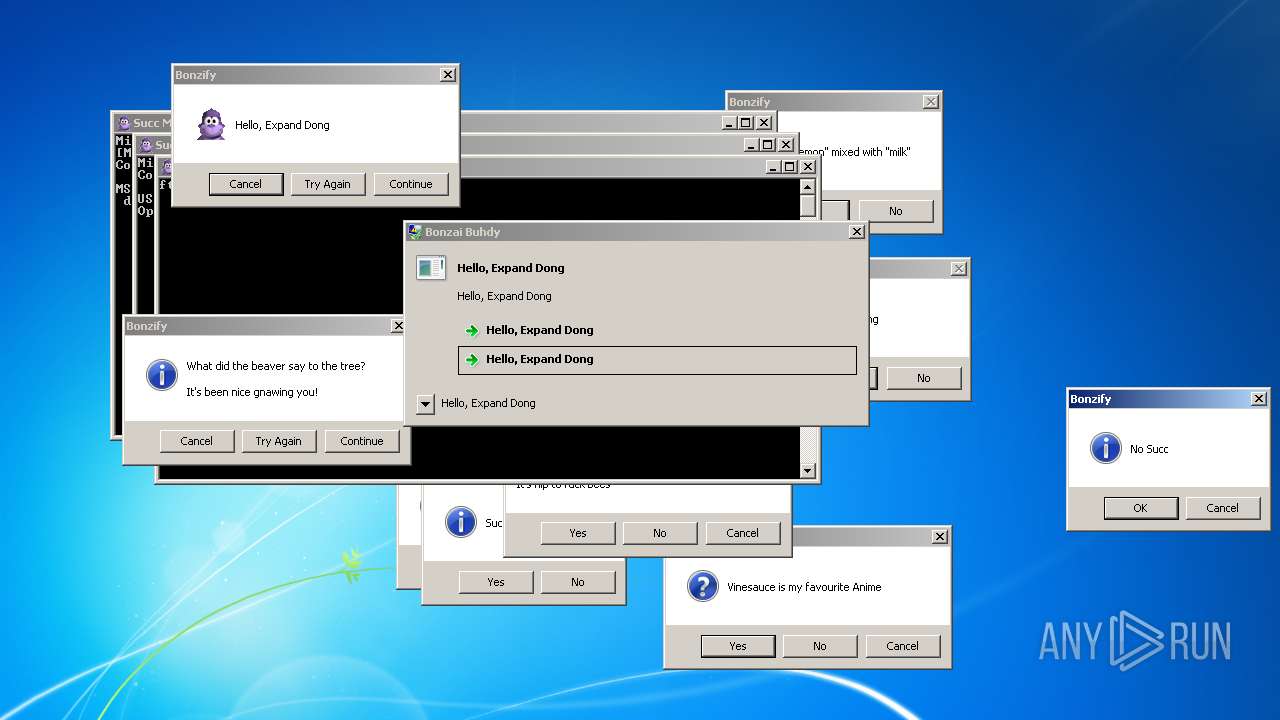
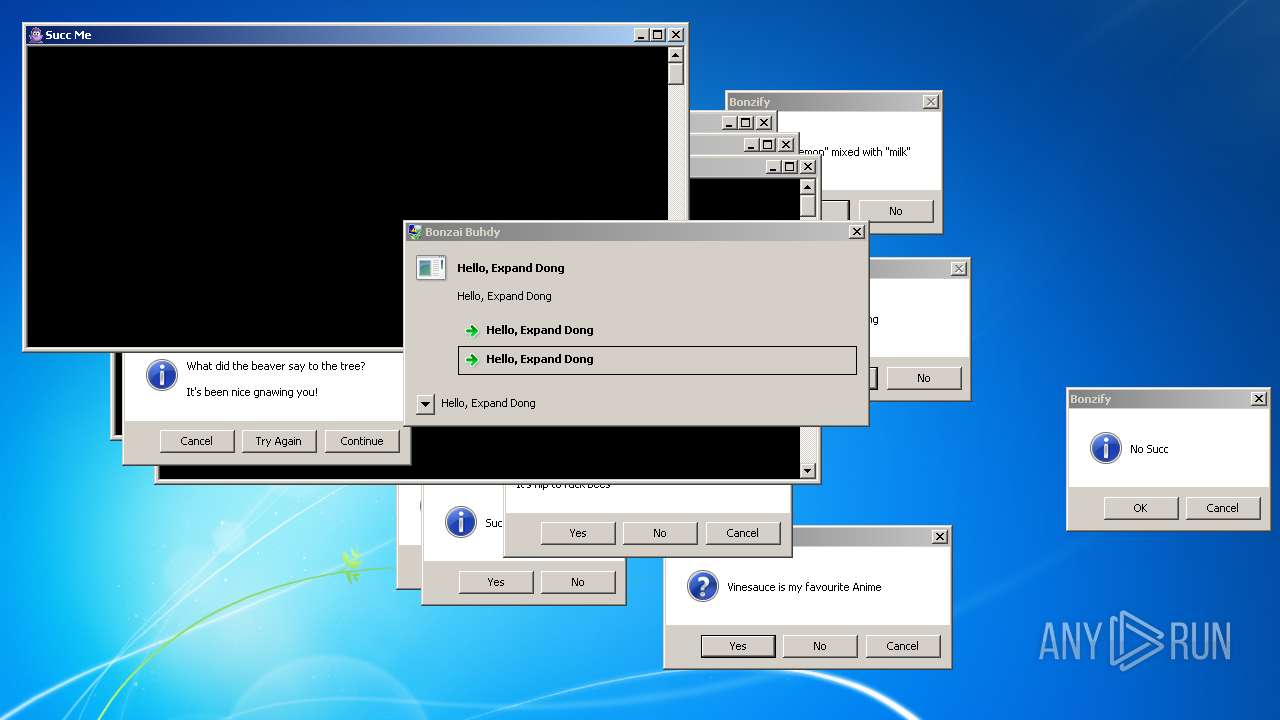
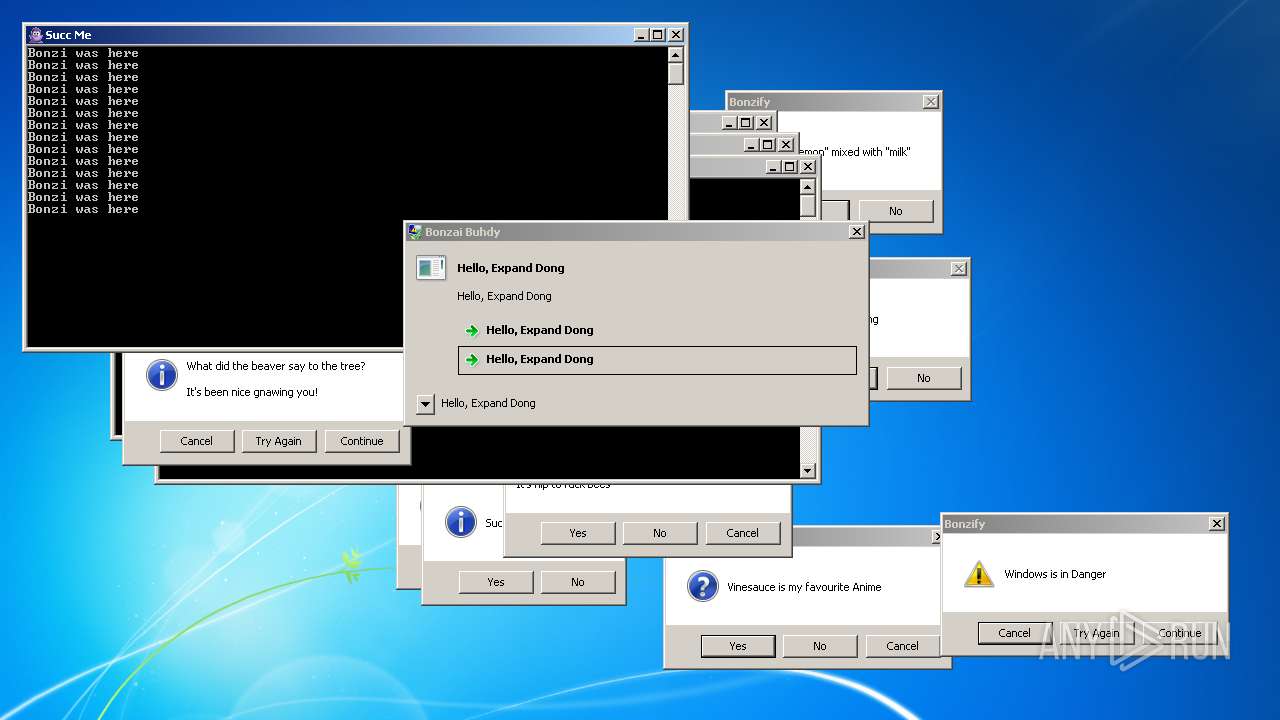
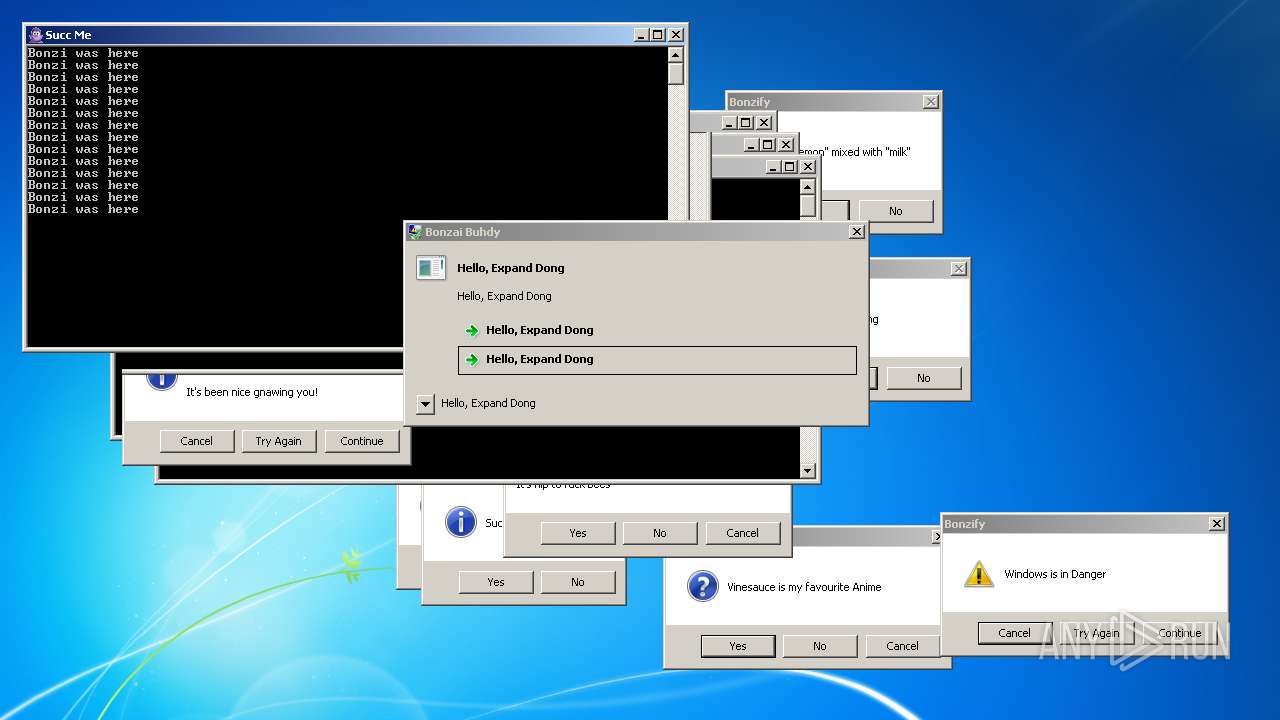
| File name: | Bonzify.exe |
| Full analysis: | https://app.any.run/tasks/e9933081-936a-4d6c-aa67-62a55f72ecee |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2024, 20:45:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9C352D2CE0C0BDC40C72F52CE3480577 |
| SHA1: | BD4C956186F33C92EB4469F7E5675510D0790E99 |
| SHA256: | D7E6580054525D3F21F86EDFC9F30B7A75FFA829A1EB67EE3CAB33F0040DBA4E |
| SSDEEP: | 196608:/dAMaWetTeAkLIdx751qFTkub//73lc6u7b5VJ2Yx5xIdk3o:naWedh+Idx75QYub//73lc6u7bLMYxDo |
MALICIOUS
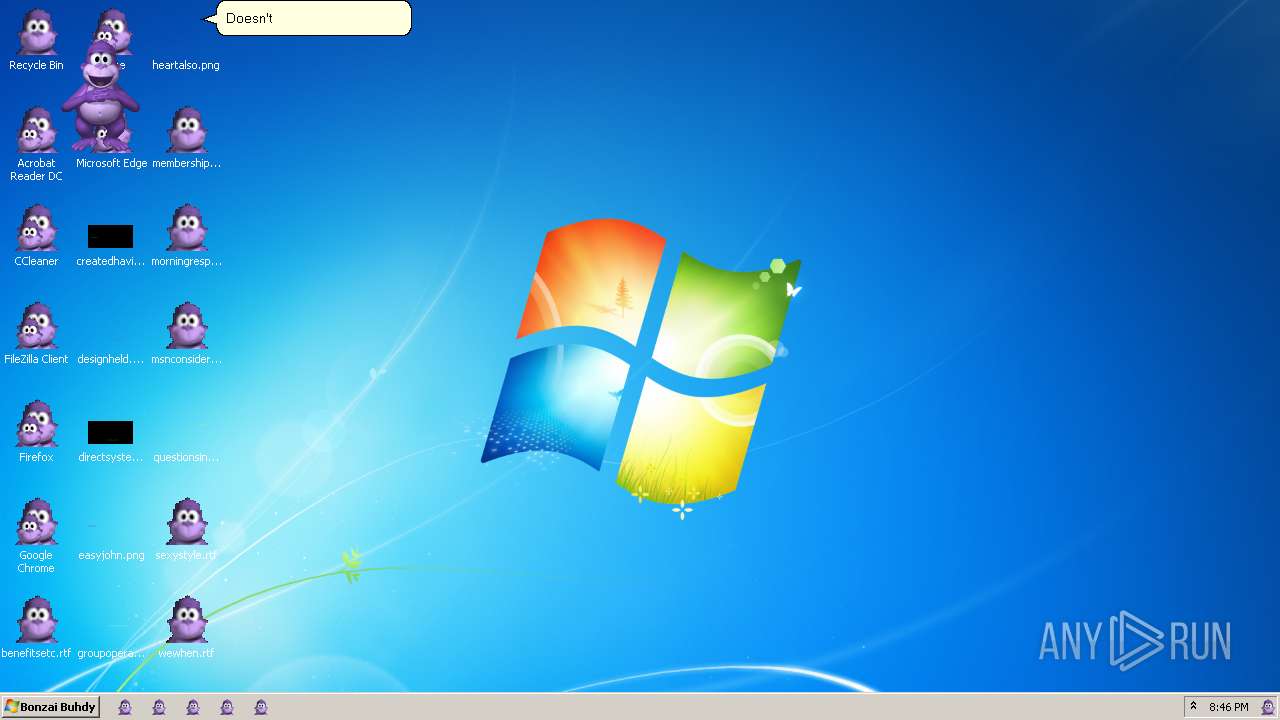
Drops the executable file immediately after the start
- Bonzify.exe (PID: 2064)
- INSTALLER.exe (PID: 1236)
- INSTALLER.exe (PID: 1536)
Registers / Runs the DLL via REGSVR32.EXE
- INSTALLER.exe (PID: 1236)
- INSTALLER.exe (PID: 1536)
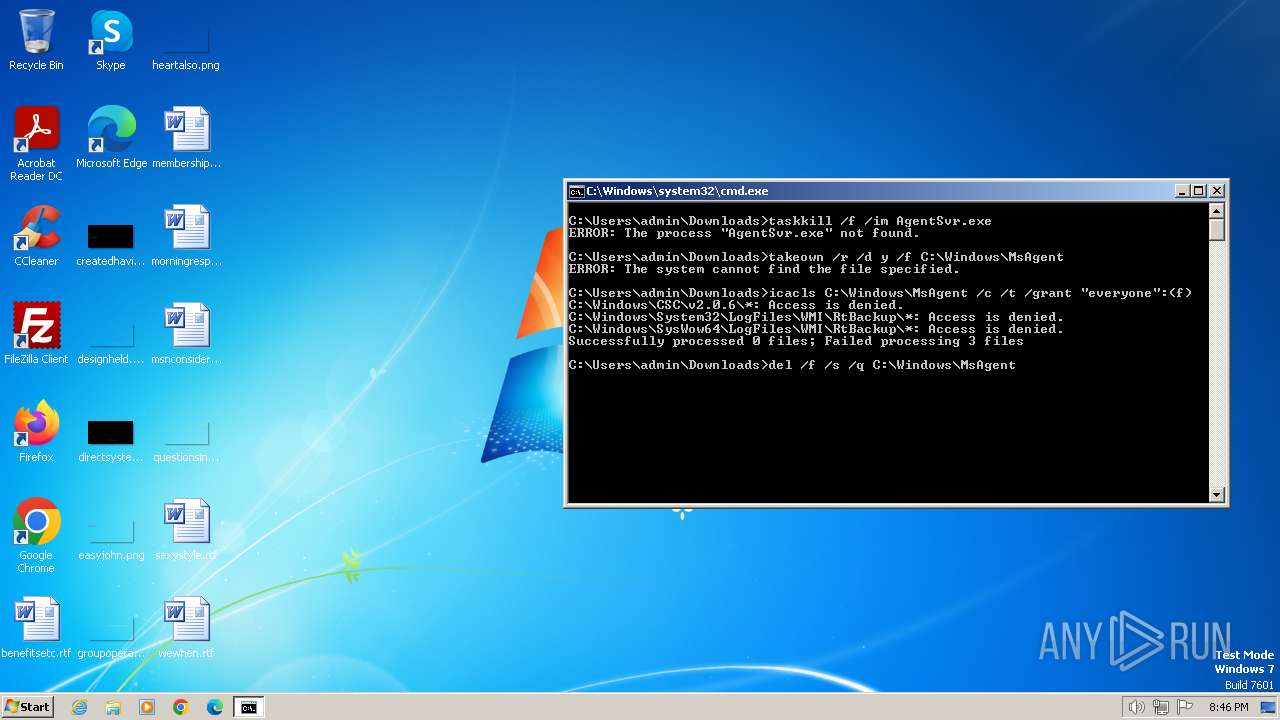
Creates a writable file in the system directory
- INSTALLER.exe (PID: 1536)
Changes the AppInit_DLLs value (autorun option)
- Bonzify.exe (PID: 2064)
Changes the autorun value in the registry
- comp.exe (PID: 2076)
- dllhost.exe (PID: 1196)
- printfilterpipelinesvc.exe (PID: 3396)
- dpapimig.exe (PID: 3752)
- SETUP.EXE (PID: 3000)
- ehvid.exe (PID: 2044)
- wuauclt.exe (PID: 5248)
- ftp.exe (PID: 5692)
- rdpclip.exe (PID: 6132)
- explorer.exe (PID: 2692)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Bonzify.exe (PID: 2064)
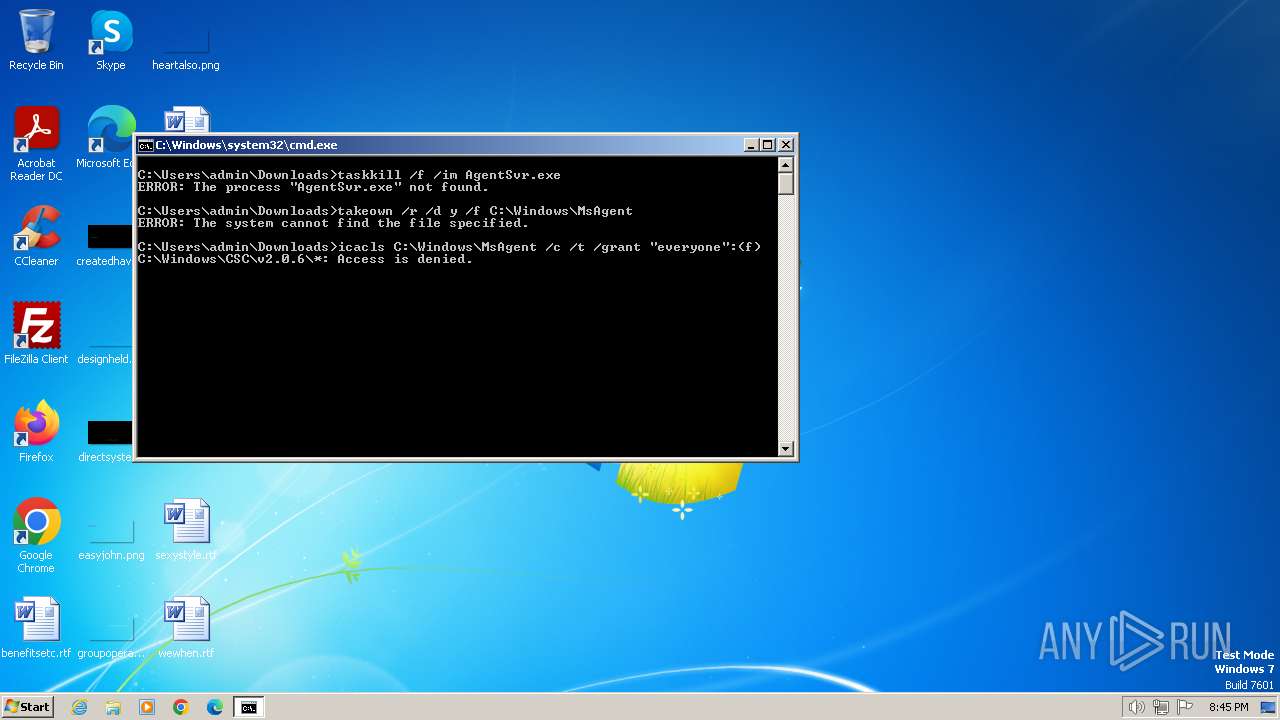
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2420)
Executing commands from a ".bat" file
- Bonzify.exe (PID: 2064)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2420)
Executable content was dropped or overwritten
- Bonzify.exe (PID: 2064)
- INSTALLER.exe (PID: 1236)
- INSTALLER.exe (PID: 1536)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 2420)
Process drops legitimate windows executable
- Bonzify.exe (PID: 2064)
- INSTALLER.exe (PID: 1236)
- INSTALLER.exe (PID: 1536)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 956)
- dllhost.exe (PID: 120)
- dllhost.exe (PID: 1196)
- label.exe (PID: 1264)
- rdpclip.exe (PID: 6132)
- conhost.exe (PID: 5460)
- SETUP.EXE (PID: 3000)
- explorer.exe (PID: 2692)
Changes internet zones settings
- comp.exe (PID: 2076)
- dllhost.exe (PID: 120)
- printfilterpipelinesvc.exe (PID: 3396)
- dllhost.exe (PID: 1196)
- SETUP.EXE (PID: 3540)
- label.exe (PID: 1264)
- ehmsas.exe (PID: 3220)
- SETUP.EXE (PID: 3000)
- conhost.exe (PID: 5460)
- explorer.exe (PID: 2692)
Changes default file association
- dllhost.exe (PID: 1196)
Checks Windows Trust Settings
- SETUP.EXE (PID: 3540)
- SETUP.EXE (PID: 3000)
Reads security settings of Internet Explorer
- SETUP.EXE (PID: 3540)
- SETUP.EXE (PID: 3000)
Reads settings of System Certificates
- SETUP.EXE (PID: 3540)
- SETUP.EXE (PID: 3000)
Starts itself from another location
- SETUP.EXE (PID: 3540)
Write to the desktop.ini file (may be used to cloak folders)
- Journal.exe (PID: 2500)
Changes the desktop background image
- ehmsas.exe (PID: 3220)
Process changes security settings for the VBA macro
- rdpclip.exe (PID: 6132)
INFO
Checks supported languages
- Bonzify.exe (PID: 2064)
- INSTALLER.exe (PID: 1236)
- AgentSvr.exe (PID: 1928)
- INSTALLER.exe (PID: 1536)
- AgentSvr.exe (PID: 2192)
- wmpnscfg.exe (PID: 3012)
- wmpnscfg.exe (PID: 3020)
- McxTask.exe (PID: 2860)
- msinfo32.exe (PID: 1812)
- printfilterpipelinesvc.exe (PID: 3396)
- dpapimig.exe (PID: 3752)
- consent.exe (PID: 2984)
- wmpenc.exe (PID: 3656)
- label.exe (PID: 1264)
- NETFXRepair.exe (PID: 3876)
- Journal.exe (PID: 2500)
- SETUP.EXE (PID: 3540)
- SearchProtocolHost.exe (PID: 3988)
- SETUP.EXE (PID: 3000)
- ehmsas.exe (PID: 3220)
- ehvid.exe (PID: 2044)
- wscript.exe (PID: 4624)
- ROUTE.EXE (PID: 4312)
- wuauclt.exe (PID: 5248)
- conhost.exe (PID: 5460)
- AxInstUI.exe (PID: 5892)
- RTLCPL.EXE (PID: 5976)
- Defrag.exe (PID: 4284)
- scrcons.exe (PID: 2372)
- dpapimig.exe (PID: 3756)
- TabTip.exe (PID: 2816)
- cttunesvr.exe (PID: 3156)
- userinit.exe (PID: 2764)
- wksprt.exe (PID: 3824)
- RegSvcs.exe (PID: 5644)
Create files in a temporary directory
- Bonzify.exe (PID: 2064)
- INSTALLER.exe (PID: 1236)
- INSTALLER.exe (PID: 1536)
- NETFXRepair.exe (PID: 3876)
- FXSSVC.exe (PID: 492)
- SETUP.EXE (PID: 3540)
- SETUP.EXE (PID: 3000)
Reads the computer name
- INSTALLER.exe (PID: 1236)
- wmpnscfg.exe (PID: 3020)
- INSTALLER.exe (PID: 1536)
- Bonzify.exe (PID: 2064)
- AgentSvr.exe (PID: 2192)
- wmpnscfg.exe (PID: 3012)
- msinfo32.exe (PID: 1812)
- dpapimig.exe (PID: 3752)
- consent.exe (PID: 2984)
