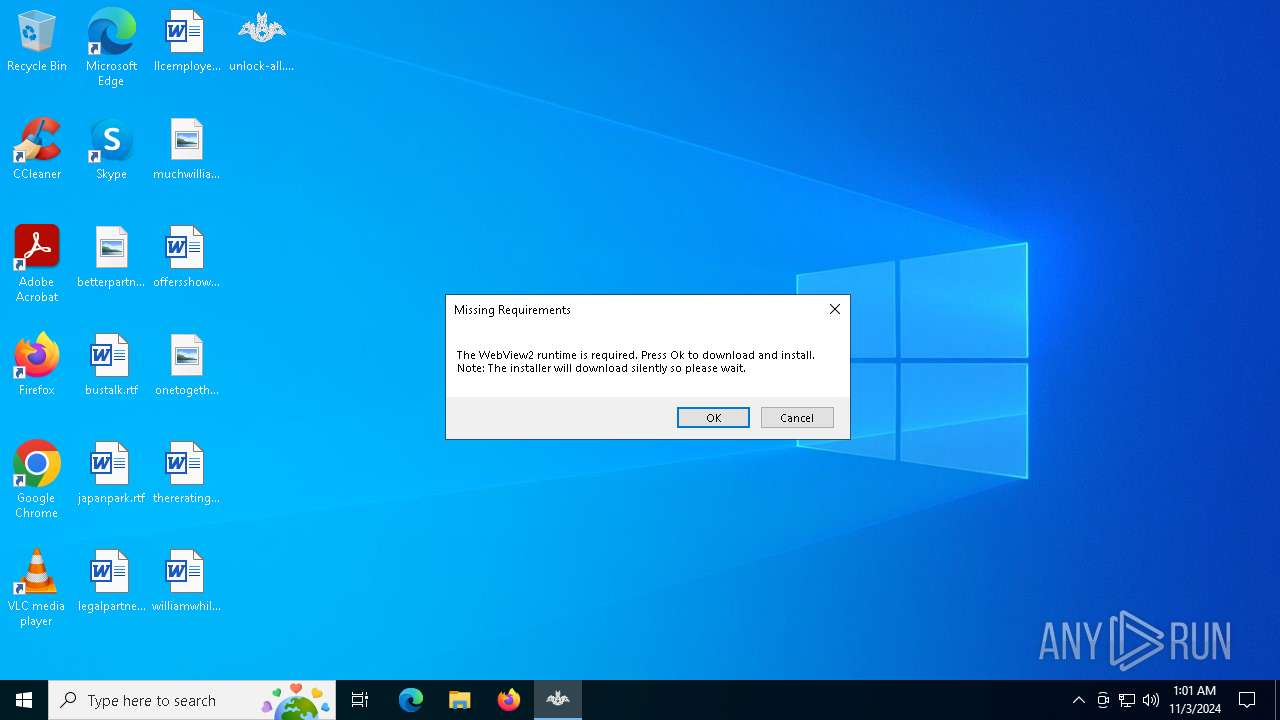
| File name: | unlock-all.exe |
| Full analysis: | https://app.any.run/tasks/09f93893-1d82-40df-bf04-6ee73529affb |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | November 03, 2024, 01:01:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 9 sections |
| MD5: | 3BBD94250371A5B8F88B969767418D70 |
| SHA1: | 19C49800B4F0942AC5E47A1BF6E5C6BE0ED06AC5 |
| SHA256: | D769D0A4F0A159403381A91F2AA1877D10872F2F7569C0B07C7CAA461985783E |
| SSDEEP: | 98304:yhYROXMtgFoKwCf9AwqUegBWEaOhh6iFzIzCFN2VO47GYdof6niJr6yqJjI2stas:tlK1 |
MALICIOUS
DISCORDGRABBER has been detected (YARA)
- unlock-all.exe (PID: 6716)
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 6852)
The DLL Hijacking
- msedgewebview2.exe (PID: 4080)
Actions looks like stealing of personal data
- unlock-all.exe (PID: 6716)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Steals credentials from Web Browsers
- unlock-all.exe (PID: 5420)
SUSPICIOUS
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 6712)
- MicrosoftEdgeUpdate.exe (PID: 6852)
Process drops legitimate windows executable
- unlock-all.exe (PID: 6716)
- MicrosoftEdgeWebview2Setup.exe (PID: 6712)
- MicrosoftEdgeUpdate.exe (PID: 6852)
- MicrosoftEdgeUpdate.exe (PID: 3944)
- MicrosoftEdge_X64_130.0.2849.56.exe (PID: 7116)
- setup.exe (PID: 7080)
Executable content was dropped or overwritten
- unlock-all.exe (PID: 6716)
- MicrosoftEdgeWebview2Setup.exe (PID: 6712)
- MicrosoftEdgeUpdate.exe (PID: 6852)
- MicrosoftEdge_X64_130.0.2849.56.exe (PID: 7116)
- setup.exe (PID: 7080)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 4432)
- MicrosoftEdgeUpdate.exe (PID: 6644)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 3916)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6604)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 6852)
Potential Corporate Privacy Violation
- MicrosoftEdgeUpdate.exe (PID: 3944)
Reads security settings of Internet Explorer
- MicrosoftEdgeUpdate.exe (PID: 3944)
- MicrosoftEdgeUpdate.exe (PID: 6852)
- msedgewebview2.exe (PID: 6396)
Checks Windows Trust Settings
- MicrosoftEdgeUpdate.exe (PID: 3944)
Application launched itself
- setup.exe (PID: 7080)
- msedgewebview2.exe (PID: 6396)
- msedgewebview2.exe (PID: 6940)
- MicrosoftEdgeUpdate.exe (PID: 3944)
- msedgewebview2.exe (PID: 3904)
Creates a software uninstall entry
- setup.exe (PID: 7080)
Searches for installed software
- setup.exe (PID: 7080)
- msedgewebview2.exe (PID: 6396)
Uses WMIC.EXE to obtain operating system information
- unlock-all.exe (PID: 6716)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Uses WMIC.EXE to obtain CPU information
- unlock-all.exe (PID: 6716)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 1344)
- WMIC.exe (PID: 1732)
- WMIC.exe (PID: 2652)
Uses WMIC.EXE to obtain a list of video controllers
- unlock-all.exe (PID: 6716)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Checks for external IP
- svchost.exe (PID: 2172)
- unlock-all.exe (PID: 6716)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 5444)
- WMIC.exe (PID: 4016)
- WMIC.exe (PID: 7060)
Uses WMIC.EXE to obtain Windows Installer data
- unlock-all.exe (PID: 6716)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 5736)
- WMIC.exe (PID: 6024)
- WMIC.exe (PID: 1732)
INFO
Reads the computer name
- unlock-all.exe (PID: 6716)
- MicrosoftEdgeUpdate.exe (PID: 6852)
- MicrosoftEdgeUpdate.exe (PID: 6644)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 3916)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 4432)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6604)
- MicrosoftEdgeUpdate.exe (PID: 6392)
- MicrosoftEdgeUpdate.exe (PID: 4904)
- MicrosoftEdgeUpdate.exe (PID: 3944)
- setup.exe (PID: 7080)
- MicrosoftEdge_X64_130.0.2849.56.exe (PID: 7116)
- MicrosoftEdgeUpdate.exe (PID: 2888)
- msedgewebview2.exe (PID: 6396)
- msedgewebview2.exe (PID: 4080)
- msedgewebview2.exe (PID: 616)
- unlock-all.exe (PID: 5420)
- msedgewebview2.exe (PID: 6940)
- msedgewebview2.exe (PID: 3904)
- unlock-all.exe (PID: 6240)
- msedgewebview2.exe (PID: 5612)
Reads Environment values
- unlock-all.exe (PID: 6716)
- MicrosoftEdgeUpdate.exe (PID: 6392)
- MicrosoftEdgeUpdate.exe (PID: 2888)
- msedgewebview2.exe (PID: 6396)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Create files in a temporary directory
- MicrosoftEdgeWebview2Setup.exe (PID: 6712)
- MicrosoftEdgeUpdate.exe (PID: 6852)
- unlock-all.exe (PID: 6716)
- MicrosoftEdgeUpdate.exe (PID: 3944)
- msedgewebview2.exe (PID: 6396)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Reads the software policy settings
- unlock-all.exe (PID: 6716)
- MicrosoftEdgeUpdate.exe (PID: 6392)
- MicrosoftEdgeUpdate.exe (PID: 3944)
- MicrosoftEdgeUpdate.exe (PID: 2888)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Checks supported languages
- MicrosoftEdgeWebview2Setup.exe (PID: 6712)
- unlock-all.exe (PID: 6716)
- MicrosoftEdgeUpdate.exe (PID: 6852)
- MicrosoftEdgeUpdate.exe (PID: 6644)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 3916)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 4432)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6604)
- MicrosoftEdgeUpdate.exe (PID: 6392)
- MicrosoftEdgeUpdate.exe (PID: 4904)
- MicrosoftEdgeUpdate.exe (PID: 3944)
- MicrosoftEdge_X64_130.0.2849.56.exe (PID: 7116)
- setup.exe (PID: 7080)
- setup.exe (PID: 3004)
- MicrosoftEdgeUpdate.exe (PID: 2888)
- msedgewebview2.exe (PID: 6396)
- msedgewebview2.exe (PID: 5332)
- msedgewebview2.exe (PID: 4080)
- msedgewebview2.exe (PID: 616)
- msedgewebview2.exe (PID: 1028)
- msedgewebview2.exe (PID: 6492)
- msedgewebview2.exe (PID: 6824)
- msedgewebview2.exe (PID: 7040)
- msedgewebview2.exe (PID: 4996)
- msedgewebview2.exe (PID: 3900)
- msedgewebview2.exe (PID: 1500)
- msedgewebview2.exe (PID: 7148)
- msedgewebview2.exe (PID: 6940)
- unlock-all.exe (PID: 5420)
- msedgewebview2.exe (PID: 6944)
- msedgewebview2.exe (PID: 944)
- msedgewebview2.exe (PID: 5324)
- unlock-all.exe (PID: 6240)
- msedgewebview2.exe (PID: 3904)
- msedgewebview2.exe (PID: 1248)
- msedgewebview2.exe (PID: 4128)
- msedgewebview2.exe (PID: 7012)
- msedgewebview2.exe (PID: 2652)
- msedgewebview2.exe (PID: 5612)
- msedgewebview2.exe (PID: 4004)
- msedgewebview2.exe (PID: 7104)
- msedgewebview2.exe (PID: 3792)
Application based on Golang
- unlock-all.exe (PID: 6716)
Reads the machine GUID from the registry
- unlock-all.exe (PID: 6716)
- MicrosoftEdgeUpdate.exe (PID: 3944)
- msedgewebview2.exe (PID: 6396)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
- msedgewebview2.exe (PID: 5612)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 6852)
- MicrosoftEdgeUpdate.exe (PID: 3944)
- setup.exe (PID: 7080)
- setup.exe (PID: 3004)
- MicrosoftEdge_X64_130.0.2849.56.exe (PID: 7116)
- msedgewebview2.exe (PID: 6396)
- msedgewebview2.exe (PID: 5332)
- msedgewebview2.exe (PID: 616)
- msedgewebview2.exe (PID: 5612)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 6852)
- setup.exe (PID: 7080)
- msedgewebview2.exe (PID: 6396)
- msedgewebview2.exe (PID: 6492)
- msedgewebview2.exe (PID: 6824)
- msedgewebview2.exe (PID: 7148)
- msedgewebview2.exe (PID: 7040)
- msedgewebview2.exe (PID: 4996)
- msedgewebview2.exe (PID: 3900)
- msedgewebview2.exe (PID: 1500)
- msedgewebview2.exe (PID: 6944)
- msedgewebview2.exe (PID: 5324)
- msedgewebview2.exe (PID: 4128)
- msedgewebview2.exe (PID: 2652)
Checks proxy server information
- MicrosoftEdgeUpdate.exe (PID: 6392)
- MicrosoftEdgeUpdate.exe (PID: 3944)
- MicrosoftEdgeUpdate.exe (PID: 2888)
- msedgewebview2.exe (PID: 6396)
Sends debugging messages
- msedgewebview2.exe (PID: 6396)
- unlock-all.exe (PID: 6716)
- unlock-all.exe (PID: 5420)
- msedgewebview2.exe (PID: 6940)
- msedgewebview2.exe (PID: 3904)
- msedgewebview2.exe (PID: 1248)
- unlock-all.exe (PID: 6240)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1344)
- WMIC.exe (PID: 1588)
- WMIC.exe (PID: 5444)
- WMIC.exe (PID: 5736)
- WMIC.exe (PID: 1732)
- WMIC.exe (PID: 4016)
- WMIC.exe (PID: 6024)
- WMIC.exe (PID: 3928)
- WMIC.exe (PID: 2652)
- WMIC.exe (PID: 7060)
- WMIC.exe (PID: 1732)
- WMIC.exe (PID: 1880)
Drops encrypted VBS script (Microsoft Script Encoder)
- unlock-all.exe (PID: 6716)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Drops encrypted JS script (Microsoft Script Encoder)
- unlock-all.exe (PID: 6716)
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Manual execution by a user
- unlock-all.exe (PID: 5420)
- unlock-all.exe (PID: 6240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (53.4) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (35.5) |
| .exe | | | Win32 Executable (generic) (5.8) |
| .exe | | | Generic Win/DOS Executable (2.5) |
| .exe | | | DOS Executable Generic (2.5) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 6632960 |
| InitializedDataSize: | 886272 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x78640 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.2.9.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Super Market |
| CompanyName: | Super Market |
| FileDescription: | procutils |
| LegalCopyright: | Super Market |
| ProductName: | procutils |
| ProductVersion: | 4.2.9 |
Total processes
207
Monitored processes
67
Malicious processes
11
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\130.0.2849.56\msedgewebview2.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --string-annotations=is-enterprise-managed=no --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Roaming\unlock-all.exe\EBWebView" --webview-exe-name=unlock-all.exe --webview-exe-version=4.2.9 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=2 --field-trial-handle=1852,i,12284734646854075519,12853159661726061452,262144 --disable-features=msSmartScreenProtection --variations-seed-version --mojo-platform-channel-handle=2100 /prefetch:3 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\130.0.2849.56\msedgewebview2.exe | msedgewebview2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge WebView2 Version: 130.0.2849.56 Modules
| |||||||||||||||
| 944 | "C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\130.0.2849.56\msedgewebview2.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --string-annotations=is-enterprise-managed=no --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Roaming\unlock-all.exe\EBWebView" --webview-exe-name=unlock-all.exe --webview-exe-version=4.2.9 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=2 --field-trial-handle=5456,i,12284734646854075519,12853159661726061452,262144 --disable-features=msSmartScreenProtection --variations-seed-version --mojo-platform-channel-handle=5500 /prefetch:8 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\130.0.2849.56\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Exit code: 0 Version: 130.0.2849.56 Modules
| |||||||||||||||
| 1028 | "C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\130.0.2849.56\msedgewebview2.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --string-annotations=is-enterprise-managed=no --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Roaming\unlock-all.exe\EBWebView" --webview-exe-name=unlock-all.exe --webview-exe-version=4.2.9 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=2 --field-trial-handle=2308,i,12284734646854075519,12853159661726061452,262144 --disable-features=msSmartScreenProtection --variations-seed-version --mojo-platform-channel-handle=2416 /prefetch:8 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\130.0.2849.56\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Version: 130.0.2849.56 Modules
| |||||||||||||||
| 1248 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\130.0.2849.56\msedgewebview2.exe --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Roaming\unlock-all.exe\EBWebView /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Roaming\unlock-all.exe\EBWebView\Crashpad --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=130.0.6723.70 --annotation=exe=C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\130.0.2849.56\msedgewebview2.exe --annotation=plat=Win64 "--annotation=prod=Edge WebView2" --annotation=ver=130.0.2849.56 --initial-client-data=0x188,0x18c,0x190,0xec,0x198,0x7ffbca114dc0,0x7ffbca114dcc,0x7ffbca114dd8 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\130.0.2849.56\msedgewebview2.exe | msedgewebview2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge WebView2 Exit code: 0 Version: 130.0.2849.56 Modules
| |||||||||||||||
| 1344 | wmic os get Caption | C:\Windows\System32\wbem\WMIC.exe | — | unlock-all.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1500 | "C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\130.0.2849.56\msedgewebview2.exe" --type=renderer --string-annotations=is-enterprise-managed=no --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Roaming\unlock-all.exe\EBWebView" --webview-exe-name=unlock-all.exe --webview-exe-version=4.2.9 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=2 --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --js-flags="--harmony-weak-refs-with-cleanup-some --expose-gc --ms-user-locale=" --field-trial-handle=4508,i,12284734646854075519,12853159661726061452,262144 --disable-features=msSmartScreenProtection --variations-seed-version --mojo-platform-channel-handle=4540 /prefetch:1 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\130.0.2849.56\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Exit code: 0 Version: 130.0.2849.56 Modules
| |||||||||||||||
| 1588 | wmic cpu get Name | C:\Windows\System32\wbem\WMIC.exe | — | unlock-all.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1732 | wmic os get Caption | C:\Windows\System32\wbem\WMIC.exe | — | unlock-all.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1732 | wmic csproduct get UUID | C:\Windows\System32\wbem\WMIC.exe | — | unlock-all.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
28 016
Read events
25 692
Write events
2 256
Delete events
68
Modification events
| (PID) Process: | (6852) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | delete value | Name: | eulaaccepted |
Value: | |||
| (PID) Process: | (6852) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | path |
Value: C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | |||
| (PID) Process: | (6852) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | UninstallCmdLine |
Value: "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /uninstall | |||
| (PID) Process: | (6852) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{F3C4FE00-EFD5-403B-9569-398A20F1BA4A} |
| Operation: | write | Name: | pv |
Value: 1.3.195.25 | |||
| (PID) Process: | (6852) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{F3C4FE00-EFD5-403B-9569-398A20F1BA4A} |
| Operation: | write | Name: | name |
Value: Microsoft Edge Update | |||
| (PID) Process: | (6852) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{F3C4FE00-EFD5-403B-9569-398A20F1BA4A} |
| Operation: | write | Name: | pv |
Value: 1.3.195.25 | |||
| (PID) Process: | (6852) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Microsoft Edge Update |
Value: "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.25\MicrosoftEdgeUpdateCore.exe" | |||
| (PID) Process: | (6852) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | edgeupdate_task_name_c |
Value: MicrosoftEdgeUpdateTaskUserS-1-5-21-1693682860-607145093-2874071422-1001Core{D6024317-D3A4-47E3-9554-863757B85C12} | |||
| (PID) Process: | (6852) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | edgeupdate_task_name_ua |
Value: MicrosoftEdgeUpdateTaskUserS-1-5-21-1693682860-607145093-2874071422-1001UA{14A7D062-9E0B-4106-A462-7D5606A3E9B2} | |||
| (PID) Process: | (3916) MicrosoftEdgeUpdateComRegisterShell64.exe | Key: | HKEY_CLASSES_ROOT\CLSID\{81093D63-7825-417B-BFC8-ADC63FA4E53D}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
Executable files
207
Suspicious files
291
Text files
58
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6712 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDC20.tmp\MicrosoftEdgeUpdateOnDemand.exe | executable | |
MD5:64309E5DDEF493FCD044041E31B44494 | SHA256:43F54C9E85C0BBC86F9AACDAB40682E330D6D58BAD89A400FD6F609F72285FE2 | |||
| 6712 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDC20.tmp\MicrosoftEdgeComRegisterShellARM64.exe | executable | |
MD5:D16DEAB532387BB817FCAA50B9BD8972 | SHA256:BA27CA798445934D02BE72A0FAA198539DFA38E922C06BDD93EB3070EE12311B | |||
| 6712 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDC20.tmp\psuser_64.dll | executable | |
MD5:16CB0B937BE08D65067B1A4F755E89A1 | SHA256:54467B33C5A347E7A3CE1AD3EA0E06F59F7A46132C7DCA6E38BB56F48D74CD8D | |||
| 6712 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDC20.tmp\MicrosoftEdgeUpdateBroker.exe | executable | |
MD5:A79F7F8BC9B419E4B18316B2770747E1 | SHA256:1856E95BA698594D5DF6A589DEA635C114762BF40A7B43160069E47FFE5080F6 | |||
| 6712 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDC20.tmp\psmachine_64.dll | executable | |
MD5:D3CFF1EF3EF23D314C8736EDCE0D8E6D | SHA256:48937A055CE355CE8CC3E9D12758B2EF065991F163DA7342479292668042270F | |||
| 6712 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDC20.tmp\psmachine.dll | executable | |
MD5:D784C91F463DAF63DB3B0621D2F6530B | SHA256:6941FB408480FD8E5936248310DBF6823F1003D84328CCBF9CA56604B3A6DF52 | |||
| 6712 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDC20.tmp\psmachine_arm64.dll | executable | |
MD5:517D9F4A900BC852A7E5B8C07C65B7FD | SHA256:86305CC725B00D82F049BA4DA267C17FBB8839706058524997039D5834FD1ED4 | |||
| 6712 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDC20.tmp\psuser.dll | executable | |
MD5:0407DC1F6D634CE9B2891656814E77C5 | SHA256:9172E1E9EC6BF144B9B38131FBE8401EB028E5428A890D46C0F45F5AF13F5561 | |||
| 6712 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDC20.tmp\MicrosoftEdgeUpdateComRegisterShell64.exe | executable | |
MD5:8CDA2D501C51F0869A69D5951F2AEC5E | SHA256:208497513FF0C793E6DC0A9935D73DFC37887C875FE00AFF4DFAEB3854054D31 | |||
| 6712 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDC20.tmp\msedgeupdate.dll | executable | |
MD5:8A816664389165F11A9E50FE42671657 | SHA256:09D9F52E86DDD5FB3391D7DD683C42A9FA9D03A2CEEE56B1273CCD42986B4851 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
99
DNS requests
85
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4236 | svchost.exe | GET | 206 | 2.19.126.157:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c12dff9-696d-48d4-bbe8-7d8bdad98e65?P1=1730976752&P2=404&P3=2&P4=HTU5z88Zb7tmilT5ZWa5qePIdOi3kCTuj9%2frJIXxUX7x6D5WwCMsoRLafDXXKrxYh%2bmzSXN6g7jBBXOGSPpDCg%3d%3d | unknown | — | — | whitelisted |
4236 | svchost.exe | GET | 206 | 2.19.126.157:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c12dff9-696d-48d4-bbe8-7d8bdad98e65?P1=1730976752&P2=404&P3=2&P4=HTU5z88Zb7tmilT5ZWa5qePIdOi3kCTuj9%2frJIXxUX7x6D5WwCMsoRLafDXXKrxYh%2bmzSXN6g7jBBXOGSPpDCg%3d%3d | unknown | — | — | whitelisted |
4236 | svchost.exe | GET | 206 | 2.19.126.157:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c12dff9-696d-48d4-bbe8-7d8bdad98e65?P1=1730976752&P2=404&P3=2&P4=HTU5z88Zb7tmilT5ZWa5qePIdOi3kCTuj9%2frJIXxUX7x6D5WwCMsoRLafDXXKrxYh%2bmzSXN6g7jBBXOGSPpDCg%3d%3d | unknown | — | — | whitelisted |
4236 | svchost.exe | GET | 206 | 2.19.126.157:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c12dff9-696d-48d4-bbe8-7d8bdad98e65?P1=1730976752&P2=404&P3=2&P4=HTU5z88Zb7tmilT5ZWa5qePIdOi3kCTuj9%2frJIXxUX7x6D5WwCMsoRLafDXXKrxYh%2bmzSXN6g7jBBXOGSPpDCg%3d%3d | unknown | — | — | whitelisted |
4236 | svchost.exe | GET | 206 | 2.19.126.157:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c12dff9-696d-48d4-bbe8-7d8bdad98e65?P1=1730976752&P2=404&P3=2&P4=HTU5z88Zb7tmilT5ZWa5qePIdOi3kCTuj9%2frJIXxUX7x6D5WwCMsoRLafDXXKrxYh%2bmzSXN6g7jBBXOGSPpDCg%3d%3d | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5740 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6272 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4360 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
msedge.sf.dl.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3944 | MicrosoftEdgeUpdate.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2172 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
6716 | unlock-all.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
2172 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6716 | unlock-all.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
6716 | unlock-all.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
6716 | unlock-all.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2172 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
5420 | unlock-all.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
5420 | unlock-all.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
Process | Message |
|---|---|
msedgewebview2.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Roaming directory exists )
|
unlock-all.exe | Warning: AddWebResourceRequestedFilter without SourceKind parameter is deprecated! It does not behave as expected for iframes.Please use AddWebResourceRequestedFilterWithRequestSourceKinds instead. For more information, please see https://go.microsoft.com/fwlink/?linkid=2286319 |
unlock-all.exe | % |
unlock-all.exe | h |
unlock-all.exe | % |
unlock-all.exe | h |
unlock-all.exe | % |
unlock-all.exe | h |
unlock-all.exe | % |
unlock-all.exe | h |