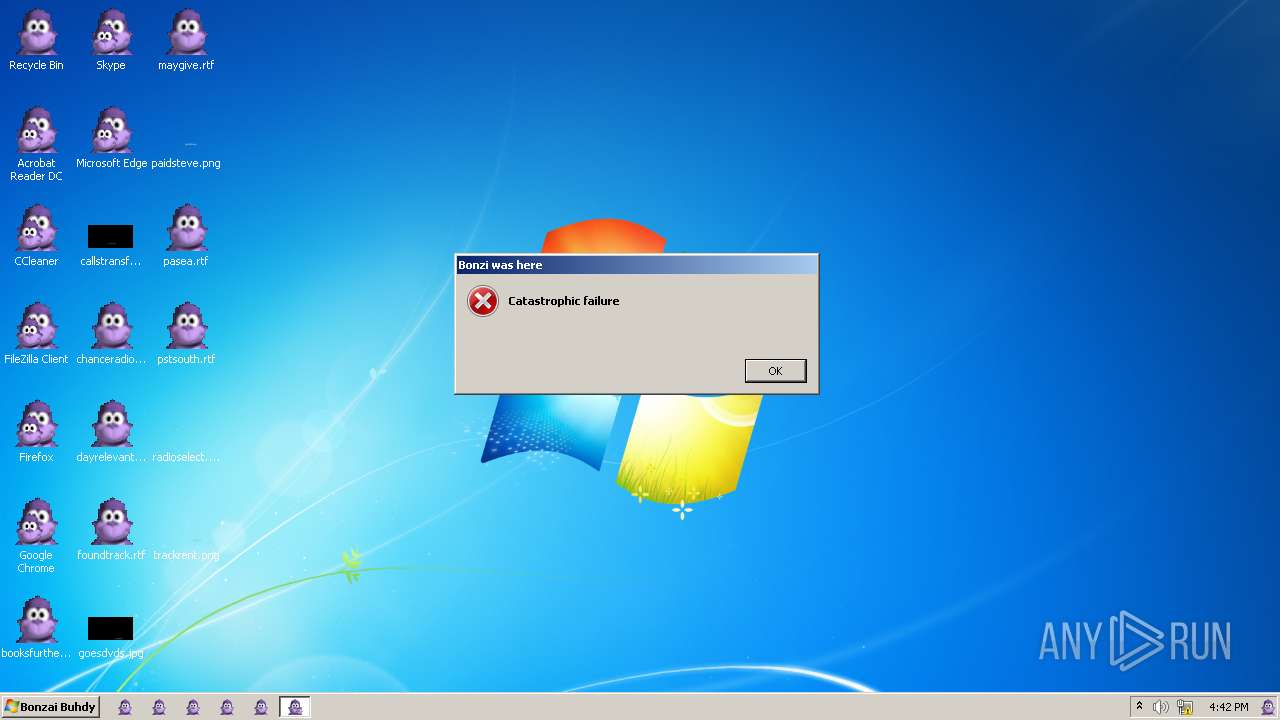
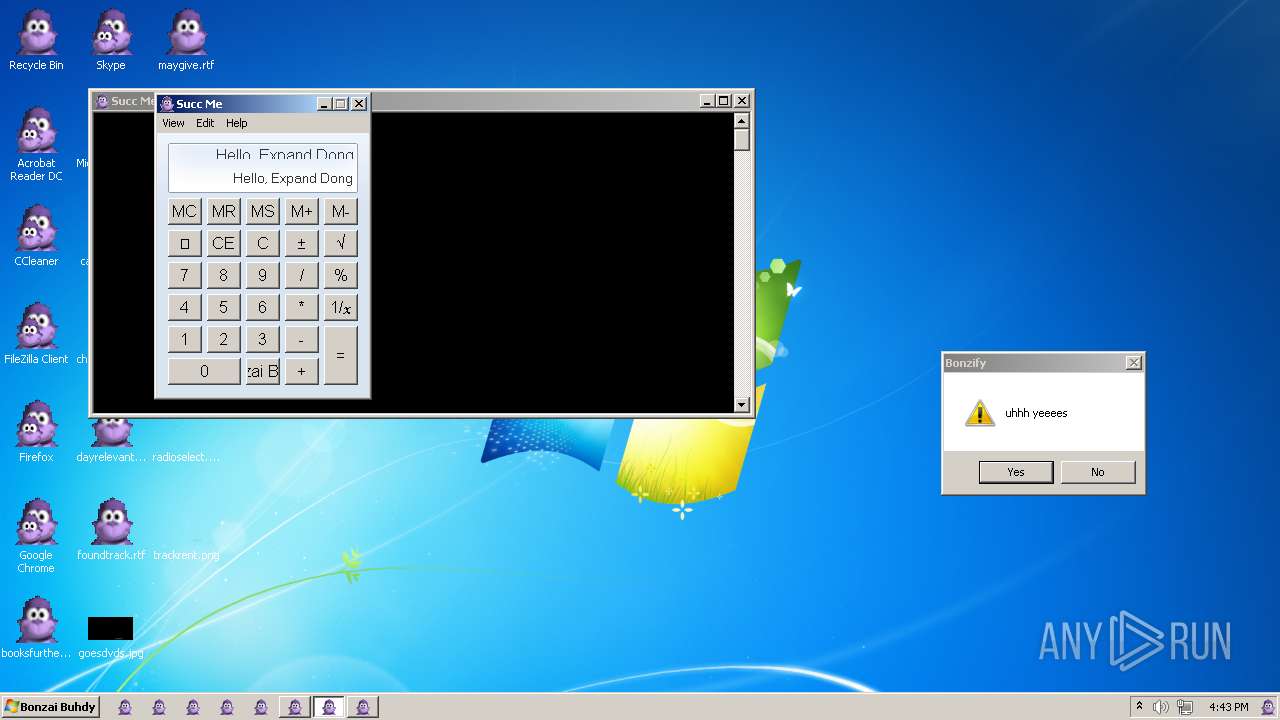
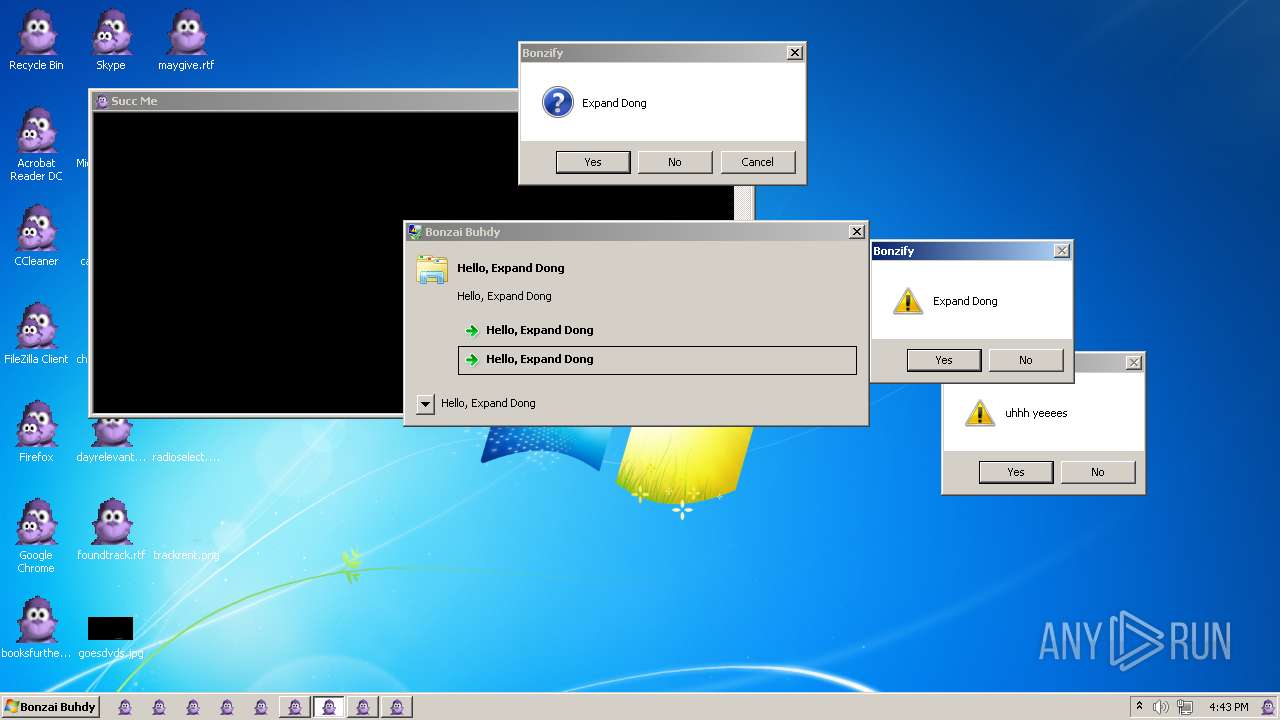
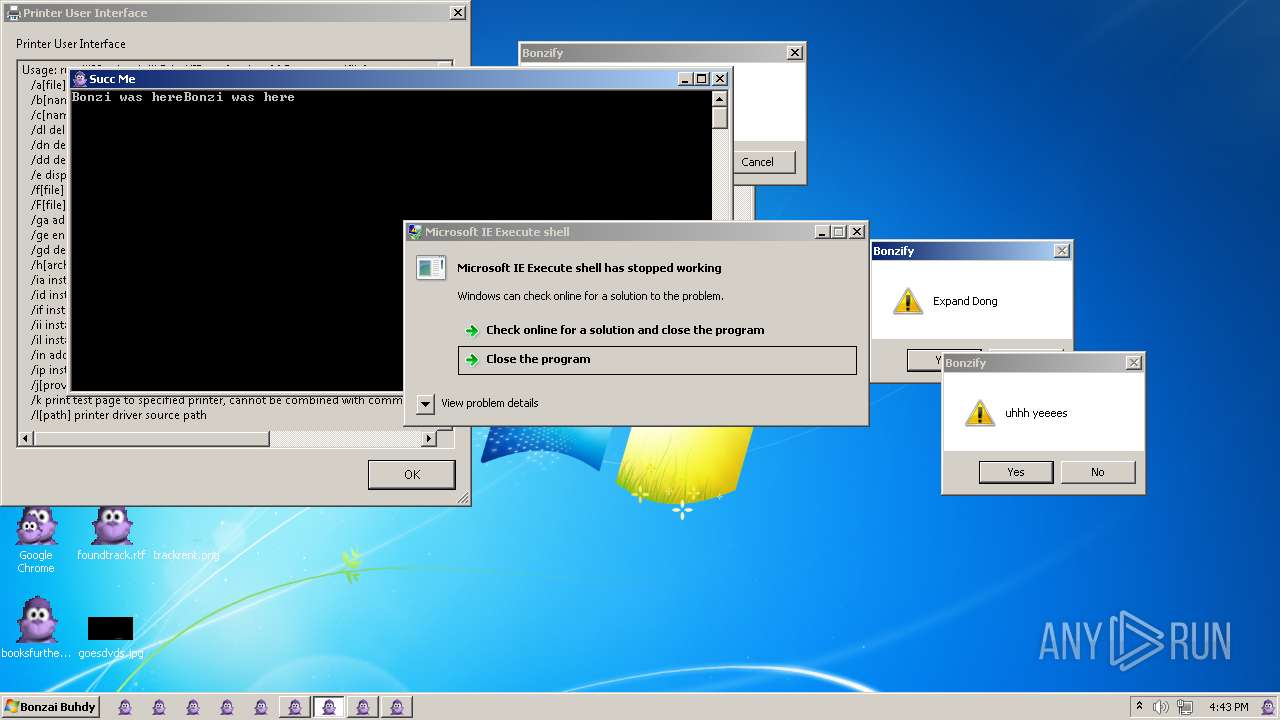
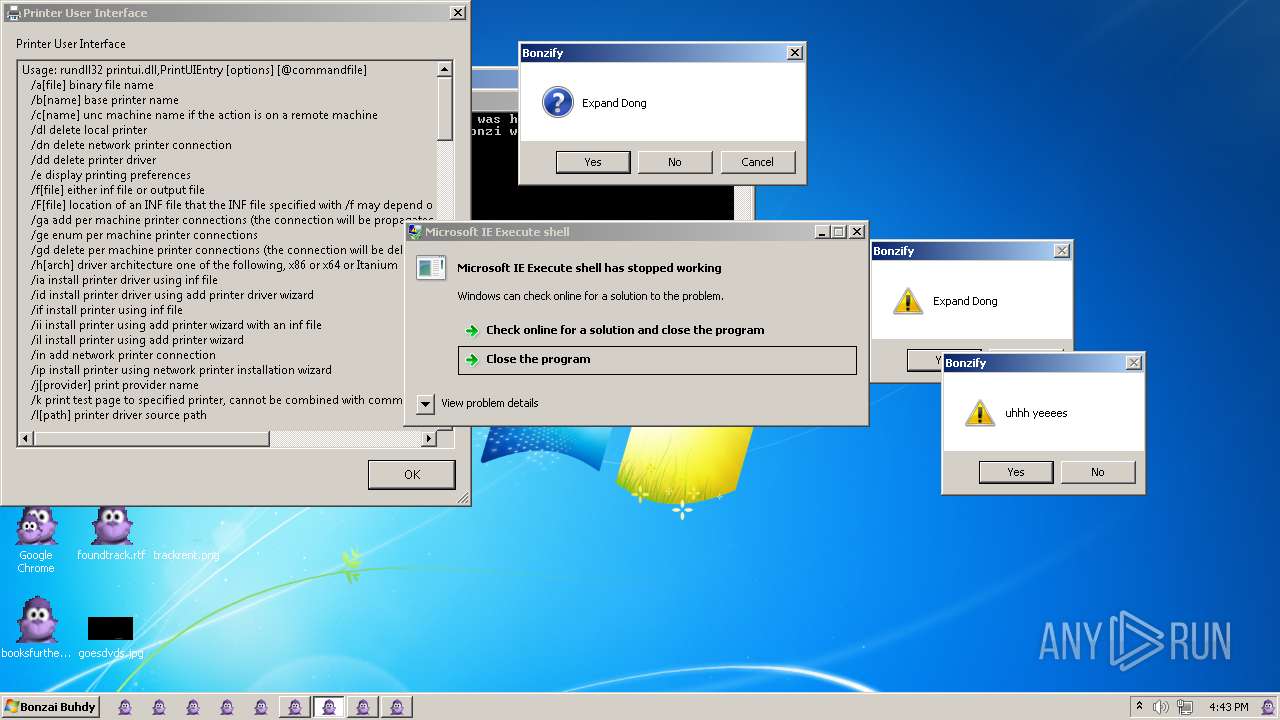
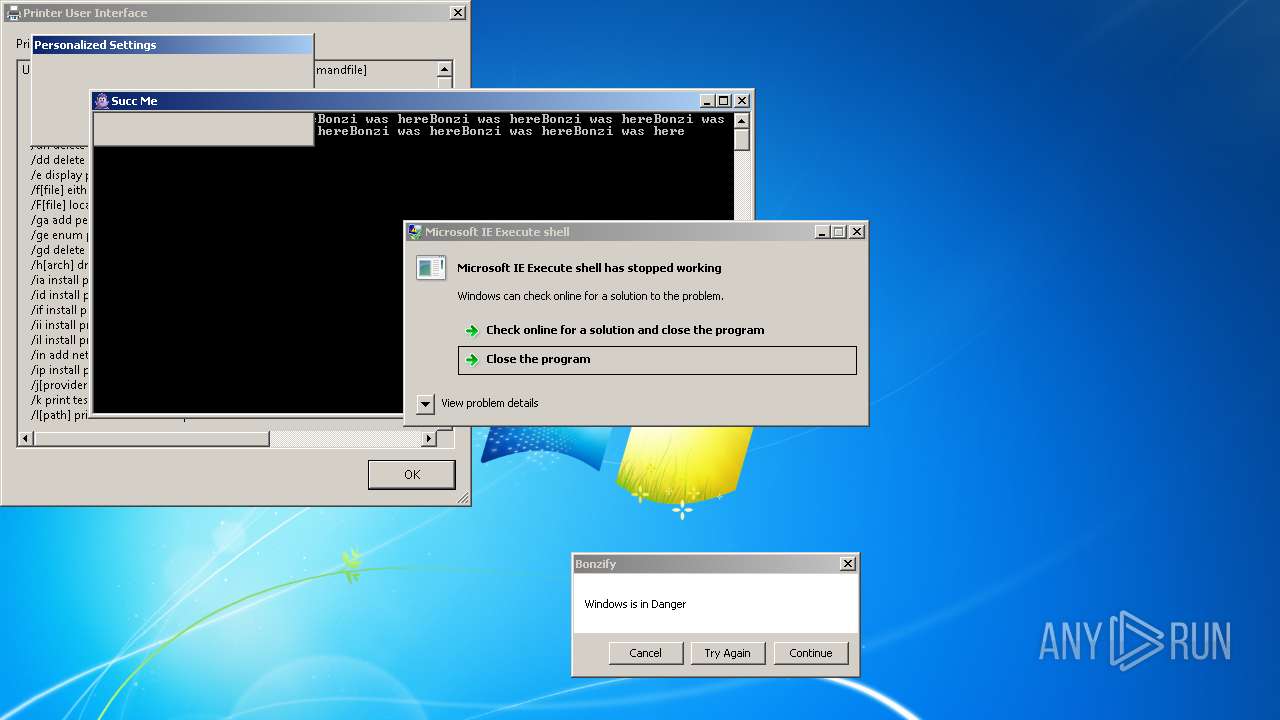
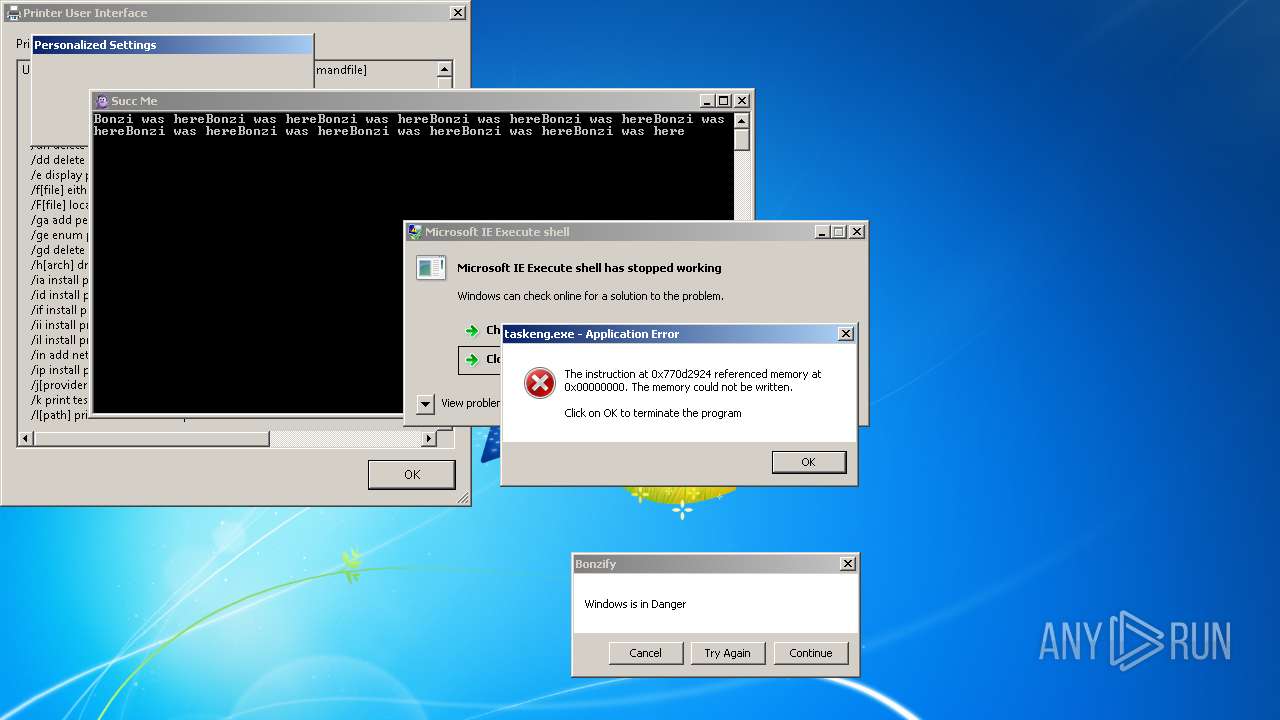
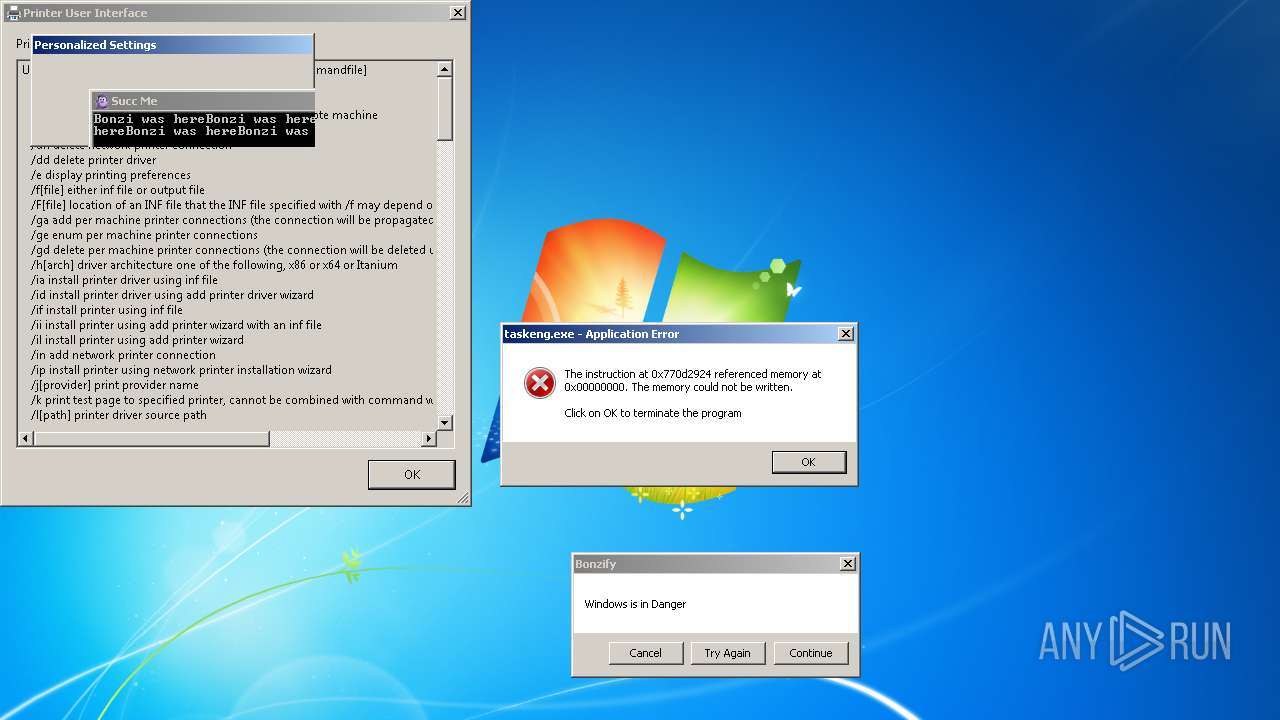
| File name: | Bonzify.exe |
| Full analysis: | https://app.any.run/tasks/44a16759-a656-4c70-883b-d032beb5cee9 |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2024, 15:40:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9C352D2CE0C0BDC40C72F52CE3480577 |
| SHA1: | BD4C956186F33C92EB4469F7E5675510D0790E99 |
| SHA256: | D7E6580054525D3F21F86EDFC9F30B7A75FFA829A1EB67EE3CAB33F0040DBA4E |
| SSDEEP: | 196608:/dAMaWetTeAkLIdx751qFTkub//73lc6u7b5VJ2Yx5xIdk3o:naWedh+Idx75QYub//73lc6u7bLMYxDo |
MALICIOUS
Drops the executable file immediately after the start
- Bonzify.exe (PID: 4064)
- INSTALLER.exe (PID: 1292)
- INSTALLER.exe (PID: 1664)
- CCleaner.exe (PID: 1408)
Registers / Runs the DLL via REGSVR32.EXE
- INSTALLER.exe (PID: 1292)
- INSTALLER.exe (PID: 1664)
Changes the autorun value in the registry
- INSTALLER.exe (PID: 1664)
- CCleaner.exe (PID: 1408)
- dllhost.exe (PID: 3376)
- IEExec.exe (PID: 2348)
- dw20.exe (PID: 2904)
- psxss.exe (PID: 4008)
- printui.exe (PID: 3132)
- wiaacmgr.exe (PID: 1884)
- conhost.exe (PID: 3380)
- PrintBrm.exe (PID: 1212)
- lpksetup.exe (PID: 3892)
- lpksetup.exe (PID: 5824)
- conhost.exe (PID: 3764)
Creates a writable file in the system directory
- INSTALLER.exe (PID: 1664)
- msdtc.exe (PID: 1296)
Changes the AppInit_DLLs value (autorun option)
- Bonzify.exe (PID: 4064)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 1408)
Steals credentials from Web Browsers
- CCleaner.exe (PID: 1408)
Changes appearance of the Explorer extensions
- wiaacmgr.exe (PID: 1884)
SUSPICIOUS
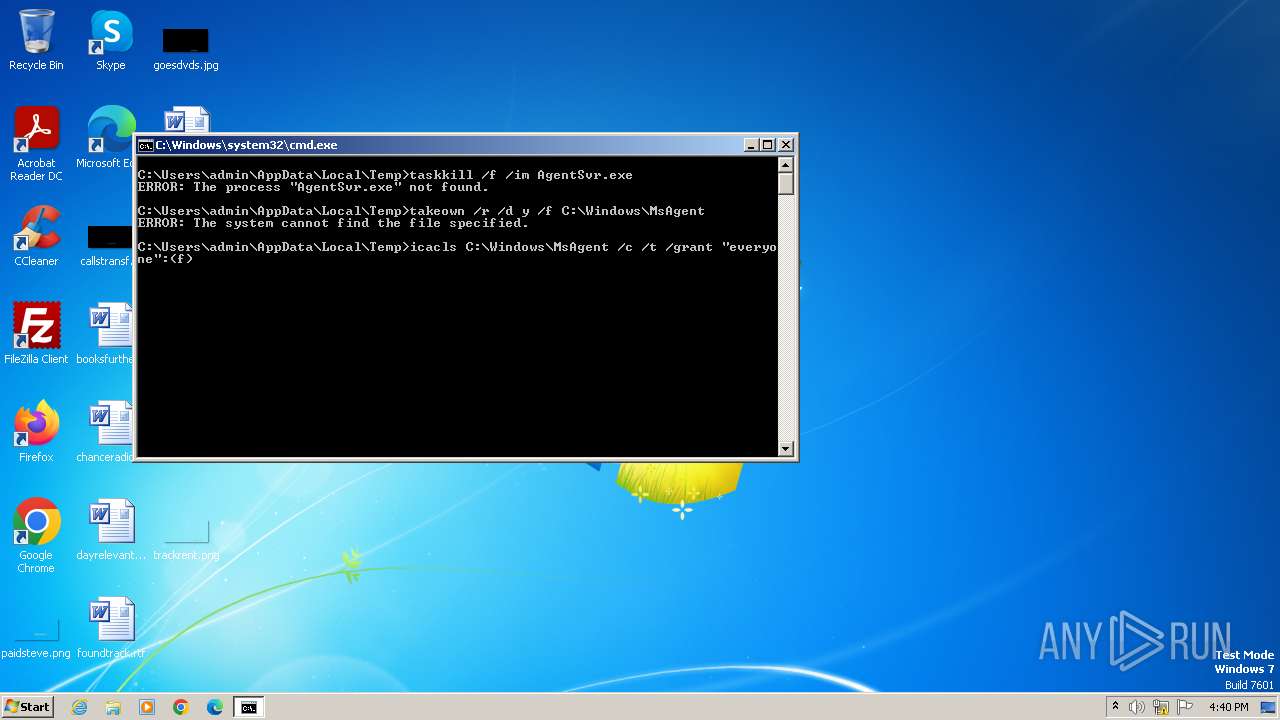
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 4084)
Executing commands from a ".bat" file
- Bonzify.exe (PID: 4064)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4084)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 4084)
Starts CMD.EXE for commands execution
- Bonzify.exe (PID: 4064)
Process drops legitimate windows executable
- Bonzify.exe (PID: 4064)
- INSTALLER.exe (PID: 1292)
- INSTALLER.exe (PID: 1664)
Starts a Microsoft application from unusual location
- INSTALLER.exe (PID: 1292)
- INSTALLER.exe (PID: 1664)
Executable content was dropped or overwritten
- Bonzify.exe (PID: 4064)
- INSTALLER.exe (PID: 1292)
- INSTALLER.exe (PID: 1664)
- CCleaner.exe (PID: 1408)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 1768)
- regsvr32.exe (PID: 2304)
- regsvr32.exe (PID: 1628)
- regsvr32.exe (PID: 660)
- regsvr32.exe (PID: 524)
- regsvr32.exe (PID: 1060)
- regsvr32.exe (PID: 1620)
- regsvr32.exe (PID: 304)
- regsvr32.exe (PID: 768)
- CCleaner.exe (PID: 1408)
- printui.exe (PID: 3132)
- wiaacmgr.exe (PID: 1884)
- dllhost.exe (PID: 3376)
- WinMail.exe (PID: 4024)
- LocationNotifications.exe (PID: 3708)
Creates a software uninstall entry
- INSTALLER.exe (PID: 1664)
- wiaacmgr.exe (PID: 1884)
Creates file in the systems drive root
- Bonzify.exe (PID: 4064)
- DFDWiz.exe (PID: 3528)
- gpscript.exe (PID: 2328)
- WMIADAP.exe (PID: 1980)
- powercfg.exe (PID: 1484)
- CCleaner.exe (PID: 3944)
- CCleaner.exe (PID: 1408)
- curl.exe (PID: 2284)
- wininit.exe (PID: 3368)
- CompatTelRunner.exe (PID: 3152)
- aspnet_state.exe (PID: 2976)
- conhost.exe (PID: 3532)
- ntvdm.exe (PID: 3796)
- CompatTelRunner.exe (PID: 3284)
- dllhost.exe (PID: 3376)
- ieUnatt.exe (PID: 3272)
- IEExec.exe (PID: 2348)
- wiaacmgr.exe (PID: 1884)
- dllhost.exe (PID: 1596)
- shrpubw.exe (PID: 1972)
- qprocess.exe (PID: 2204)
- xwizard.exe (PID: 2828)
- printui.exe (PID: 3132)
- ksetup.exe (PID: 2964)
- WsatConfig.exe (PID: 2844)
- dw20.exe (PID: 2904)
- psxss.exe (PID: 4008)
- OARPMANY.EXE (PID: 3436)
- WFS.exe (PID: 3912)
- timeout.exe (PID: 3520)
- ie4uinit.exe (PID: 1840)
- drvinst.exe (PID: 1020)
- msdt.exe (PID: 3332)
- mtstocom.exe (PID: 3508)
- Microsoft.Workflow.Compiler.exe (PID: 2340)
- msdtc.exe (PID: 1296)
- FXSUNATD.exe (PID: 1128)
- msg.exe (PID: 3596)
- makecab.exe (PID: 3532)
- runonce.exe (PID: 2512)
- conhost.exe (PID: 3380)
- alg.exe (PID: 1020)
- imjppdmg.exe (PID: 2480)
- wermgr.exe (PID: 1696)
- WinMail.exe (PID: 4024)
- PrintBrm.exe (PID: 1212)
- lpksetup.exe (PID: 3892)
- ntvdm.exe (PID: 1992)
- FreeCell.exe (PID: 992)
- WinMgmt.exe (PID: 3184)
- TSWbPrxy.exe (PID: 3652)
- ctfmon.exe (PID: 3724)
- SearchIndexer.exe (PID: 2808)
- lpksetup.exe (PID: 5824)
- LocationNotifications.exe (PID: 3708)
- iscsicpl.exe (PID: 4440)
- RMActivate.exe (PID: 5160)
- raserver.exe (PID: 4684)
- notepad.exe (PID: 5000)
- ODEPLOY.EXE (PID: 5040)
- SearchFilterHost.exe (PID: 5708)
- WsatConfig.exe (PID: 4092)
- mshta.exe (PID: 4340)
- WmiPrvSE.exe (PID: 2692)
- conhost.exe (PID: 3764)
- wextract.exe (PID: 1284)
- sbunattend.exe (PID: 6124)
- ddodiag.exe (PID: 6092)
- setupSNK.exe (PID: 2128)
- charmap.exe (PID: 6744)
The process executes via Task Scheduler
- CCleaner.exe (PID: 1408)
- aspnet_state.exe (PID: 2976)
- ntvdm.exe (PID: 3796)
- conhost.exe (PID: 3532)
- shrpubw.exe (PID: 1972)
- IEExec.exe (PID: 2348)
- ksetup.exe (PID: 2964)
- psxss.exe (PID: 4008)
Reads Internet Explorer settings
- CCleaner.exe (PID: 1408)
- WinMail.exe (PID: 4024)
Checks Windows Trust Settings
- CCleaner.exe (PID: 1408)
- WsatConfig.exe (PID: 2844)
- WsatConfig.exe (PID: 4092)
Reads security settings of Internet Explorer
- CCleaner.exe (PID: 1408)
- WsatConfig.exe (PID: 2844)
- WsatConfig.exe (PID: 4092)
Reads settings of System Certificates
- CCleaner.exe (PID: 1408)
- WsatConfig.exe (PID: 2844)
- WsatConfig.exe (PID: 4092)
- RMActivate.exe (PID: 5160)
Searches for installed software
- CCleaner.exe (PID: 1408)
Reads the date of Windows installation
- CCleaner.exe (PID: 1408)
Reads the Internet Settings
- CCleaner.exe (PID: 1408)
- ie4uinit.exe (PID: 1840)
Checks for external IP
- CCleaner.exe (PID: 1408)
Executed via WMI
- cvtres.exe (PID: 2800)
- ieUnatt.exe (PID: 3272)
- qprocess.exe (PID: 2204)
Changes internet zones settings
- CCleaner.exe (PID: 1408)
- dw20.exe (PID: 2904)
- printui.exe (PID: 3132)
- psxss.exe (PID: 4008)
- wiaacmgr.exe (PID: 1884)
- msdt.exe (PID: 3332)
- dllhost.exe (PID: 3376)
- Microsoft.Workflow.Compiler.exe (PID: 2340)
- WinMail.exe (PID: 4024)
- iscsicpl.exe (PID: 4440)
- WsatConfig.exe (PID: 4092)
- ddodiag.exe (PID: 6092)
- LocationNotifications.exe (PID: 3708)
- charmap.exe (PID: 6744)
Application launched itself
- CompatTelRunner.exe (PID: 3152)
Executes as Windows Service
- dllhost.exe (PID: 3376)
- msdtc.exe (PID: 1296)
Uses TIMEOUT.EXE to delay execution
- dllhost.exe (PID: 3376)
Changes default file association
- wiaacmgr.exe (PID: 1884)
Disables SEHOP
- wiaacmgr.exe (PID: 1884)
Adds/modifies Windows certificates
- wiaacmgr.exe (PID: 1884)
Changes Internet Explorer settings (feature browser emulation)
- lpksetup.exe (PID: 5824)
Start notepad (likely ransomware note)
- wiaacmgr.exe (PID: 1884)
Starts SC.EXE for service management
- TSWbPrxy.exe (PID: 3652)
Modifies the phishing filter of IE
- raserver.exe (PID: 4684)
Process changes security settings for the VBA macro
- lpksetup.exe (PID: 5824)
INFO
Checks supported languages
- Bonzify.exe (PID: 4064)
- INSTALLER.exe (PID: 1292)
- AgentSvr.exe (PID: 1652)
- INSTALLER.exe (PID: 1664)
- AgentSvr.exe (PID: 2060)
- wmpnscfg.exe (PID: 924)
- wmpnscfg.exe (PID: 972)
- DFDWiz.exe (PID: 3528)
- curl.exe (PID: 2284)
- WMIADAP.exe (PID: 1980)
- CCleaner.exe (PID: 3944)
- CCleaner.exe (PID: 1408)
- cvtres.exe (PID: 2800)
- aspnet_state.exe (PID: 2976)
- ieUnatt.exe (PID: 3272)
- conhost.exe (PID: 3532)
- wmpnscfg.exe (PID: 3200)
- wiaacmgr.exe (PID: 1884)
- shrpubw.exe (PID: 1972)
- dw20.exe (PID: 2904)
- IEExec.exe (PID: 2348)
- xwizard.exe (PID: 2828)
- printui.exe (PID: 3132)
- WsatConfig.exe (PID: 2844)
- psxss.exe (PID: 4008)
- WFS.exe (PID: 3912)
- OARPMANY.EXE (PID: 3436)
- drvinst.exe (PID: 1020)
- FXSUNATD.exe (PID: 1128)
- msdt.exe (PID: 3332)
- Microsoft.Workflow.Compiler.exe (PID: 2340)
- wermgr.exe (PID: 1696)
- runonce.exe (PID: 2512)
- conhost.exe (PID: 3380)
- imjppdmg.exe (PID: 2480)
- WinMail.exe (PID: 4024)
- lpksetup.exe (PID: 3892)
- FreeCell.exe (PID: 992)
- SearchIndexer.exe (PID: 2808)
- ctfmon.exe (PID: 3724)
- TSWbPrxy.exe (PID: 3652)
- wecutil.exe (PID: 4288)
- SvcIni.exe (PID: 4276)
- WsatConfig.exe (PID: 4092)
- ODEPLOY.EXE (PID: 5040)
- SearchFilterHost.exe (PID: 5708)
- auditpol.exe (PID: 4956)
- conhost.exe (PID: 3764)
- mshta.exe (PID: 4340)
Create files in a temporary directory
- Bonzify.exe (PID: 4064)
- INSTALLER.exe (PID: 1292)
- INSTALLER.exe (PID: 1664)
- msdt.exe (PID: 3332)
- ODEPLOY.EXE (PID: 5040)
Reads the computer name
- INSTALLER.exe (PID: 1292)
- INSTALLER.exe (PID: 1664)
- Bonzify.exe (PID: 4064)
- AgentSvr.exe (PID: 2060)
- wmpnscfg.exe (PID: 924)
- wmpnscfg.exe (PID: 972)
- DFDWiz.exe (PID: 3528)
- WMIADAP.exe (PID: 1980)
- CCleaner.exe (PID: 3944)
- CCleaner.exe (PID: 1408)
- aspnet_state.exe (PID: 2976)
- wmpnscfg.exe (PID: 3200)
- wiaacmgr.exe (PID: 1884)
- shrpubw.exe (PID: 1972)
- dw20.exe (PID: 2904)
- WsatConfig.exe (PID: 2844)
- msdt.exe (PID: 3332)
- Microsoft.Workflow.Compiler.exe (PID: 2340)
- lpksetup.exe (PID: 3892)
- TSWbPrxy.exe (PID: 3652)
- WinMail.exe (PID: 4024)
- wecutil.exe (PID: 4288)
- ctfmon.exe (PID: 3724)
- WsatConfig.exe (PID: 4092)
- auditpol.exe (PID: 4956)
Manual execution by a user
- wmpnscfg.exe (PID: 924)
- wmpnscfg.exe (PID: 972)
- DFDWiz.exe (PID: 3528)
- gpscript.exe (PID: 2328)
- WMIADAP.exe (PID: 1980)
- ntoskrnl.exe (PID: 3740)
- powercfg.exe (PID: 1484)
- CCleaner.exe (PID: 3944)
- curl.exe (PID: 2284)
- ntoskrnl.exe (PID: 2504)
- setupsqm.exe (PID: 2872)
- CompatTelRunner.exe (PID: 3152)
- wmpnscfg.exe (PID: 3200)
- snmptrap.exe (PID: 3972)
- wiaacmgr.exe (PID: 1884)
- ntoskrnl.exe (PID: 2544)
- ie4uinit.exe (PID: 1840)
- msg.exe (PID: 3596)
- iscsicli.exe (PID: 3812)
- ntoskrnl.exe (PID: 1772)
- WinMail.exe (PID: 4024)
- ntvdm.exe (PID: 1992)
- SearchIndexer.exe (PID: 2808)
- TSWbPrxy.exe (PID: 3652)
Reads the machine GUID from the registry
- AgentSvr.exe (PID: 2060)
- Bonzify.exe (PID: 4064)
- CCleaner.exe (PID: 3944)
- CCleaner.exe (PID: 1408)
- aspnet_state.exe (PID: 2976)
- conhost.exe (PID: 3532)
- wiaacmgr.exe (PID: 1884)
- IEExec.exe (PID: 2348)
- shrpubw.exe (PID: 1972)
- dw20.exe (PID: 2904)
- printui.exe (PID: 3132)
- WsatConfig.exe (PID: 2844)
- psxss.exe (PID: 4008)
- msdt.exe (PID: 3332)
- drvinst.exe (PID: 1020)
- Microsoft.Workflow.Compiler.exe (PID: 2340)
- runonce.exe (PID: 2512)
- conhost.exe (PID: 3380)
- FreeCell.exe (PID: 992)
- lpksetup.exe (PID: 3892)
- WMIADAP.exe (PID: 3824)
- ctfmon.exe (PID: 3724)
- TSWbPrxy.exe (PID: 3652)
- WinMail.exe (PID: 4024)
- WsatConfig.exe (PID: 4092)
- conhost.exe (PID: 3764)
Reads Environment values
- CCleaner.exe (PID: 3944)
- CCleaner.exe (PID: 1408)
Reads CPU info
- CCleaner.exe (PID: 1408)
- runonce.exe (PID: 2512)
Reads product name
- CCleaner.exe (PID: 1408)
Creates files in the program directory
- CCleaner.exe (PID: 1408)
- dw20.exe (PID: 2904)
Reads the software policy settings
- CCleaner.exe (PID: 1408)
- WsatConfig.exe (PID: 2844)
- RMActivate.exe (PID: 5160)
- WsatConfig.exe (PID: 4092)
Checks proxy server information
- CCleaner.exe (PID: 1408)
Checks transactions between databases Windows and Oracle
- dllhost.exe (PID: 3376)
- msdtc.exe (PID: 1296)
- lpksetup.exe (PID: 3892)
Process checks whether UAC notifications are on
- psxss.exe (PID: 4008)
Reads the time zone
- runonce.exe (PID: 2512)
Creates files or folders in the user directory
- WinMail.exe (PID: 4024)
Reads security settings of Internet Explorer
- RMActivate.exe (PID: 5160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 MS Cabinet Self-Extractor (WExtract stub) (86.7) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (8.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.8) |
| .exe | | | Win32 Executable (generic) (1.2) |
| .exe | | | Generic Win/DOS Executable (0.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:03:04 14:58:11+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 4096 |
| InitializedDataSize: | 6697472 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16b0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
504
Monitored processes
127
Malicious processes
21
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | regsvr32 /s "C:\Windows\msagent\AgentDP2.dll" | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 524 | regsvr32 /s "C:\Windows\msagent\AgentSR.dll" | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 660 | regsvr32 /s "C:\Windows\msagent\AgentMPx.dll" | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 768 | regsvr32 /s C:\Windows\lhsp\tv\tvenuax.dll | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 960 | "C:\Windows\System32\SystemPropertiesHardware.exe" | C:\Windows\System32\SystemPropertiesHardware.exe | — | wiaacmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Hardware Settings Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 972 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | "C:\Windows\winsxs\x86_microsoft-windows-s..inboxgames-freecell_31bf3856ad364e35_6.1.7600.16385_none_58481bbdfe2e6164\FreeCell.exe" | C:\Windows\winsxs\x86_microsoft-windows-s..inboxgames-freecell_31bf3856ad364e35_6.1.7600.16385_none_58481bbdfe2e6164\FreeCell.exe | — | wiaacmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Executable for FreeCell Game Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1020 | taskkill /f /im AgentSvr.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1020 | "C:\Windows\winsxs\x86_microsoft-windows-coreusermodepnp_31bf3856ad364e35_6.1.7601.21733_none_797c13b0a45ccd8c\drvinst.exe" | C:\Windows\winsxs\x86_microsoft-windows-coreusermodepnp_31bf3856ad364e35_6.1.7601.21733_none_797c13b0a45ccd8c\drvinst.exe | — | printui.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Installation Module Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
36 356
Read events
33 099
Write events
3 219
Delete events
38
Modification events
| (PID) Process: | (1292) INSTALLER.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.app.log |
Value: 4096 | |||
| (PID) Process: | (2304) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (2304) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F5BE8BD2-7DE6-11D0-91FE-00C04FD701A5}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (2304) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\Control |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2304) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\InprocServer32 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2304) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\MiscStatus\1 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2304) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\MiscStatus |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2304) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\ProgID |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2304) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\Programmable |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2304) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\ToolboxBitmap32 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
55
Suspicious files
23
Text files
11
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4064 | Bonzify.exe | C:\Users\admin\AppData\Local\Temp\INSTALLER.exe | executable | |
MD5:66996A076065EBDCDAC85FF9637CEAE0 | SHA256:16CA09AD70561F413376AD72550AE5664C89C6A76C85C872FFE2CB1E7F49E2AA | |||
| 1292 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTDP2.DLL | executable | |
MD5:A334BBF5F5A19B3BDB5B7F1703363981 | SHA256:C33BEABA130F8B740DDDB9980FE9012F9322AC6E94F36A6AA6086851C51B98DE | |||
| 1292 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\MSLWVTTS.DLL | executable | |
MD5:316999655FEF30C52C3854751C663996 | SHA256:EA4CA740CD60D2C88280FF8115BF354876478EF27E9E676D8B66601B4E900BA0 | |||
| 1292 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTCTL.DLL | executable | |
MD5:237E13B95AB37D0141CF0BC585B8DB94 | SHA256:D19B6B7C57BCEE7239526339E683F62D9C2F9690947D0A446001377F0B56103A | |||
| 4064 | Bonzify.exe | C:\Users\admin\AppData\Local\Temp\KillAgent.bat | text | |
MD5:EA7DF060B402326B4305241F21F39736 | SHA256:E4EDC2CB6317AB19EE1A6327993E9332AF35CFBEBAFF2AC7C3F71D43CFCBE793 | |||
| 4064 | Bonzify.exe | C:\Windows\executables.bin | binary | |
MD5:F3160BA7F8BB9D7A9C6080EF2C9869C5 | SHA256:F6A3286714A661612EAC65E4A6CB78736C370492151B692A8F1E666740C0A00E | |||
| 1292 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTMPX.DLL | executable | |
MD5:4FBBAAC42CF2ECB83543F262973D07C0 | SHA256:6550582E41FC53B8A7CCDF9AC603216937C6FF2A28E9538610ADB7E67D782AB5 | |||
| 1292 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGT0409.HLP | hlp | |
MD5:466D35E6A22924DD846A043BC7DD94B8 | SHA256:E4CCF06706E68621BB69ADD3DD88FED82D30AD8778A55907D33F6D093AC16801 | |||
| 1292 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTPSH.DLL | executable | |
MD5:B4AC608EBF5A8FDEFA2D635E83B7C0E8 | SHA256:8414DFE399813B7426C235BA1E625BD2B5635C8140DA0D0CFC947F6565FE415F | |||
| 1292 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTANM.DLL | executable | |
MD5:48C00A7493B28139CBF197CCC8D1F9ED | SHA256:905CB1A15ECCAA9B79926EE7CFE3629A6F1C6B24BDD6CEA9CCB9EBC9EAA92FF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
15
DNS requests
11
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1408 | CCleaner.exe | GET | 200 | 23.219.78.200:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | unknown |
1408 | CCleaner.exe | GET | 304 | 23.219.78.213:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d1ba94d7dfb08484 | unknown | — | — | unknown |
1408 | CCleaner.exe | GET | 304 | 23.219.78.213:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0790c116bb36ff43 | unknown | — | — | unknown |
1408 | CCleaner.exe | GET | 304 | 23.219.78.213:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d168d2dda013a763 | unknown | — | — | unknown |
1408 | CCleaner.exe | GET | 304 | 23.219.78.213:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?be239ad867a0275f | unknown | — | — | unknown |
2748 | SETUP.EXE | GET | 200 | 23.219.78.201:80 | http://crl.microsoft.com/pki/crl/products/CSPCA.crl | unknown | — | — | unknown |
284 | RMActivate.exe | GET | 200 | 23.219.78.201:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | unknown |
728 | RMActivate_isv.exe | GET | 200 | 184.25.228.216:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1408 | CCleaner.exe | 23.219.78.200:80 | ncc.avast.com | CLARO S.A. | BR | unknown |
1408 | CCleaner.exe | 34.117.223.223:443 | analytics.ff.avast.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
1408 | CCleaner.exe | 34.149.149.62:443 | ip-info.ff.avast.com | GOOGLE | US | unknown |
1408 | CCleaner.exe | 34.160.176.28:443 | shepherd.ff.avast.com | GOOGLE | US | unknown |
1408 | CCleaner.exe | 34.111.24.1:443 | ipm-provider.ff.avast.com | GOOGLE | US | unknown |
1408 | CCleaner.exe | 184.25.211.189:443 | www.ccleaner.com | Akamai International B.V. | US | unknown |
1408 | CCleaner.exe | 23.219.78.213:80 | ctldl.windowsupdate.com | CLARO S.A. | BR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ncc.avast.com |
| whitelisted |
analytics.ff.avast.com |
| whitelisted |
ip-info.ff.avast.com |
| whitelisted |
shepherd.ff.avast.com |
| whitelisted |
ipm-provider.ff.avast.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
1408 | CCleaner.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | ClaimOutput
|