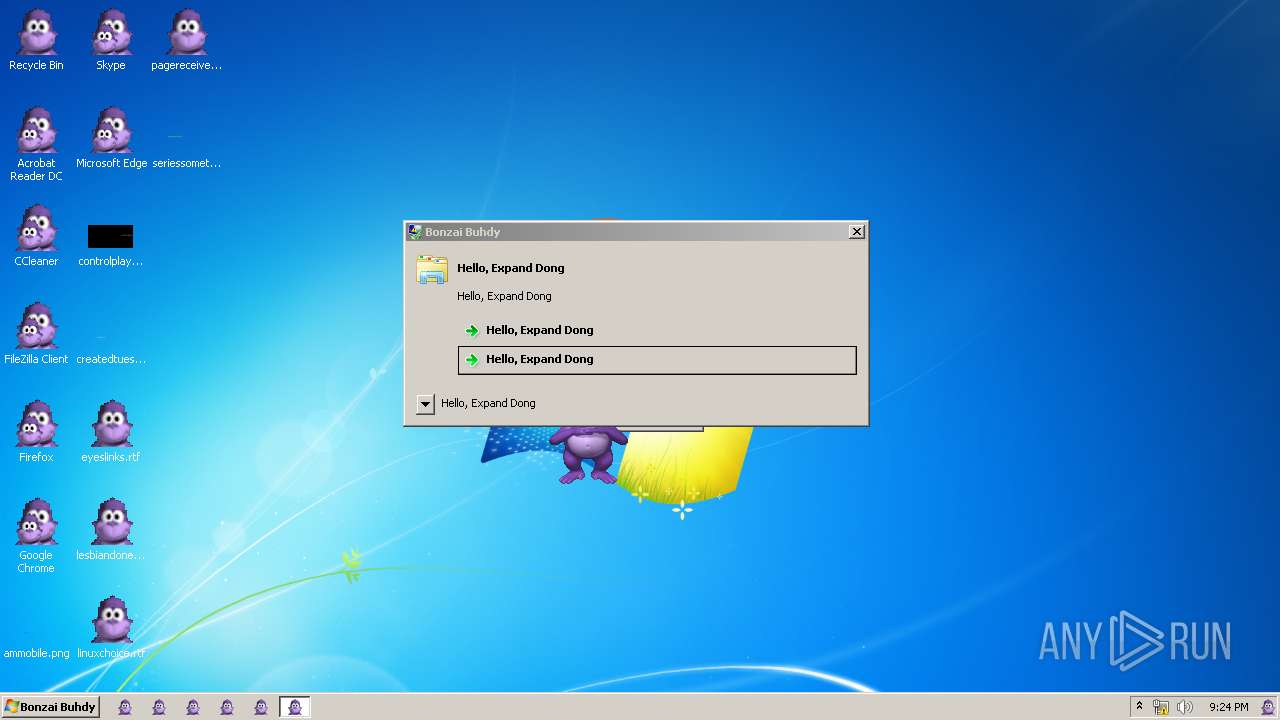
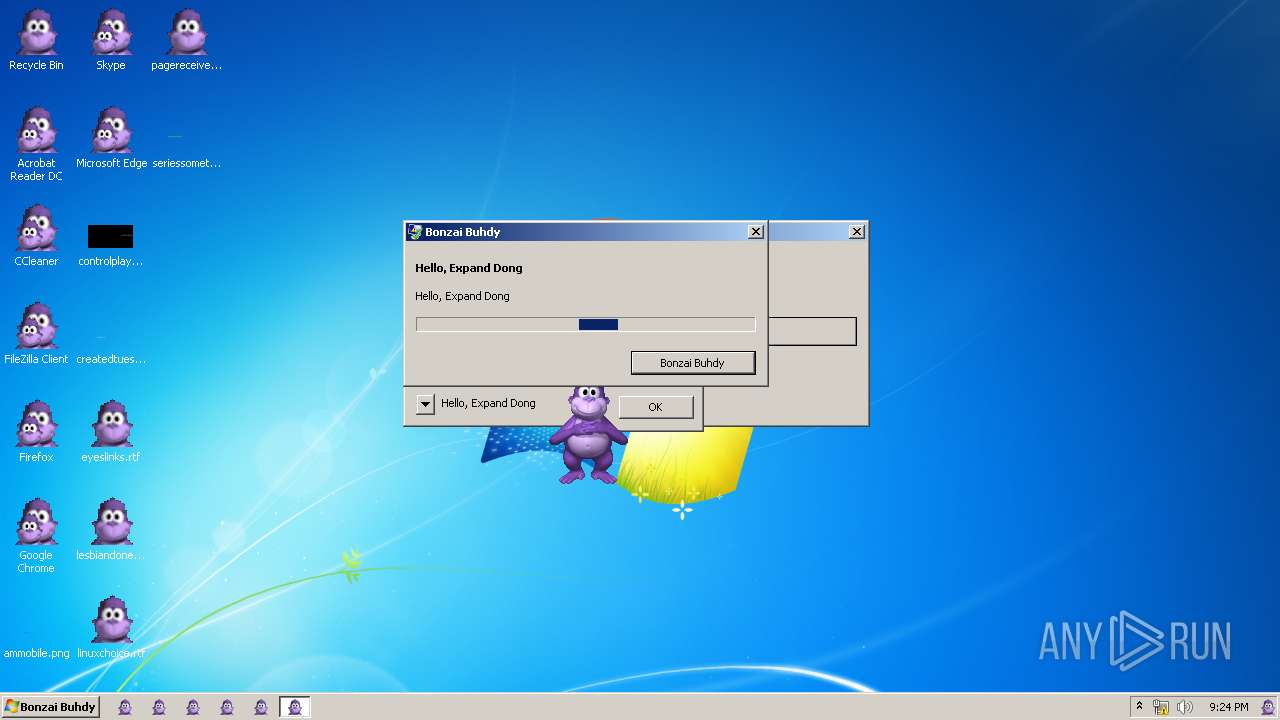
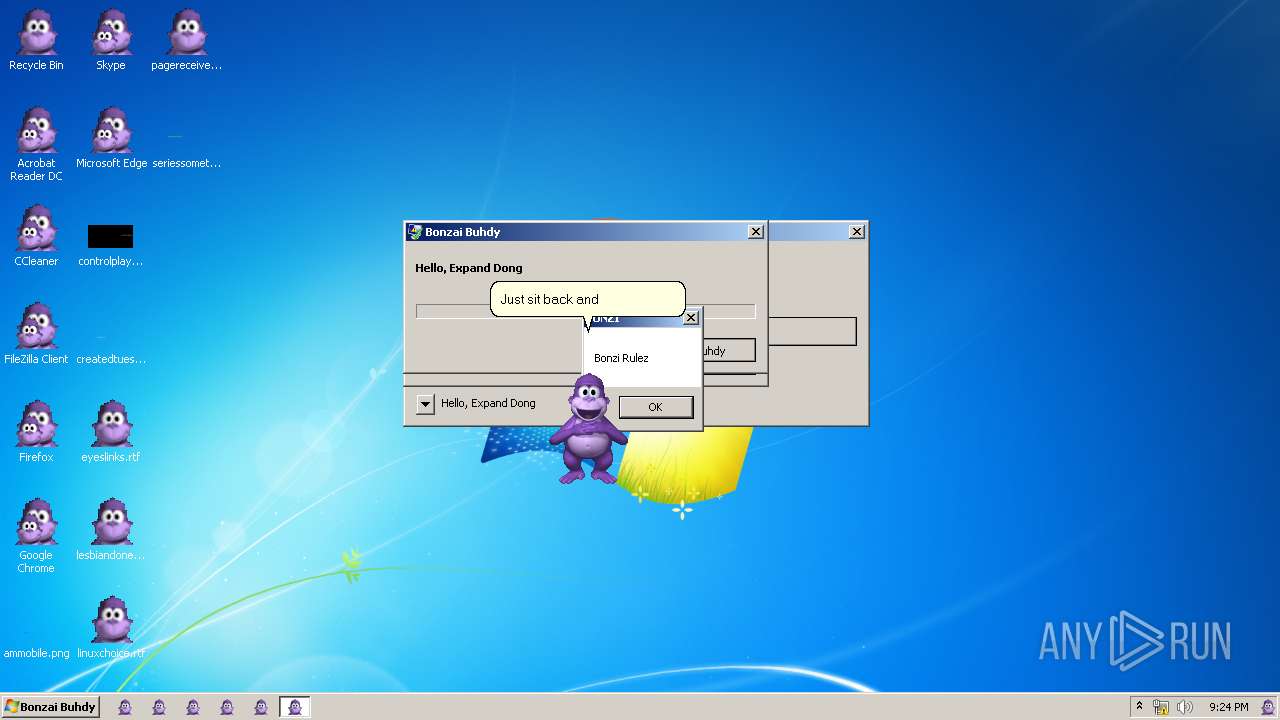
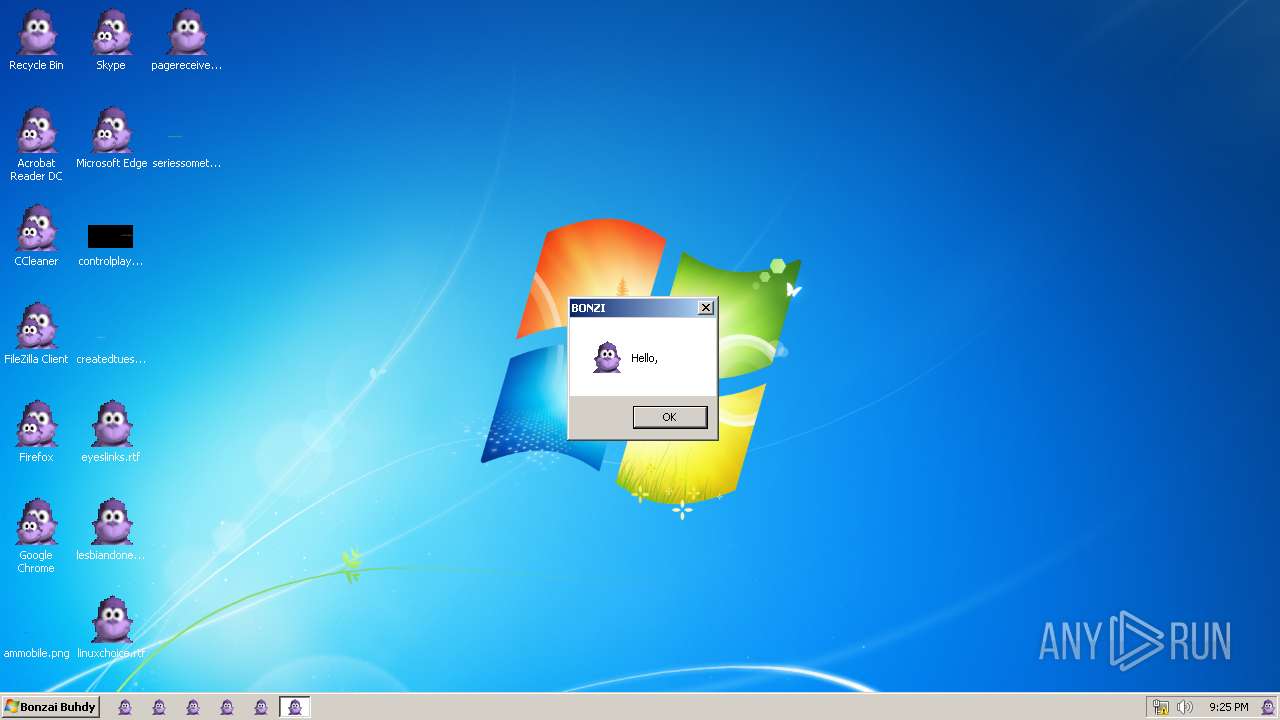
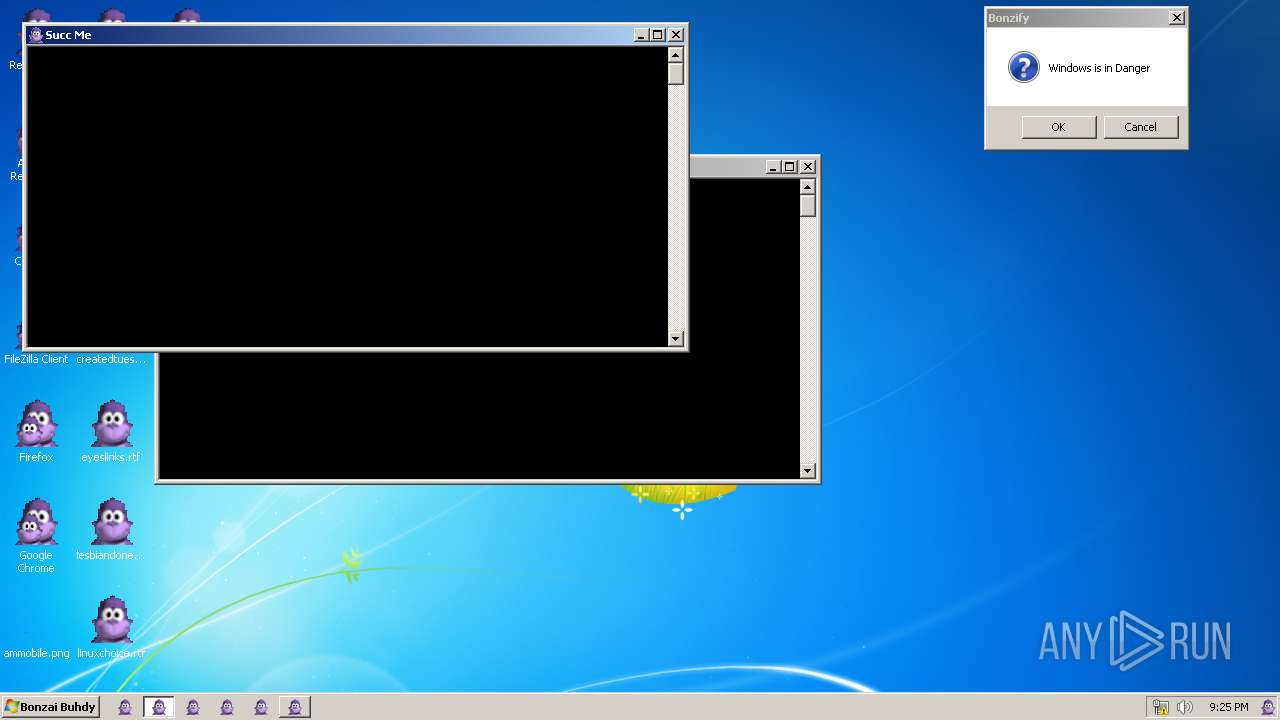
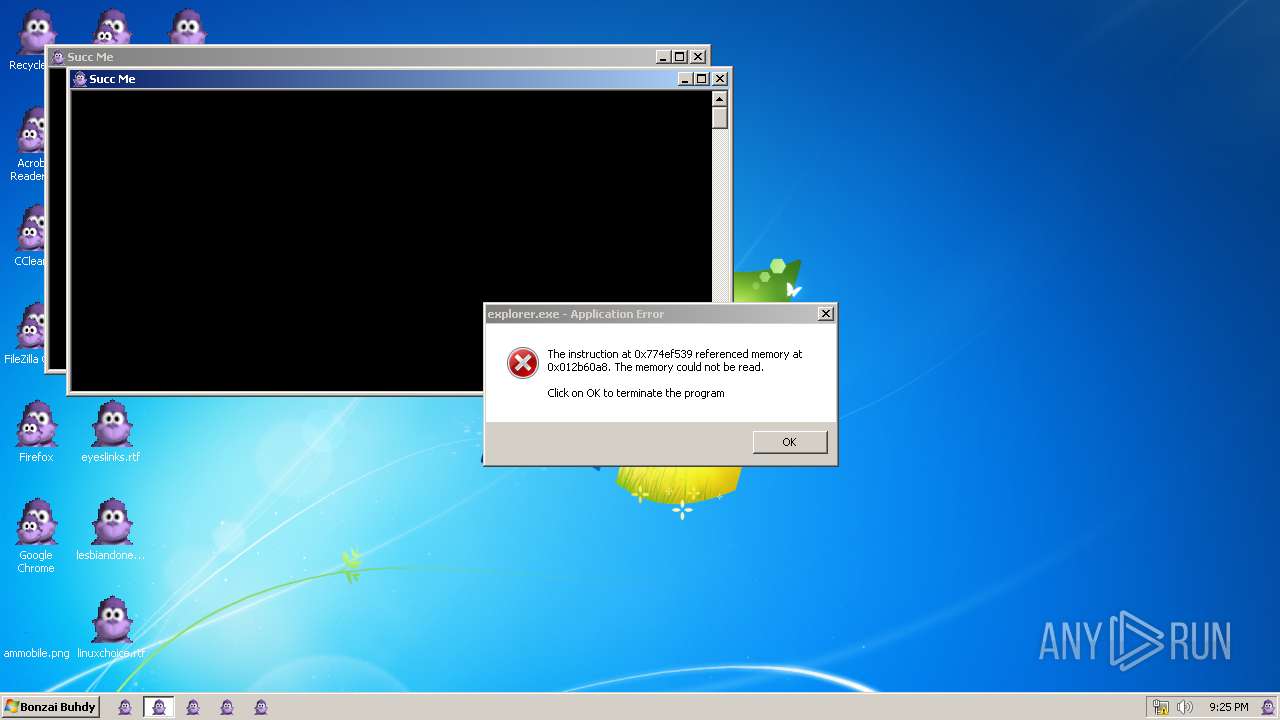
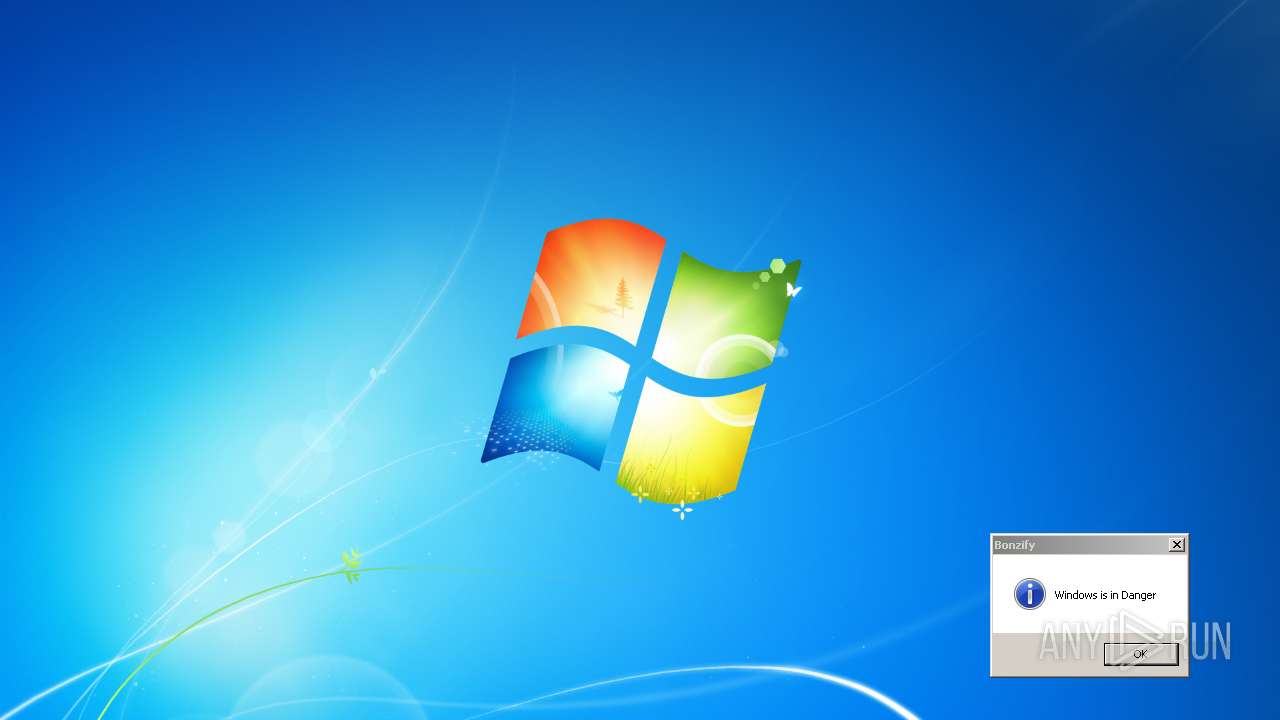
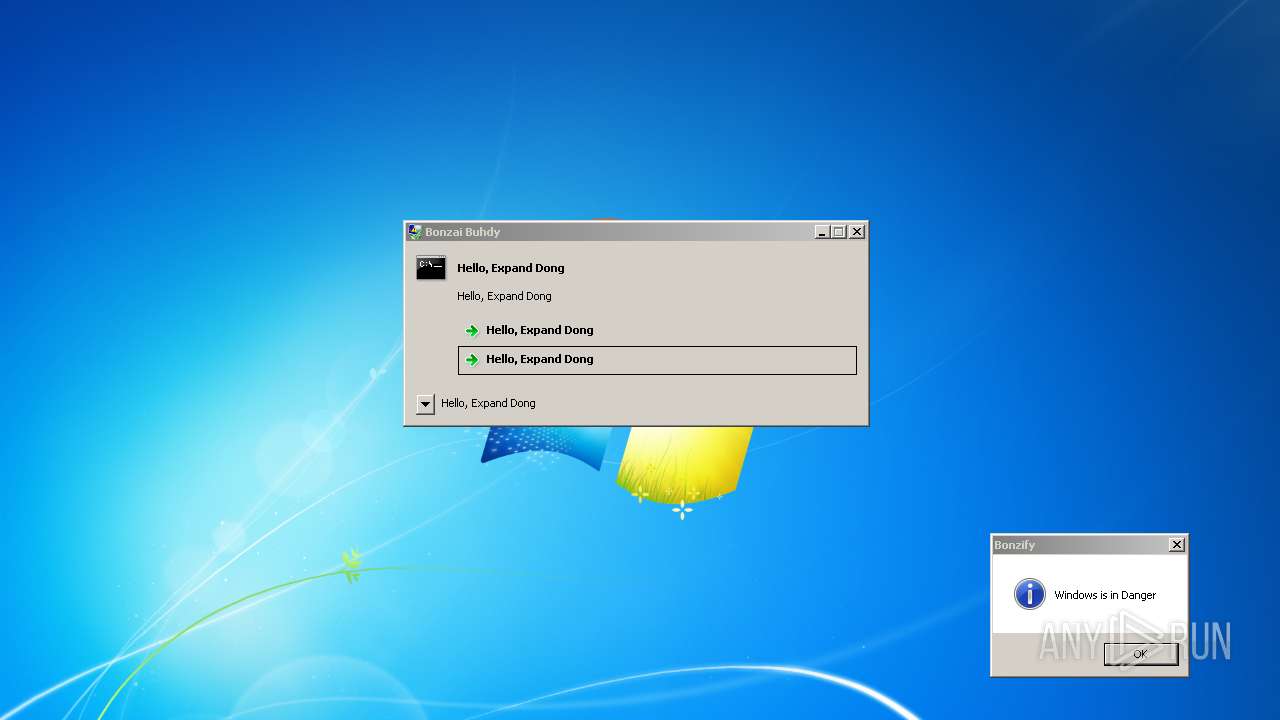
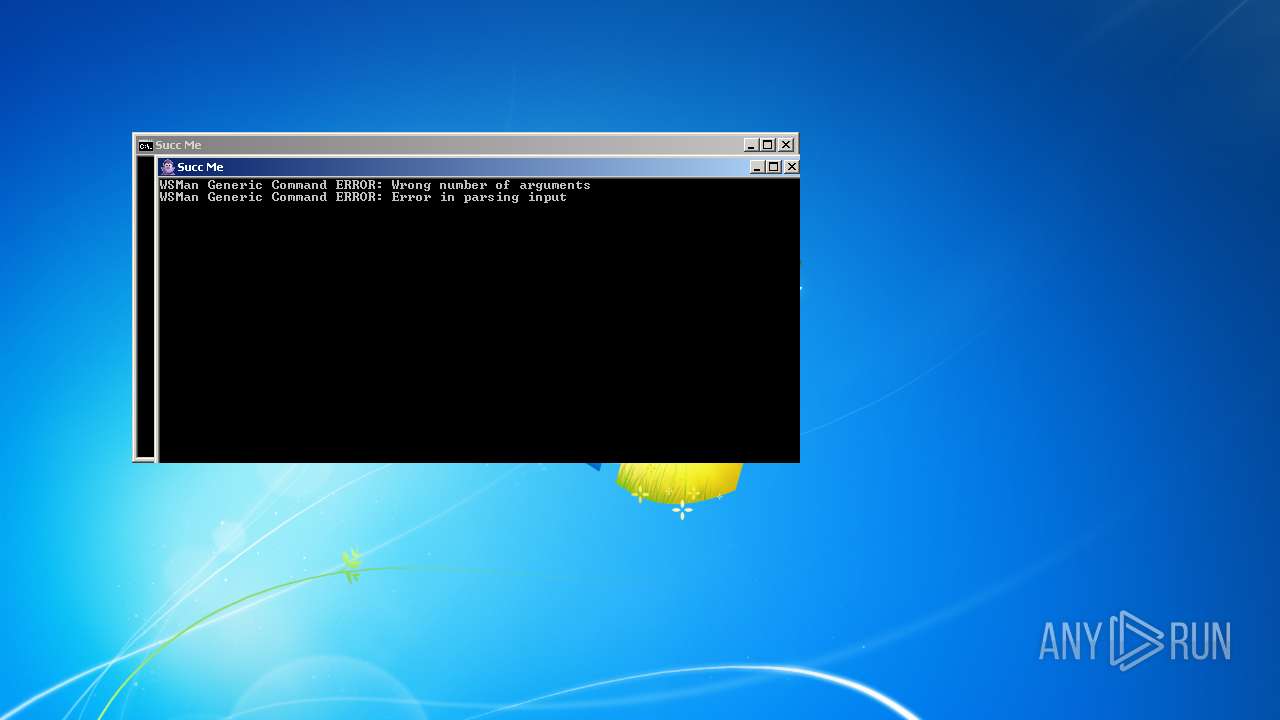
| File name: | Bonzify.exe |
| Full analysis: | https://app.any.run/tasks/aee6adac-0381-4cac-94b7-d4022cf4afd9 |
| Verdict: | Malicious activity |
| Analysis date: | October 03, 2024, 20:22:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9C352D2CE0C0BDC40C72F52CE3480577 |
| SHA1: | BD4C956186F33C92EB4469F7E5675510D0790E99 |
| SHA256: | D7E6580054525D3F21F86EDFC9F30B7A75FFA829A1EB67EE3CAB33F0040DBA4E |
| SSDEEP: | 196608:/dAMaWetTeAkLIdx751qFTkub//73lc6u7b5VJ2Yx5xIdk3o:naWedh+Idx75QYub//73lc6u7bLMYxDo |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- INSTALLER.exe (PID: 900)
- INSTALLER.exe (PID: 148)
SUSPICIOUS
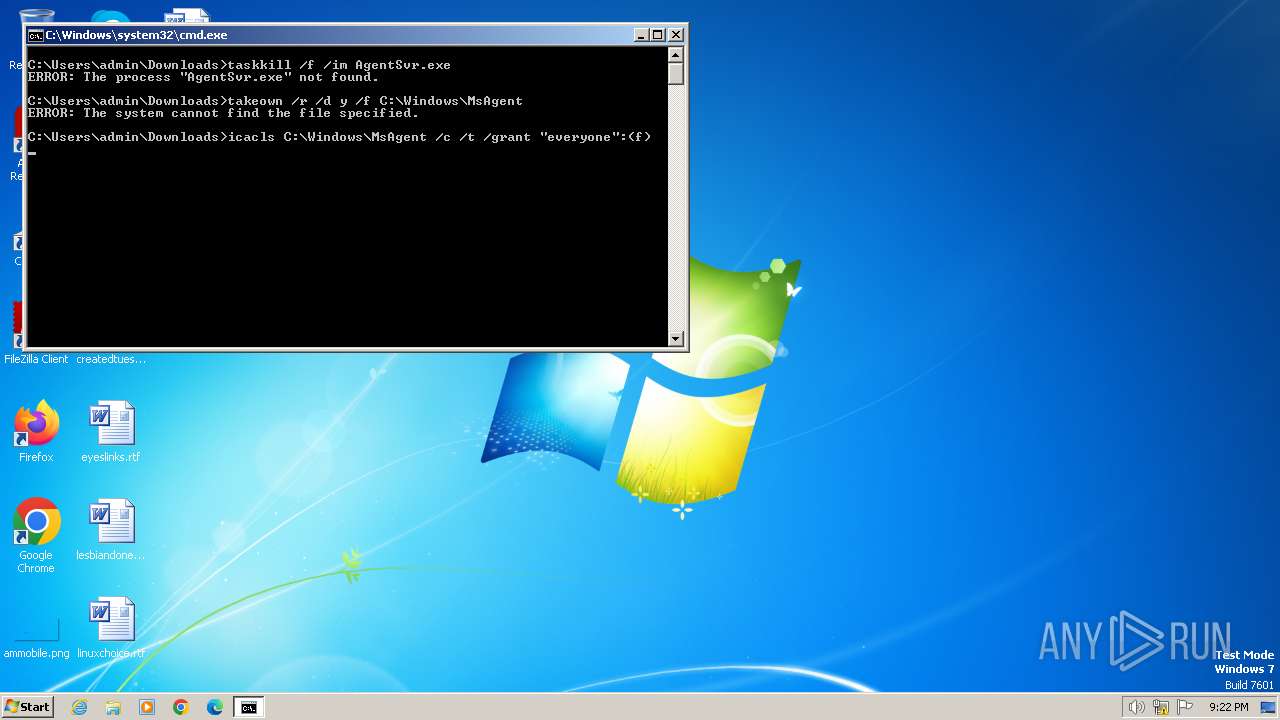
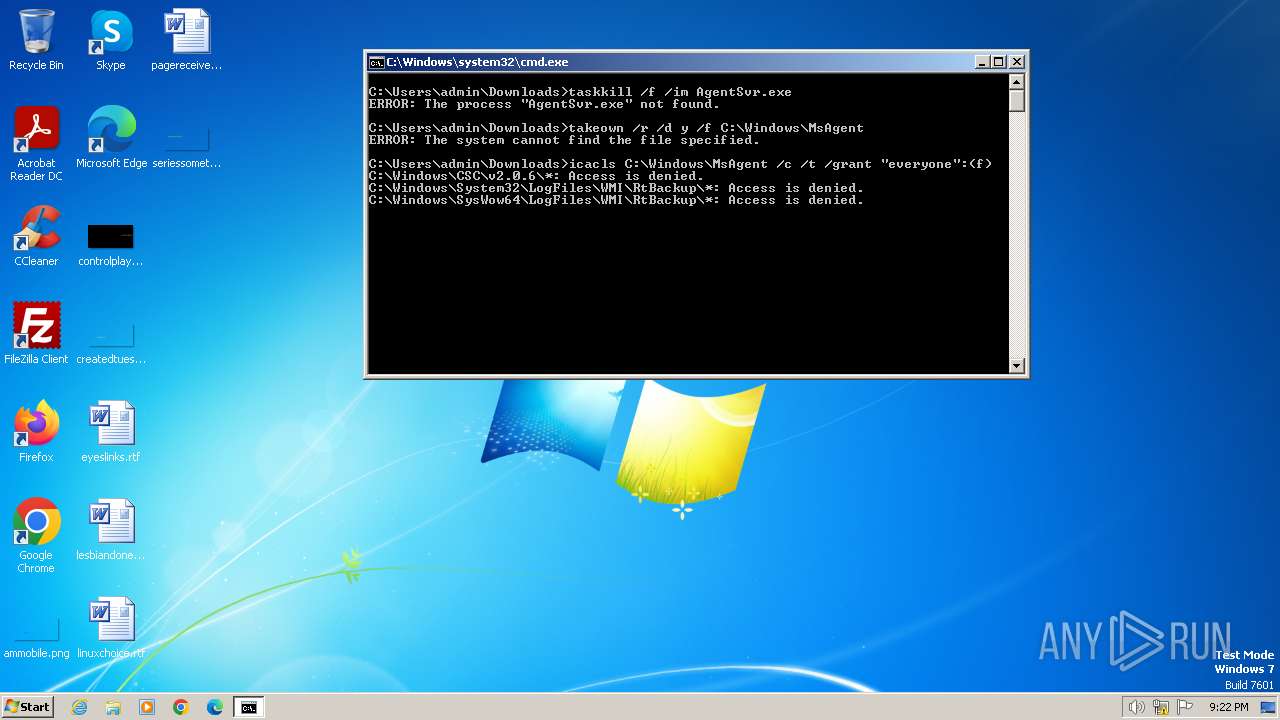
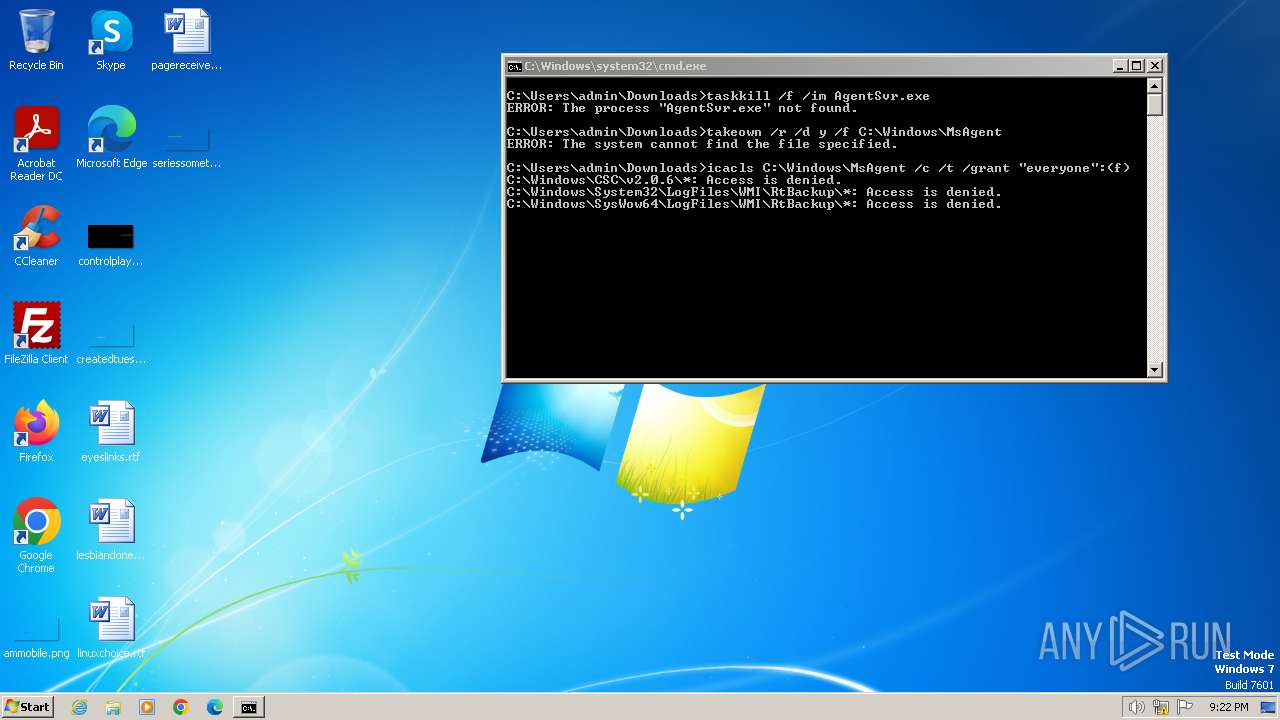
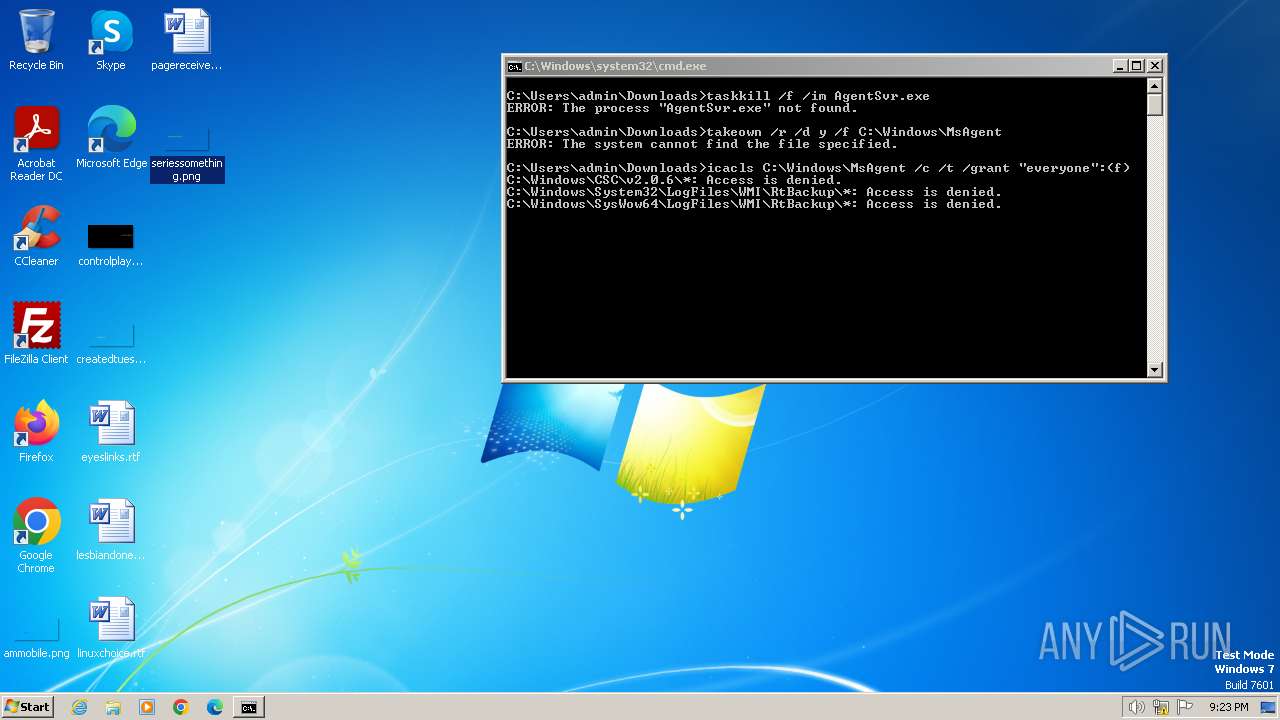
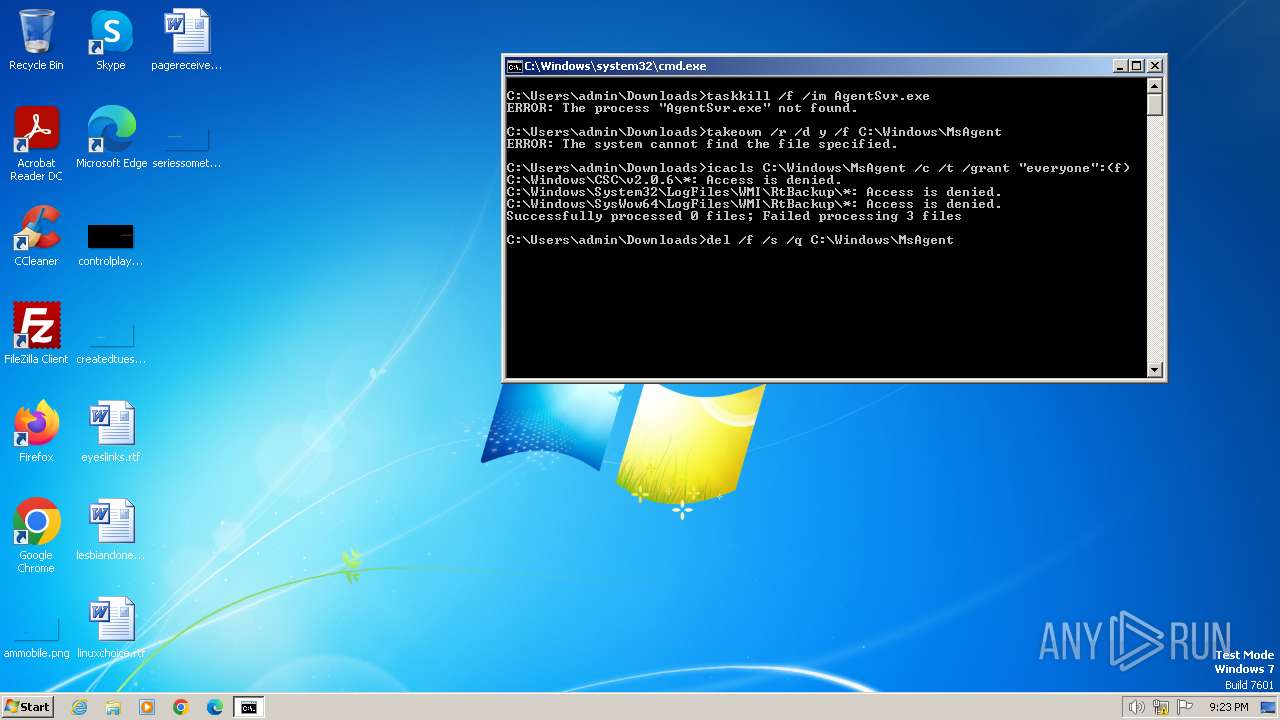
Starts CMD.EXE for commands execution
- Bonzify.exe (PID: 2136)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 3900)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3900)
Executing commands from a ".bat" file
- Bonzify.exe (PID: 2136)
Process drops legitimate windows executable
- Bonzify.exe (PID: 2136)
- INSTALLER.exe (PID: 900)
- INSTALLER.exe (PID: 148)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3900)
Starts a Microsoft application from unusual location
- INSTALLER.exe (PID: 900)
- INSTALLER.exe (PID: 148)
Executable content was dropped or overwritten
- INSTALLER.exe (PID: 900)
- Bonzify.exe (PID: 2136)
- INSTALLER.exe (PID: 148)
Executes as Windows Service
- dllhost.exe (PID: 3764)
Uses RUNDLL32.EXE to load library
- runonce.exe (PID: 288)
INFO
Checks supported languages
- Bonzify.exe (PID: 2136)
Create files in a temporary directory
- Bonzify.exe (PID: 2136)
Manual execution by a user
- PrintBrmUi.exe (PID: 1828)
- wmpnscfg.exe (PID: 2388)
- msiexec.exe (PID: 2864)
- Journal.exe (PID: 680)
- EdmGen.exe (PID: 3792)
- SMConfigInstaller.exe (PID: 2836)
- wmpnscfg.exe (PID: 1076)
- winresume.exe (PID: 3156)
- wbadmin.exe (PID: 596)
- SvcIni.exe (PID: 660)
- appidpolicyconverter.exe (PID: 3676)
- wmpnscfg.exe (PID: 3452)
- wmpnscfg.exe (PID: 2984)
- mscorsvw.exe (PID: 3248)
- rdrmemptylst.exe (PID: 3736)
- pcawrk.exe (PID: 2660)
- SyncHost.exe (PID: 3580)
- baaupdate.exe (PID: 3900)
- WFS.exe (PID: 2004)
- BrmfRsmg.exe (PID: 3228)
- runonce.exe (PID: 288)
- expand.exe (PID: 3200)
- icardagt.exe (PID: 2652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 MS Cabinet Self-Extractor (WExtract stub) (86.7) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (8.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.8) |
| .exe | | | Win32 Executable (generic) (1.2) |
| .exe | | | Generic Win/DOS Executable (0.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:03:04 14:58:11+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 4096 |
| InitializedDataSize: | 6697472 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16b0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
311
Monitored processes
50
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | INSTALLER.exe /q | C:\Users\admin\AppData\Local\Temp\INSTALLER.exe | Bonzify.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 4.71.1015.0 Modules
| |||||||||||||||
| 268 | regsvr32 /s "C:\Windows\msagent\AgentPsh.dll" | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 288 | runonce.exe /Explorer | C:\Windows\System32\runonce.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 596 | "C:\Windows\winsxs\x86_microsoft-windows-blb-cli-main_31bf3856ad364e35_6.1.7600.16385_none_4b2b3343f0594dd2\wbadmin.exe" | C:\Windows\winsxs\x86_microsoft-windows-blb-cli-main_31bf3856ad364e35_6.1.7600.16385_none_4b2b3343f0594dd2\wbadmin.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Command Line Interface for Microsoft® BLB Backup Exit code: 4294967295 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 648 | regsvr32 /s C:\Windows\lhsp\tv\tv_enua.dll | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 656 | regsvr32 /s C:\Windows\lhsp\tv\tvenuax.dll | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 660 | "C:\Windows\winsxs\x86_microsoft-windows-servicingstack_31bf3856ad364e35_6.1.7601.24544_none_0bcfb1fd3ec2d6c8\SvcIni.exe" | C:\Windows\winsxs\x86_microsoft-windows-servicingstack_31bf3856ad364e35_6.1.7601.24544_none_0bcfb1fd3ec2d6c8\SvcIni.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Generic command for servicing ini files Exit code: 87 Version: 6.1.7601.24544 (win7sp1_ldr_escrow.191230-1647) Modules
| |||||||||||||||
| 680 | "C:\Windows\winsxs\x86_microsoft-windows-tabletpc-journal_31bf3856ad364e35_6.1.7601.19112_none_19b6bc8102dc5ae8\Journal.exe" | C:\Windows\winsxs\x86_microsoft-windows-tabletpc-journal_31bf3856ad364e35_6.1.7601.19112_none_19b6bc8102dc5ae8\Journal.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Journal Exit code: 0 Version: 6.1.7601.19112 (win7sp1_gdr.160106-0600) Modules
| |||||||||||||||
| 900 | INSTALLER.exe /q | C:\Users\admin\AppData\Local\Temp\INSTALLER.exe | Bonzify.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 4.71.1015.0 Modules
| |||||||||||||||
| 1020 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 819
Read events
2 243
Write events
559
Delete events
17
Modification events
| (PID) Process: | (1020) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: DllHost.exe | |||
| (PID) Process: | (1020) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000034000000A00400008002000001000000 | |||
| (PID) Process: | (1364) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (1364) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F5BE8BD2-7DE6-11D0-91FE-00C04FD701A5}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (1364) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\Control |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1364) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\InprocServer32 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1364) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\MiscStatus\1 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1364) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\MiscStatus |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1364) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\ProgID |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1364) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\Programmable |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
55
Suspicious files
17
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | Bonzify.exe | C:\Users\admin\AppData\Local\Temp\KillAgent.bat | text | |
MD5:EA7DF060B402326B4305241F21F39736 | SHA256:E4EDC2CB6317AB19EE1A6327993E9332AF35CFBEBAFF2AC7C3F71D43CFCBE793 | |||
| 900 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGTCTL15.TLB | executable | |
MD5:F1656B80EAAE5E5201DCBFBCD3523691 | SHA256:3F8ADC1E332DD5C252BBCF92BF6079B38A74D360D94979169206DB34E6A24CD2 | |||
| 900 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTDPV.DLL | executable | |
MD5:7C5AEFB11E797129C9E90F279FBDF71B | SHA256:394A17150B8774E507B8F368C2C248C10FCE50FC43184B744E771F0E79ECAFED | |||
| 900 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTDP2.DLL | executable | |
MD5:A334BBF5F5A19B3BDB5B7F1703363981 | SHA256:C33BEABA130F8B740DDDB9980FE9012F9322AC6E94F36A6AA6086851C51B98DE | |||
| 2136 | Bonzify.exe | C:\Users\admin\AppData\Local\Temp\TakeOwn.bat | text | |
MD5:F80E36CD406022944558D8A099DB0FA7 | SHA256:7B41E5A6C2DD92F60C38CB4FE09DCBE378C3E99443F7BAF079ECE3608497BDC7 | |||
| 2136 | Bonzify.exe | C:\Users\admin\AppData\Local\Temp\INSTALLER.exe | executable | |
MD5:66996A076065EBDCDAC85FF9637CEAE0 | SHA256:16CA09AD70561F413376AD72550AE5664C89C6A76C85C872FFE2CB1E7F49E2AA | |||
| 900 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTMPX.DLL | executable | |
MD5:4FBBAAC42CF2ECB83543F262973D07C0 | SHA256:6550582E41FC53B8A7CCDF9AC603216937C6FF2A28E9538610ADB7E67D782AB5 | |||
| 900 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTSVR.EXE | executable | |
MD5:5C91BF20FE3594B81052D131DB798575 | SHA256:E8CE546196B6878A8C34DA863A6C8A7E34AF18FB9B509D4D36763734EFA2D175 | |||
| 900 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\MSLWVTTS.DLL | executable | |
MD5:316999655FEF30C52C3854751C663996 | SHA256:EA4CA740CD60D2C88280FF8115BF354876478EF27E9E676D8B66601B4E900BA0 | |||
| 900 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGT0409.DLL | executable | |
MD5:0CBF0F4C9E54D12D34CD1A772BA799E1 | SHA256:6B0B57E5B27D901F4F106B236C58D0B2551B384531A8F3DAD6C06ED4261424B1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
7
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3028 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
watson.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|