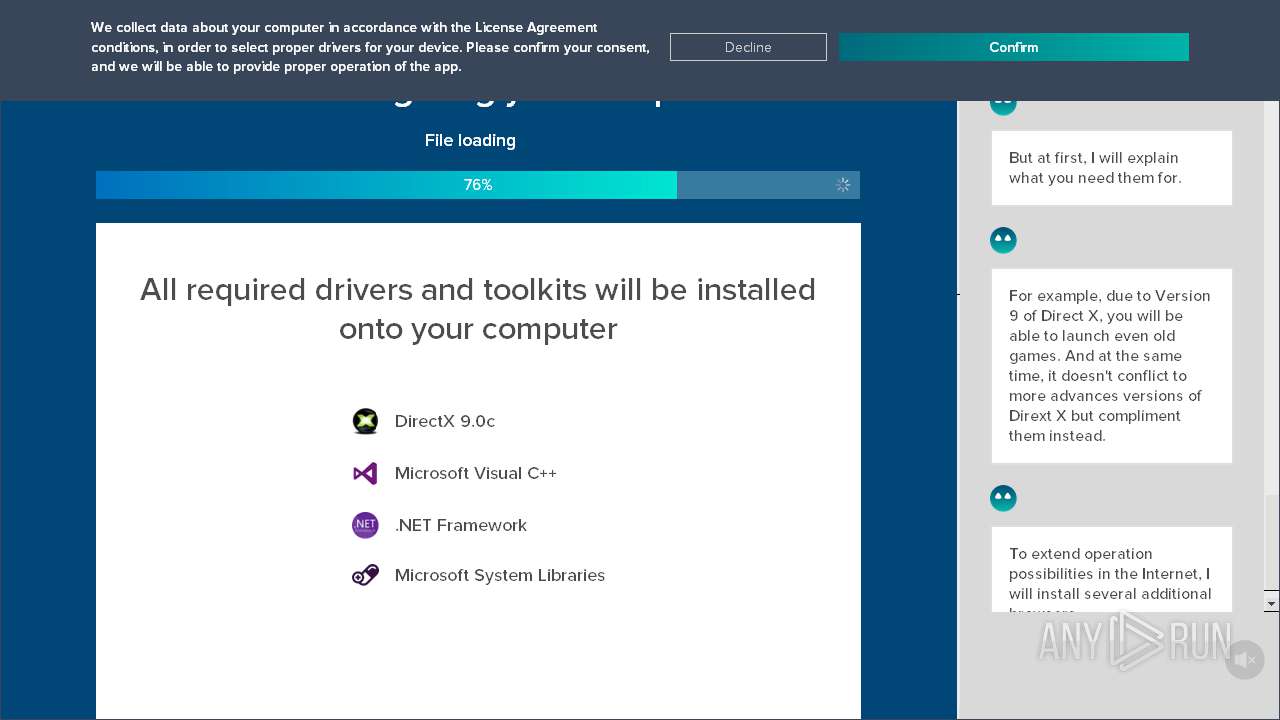
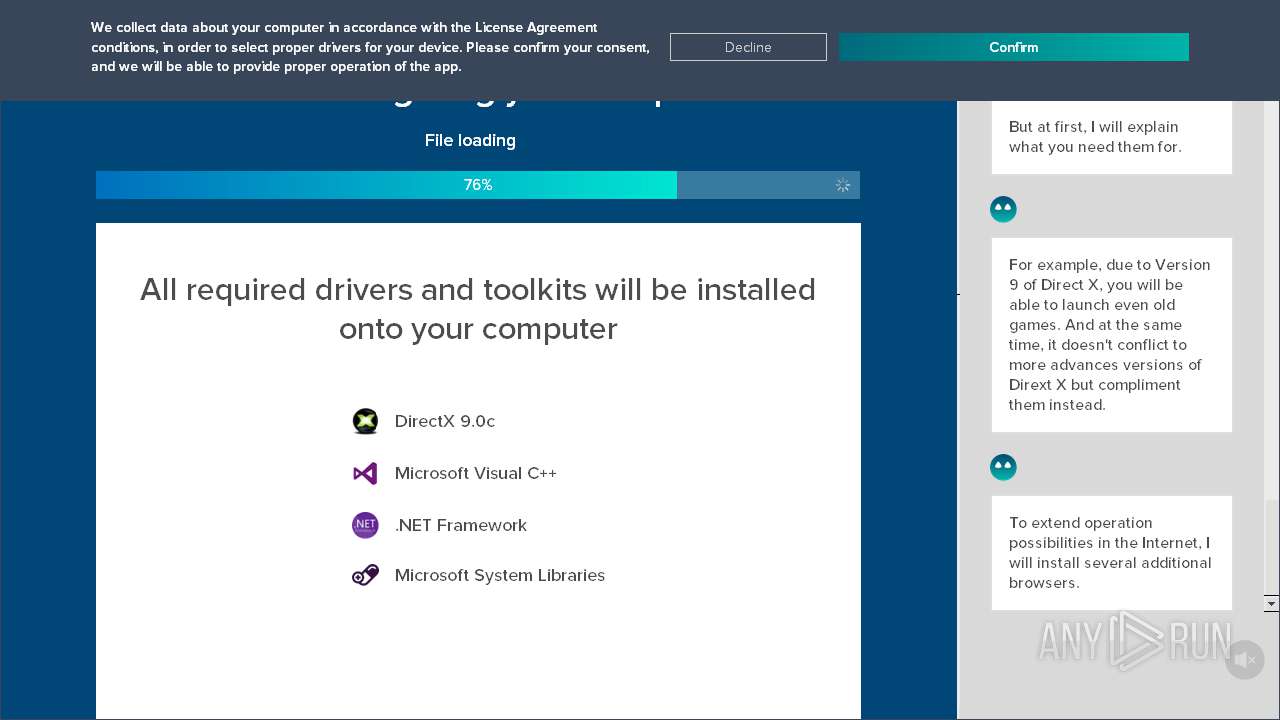
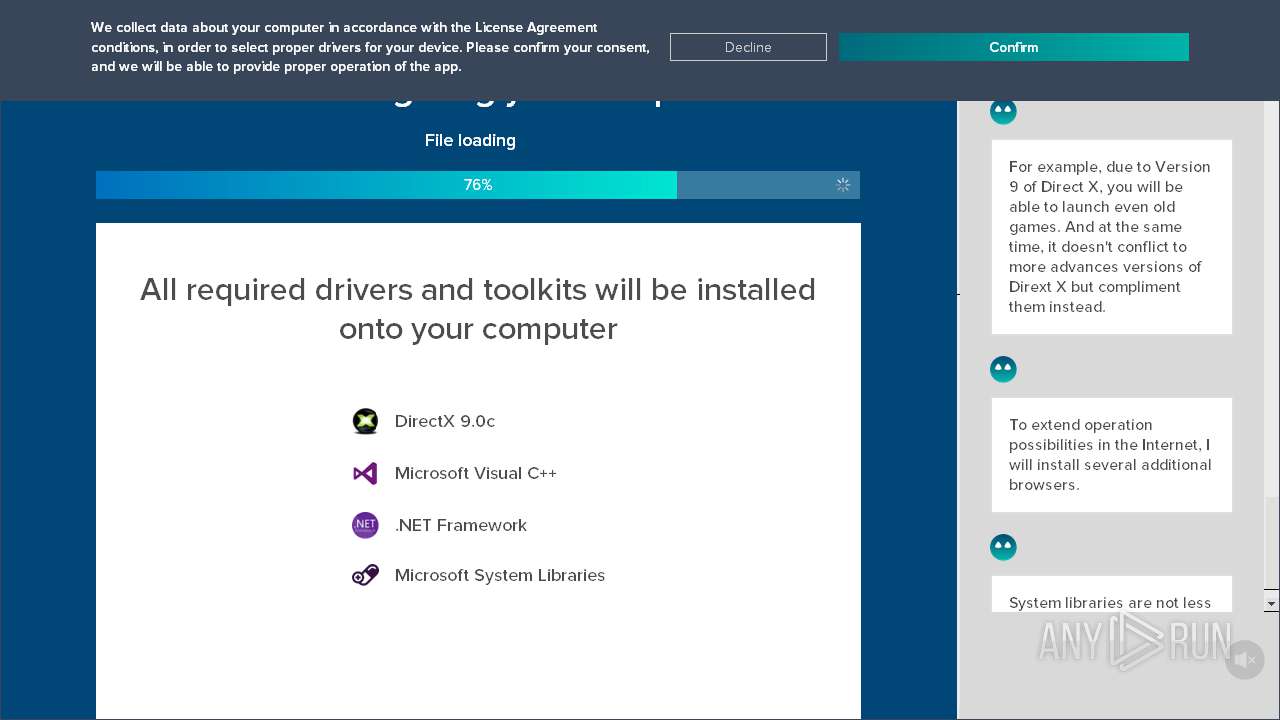
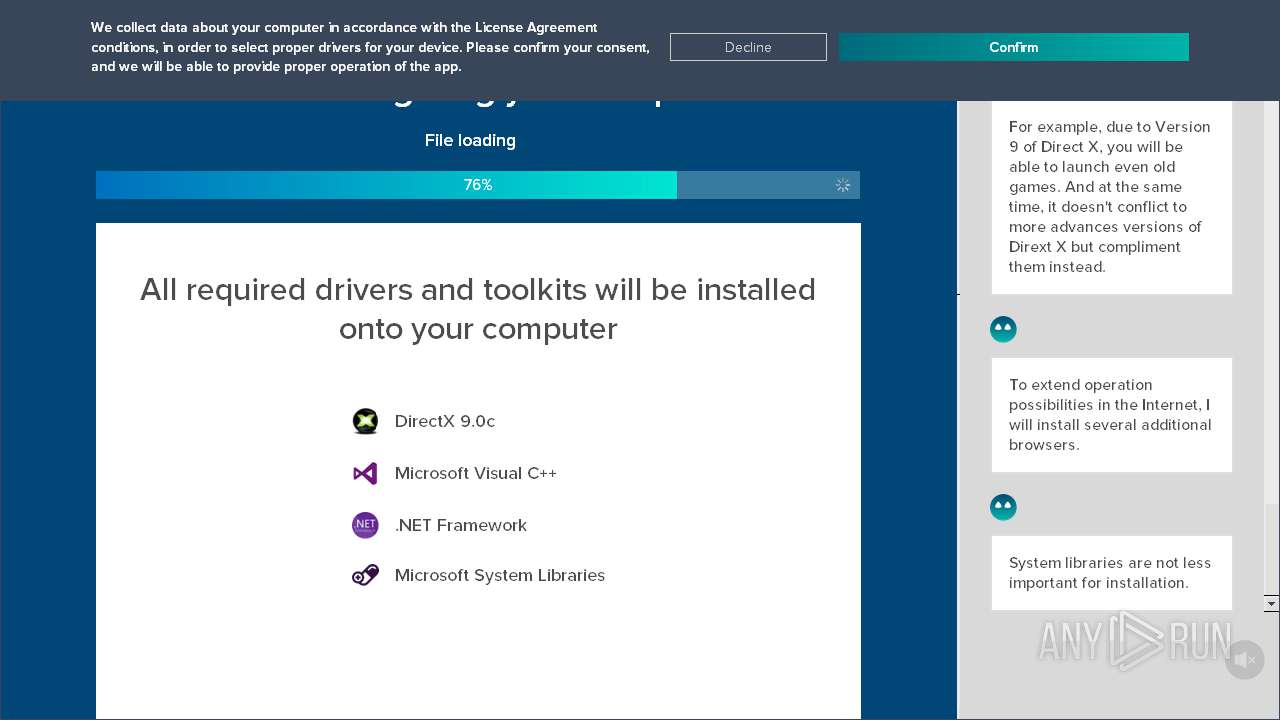
| File name: | DriverPack-17-Online_1758497922.1550022335.exe |
| Full analysis: | https://app.any.run/tasks/76b72d48-ef51-422e-a003-1aa9cf50fae2 |
| Verdict: | Malicious activity |
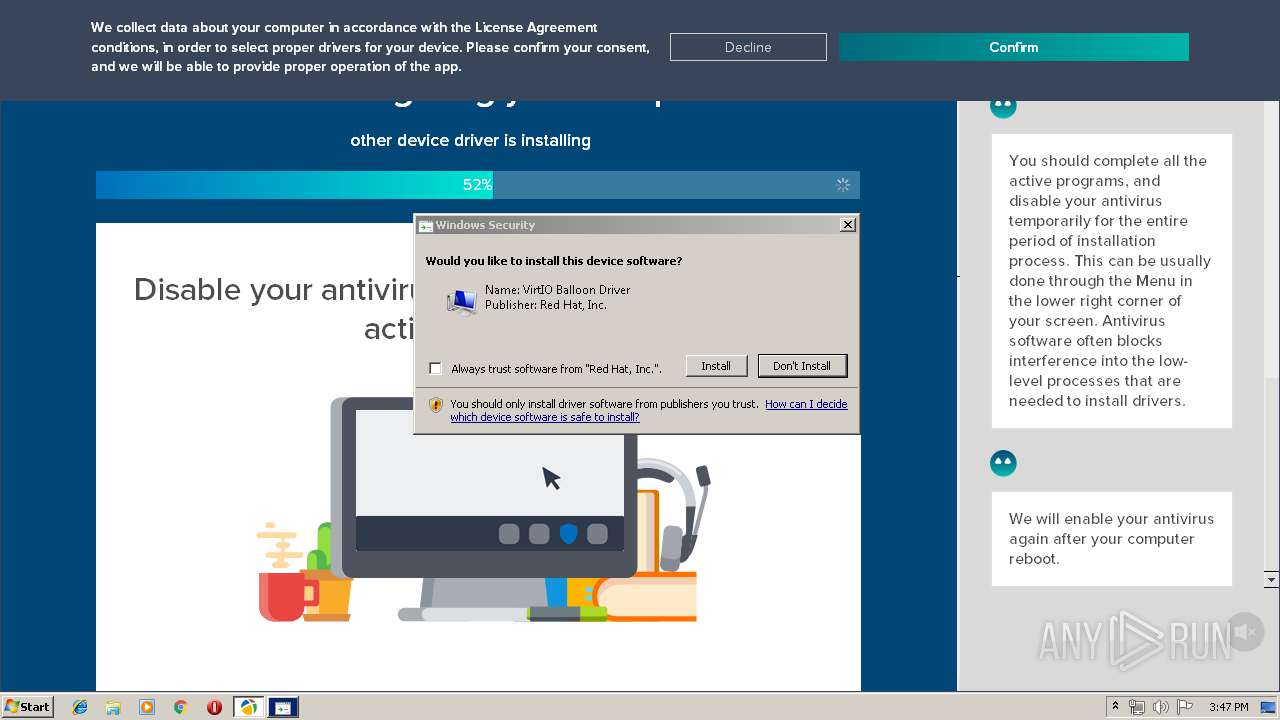
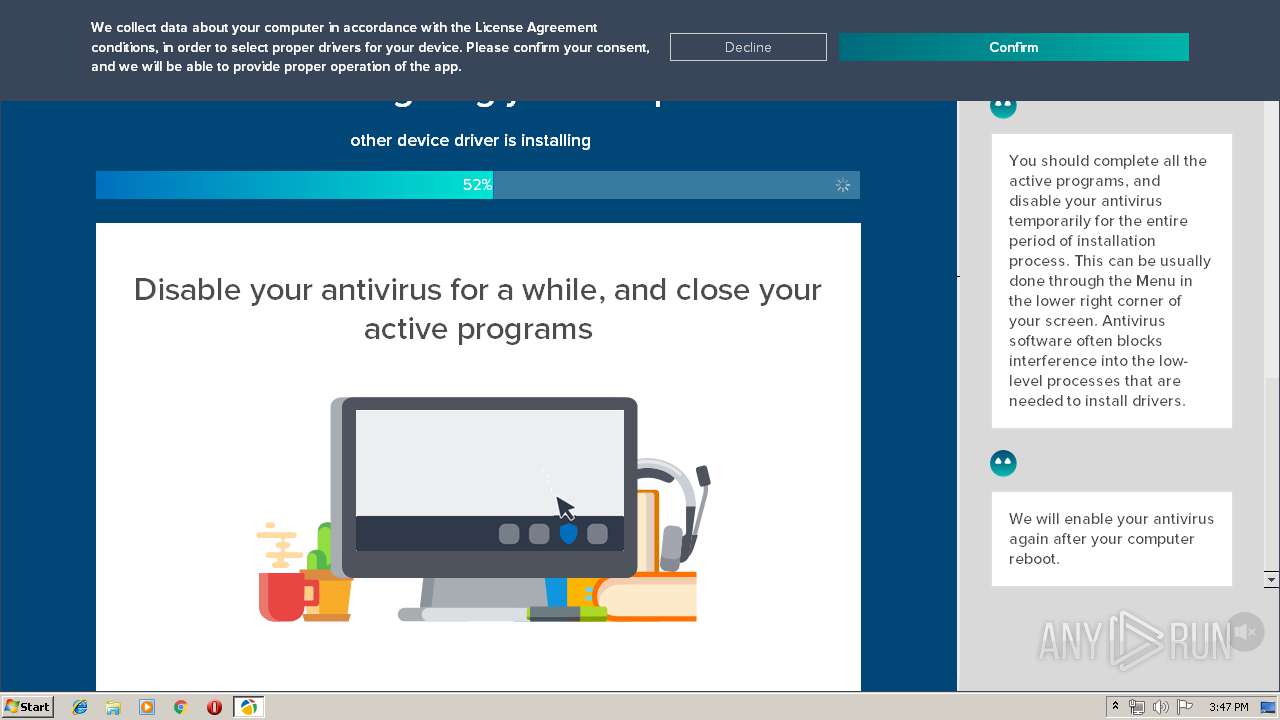
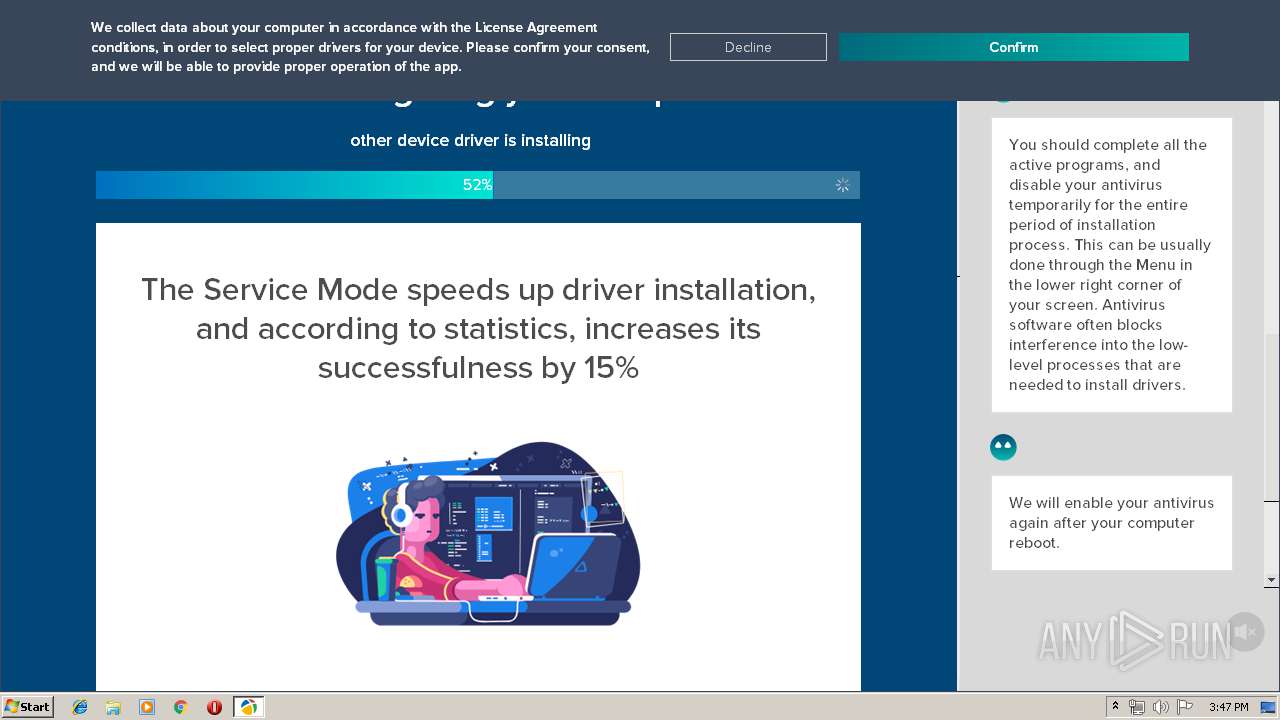
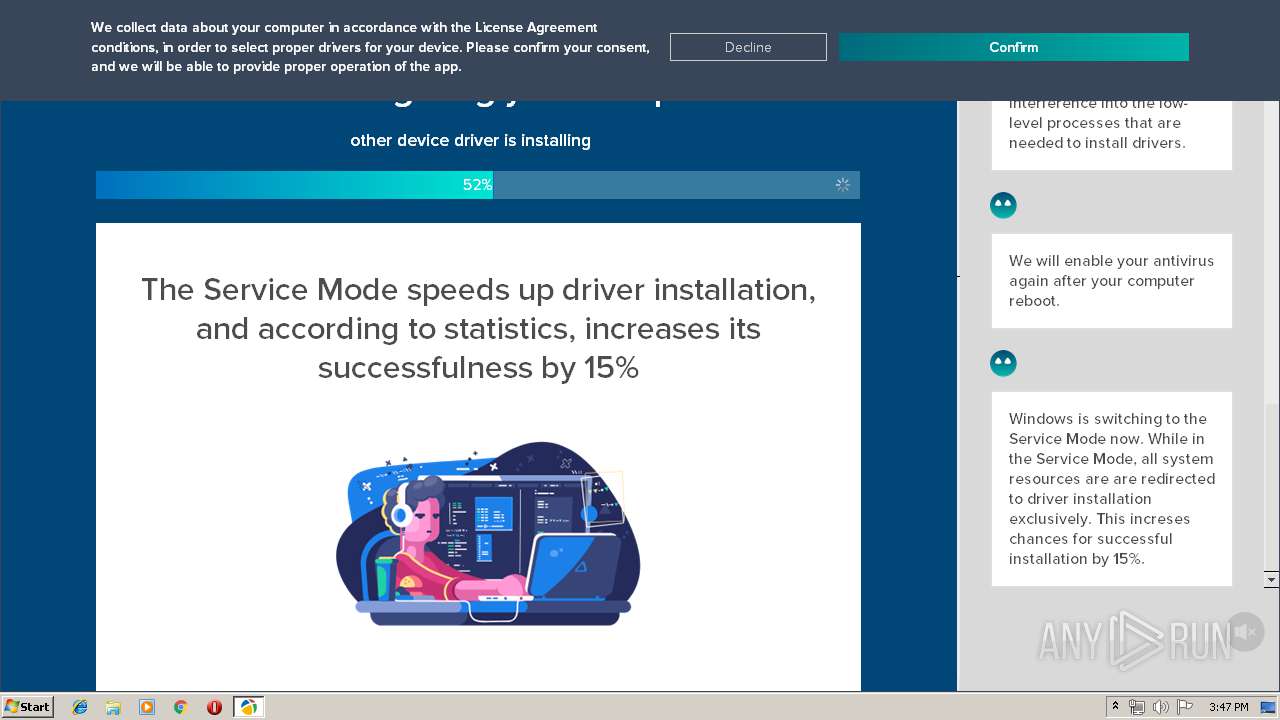
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | January 02, 2020, 15:45:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C15C7488E9F4AF222E9F14ED706EF213 |
| SHA1: | FB4C38FAB3E0B54A1E909D6E9C29273A48C95B93 |
| SHA256: | D82F09C5A4D13AE1E2329BFC2B42BC07F7E79A92C18B5E66419F1D25FD6B47B9 |
| SSDEEP: | 12288:eV60jdYFiNJ2xT5jkMR0YSTWRHDLOZKKu6toqlzqvdOYeP5WAE5mwu:ejdYgiTmBOjyNoRFOYK5Xw3u |
MALICIOUS
Downloads executable files from the Internet
- wscript.exe (PID: 716)
- aria2c.exe (PID: 3448)
Executes PowerShell scripts
- cmd.exe (PID: 1852)
Starts Visual C# compiler
- powershell.exe (PID: 1096)
Changes settings of System certificates
- mshta.exe (PID: 3096)
Application was dropped or rewritten from another process
- driverpack-7za.exe (PID: 2524)
- driverpack-wget.exe (PID: 2176)
- aria2c.exe (PID: 2492)
- aria2c.exe (PID: 3448)
- aria2c.exe (PID: 2412)
- aria2c.exe (PID: 3148)
- driverpack-7za.exe (PID: 3136)
- driverpack-7za.exe (PID: 1816)
- devcon.exe (PID: 2064)
- RuntimePack.exe (PID: 3592)
- DirectX.exe (PID: 3900)
Changes internet zones settings
- mshta.exe (PID: 3096)
Loads dropped or rewritten executable
- DrvInst.exe (PID: 2828)
- regsvr32.exe (PID: 3436)
- regsvr32.exe (PID: 3796)
- regsvr32.exe (PID: 3224)
- regsvr32.exe (PID: 1504)
- regsvr32.exe (PID: 688)
- regsvr32.exe (PID: 2808)
- regsvr32.exe (PID: 2468)
- regsvr32.exe (PID: 1028)
- regsvr32.exe (PID: 1552)
- regsvr32.exe (PID: 3584)
- regsvr32.exe (PID: 3500)
- regsvr32.exe (PID: 4012)
- regsvr32.exe (PID: 3264)
- regsvr32.exe (PID: 2988)
- regsvr32.exe (PID: 2600)
- regsvr32.exe (PID: 3112)
- DirectX.exe (PID: 3900)
- regsvr32.exe (PID: 2968)
- regsvr32.exe (PID: 3920)
- regsvr32.exe (PID: 2872)
- regsvr32.exe (PID: 2332)
- regsvr32.exe (PID: 3612)
- regsvr32.exe (PID: 3952)
- regsvr32.exe (PID: 3668)
- regsvr32.exe (PID: 1560)
- regsvr32.exe (PID: 1956)
- regsvr32.exe (PID: 3228)
- regsvr32.exe (PID: 3292)
- regsvr32.exe (PID: 2776)
- regsvr32.exe (PID: 2112)
- regsvr32.exe (PID: 3028)
- regsvr32.exe (PID: 2404)
- regsvr32.exe (PID: 2420)
- regsvr32.exe (PID: 1752)
- regsvr32.exe (PID: 3712)
- regsvr32.exe (PID: 3908)
- regsvr32.exe (PID: 1732)
- regsvr32.exe (PID: 3396)
- regsvr32.exe (PID: 3992)
- regsvr32.exe (PID: 1412)
- regsvr32.exe (PID: 3268)
- regsvr32.exe (PID: 2852)
- regsvr32.exe (PID: 1768)
- regsvr32.exe (PID: 1556)
- regsvr32.exe (PID: 2824)
- regsvr32.exe (PID: 2404)
Registers / Runs the DLL via REGSVR32.EXE
- RuntimePack.exe (PID: 3592)
- cmd.exe (PID: 1636)
- DirectX.exe (PID: 3900)
Changes the autorun value in the registry
- mshta.exe (PID: 3096)
SUSPICIOUS
Uses REG.EXE to modify Windows registry
- DriverPack-17-Online_1758497922.1550022335.exe (PID: 1532)
Starts MSHTA.EXE for opening HTA or HTMLS files
- DriverPack-17-Online_1758497922.1550022335.exe (PID: 1532)
Creates files in the user directory
- wscript.exe (PID: 3532)
- wscript.exe (PID: 184)
- wscript.exe (PID: 912)
- wscript.exe (PID: 2860)
- mshta.exe (PID: 3096)
- cmd.exe (PID: 1852)
- powershell.exe (PID: 1096)
- cmd.exe (PID: 1188)
- cmd.exe (PID: 1728)
- driverpack-7za.exe (PID: 2524)
- cmd.exe (PID: 2260)
- cmd.exe (PID: 1784)
- cmd.exe (PID: 2648)
- cmd.exe (PID: 3888)
- aria2c.exe (PID: 2492)
- aria2c.exe (PID: 3448)
- aria2c.exe (PID: 2412)
- aria2c.exe (PID: 3148)
- cmd.exe (PID: 1848)
- cmd.exe (PID: 2828)
- cmd.exe (PID: 2776)
- cmd.exe (PID: 2252)
- cmd.exe (PID: 1728)
- cmd.exe (PID: 3832)
- cmd.exe (PID: 3720)
- cmd.exe (PID: 3964)
- cmd.exe (PID: 1152)
- cmd.exe (PID: 3316)
- cmd.exe (PID: 1520)
- DriverPack-Alice.exe (PID: 2968)
Executable content was dropped or overwritten
- wscript.exe (PID: 716)
- aria2c.exe (PID: 3448)
- driverpack-7za.exe (PID: 1816)
- devcon.exe (PID: 2064)
- DrvInst.exe (PID: 2736)
- aria2c.exe (PID: 3148)
- DrvInst.exe (PID: 2828)
- RuntimePack.exe (PID: 3592)
- xcopy.exe (PID: 3192)
- xcopy.exe (PID: 3700)
- cmd.exe (PID: 1636)
- DirectX.exe (PID: 3900)
- DriverPack-Alice.exe (PID: 2968)
Executes scripts
- mshta.exe (PID: 3096)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 1188)
- cmd.exe (PID: 1728)
- cmd.exe (PID: 2648)
- mshta.exe (PID: 3096)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 3096)
- cmd.exe (PID: 1728)
- RuntimePack.exe (PID: 3592)
Adds / modifies Windows certificates
- mshta.exe (PID: 3096)
Uses RUNDLL32.EXE to load library
- mshta.exe (PID: 3096)
- DrvInst.exe (PID: 2736)
Starts application with an unusual extension
- cmd.exe (PID: 2648)
- cmd.exe (PID: 1728)
Reads Internet Cache Settings
- mshta.exe (PID: 3096)
Starts SC.EXE for service management
- cmd.exe (PID: 1784)
Executed as Windows Service
- vssvc.exe (PID: 2536)
Executed via COM
- DllHost.exe (PID: 564)
- DrvInst.exe (PID: 2736)
- DrvInst.exe (PID: 2828)
Connects to unusual port
- aria2c.exe (PID: 3148)
- aria2c.exe (PID: 2412)
Creates files in the Windows directory
- DrvInst.exe (PID: 2736)
- DrvInst.exe (PID: 2828)
- xcopy.exe (PID: 3700)
- xcopy.exe (PID: 3192)
- cmd.exe (PID: 1636)
- DirectX.exe (PID: 3900)
Creates files in the driver directory
- DrvInst.exe (PID: 2736)
- DrvInst.exe (PID: 2828)
Removes files from Windows directory
- DrvInst.exe (PID: 2736)
- DrvInst.exe (PID: 2828)
Uses TASKLIST.EXE to query information about running processes
- cmd.exe (PID: 1728)
Application launched itself
- cmd.exe (PID: 1728)
Creates COM task schedule object
- regsvr32.exe (PID: 2988)
- regsvr32.exe (PID: 4012)
- regsvr32.exe (PID: 2776)
- regsvr32.exe (PID: 3028)
- regsvr32.exe (PID: 2404)
- regsvr32.exe (PID: 2112)
- regsvr32.exe (PID: 3268)
- regsvr32.exe (PID: 1412)
- regsvr32.exe (PID: 1768)
- regsvr32.exe (PID: 3396)
- regsvr32.exe (PID: 2404)
- regsvr32.exe (PID: 1732)
- regsvr32.exe (PID: 3292)
- regsvr32.exe (PID: 3908)
- regsvr32.exe (PID: 3712)
- regsvr32.exe (PID: 2824)
- regsvr32.exe (PID: 1556)
- regsvr32.exe (PID: 2872)
- regsvr32.exe (PID: 1560)
- regsvr32.exe (PID: 3228)
- regsvr32.exe (PID: 1956)
- regsvr32.exe (PID: 3612)
- regsvr32.exe (PID: 3668)
- regsvr32.exe (PID: 2332)
- regsvr32.exe (PID: 3952)
- regsvr32.exe (PID: 3992)
- regsvr32.exe (PID: 2852)
- regsvr32.exe (PID: 1752)
- regsvr32.exe (PID: 2420)
INFO
Reads internet explorer settings
- mshta.exe (PID: 3096)
Reads settings of System Certificates
- mshta.exe (PID: 3096)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2536)
Reads the hosts file
- aria2c.exe (PID: 2492)
- aria2c.exe (PID: 3148)
- aria2c.exe (PID: 3448)
- aria2c.exe (PID: 2412)
Searches for installed software
- DrvInst.exe (PID: 2736)
Dropped object may contain Bitcoin addresses
- DriverPack-Alice.exe (PID: 2968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:03:20 08:29:28+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 111616 |
| InitializedDataSize: | 375296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1b9bf |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 17.9.1.0 |
| ProductVersionNumber: | 17.9.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | DriverPack Solution |
| FileDescription: | DriverPack |
| FileVersion: | 17.9.1 |
| InternalName: | DriverPack |
| LegalCopyright: | Copyright © Kuzyakov Artur |
| OriginalFileName: | DriverPack-Online-v17.9.1-4c48a93.exe |
| PrivateBuild: | 2018 |
| ProductName: | driverpack online |
| ProductVersion: | 17.9.1 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 20-Mar-2016 07:29:28 |
| Detected languages: |
|
| CompanyName: | DriverPack Solution |
| FileDescription: | DriverPack |
| FileVersion: | 17.9.1 |
| InternalName: | DriverPack |
| LegalCopyright: | Copyright © Kuzyakov Artur |
| OriginalFilename: | DriverPack-Online-v17.9.1-4c48a93.exe |
| PrivateBuild: | 2018 |
| ProductName: | driverpack online |
| ProductVersion: | 17.9.1 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0060 |
| Pages in file: | 0x0001 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000060 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 20-Mar-2016 07:29:28 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0001B36A | 0x0001B400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.69607 |
.rdata | 0x0001D000 | 0x000040D2 | 0x00004200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.65115 |
.data | 0x00022000 | 0x00004C30 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.82595 |
.rsrc | 0x00027000 | 0x00057000 | 0x00057000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.83401 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.23595 | 932 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 2.9356 | 19496 | Latin 1 / Western European | Russian - Russia | RT_ICON |
3 | 3.23783 | 11432 | Latin 1 / Western European | Russian - Russia | RT_ICON |
4 | 3.5842 | 5672 | Latin 1 / Western European | Russian - Russia | RT_ICON |
5 | 4.08499 | 3752 | UNKNOWN | Russian - Russia | RT_ICON |
6 | 4.47772 | 2216 | UNKNOWN | Russian - Russia | RT_ICON |
7 | 4.59548 | 1736 | UNKNOWN | Russian - Russia | RT_ICON |
8 | 4.67063 | 1384 | UNKNOWN | Russian - Russia | RT_ICON |
9 | 7.94023 | 15006 | UNKNOWN | Russian - Russia | RT_ICON |
10 | 2.61384 | 67624 | UNKNOWN | Russian - Russia | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
MSVCRT.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
197
Monitored processes
127
Malicious processes
17
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Windows\System32\wscript.exe" //B prepare.js drivers | C:\Windows\System32\wscript.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 564 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 688 | "C:\Windows\System32\regsvr32.exe" /S mscomctl.ocx | C:\Windows\System32\regsvr32.exe | — | RuntimePack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 716 | "C:\Windows\System32\wscript.exe" //B prepare.js binaries | C:\Windows\System32\wscript.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 912 | "C:\Windows\System32\wscript.exe" //B prepare.js newsoft | C:\Windows\System32\wscript.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 952 | "C:\Windows\System32\regsvr32.exe" /S dblist32.ocx | C:\Windows\System32\regsvr32.exe | — | RuntimePack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1012 | wmic.exe /Namespace:\\root\default Path SystemRestore Call CreateRestorePoint "DriverPack 17.11.21", 100, 10 | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | "C:\Windows\System32\regsvr32.exe" /S mshflxgd.ocx | C:\Windows\System32\regsvr32.exe | — | RuntimePack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1096 | powershell -NonInteractive -NoLogo -NoProfile -ExecutionPolicy Bypass "Get-Content 'C:\Users\admin\AppData\Roaming\DRPSu\temp\ps.k4wwjm9z.o6xns.cmd.txt' -Wait | Invoke-Expression" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1152 | "C:\Windows\System32\cmd.exe" /c ""C:\Users\admin\AppData\Roaming\DRPSu\PROGRAMS\DirectX.exe" || echo Done & call echo Done %^errorLevel% > "C:\Users\admin\AppData\Roaming\DRPSu\temp\installing_89719.txt"" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
7 421
Read events
2 813
Write events
4 302
Delete events
306
Modification events
| (PID) Process: | (2260) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\drp.su\update |
| Operation: | write | Name: | http |
Value: 1 | |||
| (PID) Process: | (2260) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\drp.su\update |
| Operation: | write | Name: | https |
Value: 1 | |||
| (PID) Process: | (2260) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | GlobalUserOffline |
Value: 0 | |||
| (PID) Process: | (2260) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Styles |
| Operation: | write | Name: | MaxScriptStatements |
Value: 4294967295 | |||
| (PID) Process: | (2260) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Styles |
| Operation: | write | Name: | MaxScriptStatements |
Value: 4294967295 | |||
| (PID) Process: | (1532) DriverPack-17-Online_1758497922.1550022335.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1532) DriverPack-17-Online_1758497922.1550022335.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3096) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3096) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3096) mshta.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\DirectDraw\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: mshta.exe | |||
Executable files
284
Suspicious files
107
Text files
6 622
Unknown types
57
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1532 | DriverPack-17-Online_1758497922.1550022335.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\bin\img\screens\globe_hover.png | image | |
MD5:FE8F79F2AA6887CC155478C1B2BB8A9D | SHA256:4D255348C5462408FF1A9EAAB744E82CAB23BCE5024D29C658905937182735D0 | |||
| 1532 | DriverPack-17-Online_1758497922.1550022335.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\bin\img\screens\language-arrow.png | image | |
MD5:5426437801A1BA94BDE2A04FDECC8B14 | SHA256:C856CCD26C814F800DADB7C44317F1B6728EA71B5A87E1A9B549E424B425A9C7 | |||
| 1532 | DriverPack-17-Online_1758497922.1550022335.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\bin\img\screens\globe_normal.png | image | |
MD5:A42CCA03383138F026F43CF9C0A36AA6 | SHA256:29624620F0FD8B8904418A8248B90E5CAC58904C07C5F2EB6C29BE510D0121AA | |||
| 1532 | DriverPack-17-Online_1758497922.1550022335.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\bin\img\screens\new-logo.png | image | |
MD5:3878A76A6B6724B2F7847E13CCE4B320 | SHA256:78D8A5C194ABF73D655126C8CD09FBA5CA4B46F3773667E8A55D3B6F24D85697 | |||
| 1532 | DriverPack-17-Online_1758497922.1550022335.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\bin\img\header\header-logo$2x.png | image | |
MD5:074E86D2232B86271D9BBB3ABE47EE1A | SHA256:B0A53BFB7F2B8780F736425ED686CE741829724682DE3365FADFEF5998F70469 | |||
| 1532 | DriverPack-17-Online_1758497922.1550022335.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\bin\img\no_internet\no_internet-complete.png | image | |
MD5:9317F902A1A6C30F7B7D2D6BE2002803 | SHA256:196DA0C1548EB42D823CF27F62DD25BA79B4E70CB858BBA00BFDF23BE385626B | |||
| 1532 | DriverPack-17-Online_1758497922.1550022335.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\bin\img\no_internet\no_internet-connection.png | image | |
MD5:A43605B4AB97297A27AC68B3747E61FB | SHA256:677B6AE48B0A71E404D57534F943EF323C41E58212F55D81F96321664AAC440C | |||
| 1532 | DriverPack-17-Online_1758497922.1550022335.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\bin\img\programs\scan.png | image | |
MD5:33DDC7F529563C10320F2F3743A62D9D | SHA256:610F8F16AD537BBD378367CA75B0D2B7C5AE83374068AF5C7658E487087826D1 | |||
| 1532 | DriverPack-17-Online_1758497922.1550022335.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\bin\Tools\Icon.ico | image | |
MD5:733D67C2E70BC804CD9497D20FE96696 | SHA256:0A3EDD3D1FD9AE649D0D6164858705017DC482CE56D090A478F57D02619E88CE | |||
| 1532 | DriverPack-17-Online_1758497922.1550022335.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\bin\img\no_internet\no_internet-step1.png | image | |
MD5:FEDBAE40F618A1315DBCA54071708013 | SHA256:018E28F327C21D124BD38DC6C7D80BF8B3A1E61CDD533C31F57F8685F90CB0FB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
399
TCP/UDP connections
354
DNS requests
26
Threats
476
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3096 | mshta.exe | GET | 301 | 104.26.6.24:80 | http://allfont.ru/allfont.css?fonts=lucida-console | US | html | 552 b | whitelisted |
3096 | mshta.exe | GET | 200 | 87.117.235.116:80 | http://update.drp.su/v2/ | GB | text | 57.4 Kb | malicious |
3096 | mshta.exe | GET | 200 | 87.117.235.116:80 | http://update.drp.su/beetle/17.11.21/DriverPackSolution.html | GB | html | 1.66 Kb | malicious |
3096 | mshta.exe | GET | 200 | 87.117.235.116:80 | http://update.drp.su/beetle/17.11.21/css/roboto.css | GB | text | 263 b | malicious |
3096 | mshta.exe | GET | 200 | 87.117.235.116:80 | http://update.drp.su/beetle/17.11.21/css/proximanova.css | GB | text | 360 b | malicious |
3096 | mshta.exe | GET | 200 | 87.117.235.116:80 | http://update.drp.su/beetle/17.11.21/css/normalize.min.css | GB | text | 906 b | malicious |
3096 | mshta.exe | GET | 200 | 87.117.235.116:80 | http://update.drp.su/beetle/17.11.21/css/custom-control.css | GB | text | 1.91 Kb | malicious |
3096 | mshta.exe | GET | 200 | 87.117.235.116:80 | http://update.drp.su/beetle/17.11.21/config.js | GB | text | 1012 b | malicious |
3096 | mshta.exe | GET | 200 | 87.117.235.116:80 | http://update.drp.su/beetle/17.11.21/css/icons.css | GB | text | 217 b | malicious |
3096 | mshta.exe | GET | 200 | 87.117.235.116:80 | http://update.drp.su/beetle/17.11.21/css/icons-checkbox.css | GB | text | 193 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3096 | mshta.exe | 87.117.235.116:80 | update.drp.su | iomart Cloud Services Limited. | GB | unknown |
716 | wscript.exe | 81.94.205.66:80 | download.drp.su | iomart Cloud Services Limited. | GB | malicious |
3096 | mshta.exe | 82.145.55.124:80 | update.drp.su | iomart Cloud Services Limited. | GB | unknown |
3096 | mshta.exe | 104.26.6.24:80 | allfont.ru | Cloudflare Inc | US | unknown |
3096 | mshta.exe | 87.250.251.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
3096 | mshta.exe | 178.162.204.5:80 | auth.drp.su | Leaseweb Deutschland GmbH | DE | suspicious |
3096 | mshta.exe | 172.217.18.110:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
3096 | mshta.exe | 81.94.205.66:80 | download.drp.su | iomart Cloud Services Limited. | GB | malicious |
2176 | driverpack-wget.exe | 81.94.205.66:80 | download.drp.su | iomart Cloud Services Limited. | GB | malicious |
— | — | 82.145.55.124:80 | update.drp.su | iomart Cloud Services Limited. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
update.drp.su |
| malicious |
download.drp.su |
| malicious |
allfont.ru |
| whitelisted |
auth.drp.su |
| suspicious |
mc.yandex.ru |
| whitelisted |
dl.drp.su |
| whitelisted |
www.google-analytics.com |
| whitelisted |
www.msftncsi.com |
| whitelisted |
bt2.driverpacks.net |
| suspicious |
download.driverpacks.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
3096 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3096 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3096 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3096 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3096 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3096 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3096 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3096 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3096 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
57 ETPRO signatures available at the full report
Process | Message |
|---|---|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cppҔ⦴캪솃ǕҔ
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|