| File name: | HyperHide.zip |
| Full analysis: | https://app.any.run/tasks/92f668d4-bd33-4988-8ad8-e548d1d59bad |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2024, 01:14:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | C9718E166D36B811B430A6D0E1227F38 |
| SHA1: | 91BCE80F2EE6DF1CFF2CF533049F630E7B2A5770 |
| SHA256: | D7A5C3C1340AA5CFA233064890DA2FC2B3AFDF226C9FCA140D5D0591D9228186 |
| SSDEEP: | 49152:CtbauM8rWslVgPi6+NiGXQ44Axqs4ZZpYKfbm4SLaOLRkjtnxeXsqgdOc66KuL2+:Ctbaf8rWHi6+AGTxfKwKf6W7txeXLgxh |
MALICIOUS
No malicious indicators.SUSPICIOUS
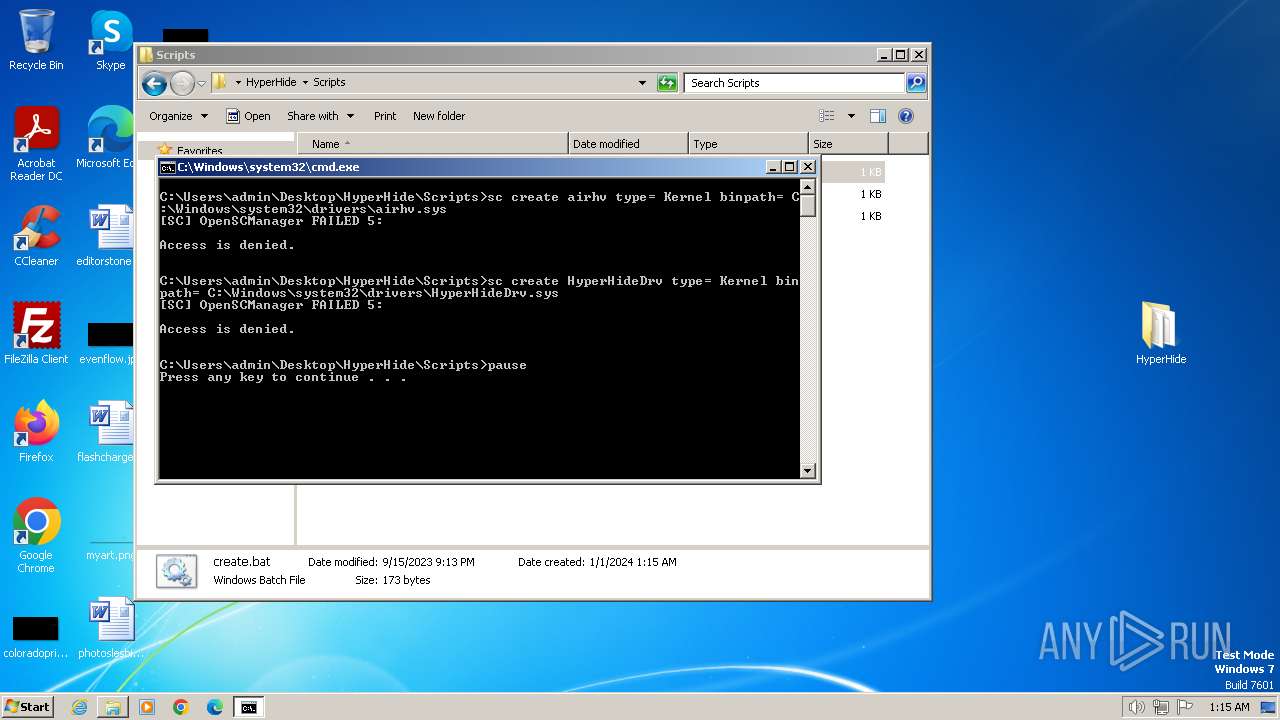
Starts SC.EXE for service management
- cmd.exe (PID: 696)
- cmd.exe (PID: 552)
- cmd.exe (PID: 1748)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 2040)
INFO
Manual execution by a user
- cmd.exe (PID: 696)
- cmd.exe (PID: 552)
- rundll32.exe (PID: 920)
- cmd.exe (PID: 1748)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:09:15 22:13:40 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | HyperHide/ |
Total processes
57
Monitored processes
11
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
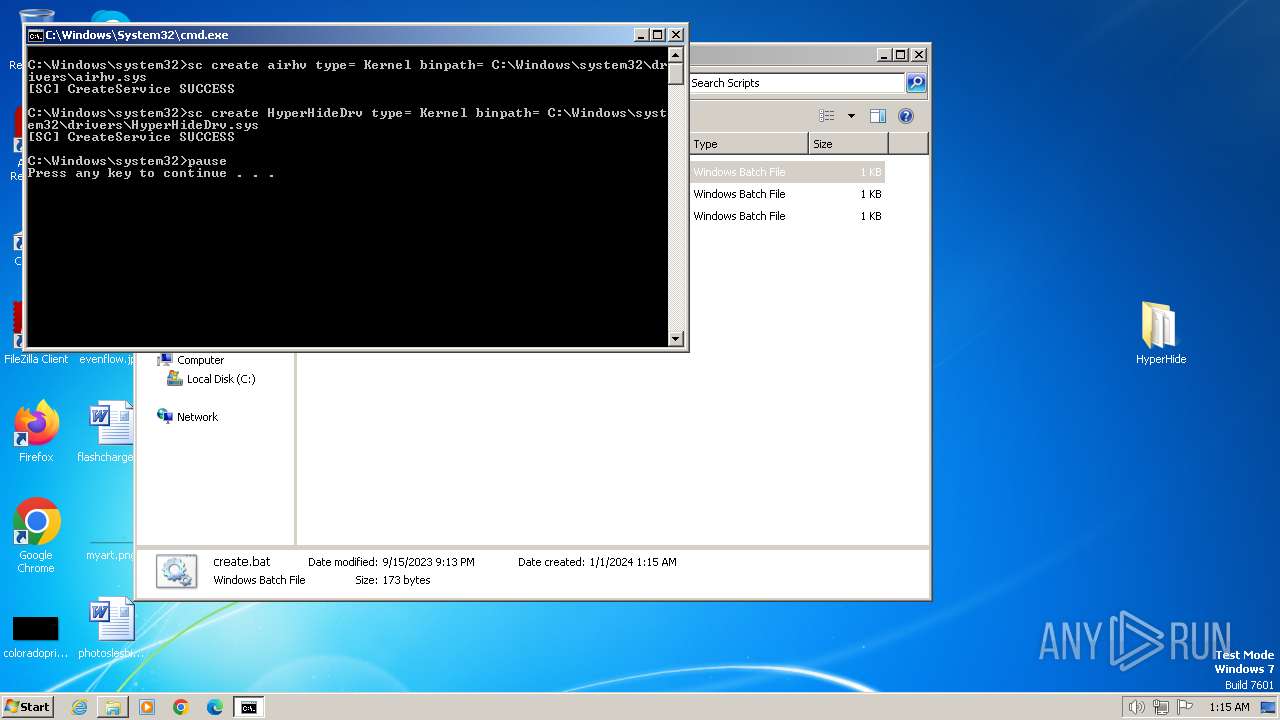
| 552 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\HyperHide\Scripts\on.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 696 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\HyperHide\Scripts\create.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 712 | sc create airhv type= Kernel binpath= C:\Windows\system32\drivers\airhv.sys | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 920 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\HyperHideDrv.sys | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
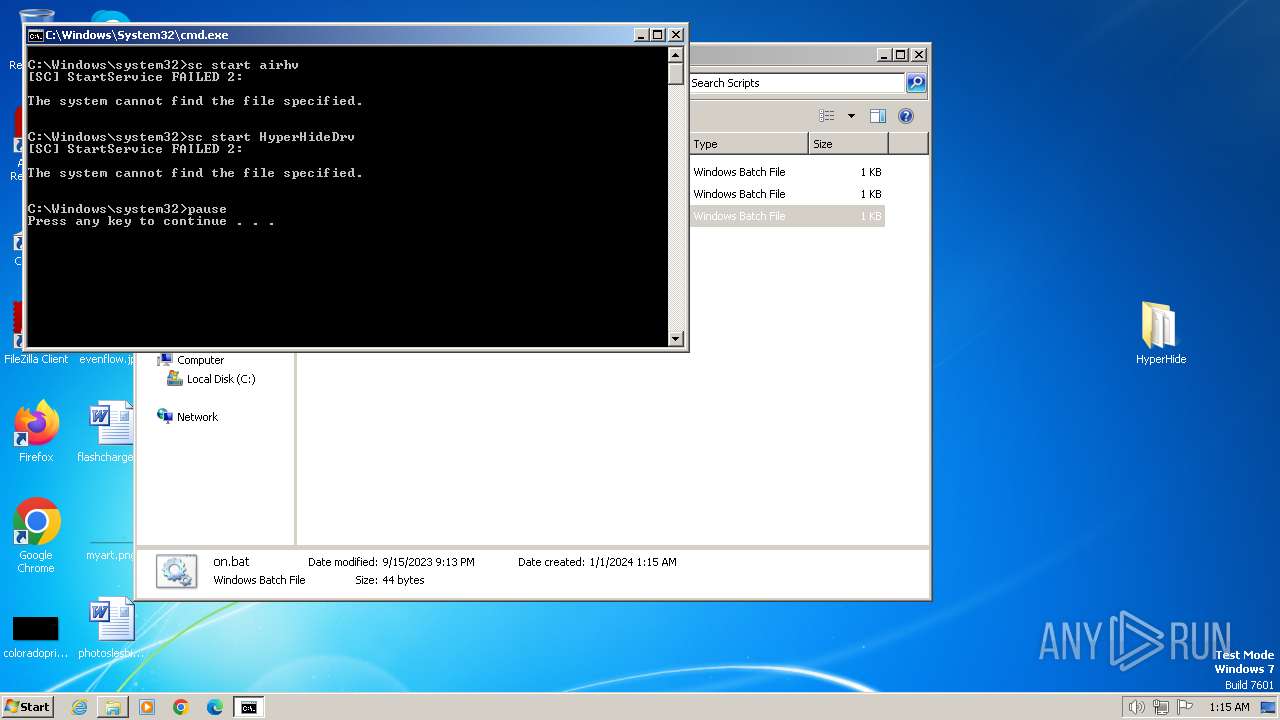
| 984 | sc start airhv | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1748 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\HyperHide\Scripts\create.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1816 | sc create HyperHideDrv type= Kernel binpath= C:\Windows\system32\drivers\HyperHideDrv.sys | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1904 | sc start HyperHideDrv | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2040 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\HyperHide.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2328 | sc create HyperHideDrv type= Kernel binpath= C:\Windows\system32\drivers\HyperHideDrv.sys | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 129
Read events
1 108
Write events
21
Delete events
0
Modification events
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
4
Suspicious files
4
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2040.20607\HyperHide\HyperHide.pdb | binary | |
MD5:D4FF8FF7EF150E12026ECB67F7DC943E | SHA256:8631053EF0E4A8E06CF8AC7854E6C1559EA8ECAD0AB3D00B96A7AE040AFAF3F8 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2040.20607\HyperHide\HyperHide.dp64 | executable | |
MD5:9648EFDF78B9D44C1BCC5C08BC588262 | SHA256:255A8F165CA26363662E892E65C2C50011DEF78190F65F6882A52940E3BFCB85 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2040.20607\HyperHide\HyperHide.ini | ini | |
MD5:0FCECAB18B898952FA9D8259F9D6340C | SHA256:A69D29053EFA138F9776A32FDEAEA9D7429CB54B53A3B4889BB02826C2428429 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2040.20607\HyperHide\airhv.pdb | binary | |
MD5:BB04E3FE57E24ABE6F9BFD5C1D69609F | SHA256:96A7703555C0A2C70A09A205EEAF57A7F198AD95F658CB2FF2BFBC3B0B552668 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2040.20607\HyperHide\airhv.sys | executable | |
MD5:E7CA735A5852D7DBA3C08176E27A217E | SHA256:D636D48E126289571005BF550F085081E0F49FDBAB5A84BE603481D56BAA7E84 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2040.20607\HyperHide\Scripts\off.bat | text | |
MD5:D28BE857ECF932BC9F128F9545E27247 | SHA256:321759A19E0326CE38891D416F7B50923A818756629DDB891C8F6236CCA39BCF | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2040.20607\HyperHide\HyperHide32.pdb | binary | |
MD5:52137D0B273770DCD97D010B127C2988 | SHA256:CFDDF423B991B3D40C7DA80762861CA5FBE1F878EB4DDF321BE682844BEEE320 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2040.20607\HyperHide\Scripts\on.bat | text | |
MD5:7CC3ECE390B8D498E03A839C166CC444 | SHA256:6E40EE16459A2CBFF20F0FEFA668B07D9519823E9A856CF516642DE1F23B088E | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2040.20607\HyperHide\HyperHideDrv.pdb | binary | |
MD5:C4435AA6C177F81F91DA88449E0C0B14 | SHA256:03D2BE798B4ACBA6DEF441B066B3A1F4BBB83FA5C8B87F3BEB91A4CA95792338 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2040.20607\HyperHide\HyperHideDrv.sys | executable | |
MD5:31C8F35BF424C553D453EEFDF9F5E3CD | SHA256:21636BFAE52FB93E15AF1FA98A63A78A2D3A4F4C454D634E40DFD496B8FBC84F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |