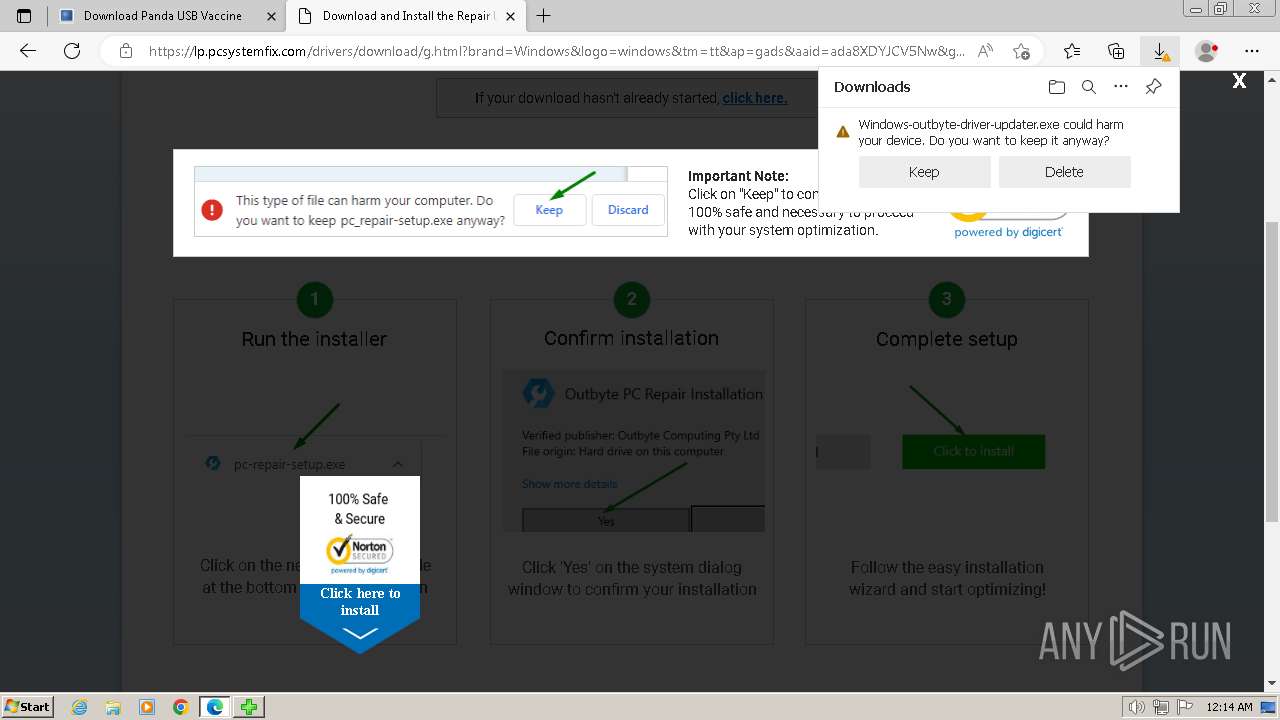
| File name: | Rem-VBSworm_8.0.exe |
| Full analysis: | https://app.any.run/tasks/41fee555-7f7a-4493-9ec9-976c1b98d5b7 |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2024, 00:13:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 4C37021F17E02FB9FDB7DB3287906BD5 |
| SHA1: | 7FEF4A43F70262710127051778E0A50EC7A94E64 |
| SHA256: | D76449A92E9F745FD422B6CF769EB6734DB68AE8DB8517AF959D6809E3403A35 |
| SSDEEP: | 1536:mMhgHa6qFi77jvHyxWKoRF3xTbZYxP5RI8gcg7WCRCfa4cX:mMmHa6Ki77LyHExTlgPPILrrRCi4cX |
MALICIOUS
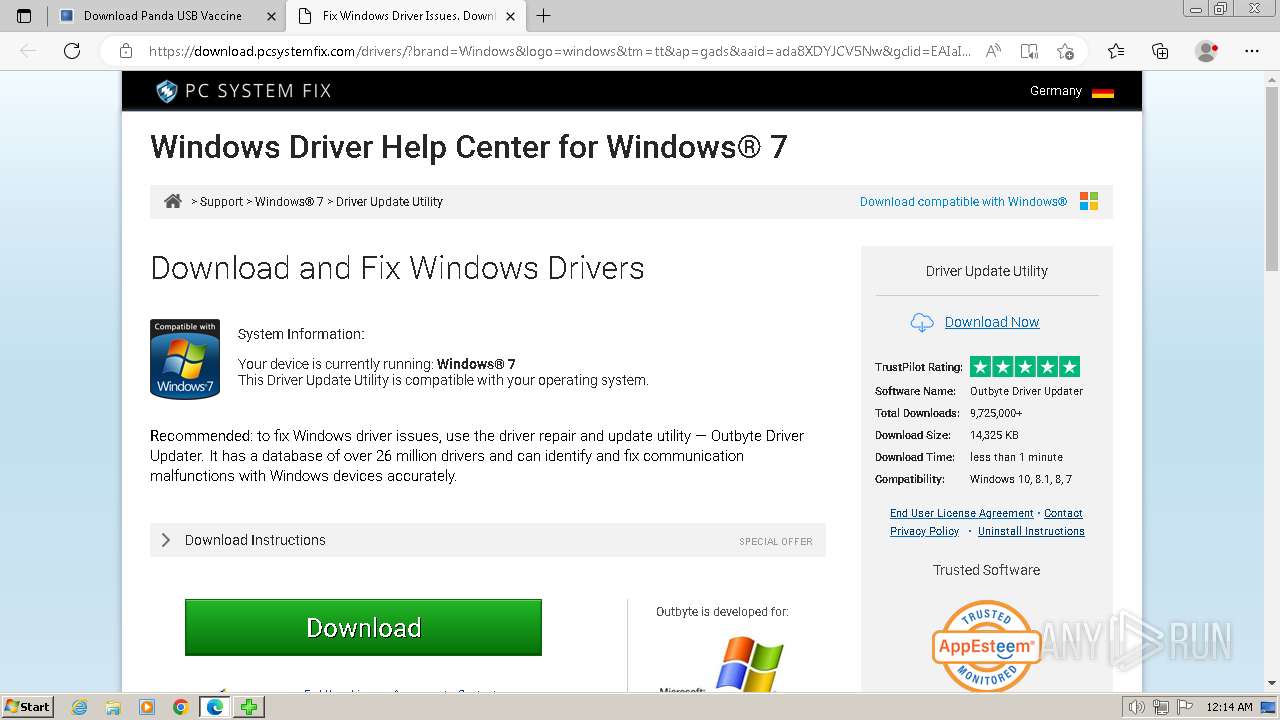
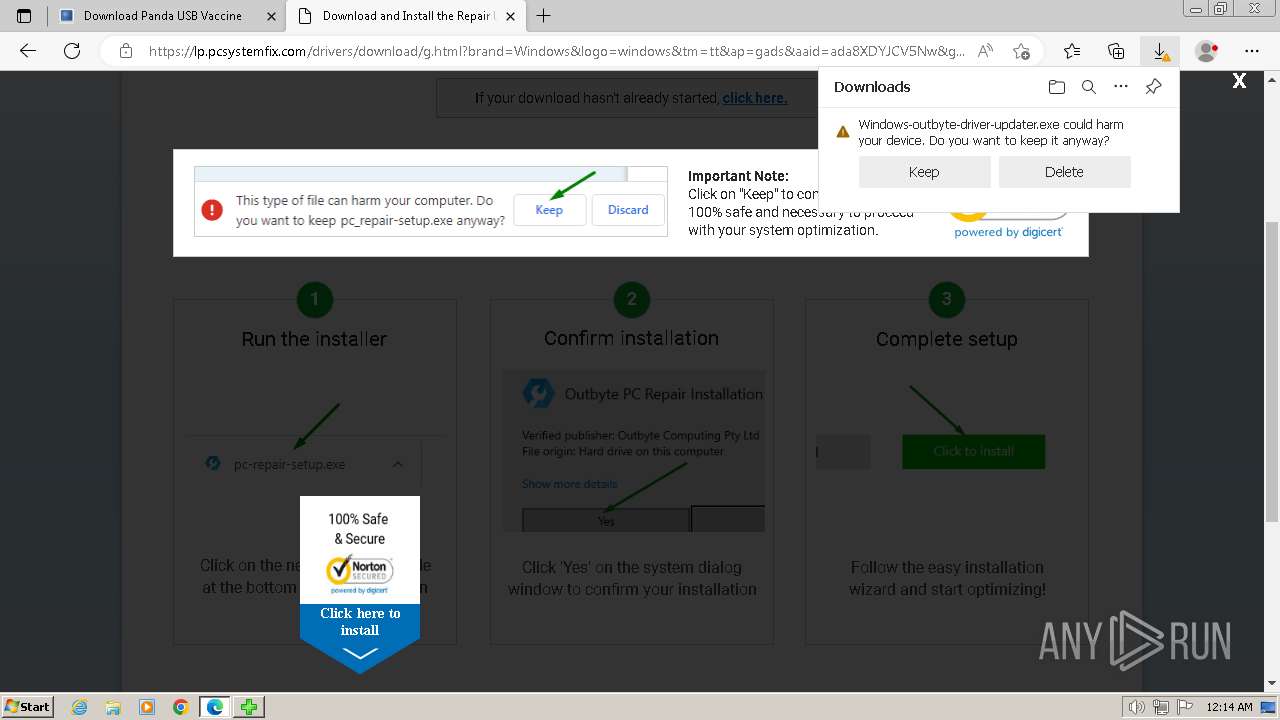
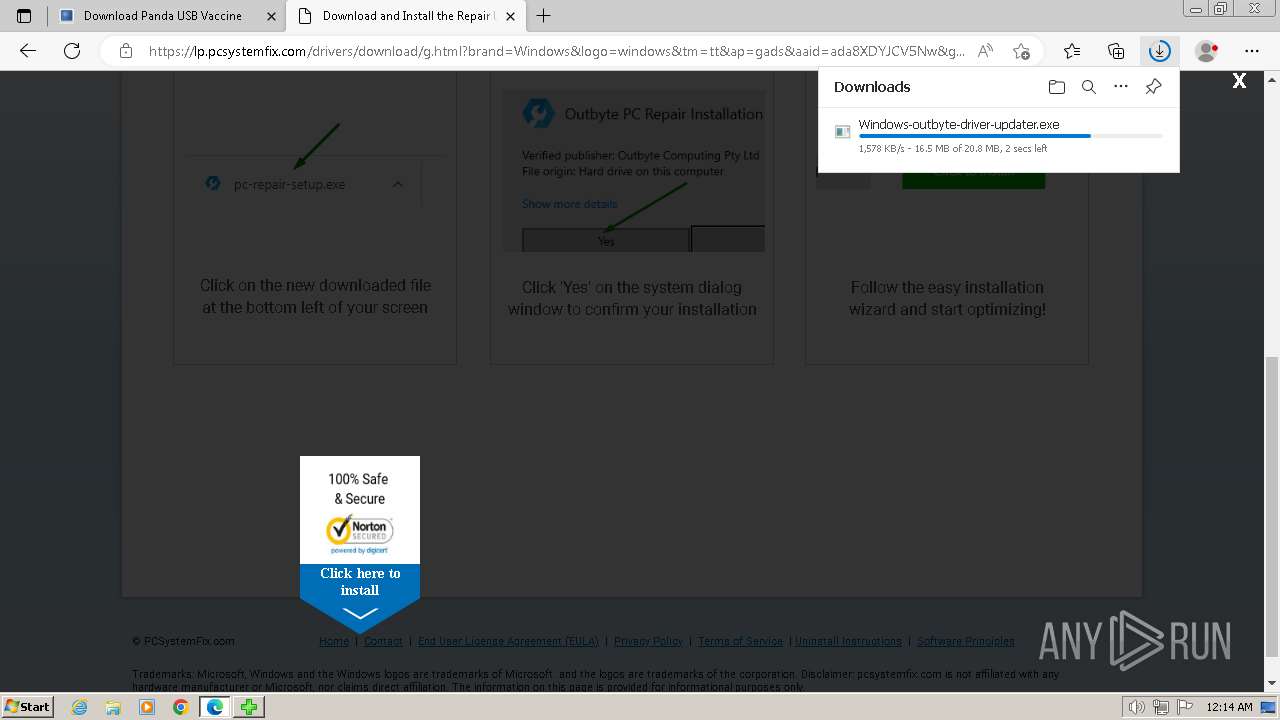
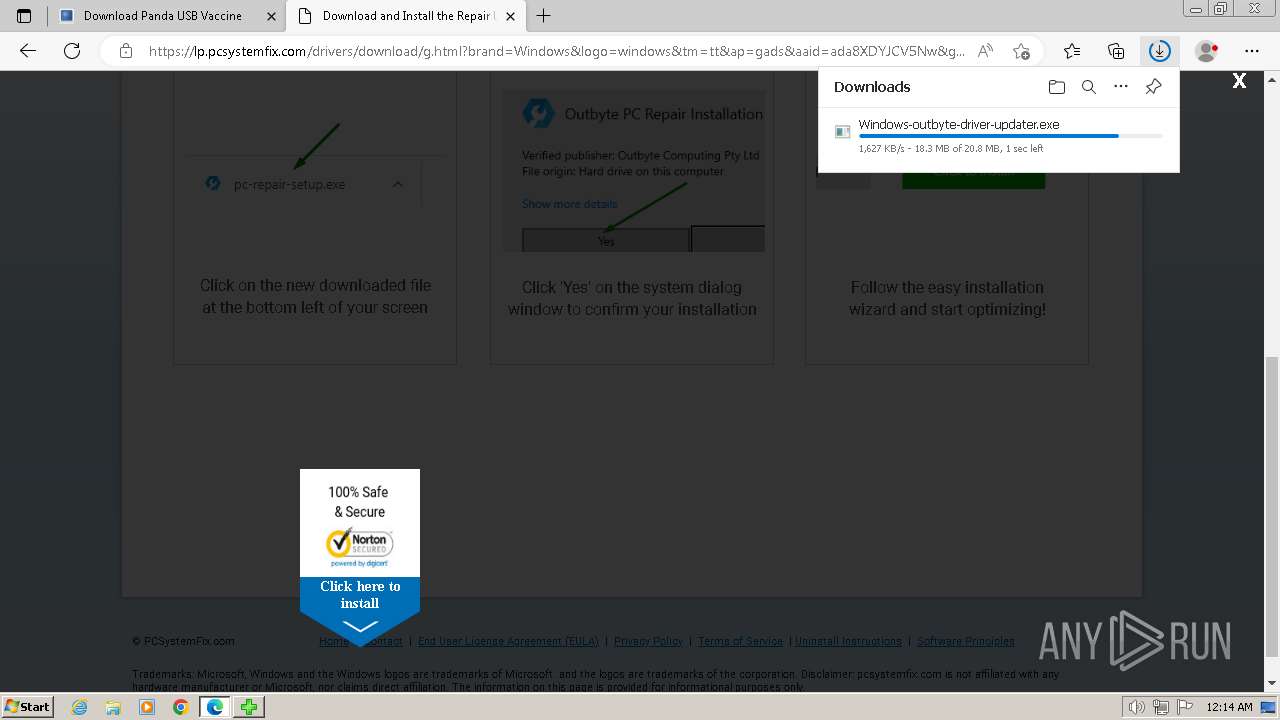
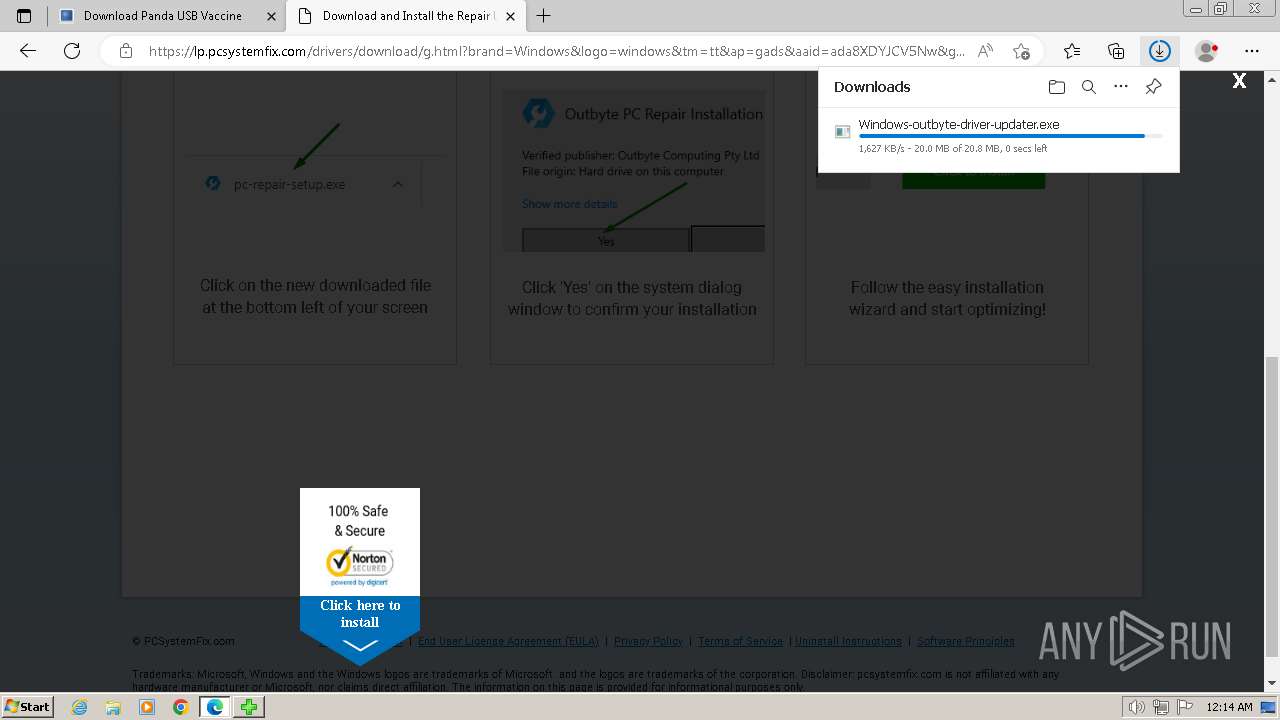
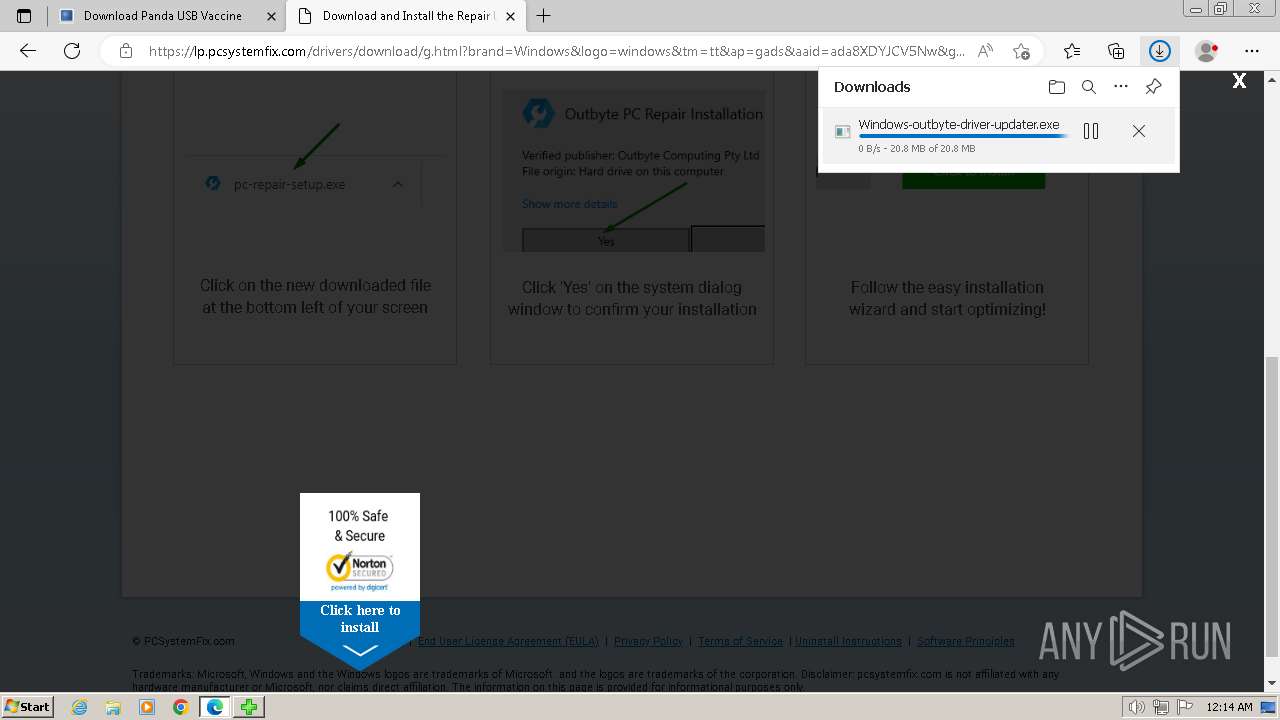
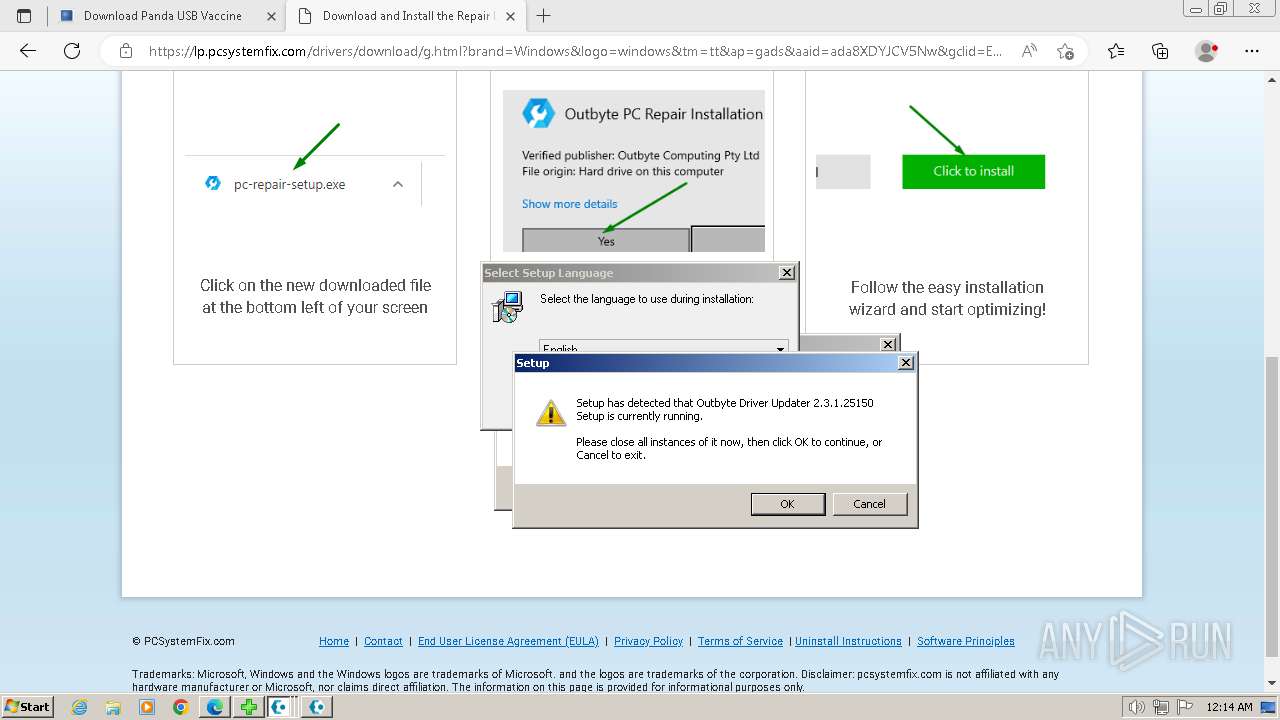
Drops the executable file immediately after the start
- Rem-VBSworm_8.0.exe (PID: 2844)
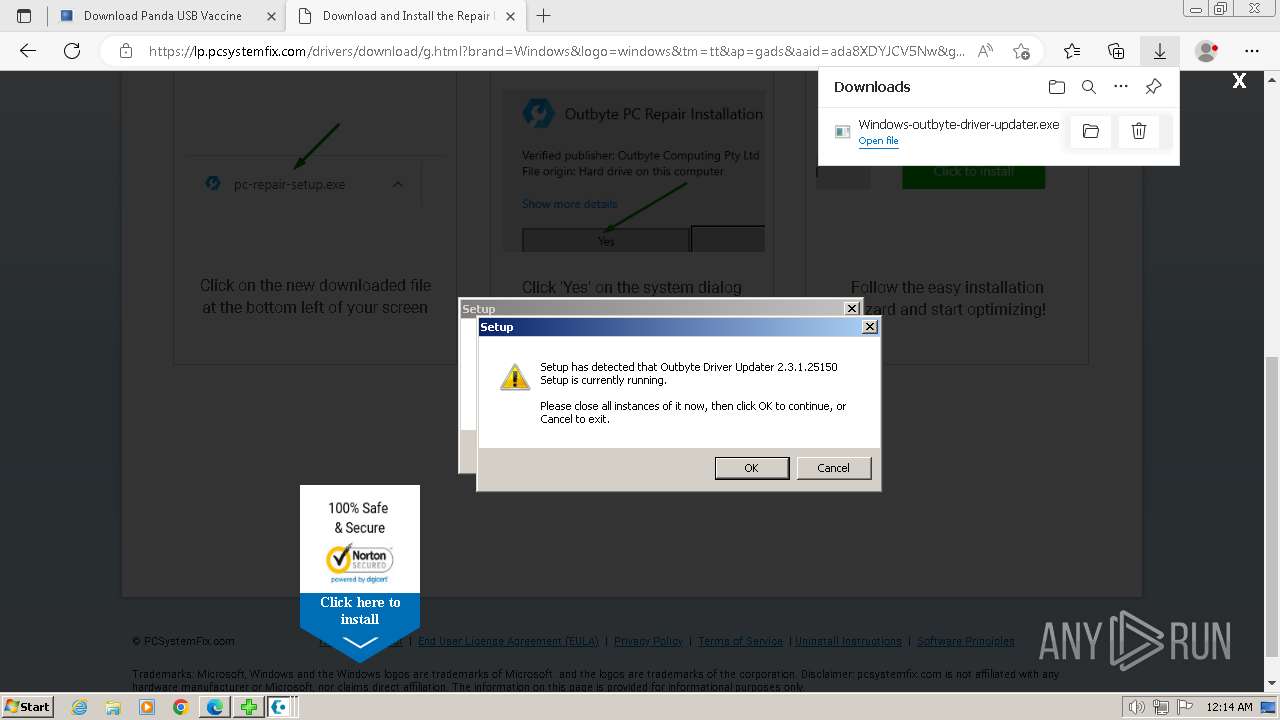
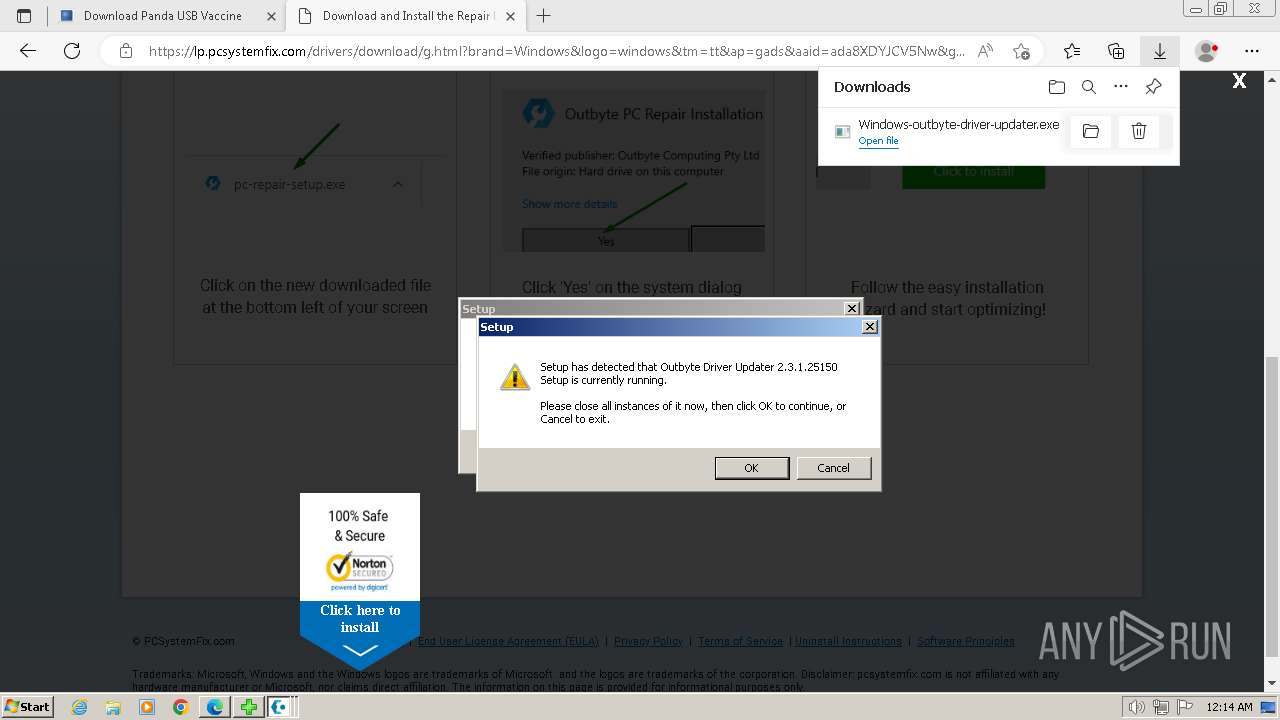
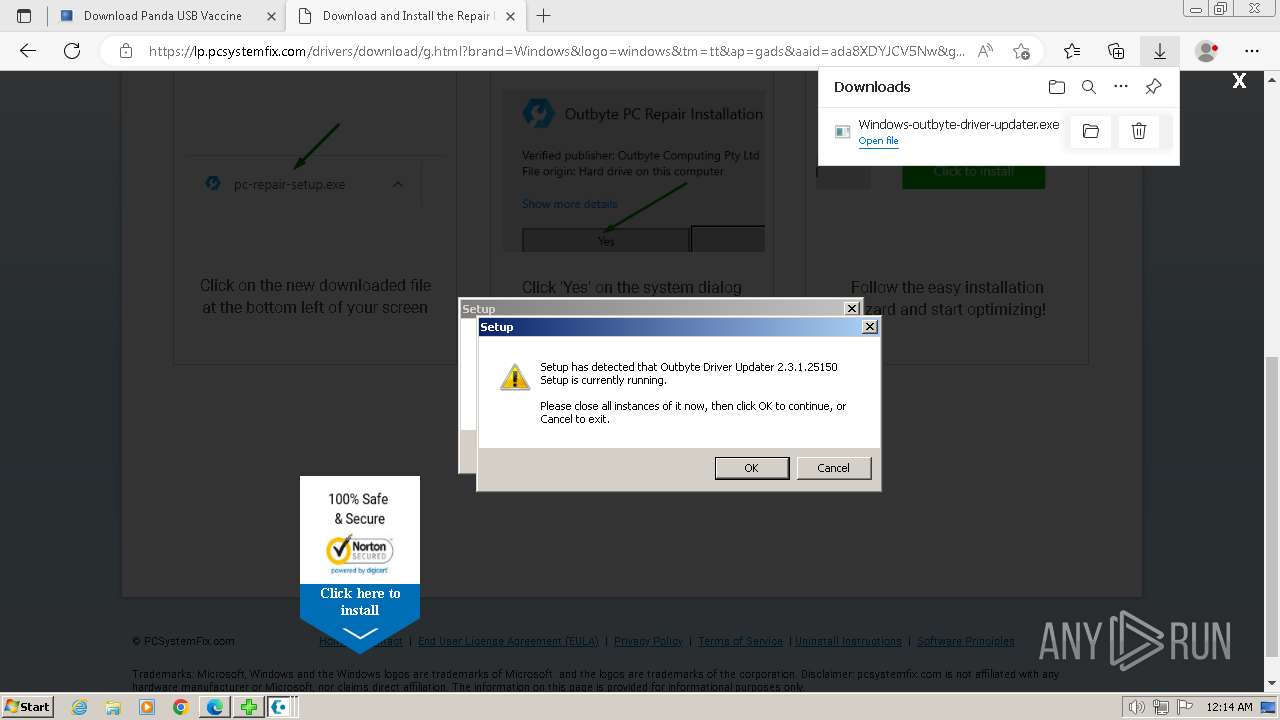
- Windows-outbyte-driver-updater.exe (PID: 4976)
- Windows-outbyte-driver-updater.exe (PID: 5104)
- Windows-outbyte-driver-updater.exe (PID: 5084)
- Windows-outbyte-driver-updater.exe (PID: 4968)
- Windows-outbyte-driver-updater.exe (PID: 5468)
- Windows-outbyte-driver-updater.exe (PID: 5476)
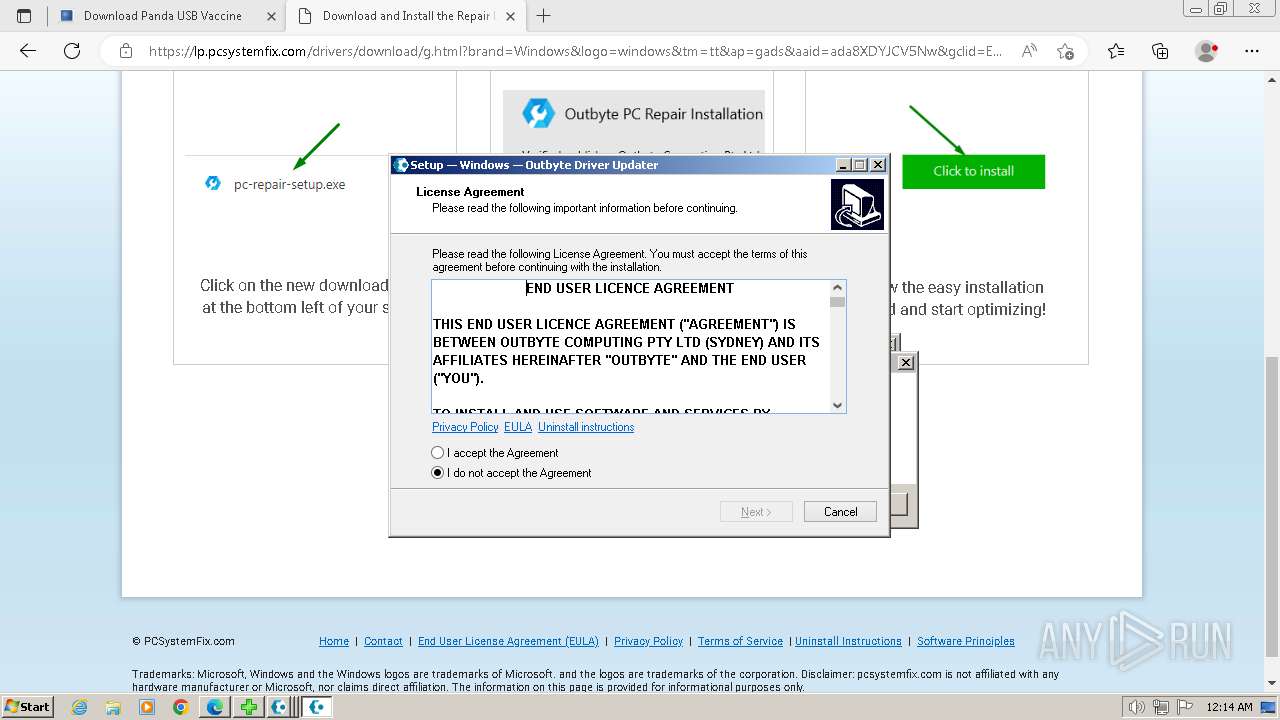
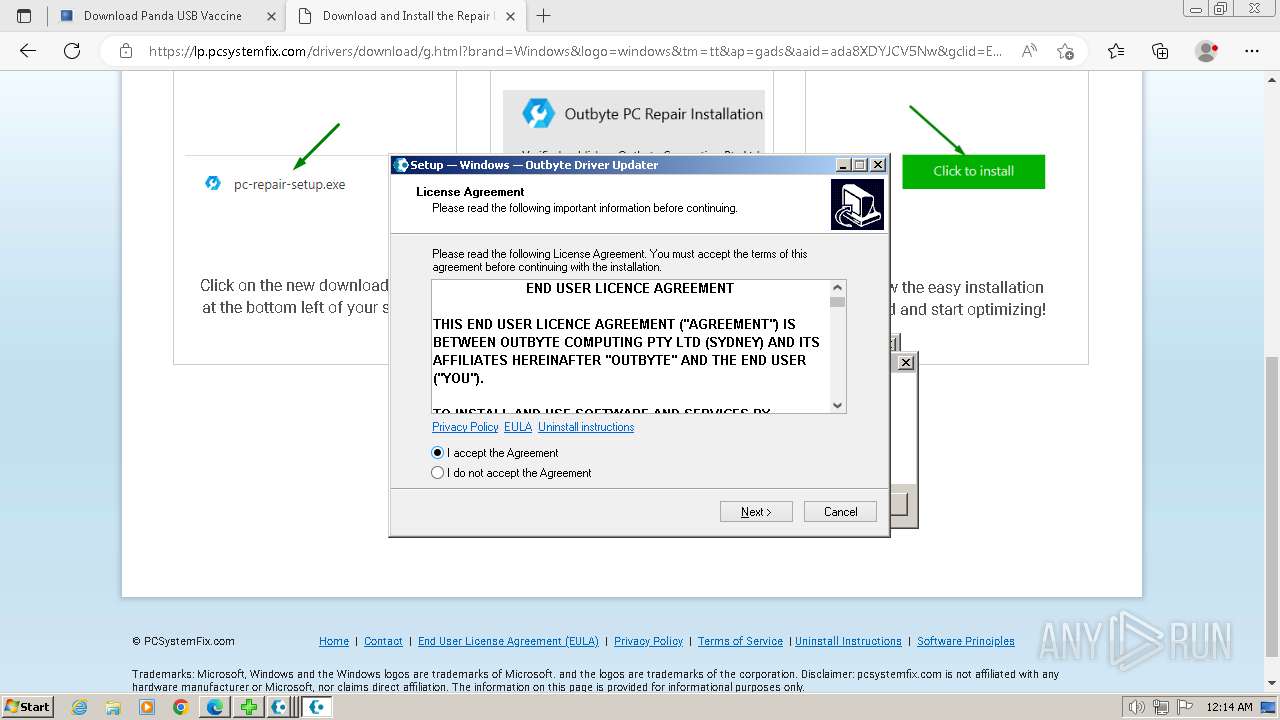
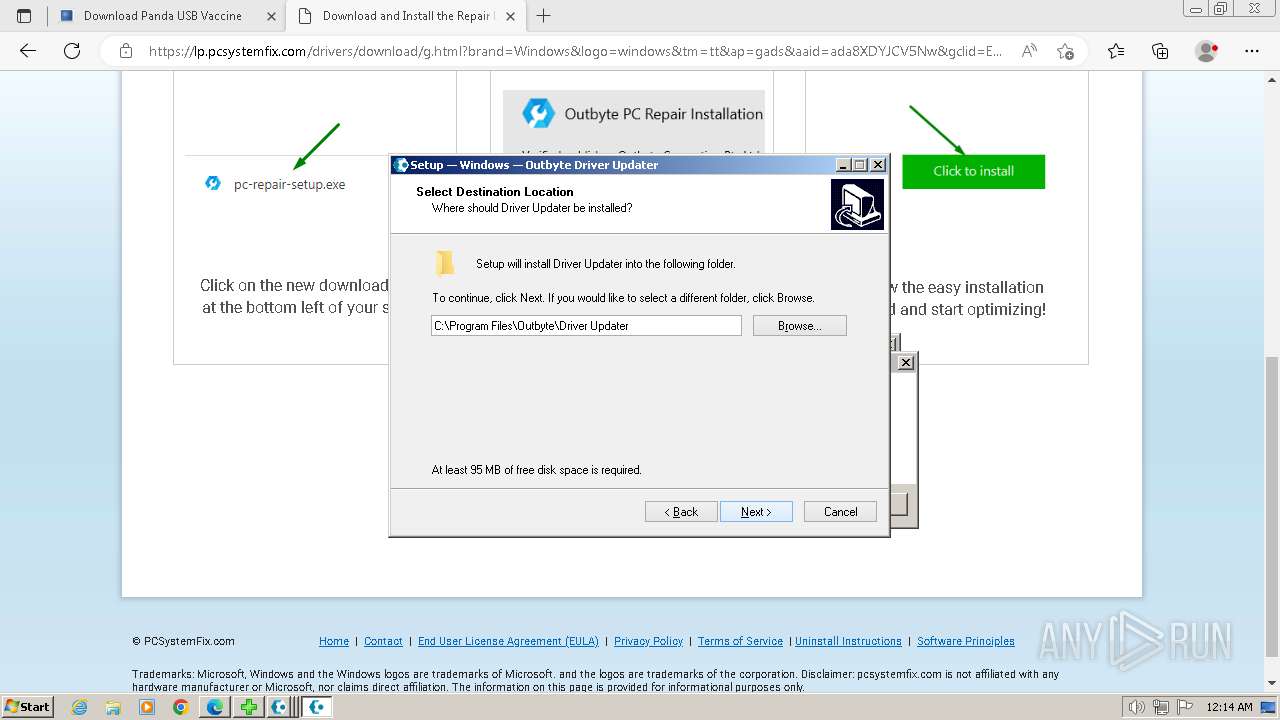
- Installer.exe (PID: 5164)
Actions looks like stealing of personal data
- cmd.exe (PID: 2752)
- DriverUpdater.exe (PID: 5812)
Create files in the Startup directory
- cmd.exe (PID: 2752)
Rurat mutex has been detected
- Installer.exe (PID: 5164)
- ServiceHelper.Agent.exe (PID: 5632)
- ServiceHelper.Agent.exe (PID: 5608)
- DriverUpdater.exe (PID: 5812)
Steals credentials from Web Browsers
- DriverUpdater.exe (PID: 5812)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Rem-VBSworm_8.0.exe (PID: 2844)
- cmd.exe (PID: 2752)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 3848)
Executing commands from a ".bat" file
- Rem-VBSworm_8.0.exe (PID: 2844)
- cmd.exe (PID: 2752)
Reads the Internet Settings
- WMIC.exe (PID: 3848)
- WMIC.exe (PID: 120)
- WMIC.exe (PID: 2648)
- WMIC.exe (PID: 3940)
- WMIC.exe (PID: 1628)
- WMIC.exe (PID: 1584)
- WMIC.exe (PID: 664)
- WMIC.exe (PID: 2656)
- WMIC.exe (PID: 3792)
- WMIC.exe (PID: 2080)
- cmd.exe (PID: 2752)
- Windows-outbyte-driver-updater.exe (PID: 4968)
- Installer.exe (PID: 5164)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 2752)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2752)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2752)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2752)
- cmd.exe (PID: 3324)
- cmd.exe (PID: 2240)
- cmd.exe (PID: 1308)
- cmd.exe (PID: 2804)
- cmd.exe (PID: 568)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 1892)
- cmd.exe (PID: 2668)
- cmd.exe (PID: 1544)
- cmd.exe (PID: 3444)
- cmd.exe (PID: 296)
- cmd.exe (PID: 2808)
- cmd.exe (PID: 784)
- cmd.exe (PID: 2248)
- cmd.exe (PID: 1392)
- cmd.exe (PID: 548)
- cmd.exe (PID: 3128)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3324)
- cmd.exe (PID: 1308)
- cmd.exe (PID: 2240)
- cmd.exe (PID: 2804)
- cmd.exe (PID: 2248)
- cmd.exe (PID: 568)
- cmd.exe (PID: 2752)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 2808)
- cmd.exe (PID: 2668)
- cmd.exe (PID: 1544)
- cmd.exe (PID: 3444)
- cmd.exe (PID: 296)
- cmd.exe (PID: 784)
- cmd.exe (PID: 1892)
- cmd.exe (PID: 3128)
- cmd.exe (PID: 1392)
- cmd.exe (PID: 548)
Uses WMIC.EXE to obtain volume information
- cmd.exe (PID: 2752)
Application launched itself
- cmd.exe (PID: 2752)
Uses WMIC.EXE to obtain user accounts information
- cmd.exe (PID: 2752)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2752)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2752)
