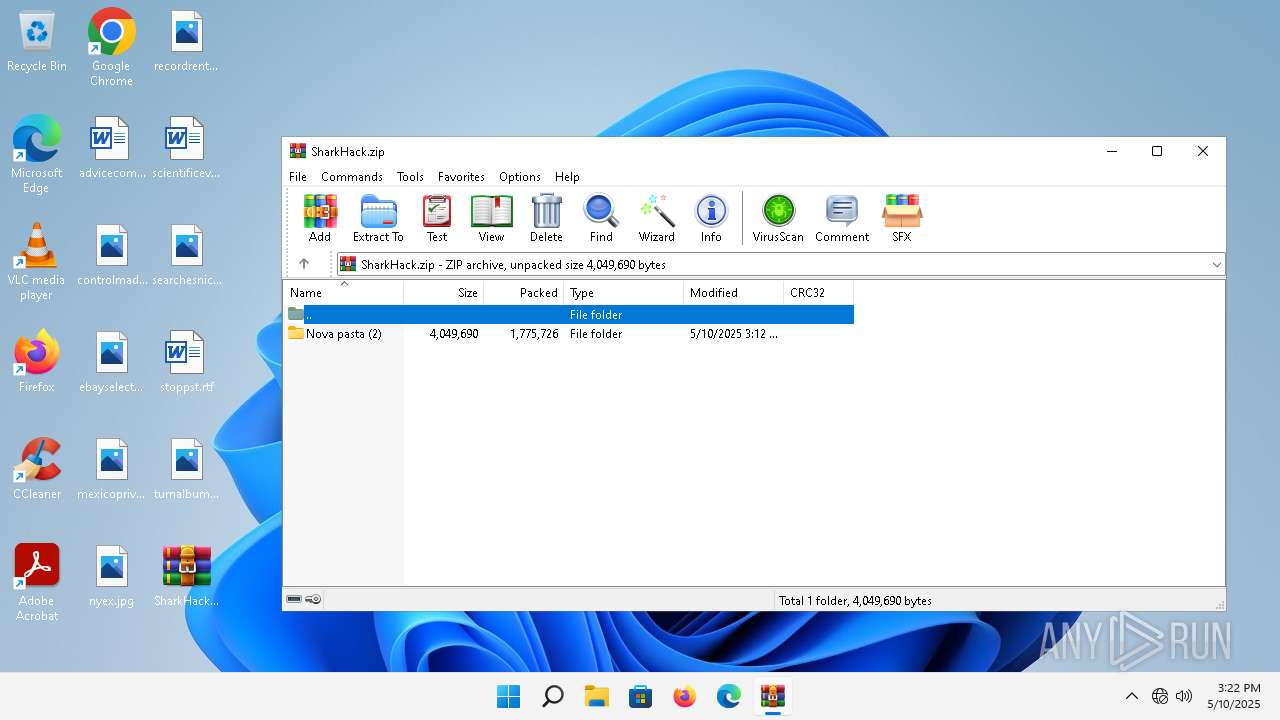
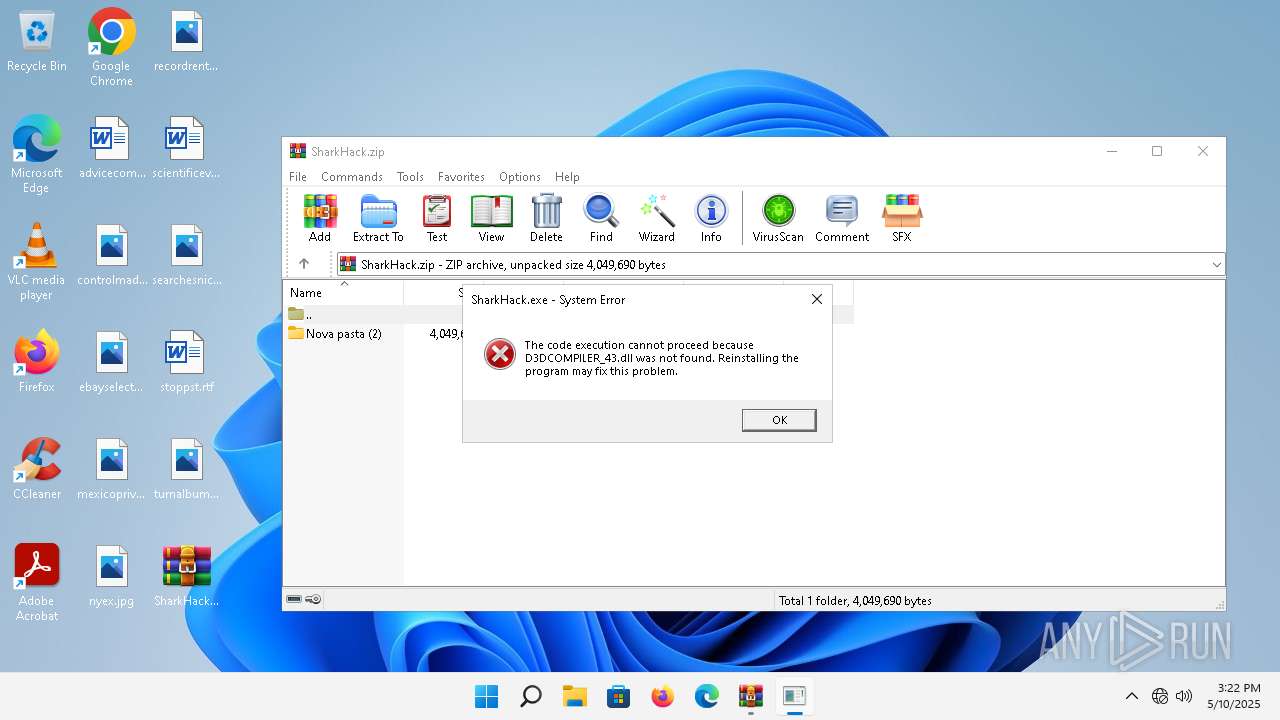
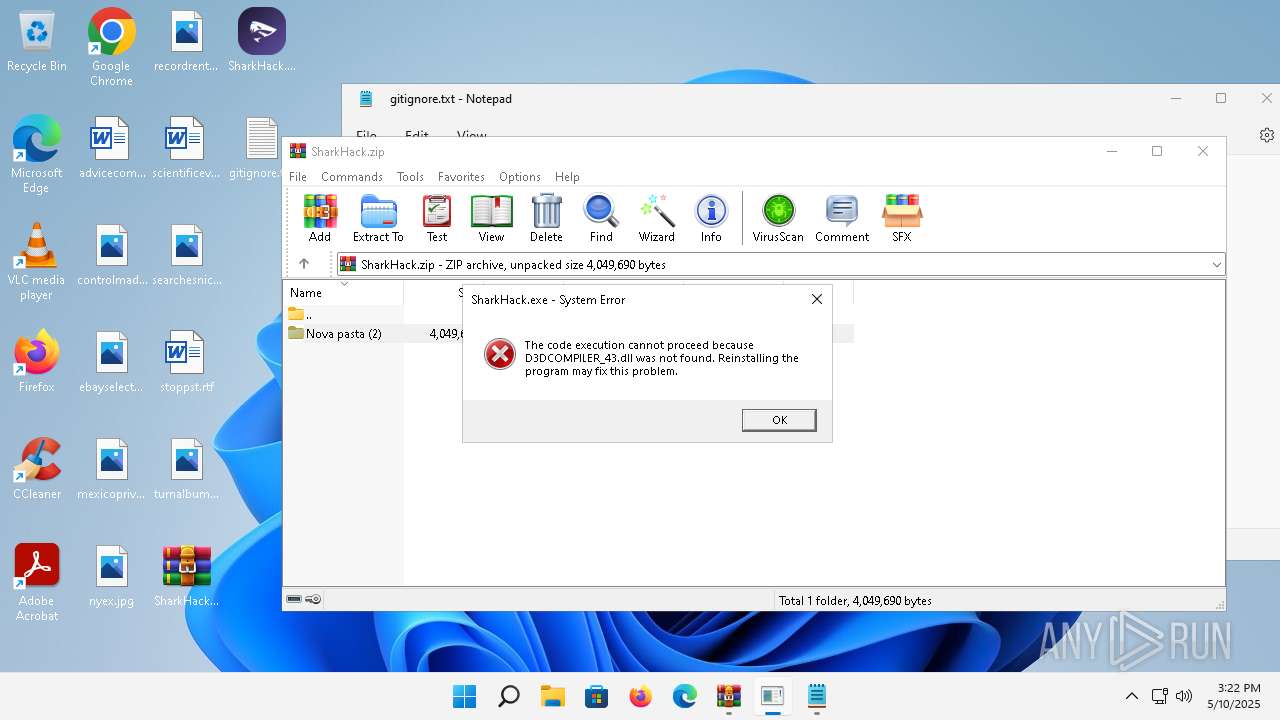
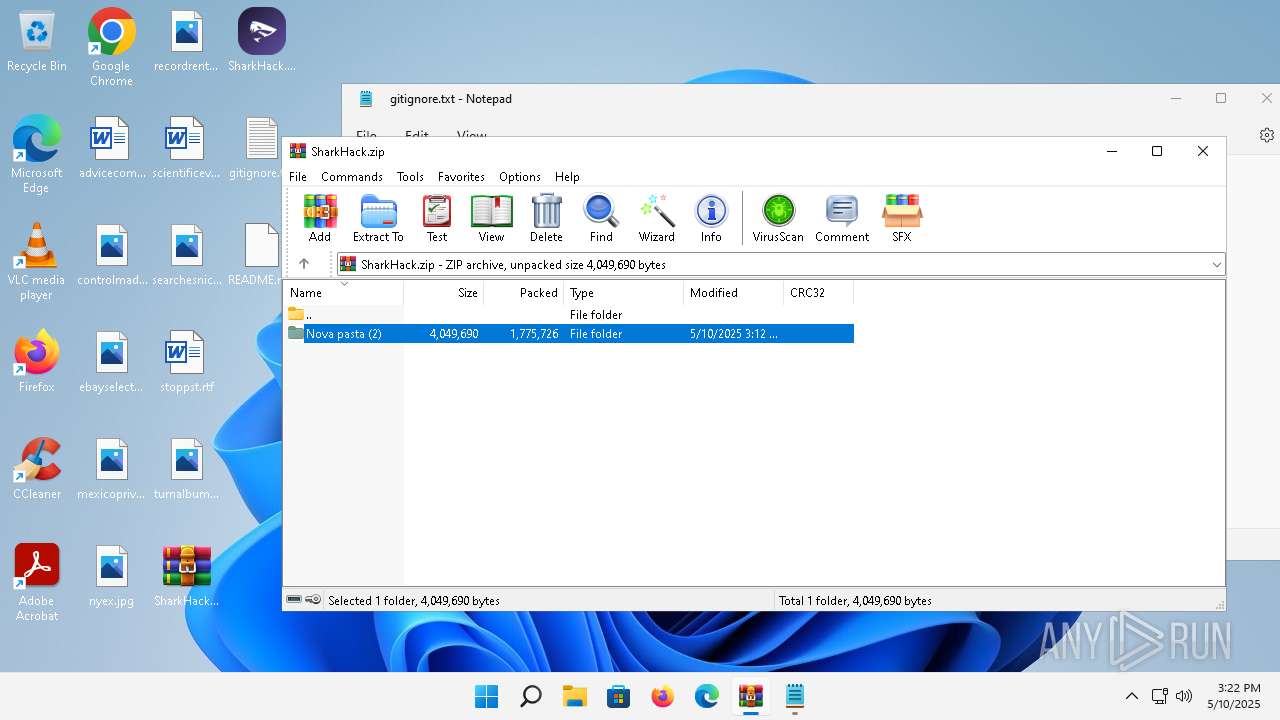
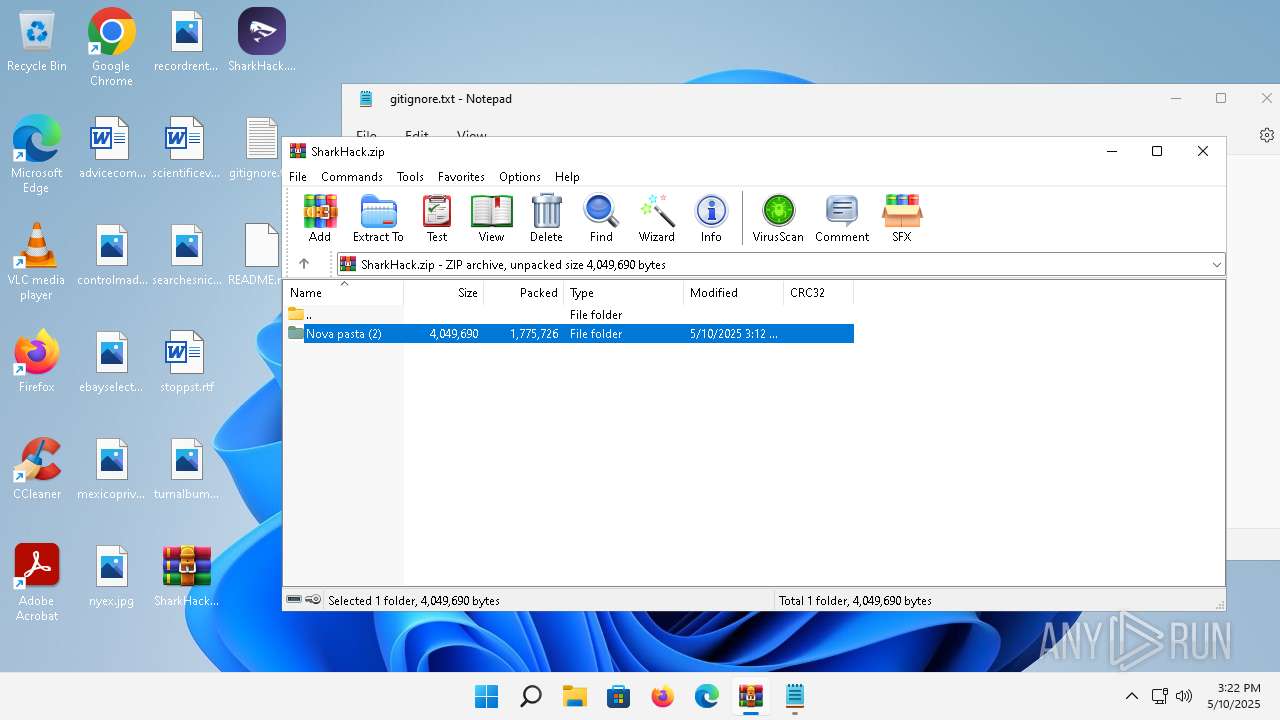
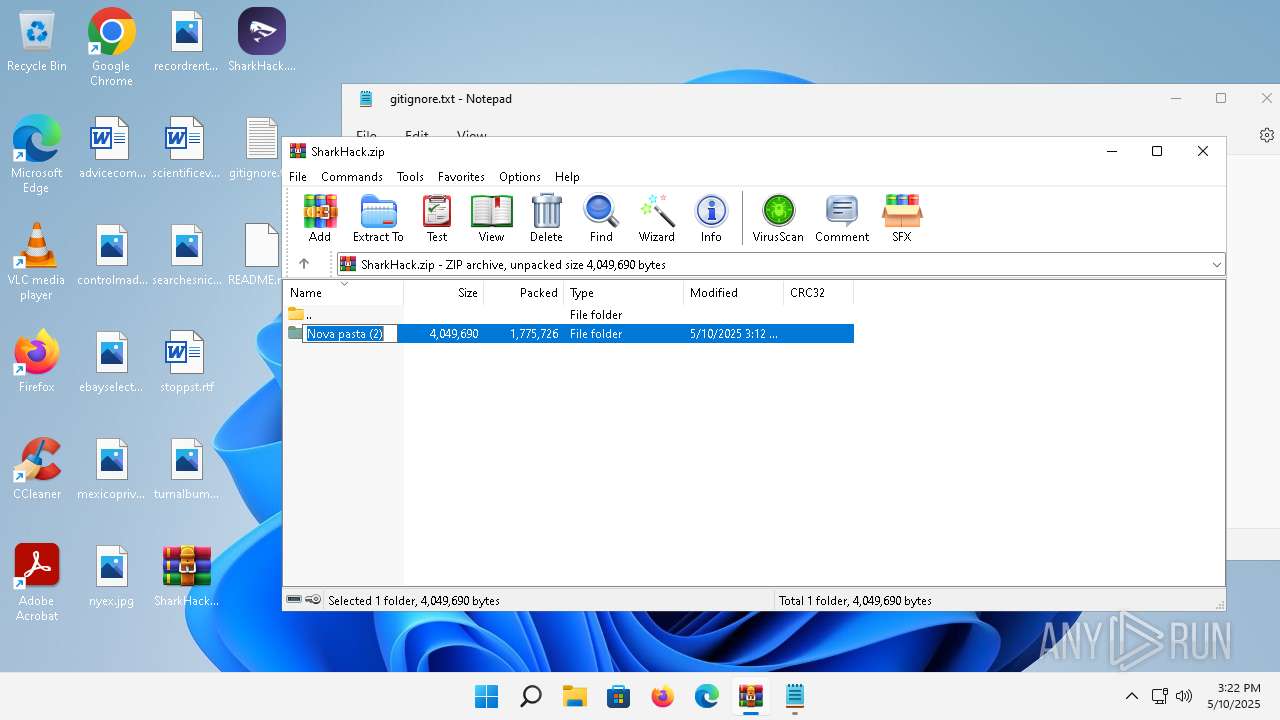
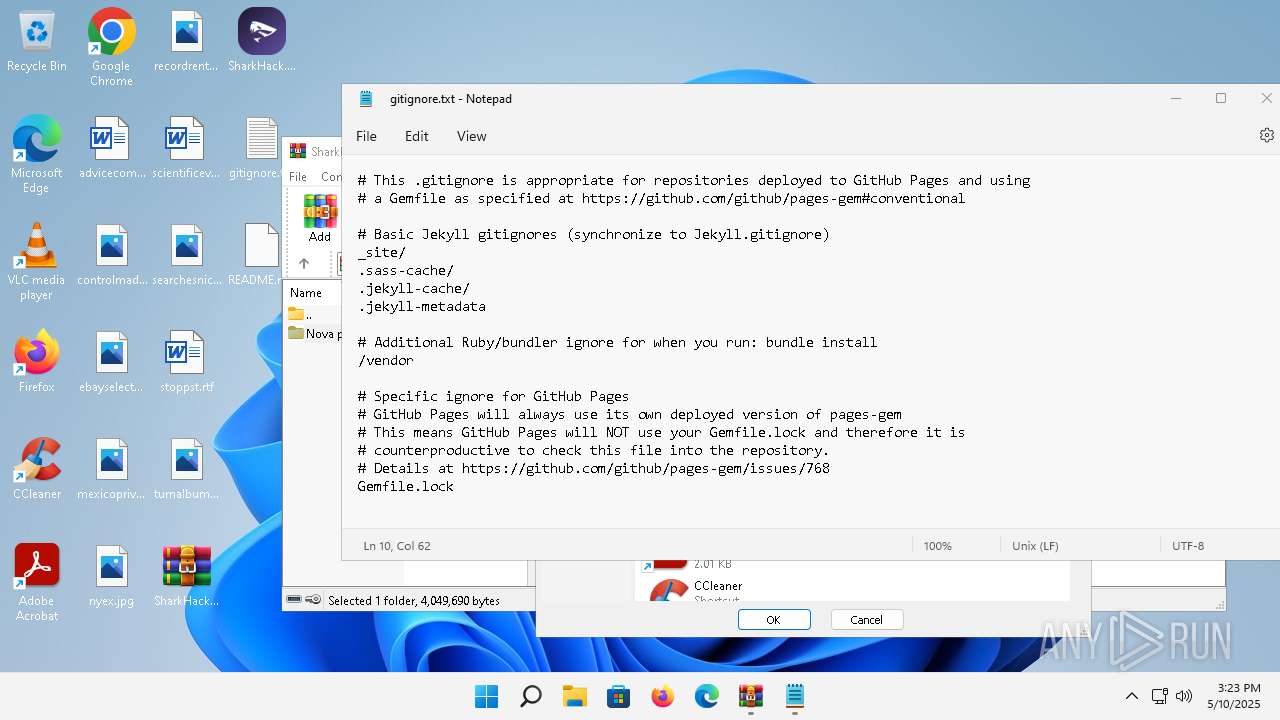
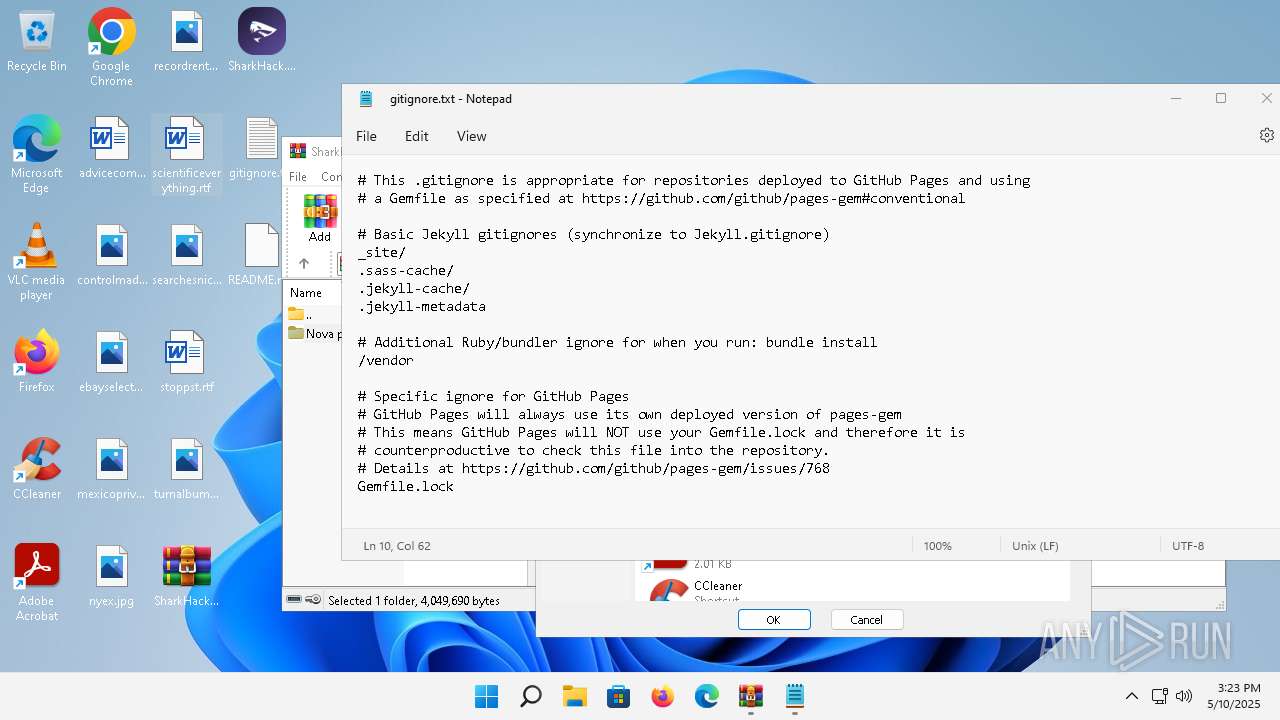
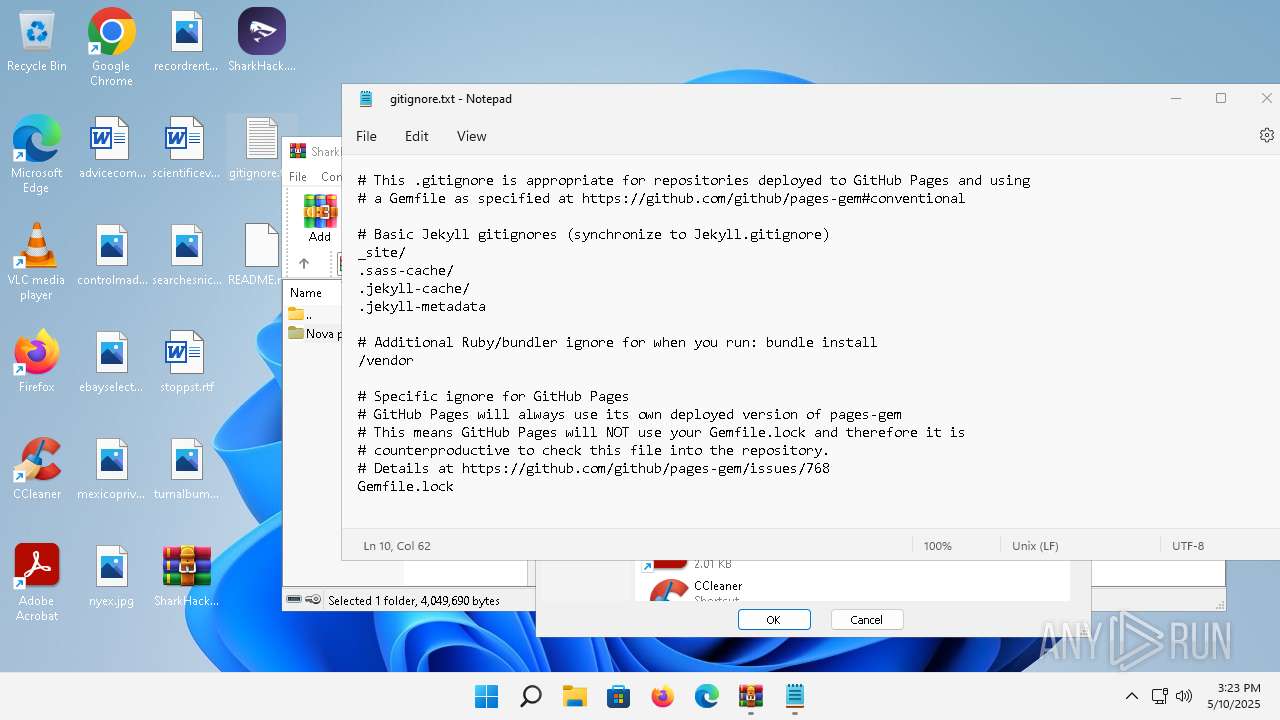
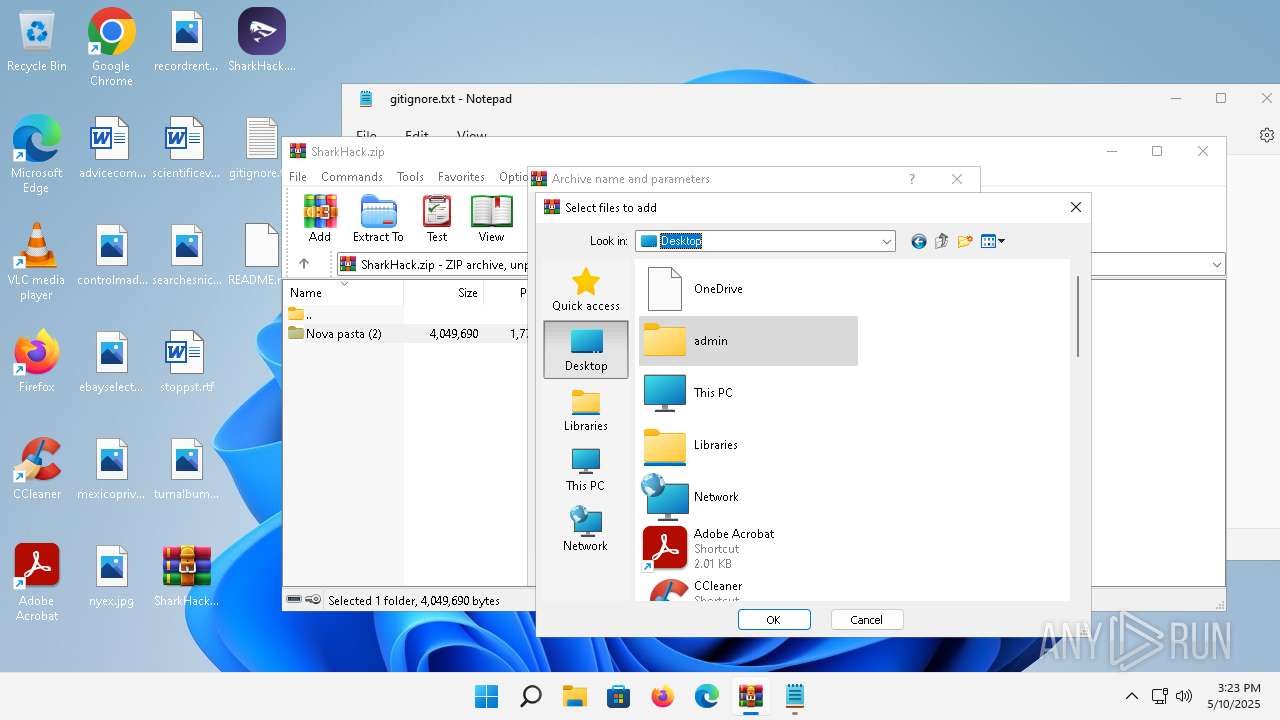
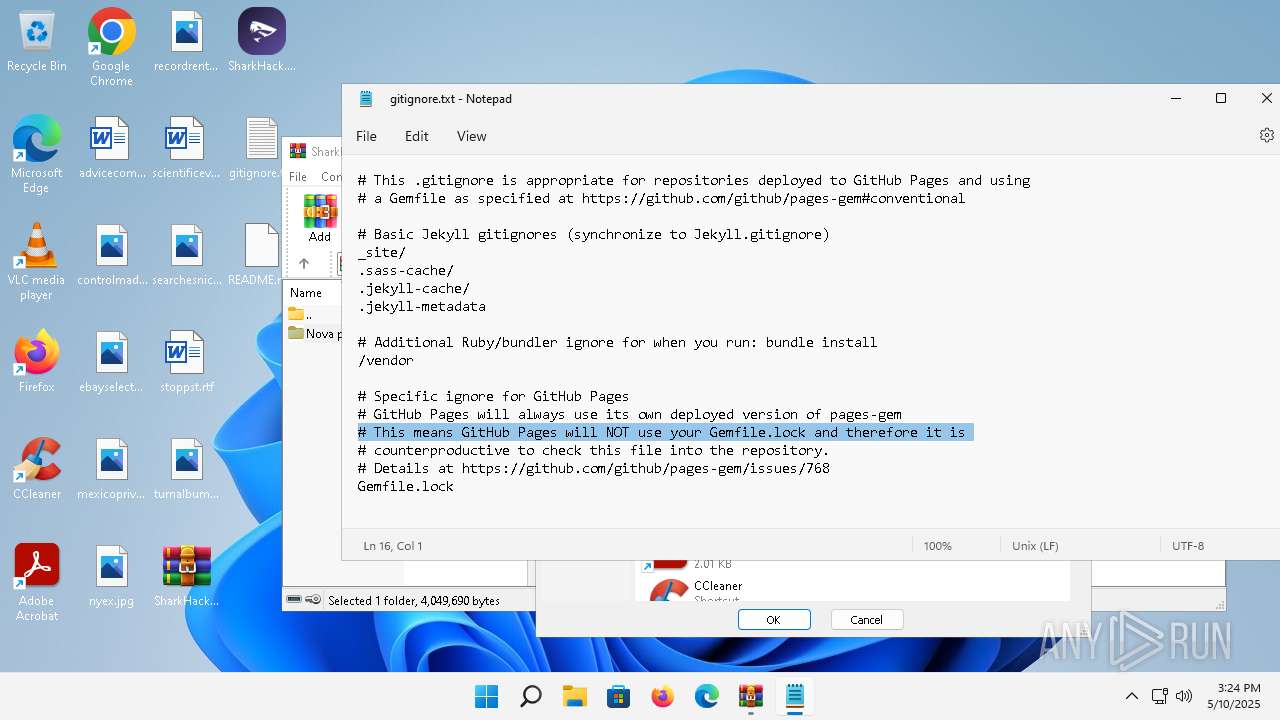
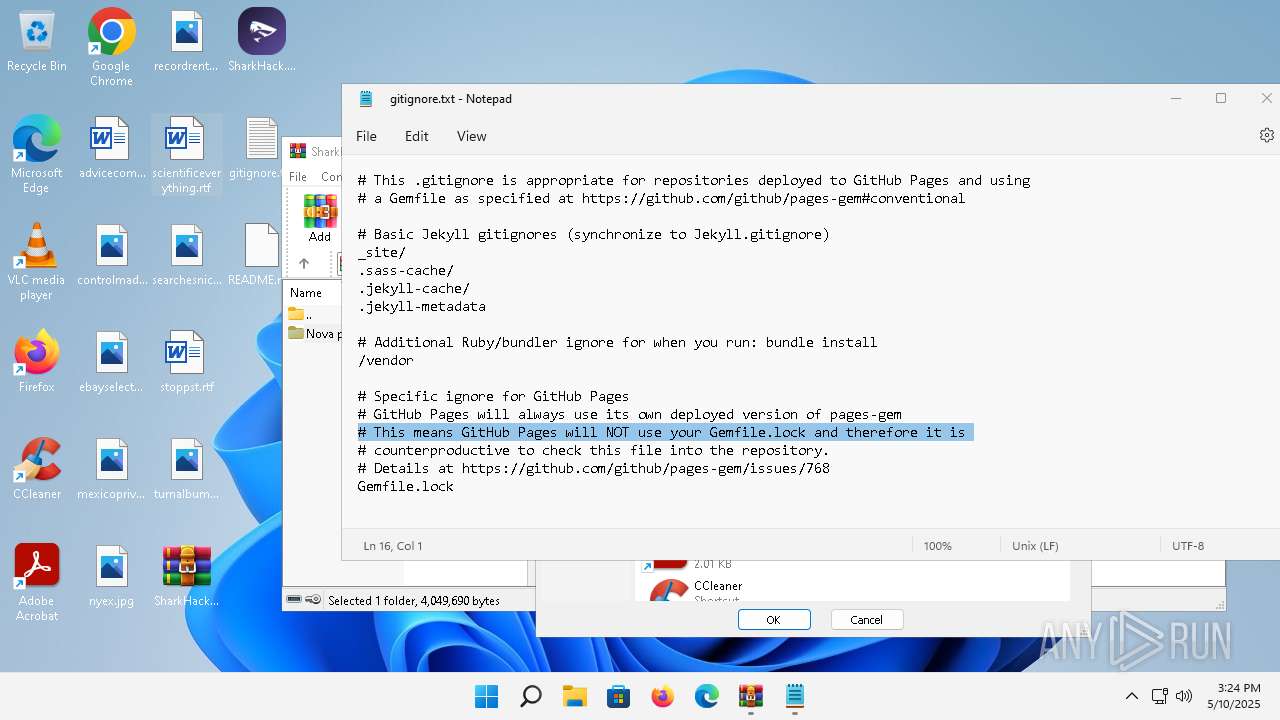
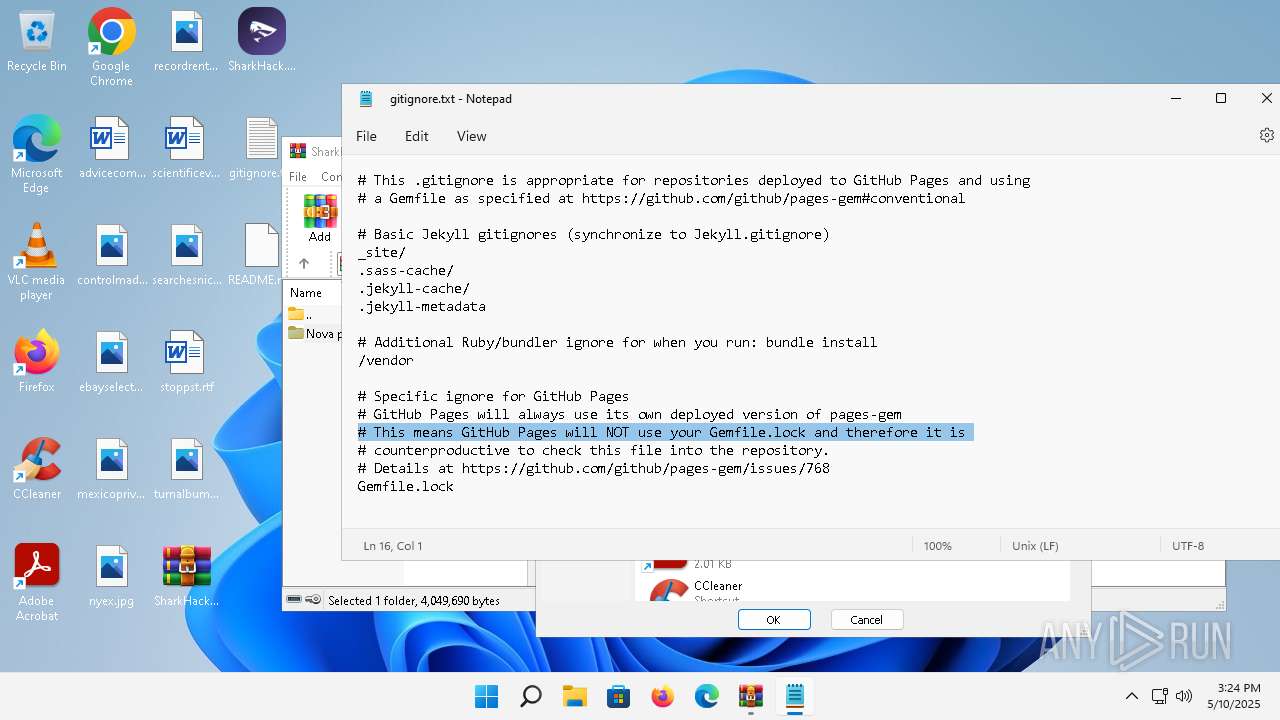
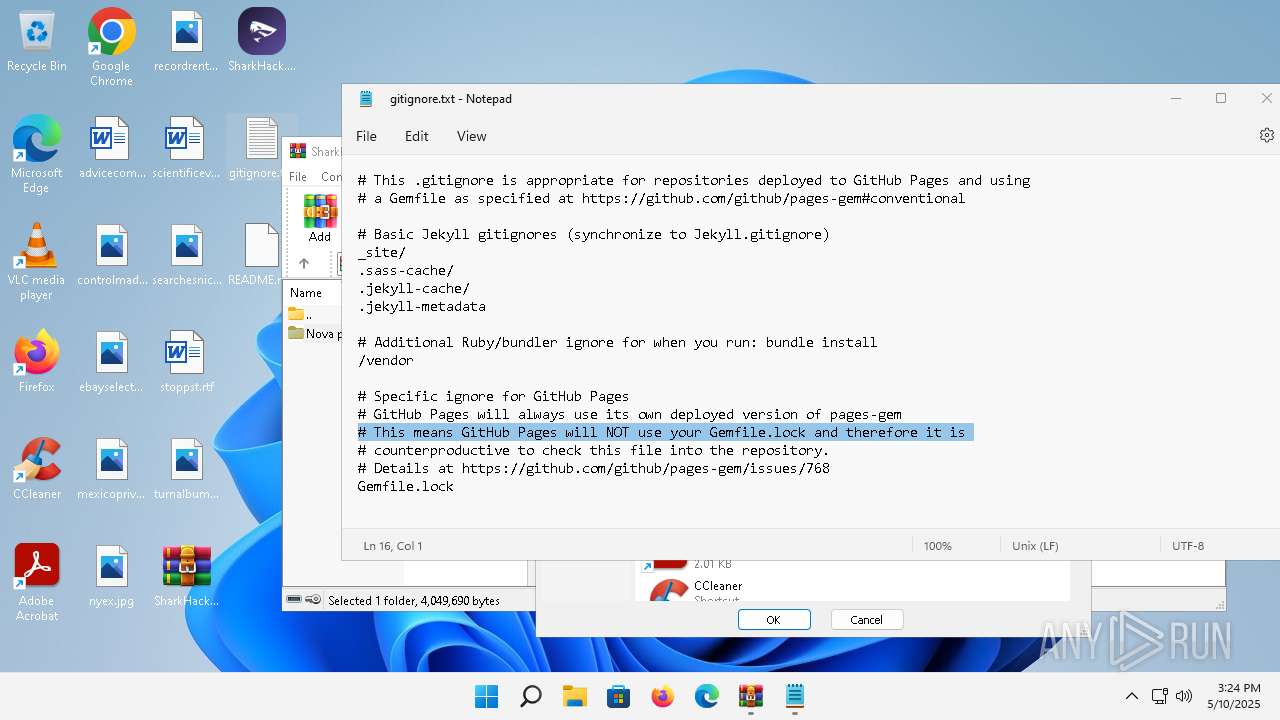
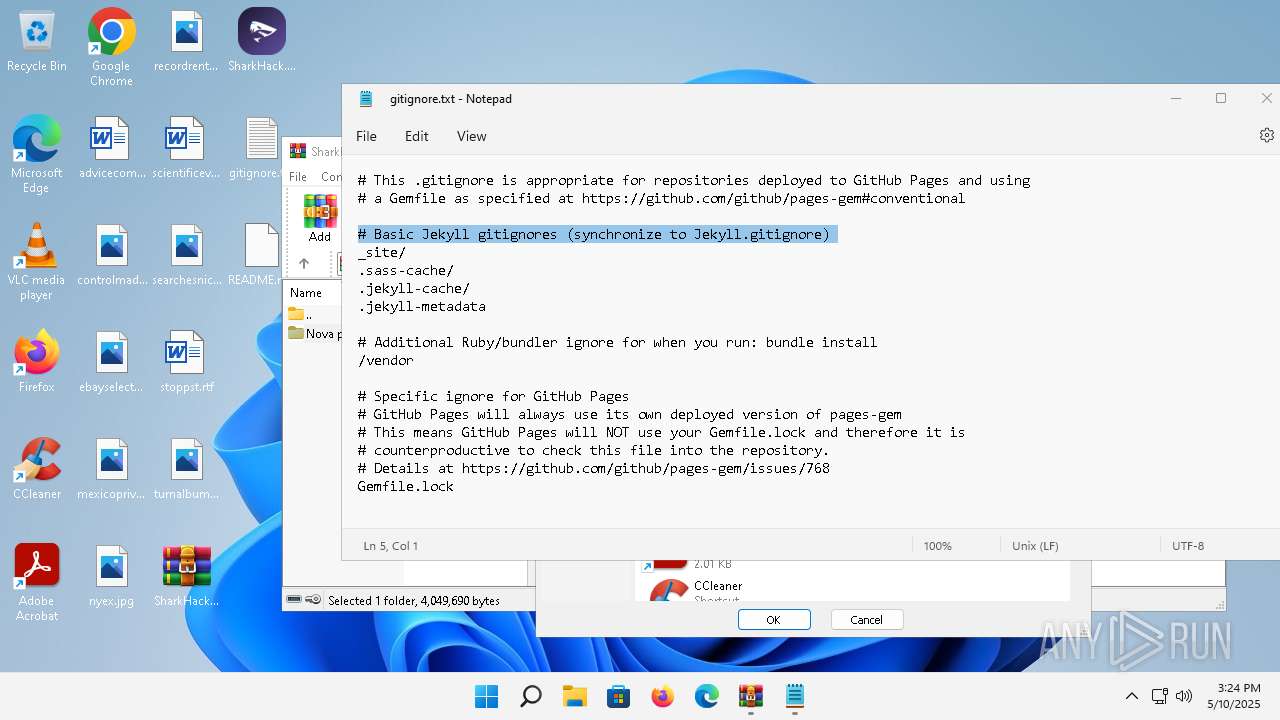
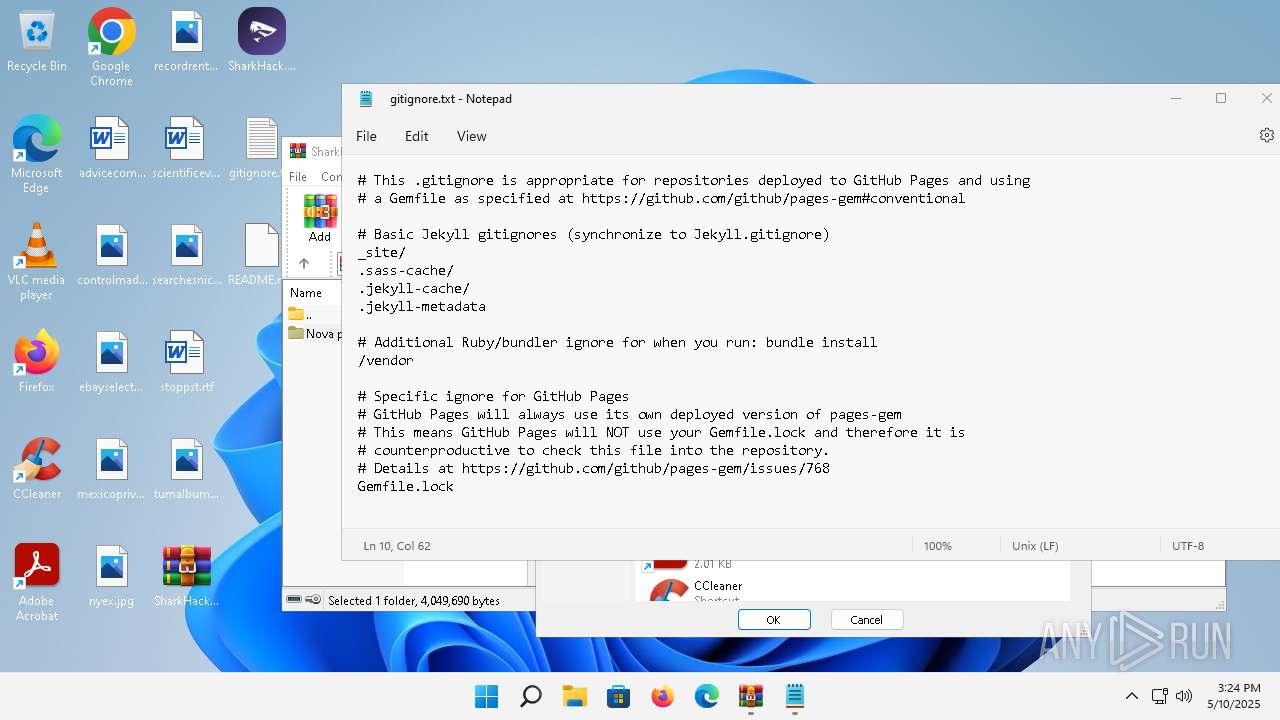
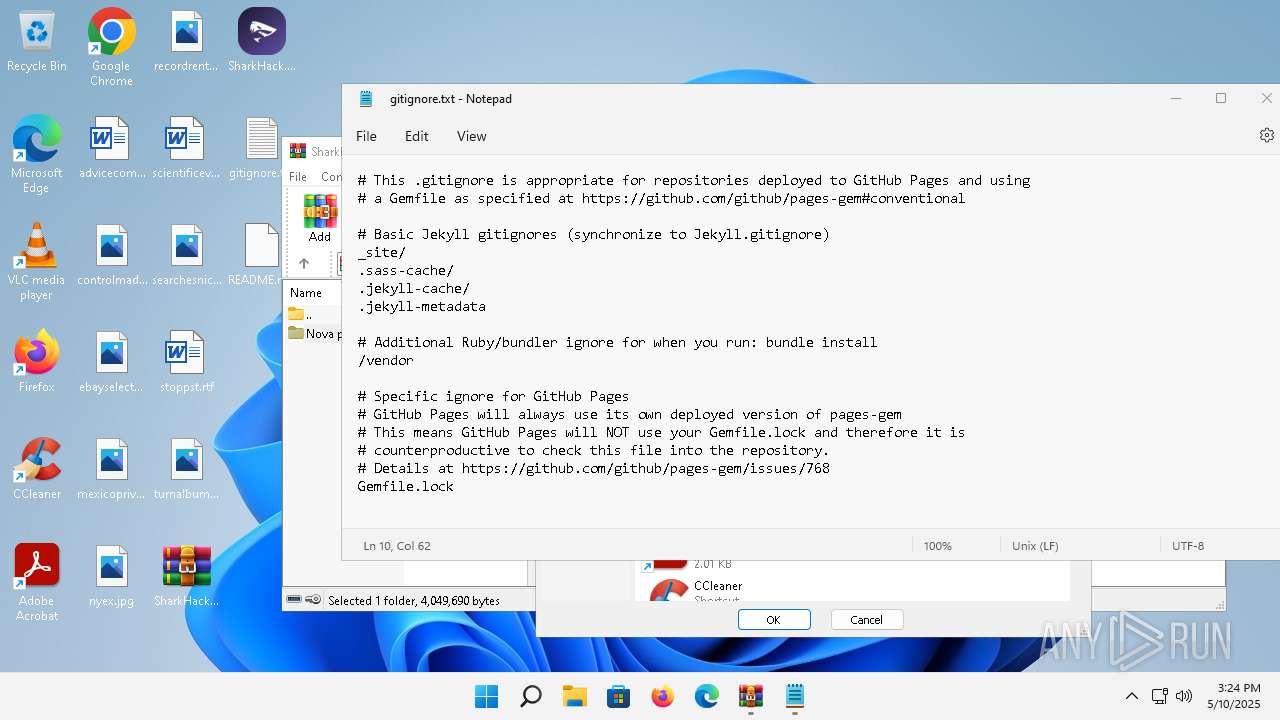
| File name: | SharkHack.zip |
| Full analysis: | https://app.any.run/tasks/8bf2907c-a0a7-45fc-8065-988b89fc29ec |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2025, 15:22:07 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | CCE31F97A8AAC6F409F3CCA5CAC0E598 |
| SHA1: | C615B8ACEB5F2B7A3C1FF73443503AAA3B753008 |
| SHA256: | D827716CA81CDFAF7BA3BBB6D558FBCC068D0DC5E1619468C57034A8327CC144 |
| SSDEEP: | 98304:3AEkXhH0cPh3qudzqclLJGoS0qYZ5bP3iT6VmE9Kpfco9T+XMGvAMhpKTmNl0:2O |
MALICIOUS
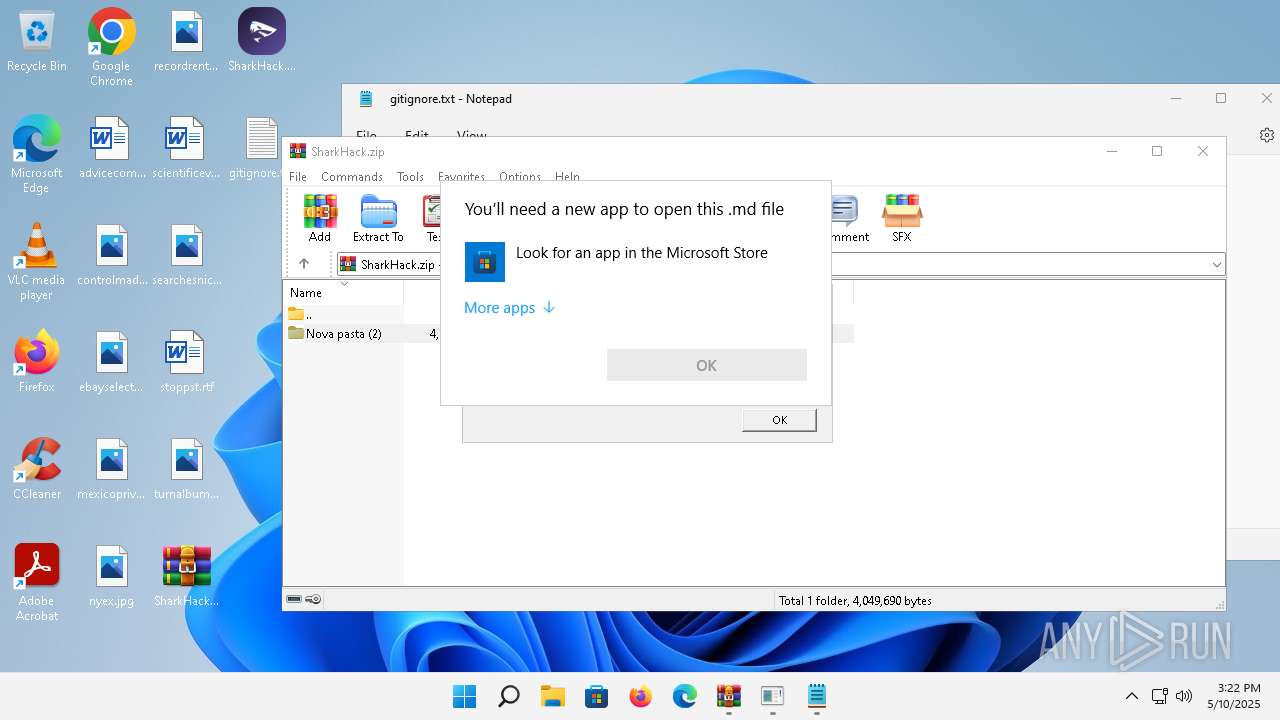
Generic archive extractor
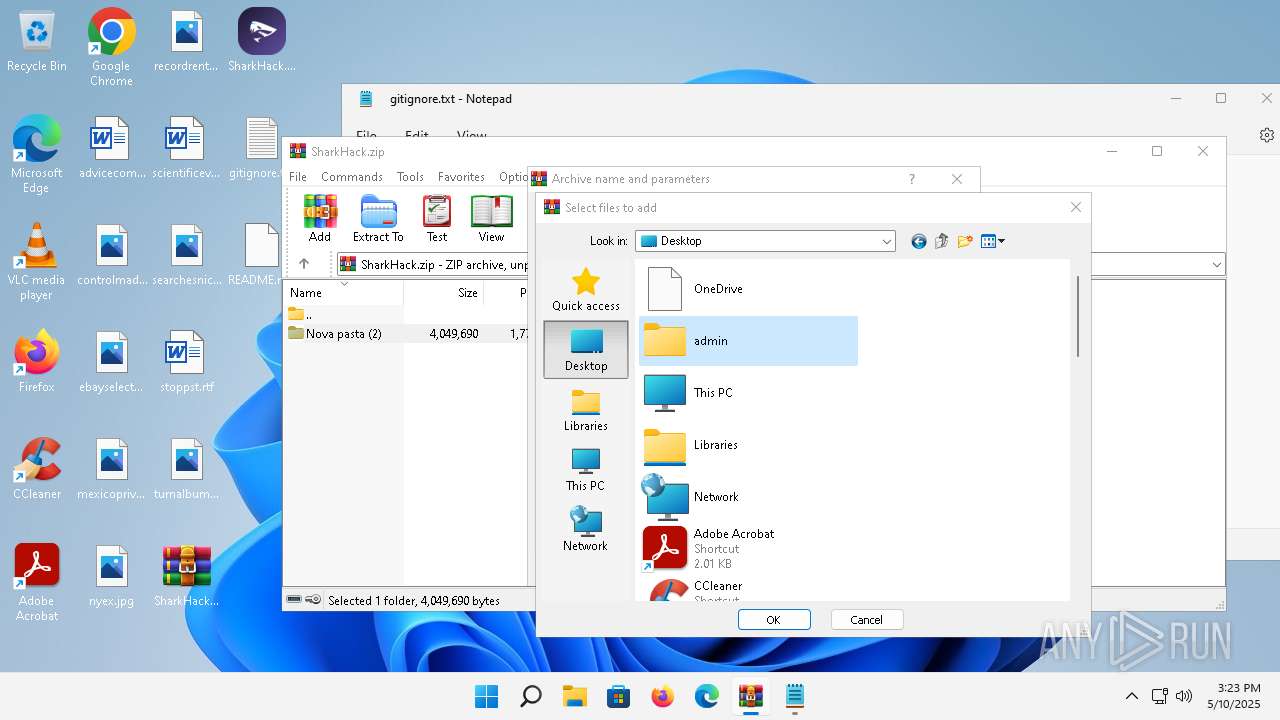
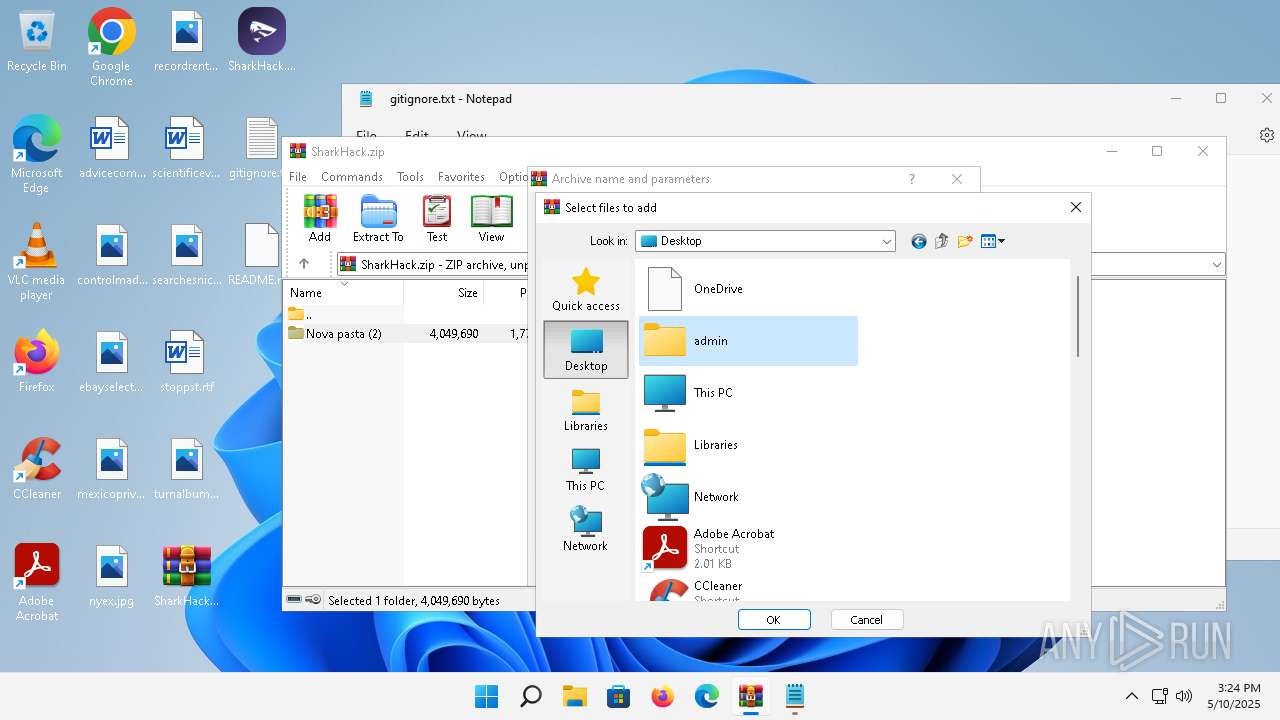
- WinRAR.exe (PID: 3920)
SUSPICIOUS
Reads the Internet Settings
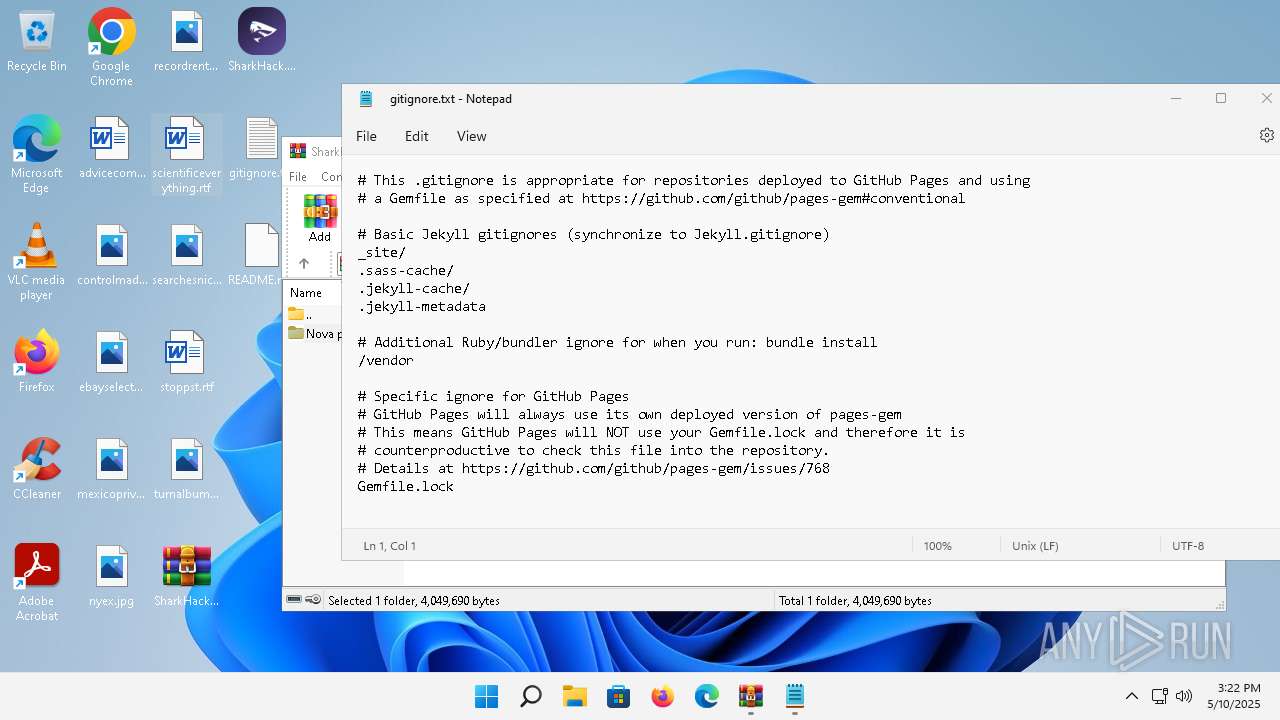
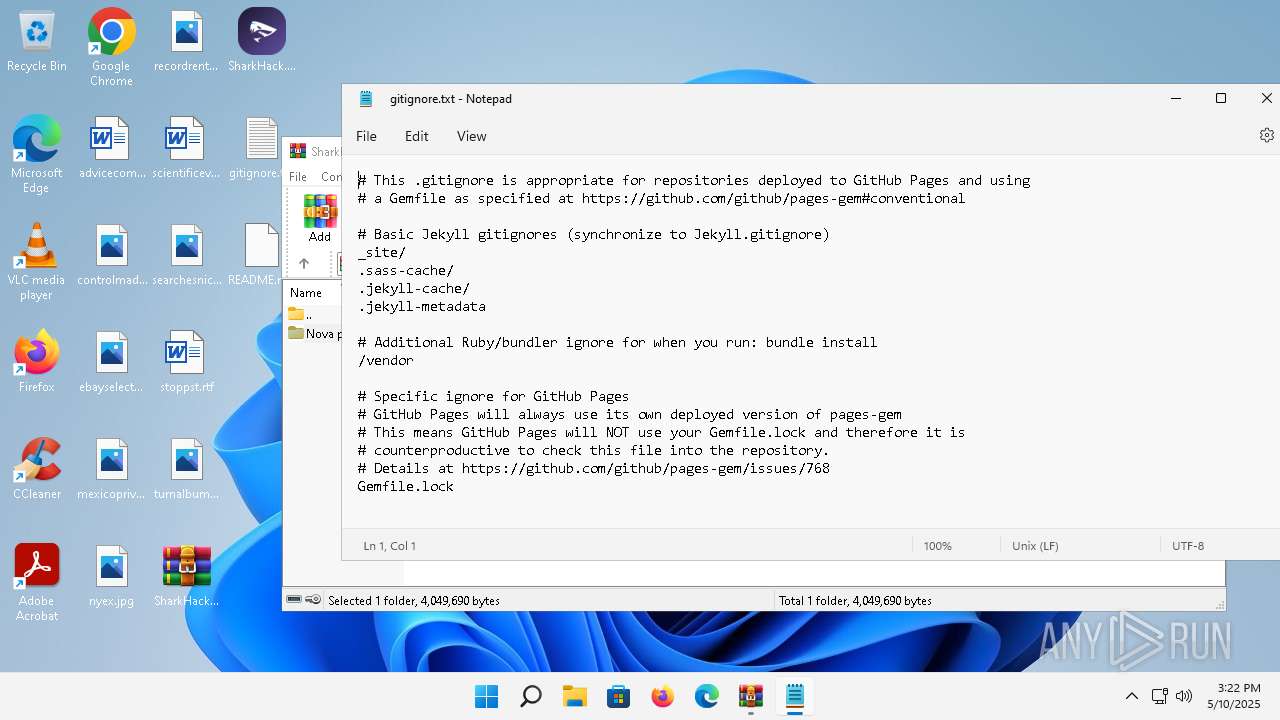
- Notepad.exe (PID: 136)
- OpenWith.exe (PID: 2088)
Reads security settings of Internet Explorer
- Notepad.exe (PID: 136)
- WinRAR.exe (PID: 3920)
INFO
Manual execution by a user
- SharkHack.exe (PID: 3296)
- Notepad.exe (PID: 136)
- OpenWith.exe (PID: 2088)
Reads the computer name
- Notepad.exe (PID: 136)
Checks supported languages
- Notepad.exe (PID: 136)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 2088)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 2088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:10 15:12:40 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Nova pasta (2)/ |
Total processes
104
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
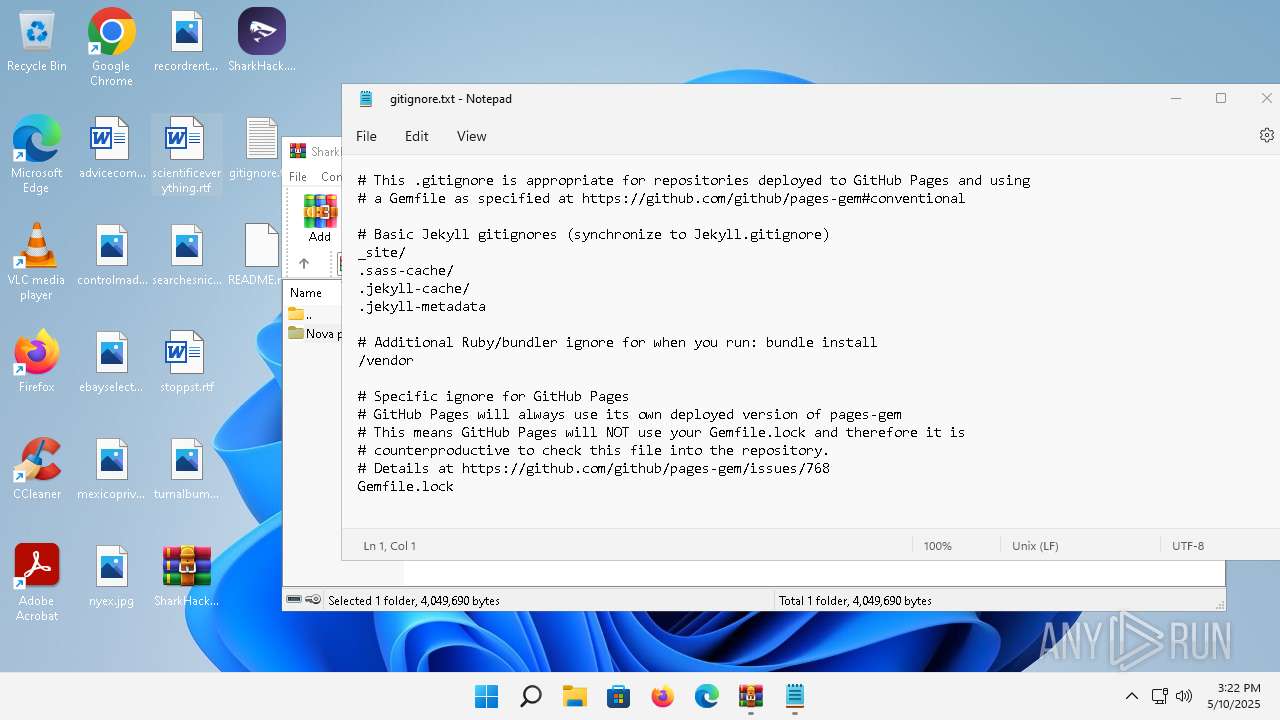
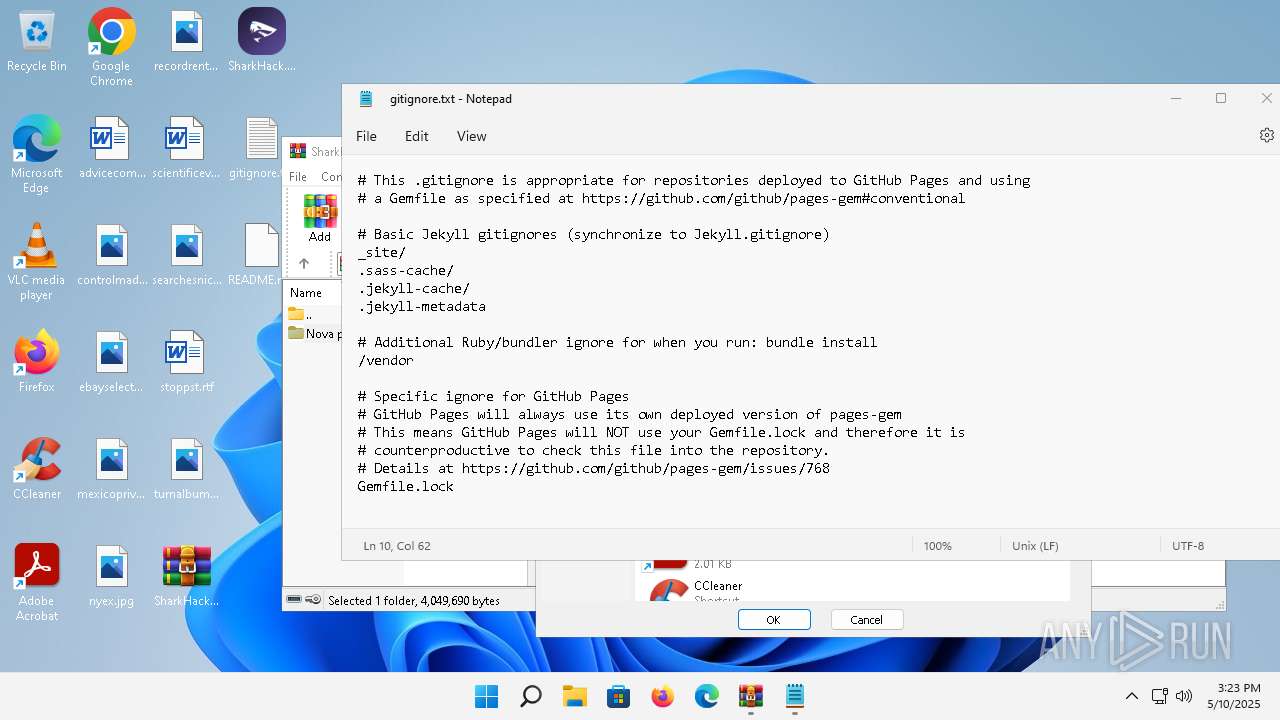
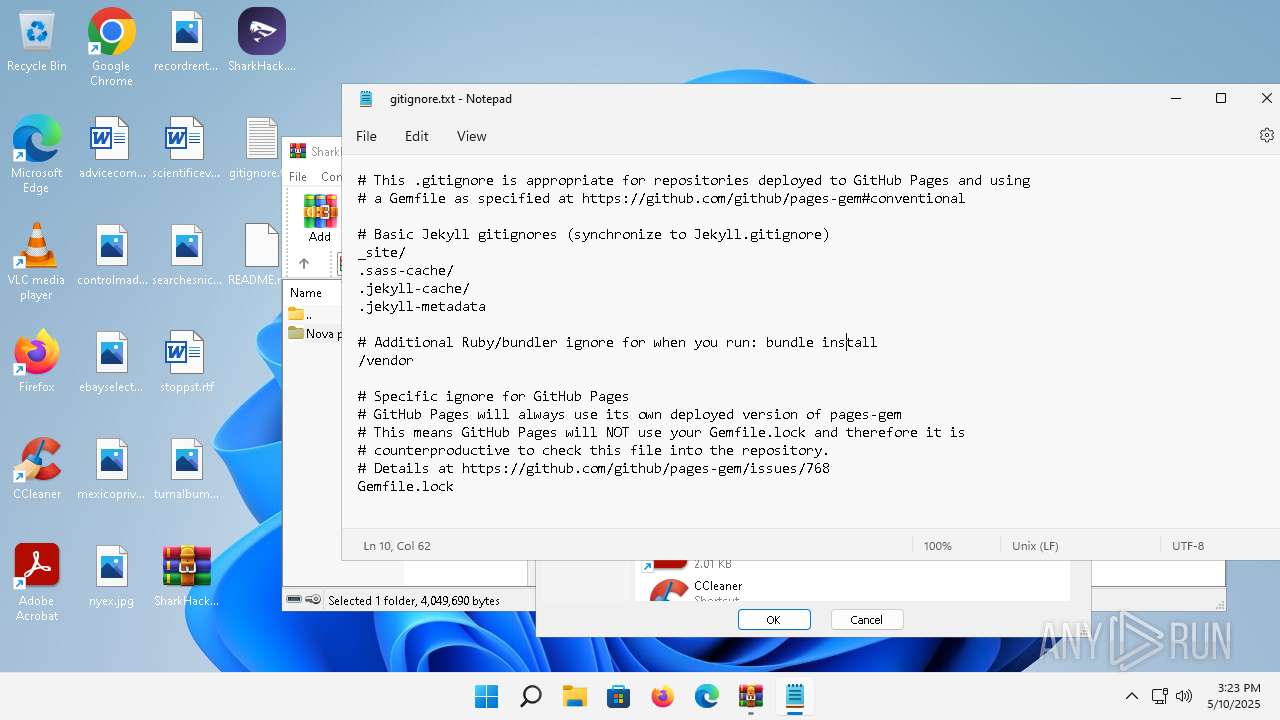
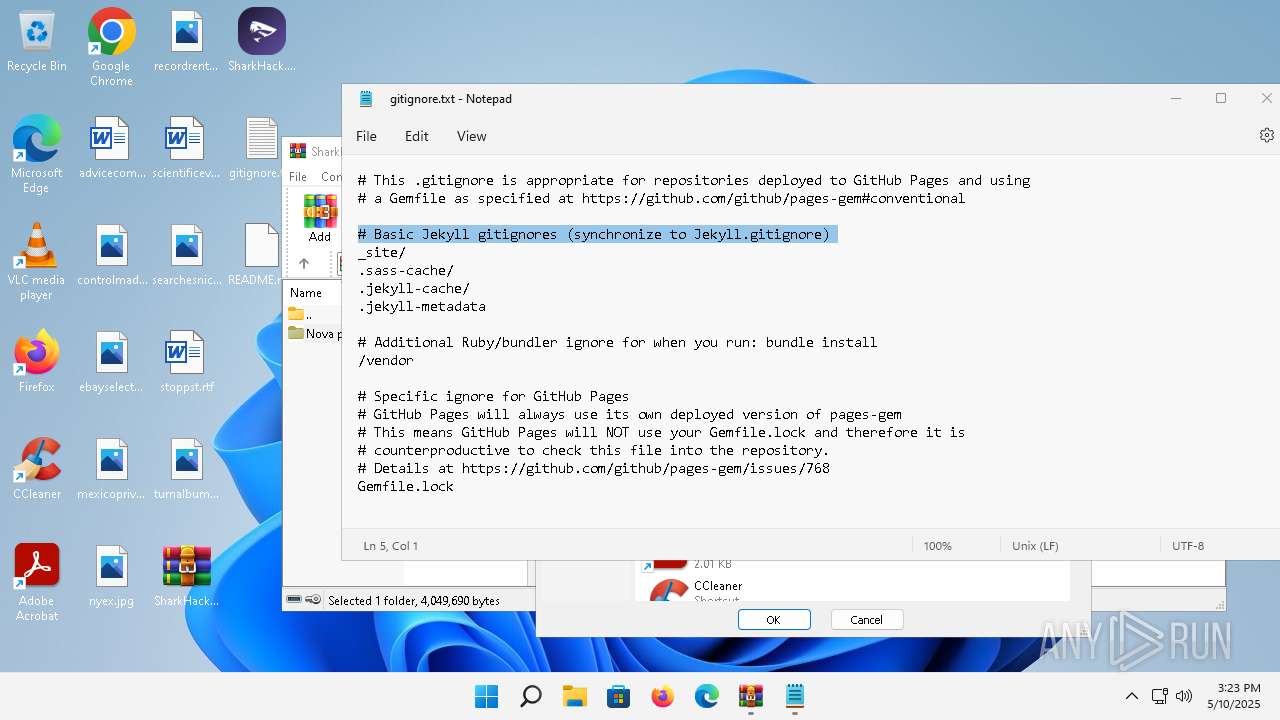
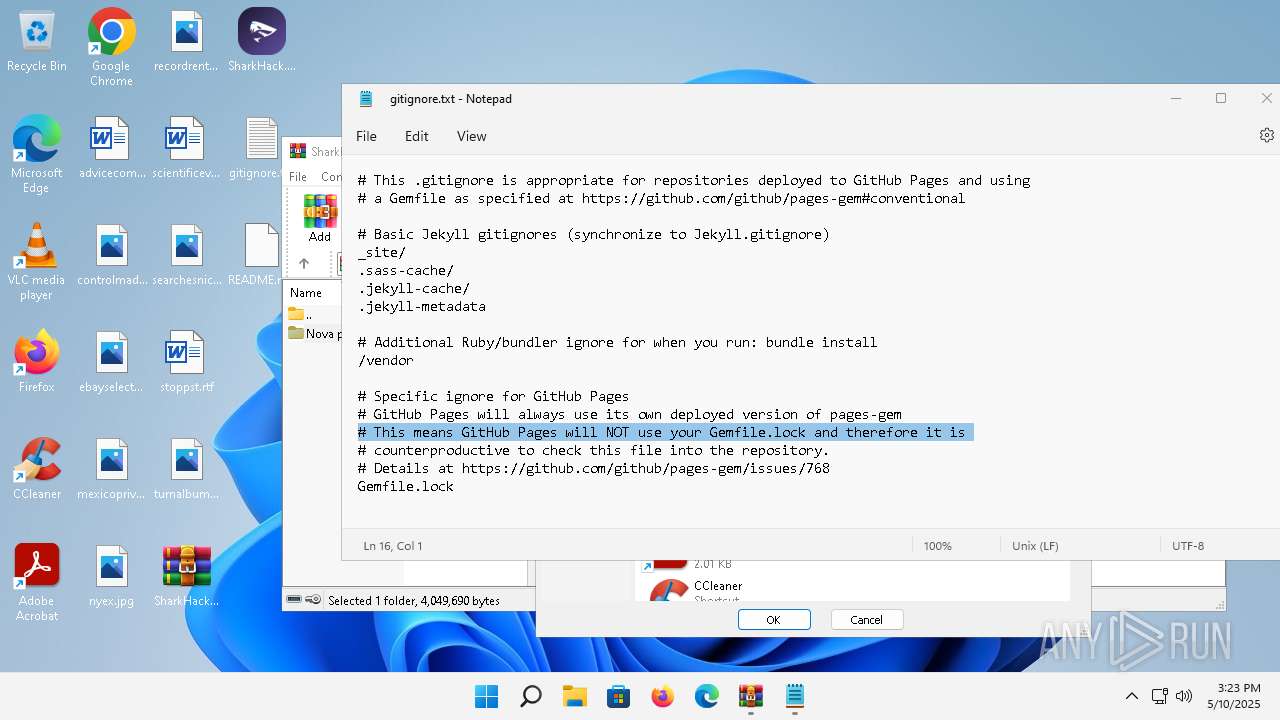
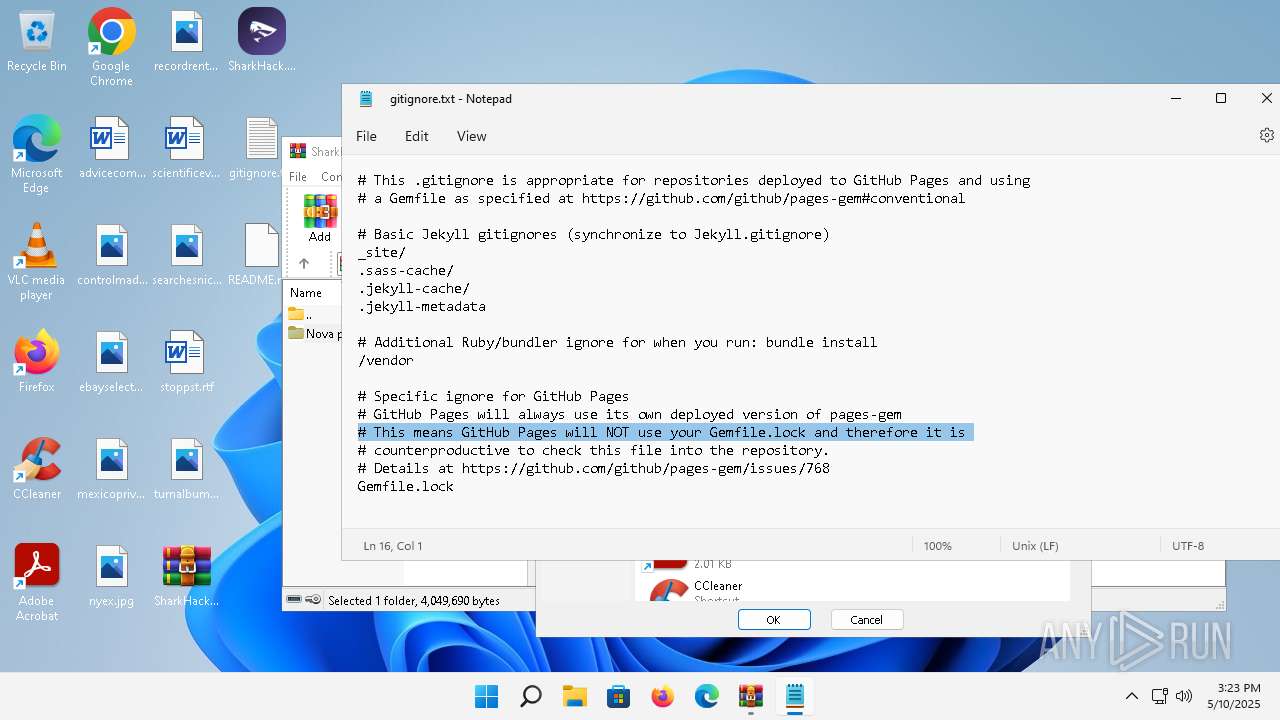
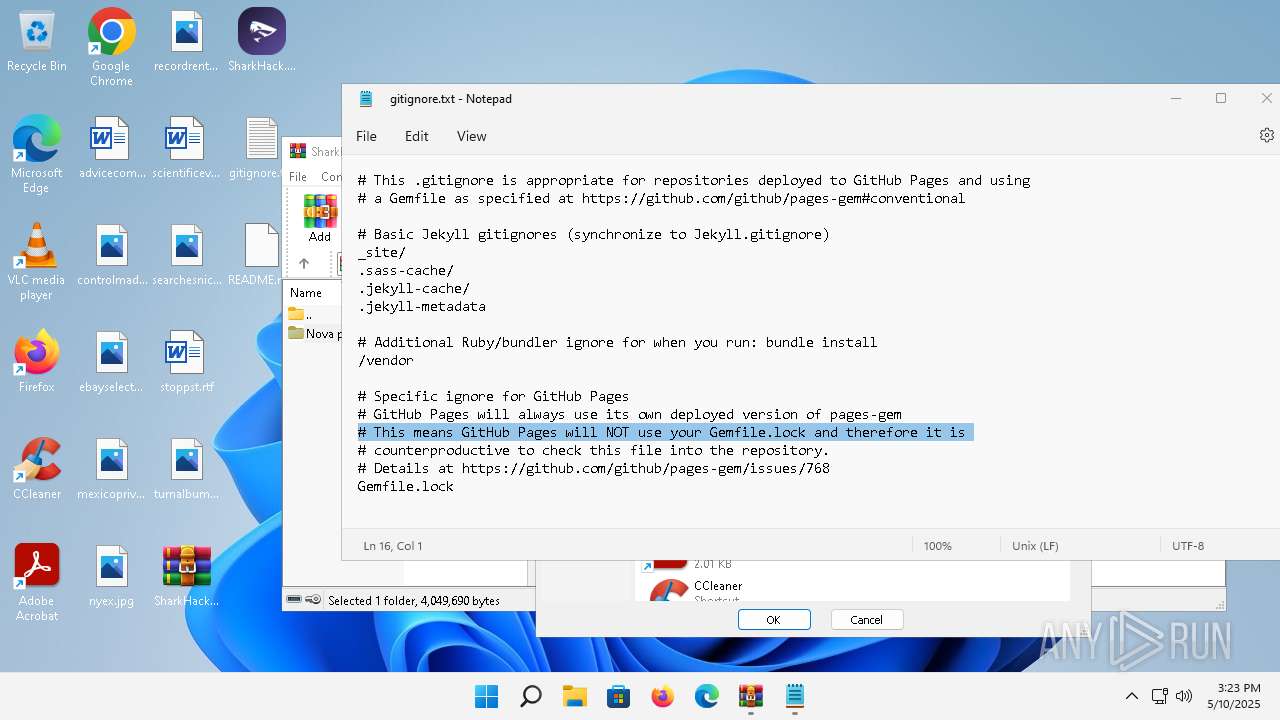
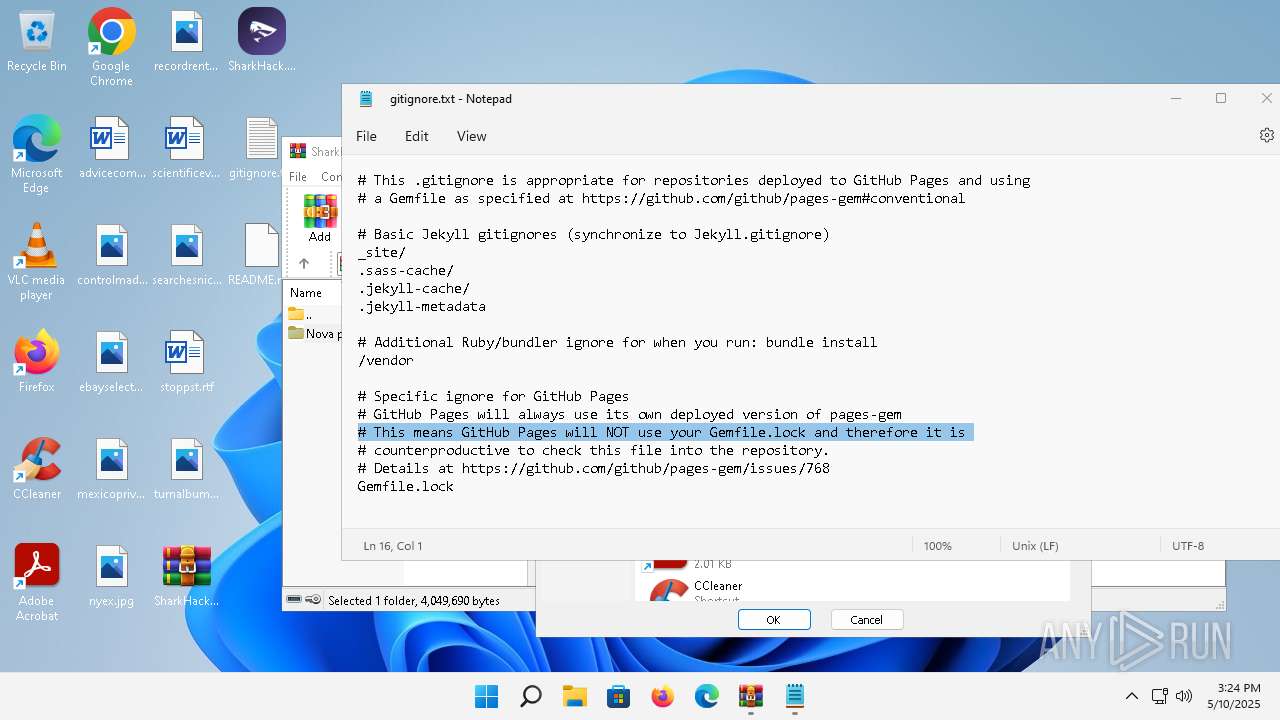
| 136 | "C:\Windows\system32\notepad.exe" C:\Users\admin\Desktop\gitignore.txt | C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2088 | "C:\Windows\System32\OpenWith.exe" C:\Users\admin\Desktop\README.md | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
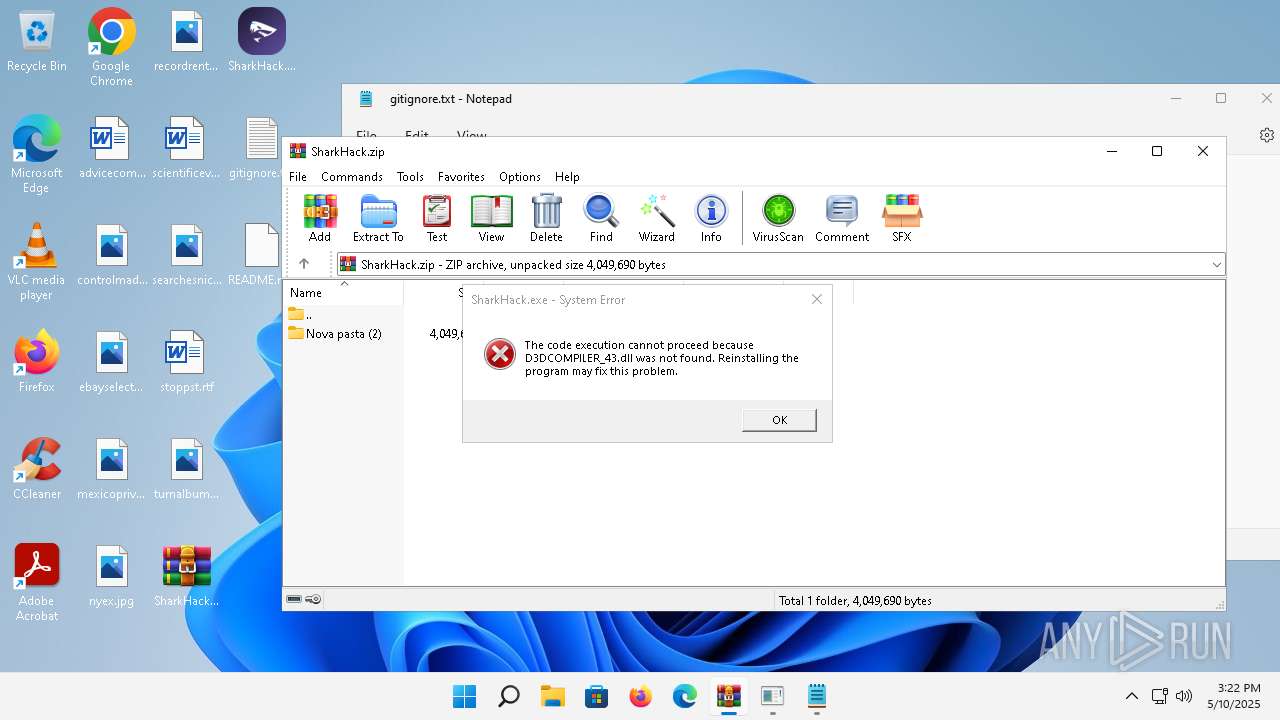
| 3296 | "C:\Users\admin\Desktop\SharkHack.exe" | C:\Users\admin\Desktop\SharkHack.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
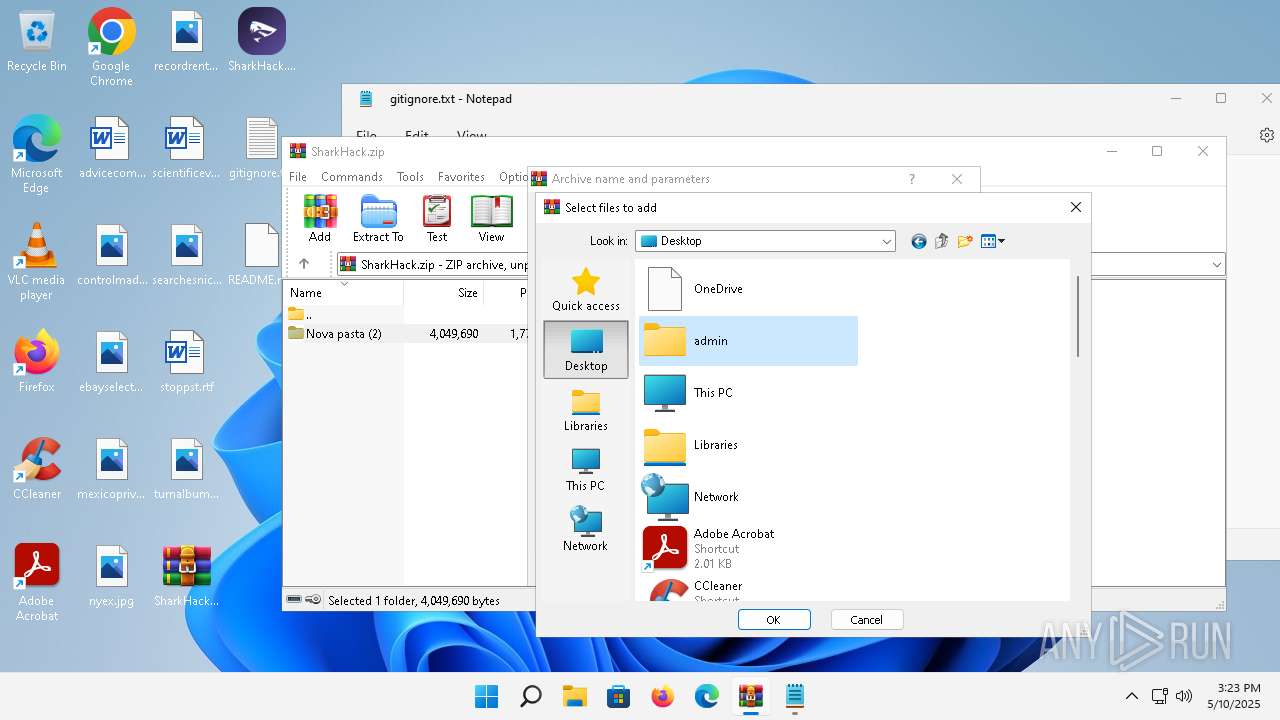
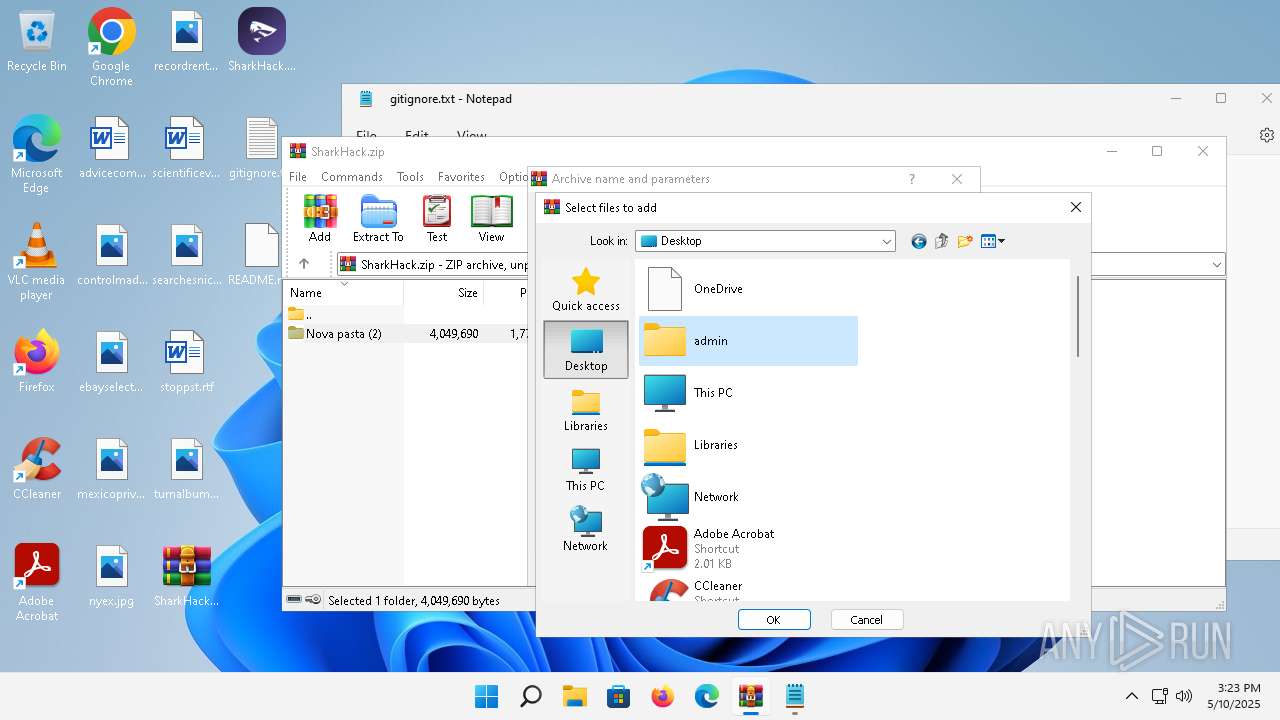
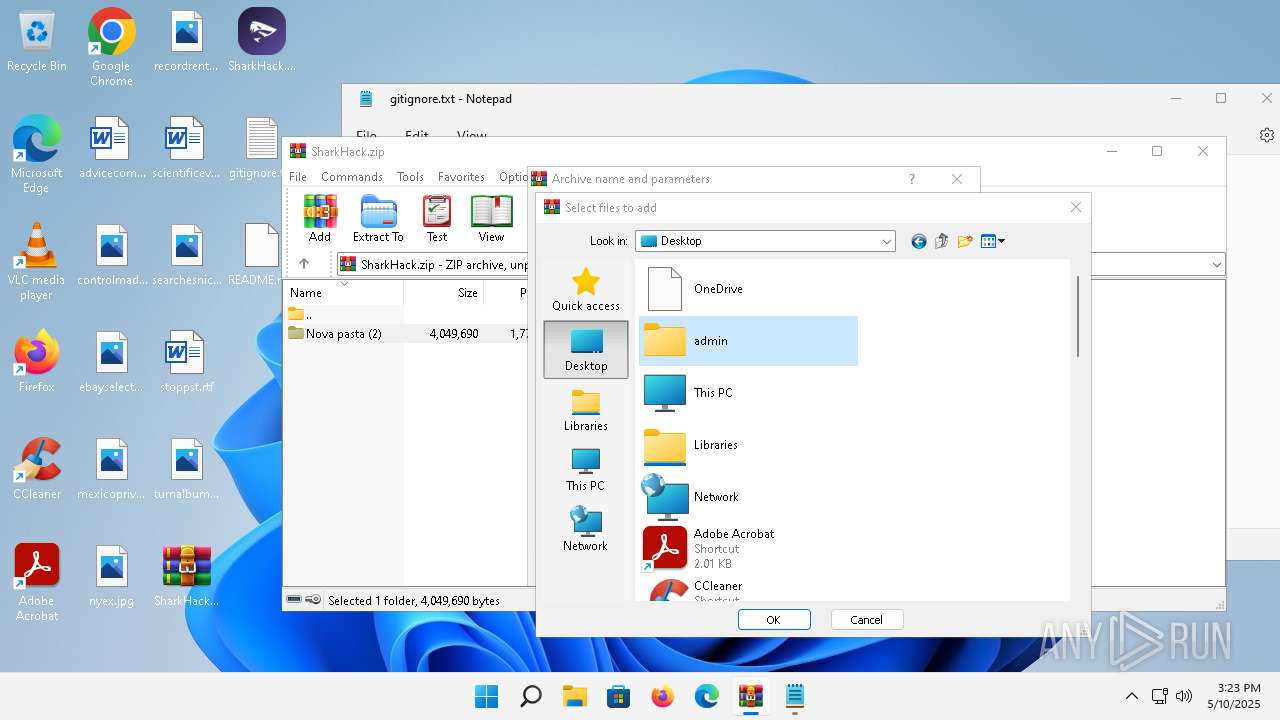
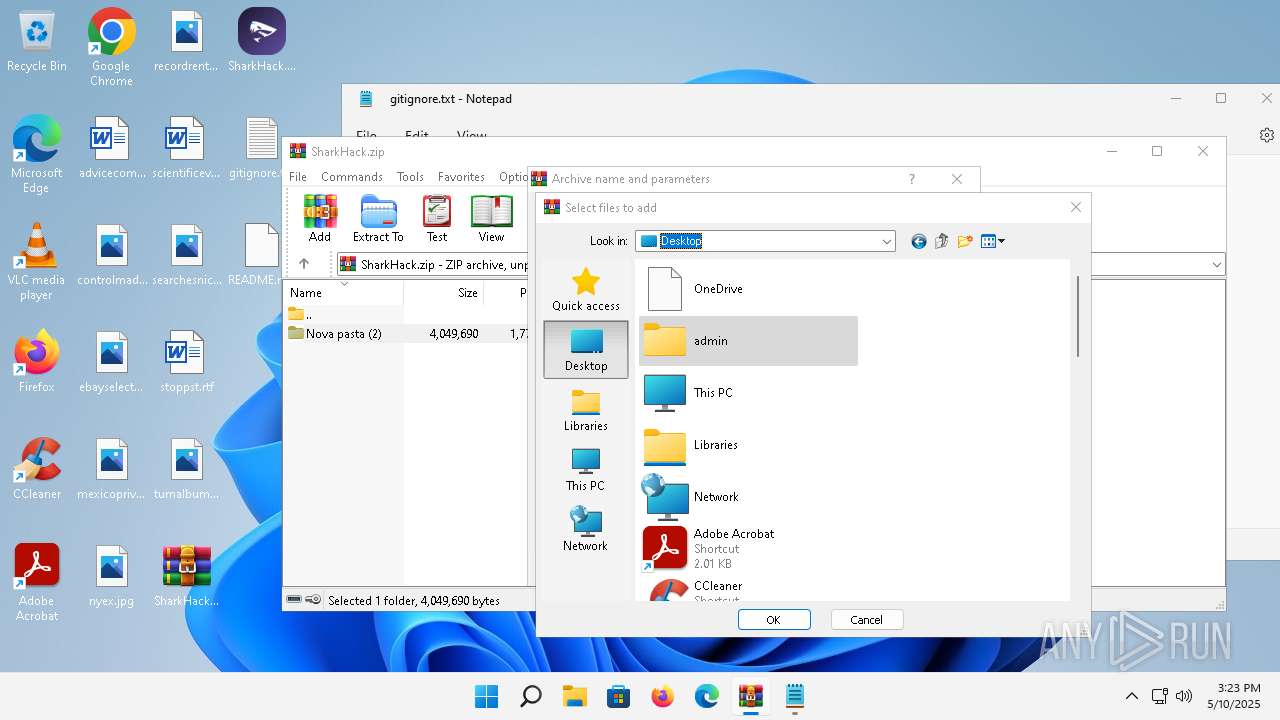
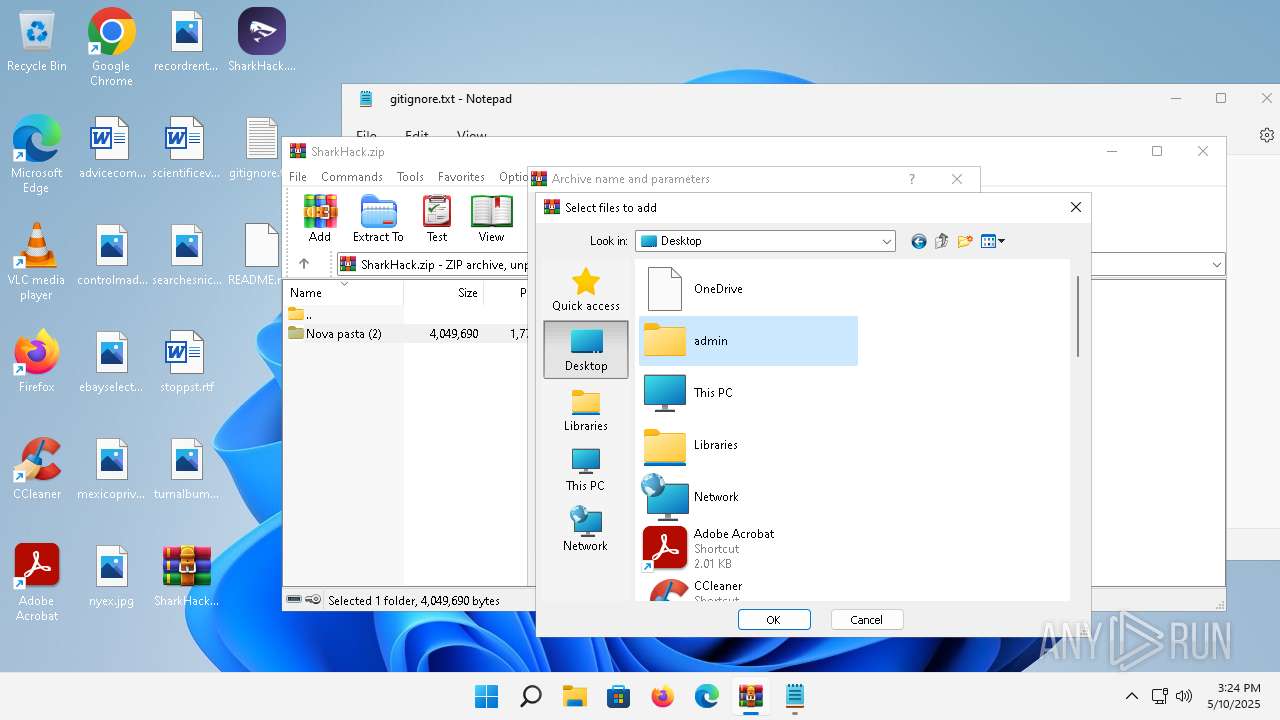
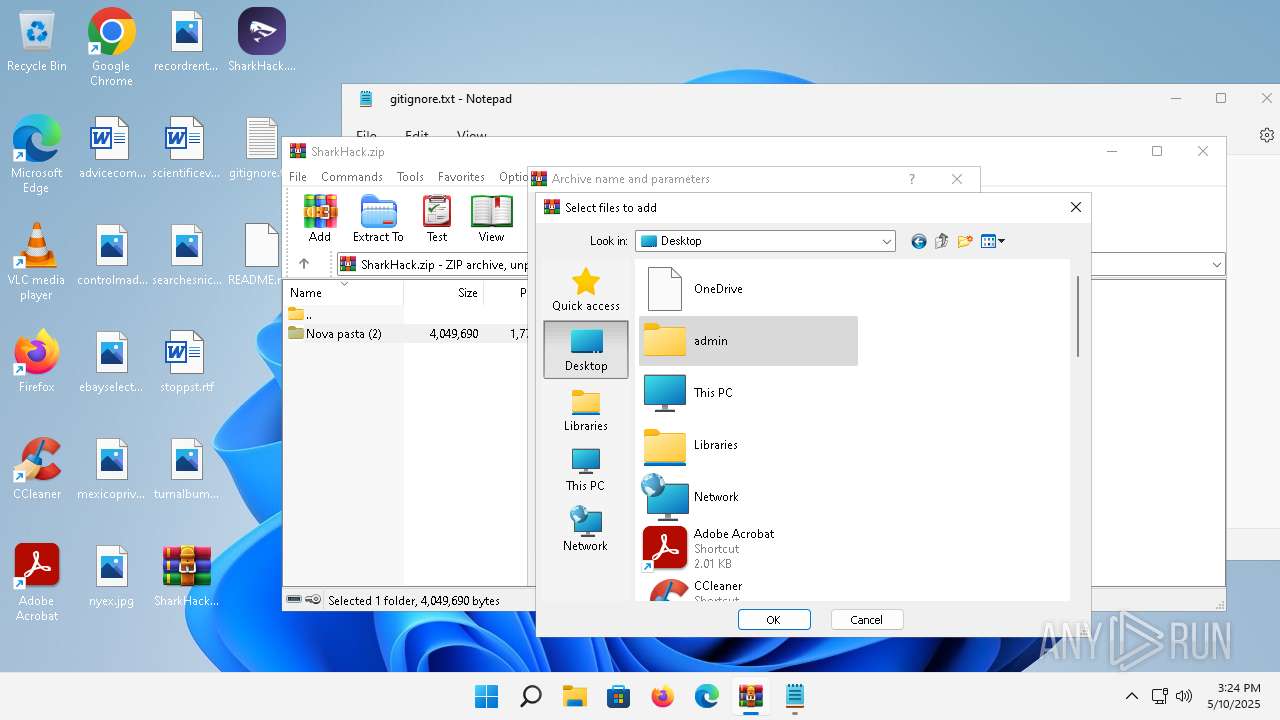
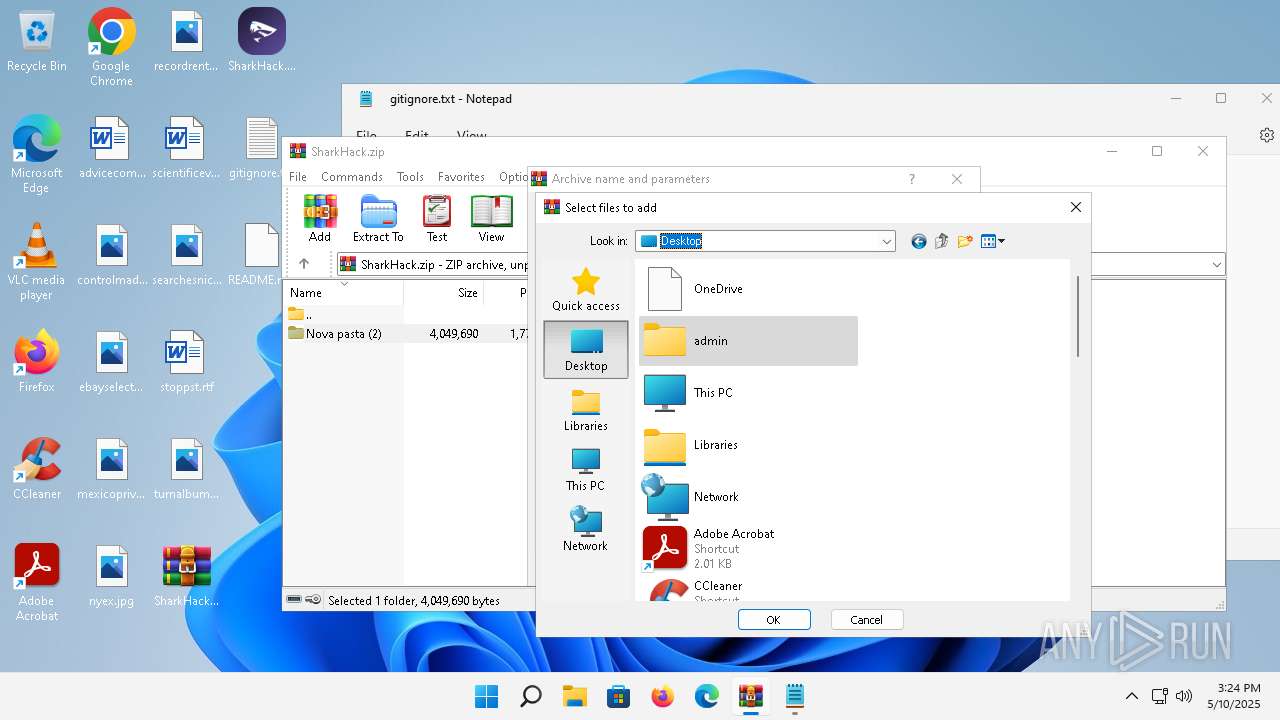
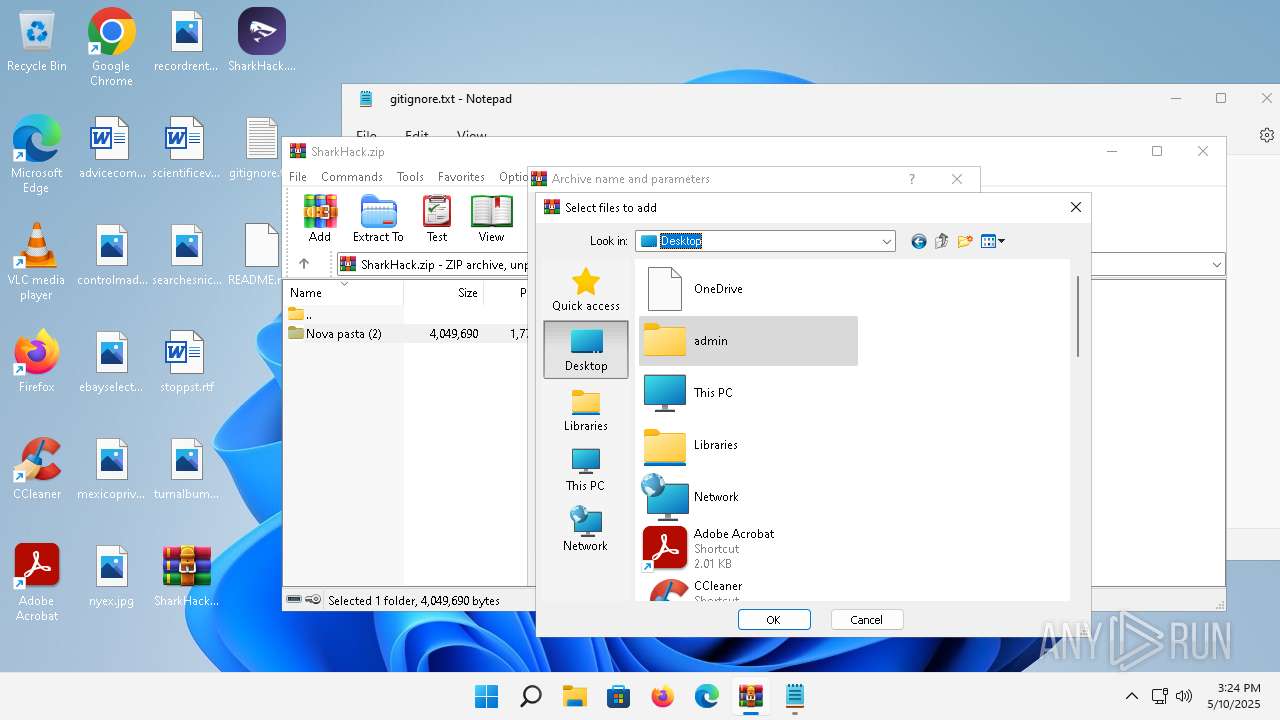
| 3920 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\SharkHack.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
9 563
Read events
8 688
Write events
799
Delete events
76
Modification events
| (PID) Process: | (3920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SharkHack.zip | |||
