| File name: | Click me.exe |
| Full analysis: | https://app.any.run/tasks/f012379f-8410-4f2d-afcf-4c3dd4453733 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2024, 02:42:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 9852EA91FB255FDD3B05EB4AB2D626D8 |
| SHA1: | 9DC754FEB7E5F3049CD548563D592E0CE0AF78A9 |
| SHA256: | D7D55F6CBD54DC9659A243072E680364A237E150E140E80D302116AE3DCAD92F |
| SSDEEP: | 12288:20mRS9Z656af2azEW2gotg9tIpmMYnhg7iywRn:20m8sDf2azEW2goi9tIpmMYny7iZ |
MALICIOUS
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 7028)
- cmd.exe (PID: 4716)
SUSPICIOUS
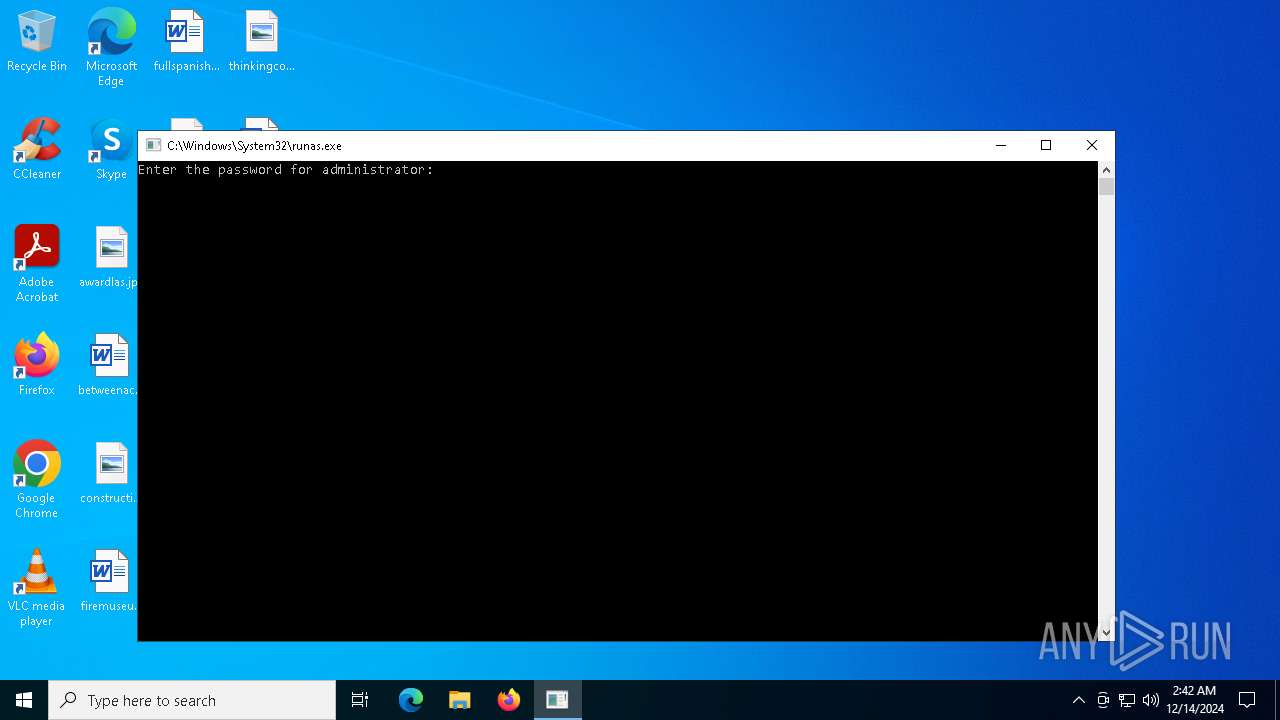
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 6308)
Reads the date of Windows installation
- Click me.exe (PID: 6964)
- Click me.exe (PID: 3608)
Executing commands from a ".bat" file
- Click me.exe (PID: 6964)
- Click me.exe (PID: 3608)
Starts CMD.EXE for commands execution
- Click me.exe (PID: 6964)
- Click me.exe (PID: 3608)
Reads security settings of Internet Explorer
- Click me.exe (PID: 3608)
- Click me.exe (PID: 6964)
INFO
Checks supported languages
- Click me.exe (PID: 6964)
- Click me.exe (PID: 3608)
Reads the computer name
- Click me.exe (PID: 6964)
- Click me.exe (PID: 3608)
The process uses the downloaded file
- Click me.exe (PID: 6964)
- Click me.exe (PID: 3608)
Creates files in the program directory
- cmd.exe (PID: 7028)
Manual execution by a user
- Click me.exe (PID: 3724)
- Click me.exe (PID: 3608)
Create files in a temporary directory
- Click me.exe (PID: 3608)
Process checks computer location settings
- Click me.exe (PID: 3608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2018:02:01 19:43:24+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 90112 |
| InitializedDataSize: | 206848 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
142
Monitored processes
13
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3608 | "C:\Users\admin\Desktop\Click me.exe" | C:\Users\admin\Desktop\Click me.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3724 | "C:\Users\admin\Desktop\Click me.exe" | C:\Users\admin\Desktop\Click me.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4716 | "C:\WINDOWS\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\BAE7.tmp\BAE8.tmp\BAE9.bat "C:\Users\admin\Desktop\Click me.exe"" | C:\Windows\System32\cmd.exe | Click me.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6308 | "C:\Windows\System32\runas.exe" /user:administrator "C:\Users\admin\Desktop\Click me.exe" | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6316 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | runas.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6416 | xcopy _\DontOpenMe C:\ProgramData\Microsoft\Windows\system32 | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
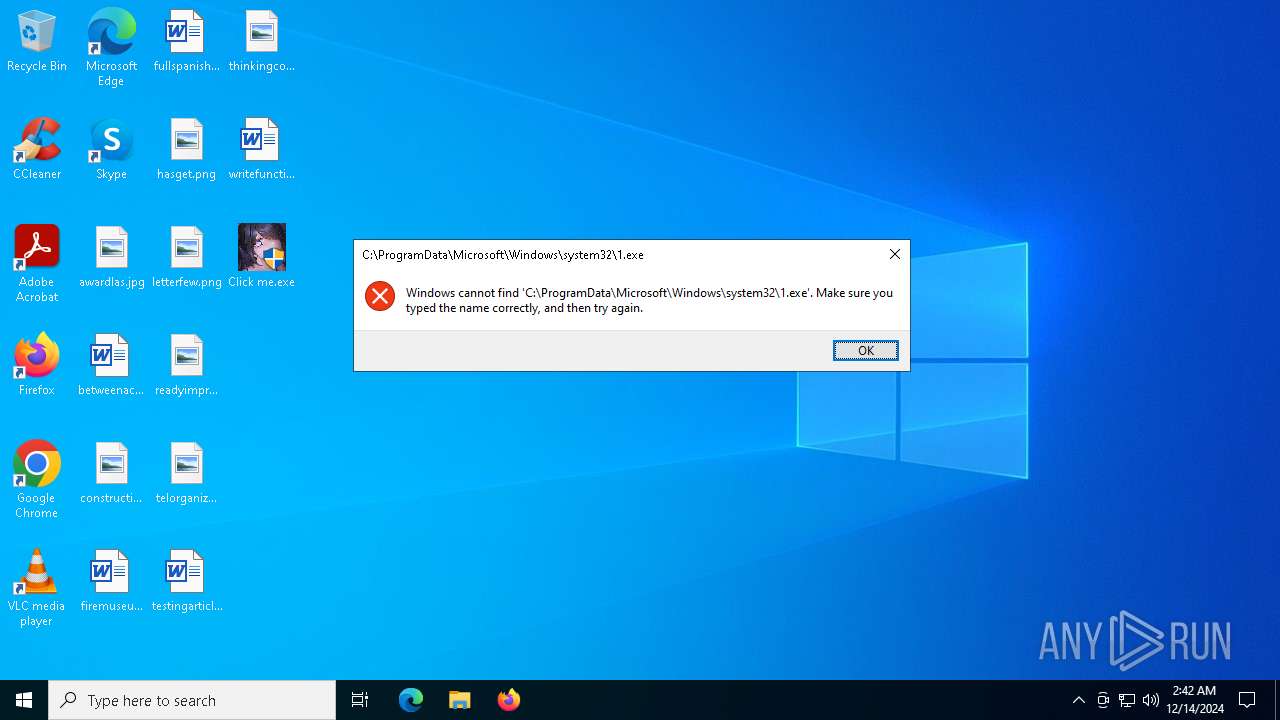
| 6424 | schtasks /create /tn "StartTW" /tr C:\ProgramData\Microsoft\Windows\system32\1.exe /sc ONLOGON | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6964 | "C:\Users\admin\Desktop\Click me.exe" | C:\Users\admin\Desktop\Click me.exe | runas.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 7028 | "C:\WINDOWS\system32\cmd.exe" /c "C:\Users\Administrator\AppData\Local\Temp\63AF.tmp\63B0.tmp\63B1.bat "C:\Users\admin\Desktop\Click me.exe"" | C:\Windows\System32\cmd.exe | Click me.exe | ||||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 033
Read events
1 033
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6964 | Click me.exe | C:\Users\Administrator\AppData\Local\Temp\63AF.tmp\63B0.tmp\63B1.bat | text | |
MD5:7191E2C20EED62CDB428918371ECFC72 | SHA256:8B4195E0C38E29C4ABA50D98CA47767448451BDB1856796552705E57EE79E009 | |||
| 3608 | Click me.exe | C:\Users\admin\AppData\Local\Temp\BAE7.tmp\BAE8.tmp\BAE9.bat | text | |
MD5:7191E2C20EED62CDB428918371ECFC72 | SHA256:8B4195E0C38E29C4ABA50D98CA47767448451BDB1856796552705E57EE79E009 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
29
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6280 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6280 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2624 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4704 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.144:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |