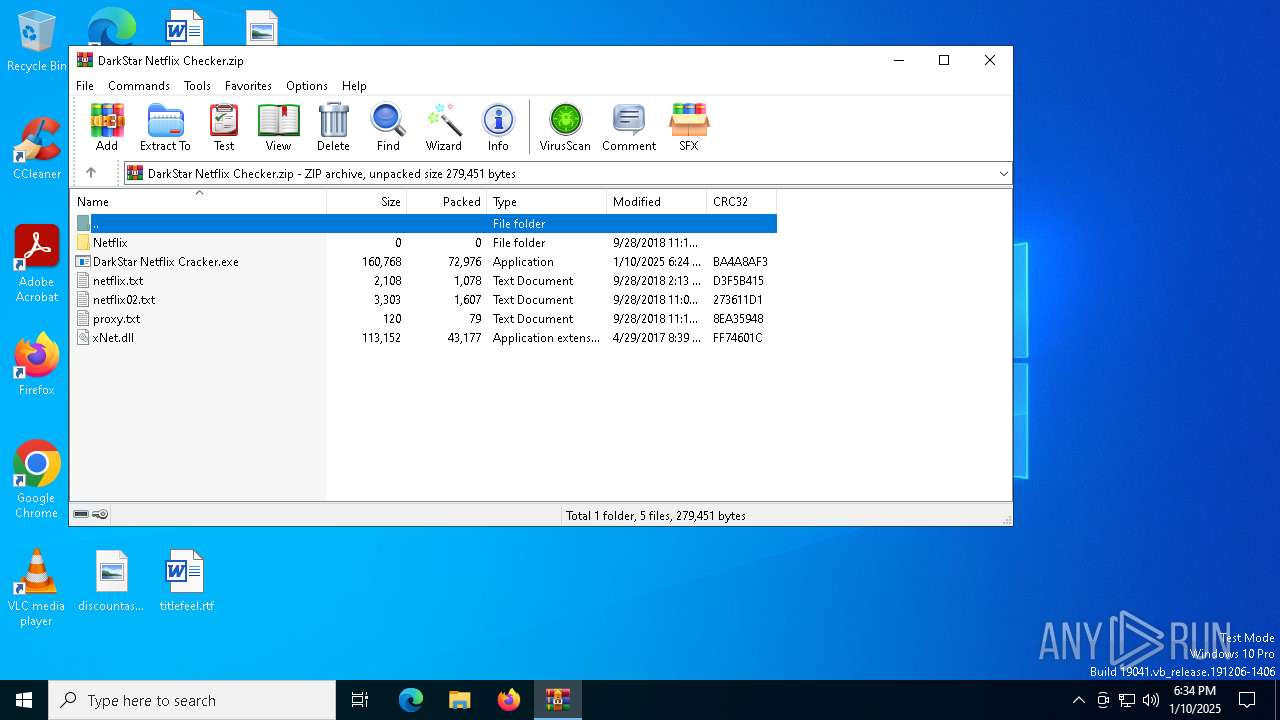
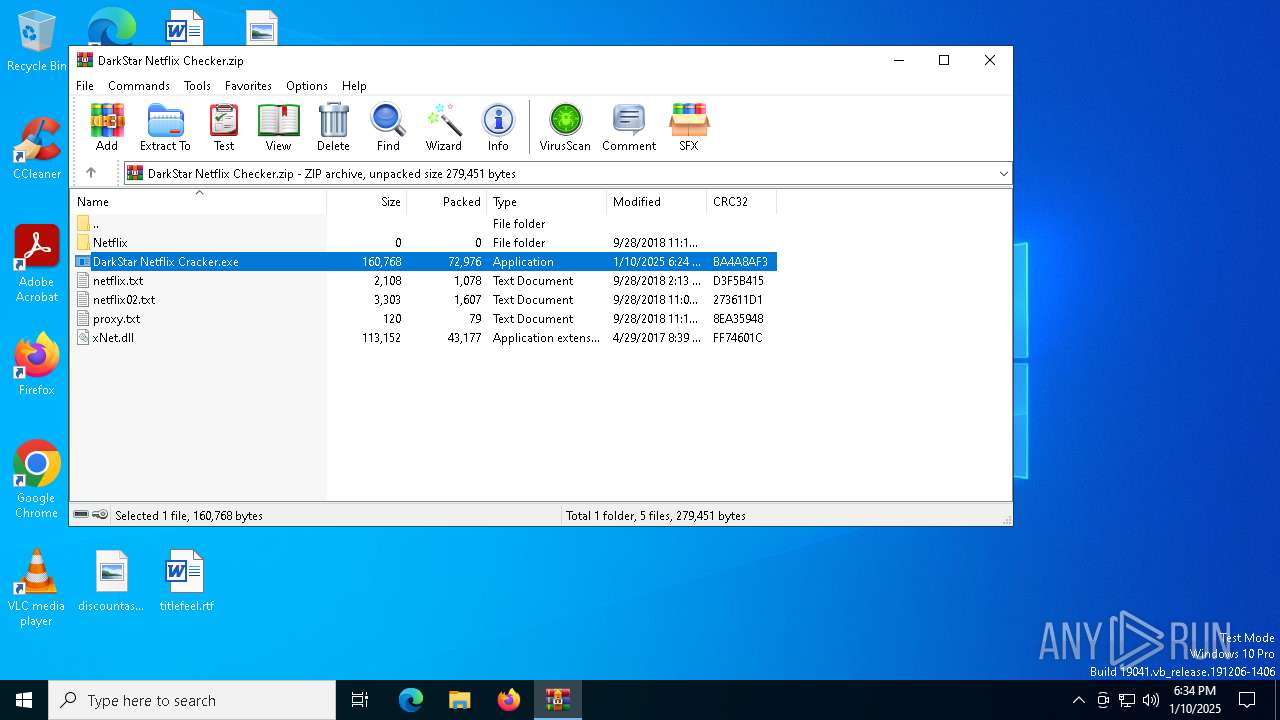
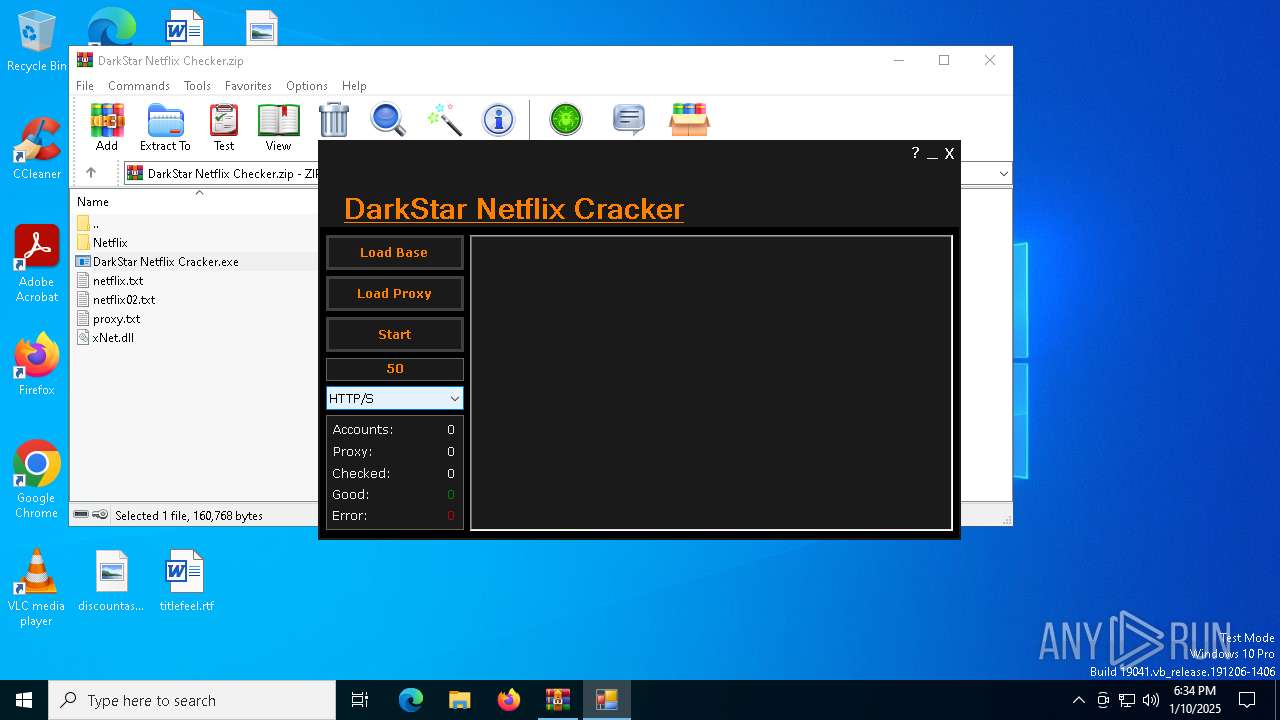
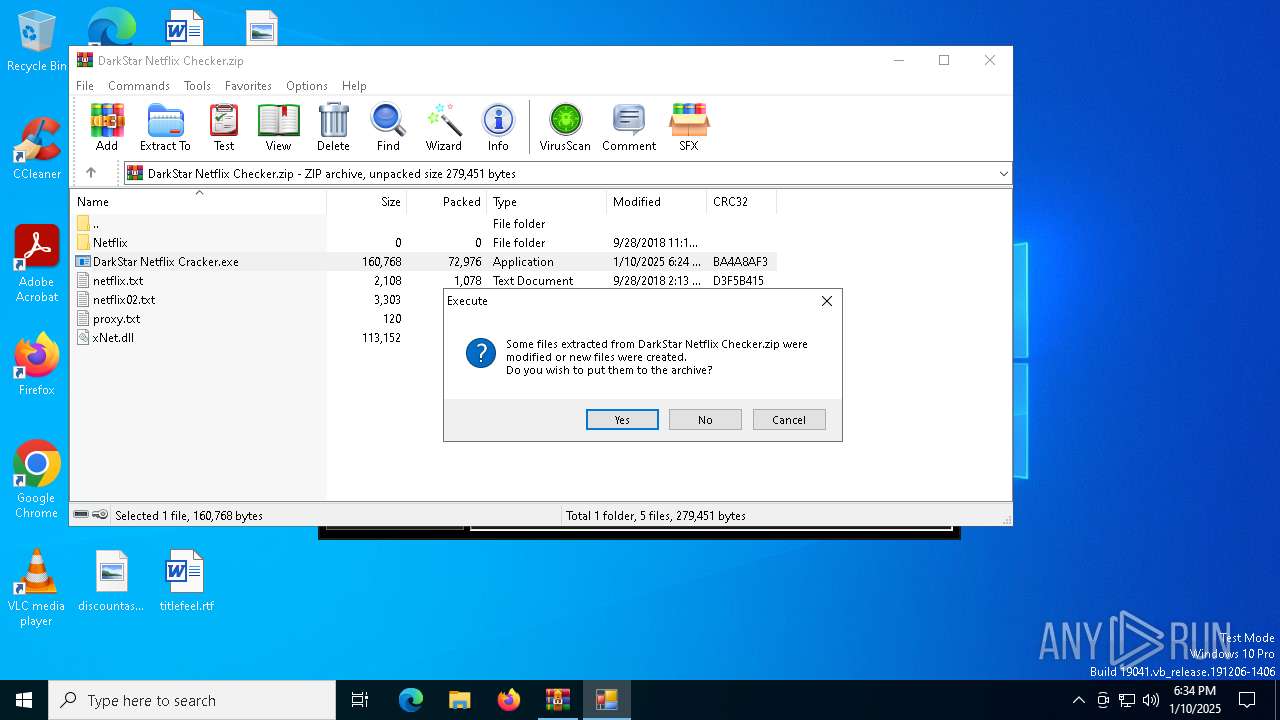
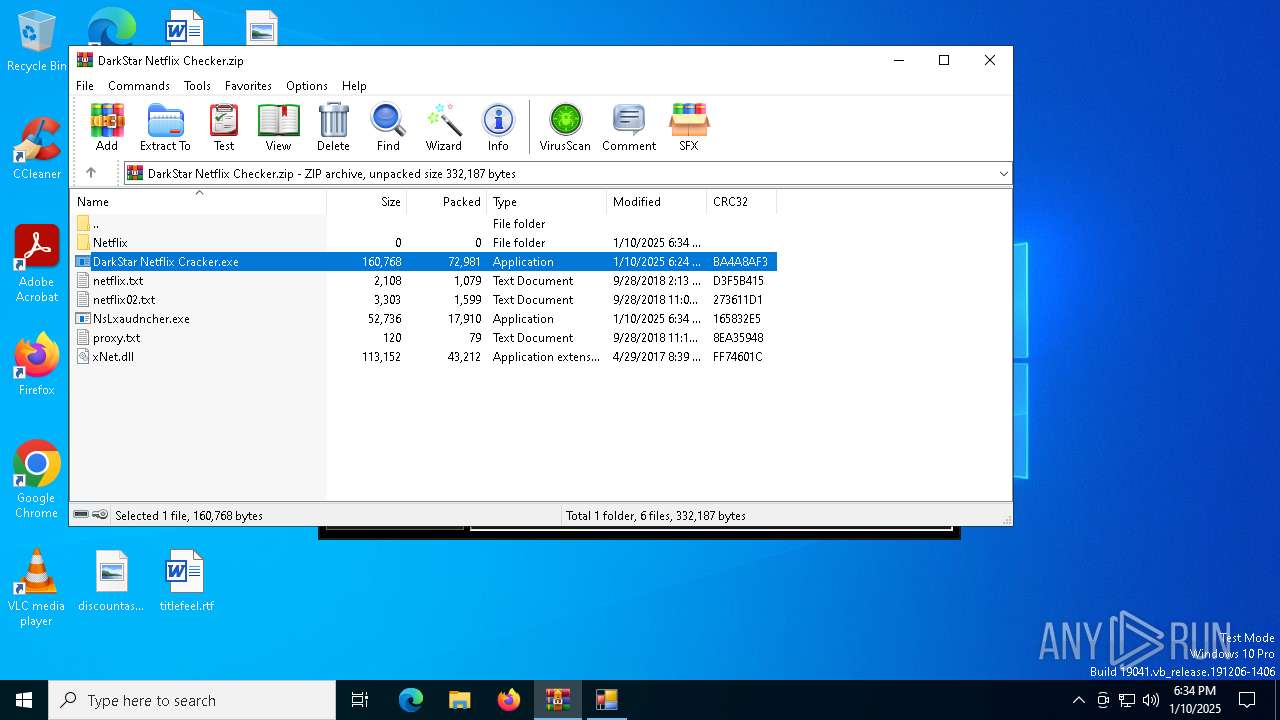
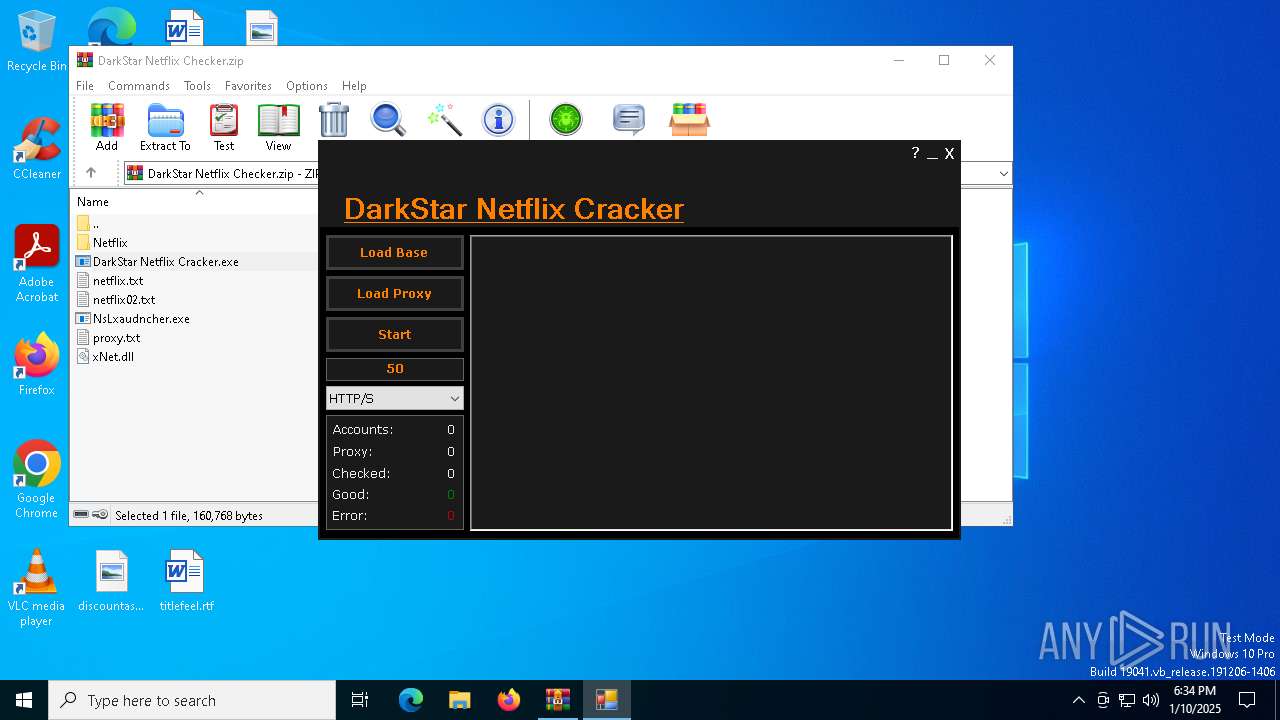
| File name: | DarkStar Netflix Checker.zip |
| Full analysis: | https://app.any.run/tasks/3cb6021b-c5d1-46a2-95c5-fb7739b5191e |
| Verdict: | Malicious activity |
| Analysis date: | January 10, 2025, 18:34:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 98CB799533E1F7958AF80589BD894FAB |
| SHA1: | 5726213A6F88D61401442D73C8A60F5D66C55B2F |
| SHA256: | D79C6C2738A93BC5D12F493508FE51CF2E1800163B7328E5AEF265CA46006FDE |
| SSDEEP: | 3072:3DYNOhAQwv7x0RzS1EHguJIBOJbFRLREpamGmpt0vH/X4:3DgOu1szSkyAfBmRz0vv4 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2600)
Changes the autorun value in the registry
- audiodg.exe (PID: 6780)
- wixndowsapps.exe (PID: 6712)
- msiexec.exe (PID: 6768)
- explorer.exe (PID: 4488)
- svchost.exe (PID: 6756)
Application was injected by another process
- explorer.exe (PID: 4488)
Runs injected code in another process
- svchost.exe (PID: 6756)
SUSPICIOUS
Executable content was dropped or overwritten
- wixndowsapps.exe (PID: 6712)
- DarkStar Netflix Cracker.exe (PID: 6692)
Connects to the server without a host name
- svchost.exe (PID: 6756)
- explorer.exe (PID: 4488)
Process drops legitimate windows executable
- DarkStar Netflix Cracker.exe (PID: 6692)
- wixndowsapps.exe (PID: 6712)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2600)
Reads security settings of Internet Explorer
- svchost.exe (PID: 6756)
- explorer.exe (PID: 4488)
Checks supported languages
- NsLxaudncher.exe (PID: 6720)
- wixndowsapps.exe (PID: 6712)
- DarkStar Netflix Cracker.exe (PID: 6692)
The sample compiled with english language support
- wixndowsapps.exe (PID: 6712)
- DarkStar Netflix Cracker.exe (PID: 6692)
Reads the computer name
- NsLxaudncher.exe (PID: 6720)
Checks proxy server information
- svchost.exe (PID: 6756)
- explorer.exe (PID: 4488)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2600)
Create files in a temporary directory
- NsLxaudncher.exe (PID: 6720)
Reads the machine GUID from the registry
- NsLxaudncher.exe (PID: 6720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:09:27 19:13:46 |
| ZipCRC: | 0xd3f5b415 |
| ZipCompressedSize: | 1078 |
| ZipUncompressedSize: | 2108 |
| ZipFileName: | netflix.txt |
Total processes
132
Monitored processes
8
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2600 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\DarkStar Netflix Checker.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4488 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6692 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2600.37351\DarkStar Netflix Cracker.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2600.37351\DarkStar Netflix Cracker.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6712 | "C:\Users\admin\AppData\Roaming\wixndowsapps.exe" | C:\Users\admin\AppData\Roaming\wixndowsapps.exe | DarkStar Netflix Cracker.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: System Exit code: 0 Version: 2.0.0.1 Modules
| |||||||||||||||
| 6720 | "NsLxaudncher.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2600.37351\NsLxaudncher.exe | — | DarkStar Netflix Cracker.exe | |||||||||||
User: admin Company: Samad.Dz Integrity Level: MEDIUM Description: Netflix.com Checker 1.1 Version: 1.1.0.0 Modules
| |||||||||||||||
| 6756 | "C:\WINDOWS\system32\svchost.exe" | C:\Windows\System32\svchost.exe | wixndowsapps.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6768 | "C:\WINDOWS\system32\msiexec.exe" | C:\Windows\System32\msiexec.exe | wixndowsapps.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6780 | "C:\WINDOWS\system32\audiodg.exe" | C:\Windows\System32\audiodg.exe | wixndowsapps.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Audio Device Graph Isolation Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 498
Read events
3 454
Write events
42
Delete events
2
Modification events
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DarkStar Netflix Checker.zip | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000502F6 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (6756) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
5
Suspicious files
3
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4488 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 6712 | wixndowsapps.exe | C:\Users\admin\AppData\Roaming\2F33566DA0B91573532102\2F33566DA0B91573532102.exe | executable | |
MD5:3647F708A719CB186898C4697077CE73 | SHA256:ACC042ACB2862881C187476C7D4544B54BA76855C2A4688B98A8E6E82628F03A | |||
| 2600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2600.37351\netflix.txt | text | |
MD5:3EE1FF8651B31DDA2F4FD144939BD1A1 | SHA256:D5A267E2249A59BE7DE945BDE82C436566E52E12D83382D983D02E6DAC64FC36 | |||
| 2600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rzi_2600.37993 | compressed | |
MD5:FEAE1FC365F21660AF3D808821FD023F | SHA256:FA7390097256B0615496AFA6E7834F58FDC3573FBB64CF917FBCBCE98F72C391 | |||
| 6692 | DarkStar Netflix Cracker.exe | C:\Users\admin\AppData\Roaming\wixndowsapps.exe | executable | |
MD5:3647F708A719CB186898C4697077CE73 | SHA256:ACC042ACB2862881C187476C7D4544B54BA76855C2A4688B98A8E6E82628F03A | |||
| 2600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2600.37351\proxy.txt | text | |
MD5:1442F22E5C8CF0F8BE8D2649189A652D | SHA256:E081176F579D6673EF45D0431006FEED9B3FCE754AAAC80F8F88DC9B71171639 | |||
| 2600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2600.37351\DarkStar Netflix Cracker.exe | executable | |
MD5:3F7FCAA3F88057C2800BB7C3C5102919 | SHA256:C388DD2F5E8EB725243AE8A98B72B43892077A099B1047D94829B8D3D368B551 | |||
| 2600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2600.37351\xNet.dll | executable | |
MD5:AC1DCEDDBC66A1AB7915AC9931F0CFEC | SHA256:CC949931EF9533ADCED83F3D58862E9732E5DB7AD17B5FD4CB9D209A99EDB592 | |||
| 2600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DarkStar Netflix Checker.zip | compressed | |
MD5:FEAE1FC365F21660AF3D808821FD023F | SHA256:FA7390097256B0615496AFA6E7834F58FDC3573FBB64CF917FBCBCE98F72C391 | |||
| 2600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2600.37351\netflix02.txt | text | |
MD5:97D8BA14AAC9BBFA39C3FEF209B70582 | SHA256:4F551A8FDD9462AFD58ABCB50177F33A304C441D9C4BEB7E3007B452491AF0AE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
26
DNS requests
8
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4488 | explorer.exe | GET | 200 | 185.81.68.147:80 | http://185.81.68.147/bin/bot64.bin | unknown | — | — | malicious |
6756 | svchost.exe | GET | 200 | 185.81.68.147:80 | http://185.81.68.147/bin/bot64.bin | unknown | — | — | malicious |
4488 | explorer.exe | POST | 200 | 185.81.68.147:80 | http://185.81.68.147/VzCAHn.php?2F33566DA0B91573532102 | unknown | — | — | malicious |
4488 | explorer.exe | POST | 200 | 185.81.68.147:80 | http://185.81.68.147/VzCAHn.php?2F33566DA0B91573532102 | unknown | — | — | malicious |
4488 | explorer.exe | POST | 200 | 185.81.68.147:80 | http://185.81.68.147/VzCAHn.php?2F33566DA0B91573532102 | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4992 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.59:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.48.23.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6756 | svchost.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
6756 | svchost.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
4488 | explorer.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
4488 | explorer.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |