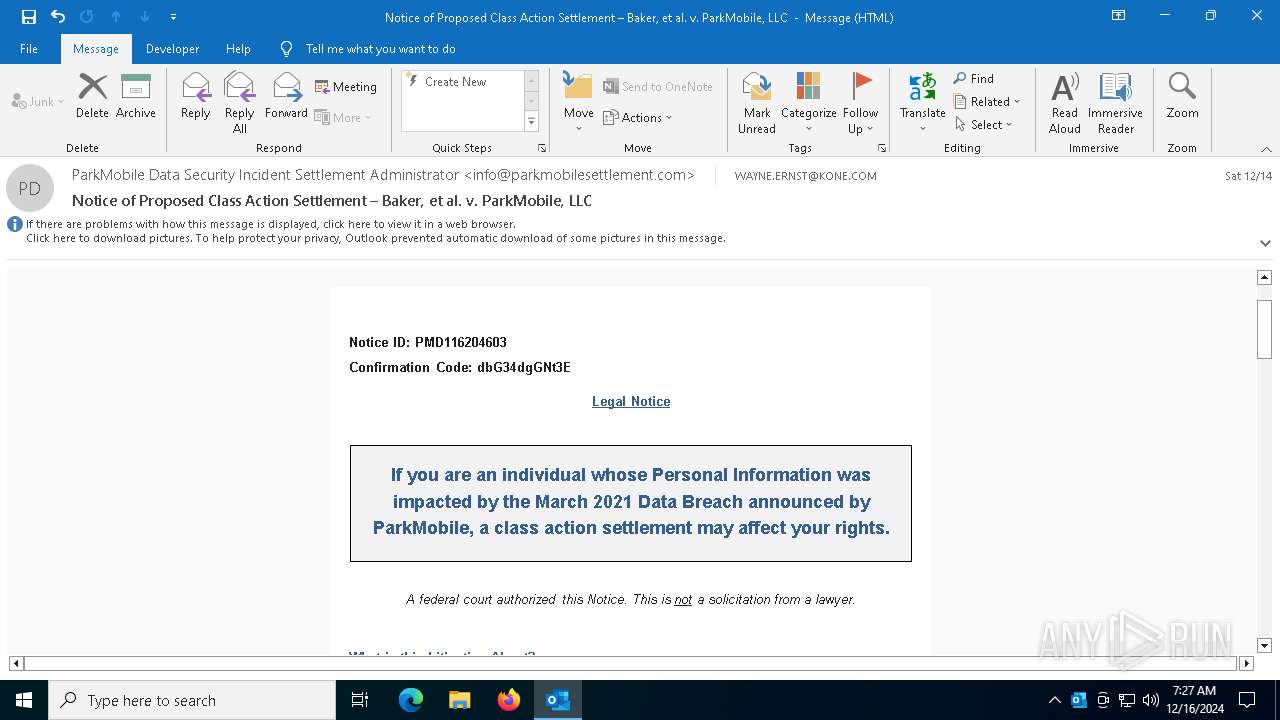
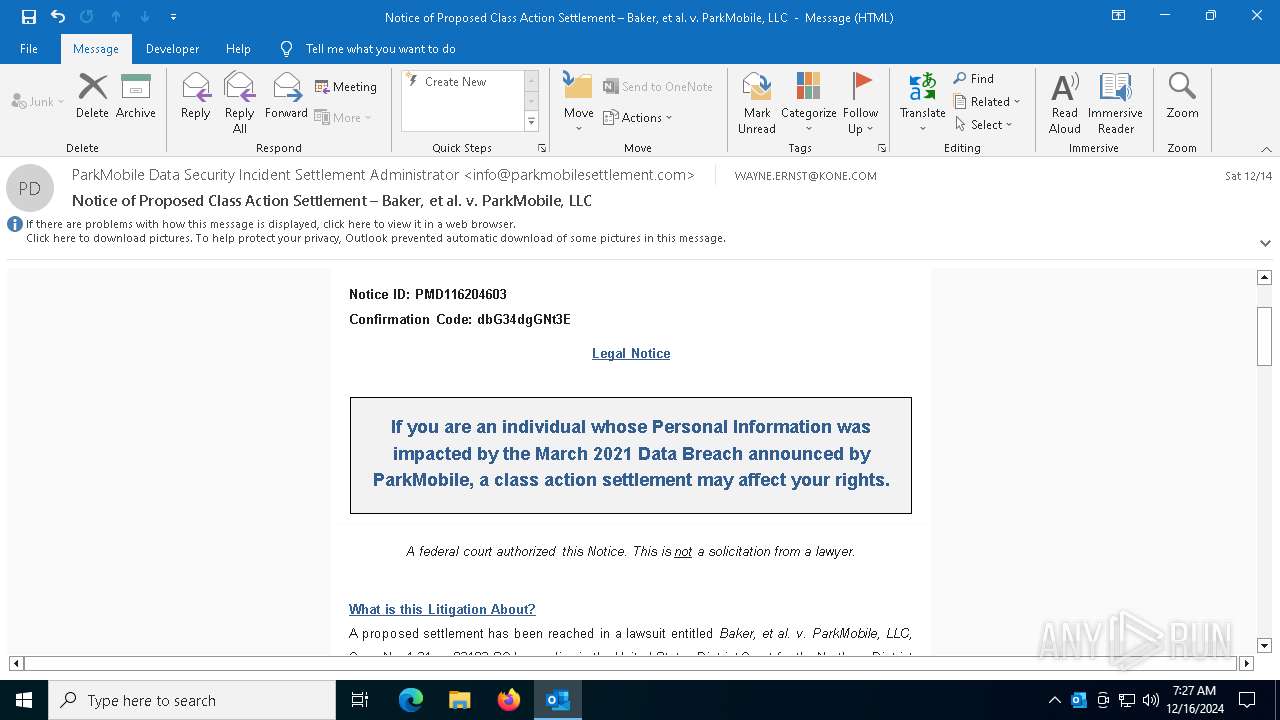
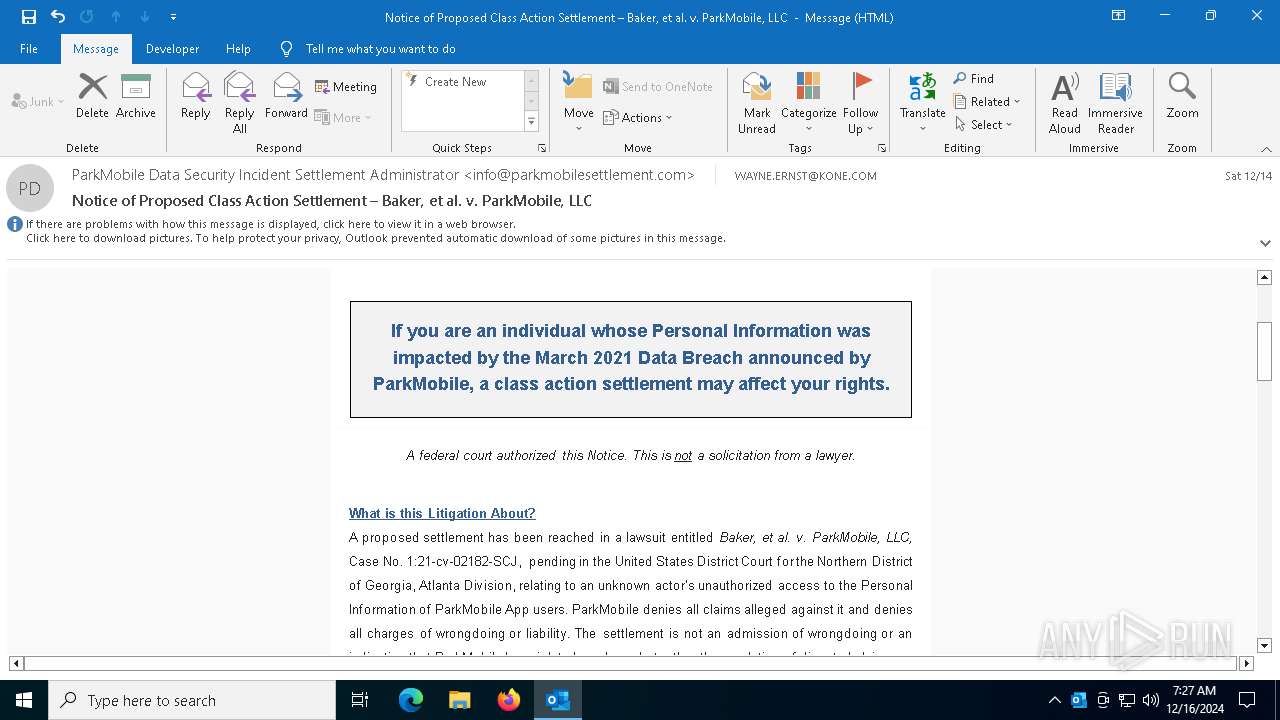
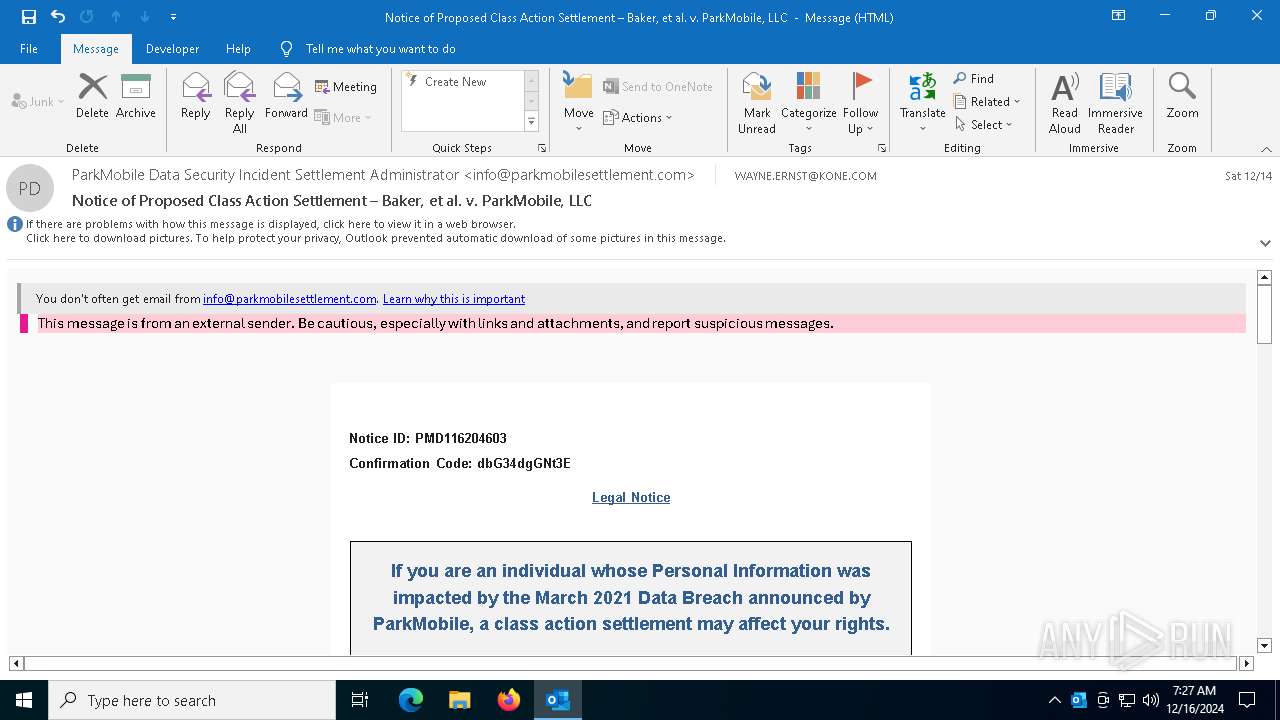
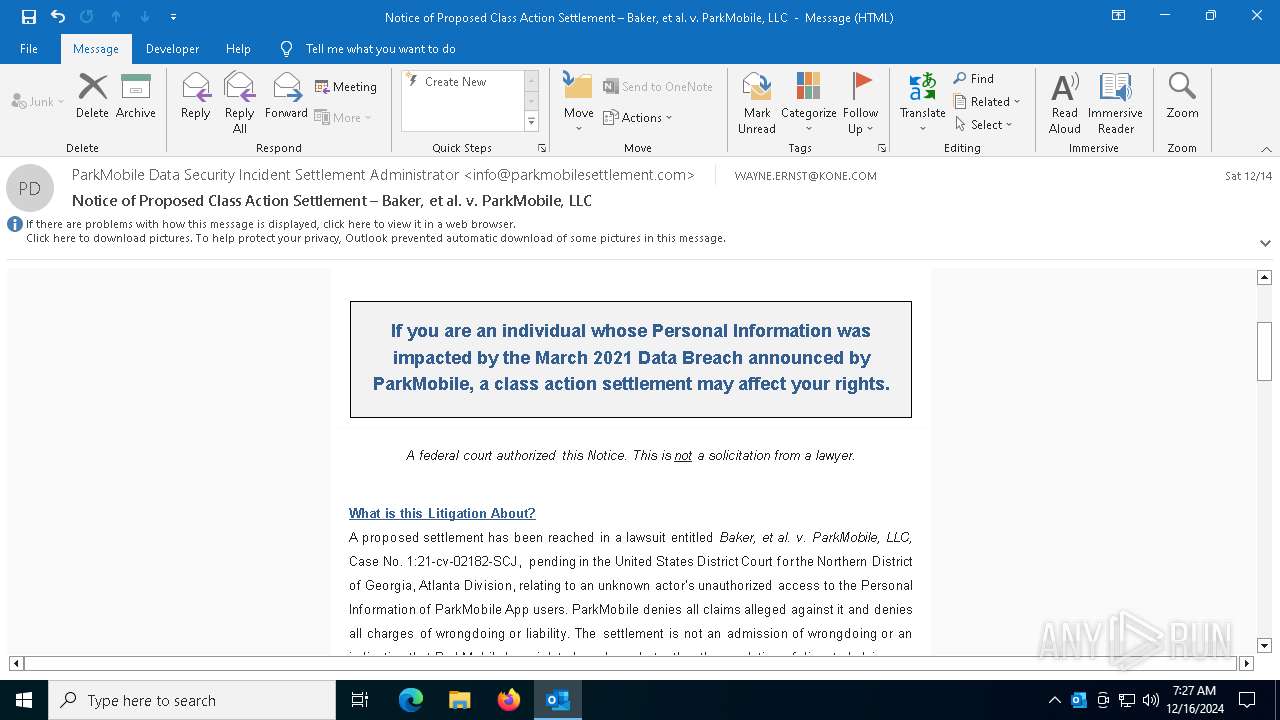
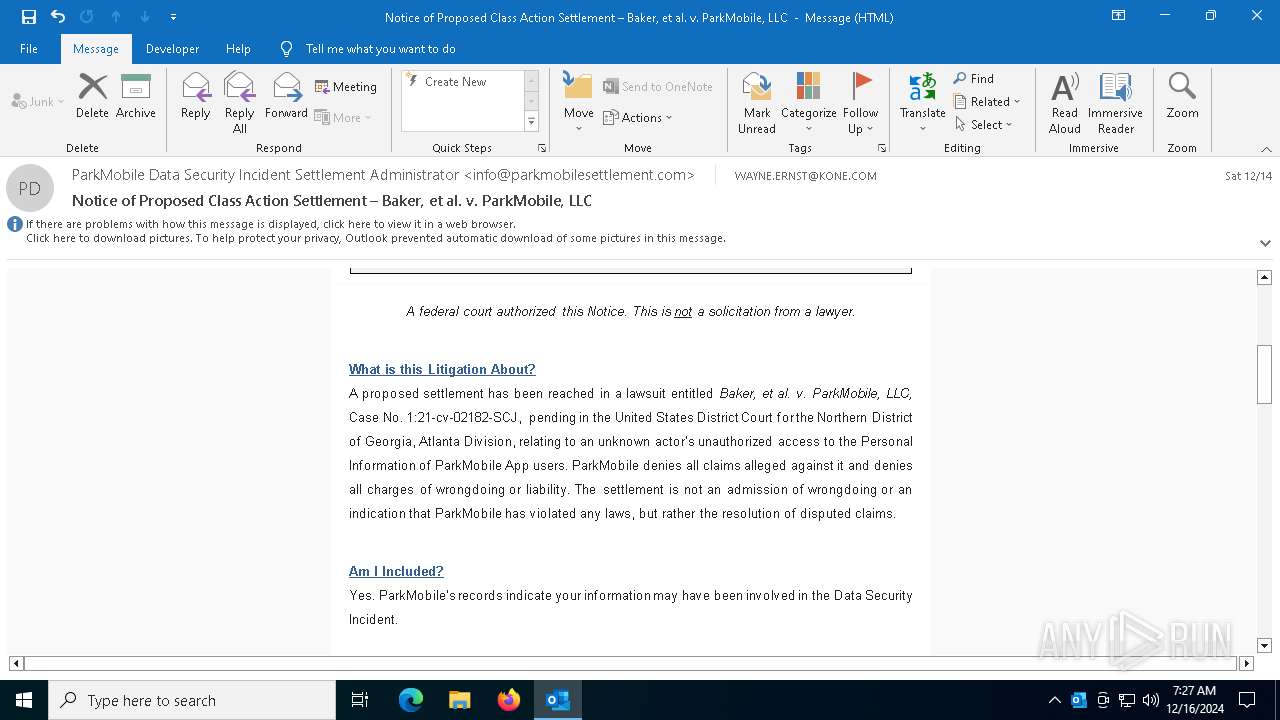
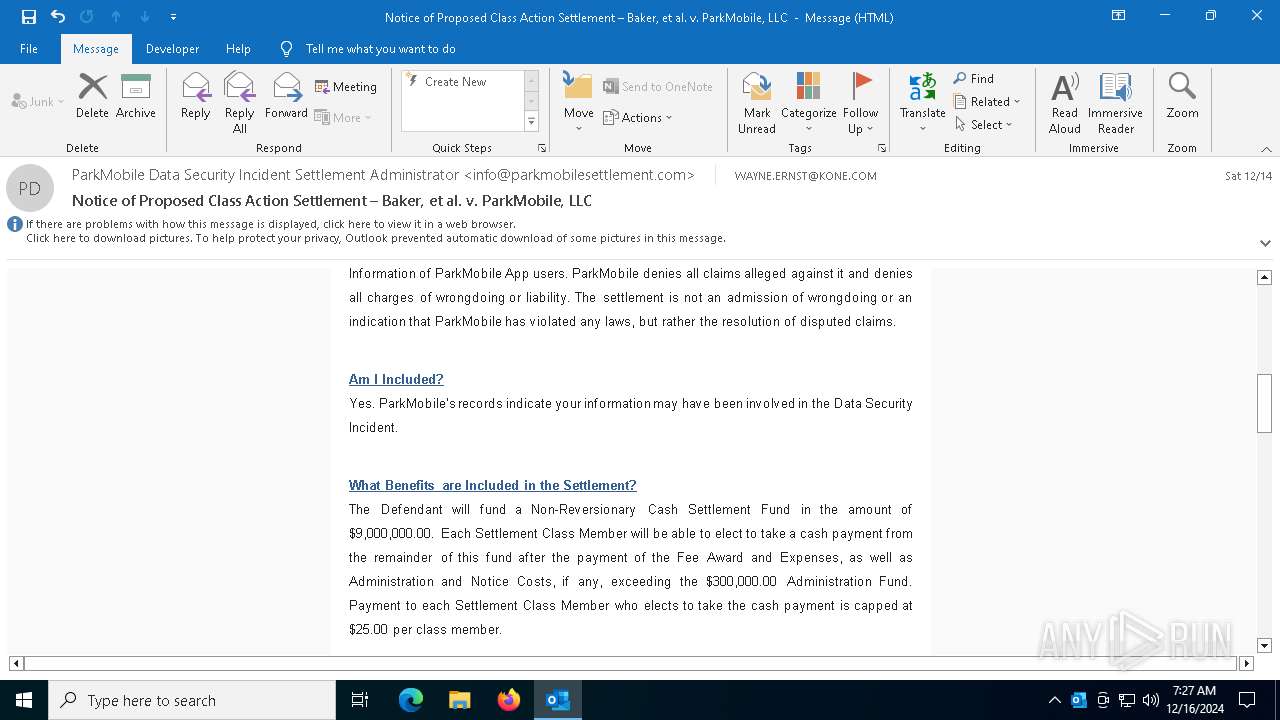
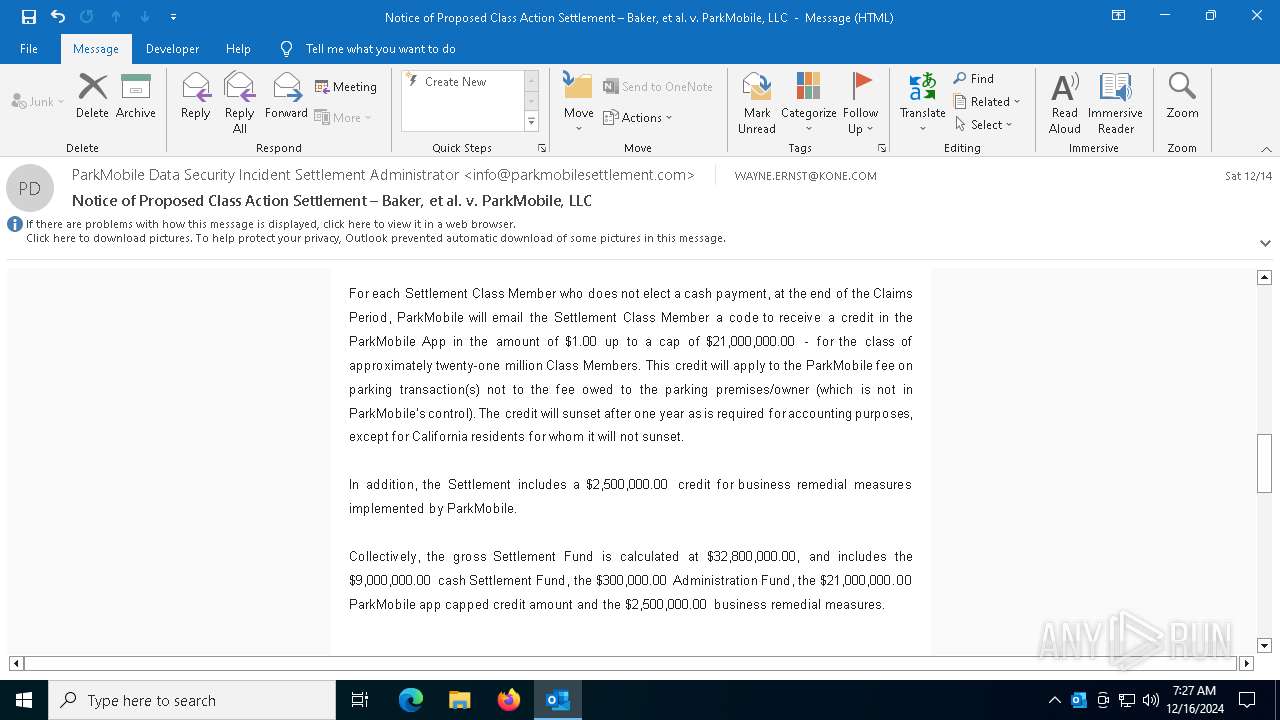
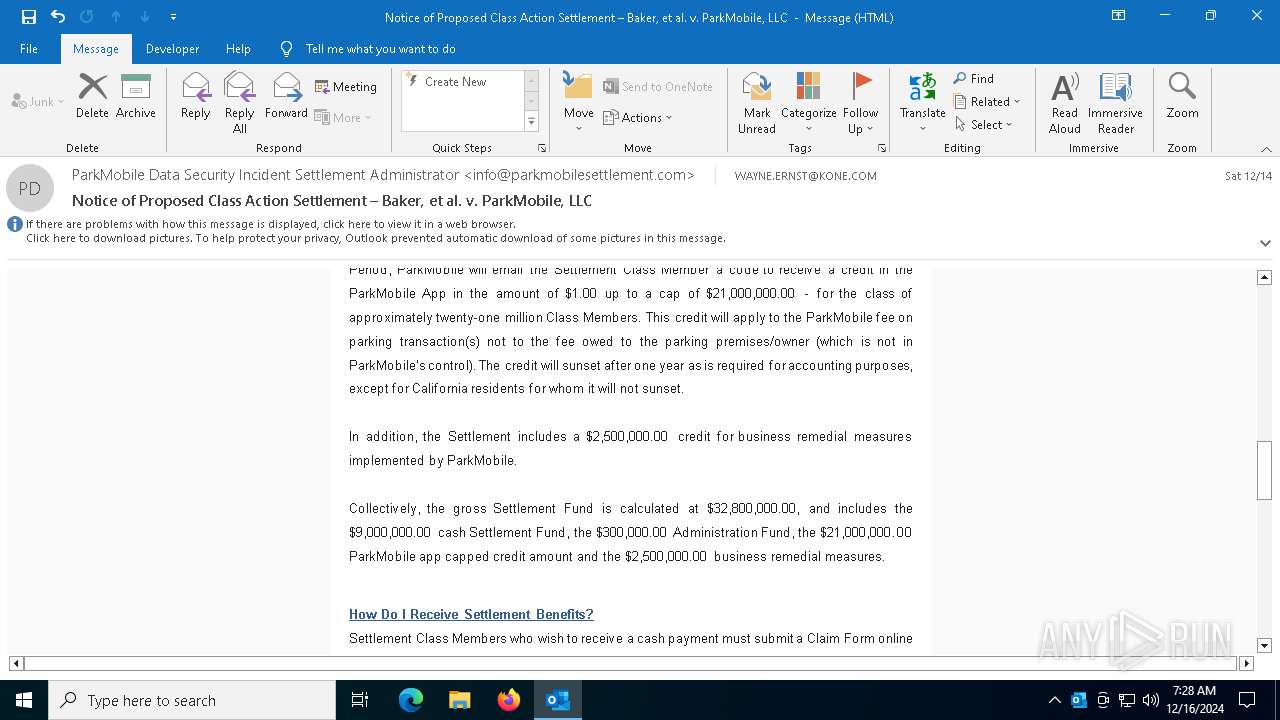
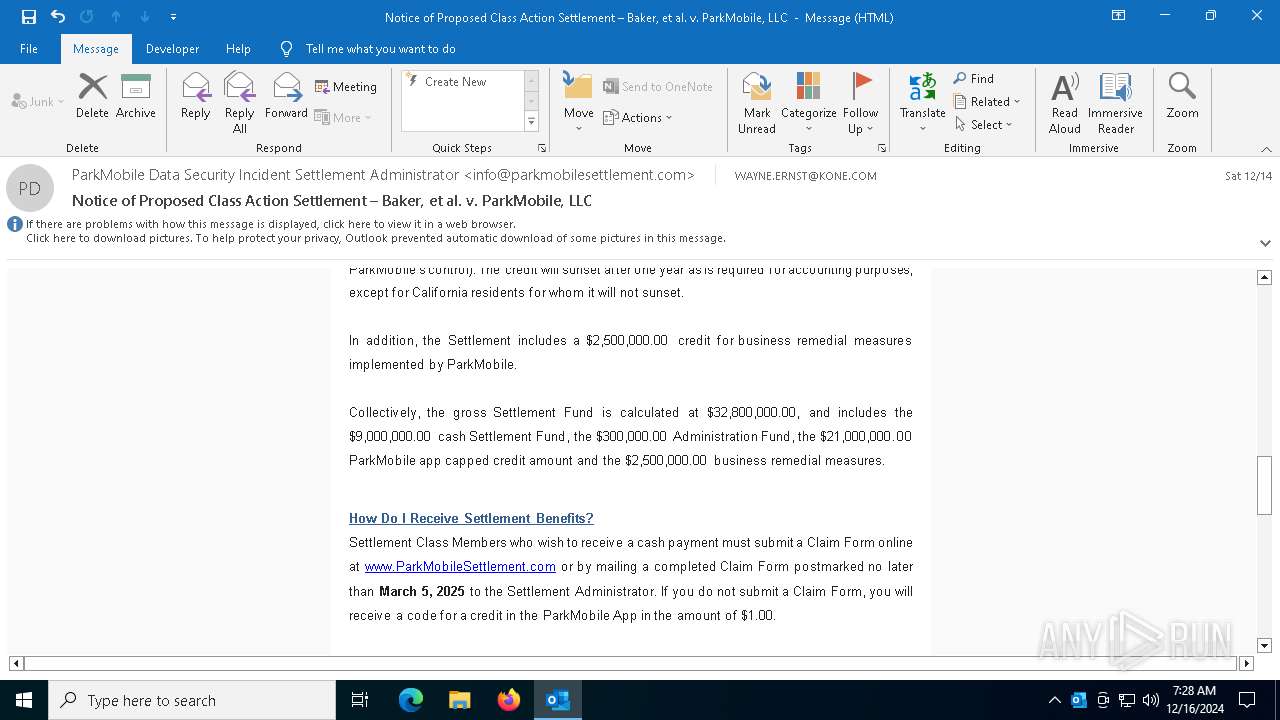
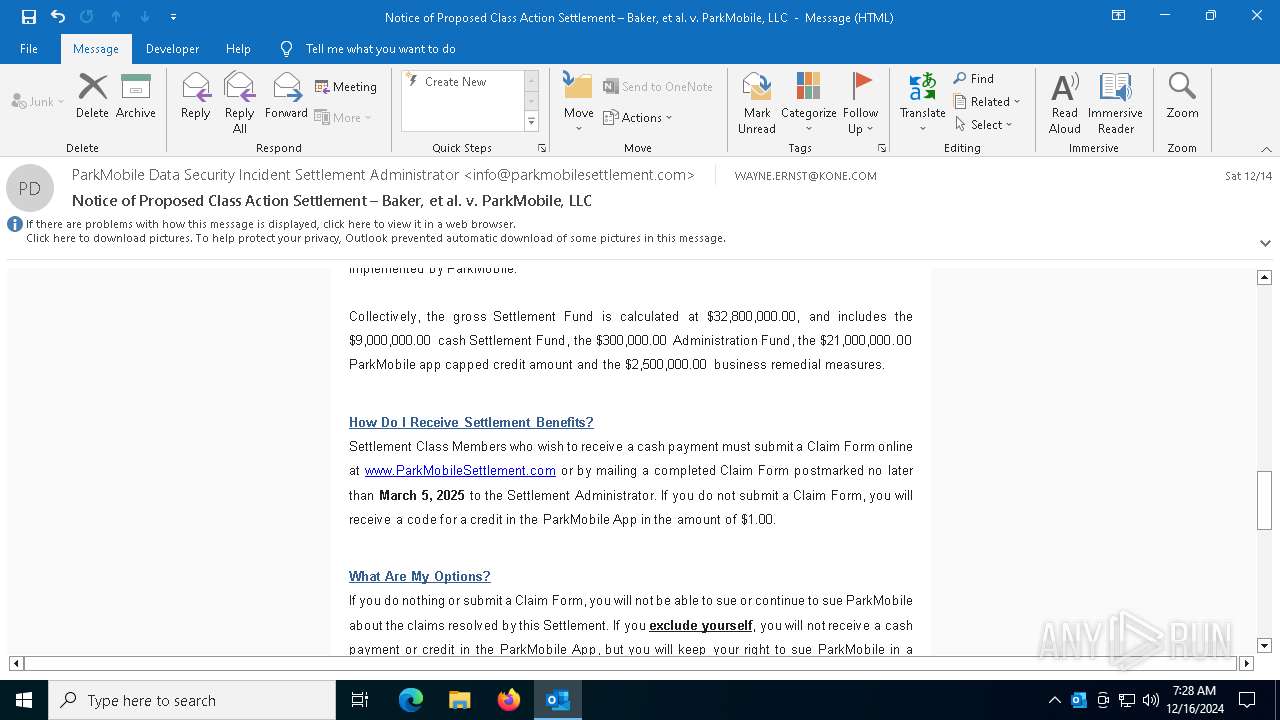
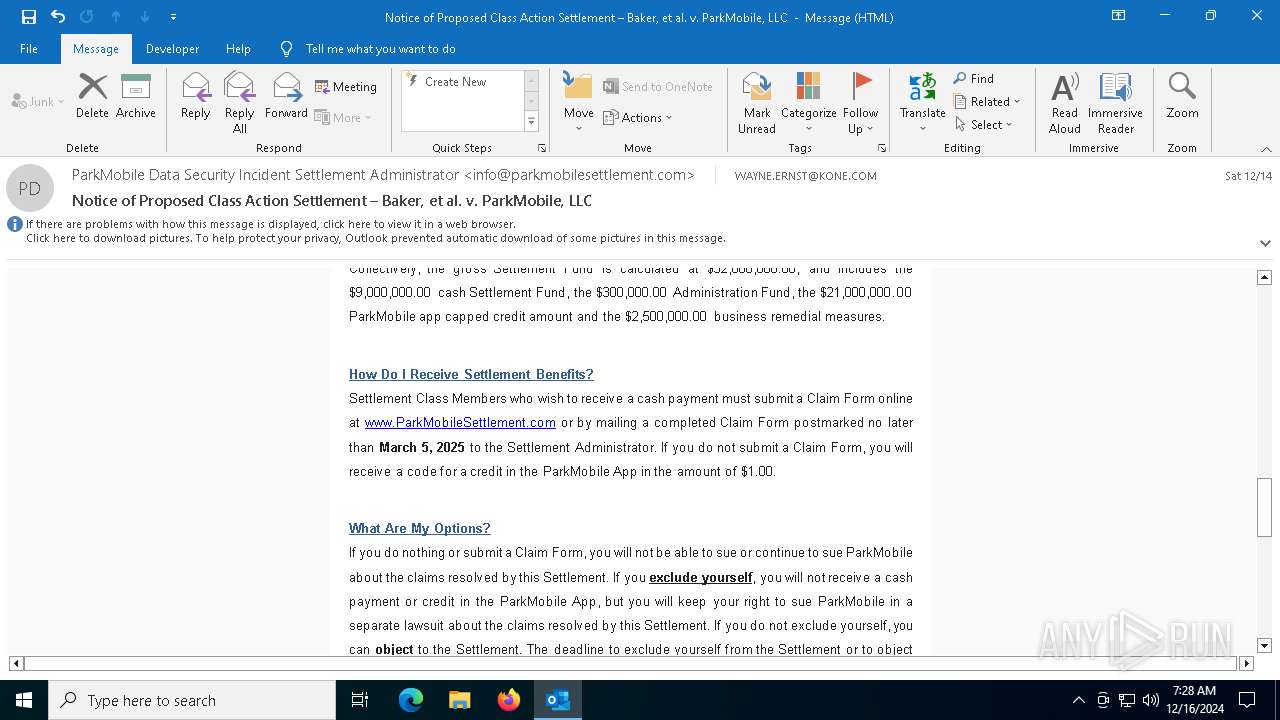
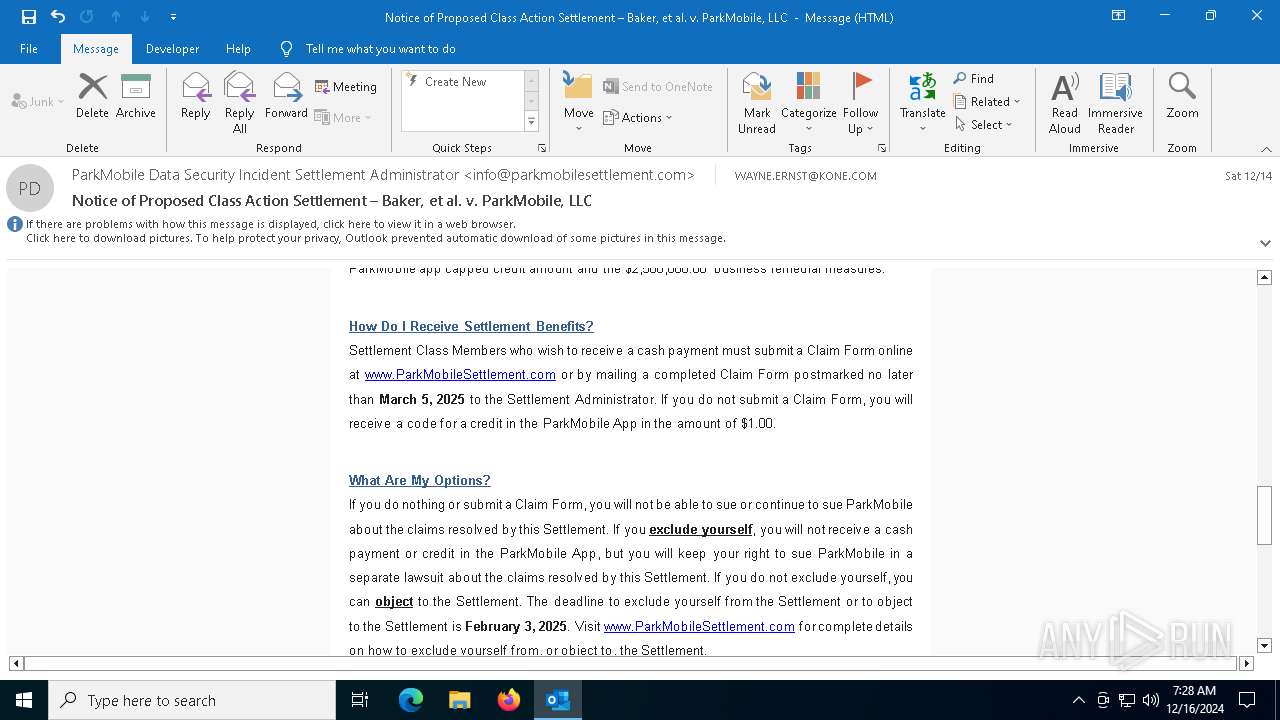
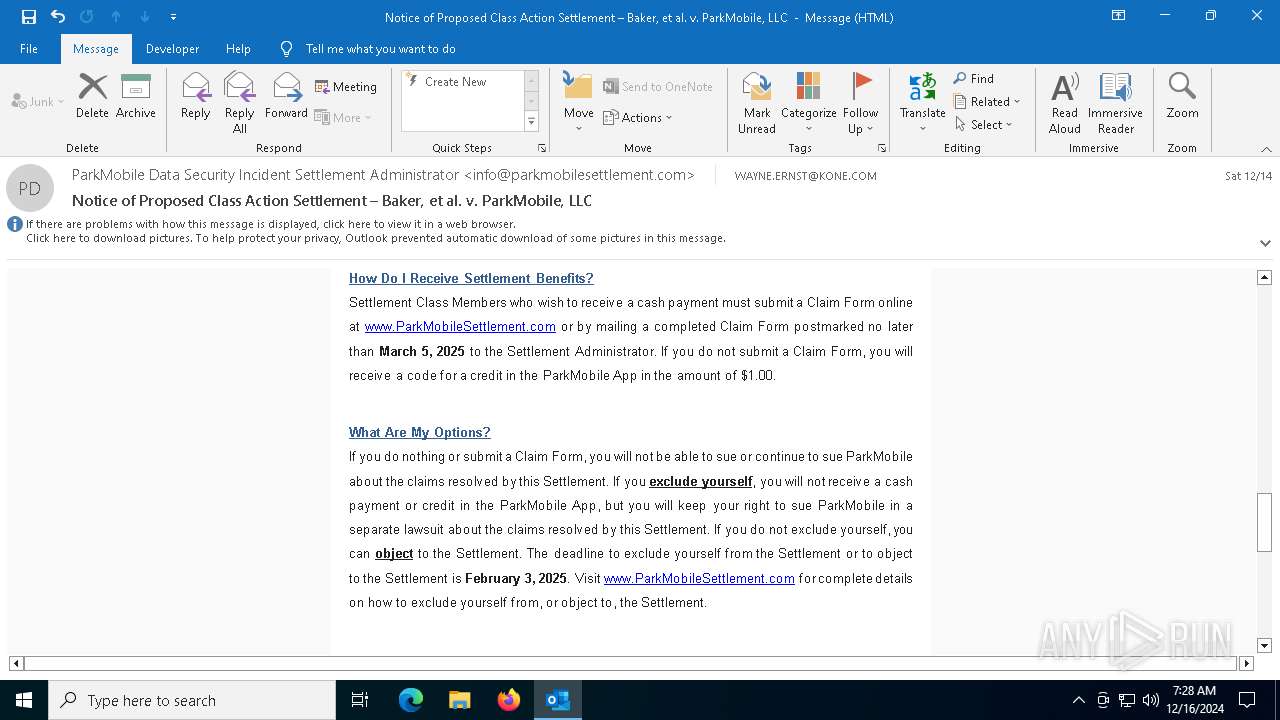
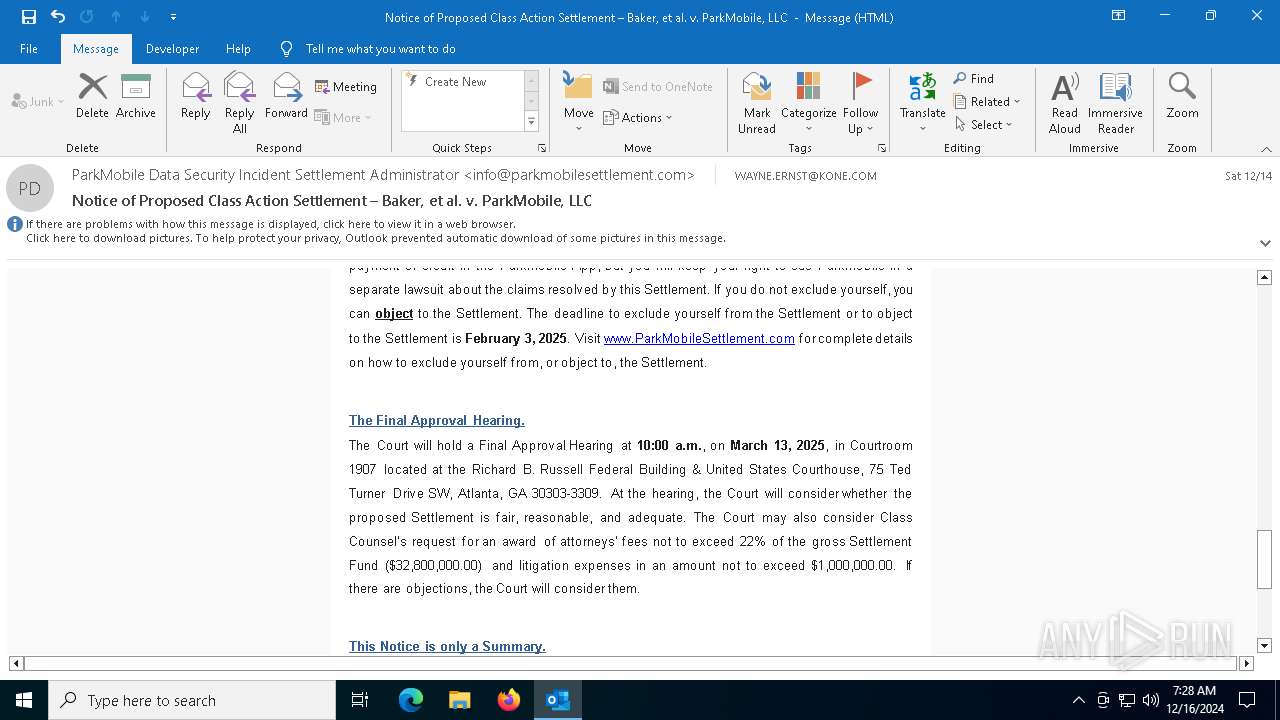
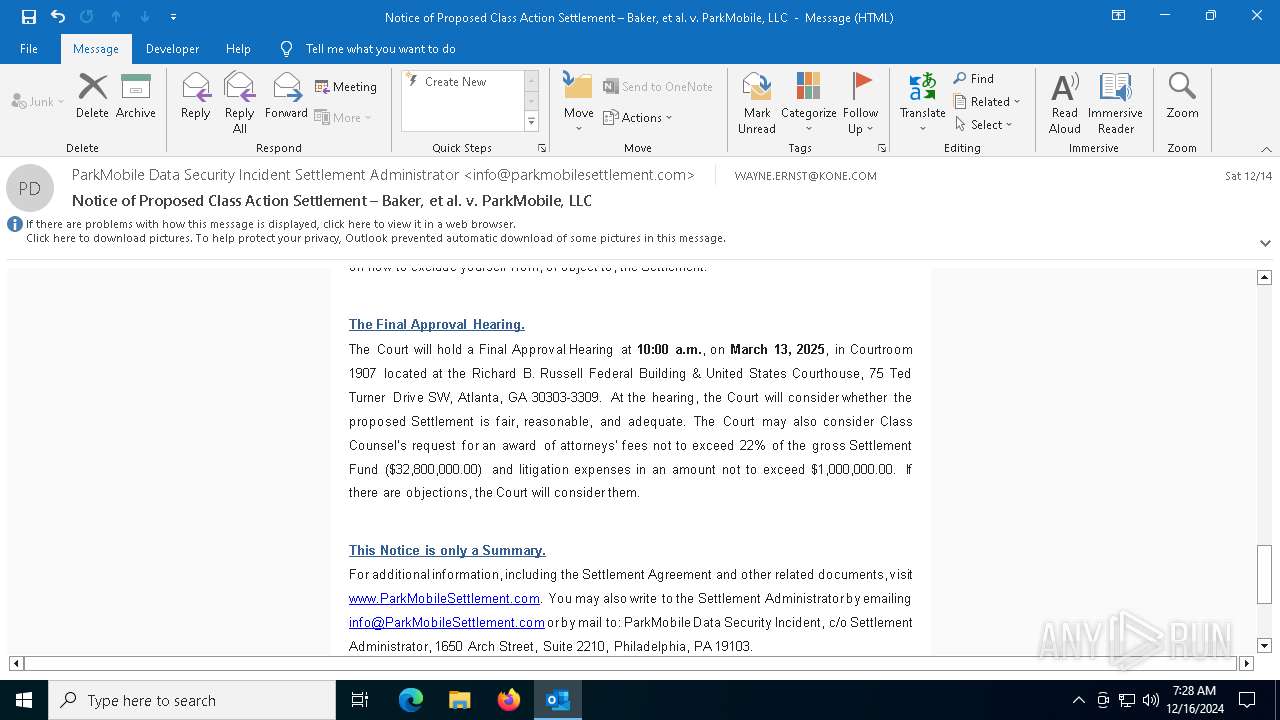
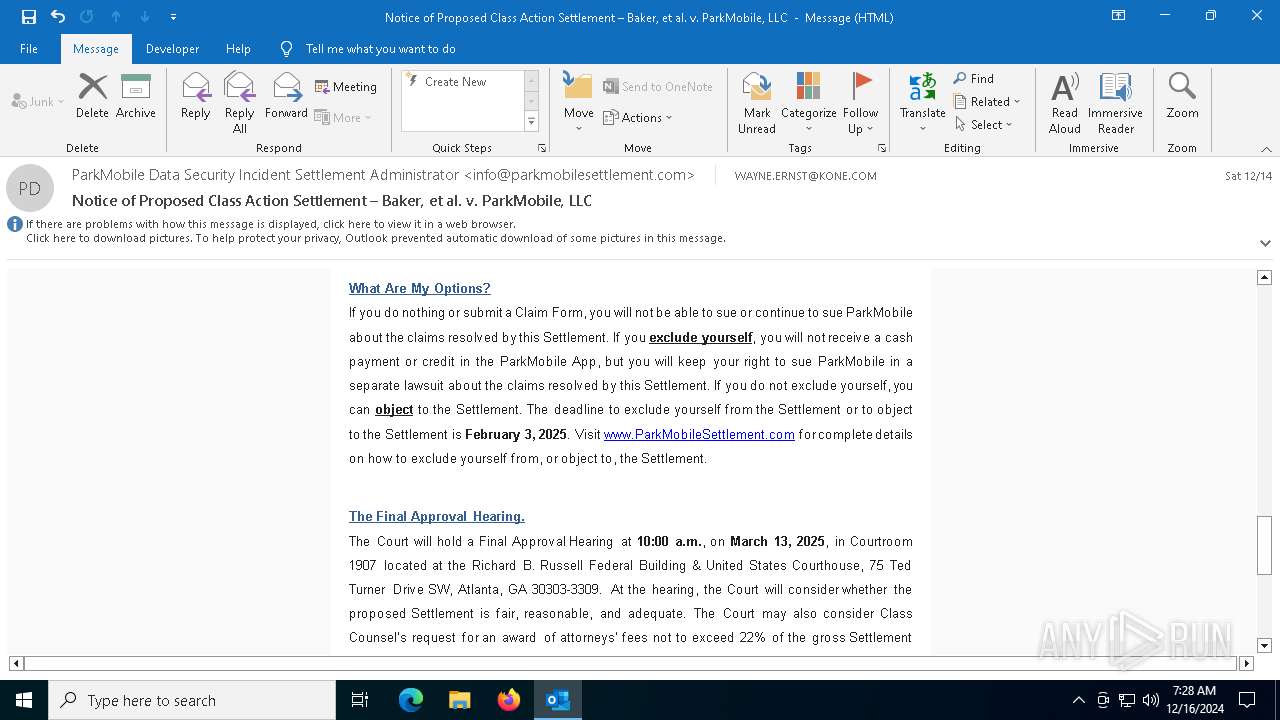
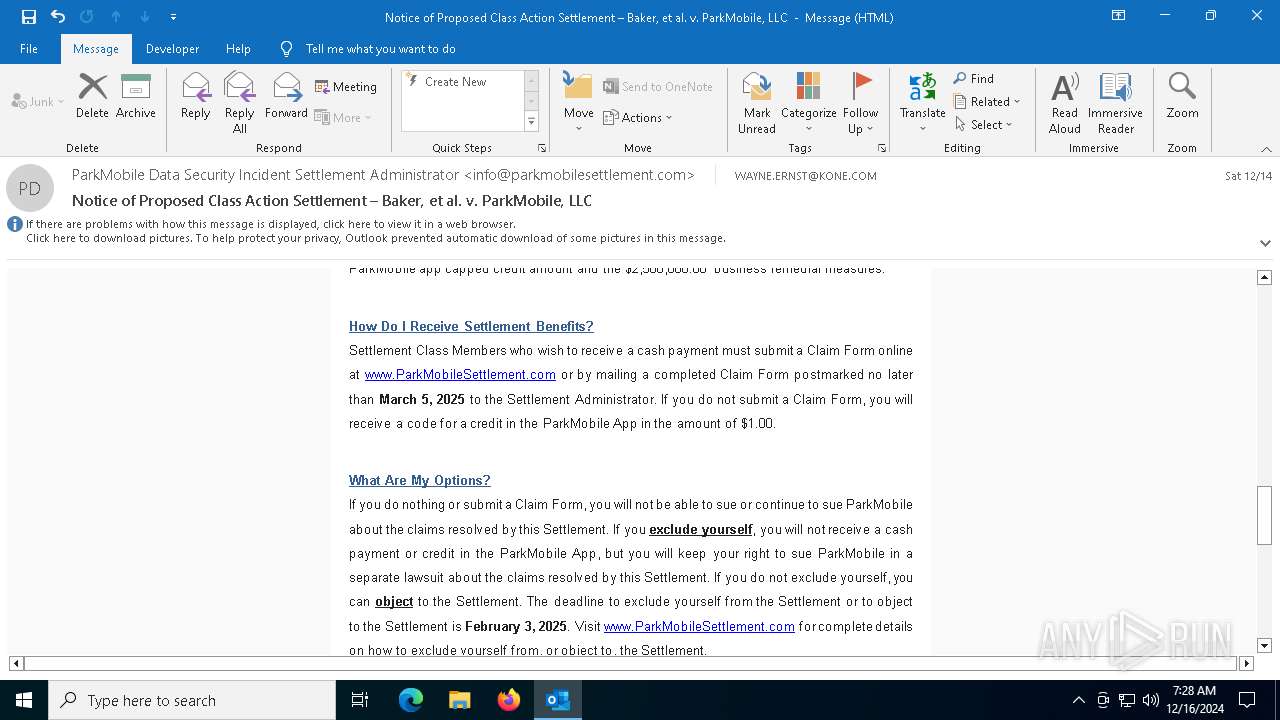
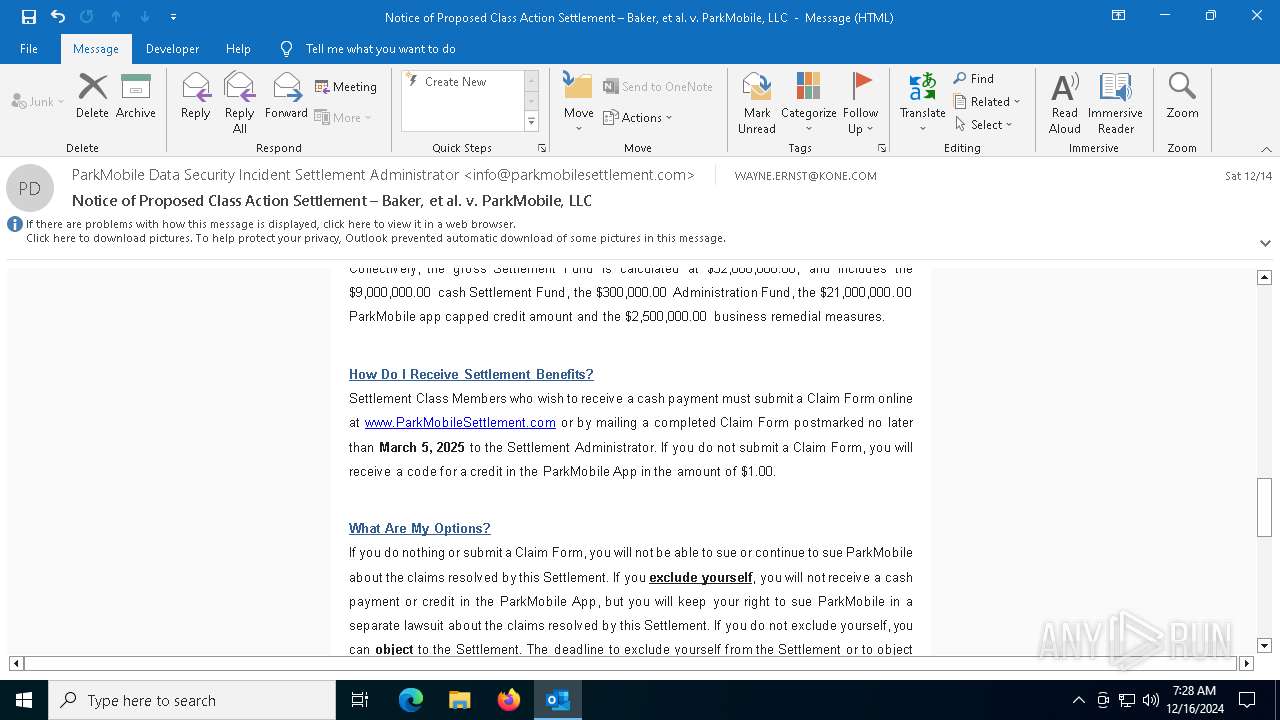
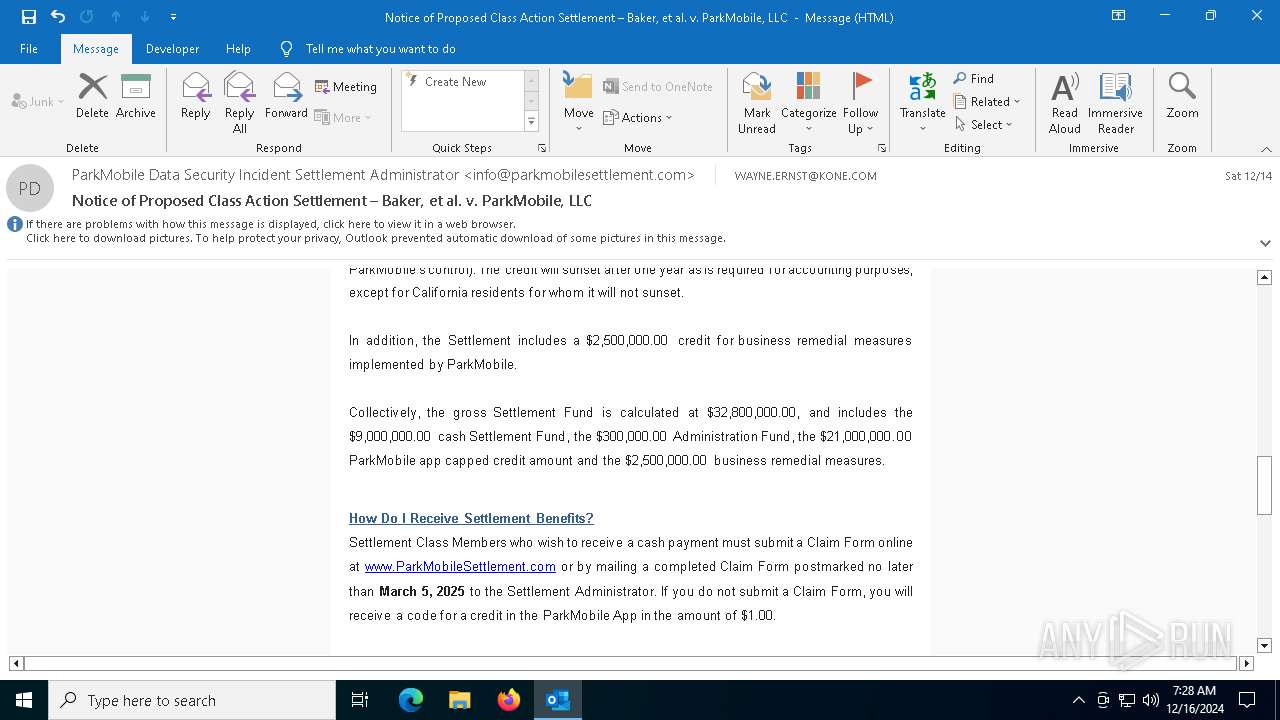
| File name: | Notice of Proposed Class Action Settlement – Baker, et al. v. ParkMobile, LLC.eml |
| Full analysis: | https://app.any.run/tasks/8ff58027-8ecb-4757-bffc-502c0888a1bf |
| Verdict: | Malicious activity |
| Analysis date: | December 16, 2024, 07:27:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, Unicode text, UTF-8 (with BOM) text, with very long lines (310), with CRLF line terminators |
| MD5: | 66459C048E2F390BB170F93395548CFF |
| SHA1: | EADF21223A7A64B55E45C08DA3D6785F6AEFA65B |
| SHA256: | D7C3F62D8222EF66316E7544D476CD06A9320457C455002F9C1C32C237557E74 |
| SSDEEP: | 1536:tNEp8VoW//RM2z61To/qKKitO3S5O8BrgsE:wY/ReqDtO3UO8BrgsE |
MALICIOUS
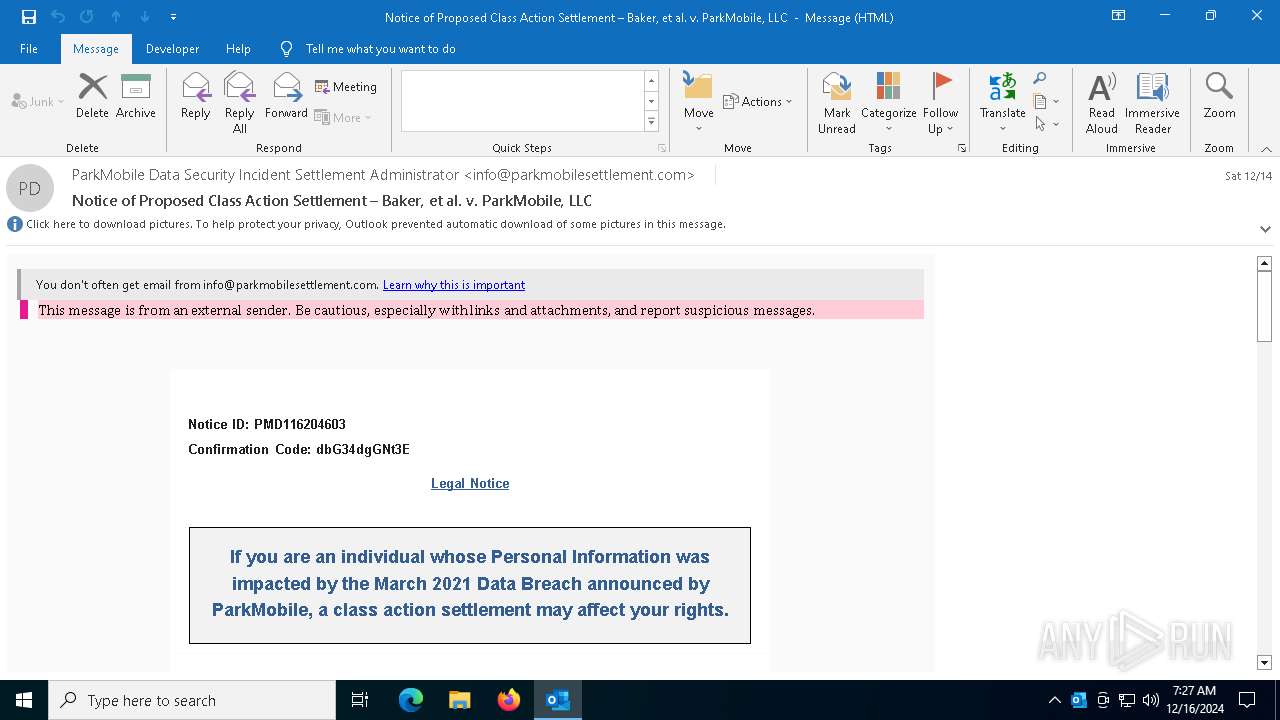
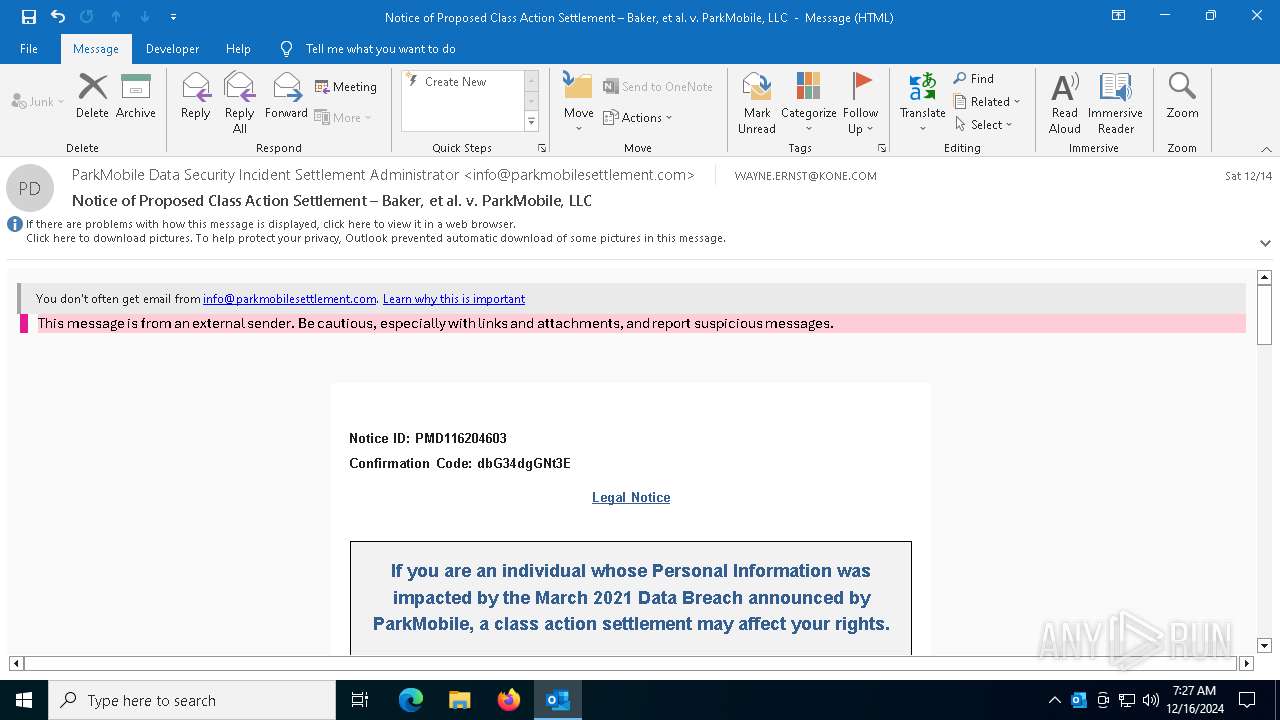
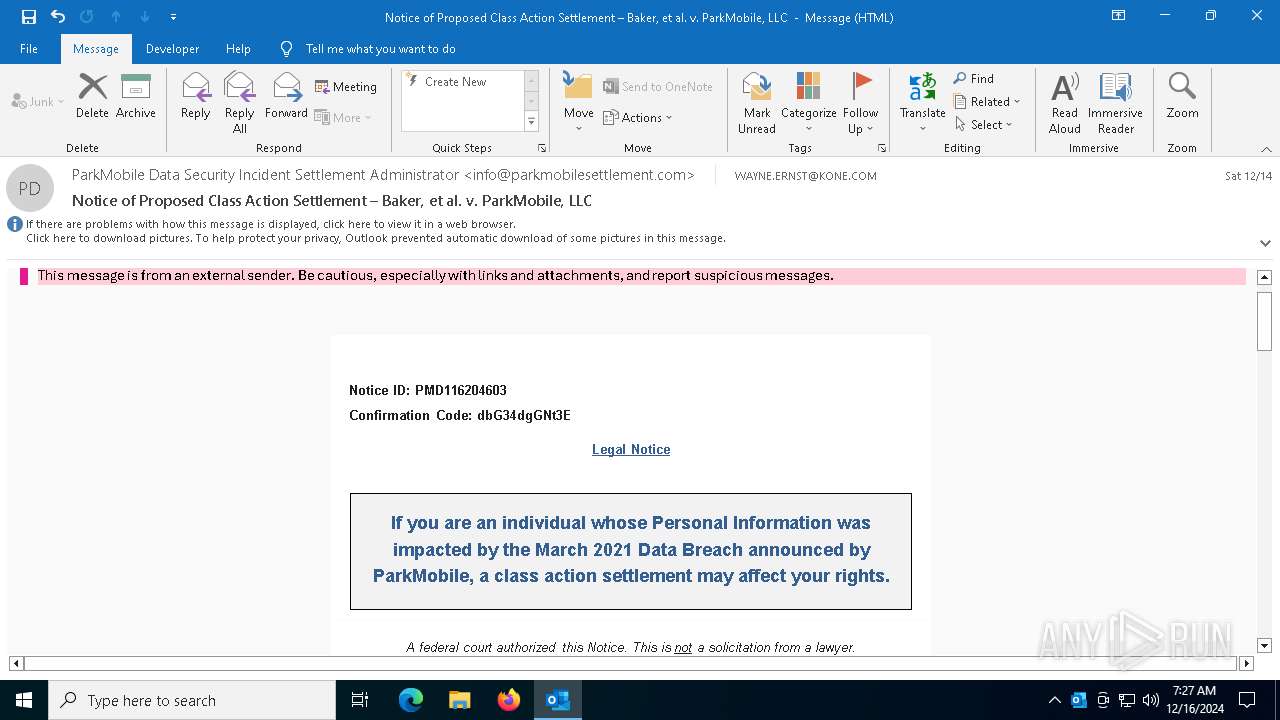
Email came from third-party service (Amazon SES)