Executable content was dropped or overwritten
- Windows-outbyte-driver-updater.exe (PID: 4968)
- Windows-outbyte-driver-updater.exe (PID: 4976)
- Windows-outbyte-driver-updater.exe (PID: 5104)
- Windows-outbyte-driver-updater.exe (PID: 5084)
- Windows-outbyte-driver-updater.exe (PID: 5468)
- Windows-outbyte-driver-updater.exe (PID: 5476)
- Installer.exe (PID: 5164)
Checks Windows Trust Settings
- Installer.exe (PID: 5164)
- DriverUpdater.exe (PID: 5812)
Reads security settings of Internet Explorer
- Installer.exe (PID: 5164)
- DriverUpdater.exe (PID: 5812)
Reads settings of System Certificates
- Installer.exe (PID: 5164)
- DriverUpdater.exe (PID: 5812)
Reads the BIOS version
- Installer.exe (PID: 5164)
- DriverUpdater.exe (PID: 5812)
Adds/modifies Windows certificates
- Installer.exe (PID: 5164)
- DriverUpdater.exe (PID: 5812)
Reads the Windows owner or organization settings
- Installer.exe (PID: 5164)
Creates a software uninstall entry
- Installer.exe (PID: 5164)
Process drops SQLite DLL files
- Installer.exe (PID: 5164)
Executes as Windows Service
- ServiceHelper.Agent.exe (PID: 5632)
- VSSVC.exe (PID: 6068)
Process drops legitimate windows executable
- Installer.exe (PID: 5164)
Searches for installed software
- dllhost.exe (PID: 6036)
- DriverUpdater.exe (PID: 5812)
INFO
Checks supported languages
- Rem-VBSworm_8.0.exe (PID: 2844)
- Windows-outbyte-driver-updater.exe (PID: 4976)
- Windows-outbyte-driver-updater.exe (PID: 4968)
- Windows-outbyte-driver-updater.exe (PID: 5084)
- Windows-outbyte-driver-updater.exe (PID: 5104)
- Installer.exe (PID: 5164)
- Windows-outbyte-driver-updater.exe (PID: 5476)
- Windows-outbyte-driver-updater.exe (PID: 5468)
- ServiceHelper.Agent.exe (PID: 5608)
- ServiceHelper.Agent.exe (PID: 5632)
- DriverUpdater.exe (PID: 5812)
- msiexec.exe (PID: 1044)
Create files in a temporary directory
- Rem-VBSworm_8.0.exe (PID: 2844)
- Windows-outbyte-driver-updater.exe (PID: 4968)
- Windows-outbyte-driver-updater.exe (PID: 4976)
- Windows-outbyte-driver-updater.exe (PID: 5084)
- Windows-outbyte-driver-updater.exe (PID: 5104)
- Windows-outbyte-driver-updater.exe (PID: 5468)
- Windows-outbyte-driver-updater.exe (PID: 5476)
- Installer.exe (PID: 5164)
Application launched itself
- msedge.exe (PID: 3508)
- msedge.exe (PID: 2788)
Creates files in the program directory
- cmd.exe (PID: 2752)
- Installer.exe (PID: 5164)
- DriverUpdater.exe (PID: 5812)
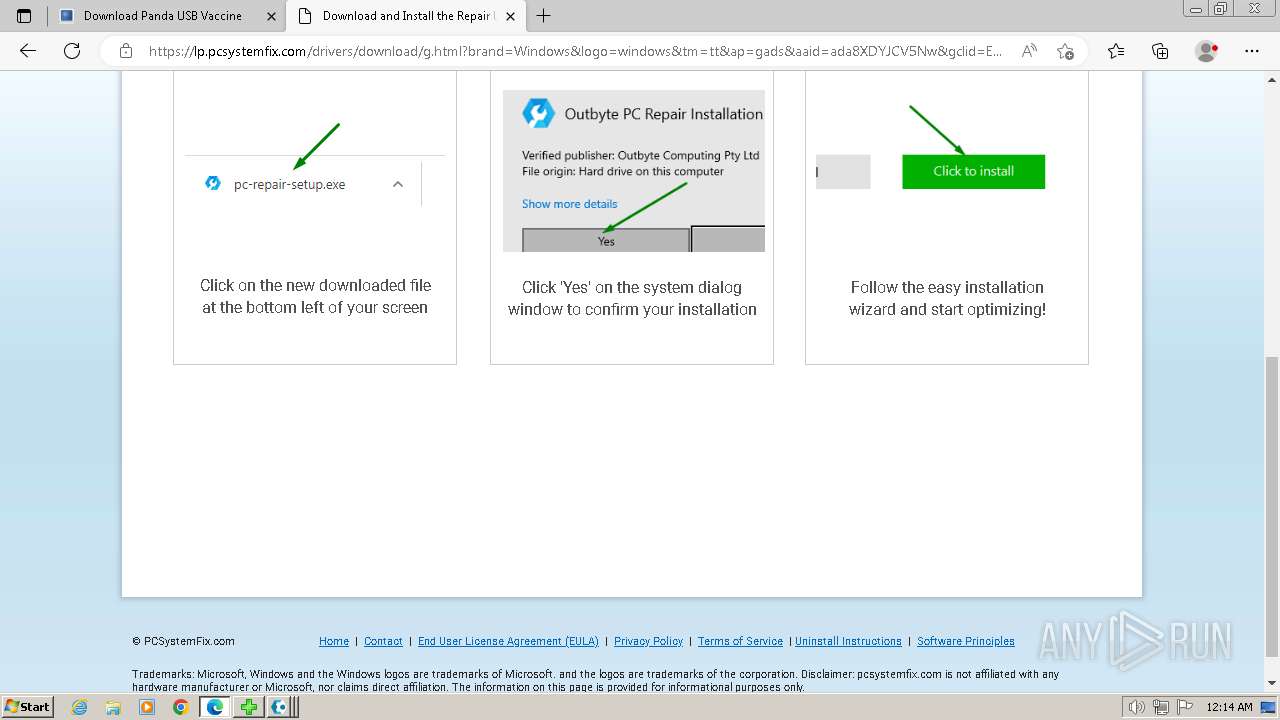
Manual execution by a user
- msedge.exe (PID: 2788)
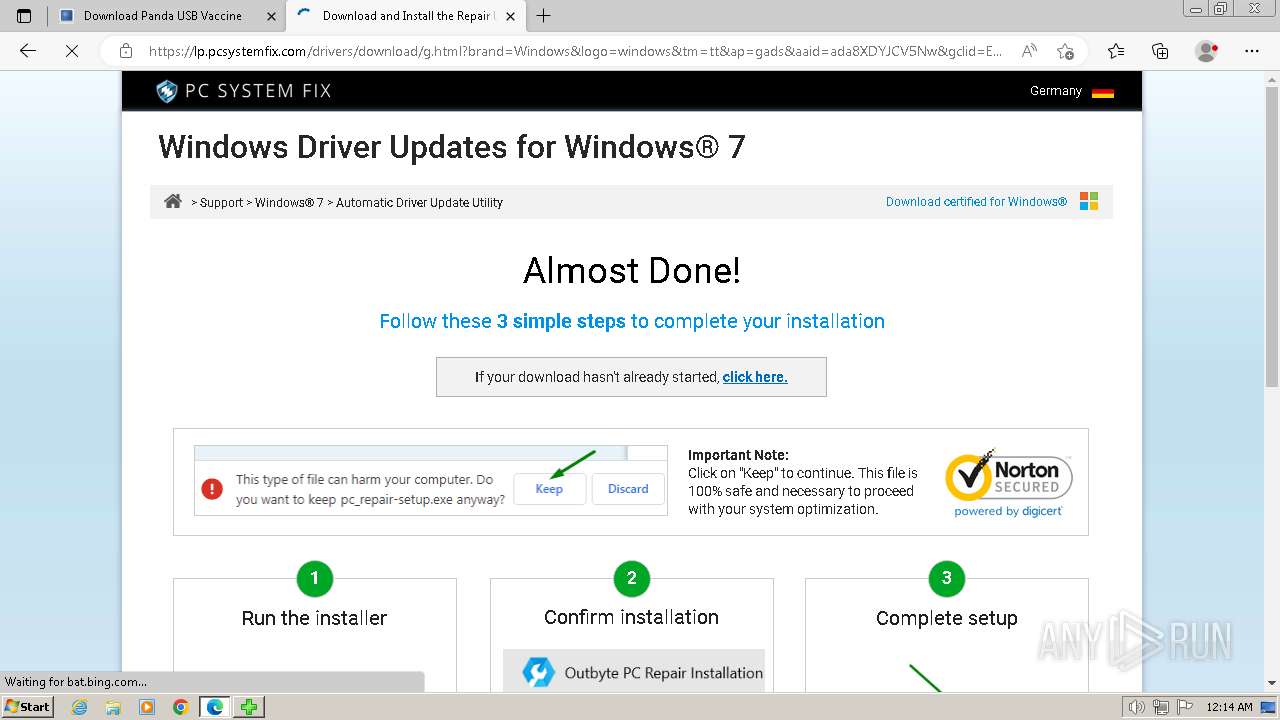
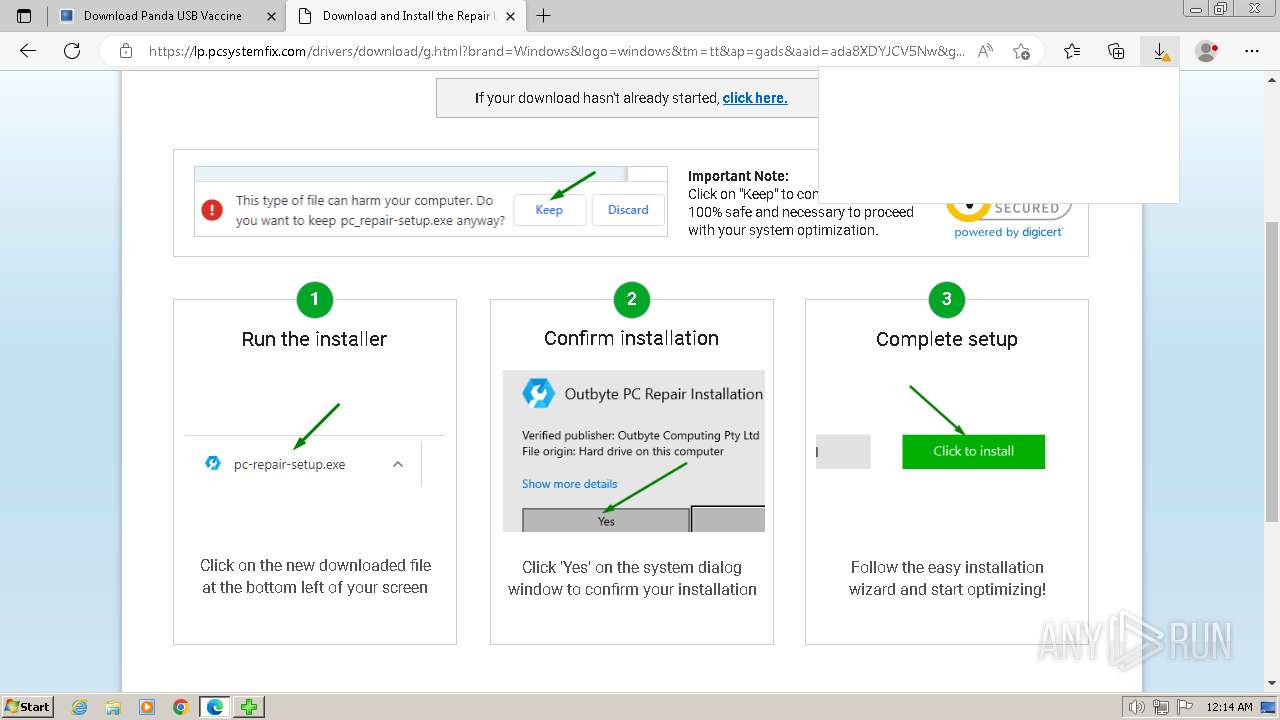
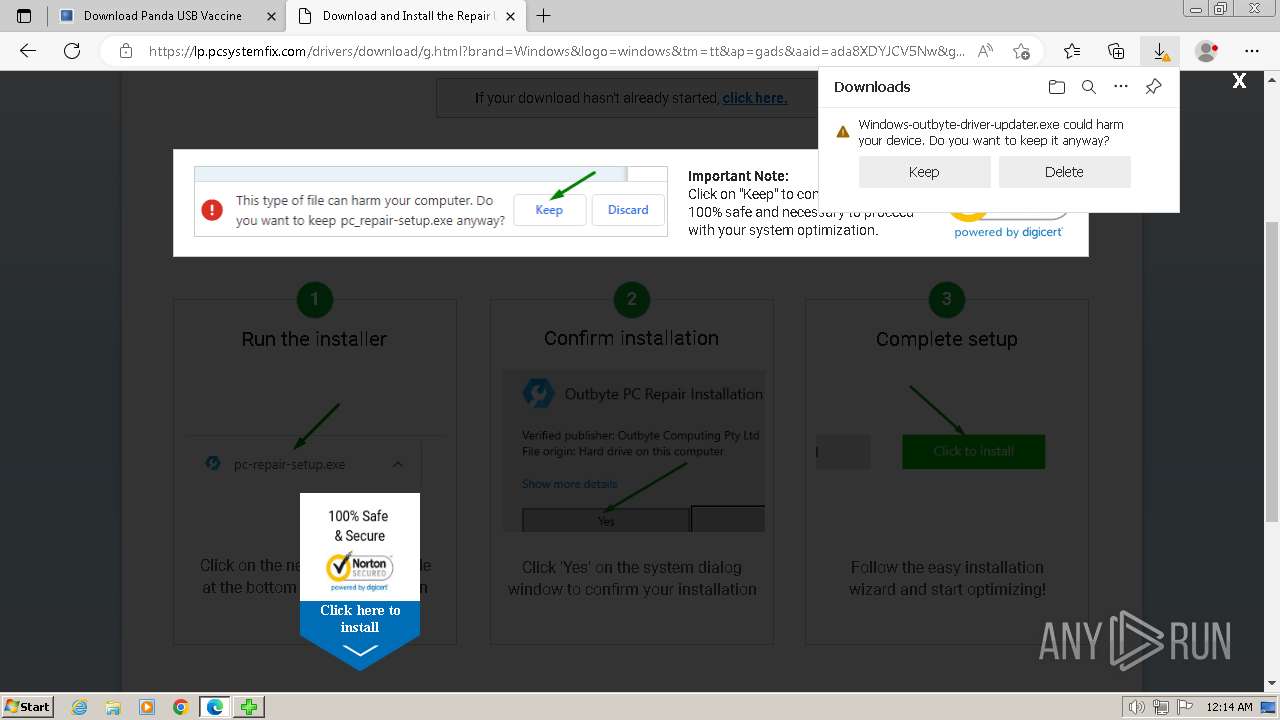
Drops the executable file immediately after the start
- msedge.exe (PID: 1596)
- msedge.exe (PID: 2788)
The process uses the downloaded file
- msedge.exe (PID: 4680)
- msedge.exe (PID: 2788)
Process checks computer location settings
- Windows-outbyte-driver-updater.exe (PID: 4968)
- Installer.exe (PID: 5164)
Executable content was dropped or overwritten
- msedge.exe (PID: 2788)
- msedge.exe (PID: 1596)
Reads the computer name
- Windows-outbyte-driver-updater.exe (PID: 4968)
- Installer.exe (PID: 5164)
- ServiceHelper.Agent.exe (PID: 5608)
- ServiceHelper.Agent.exe (PID: 5632)
- DriverUpdater.exe (PID: 5812)
- msiexec.exe (PID: 1044)
Checks proxy server information
- Windows-outbyte-driver-updater.exe (PID: 4968)
- Installer.exe (PID: 5164)
Reads the machine GUID from the registry
- Installer.exe (PID: 5164)
- DriverUpdater.exe (PID: 5812)
- msiexec.exe (PID: 1044)
Reads Windows Product ID
- Installer.exe (PID: 5164)
- DriverUpdater.exe (PID: 5812)
Reads the software policy settings
- Installer.exe (PID: 5164)
- DriverUpdater.exe (PID: 5812)
Creates files or folders in the user directory
- Installer.exe (PID: 5164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (57.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (18.2) |
| .exe | | | Win16/32 Executable Delphi generic (8.3) |
| .exe | | | Generic Win/DOS Executable (8) |
| .exe | | | DOS Executable Generic (8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:11:16 22:57:01+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 35328 |
| InitializedDataSize: | 77824 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa13c |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 8.0.0.0 |
| ProductVersionNumber: | 8.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | bartblaze |
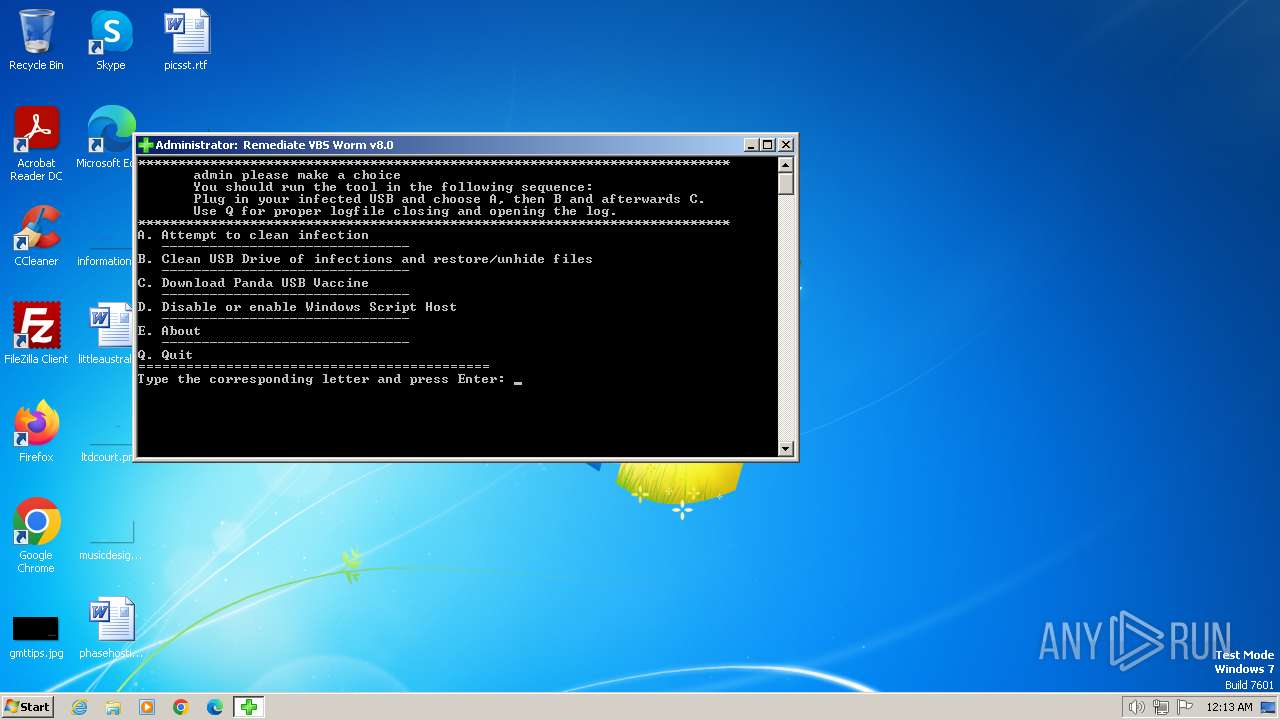
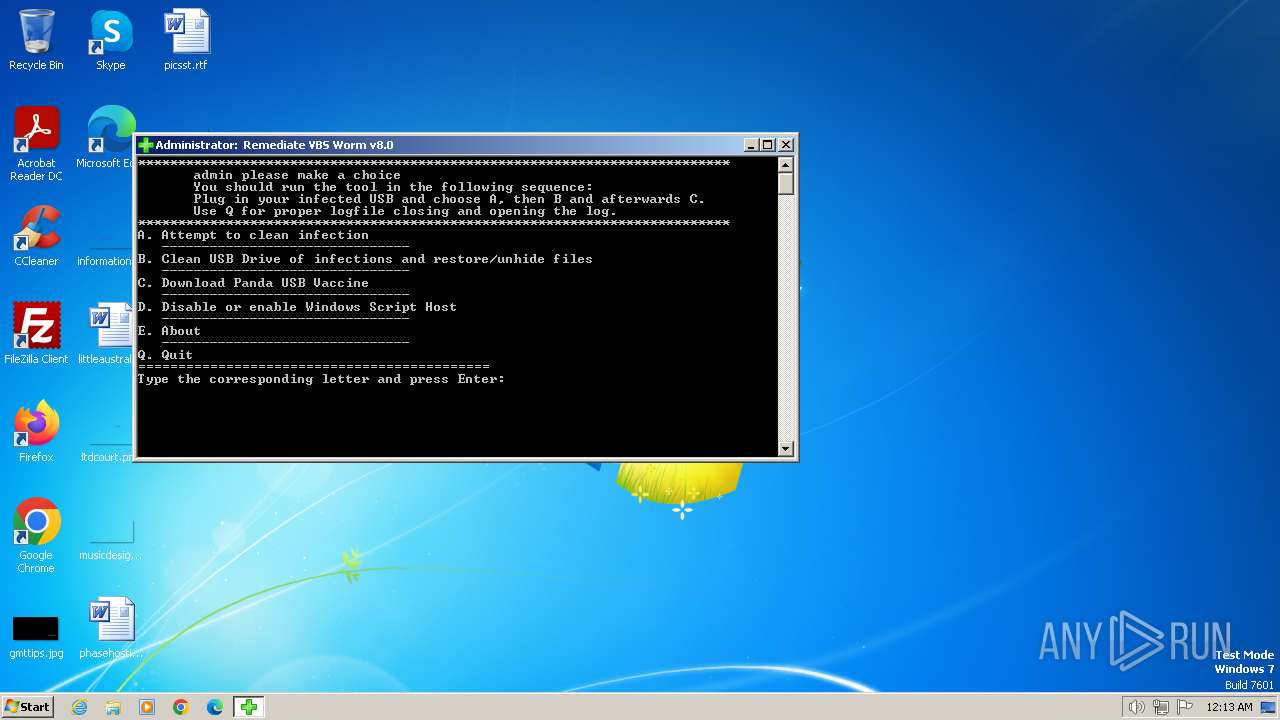
| FileDescription: | Tool to delete VBS autorun worms & unhide files |
| FileVersion: | 8. 0. 0. 0 |
| InternalName: | Rem-VBSworm |
| LegalCopyright: | bartblaze |
| LegalTrademarks: | bartblaze |
| OriginalFileName: | Rem-VBSworm |
| ProductName: | Remediate VBS Worm |
| ProductVersion: | 8. 0. 0. 0 |
| Comments: | https://bartblaze.blogspot.com/2014/02/remediate-vbs-malware.html |
Total processes
245
Monitored processes
189
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | wmic COMPUTERSYSTEM GET BootupState | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | reg query "HKU\S-1-5-21-1302019708-1500728564-335382590-1000\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /s | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 296 | C:\Windows\system32\cmd.exe /c reg query "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /s|findstr /ic:"winlogon.bat" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 316 | reg query "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /s | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 448 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1440 --field-trial-handle=1272,i,553530810049386623,15029216796010446477,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 548 | C:\Windows\system32\cmd.exe /c reg query "HKU\S-1-5-21-1302019708-1500728564-335382590-1000\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /s|findstr /ic:"winlogon.bat" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 568 | C:\Windows\system32\cmd.exe /c reg query "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /s|findstr /ic:"\.a3x" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 664 | wmic useraccount where name='admin' get sid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | FINDSTR "^S-" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 784 | C:\Windows\system32\cmd.exe /c reg query "HKU\S-1-5-21-1302019708-1500728564-335382590-1000\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /s|findstr /ic:"\.vbe" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
57 698
Read events
57 271
Write events
384
Delete events
43
Modification events
| (PID) Process: | (1928) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoDriveTypeAutoRun |
Value: 255 | |||
| (PID) Process: | (3724) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoDriveTypeAutoRun |
Value: 255 | |||
| (PID) Process: | (3684) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (2072) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (2148) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (3776) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (1644) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | delete value | Name: | NoRun |
Value: | |||
| (PID) Process: | (3236) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | 101 lyrics |
Value: | |||
| (PID) Process: | (3108) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | 101 lyrics |
Value: | |||
| (PID) Process: | (2032) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | 101 lyrics |
Value: | |||
Executable files
112
Suspicious files
140
Text files
65
Unknown types
197
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2516 | findstr.exe | C:\Users\admin\AppData\Local\Temp\tmp.txt | text | |
MD5:35A8A59DE53D68C46833409EA18F2EE6 | SHA256:DCC74584853B2CEE3C506468917AA64193E531F122DC53B716F0493BF1E20EBA | |||
| 2752 | cmd.exe | C:\Rem-VBS.log | text | |
MD5:2D1907EBC3798FFA64D6ACF7D47B1E00 | SHA256:8BD59BEB64EB2F17298825DFFA13E85FA75788EF0A90CFC286BA55BB69F075B5 | |||
| 3232 | findstr.exe | C:\Users\admin\AppData\Local\Temp\tmp.txt | text | |
MD5:35A8A59DE53D68C46833409EA18F2EE6 | SHA256:DCC74584853B2CEE3C506468917AA64193E531F122DC53B716F0493BF1E20EBA | |||
| 2752 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\errorlog.txt | text | |
MD5:8A5D736F4636151458F7F4CD26655A44 | SHA256:2623220DB7A832F3BF690EB40CC1292D8A7418FBCCEFA594D23B7FFEB346339A | |||
| 2752 | cmd.exe | C:\Users\admin\AppData\Local\Temp\errorlog.txt | text | |
MD5:66A396744B6B916A80EBBAC28C53A8A3 | SHA256:0547BA61614A6517FB269280040B36D26967363933A950F8AD20454C9656D75E | |||
| 764 | findstr.exe | C:\Users\admin\AppData\Local\Temp\tmp.txt | text | |
MD5:35A8A59DE53D68C46833409EA18F2EE6 | SHA256:DCC74584853B2CEE3C506468917AA64193E531F122DC53B716F0493BF1E20EBA | |||
| 1956 | findstr.exe | C:\Users\admin\AppData\Local\Temp\tmp.txt | text | |
MD5:35A8A59DE53D68C46833409EA18F2EE6 | SHA256:DCC74584853B2CEE3C506468917AA64193E531F122DC53B716F0493BF1E20EBA | |||
| 2752 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\errorlog.txt | text | |
MD5:71FE7C2544B05D2F6E74922BE6D1EF15 | SHA256:7956325BE44EC90B55F3B2CC2EE8F0659C480CEBEF7D71899FFE0CD2B4E30C96 | |||
| 2416 | findstr.exe | C:\Users\admin\AppData\Local\Temp\tmp.txt | text | |
MD5:35A8A59DE53D68C46833409EA18F2EE6 | SHA256:DCC74584853B2CEE3C506468917AA64193E531F122DC53B716F0493BF1E20EBA | |||
| 2752 | cmd.exe | C:\Users\admin\AppData\Roaming\errorlog.txt | text | |
MD5:388A0BFDBFA57768D23ED504187ACE60 | SHA256:F458893C1CB86FDFD303DE6FC69F2574BC56A8B3B59B5FDD2FE88CCEDB464ACF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
292
DNS requests
379
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5164 | Installer.exe | GET | 304 | 173.222.108.210:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b76101c44e657a72 | unknown | — | — | unknown |
1596 | msedge.exe | GET | 200 | 192.229.221.95:80 | http://cacerts.digicert.com/DigiCertTLSRSASHA2562020CA1-1.crt | unknown | binary | 1.19 Kb | unknown |
5164 | Installer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAsllCLO2YEqFaBOmVKKDvo%3D | unknown | binary | 471 b | unknown |
5164 | Installer.exe | GET | 200 | 192.229.221.95:80 | http://status.rapidssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJiUKgT2m88fZ4nxc1Lu6M%2FjvkagQUDNtsgkkPSmcKuBTuesRIUojrVjgCEAOiOjjuz1GXFL4ZZIGXed8%3D | unknown | binary | 471 b | unknown |
5164 | Installer.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
5164 | Installer.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
5164 | Installer.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEE80yiW5Mf2wCipGbb3nZn0%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e90c163b6659448e | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2788 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
1596 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1596 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
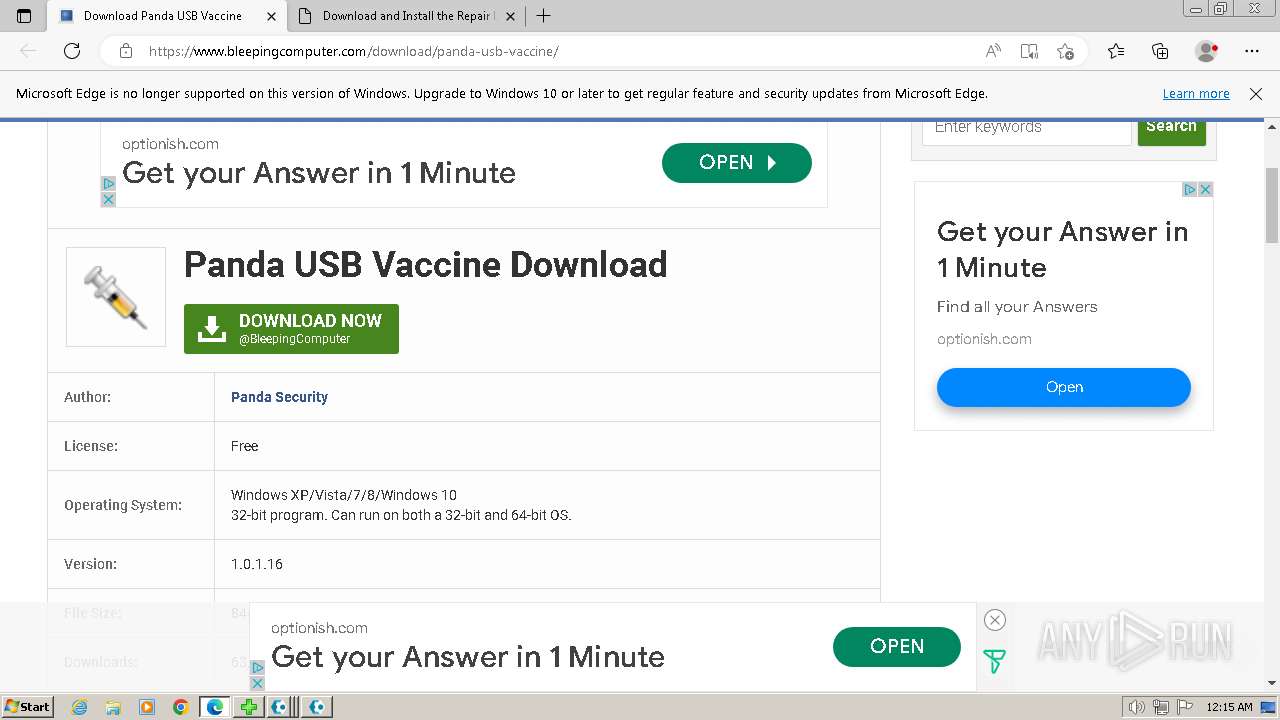
1596 | msedge.exe | 104.20.60.209:443 | www.bleepingcomputer.com | CLOUDFLARENET | — | shared |
1596 | msedge.exe | 142.250.186.42:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
1596 | msedge.exe | 104.26.12.6:443 | www.bleepstatic.com | CLOUDFLARENET | US | unknown |
1596 | msedge.exe | 104.18.20.206:443 | a.pub.network | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
www.bleepingcomputer.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.bleepstatic.com |
| whitelisted |
a.pub.network |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
www.google-analytics.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1596 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |