| File name: | Bat_To_Exe_Converter.exe |
| Full analysis: | https://app.any.run/tasks/8b73d73f-8692-4560-93b4-c027502a2bb2 |
| Verdict: | Malicious activity |
| Analysis date: | October 29, 2020, 23:38:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 603F241C0CB4530ACE1F37F3E8D86D04 |
| SHA1: | 389B4135578245D0D938E883A5FD5B713DB57EB5 |
| SHA256: | D853C4B83A9C8180C16FD22C3D63A899B101B9E7B5D9328777F37484C8649402 |
| SSDEEP: | 49152:wju1jBAZYEZAgMujB8v+mPEL1b2DlkNXNdcmuCpjil+0ugm:wUjBI7TVOELk5kN/zuCpj++0ugm |
MALICIOUS
Loads dropped or rewritten executable
- Bat_To_Exe_Converter.exe (PID: 2664)
SUSPICIOUS
Executable content was dropped or overwritten
- Bat_To_Exe_Converter.exe (PID: 2664)
Reads Internet Cache Settings
- Bat_To_Exe_Converter.exe (PID: 2664)
Application launched itself
- Bat_To_Exe_Converter.exe (PID: 2664)
Reads internet explorer settings
- Bat_To_Exe_Converter.exe (PID: 2664)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (64.1) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.5) |
| .exe | | | Win32 Executable (generic) (10.6) |
| .exe | | | Generic Win/DOS Executable (4.7) |
| .exe | | | DOS Executable Generic (4.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:01 21:50:01+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 1781760 |
| InitializedDataSize: | 147456 |
| UninitializedDataSize: | 1523712 |
| EntryPoint: | 0x327340 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.8.0 |
| ProductVersionNumber: | 3.0.8.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Fatih Kodak |
| ProductName: | Bat To Exe Converter |
| ProductVersion: | 3.0.8 |
| FileVersion: | 3.0.8 |
| FileDescription: | Bat To Exe Converter |
| InternalName: | Bat To Exe Converter |
| OriginalFileName: | Bat To Exe Converter |
| Email: | webmaster@f2ko.de |
| Website: | http://www.f2ko.de |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Feb-2018 20:50:01 |
| Detected languages: |
|
| CompanyName: | Fatih Kodak |
| ProductName: | Bat To Exe Converter |
| ProductVersion: | 3.0.8 |
| FileVersion: | 3.0.8 |
| FileDescription: | Bat To Exe Converter |
| InternalName: | Bat To Exe Converter |
| OriginalFilename: | Bat To Exe Converter |
| Email: | webmaster@f2ko.de |
| Website: | http://www.f2ko.de |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 01-Feb-2018 20:50:01 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00174000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00175000 | 0x001B3000 | 0x001B3000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99984 |
.rsrc | 0x00328000 | 0x00024000 | 0x00023C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.57072 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.92322 | 611 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.72897 | 67624 | UNKNOWN | English - United States | RT_ICON |
3 | 5.71122 | 16936 | UNKNOWN | English - United States | RT_ICON |
4 | 5.68138 | 9640 | UNKNOWN | English - United States | RT_ICON |
5 | 5.92516 | 4264 | UNKNOWN | English - United States | RT_ICON |
6 | 5.98264 | 2440 | UNKNOWN | English - United States | RT_ICON |
7 | 5.99869 | 1128 | UNKNOWN | English - United States | RT_ICON |
Imports
ADVAPI32.DLL |
COMCTL32.DLL |
COMDLG32.DLL |
GDI32.DLL |
KERNEL32.DLL |
MSVCRT.dll |
OLE32.DLL |
OLEAUT32.DLL |
SHELL32.DLL |
SHLWAPI.DLL |
Total processes
37
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2664 | "C:\Users\admin\AppData\Local\Temp\Bat_To_Exe_Converter.exe" | C:\Users\admin\AppData\Local\Temp\Bat_To_Exe_Converter.exe | explorer.exe | ||||||||||||
User: admin Company: Fatih Kodak Integrity Level: MEDIUM Description: Bat To Exe Converter Exit code: 0 Version: 3.0.8 Modules
| |||||||||||||||
| 3500 | "C:\Users\admin\AppData\Local\Temp\Bat_To_Exe_Converter.exe" /? | C:\Users\admin\AppData\Local\Temp\Bat_To_Exe_Converter.exe | — | Bat_To_Exe_Converter.exe | |||||||||||
User: admin Company: Fatih Kodak Integrity Level: MEDIUM Description: Bat To Exe Converter Exit code: 0 Version: 3.0.8 Modules
| |||||||||||||||
Total events
475
Read events
466
Write events
9
Delete events
0
Modification events
| (PID) Process: | (2664) Bat_To_Exe_Converter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2664) Bat_To_Exe_Converter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2664) Bat_To_Exe_Converter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2664) Bat_To_Exe_Converter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2664) Bat_To_Exe_Converter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2664) Bat_To_Exe_Converter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2664) Bat_To_Exe_Converter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
Executable files
4
Suspicious files
1
Text files
31
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2664 | Bat_To_Exe_Converter.exe | C:\Users\admin\AppData\Local\Temp\41B1.tmp\1960178370.cmd | — | |
MD5:— | SHA256:— | |||
| 2664 | Bat_To_Exe_Converter.exe | C:\Users\admin\AppData\Local\Temp\41B1.tmp\GoRC.exe | executable | |
MD5:F69B0E5F35B5DAE1B11B950CFF157FB3 | SHA256:ED010C50A7CEB43B9666E7FBCA13D8377D30B79203207BAD77004A890ADEEA17 | |||
| 2664 | Bat_To_Exe_Converter.exe | C:\Users\admin\AppData\Local\Temp\41B1.tmp\lng\Português Brasileiro (Portuguese Brazilian).lng | text | |
MD5:60B2F5E8EE608D48E23A7F0096F4FAC9 | SHA256:42C56325E83DFBB8112FDF93F56584D91D3FABB4C56C3EF710FD427F2FA6A8DA | |||
| 2664 | Bat_To_Exe_Converter.exe | C:\Users\admin\AppData\Local\Temp\41B1.tmp\GoLink.exe | executable | |
MD5:CAFC4EEC8A4F05B8DFEE4067FB5B9076 | SHA256:1FA554D18490CB5E56D624CD97069F42E63800688136C6CF3C521E4EF6E83E28 | |||
| 2664 | Bat_To_Exe_Converter.exe | C:\Users\admin\AppData\Local\Temp\41B1.tmp\lng\Français (French).lng | text | |
MD5:BEF8EC23F8162F30BCDB19B9E63BEF90 | SHA256:85407106B34A3C4451CEA55786DF36D2408BC579A4211C02D12AB3650C96A86E | |||
| 2664 | Bat_To_Exe_Converter.exe | C:\Users\admin\AppData\Local\Temp\41B1.tmp\374600396.bat | binary | |
MD5:93B885ADFE0DA089CDF634904FD59F71 | SHA256:6E340B9CFFB37A989CA544E6BB780A2C78901D3FB33738768511A30617AFA01D | |||
| 2664 | Bat_To_Exe_Converter.exe | C:\Users\admin\AppData\Local\Temp\41B1.tmp\lng\简化中国 (Chinese Simplified).lng | text | |
MD5:8AB06A4B804350D0A232E65B82E992E1 | SHA256:5A5FBE8998D1AA2C6CB7E16FA50861910C806AC3DF99E2026E8B577175B36133 | |||
| 2664 | Bat_To_Exe_Converter.exe | C:\Users\admin\AppData\Local\Temp\41B1.tmp\lng\日本語 (Japanese).lng | text | |
MD5:2125B2D9BFDA91CECA3ED41F4C861B4C | SHA256:876D4162596D4EFA962D5E214A3A801EAE4C8BFD36439D20880D5098F602321B | |||
| 2664 | Bat_To_Exe_Converter.exe | C:\Users\admin\AppData\Local\Temp\41B1.tmp\lng\Slovenský (Slovak).lng | text | |
MD5:F19CD4F6CCE52F99B6C62802E0D690C4 | SHA256:9442A4ED768B0F65D4A8DD5C1E91C9E7EDBEA4235C8C8E5C6AB44A54F93297A1 | |||
| 2664 | Bat_To_Exe_Converter.exe | C:\Users\admin\AppData\Local\Temp\41B1.tmp\extd.chm | chi | |
MD5:D4FC8C71A167383B2CEA62137B12F63D | SHA256:2786F9B9CDF8A73396405CE59CB6D00FAD9D51E5136183999D14A5CB9F5D80FB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
3
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2664 | Bat_To_Exe_Converter.exe | GET | 404 | 179.61.149.162:80 | http://www.f2ko.de/donate.php?app=b2e | US | html | 5.99 Kb | malicious |
2664 | Bat_To_Exe_Converter.exe | GET | 200 | 179.61.149.162:80 | http://www.f2ko.de/wp-content/plugins/contact-form-7/includes/js/scripts.js?ver=5.3 | US | text | 4.55 Kb | malicious |
2664 | Bat_To_Exe_Converter.exe | GET | 200 | 179.61.149.162:80 | http://www.f2ko.de/wp-includes/js/wp-embed.min.js?ver=5.4.3 | US | text | 784 b | malicious |
2664 | Bat_To_Exe_Converter.exe | GET | 200 | 179.61.149.162:80 | http://www.f2ko.de/wp-content/themes/twentytwenty/style.css?ver=1.5 | US | text | 29.7 Kb | malicious |
2664 | Bat_To_Exe_Converter.exe | GET | 200 | 179.61.149.162:80 | http://www.f2ko.de/wp-content/themes/twentytwenty/print.css?ver=1.5 | US | text | 1.03 Kb | malicious |
2664 | Bat_To_Exe_Converter.exe | GET | 200 | 179.61.149.162:80 | http://www.f2ko.de/wp-includes/js/wp-emoji-release.min.js?ver=5.4.3 | US | text | 5.12 Kb | malicious |
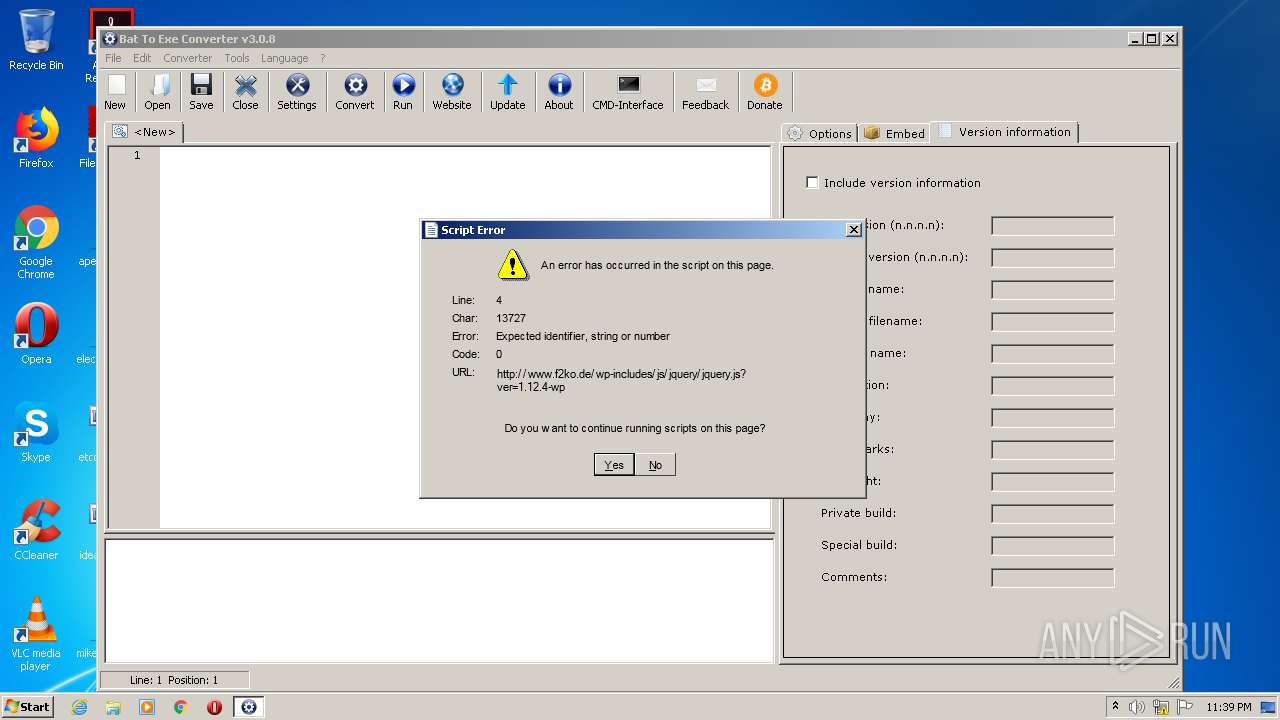
2664 | Bat_To_Exe_Converter.exe | GET | 200 | 179.61.149.162:80 | http://www.f2ko.de/wp-includes/js/jquery/jquery.js?ver=1.12.4-wp | US | text | 38.4 Kb | malicious |
2664 | Bat_To_Exe_Converter.exe | GET | 200 | 179.61.149.162:80 | http://www.f2ko.de/wp-includes/js/jquery/jquery-migrate.min.js?ver=1.4.1 | US | text | 4.20 Kb | malicious |
2664 | Bat_To_Exe_Converter.exe | GET | 200 | 179.61.149.162:80 | http://www.f2ko.de/wp-content/themes/twentytwenty/assets/js/index.js?ver=1.5 | US | text | 8.00 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2664 | Bat_To_Exe_Converter.exe | 179.61.149.162:80 | www.f2ko.de | Digital Energy Technologies Limited | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.f2ko.de |
| malicious |