| (PID) Process: | (3920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
19
DNS requests
9
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1352 | svchost.exe | GET | 200 | 184.24.77.4:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
2860 | smartscreen.exe | GET | 200 | 88.221.110.91:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c0c80cf0763e7b22 | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 23.197.142.186:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | unknown |
2768 | svchost.exe | GET | 200 | 88.221.110.106:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?4c1c53e3976db8c9 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 88.221.110.106:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?f73e7201b5c209eb | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 88.221.110.106:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?6735a5a4e0c320f8 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 88.221.110.106:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?673bef073e0b4dd4 | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.3:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
— | — | POST | 200 | 4.209.164.61:443 | https://checkappexec.microsoft.com/windows/shell/actions | unknown | binary | 182 b | whitelisted |
— | — | POST | 200 | 40.126.31.1:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1352 | svchost.exe | 184.24.77.4:80 | — | Akamai International B.V. | DE | unknown |
2860 | smartscreen.exe | 98.64.238.3:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2860 | smartscreen.exe | 88.221.110.91:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
5336 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3640 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2596 | svchost.exe | 23.60.203.209:443 | fs.microsoft.com | AKAMAI-AS | DE | whitelisted |
2776 | svchost.exe | 20.189.173.12:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2988 | OfficeClickToRun.exe | 52.182.143.208:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
1352 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |