| URL: | https://github.com/pankoza2-pl/malware |
| Full analysis: | https://app.any.run/tasks/03308565-14d8-437b-a5f5-15fa7bfb43ba |
| Verdict: | Malicious activity |
| Analysis date: | November 09, 2024, 21:28:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E2218E70AC9D40A8213167C331BF673A |
| SHA1: | E7E81DCD8F9D4D6681BC5D260182ACE3FE787192 |
| SHA256: | D7C9F837F6B4156272917E8AC28146F63B475516E3D1AF4FE253877EF6055C70 |
| SSDEEP: | 3:N8tEdlELlf3VJIc/:2uoLFlSC |
MALICIOUS
Uses Task Scheduler to run other applications
- MBRPayload.exe (PID: 7248)
SUSPICIOUS
The executable file from the user directory is run by the CMD process
- MBRPayload.exe (PID: 7248)
- melter.exe (PID: 4228)
- Craze.exe (PID: 8860)
- screenscrew.exe (PID: 8816)
- lines.exe (PID: 9168)
- INV.exe (PID: 8688)
- Craze.exe (PID: 6612)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3676)
The process executes VB scripts
- cmd.exe (PID: 3676)
Executing commands from a ".bat" file
- PanKozaDestructive.exe (PID: 7896)
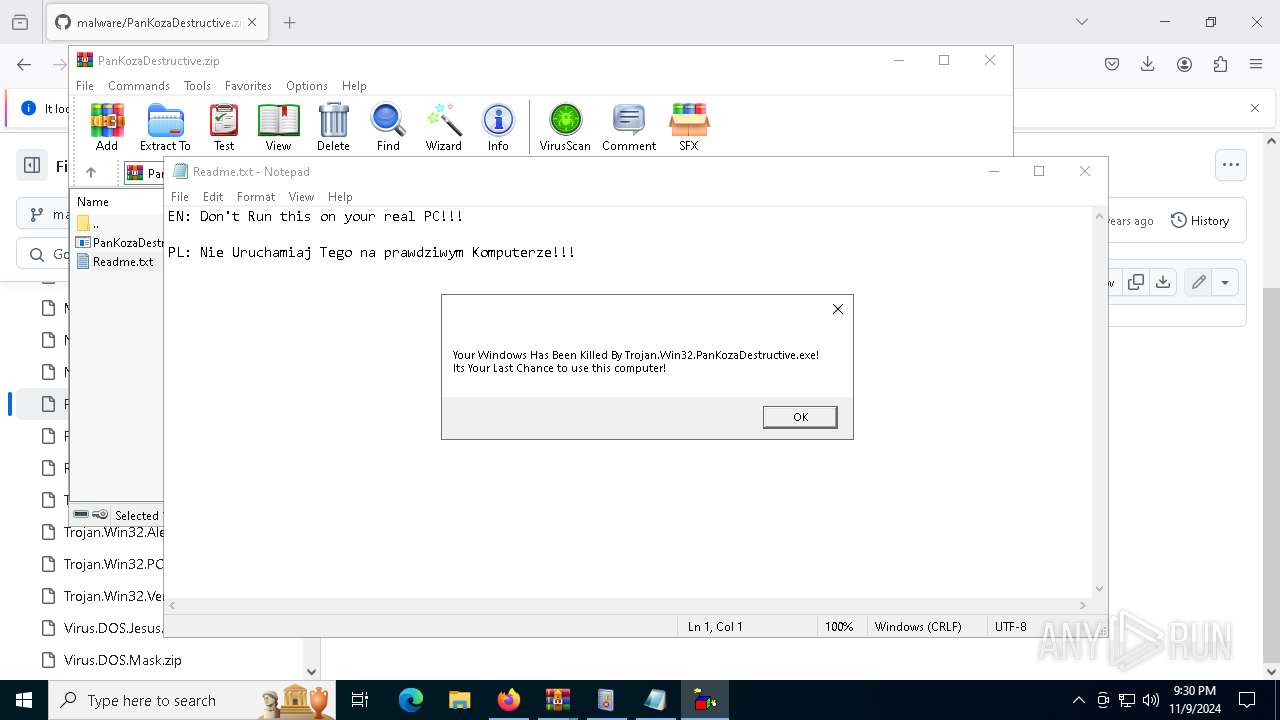
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 6460)
Executable content was dropped or overwritten
- PanKozaDestructive.exe (PID: 7896)
- icarus.exe (PID: 7552)
- avast_free_antivirus_online-installation.exe (PID: 1584)
- avast_free_antivirus_online_setup.exe (PID: 4380)
- icarus.exe (PID: 8108)
Probably fake Windows Update
- schtasks.exe (PID: 5184)
Starts CMD.EXE for commands execution
- PanKozaDestructive.exe (PID: 7896)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3676)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3676)
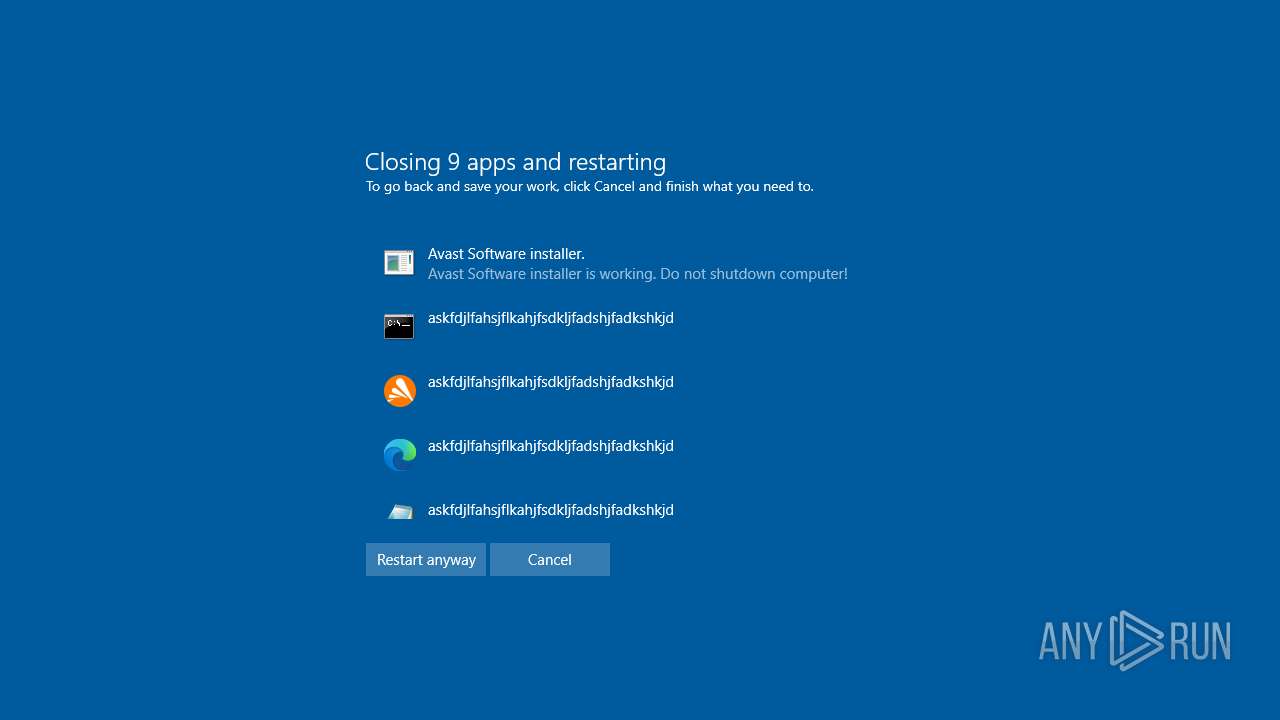
The system shut down or reboot
- cmd.exe (PID: 3676)
- cmd.exe (PID: 7812)
Starts itself from another location
- icarus.exe (PID: 8108)
Process drops legitimate windows executable
- icarus.exe (PID: 7552)
The process drops C-runtime libraries
- icarus.exe (PID: 7552)
INFO
Application launched itself
- firefox.exe (PID: 6152)
- firefox.exe (PID: 4340)
- msedge.exe (PID: 3904)
- msedge.exe (PID: 6516)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7276)
- WinRAR.exe (PID: 6460)
- msedge.exe (PID: 780)
- msedge.exe (PID: 3904)
Found Base64 encoded text manipulation via PowerShell (YARA)
- mmc.exe (PID: 7868)
Found Base64 encoded reflection usage via PowerShell (YARA)
- mmc.exe (PID: 7868)
Manual execution by a user
- WinRAR.exe (PID: 6460)
- msedge.exe (PID: 3904)
- WinRAR.exe (PID: 7276)
- cmd.exe (PID: 7812)
UPX packer has been detected
- PanKozaDestructive.exe (PID: 7896)
Aspack has been detected
- PanKozaDestructive.exe (PID: 7896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
280
Monitored processes
130
Malicious processes
3
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 696 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa6460.13372\Readme.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 1073807364 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 780 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2512 --field-trial-handle=2440,i,6730828179766919257,11828573862004697589,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | ||||
| 848 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2360 --field-trial-handle=2344,i,5453608665468533086,1533641061363002879,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | ||||
| 884 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --no-appcompat-clear --mojo-platform-channel-handle=7172 --field-trial-handle=2440,i,6730828179766919257,11828573862004697589,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | ||||
| 884 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=49 --mojo-platform-channel-handle=4180 --field-trial-handle=2440,i,6730828179766919257,11828573862004697589,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | ||||
| 1584 | "C:\Users\admin\Downloads\avast_free_antivirus_online-installation.exe" | C:\Users\admin\Downloads\avast_free_antivirus_online-installation.exe | msedge.exe | |
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: Avast Installer Exit code: 1073807364 Version: 2.1.133.0 | ||||
| 1712 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3808 --field-trial-handle=2440,i,6730828179766919257,11828573862004697589,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | ||||
| 1792 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3992 --field-trial-handle=2440,i,6730828179766919257,11828573862004697589,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | ||||
| 2084 | timeout 5 /nobreak | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
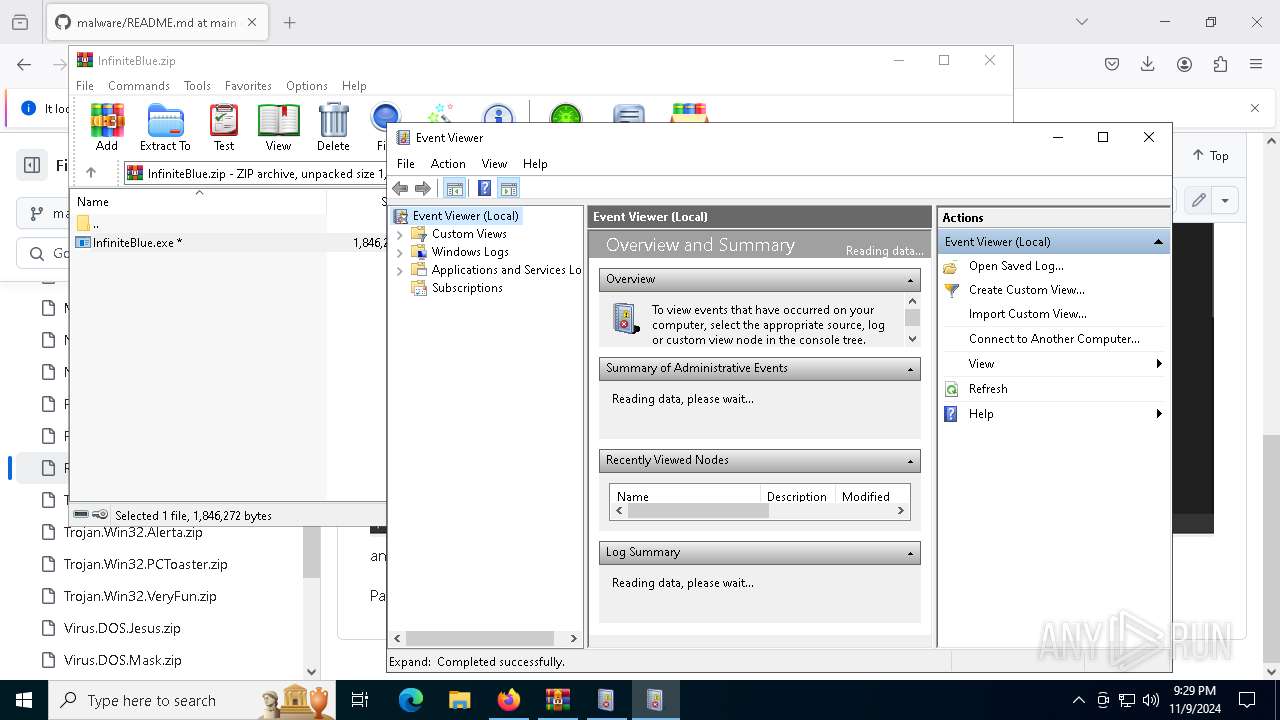
| 2684 | "C:\Windows\System32\eventvwr.exe" | C:\Windows\System32\eventvwr.exe | — | InfiniteBlue.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Event Viewer Snapin Launcher Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
Total events
15 190
Read events
15 173
Write events
12
Delete events
5
Modification events
| (PID) Process: | (4340) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\InfiniteBlue.zip | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7912) InfiniteBlue.exe | Key: | HKEY_CLASSES_ROOT\.msc |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7912) InfiniteBlue.exe | Key: | HKEY_CLASSES_ROOT\mscfile\shell\open\command |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
315
Suspicious files
1 553
Text files
259
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4340 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 4340 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4340 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4340 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | dbf | |
MD5:4006DDC2918B16C7EF5516C58373842B | SHA256:269EA23B77EDE0874628BD8611BCC5A3E87E0C44CA8A821C0D028B929D4F468F | |||
| 4340 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:1985F9A04CE70D2C69DDB753192D0B83 | SHA256:868D7F8692A449A055897C472007AAAF2C7B01825793503288E203BE20DC6E9C | |||
| 4340 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 4340 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4340 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\activity-stream.discovery_stream.json.tmp | binary | |
MD5:0D501F23584ABA54AA0A27588F1EDCAA | SHA256:920E29F5AF90ACE2DC9EF3828E2B562C47FEB8DA0F9BCF1CDFE9F3C81DDA4814 | |||
| 4340 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:C09FF302D57C404B61E6A89B0B9F36E7 | SHA256:6A5B4F82595799346D0E501FE6CC8629E0FD6ED27B74D0E6CB5073DDB2E3C40B | |||
| 4340 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
55
TCP/UDP connections
320
DNS requests
416
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4340 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
4340 | firefox.exe | POST | 200 | 142.250.185.227:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
4340 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
4340 | firefox.exe | POST | — | 2.16.168.11:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4340 | firefox.exe | POST | 200 | 2.16.168.11:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4340 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
4340 | firefox.exe | POST | 200 | 2.16.168.11:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4340 | firefox.exe | POST | 200 | 2.16.168.11:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4340 | firefox.exe | POST | 200 | 142.250.185.227:80 | http://o.pki.goog/s/wr3/yvU | unknown | — | — | whitelisted |
4340 | firefox.exe | POST | 200 | 2.16.168.7:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3524 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4340 | firefox.exe | 140.82.121.3:443 | github.com | GITHUB | US | shared |
4340 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
4340 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
4340 | firefox.exe | 142.250.185.227:80 | o.pki.goog | GOOGLE | US | whitelisted |
4340 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| shared |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
— | — | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|
mmc.exe | Getting next publisher from enum failed-259-No more data is available
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|
mmc.exe | ExpandNode:After EventsNode:InsertChildren CountOfChildren = 5
|
mmc.exe | Wrong type received for PublisherMetadataPublisherGuid
|
mmc.exe | PublisherMetadataKeywordName failed for not providing enough memory. Trying with the correct memory -122-The data area passed to a system call is too small
|