| File name: | نتائج استفتاء الدستور-الخارج.xls |
| Full analysis: | https://app.any.run/tasks/ba9b0afd-ddc8-4085-b5d8-752d97a4298f |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 11:32:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: Admin, Last Saved By: Research, Name of Creating Application: Microsoft Excel, Create Time/Date: Sat Apr 13 10:30:01 2019, Last Saved Time/Date: Mon Apr 22 14:15:51 2019, Security: 1 |
| MD5: | 44B9203FED19829E24D1601DBD141C0E |
| SHA1: | 2DAC9ED7BE4DD83DF607A6C7F847C1ED92FA0219 |
| SHA256: | D8589625BBEA522E927FC1B7A3484308F79C481C5D32294BA26A496DFEF18F94 |
| SSDEEP: | 768:f5wOYrxfcfo9nJgafwgEuKpzOsNAzBGoydrpU8Pd8Q:f5wHkfanJgewgoxNyBGXFUcd |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3860)
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 3860)
SUSPICIOUS
Executes PowerShell scripts
- forfiles.exe (PID: 2100)
Executes scripts
- explorer.exe (PID: 272)
Creates files in the user directory
- powershell.exe (PID: 3152)
- WScript.exe (PID: 3704)
INFO
Creates files in the user directory
- EXCEL.EXE (PID: 3860)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| CompObjUserTypeLen: | 31 |
|---|---|
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
| Author: | Admin |
| LastModifiedBy: | Research |
| Software: | Microsoft Excel |
| CreateDate: | 2019:04:13 09:30:01 |
| ModifyDate: | 2019:04:22 13:15:51 |
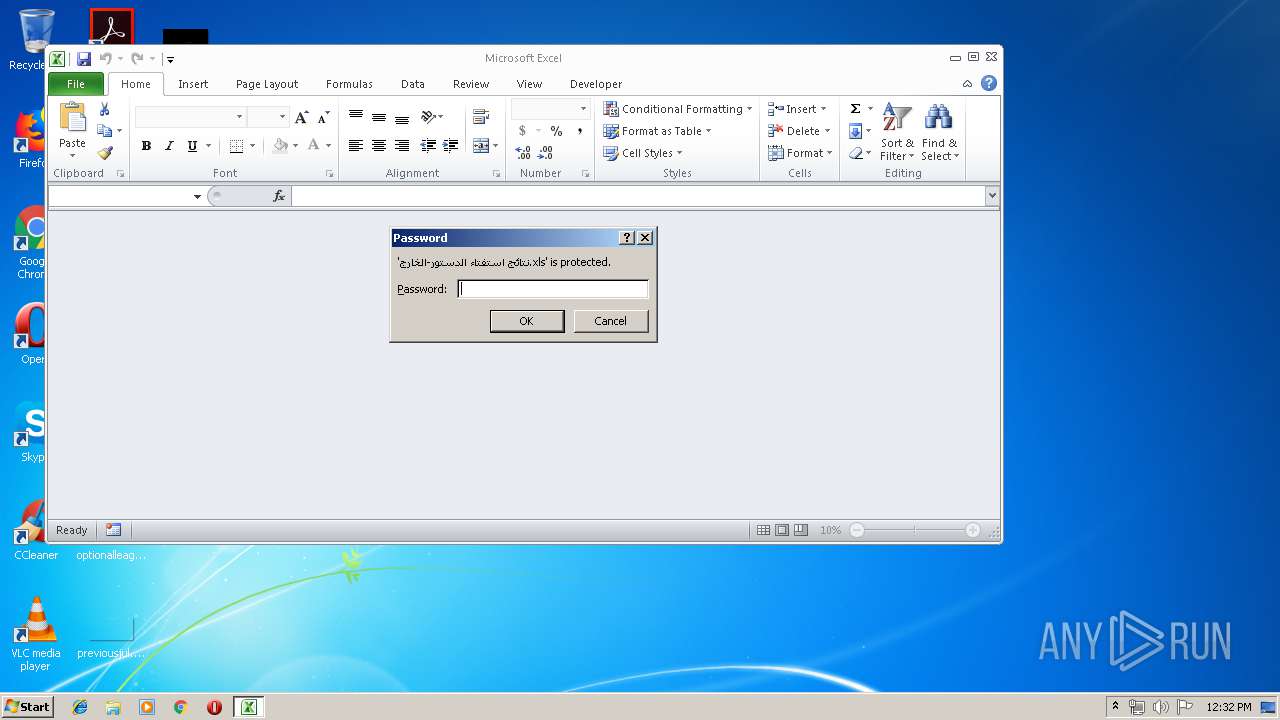
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
40
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1804 | cmd.exe /C echo %appdata%\Microsoft\Protect\Update.vbs > C:\Users\Public\t.txt | C:\Windows\system32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2100 | "C:\Windows\System32\forfiles.exe" /p c:\windows\system32 /m calc.exe /c "powershell -C (Get-Content "$ENV:APPDATA\Microsoft\Protect\antiquityn.txt") | iex" | C:\Windows\System32\forfiles.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ForFiles - Executes a command on selected files Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2716 | explorer.exe C:\Users\admin\AppData\Roaming\Microsoft\Protect\Update.vbs | C:\Windows\explorer.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3152 | -C (Get-Content $ENV:APPDATA\Microsoft\Protect\antiquityn.txt) | iex | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | forfiles.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3704 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Protect\Update.vbs" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3860 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
926
Read events
809
Write events
110
Delete events
7
Modification events
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | "j |
Value: 226A2000140F0000010000000000000000000000 | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 140F0000EC96153DC8F9D40100000000 | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | "j |
Value: 226A2000140F0000010000000000000000000000 | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\113268 |
| Operation: | write | Name: | 113268 |
Value: 04000000140F00004200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C0046062A06270626062C062000270633062A0641062A06270621062000270644062F0633062A06480631062D00270644062E06270631062C062E0078006C007300000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00010000000000000010C61B3EC8F9D401683211006832110000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3860 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR2DF3.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3152 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\TEBJ0I0UNGIHSFU3HBVI.temp | — | |
MD5:— | SHA256:— | |||
| 1804 | cmd.exe | C:\Users\Public\t.txt | text | |
MD5:— | SHA256:— | |||
| 3152 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3152 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF117164.TMP | binary | |
MD5:— | SHA256:— | |||
| 3704 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Protect\antiquityn.txt | text | |
MD5:— | SHA256:— | |||
| 3860 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Protect\Update.vbs | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3152 | powershell.exe | 50.16.229.140:443 | api.ipify.org | Amazon.com, Inc. | US | malicious |
3152 | powershell.exe | 104.18.33.7:443 | windows-security.net | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
windows-security.net |
| suspicious |
api.ipify.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3152 | powershell.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
3152 | powershell.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
1 ETPRO signatures available at the full report