| File name: | Snipaste-1.16.2-x64.zip |
| Full analysis: | https://app.any.run/tasks/f7c49375-883f-4104-8d38-0d29799fc38c |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 03:23:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D1BA68AB665533F953633502FB7052F2 |
| SHA1: | 07681CEEB45DC4F8ACBC1C2F3731773CEF82162D |
| SHA256: | D72B81BB2858462EB88F26B81455ADEA2FE57E6E0A371BDC74D7333290BF2D55 |
| SSDEEP: | 393216:T7Eg+MhlpgECAaI9XKEYFr4ulVHxL1GZy5eyAnShzD:T7EJMhUNoalFD/1Gk5epnmzD |
MALICIOUS
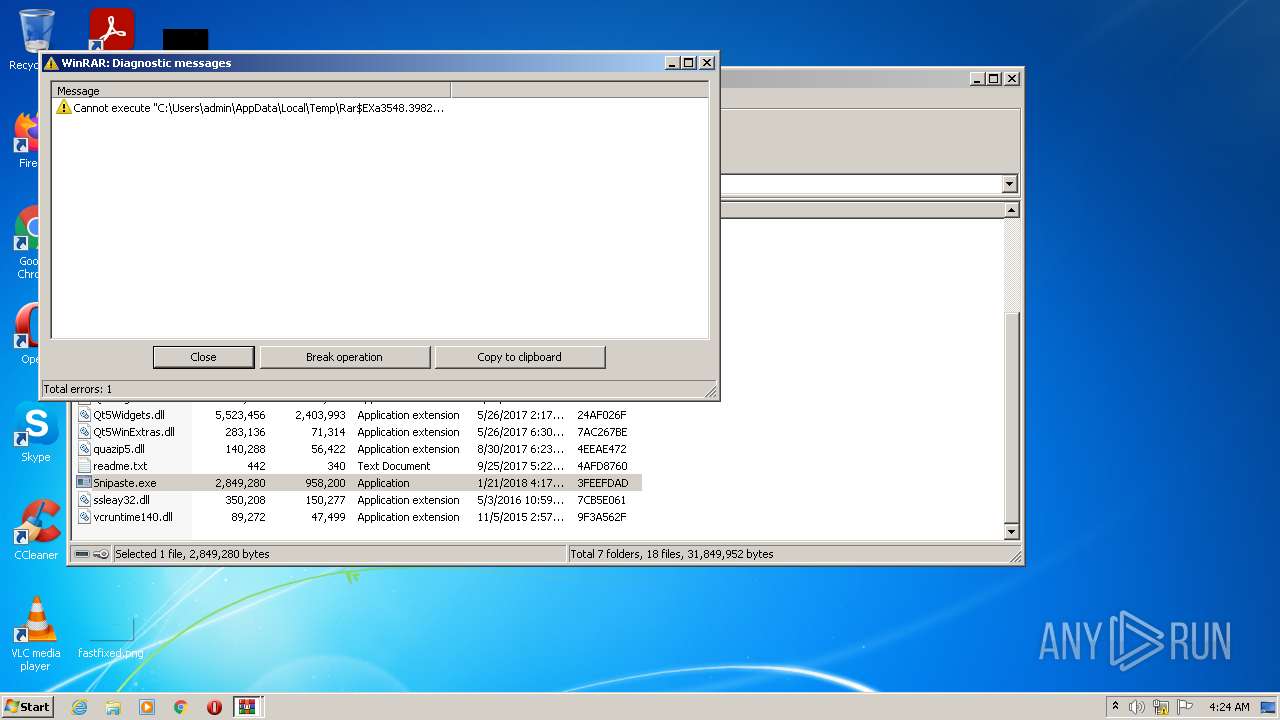
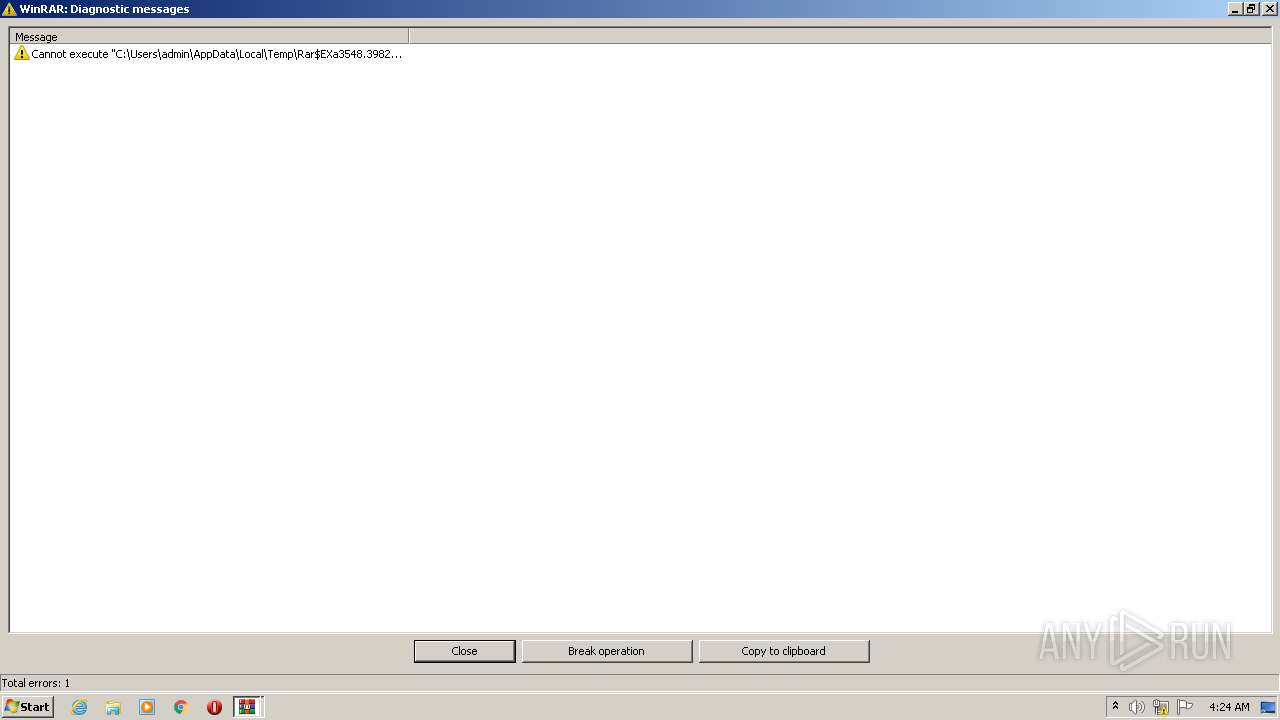
Drops executable file immediately after starts
- WinRAR.exe (PID: 3548)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3548)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3548)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3548)
Checks supported languages
- WinRAR.exe (PID: 3548)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
Total processes
34
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3548 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Snipaste-1.16.2-x64.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 030
Read events
999
Write events
31
Delete events
0
Modification events
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Snipaste-1.16.2-x64.zip | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
31
Suspicious files
0
Text files
1
Unknown types
32
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3548.39827\iconengines\qsvgicon.dll | executable | |
MD5:AF62439D5478E2F8A64EB952B24F6428 | SHA256:1E3132A6B38B4EF0B314F5C3D3EDEE60ADAB103F71CE1DC4AA7D7EC4365C875F | |||
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3548.39827\imageformats\qicns.dll | executable | |
MD5:C969A2D69AE29DE635E90B808C204B80 | SHA256:541A8AB55D06BB1C45AE1AD5349EF4D12570F601D27276925E6D969B648A9182 | |||
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3548.39827\lang\ar_jo.qm | qm | |
MD5:FA0B0F46B887D9CE3D35C6049FD82BDA | SHA256:90E8C5472C9C3FD9854A2444409029CA6E905BDA0C2C592BDC8DBA8D201FE2EA | |||
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3548.39827\lang\de_de.qm | qm | |
MD5:2EBB2C59C5FEC75AD789DF97D0BD030C | SHA256:42D81AA872488D1FB1DD7A2E15E84E7BD2F33BD4E2C402347D463CB43D02562B | |||
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3548.39827\imageformats\qjpeg.dll | executable | |
MD5:85E46CA17B81821A568D721AFD93FA06 | SHA256:C6B283B89FB32320EEC47CD25C017F530F35DAB22C67DC2B9814F2F3B0DB9853 | |||
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3548.39827\audio\qtaudio_windows.dll | executable | |
MD5:7A730A9D4DD72238F976B111BEDB03B2 | SHA256:1732C512A32E515CD277281F9FFF618182F216EE167746D3247E04FCD71BC556 | |||
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3548.39827\lang\fr_fr.qm | qm | |
MD5:783C2B42AADA1ED243709E6070262325 | SHA256:10B95F131DAF53AA3FD127C4EF914078FB4911E48145215B0FB9FC07F0715998 | |||
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3548.39827\hoedown.dll | executable | |
MD5:563196B167690F130AD5DE9B49B293AC | SHA256:0C2BF16F68A64EDE7E2DA509C6497E41B735887D21678FB86CCFCCBBA164D4DF | |||
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3548.39827\imageformats\qwbmp.dll | executable | |
MD5:354EECCE0FDDD8330FA014D38C0E0812 | SHA256:B6671368CA4DB77F8F7227386CC24A6812C72B36C61946D43D39730035562D47 | |||
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3548.39827\imageformats\qsvg.dll | executable | |
MD5:42C8FEC602252658F3D6DE2BFA2FE9FD | SHA256:45A11F9B597C2361C8A40837625C3F93AE3443562D088BC0DC6514E09E20B1ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report