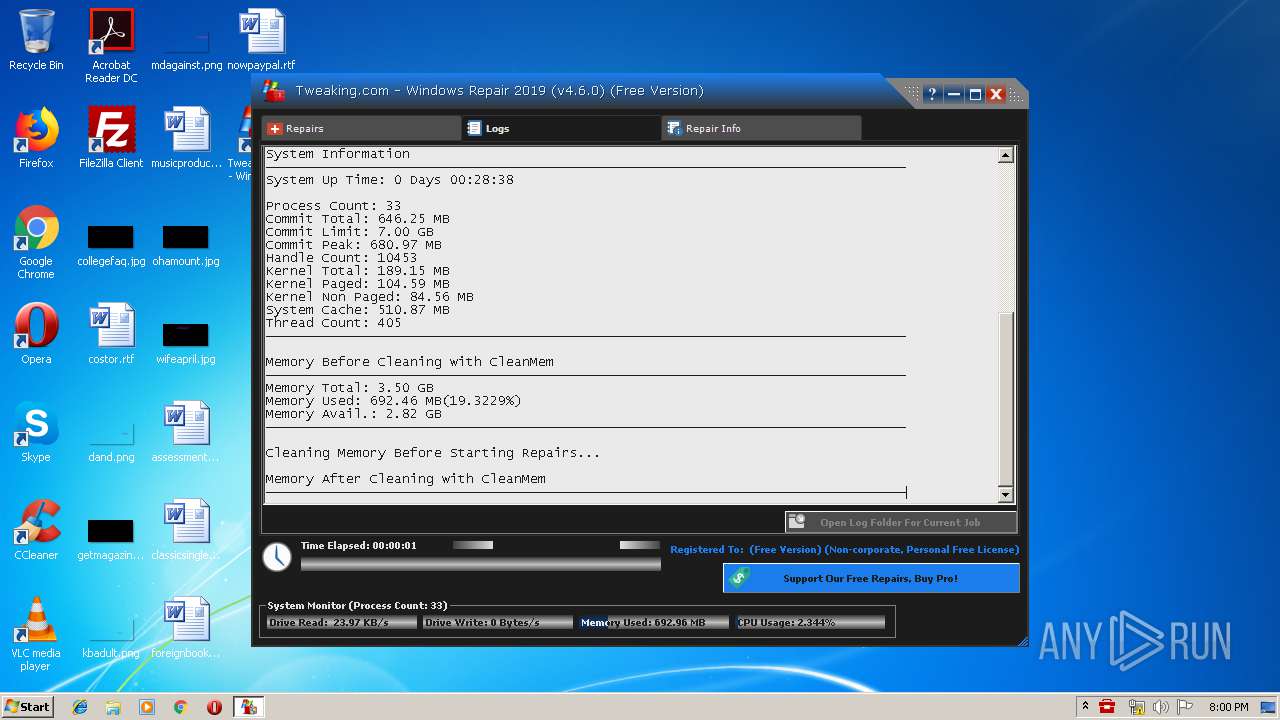
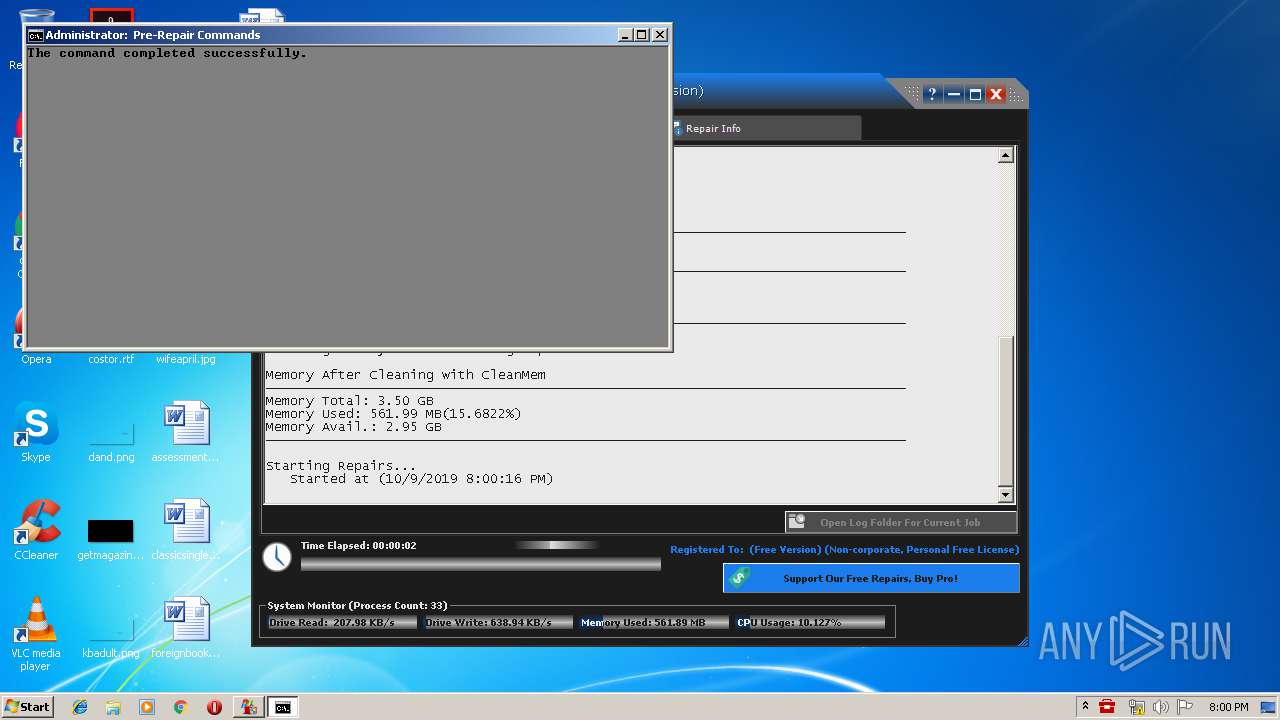
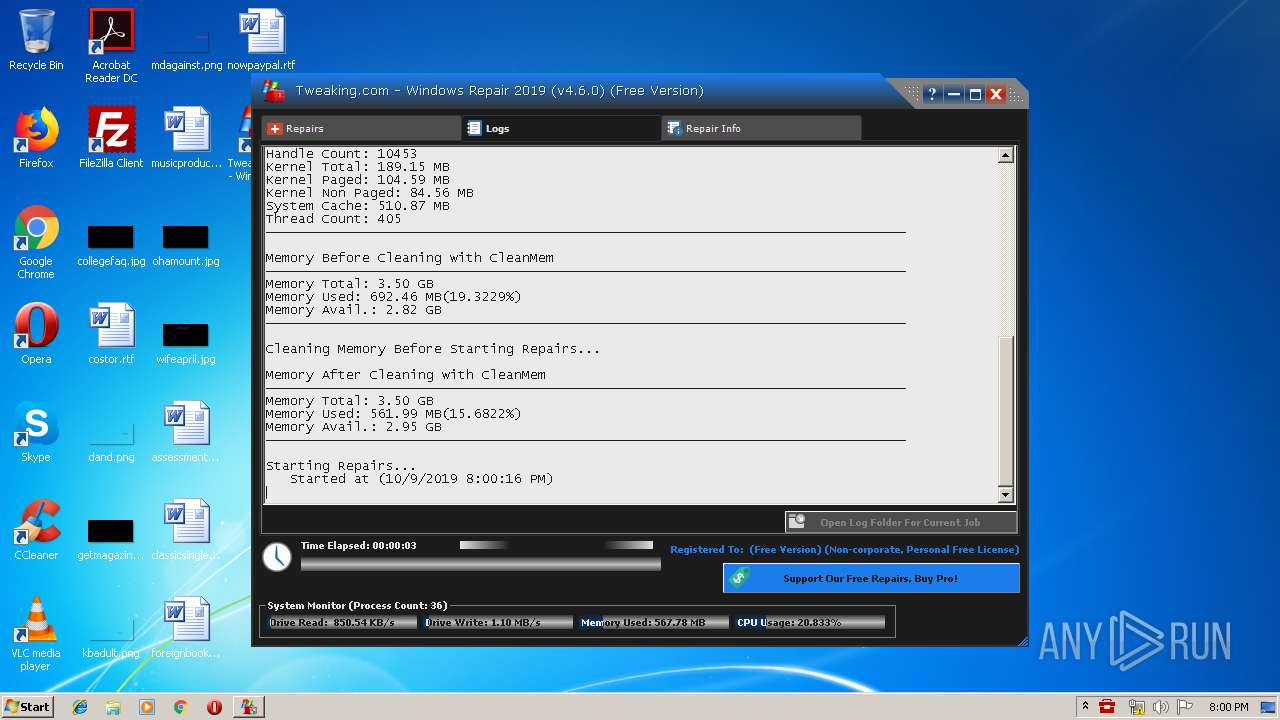
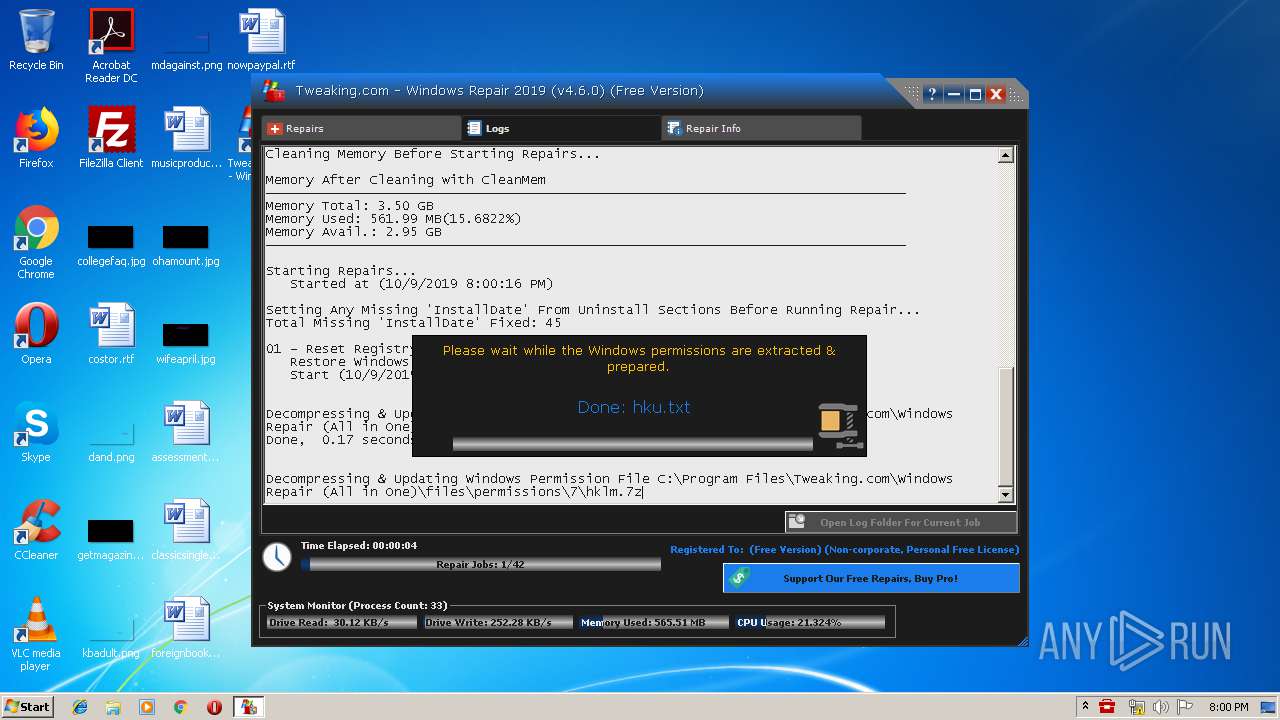
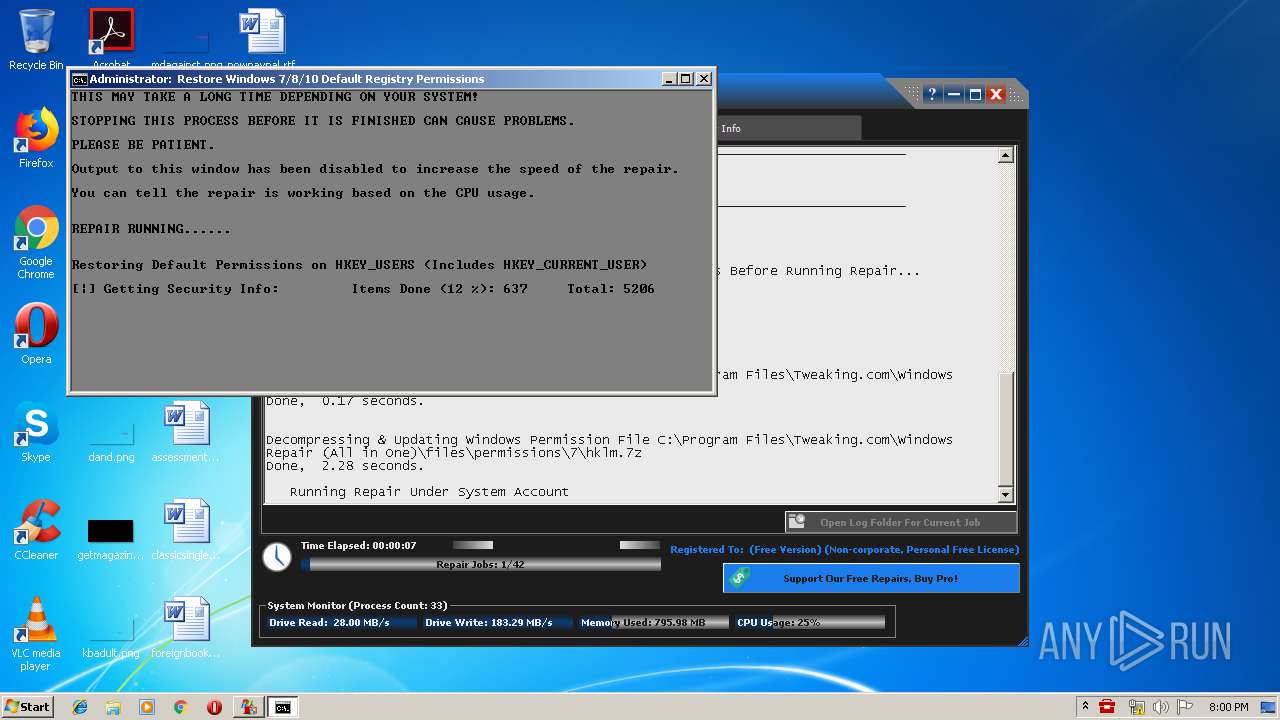
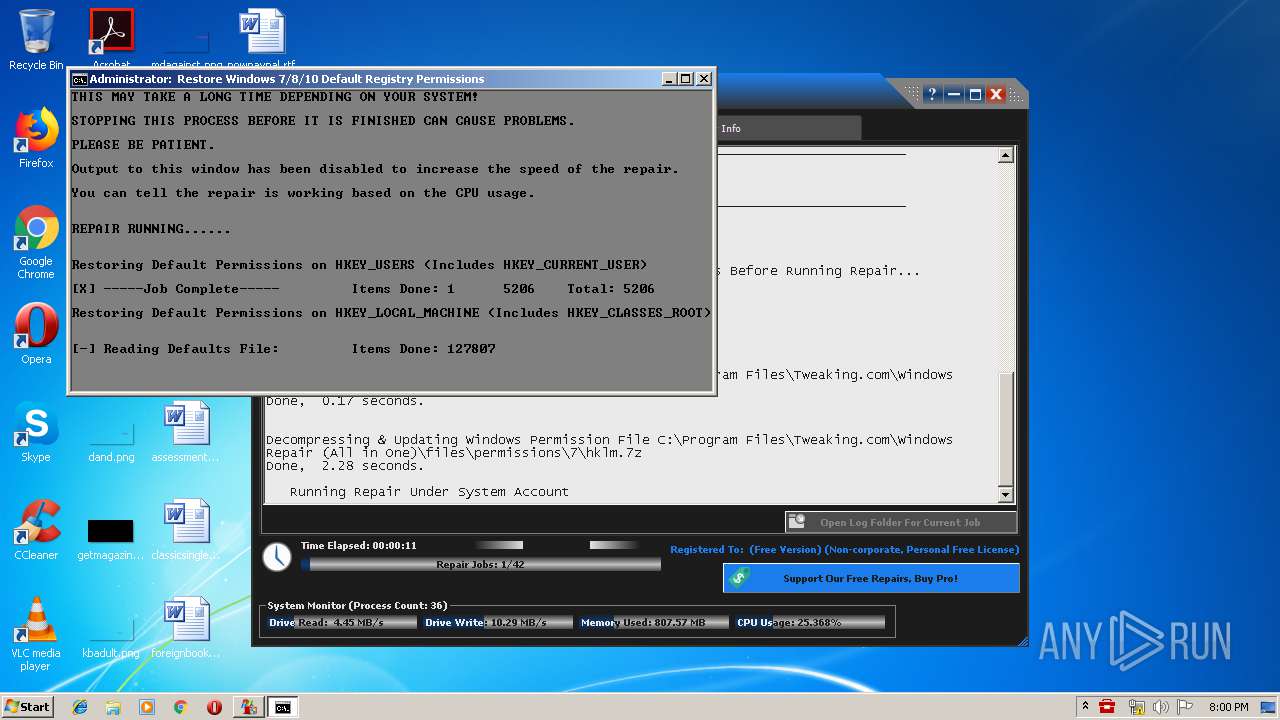
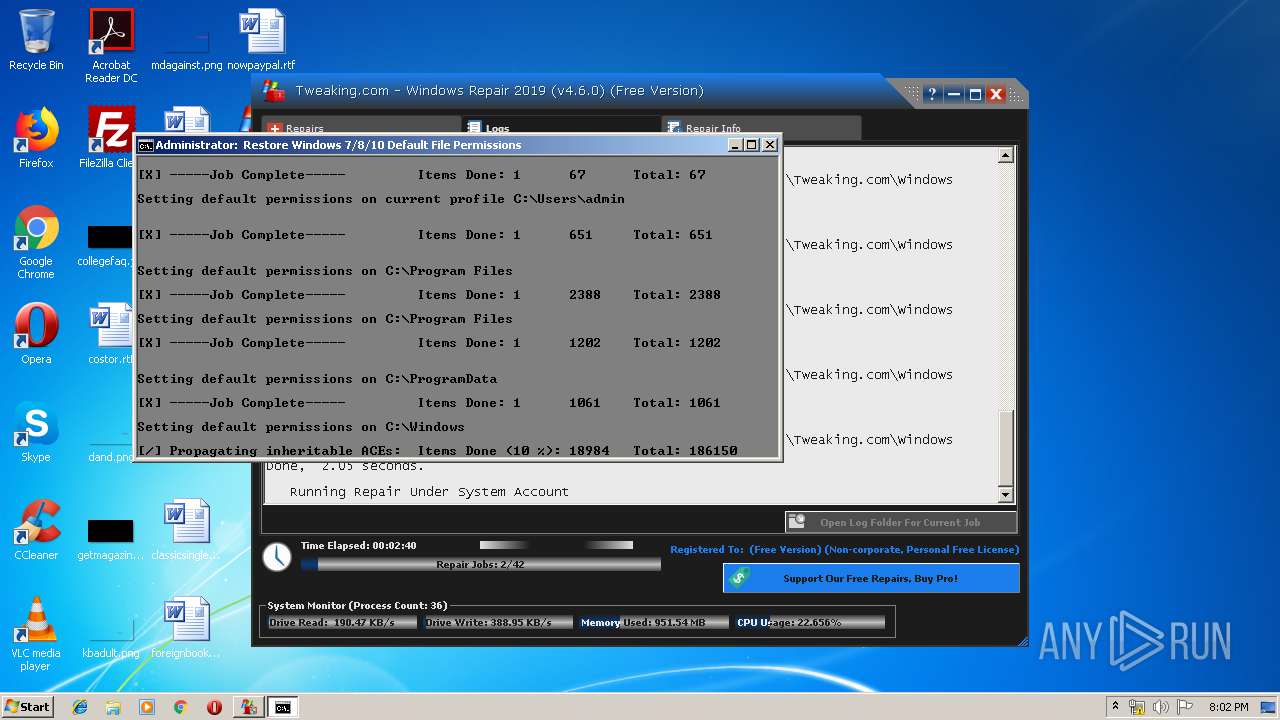
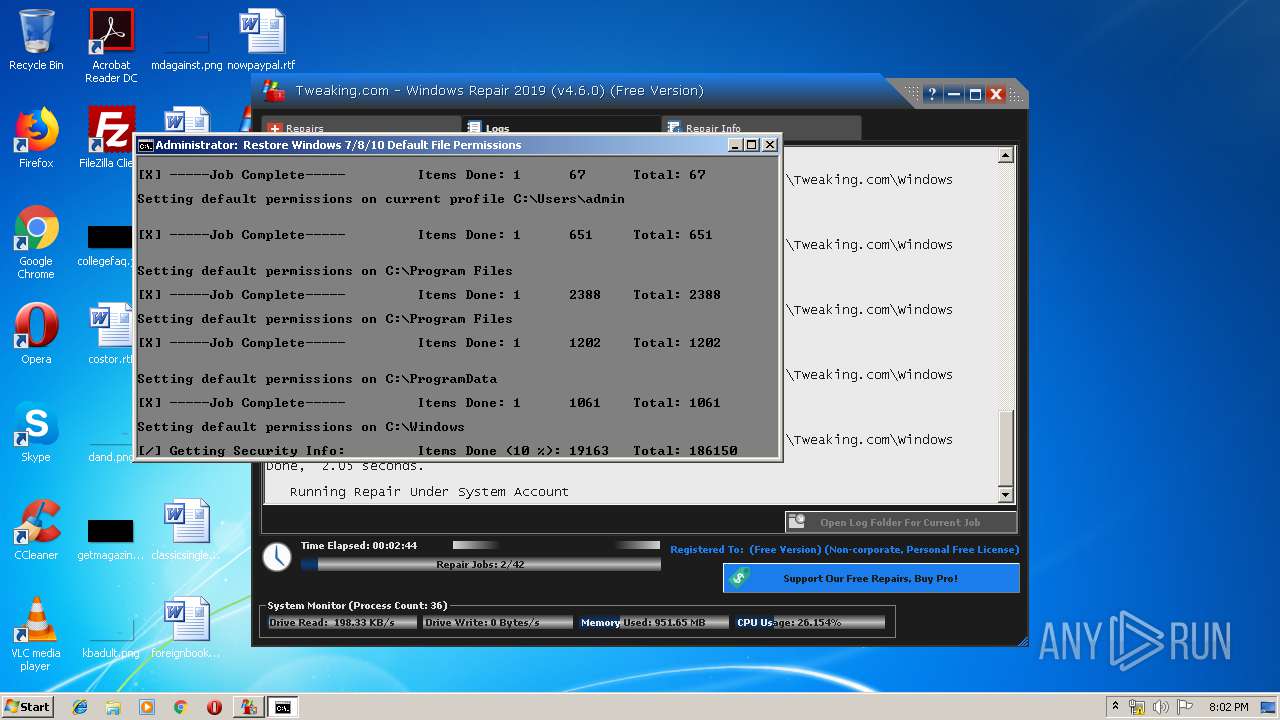
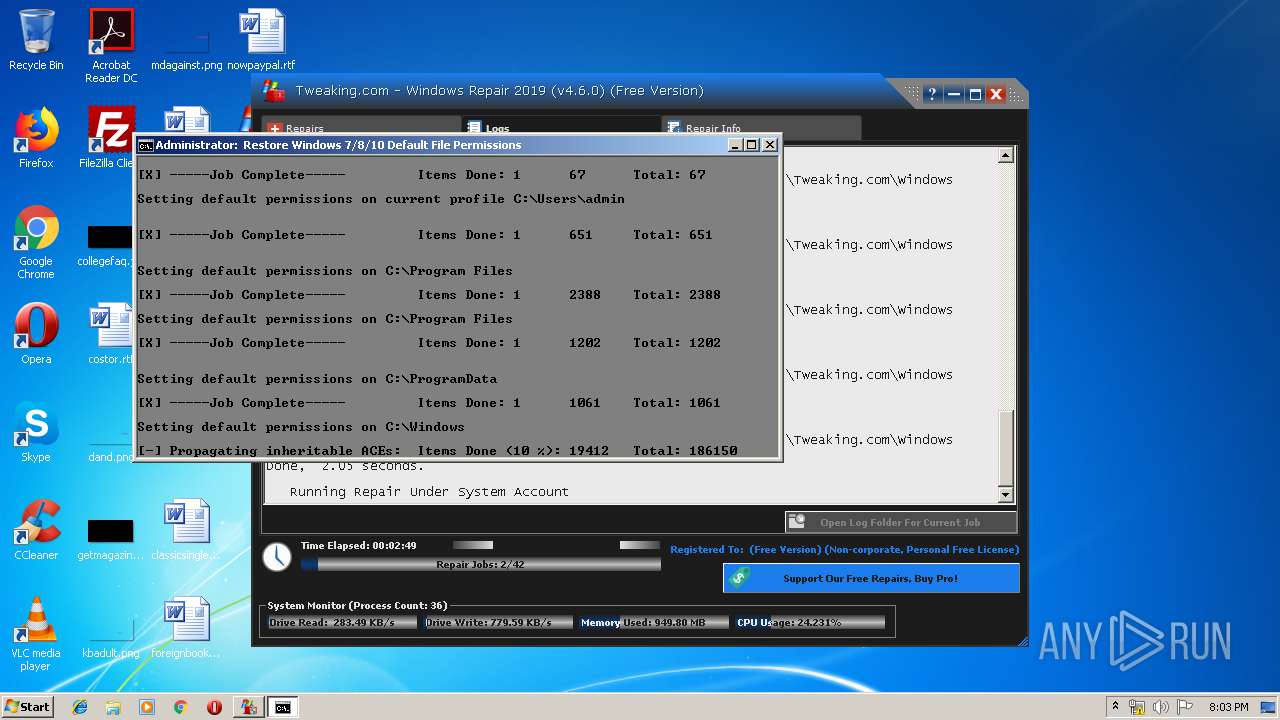
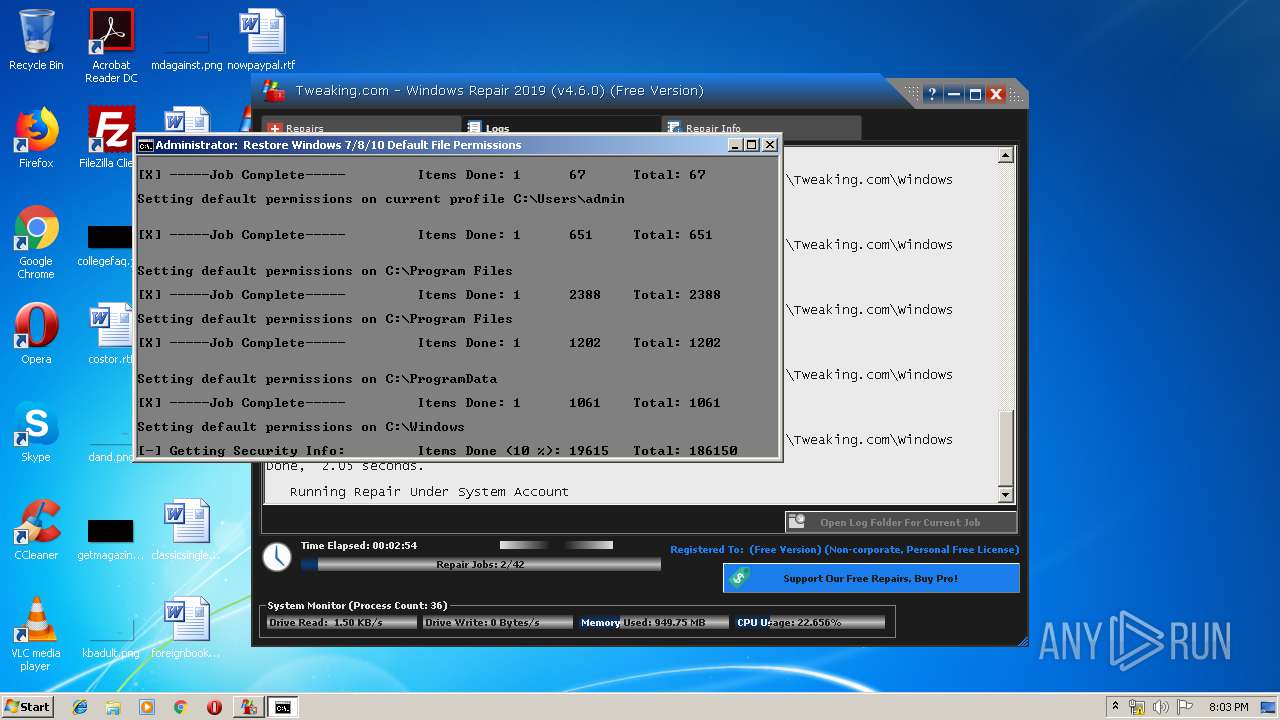
| URL: | https://www.tweaking.com/files/setups/tweaking.com_windows_repair_aio_setup.exe |
| Full analysis: | https://app.any.run/tasks/e8d03be3-49d1-49f9-8ee6-aadf99b0de9f |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | October 09, 2019, 18:57:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 66A921EDFF305214926F6F65FDC3EEF8 |
| SHA1: | 0104474C28C5AD716D7C9C340BBD4A385AA6822B |
| SHA256: | D861925A5E834465CBE580B91569BAA8361C7E36793D1FA0B84E5C9B2FB347D1 |
| SSDEEP: | 3:N8DSL5EjLCx0KxAWKRzKC18zVlqQDh4A:2OL5EjLCLADzKC18zVoeh4A |
MALICIOUS
Application was dropped or rewritten from another process
- irsetup.exe (PID: 1644)
- irsetup.exe (PID: 1828)
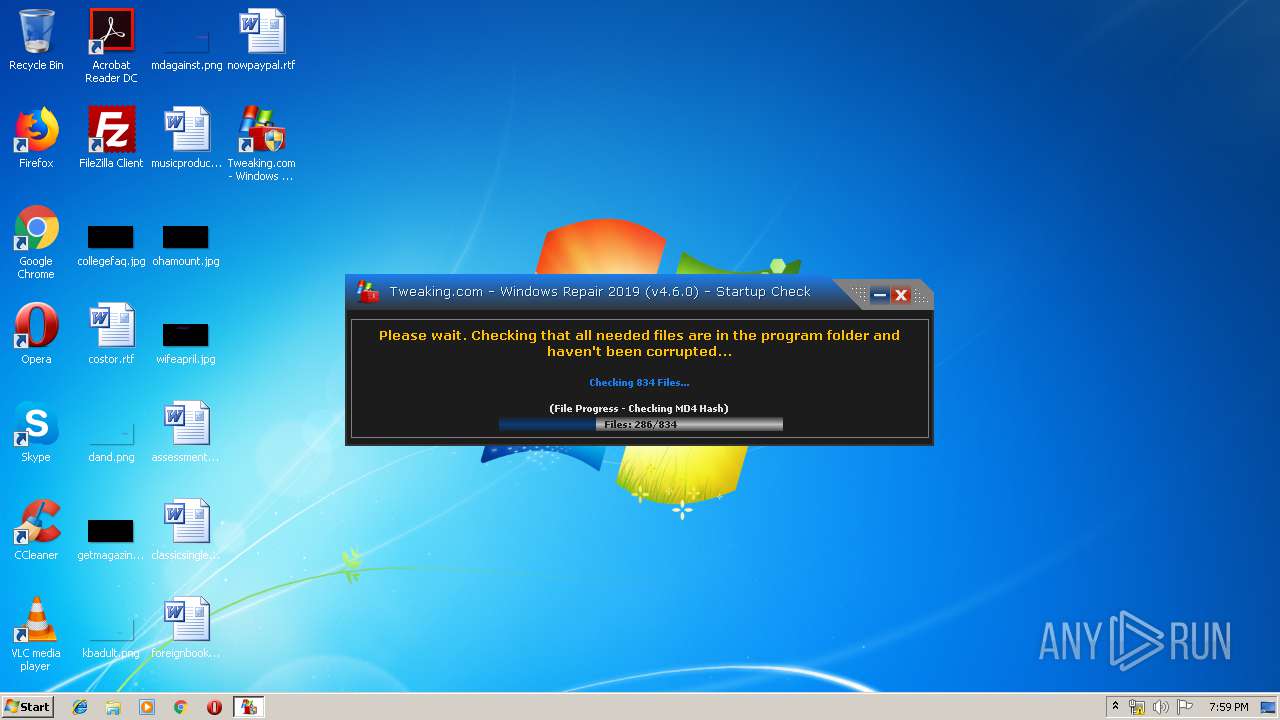
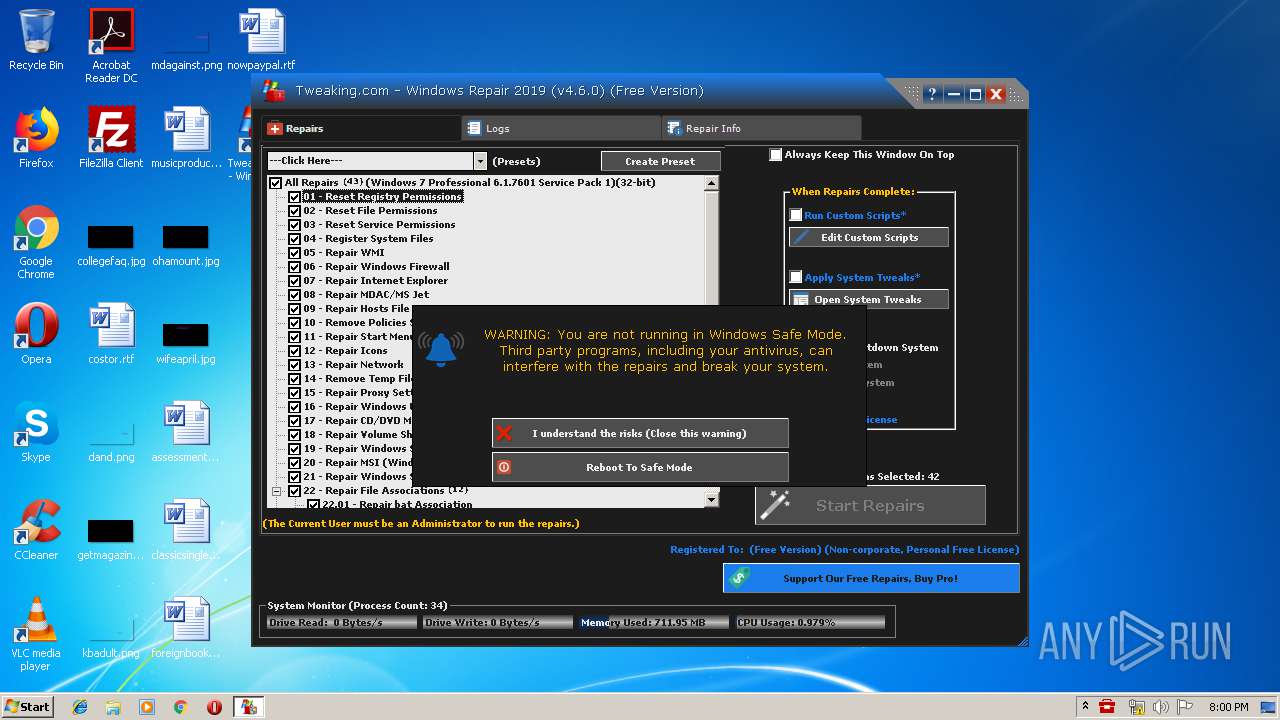
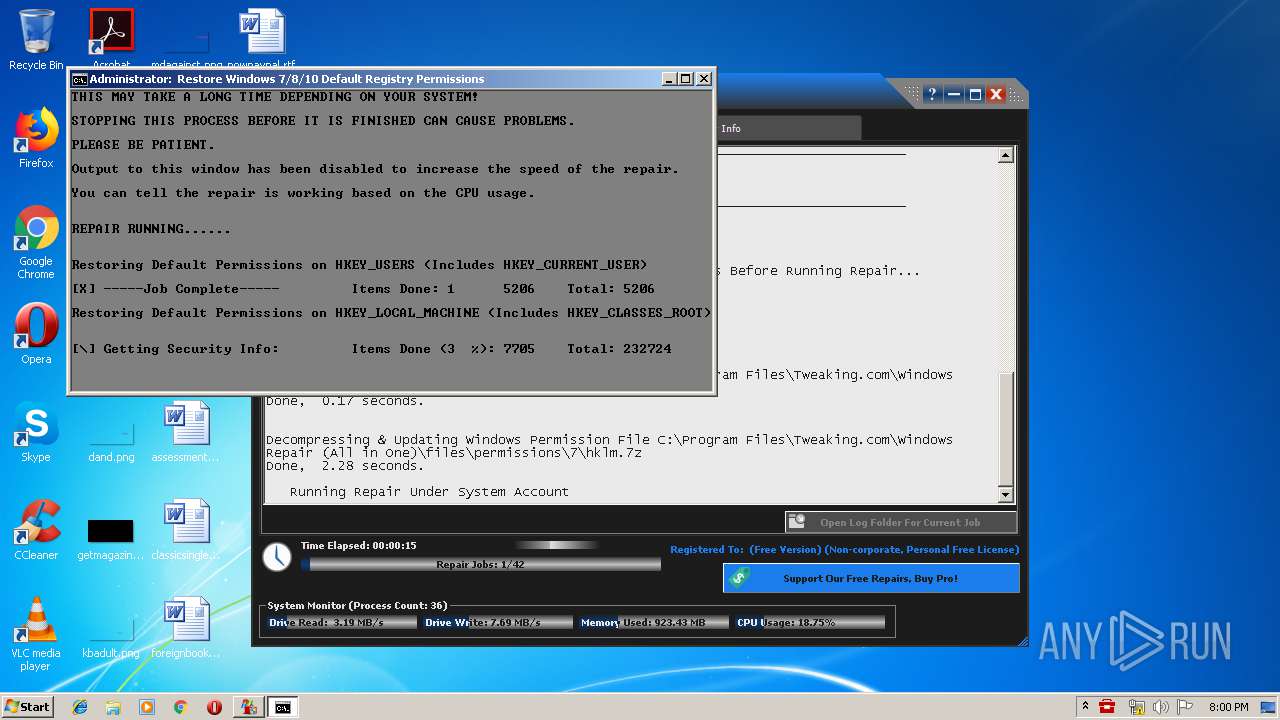
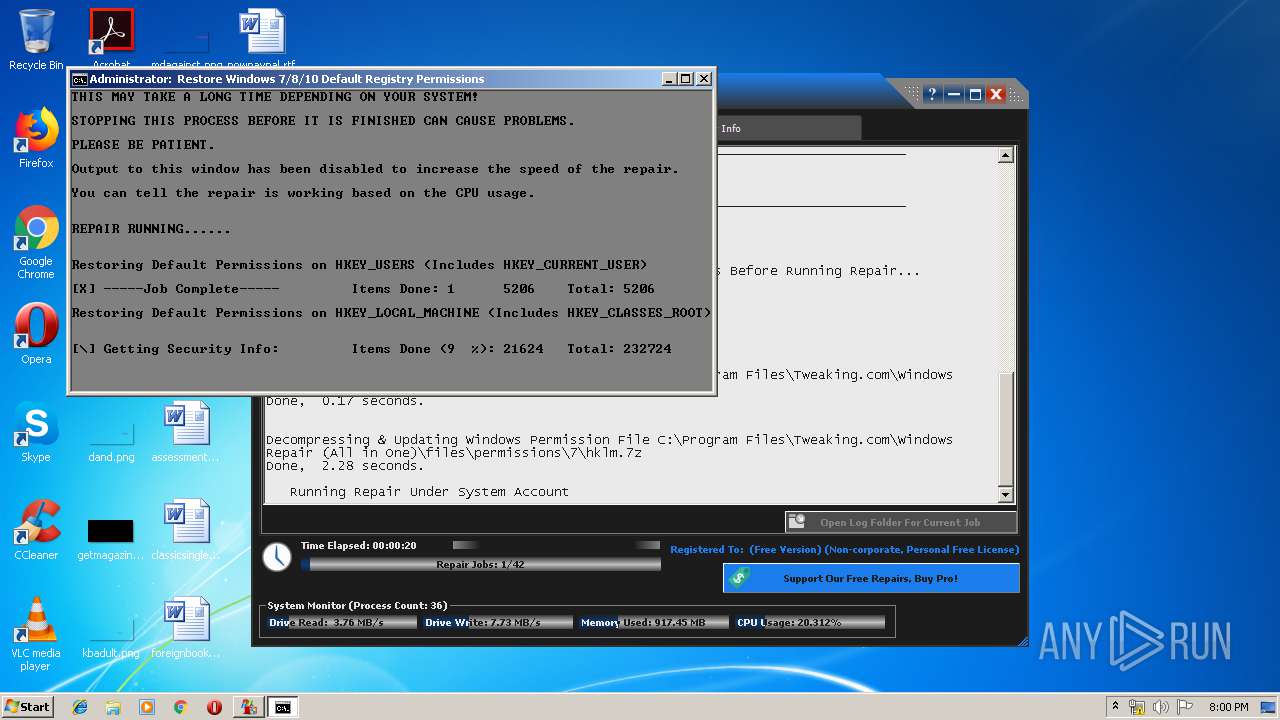
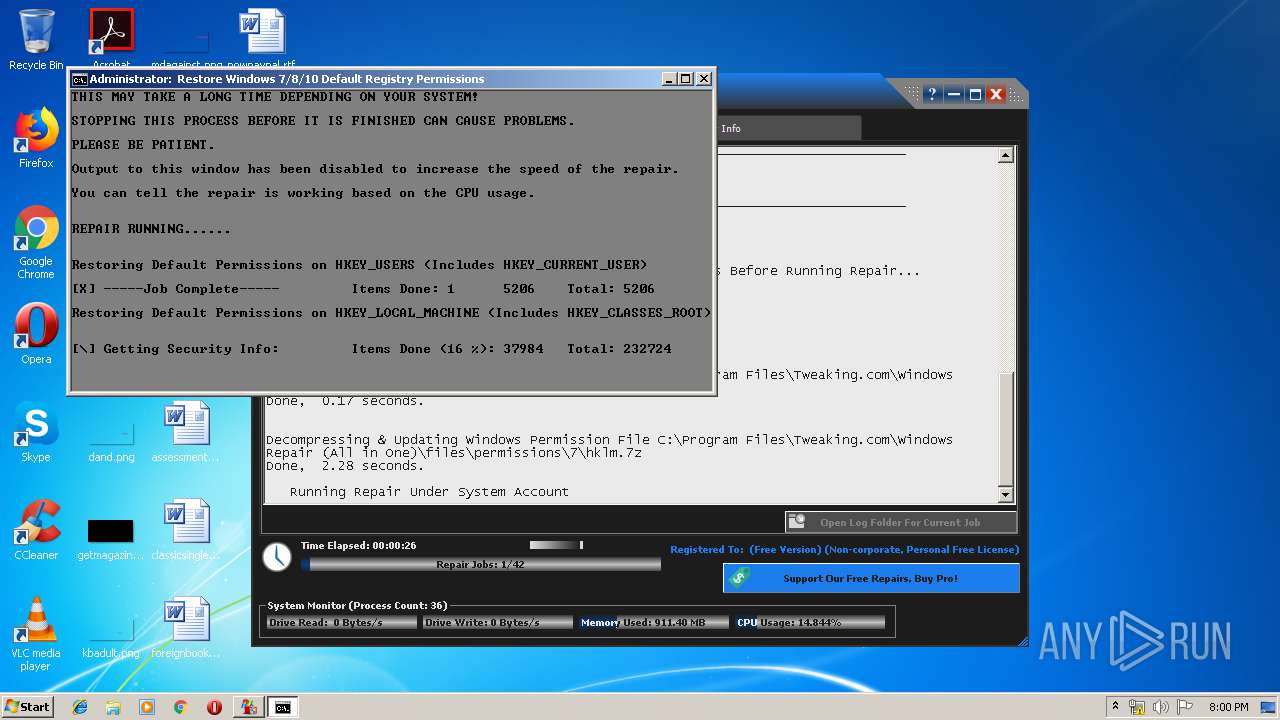
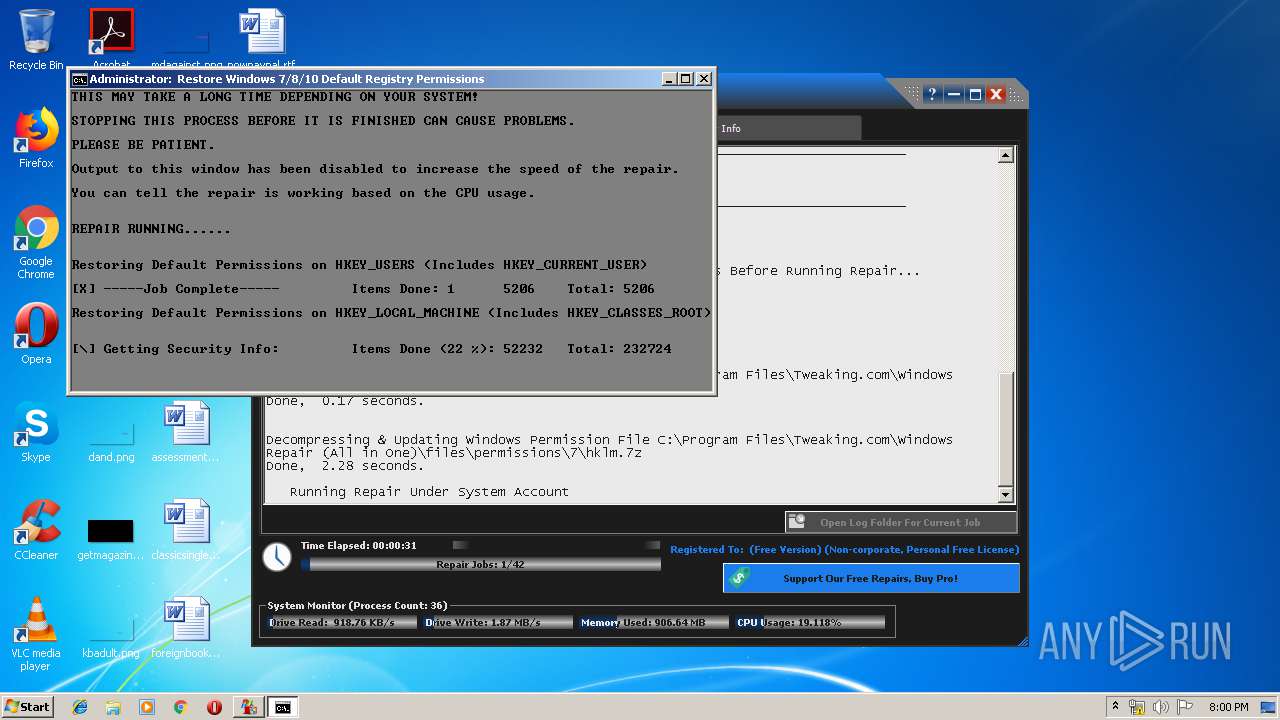
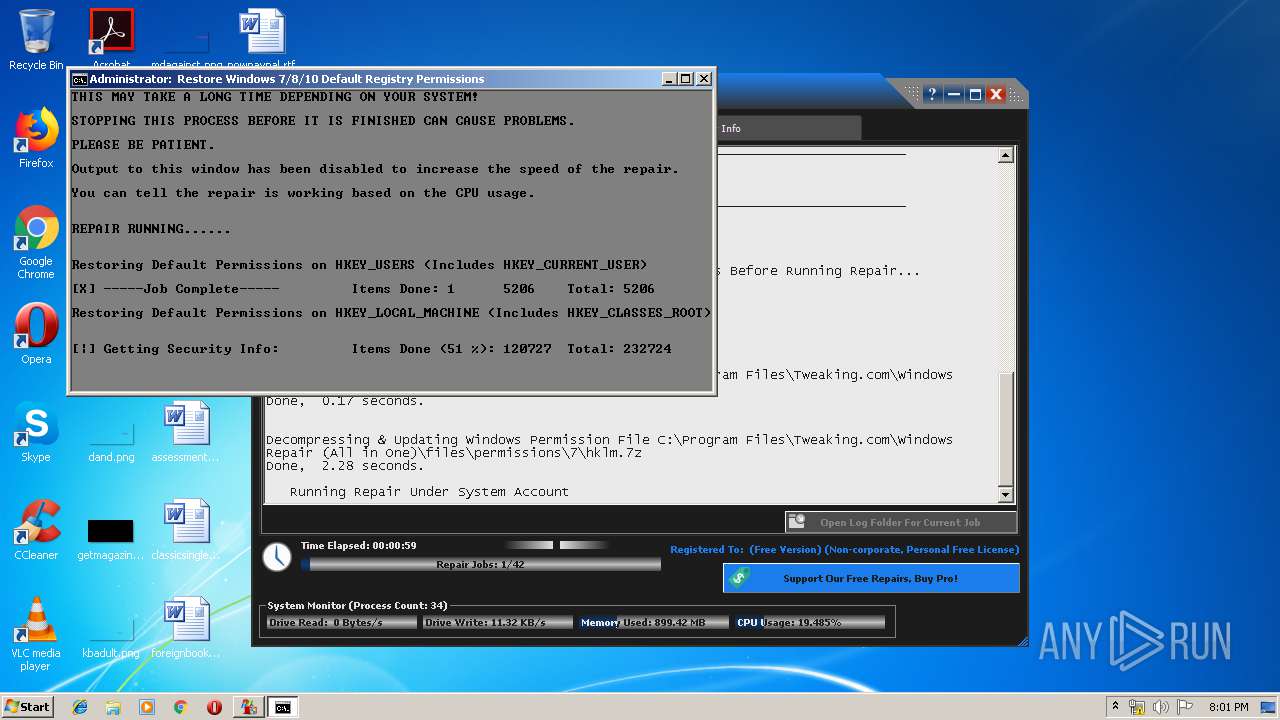
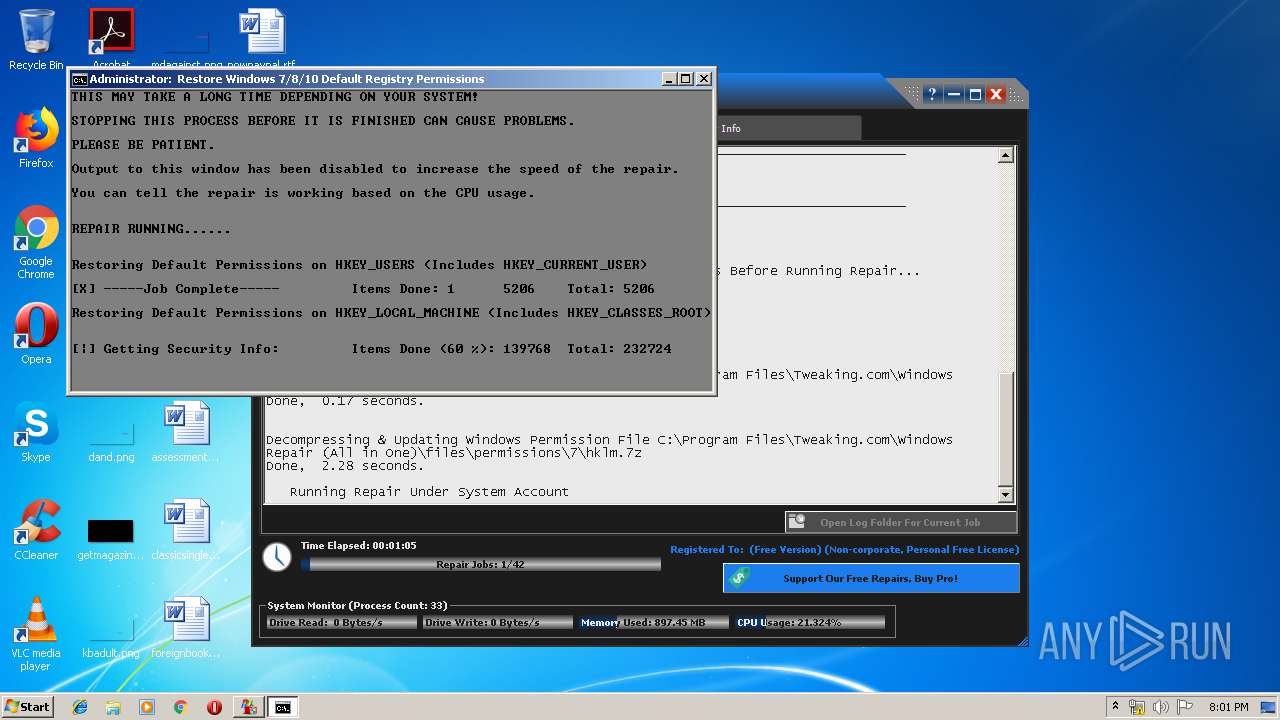
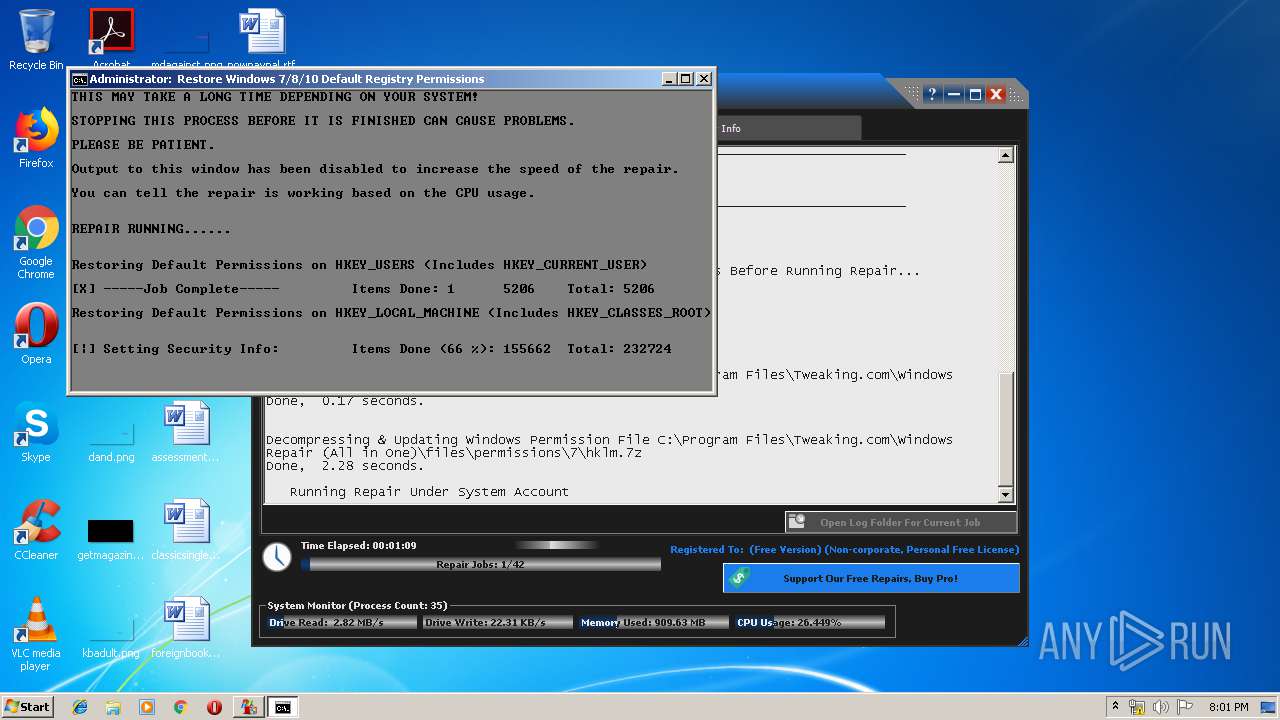
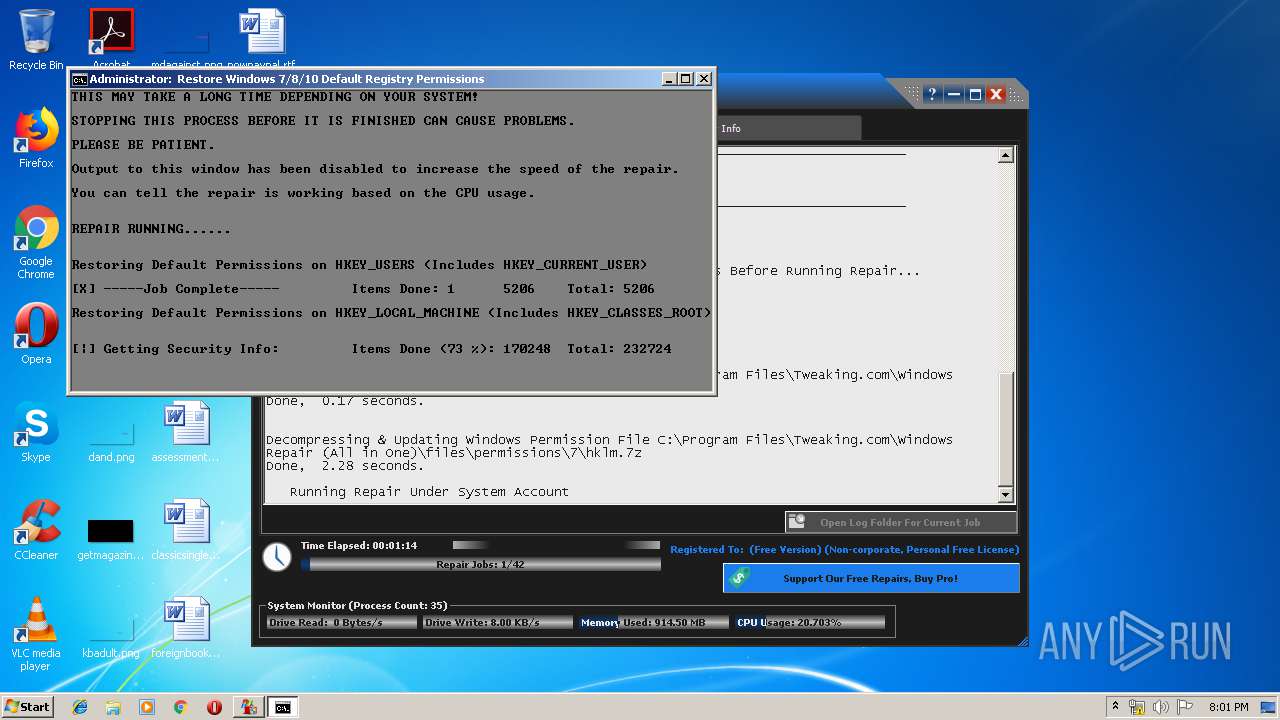
- Repair_Windows.exe (PID: 1828)
- WR_Tray_Icon.exe (PID: 2680)
- Repair_Windows.exe (PID: 1668)
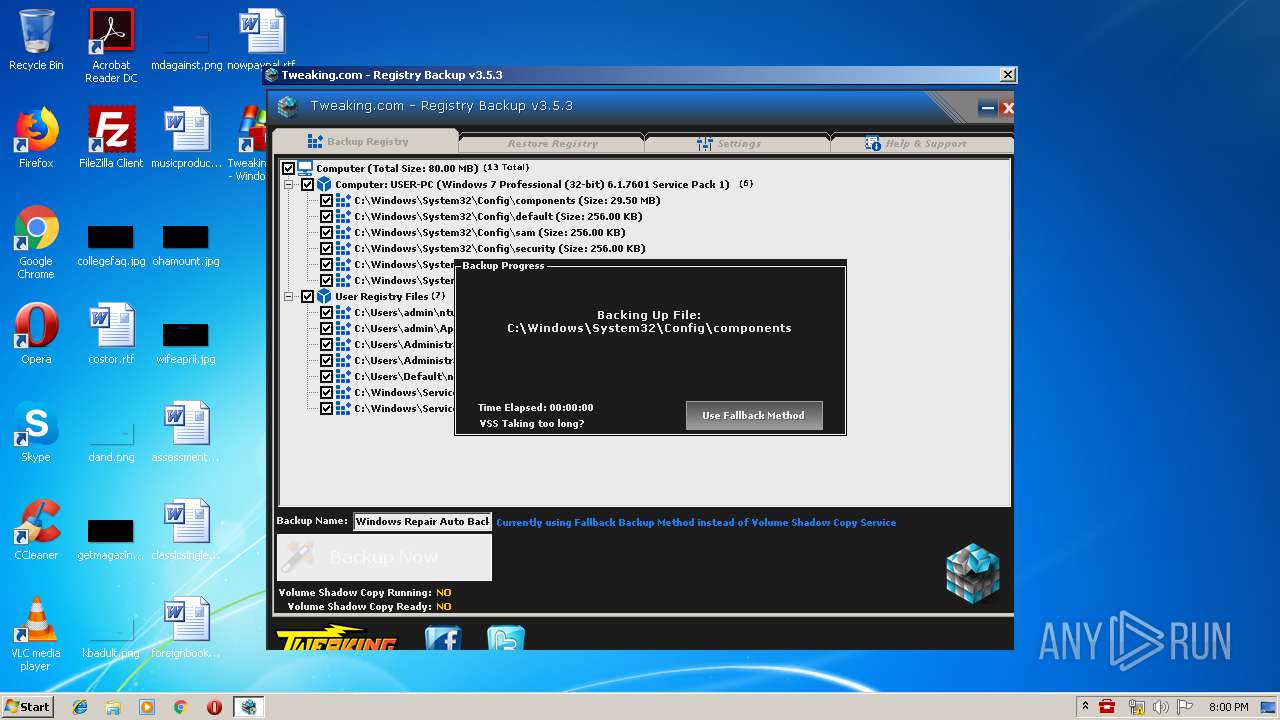
- TweakingRegistryBackup.exe (PID: 720)
- tweaking_ras.exe (PID: 3888)
- tweaking_ras.exe (PID: 3676)
- Tweaking_CleanMem.exe (PID: 2756)
- tweaking_ras.exe (PID: 3452)
- ManageACL_32.exe (PID: 2532)
- ManageACL_32.exe (PID: 2516)
- tweaking_ras.exe (PID: 3968)
- tweaking_ras.exe (PID: 3932)
- ManageACL_32.exe (PID: 364)
- ManageACL_32.exe (PID: 3372)
- tweaking_ras.exe (PID: 3000)
- ManageACL_32.exe (PID: 2780)
- ManageACL_32.exe (PID: 1656)
- ManageACL_32.exe (PID: 3188)
- ManageACL_32.exe (PID: 3216)
Loads dropped or rewritten executable
- Repair_Windows.exe (PID: 1668)
- irsetup.exe (PID: 1644)
- TweakingRegistryBackup.exe (PID: 720)
- Repair_Windows.exe (PID: 1828)
Loads the Task Scheduler COM API
- Repair_Windows.exe (PID: 1668)
Loads the Task Scheduler DLL interface
- Repair_Windows.exe (PID: 1668)
Starts NET.EXE for service management
- cmd.exe (PID: 1456)
- cmd.exe (PID: 3500)
- cmd.exe (PID: 2600)
Starts NET.EXE to view/change users group
- cmd.exe (PID: 1404)
Stealing of credential data
- TweakingRegistryBackup.exe (PID: 720)
Actions looks like stealing of personal data
- ManageACL_32.exe (PID: 3372)
SUSPICIOUS
Executable content was dropped or overwritten
- tweaking.com_windows_repair_aio_setup[1].exe (PID: 3060)
- irsetup.exe (PID: 1644)
Uses REG.EXE to modify Windows registry
- Repair_Windows.exe (PID: 1668)
- cmd.exe (PID: 1404)
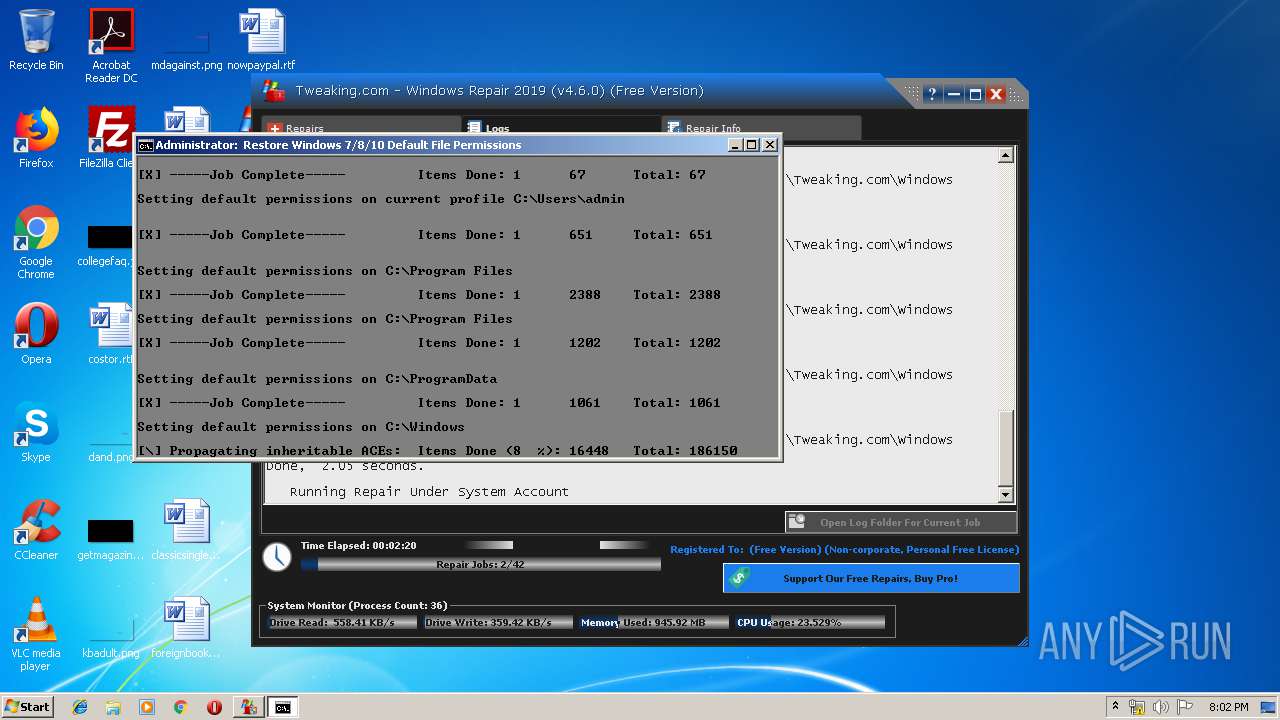
Creates files in the Windows directory
- irsetup.exe (PID: 1644)
- TweakingRegistryBackup.exe (PID: 720)
- Repair_Windows.exe (PID: 1828)
Creates a software uninstall entry
- irsetup.exe (PID: 1644)
- Repair_Windows.exe (PID: 1828)
Creates files in the program directory
- Repair_Windows.exe (PID: 1828)
- ManageACL_32.exe (PID: 2532)
- ManageACL_32.exe (PID: 3188)
- ManageACL_32.exe (PID: 364)
- ManageACL_32.exe (PID: 3372)
- ManageACL_32.exe (PID: 1656)
- ManageACL_32.exe (PID: 3216)
- ManageACL_32.exe (PID: 2780)
- irsetup.exe (PID: 1644)
Starts CMD.EXE for commands execution
- tweaking_ras.exe (PID: 3676)
- cmd.exe (PID: 3028)
- tweaking_ras.exe (PID: 3888)
- tweaking_ras.exe (PID: 3452)
- cmd.exe (PID: 2536)
- tweaking_ras.exe (PID: 3932)
- tweaking_ras.exe (PID: 3968)
- tweaking_ras.exe (PID: 3000)
- cmd.exe (PID: 3720)
Removes files from Windows directory
- Repair_Windows.exe (PID: 1828)
- cmd.exe (PID: 3952)
- cmd.exe (PID: 1404)
Executed as Windows Service
- tweaking_ras.exe (PID: 3968)
- tweaking_ras.exe (PID: 3676)
- tweaking_ras.exe (PID: 3000)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 928)
- iexplore.exe (PID: 2884)
Changes internet zones settings
- iexplore.exe (PID: 2884)
Dropped object may contain Bitcoin addresses
- irsetup.exe (PID: 1644)
- Repair_Windows.exe (PID: 1828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
118
Monitored processes
62
Malicious processes
17
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | "C:\Program Files\Tweaking.com\Windows Repair (All in One)\files\ManageACL_32.exe" -on "C:\Program Files" -ot file -actn restore -bckp "C:\Windows\Temp\1program_files.txt" -silent -ignoreerr -log "C:\Program Files\Tweaking.com\Windows Repair (All in One)\Logs\10.9.2019_8.00.14-PM\Restore_Program_Files_Permissions_Error_Log.txt" | C:\Program Files\Tweaking.com\Windows Repair (All in One)\files\ManageACL_32.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Tweaking.com Integrity Level: SYSTEM Description: Tweaking.com - ManageACL Exit code: 0 Version: 1.7.0.0 Modules
| |||||||||||||||
| 720 | "C:\Program Files\Tweaking.com\Windows Repair (All in One)\files\registry_backup_tool\TweakingRegistryBackup.exe" /auto | C:\Program Files\Tweaking.com\Windows Repair (All in One)\files\registry_backup_tool\TweakingRegistryBackup.exe | Repair_Windows.exe | ||||||||||||
User: admin Company: Tweaking.com Integrity Level: HIGH Description: Tweaking.com - Registry Backup Exit code: 0 Version: 3.5.0.3 Modules
| |||||||||||||||
| 928 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2884 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 996 | "C:\Windows\System32\reg.exe" DELETE HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Environment /v SAFEBOOT_OPTION /f | C:\Windows\System32\reg.exe | — | Repair_Windows.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1144 | REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Windows" /v NoInteractiveServices /t REG_DWORD /d 0 /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1404 | C:\Windows\System32\cmd.exe /c "C:\Windows\Temp\temp49509.bat" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1456 | cmd.exe /c net start TweakingRunAsSystem0001 | C:\Windows\system32\cmd.exe | — | tweaking_ras.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1472 | C:\Windows\system32\net1 localgroup "Administrators" "NT Authority\Service" /add | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1564 | C:\Windows\system32\net1 start TweakingRunAsSystem0003 | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1632 | C:\Windows\System32\cmd.exe /c "C:\Windows\Temp\temp85846.bat" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 544
Read events
1 342
Write events
199
Delete events
3
Modification events
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {BF214A8B-EAC6-11E9-837B-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (2884) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070A000300090012003A000F00EA01 | |||
Executable files
43
Suspicious files
41
Text files
1 019
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2884 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE6BB2A2215C609A7.TMP | — | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\1KS7E6X7\tweaking.com_windows_repair_aio_setup[1].exe | — | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\tweaking.com_windows_repair_aio_setup[1].exe | — | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019092020190921\index.dat | — | |
MD5:— | SHA256:— | |||
| 1644 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.dat | — | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF39ECA9ED55740781.TMP | — | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{BF214A8B-EAC6-11E9-837B-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 1644 | irsetup.exe | C:\Program Files\Tweaking.com\Windows Repair (All in One)\Uninstall\uni8360.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
5
DNS requests
4
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1644 | irsetup.exe | GET | 200 | 52.21.98.236:80 | http://track.tweaking.com/ev-install-end.php?type=install-end&computer=S-1-5-21-1302019708-1500728564-335382590-1000 | US | text | 9 b | malicious |
1644 | irsetup.exe | GET | 200 | 52.21.98.236:80 | http://track.tweaking.com/ev-install-end.php?type=install-end&computer=S-1-5-21-1302019708-1500728564-335382590-1000 | US | text | 9 b | malicious |
1828 | Repair_Windows.exe | GET | 200 | 199.119.100.39:80 | http://update.tweaking.com/update4.php?fr=1&nt=61&k=Free_Version&v=4.6.0&r=na | US | text | 41 b | suspicious |
1828 | Repair_Windows.exe | GET | 200 | 199.119.100.39:80 | http://www.tweaking.com/files/updates/windows_repair/update.htm | US | text | 5 b | suspicious |
1644 | irsetup.exe | GET | 200 | 52.21.98.236:80 | http://track.tweaking.com/ev-install-start.php?type=install-start&computer=S-1-5-21-1302019708-1500728564-335382590-1000 | US | text | 9 b | malicious |
1644 | irsetup.exe | GET | 200 | 52.21.98.236:80 | http://track.tweaking.com/ev-install-start.php?type=install-start&computer=S-1-5-21-1302019708-1500728564-335382590-1000 | US | text | 9 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
928 | iexplore.exe | 199.119.100.39:443 | www.tweaking.com | HIVELOCITY VENTURES CORP | US | suspicious |
2884 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1644 | irsetup.exe | 52.21.98.236:80 | track.tweaking.com | Amazon.com, Inc. | US | suspicious |
1828 | Repair_Windows.exe | 199.119.100.39:80 | www.tweaking.com | HIVELOCITY VENTURES CORP | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.tweaking.com |
| suspicious |
www.bing.com |
| whitelisted |
track.tweaking.com |
| malicious |
update.tweaking.com |
| suspicious |
Threats
4 ETPRO signatures available at the full report