- printfilterpipelinesvc.exe (PID: 3396)
- wmpenc.exe (PID: 3656)
- Journal.exe (PID: 2500)
- SETUP.EXE (PID: 3540)
- SETUP.EXE (PID: 3000)
- ehmsas.exe (PID: 3220)
- ehvid.exe (PID: 2044)
- wscript.exe (PID: 4624)
- wuauclt.exe (PID: 5248)
- dpapimig.exe (PID: 3756)
- TabTip.exe (PID: 2816)
- cttunesvr.exe (PID: 3156)
Reads the machine GUID from the registry
- AgentSvr.exe (PID: 2192)
- Bonzify.exe (PID: 2064)
- msinfo32.exe (PID: 1812)
- dpapimig.exe (PID: 3752)
- printfilterpipelinesvc.exe (PID: 3396)
- wmpenc.exe (PID: 3656)
- label.exe (PID: 1264)
- Journal.exe (PID: 2500)
- SearchProtocolHost.exe (PID: 3988)
- SETUP.EXE (PID: 3540)
- SETUP.EXE (PID: 3000)
- ehmsas.exe (PID: 3220)
- ehvid.exe (PID: 2044)
- wscript.exe (PID: 4624)
- wuauclt.exe (PID: 5248)
- conhost.exe (PID: 5460)
- RTLCPL.EXE (PID: 5976)
- TabTip.exe (PID: 2816)
- userinit.exe (PID: 2764)
- cttunesvr.exe (PID: 3156)
Manual execution by a user
- wmpnscfg.exe (PID: 3020)
- wmpnscfg.exe (PID: 3012)
- services.exe (PID: 2956)
- InfDefaultInstall.exe (PID: 1544)
- powershell.exe (PID: 2308)
- msinfo32.exe (PID: 1812)
- bcdedit.exe (PID: 2852)
- dpapimig.exe (PID: 3752)
- comp.exe (PID: 2076)
- wmpconfig.exe (PID: 3500)
- audit.exe (PID: 1652)
- rrinstaller.exe (PID: 1220)
- DismHost.exe (PID: 3808)
- sdbinst.exe (PID: 4000)
- Defrag.exe (PID: 4284)
- RTLCPL.EXE (PID: 5976)
- expand.exe (PID: 1880)
- dw20.exe (PID: 3284)
- regedt32.exe (PID: 1348)
- wksprt.exe (PID: 3824)
- ComSvcConfig.exe (PID: 5200)
Reads the time zone
- runonce.exe (PID: 392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 MS Cabinet Self-Extractor (WExtract stub) (86.7) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (8.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.8) |
| .exe | | | Win32 Executable (generic) (1.2) |
| .exe | | | Generic Win/DOS Executable (0.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:03:04 15:58:11+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 4096 |
| InitializedDataSize: | 6697472 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16b0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
428
Monitored processes
101
Malicious processes
16
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | C:\Windows\system32\DllHost.exe /Processid:{EA2C6B24-C590-457B-BAC8-4A0F9B13B5B8} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 3221226356 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | "C:\Windows\System32\runonce.exe" | C:\Windows\System32\runonce.exe | — | label.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 492 | "C:\Windows\System32\FXSSVC.exe" | C:\Windows\System32\FXSSVC.exe | — | printfilterpipelinesvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Fax Service Exit code: 1063 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 584 | takeown /r /d y /f C:\Windows\MsAgent | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 712 | regsvr32 /s "C:\Windows\msagent\AgentDP2.dll" | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 956 | regsvr32 /s "C:\Windows\msagent\AgentCtl.dll" | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 968 | C:\Windows\system32\DeviceDisplayObjectProvider.exe -Embedding | C:\Windows\System32\DeviceDisplayObjectProvider.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Device Display Object Function Discovery Provider Exit code: 2147942405 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1196 | C:\Windows\system32\DllHost.exe /Processid:{06C792F8-6212-4F39-BF70-E8C0AC965C23} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1220 | "C:\Windows\winsxs\x86_microsoft-windows-mediafoundation_31bf3856ad364e35_6.1.7601.17514_none_9e6699276b03c38e\rrinstaller.exe" | C:\Windows\winsxs\x86_microsoft-windows-mediafoundation_31bf3856ad364e35_6.1.7601.17514_none_9e6699276b03c38e\rrinstaller.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: R&R installer Exit code: 3221226540 Version: 11.0.7600.16385 Modules
| |||||||||||||||
| 1236 | INSTALLER.exe /q | C:\Users\admin\AppData\Local\Temp\INSTALLER.exe | Bonzify.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 4.71.1015.0 Modules
| |||||||||||||||
Total events
11 639
Read events
8 957
Write events
2 661
Delete events
21
Modification events
| (PID) Process: | (956) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\Control |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (956) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\InprocServer32 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (956) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\MiscStatus\1 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (956) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\MiscStatus |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (956) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\ProgID |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (956) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\Programmable |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (956) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\ToolboxBitmap32 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (956) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\TypeLib |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (956) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\Version |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (956) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\VersionIndependentProgID |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
55
Suspicious files
20
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2064 | Bonzify.exe | C:\Users\admin\AppData\Local\Temp\KillAgent.bat | text | |
MD5:EA7DF060B402326B4305241F21F39736 | SHA256:E4EDC2CB6317AB19EE1A6327993E9332AF35CFBEBAFF2AC7C3F71D43CFCBE793 | |||
| 1236 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGT0409.DLL | executable | |
MD5:0CBF0F4C9E54D12D34CD1A772BA799E1 | SHA256:6B0B57E5B27D901F4F106B236C58D0B2551B384531A8F3DAD6C06ED4261424B1 | |||
| 2064 | Bonzify.exe | C:\Windows\executables.bin | binary | |
MD5:F3160BA7F8BB9D7A9C6080EF2C9869C5 | SHA256:F6A3286714A661612EAC65E4A6CB78736C370492151B692A8F1E666740C0A00E | |||
| 1236 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTSR.DLL | executable | |
MD5:9FAFB9D0591F2BE4C2A846F63D82D301 | SHA256:E78E74C24D468284639FAF9DCFDBA855F3E4F00B2F26DB6B2C491FA51DA8916D | |||
| 1236 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTDPV.DLL | executable | |
MD5:7C5AEFB11E797129C9E90F279FBDF71B | SHA256:394A17150B8774E507B8F368C2C248C10FCE50FC43184B744E771F0E79ECAFED | |||
| 1236 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGT0409.HLP | binary | |
MD5:466D35E6A22924DD846A043BC7DD94B8 | SHA256:E4CCF06706E68621BB69ADD3DD88FED82D30AD8778A55907D33F6D093AC16801 | |||
| 1236 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTANM.DLL | executable | |
MD5:48C00A7493B28139CBF197CCC8D1F9ED | SHA256:905CB1A15ECCAA9B79926EE7CFE3629A6F1C6B24BDD6CEA9CCB9EBC9EAA92FF7 | |||
| 1236 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGTCTL15.TLB | executable | |
MD5:F1656B80EAAE5E5201DCBFBCD3523691 | SHA256:3F8ADC1E332DD5C252BBCF92BF6079B38A74D360D94979169206DB34E6A24CD2 | |||
| 1236 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGTEULA.TXT | text | |
MD5:7070B77ED401307D2E9A0F8EAAAA543B | SHA256:225D227ABBD45BF54D01DFC9FA6E54208BF5AE452A32CC75B15D86456A669712 | |||
| 1236 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGT20.INF | binary | |
MD5:E4A499B9E1FE33991DBCFB4E926C8821 | SHA256:49E6B848F5A708D161F795157333D7E1C7103455A2F47F50895683EF6A1ABE4D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4896 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
iecvlist.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | ClaimOutput
|