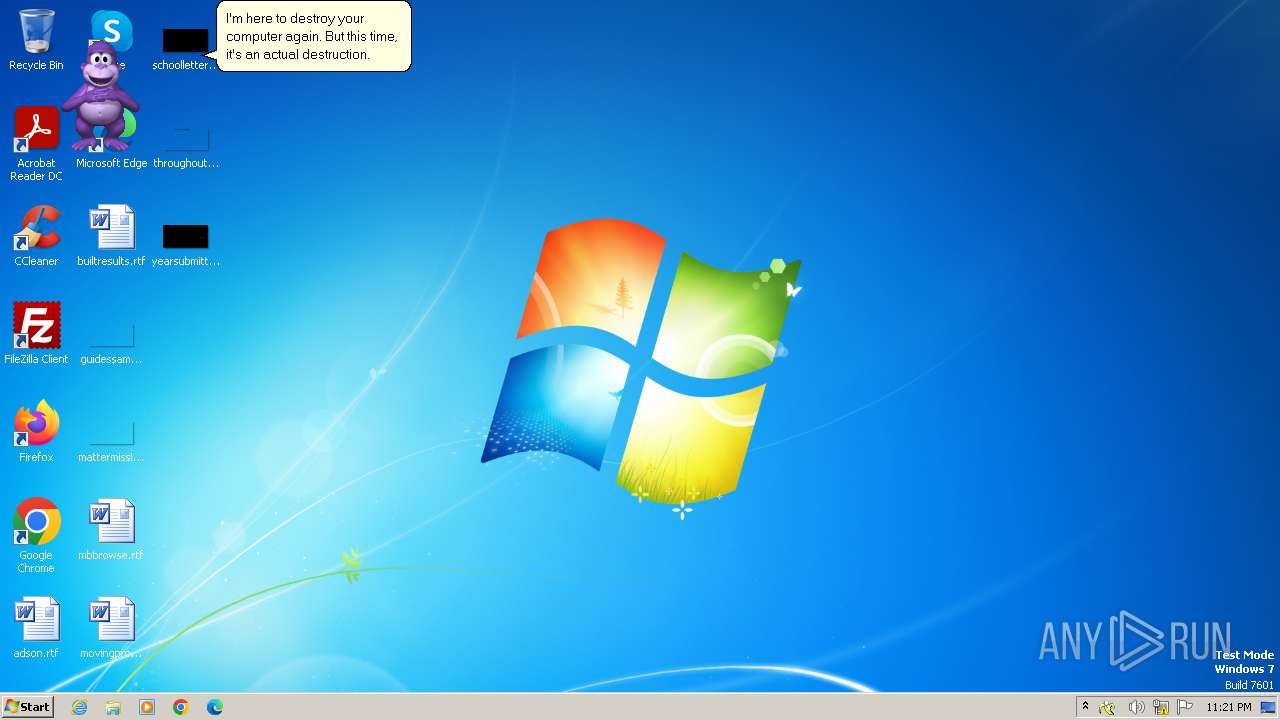
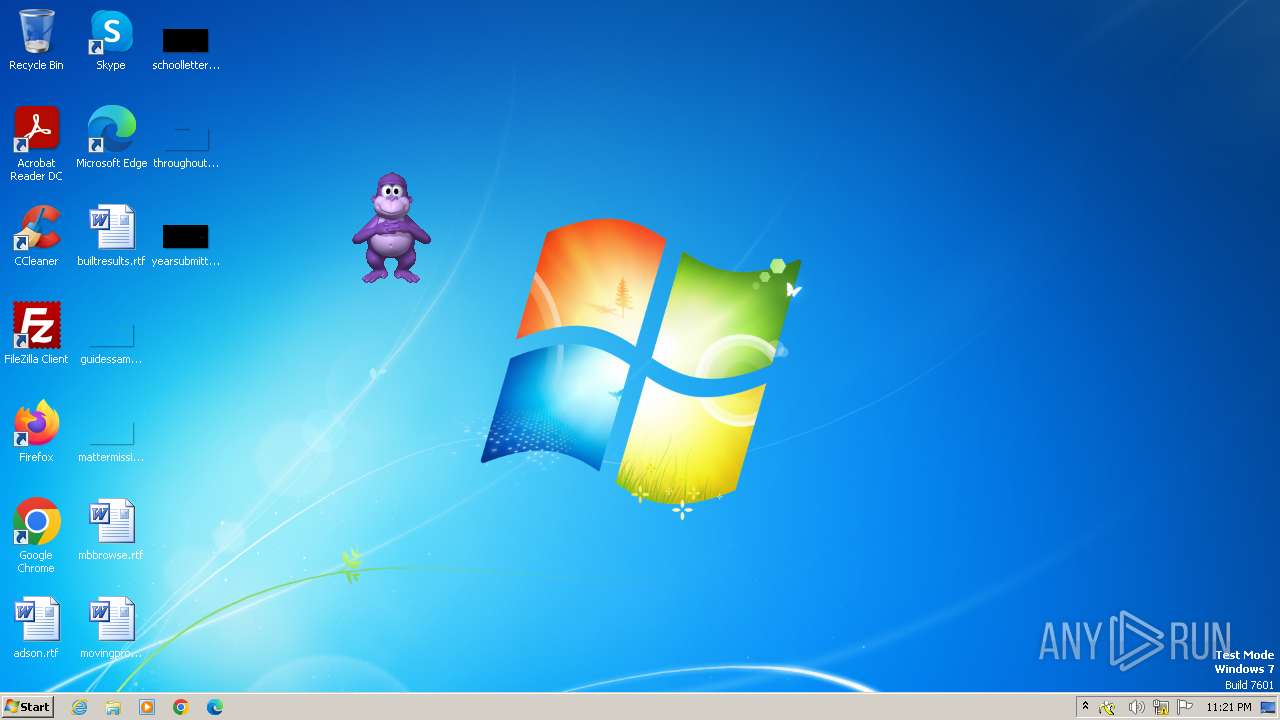
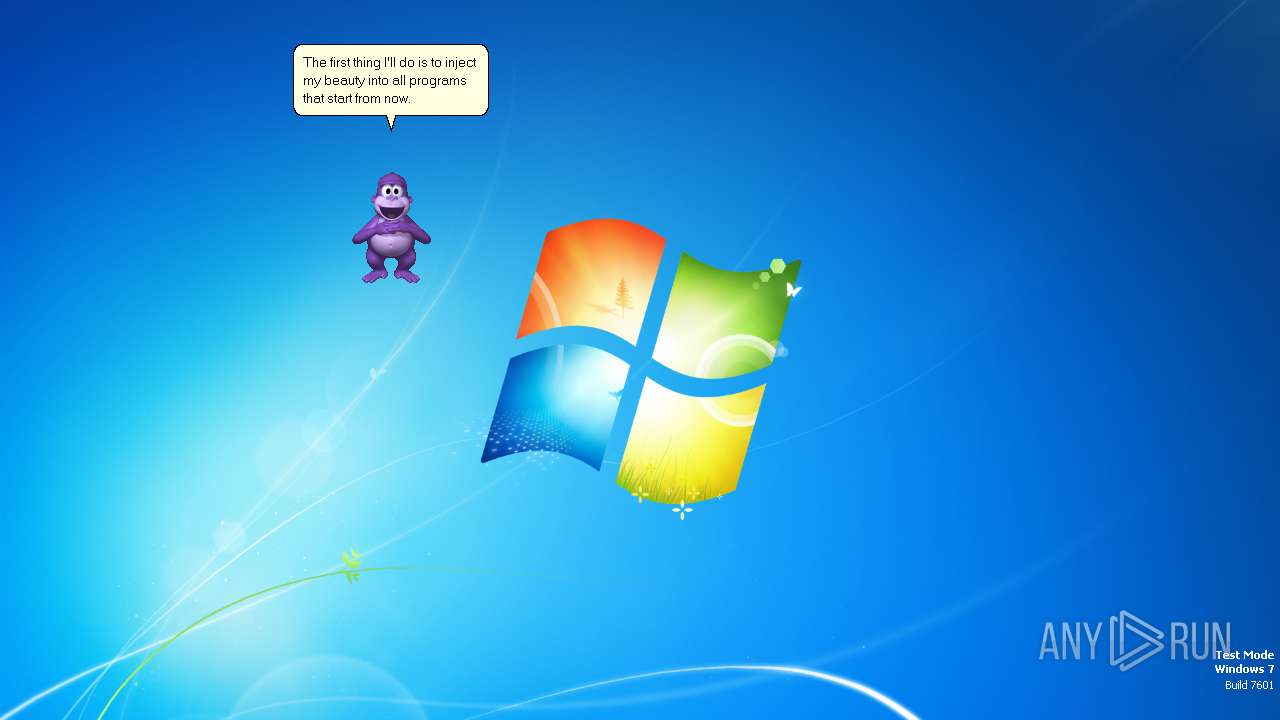
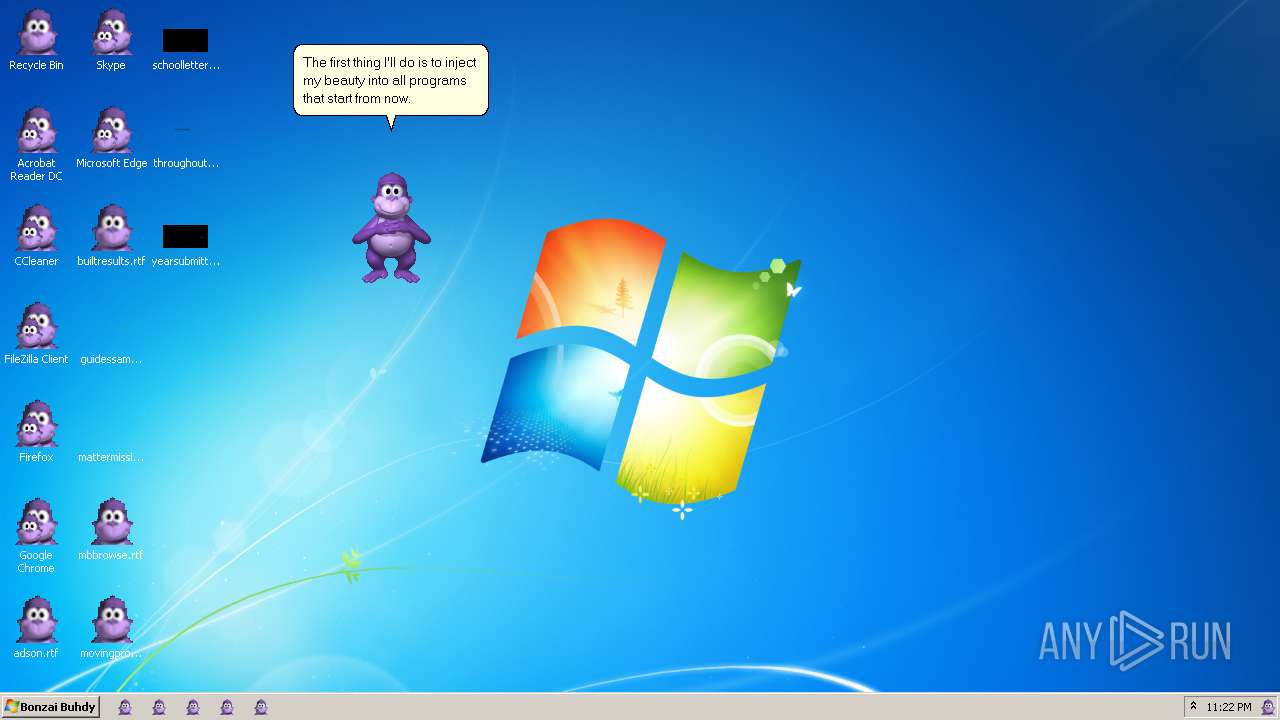
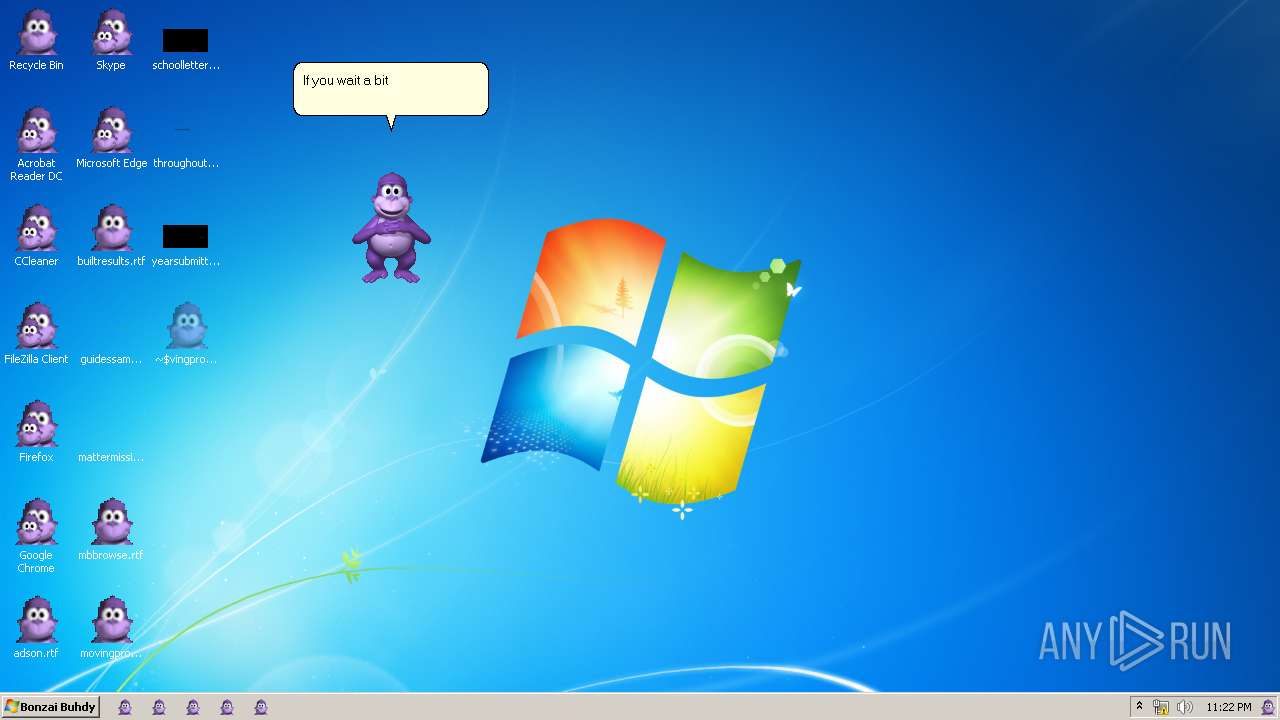
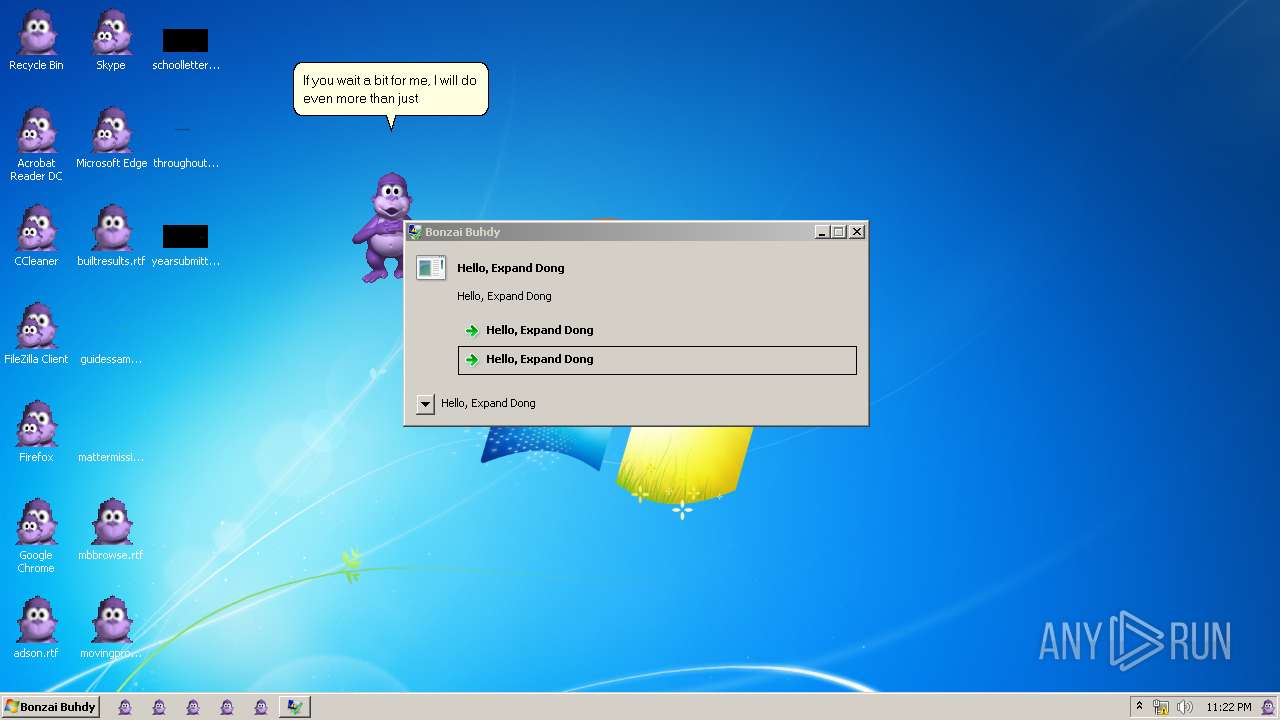
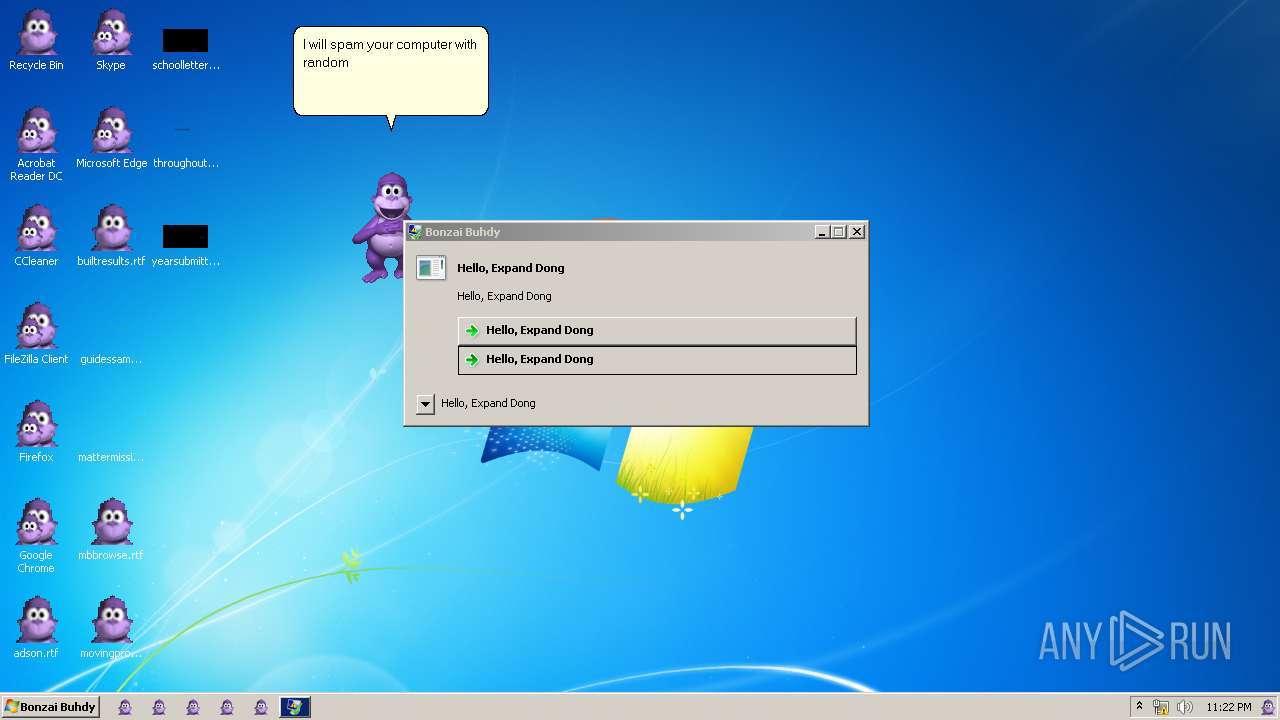
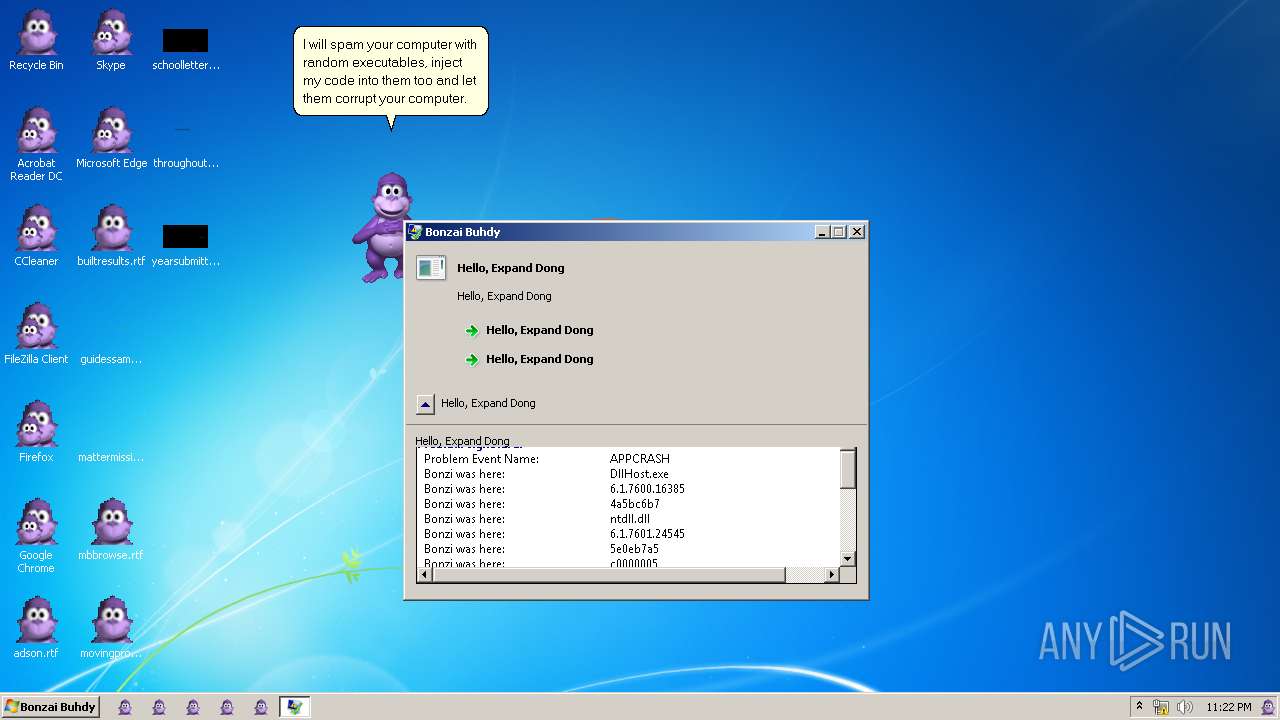
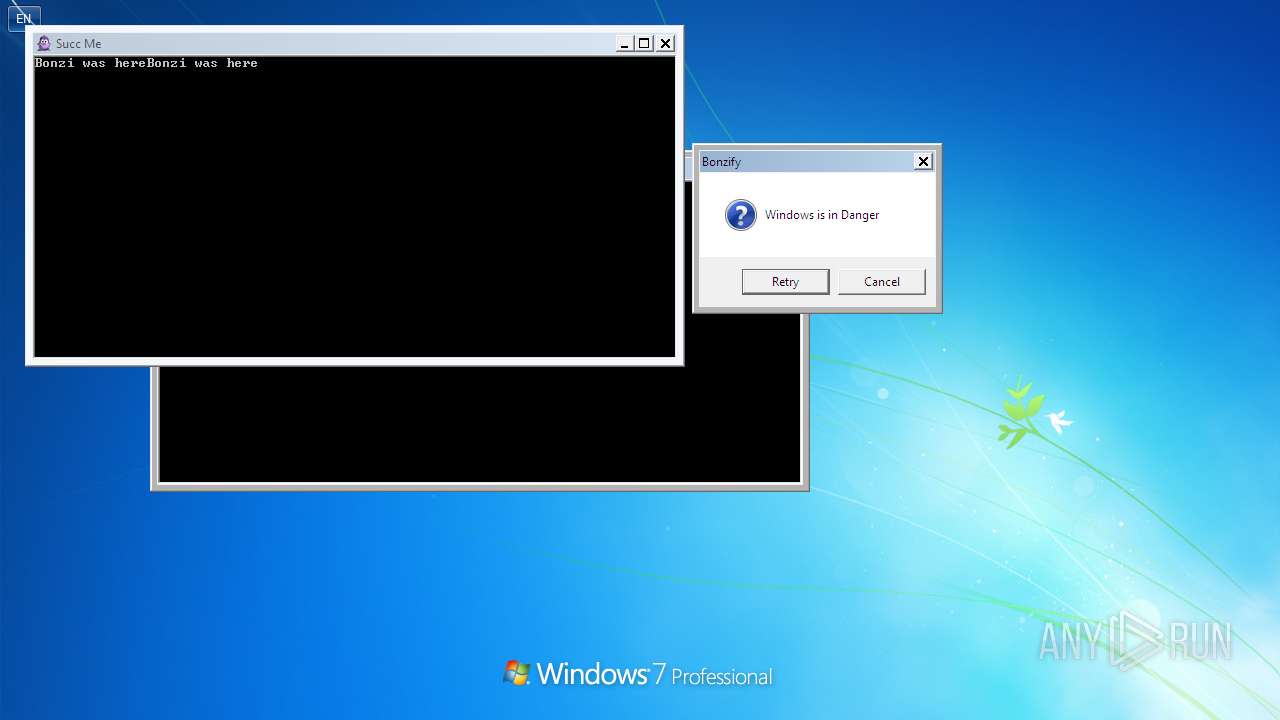
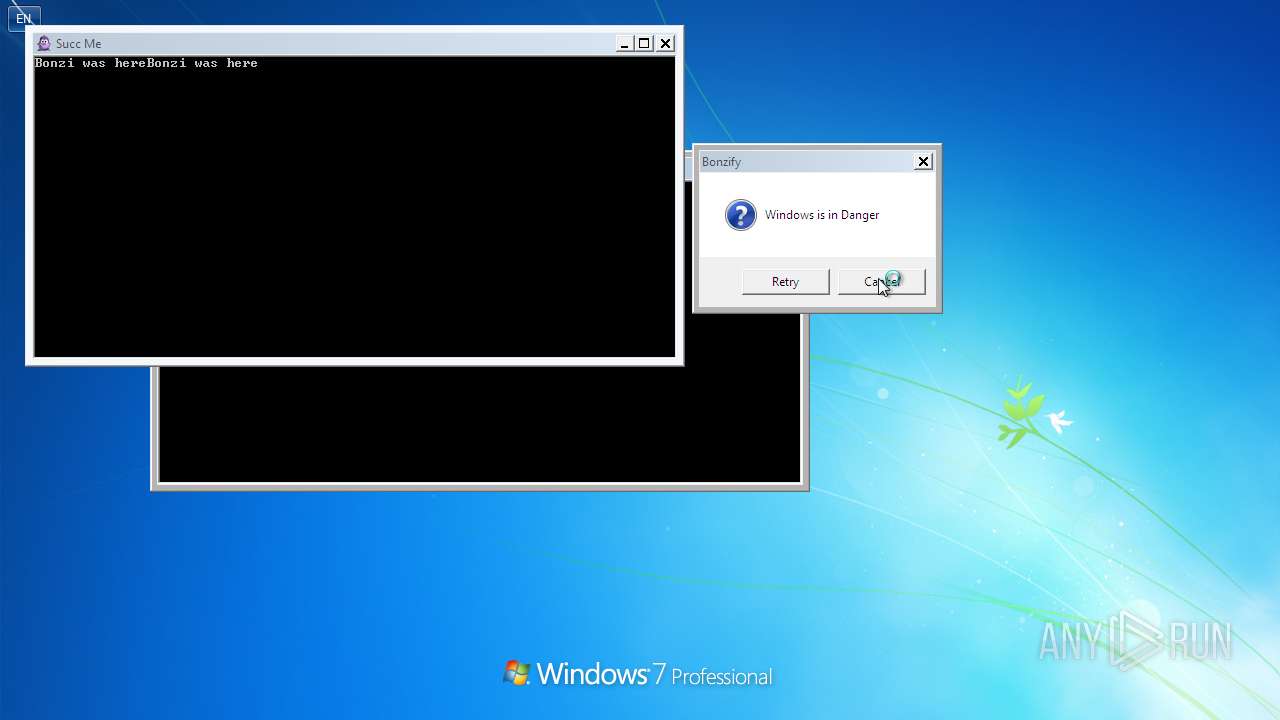
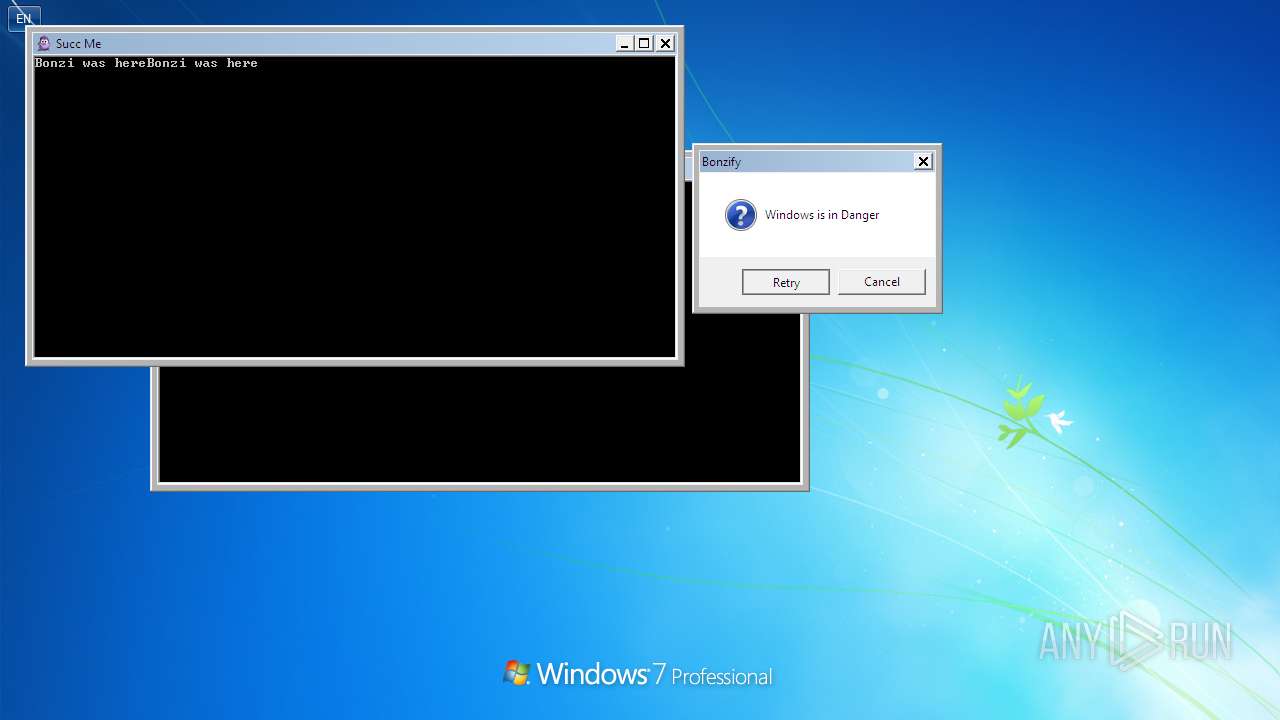
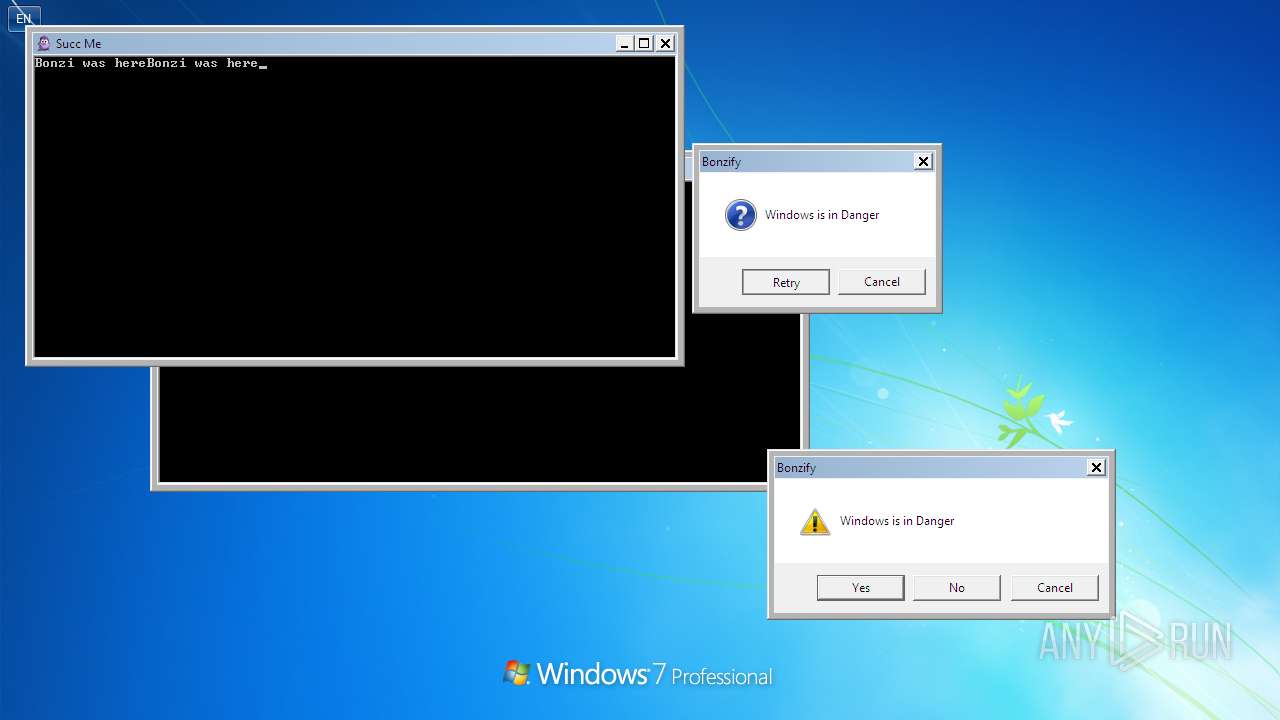
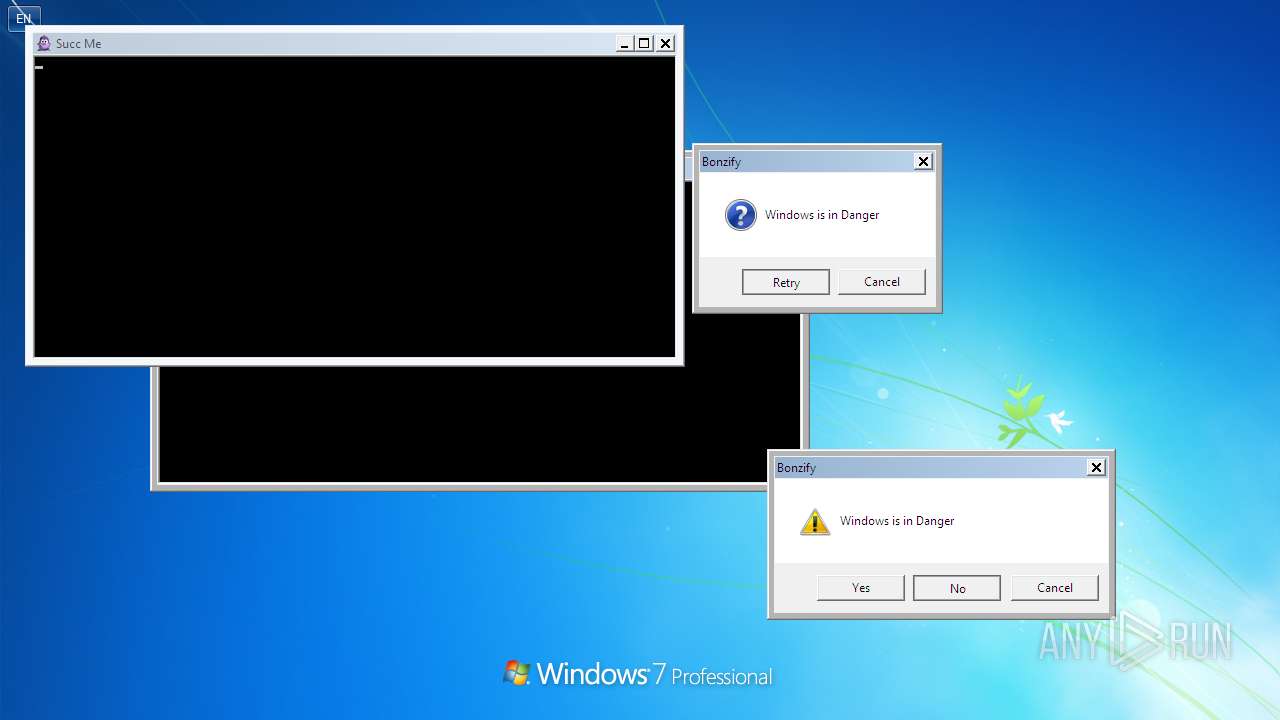
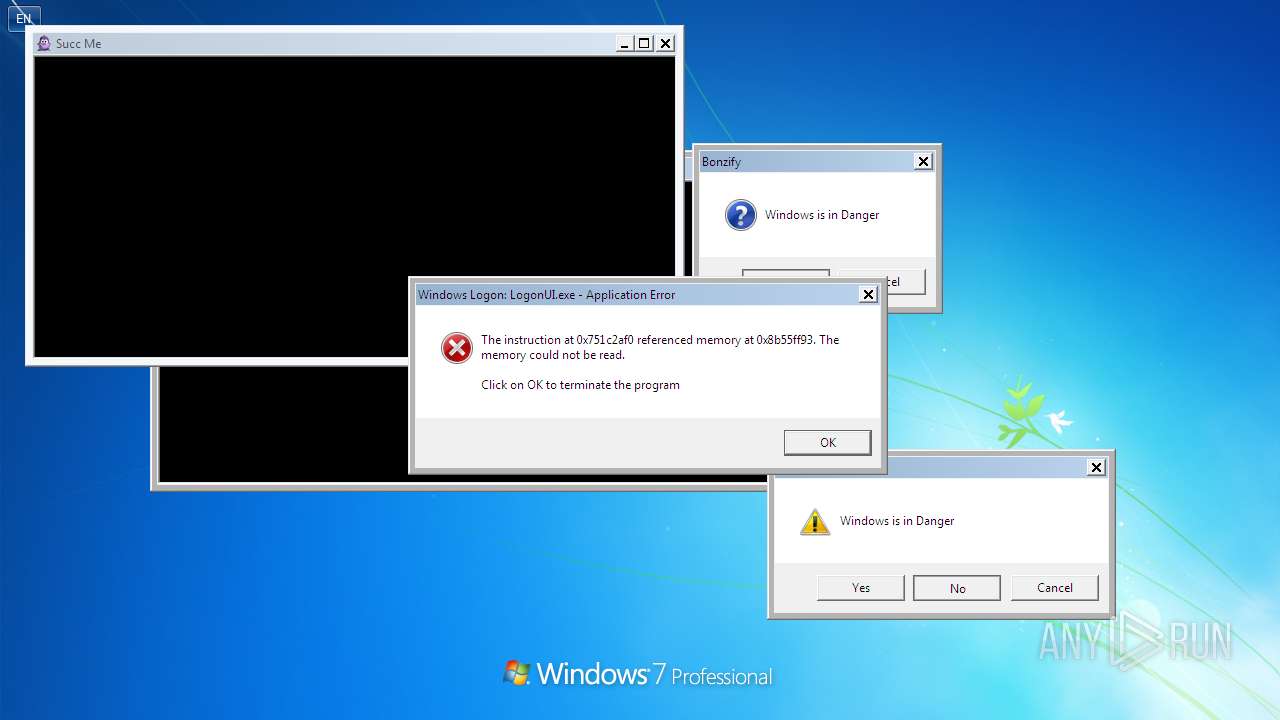
| File name: | Bonzify.exe |
| Full analysis: | https://app.any.run/tasks/3887ee86-94f2-4a29-9818-8e38247b94be |
| Verdict: | Malicious activity |
| Analysis date: | June 15, 2024, 22:21:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9C352D2CE0C0BDC40C72F52CE3480577 |
| SHA1: | BD4C956186F33C92EB4469F7E5675510D0790E99 |
| SHA256: | D7E6580054525D3F21F86EDFC9F30B7A75FFA829A1EB67EE3CAB33F0040DBA4E |
| SSDEEP: | 196608:/dAMaWetTeAkLIdx751qFTkub//73lc6u7b5VJ2Yx5xIdk3o:naWedh+Idx75QYub//73lc6u7bLMYxDo |
MALICIOUS
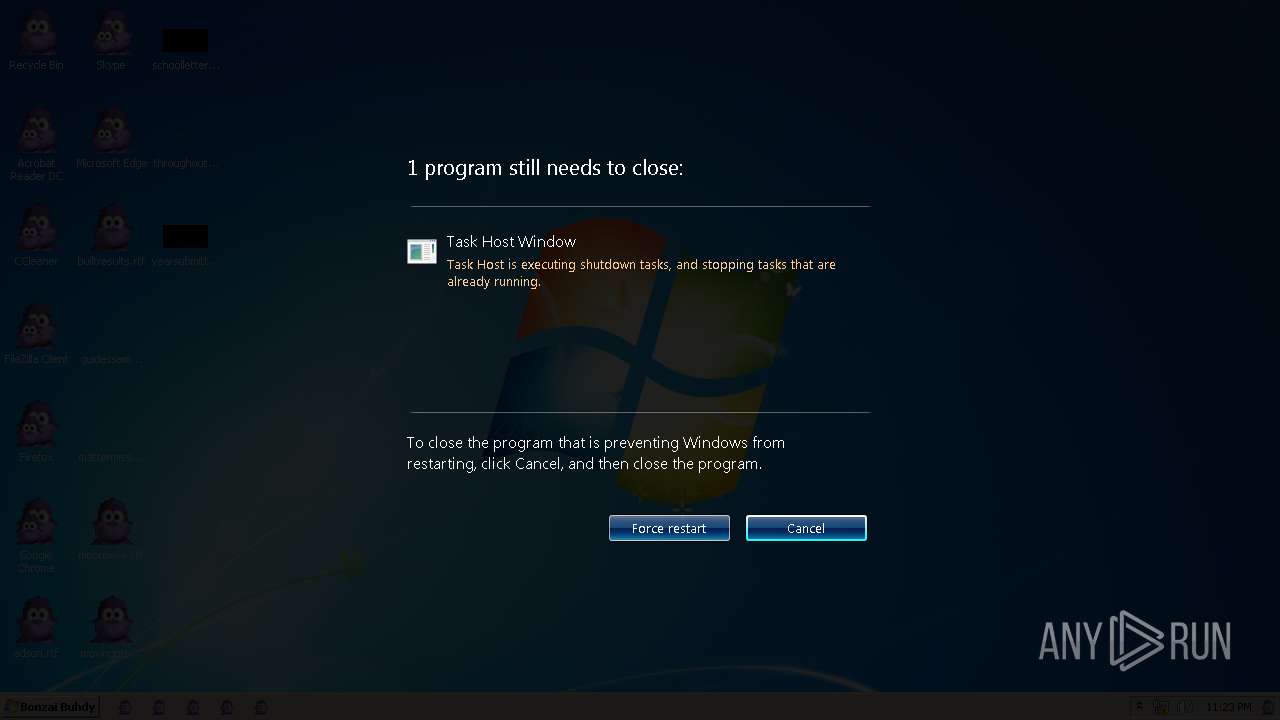
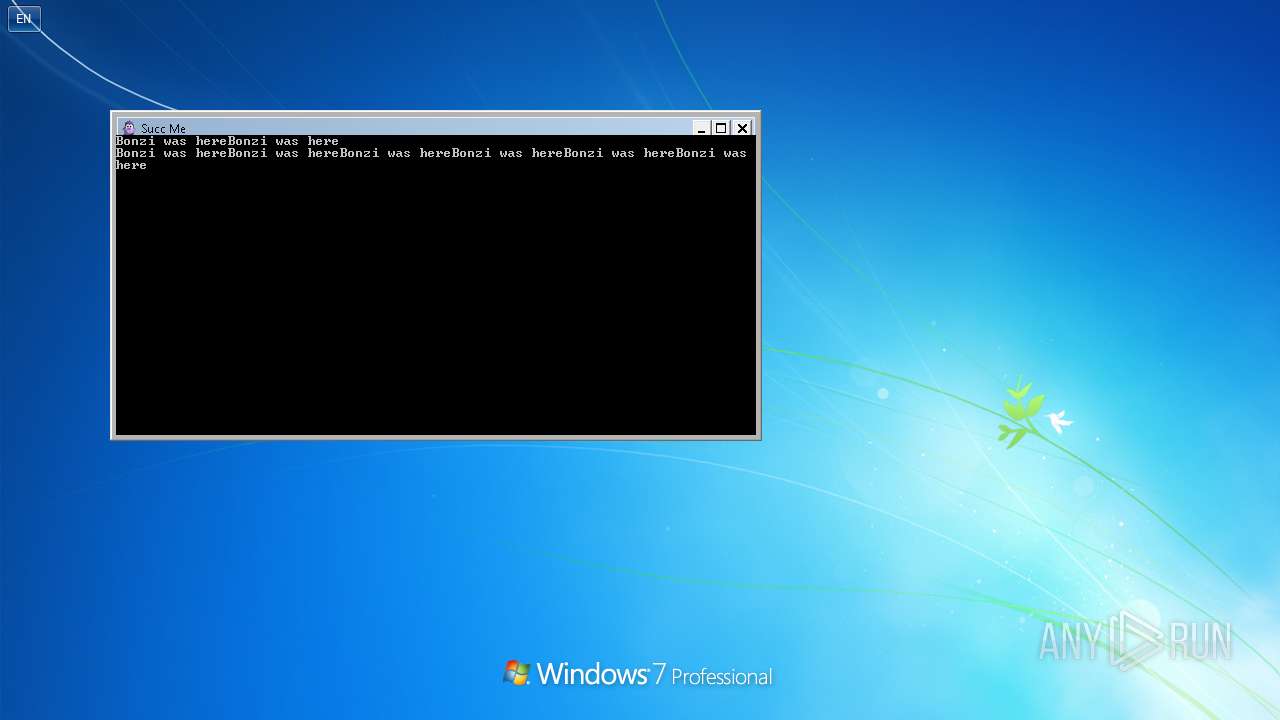
Drops the executable file immediately after the start
- Bonzify.exe (PID: 4088)
- INSTALLER.exe (PID: 2304)
- INSTALLER.exe (PID: 1620)
Registers / Runs the DLL via REGSVR32.EXE
- INSTALLER.exe (PID: 2304)
- INSTALLER.exe (PID: 1620)
Creates a writable file in the system directory
- INSTALLER.exe (PID: 1620)
Changes the autorun value in the registry
- INSTALLER.exe (PID: 1620)
Changes the AppInit_DLLs value (autorun option)
- Bonzify.exe (PID: 4088)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Bonzify.exe (PID: 4088)
Executable content was dropped or overwritten
- Bonzify.exe (PID: 4088)
- INSTALLER.exe (PID: 2304)
- INSTALLER.exe (PID: 1620)
Process drops legitimate windows executable
- INSTALLER.exe (PID: 2304)
- INSTALLER.exe (PID: 1620)
- Bonzify.exe (PID: 4088)
Executing commands from a ".bat" file
- Bonzify.exe (PID: 4088)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 308)
- regsvr32.exe (PID: 552)
- regsvr32.exe (PID: 1056)
- regsvr32.exe (PID: 728)
- regsvr32.exe (PID: 1488)
- regsvr32.exe (PID: 1840)
- regsvr32.exe (PID: 1764)
- regsvr32.exe (PID: 284)
- regsvr32.exe (PID: 1284)
Starts a Microsoft application from unusual location
- INSTALLER.exe (PID: 1620)
- INSTALLER.exe (PID: 2304)
Creates a software uninstall entry
- INSTALLER.exe (PID: 1620)
Creates file in the systems drive root
- Bonzify.exe (PID: 4088)
- WINWORD.EXE (PID: 1280)
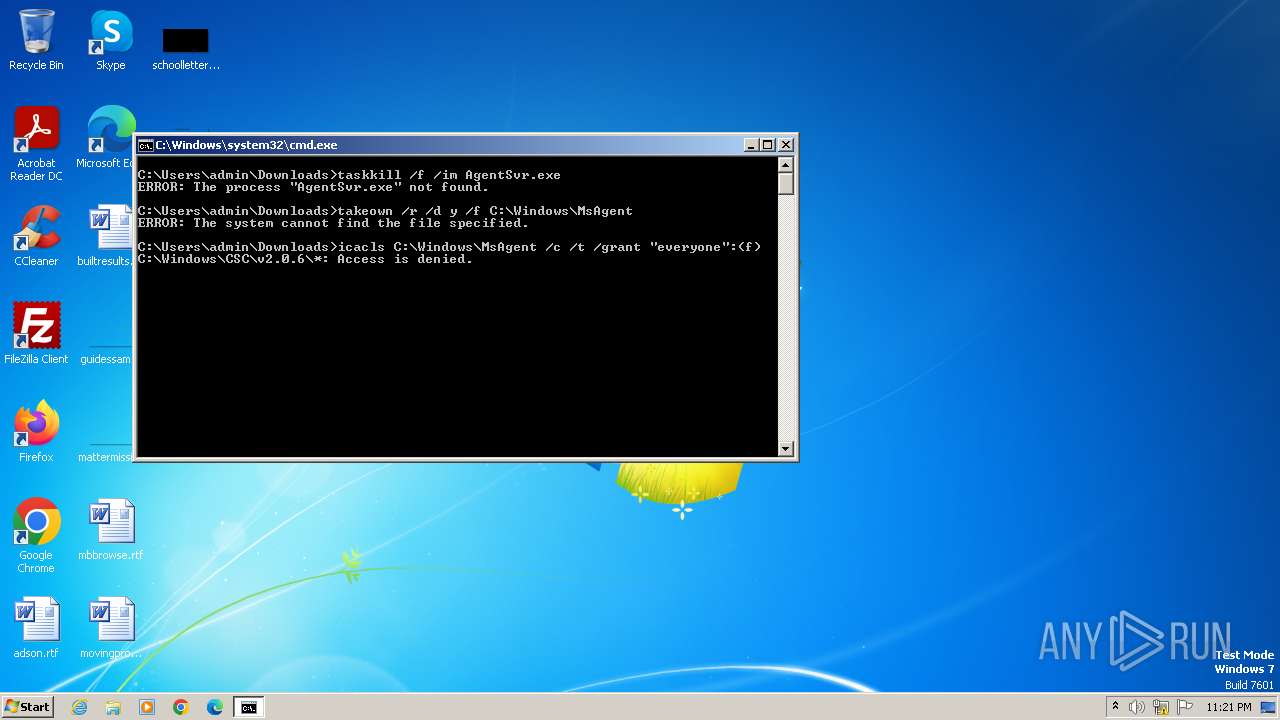
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 1020)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1020)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1020)
INFO
Create files in a temporary directory
- Bonzify.exe (PID: 4088)
- INSTALLER.exe (PID: 2304)
- INSTALLER.exe (PID: 1620)
Checks supported languages
- INSTALLER.exe (PID: 2304)
- AgentSvr.exe (PID: 588)
- INSTALLER.exe (PID: 1620)
- AgentSvr.exe (PID: 1948)
- wmpnscfg.exe (PID: 2792)
- wmpnscfg.exe (PID: 2940)
- wmpnscfg.exe (PID: 1840)
- wmpnscfg.exe (PID: 692)
- Bonzify.exe (PID: 4088)
Reads the computer name
- INSTALLER.exe (PID: 2304)
- INSTALLER.exe (PID: 1620)
- Bonzify.exe (PID: 4088)
- AgentSvr.exe (PID: 1948)
- wmpnscfg.exe (PID: 2792)
- wmpnscfg.exe (PID: 2940)
- wmpnscfg.exe (PID: 1840)
- wmpnscfg.exe (PID: 692)
Reads the machine GUID from the registry
- Bonzify.exe (PID: 4088)
- AgentSvr.exe (PID: 1948)
Manual execution by a user
- WINWORD.EXE (PID: 1280)
- wmpnscfg.exe (PID: 2792)
- wmpnscfg.exe (PID: 2940)
- wmpnscfg.exe (PID: 1840)
- wmpnscfg.exe (PID: 692)
- DFDWiz.exe (PID: 2284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 MS Cabinet Self-Extractor (WExtract stub) (86.7) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (8.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.8) |
| .exe | | | Win32 Executable (generic) (1.2) |
| .exe | | | Generic Win/DOS Executable (0.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:03:04 14:58:11+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 4096 |
| InitializedDataSize: | 6697472 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16b0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
132
Monitored processes
27
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | regsvr32 /s C:\Windows\lhsp\tv\tv_enua.dll | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 308 | regsvr32 /s "C:\Windows\msagent\AgentDPv.dll" | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | regsvr32 /s "C:\Windows\msagent\mslwvtts.dll" | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 588 | "C:\Windows\msagent\AgentSvr.exe" /regserver | C:\Windows\msagent\AgentSvr.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Agent Server Exit code: 0 Version: 2.00.0.2202 Modules
| |||||||||||||||
| 692 | grpconv.exe -o | C:\Windows\System32\grpconv.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 692 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 728 | regsvr32 /s "C:\Windows\msagent\AgentDP2.dll" | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 864 | taskkill /f /im AgentSvr.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1020 | C:\Windows\system32\cmd.exe /c "C:\Users\admin\AppData\Local\Temp\KillAgent.bat" | C:\Windows\System32\cmd.exe | — | Bonzify.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1056 | regsvr32 /s "C:\Windows\msagent\AgentMPx.dll" | C:\Windows\System32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
7 031
Read events
6 471
Write events
230
Delete events
330
Modification events
| (PID) Process: | (2304) INSTALLER.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.app.log |
Value: 4096 | |||
| (PID) Process: | (1764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (1764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F5BE8BD2-7DE6-11D0-91FE-00C04FD701A5}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (1764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\Control |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\InprocServer32 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\MiscStatus\1 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\MiscStatus |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\ProgID |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\Programmable |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\ToolboxBitmap32 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
54
Suspicious files
19
Text files
5
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4088 | Bonzify.exe | C:\Users\admin\AppData\Local\Temp\INSTALLER.exe | executable | |
MD5:66996A076065EBDCDAC85FF9637CEAE0 | SHA256:16CA09AD70561F413376AD72550AE5664C89C6A76C85C872FFE2CB1E7F49E2AA | |||
| 4088 | Bonzify.exe | C:\Users\admin\AppData\Local\Temp\TakeOwn.bat | text | |
MD5:F80E36CD406022944558D8A099DB0FA7 | SHA256:7B41E5A6C2DD92F60C38CB4FE09DCBE378C3E99443F7BAF079ECE3608497BDC7 | |||
| 2304 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTDPV.DLL | executable | |
MD5:7C5AEFB11E797129C9E90F279FBDF71B | SHA256:394A17150B8774E507B8F368C2C248C10FCE50FC43184B744E771F0E79ECAFED | |||
| 2304 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTCTL.DLL | executable | |
MD5:237E13B95AB37D0141CF0BC585B8DB94 | SHA256:D19B6B7C57BCEE7239526339E683F62D9C2F9690947D0A446001377F0B56103A | |||
| 4088 | Bonzify.exe | C:\Windows\executables.bin | binary | |
MD5:F3160BA7F8BB9D7A9C6080EF2C9869C5 | SHA256:F6A3286714A661612EAC65E4A6CB78736C370492151B692A8F1E666740C0A00E | |||
| 2304 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTSR.DLL | executable | |
MD5:9FAFB9D0591F2BE4C2A846F63D82D301 | SHA256:E78E74C24D468284639FAF9DCFDBA855F3E4F00B2F26DB6B2C491FA51DA8916D | |||
| 2304 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTANM.DLL | executable | |
MD5:48C00A7493B28139CBF197CCC8D1F9ED | SHA256:905CB1A15ECCAA9B79926EE7CFE3629A6F1C6B24BDD6CEA9CCB9EBC9EAA92FF7 | |||
| 2304 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTDP2.DLL | executable | |
MD5:A334BBF5F5A19B3BDB5B7F1703363981 | SHA256:C33BEABA130F8B740DDDB9980FE9012F9322AC6E94F36A6AA6086851C51B98DE | |||
| 2304 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\MSLWVTTS.DLL | executable | |
MD5:316999655FEF30C52C3854751C663996 | SHA256:EA4CA740CD60D2C88280FF8115BF354876478EF27E9E676D8B66601B4E900BA0 | |||
| 2304 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AGENTPSH.DLL | executable | |
MD5:B4AC608EBF5A8FDEFA2D635E83B7C0E8 | SHA256:8414DFE399813B7426C235BA1E625BD2B5635C8140DA0D0CFC947F6565FE415F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|