- OUTLOOK.EXE (PID: 6396)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-8 encoded (100) |
|---|
Total processes
126
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6204 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "49EE92E7-E769-441B-AC8E-973192A55B44" "2CEA3AF8-9E39-45DB-BA9A-7B3B7B6E41C8" "6396" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 | |||||||||||||||
| 6396 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Notice of Proposed Class Action Settlement – Baker, et al. v. ParkMobile, LLC.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
3 803
Read events
3 602
Write events
157
Delete events
44
Modification events
| (PID) Process: | (6396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingConfigurableSettings |
Value: DC00000000000000803A090041060100010001000000000000000000000000000000000000000000201C0000201C00008051010080510100805101008051010080F4030080F4030080F403002C01000084030000805101000000000084030000805101000A0000001E0000001E000000000000000000000080510100010000000100000000000000000000000000000000000000008D2700008D2700008D2700010000000A000000805101000000300000003000000030000000000084030000805101001E0000008403000080510100050000000500000005000000 | |||
| (PID) Process: | (6396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingConfigurableSettings |
Value: DC00000000000000803A0900E8070C000100100007001B001D000001000000000000000000000000201C0000201C00008051010080510100805101008051010080F4030080F4030080F403002C01000084030000805101000000000084030000805101000A0000001E0000001E000000000000000000000080510100010000000100000000000000000000000000000000000000008D2700008D2700008D2700010000000A000000805101000000300000003000000030000000000084030000805101001E0000008403000080510100050000000500000005000000 | |||
| (PID) Process: | (6396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingLastSyncTimeOutlook |
Value: E8070C000100100007001B001D000001 | |||
| (PID) Process: | (6396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingLastWriteTimeOutlook |
Value: E8070C000100100007001B001D000001 | |||
| (PID) Process: | (6396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Display Types\Balloons |
| Operation: | write | Name: | HWND64ForOrphanedNotIcon |
Value: 2A020C0000000000 | |||
| (PID) Process: | (6396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\AddInLoadTimes |
| Operation: | write | Name: | ImeOutlookAddIn.15 |
Value: 030000000F00000000000000000000000000000000000000 | |||
| (PID) Process: | (6396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete value | Name: | c, |
Value: 挠, | |||
| (PID) Process: | (6396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6396 |
| Operation: | write | Name: | 0 |
Value: 0B0E10D6F26FACF3F125438831DA7D62885B80230046ECE8ECA8BFF1D3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E226167744D4D376D6E37724E714D64446A3454702F5567414E3877506264464A494D5A41376266396E6D7A383D22CA0D4201A200C2190000C50E8908C91003783634C511FC31D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
Executable files
0
Suspicious files
10
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6396 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\5EE1F3CE-964F-40C4-87E8-F7B0D612CD23 | xml | |
MD5:9718F778D4B8E8DDA63961CAA61896B2 | SHA256:A56D26AE788DE9CAFB5CBB06ED024B08A73A2573695DC1AD5389A597A3BC1430 | |||
| 6396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:1A33545DA1F77C080E3BD92BD3E5CCA0 | SHA256:4DEC253C0E3E3CFCDCF718A1E938777A1834A3EE5579783B4196EB64F35900F1 | |||
| 6396 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:2AFE59492B9D9C5891CA80E5383D084E | SHA256:45A4ACEF3B5E0E1163054E74AD1C8DC78F7C3638EC86F8C8D31E81FD4BDD1C30 | |||
| 6396 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:0EAABCA061A20987CC561D20AC9F69D5 | SHA256:CAC6243ABCB74EEC149A1CBD57FD3FD5E379579AF1BD78CFDDBE1B1EEF710FA4 | |||
| 6396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:B94BC53E8E266F935D3E16FFC31FF83D | SHA256:7EE5DC50B052D9D1BAF2DB798E8AAF519C163FE2C394177116B4F42992E69FEF | |||
| 6396 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:A35A9D1000EC1C053A70A34B8DB14562 | SHA256:AE0AD792325945A4C58B0081A664157A819CEE054CD42AAD780E594BD905FD4F | |||
| 6396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6396 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:30D789B35D3BD299A14928813B7E44D4 | SHA256:5711DB392F67108217AC88CF7DAF5DC837BEFD256E7E5B64F598CC59B6D08A6D | |||
| 6396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_40.ttf | binary | |
MD5:4296A064B917926682E7EED650D4A745 | SHA256:E04E41C74D6C78213BA1588BACEE64B42C0EDECE85224C474A714F39960D8083 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
44
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
900 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
900 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6628 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
900 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
900 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |