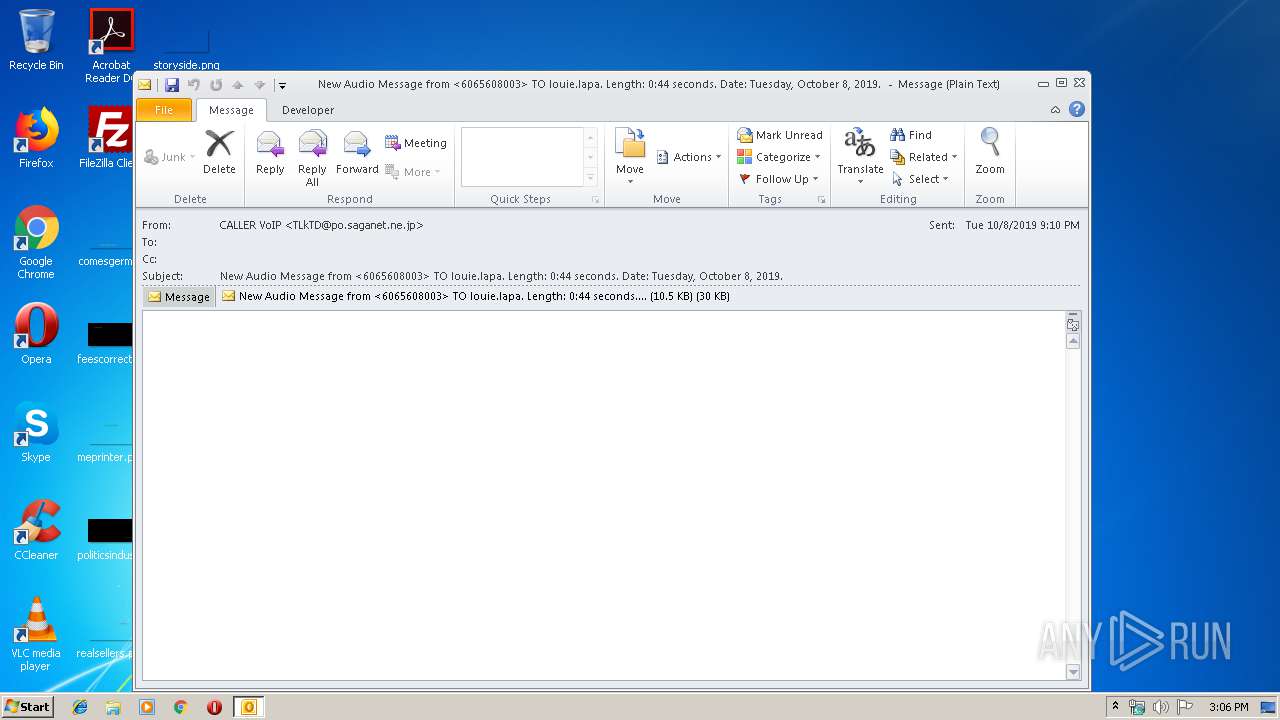
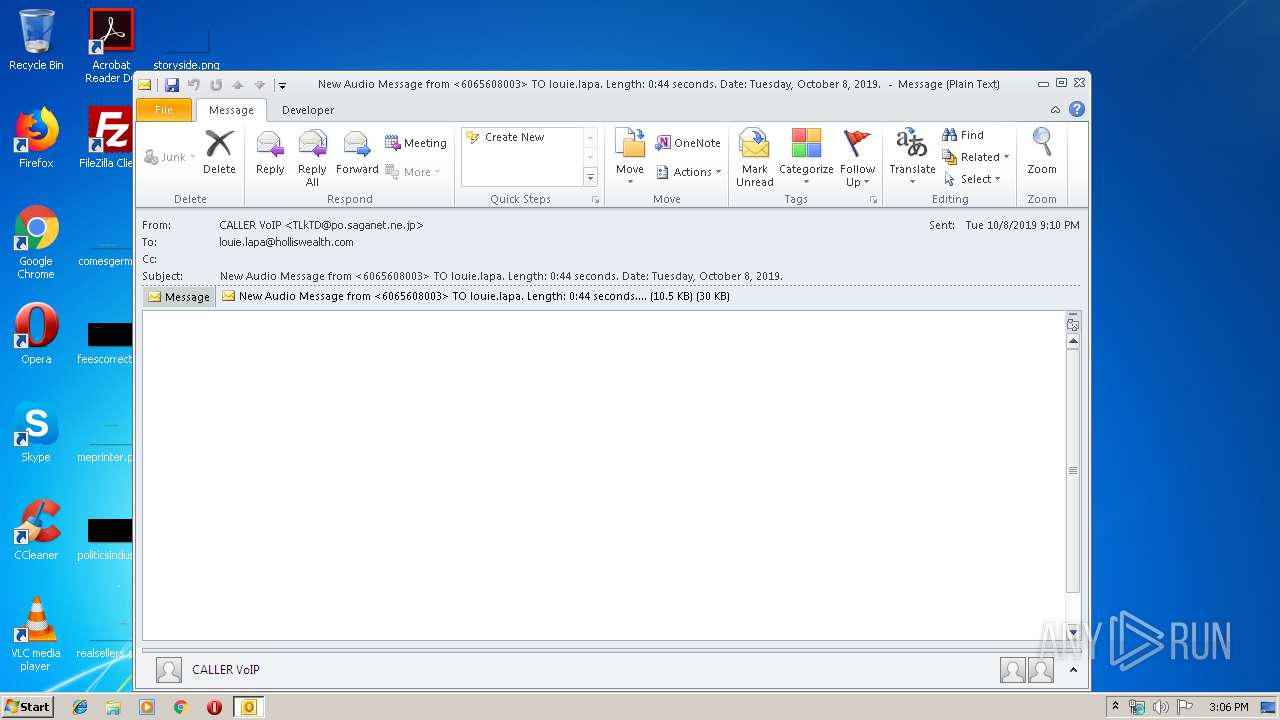
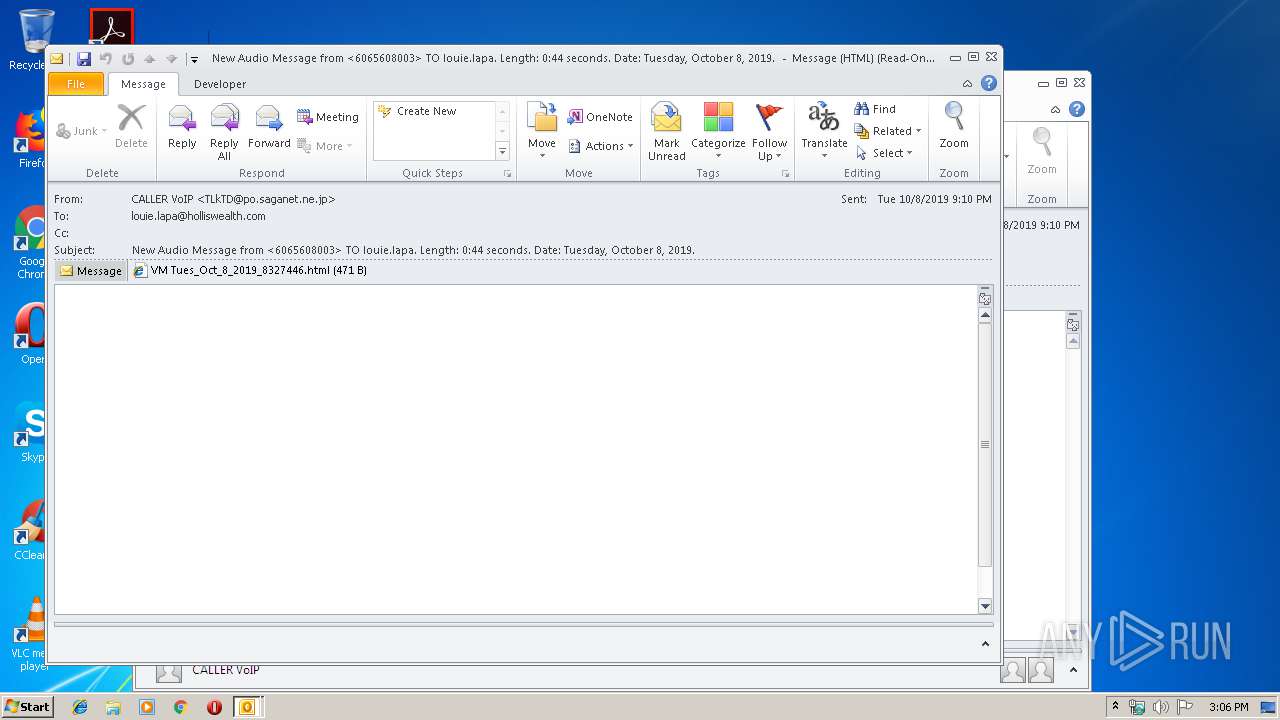
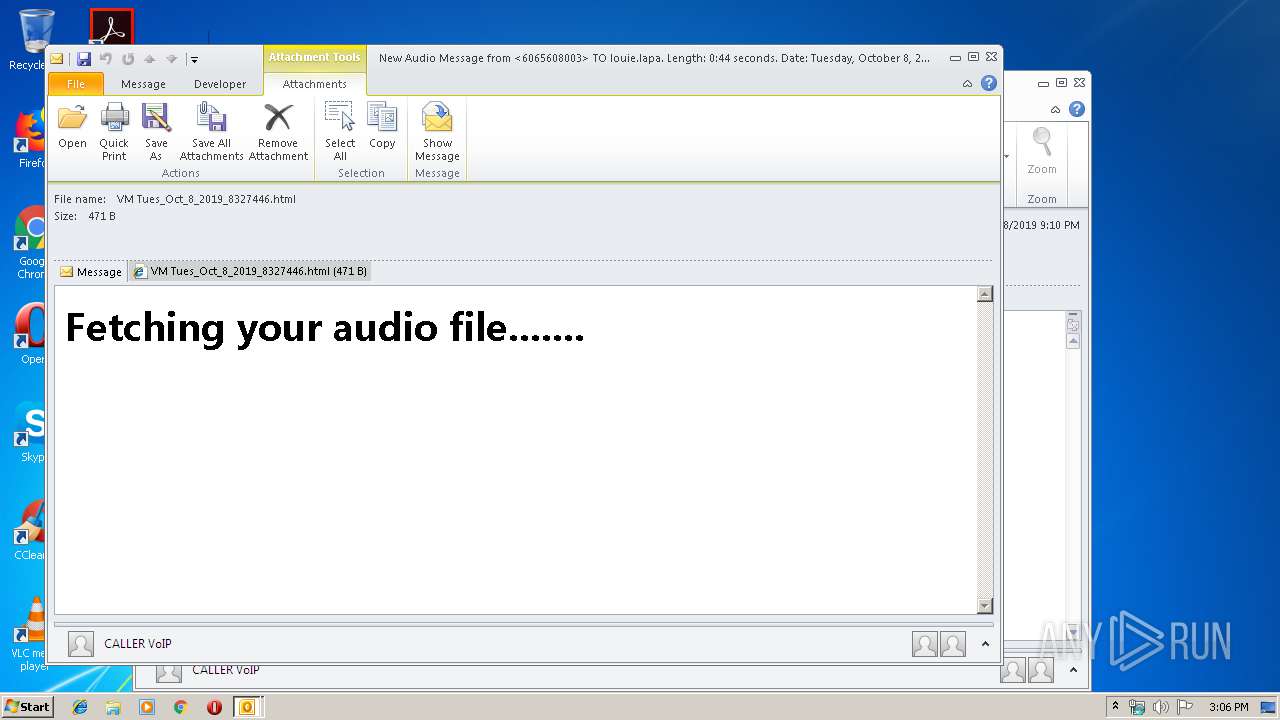
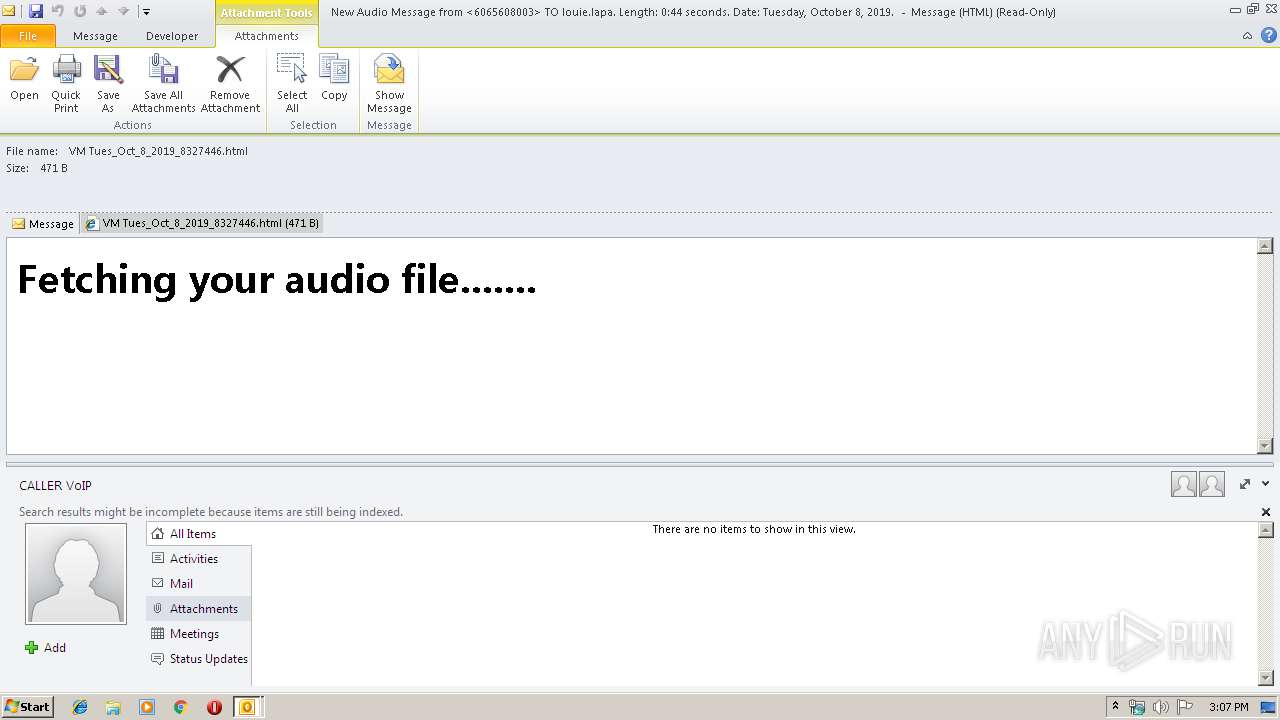
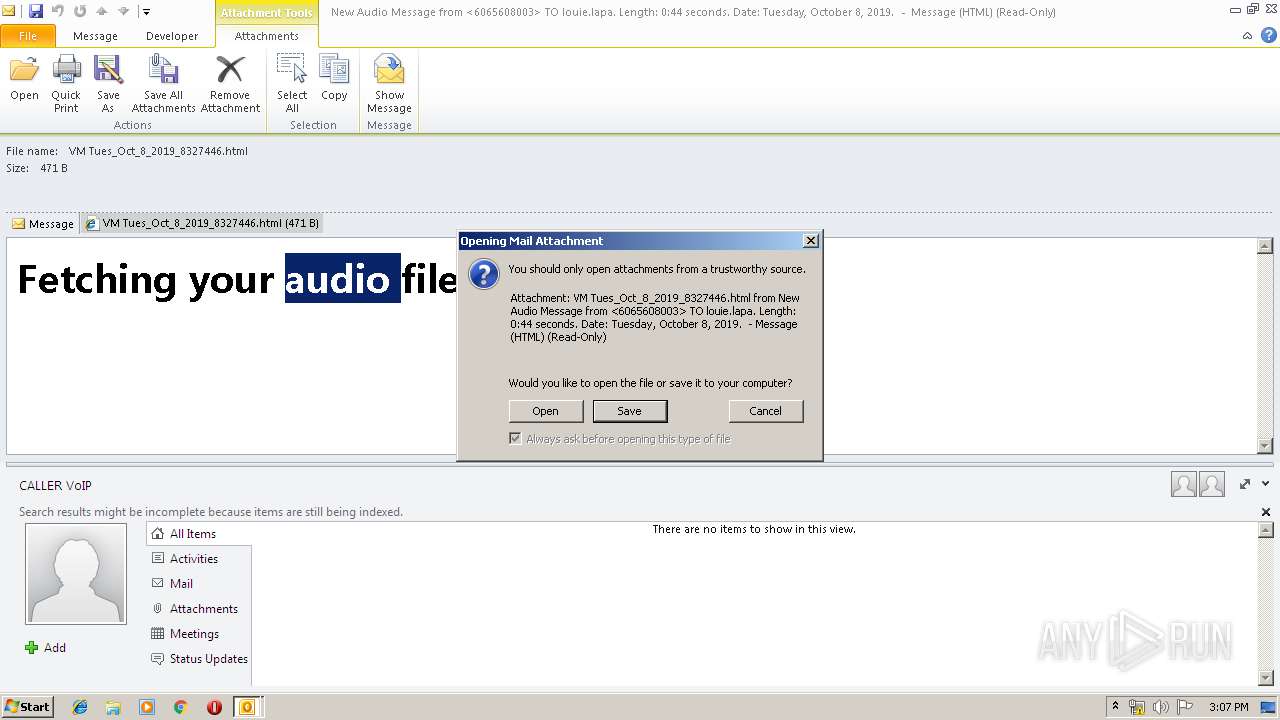
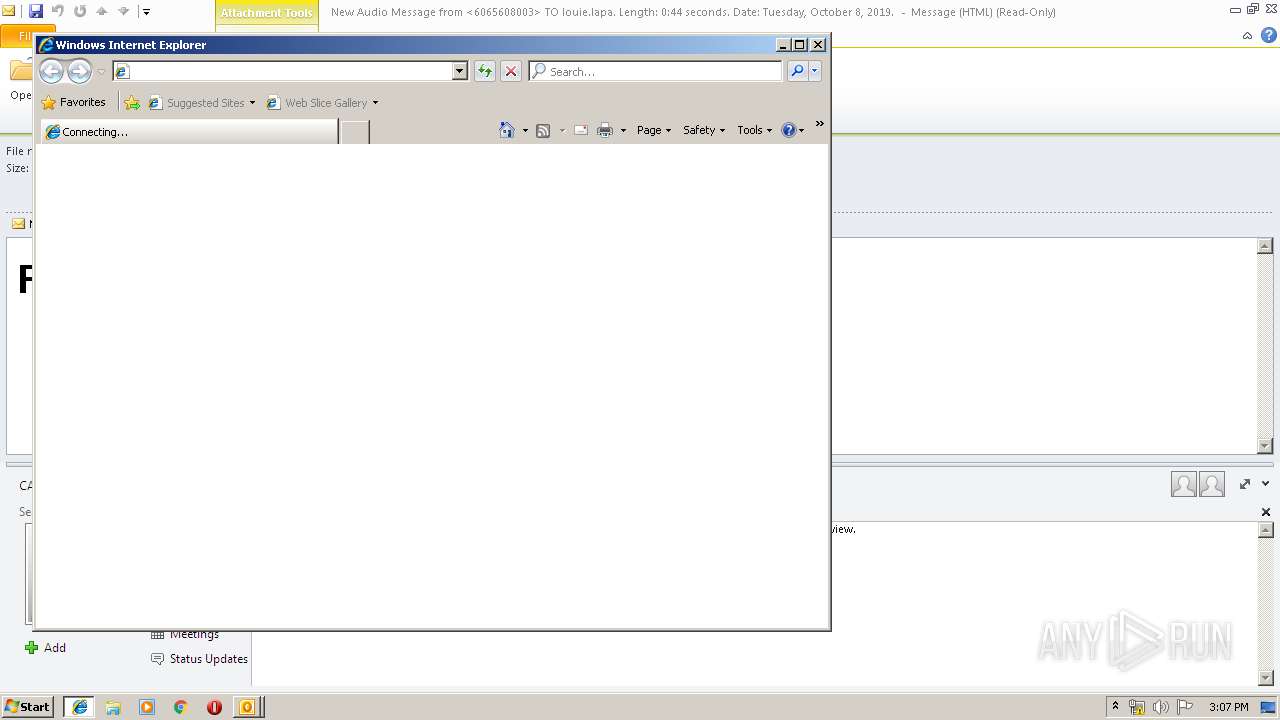
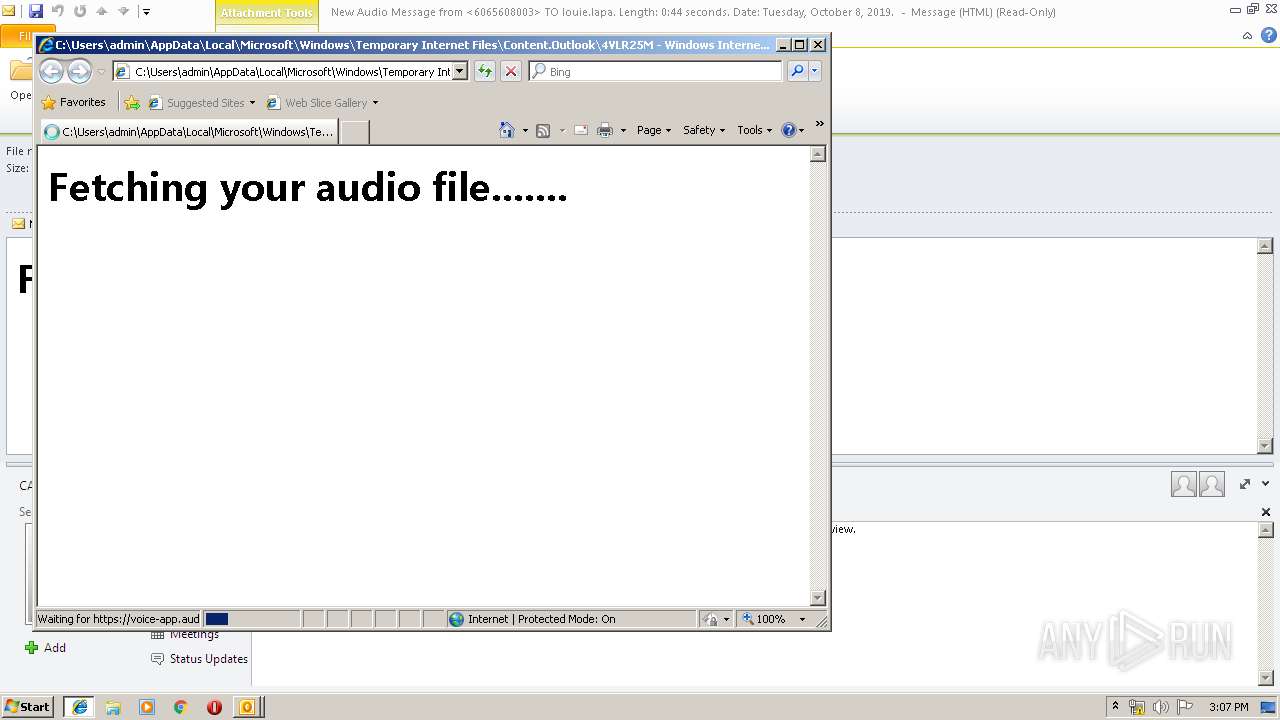
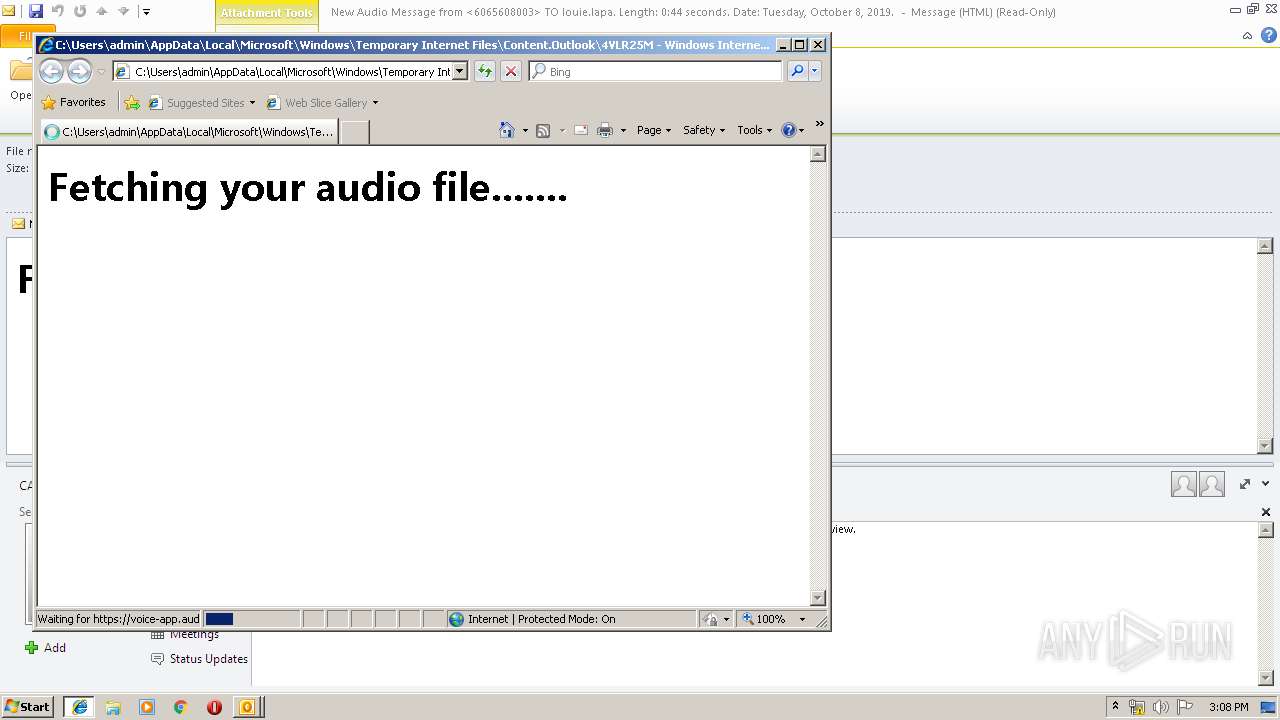
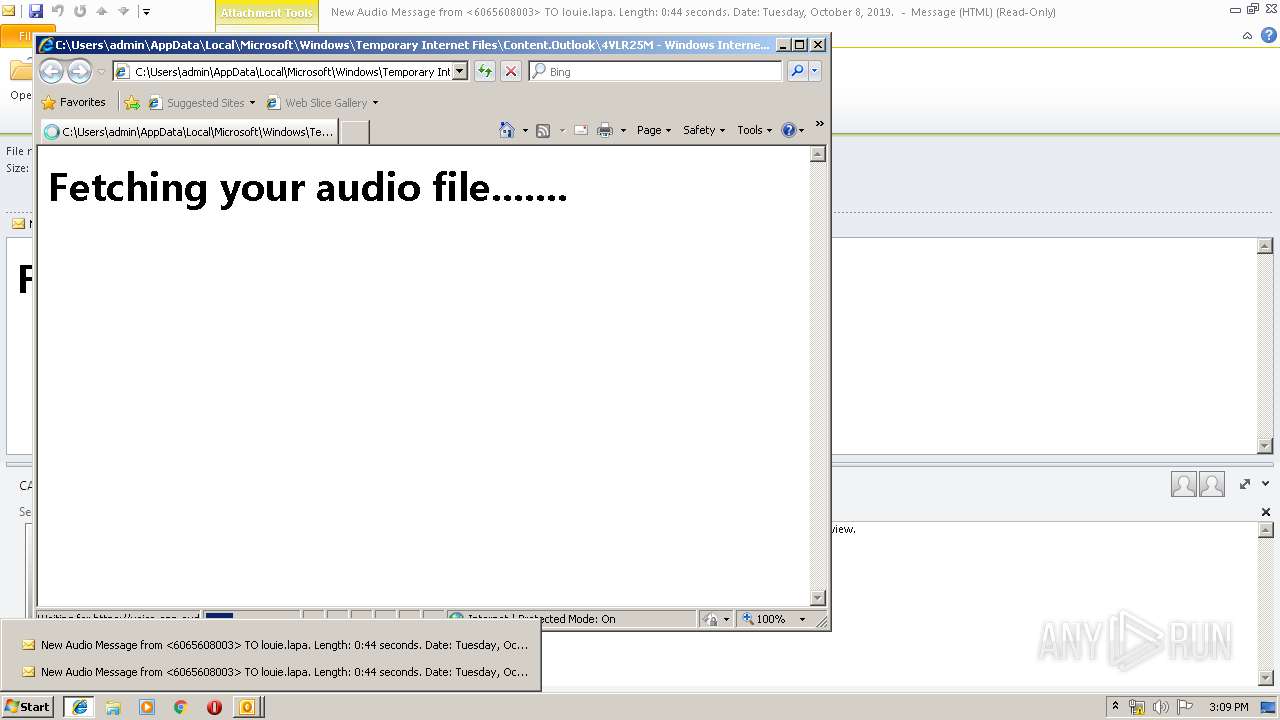
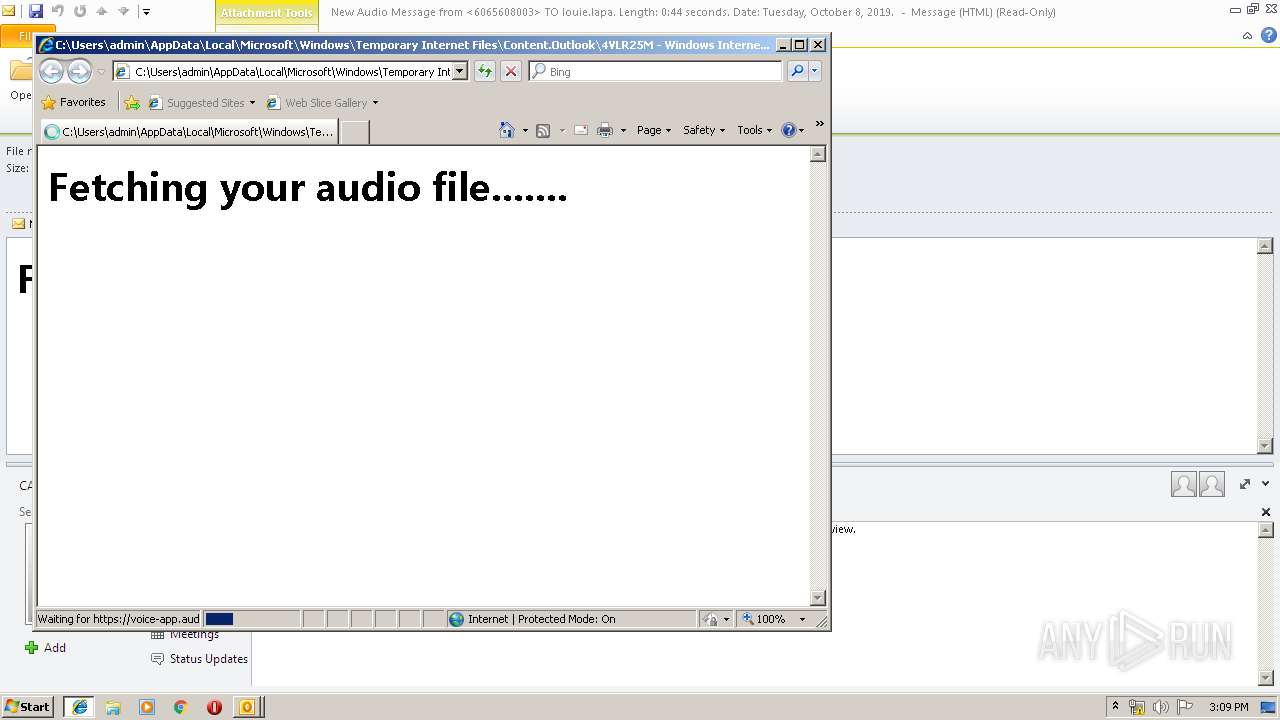
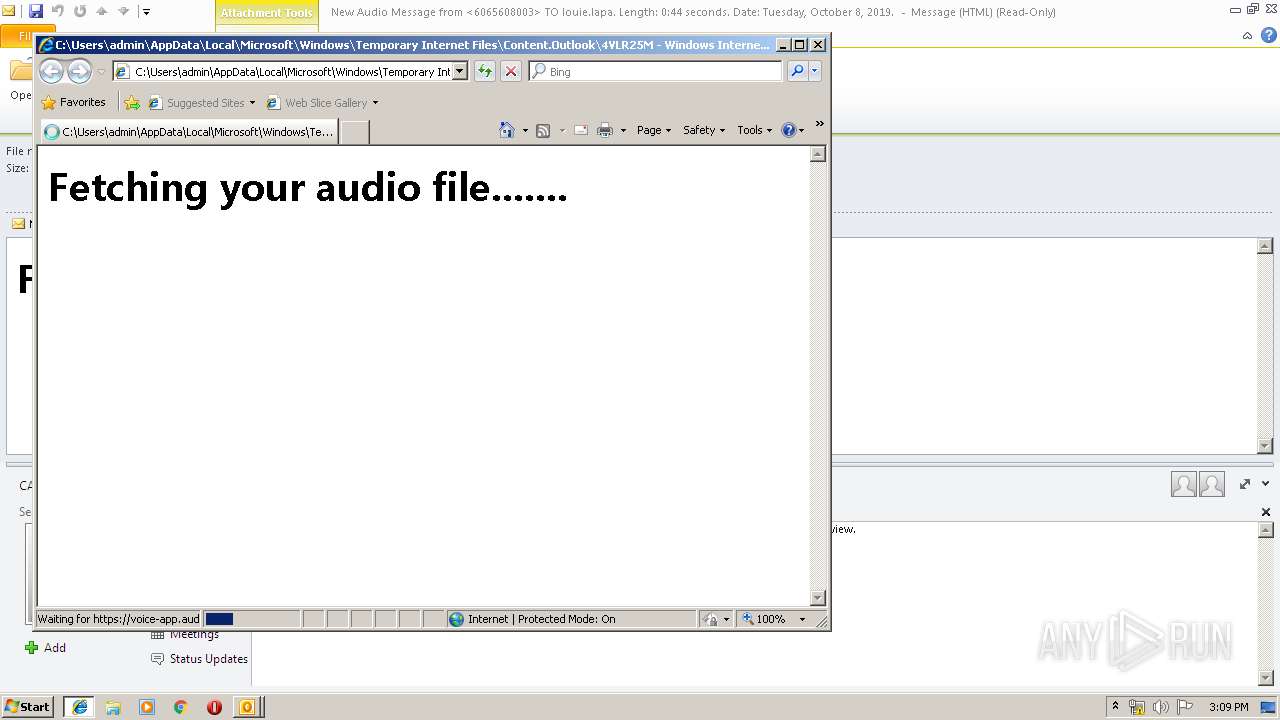
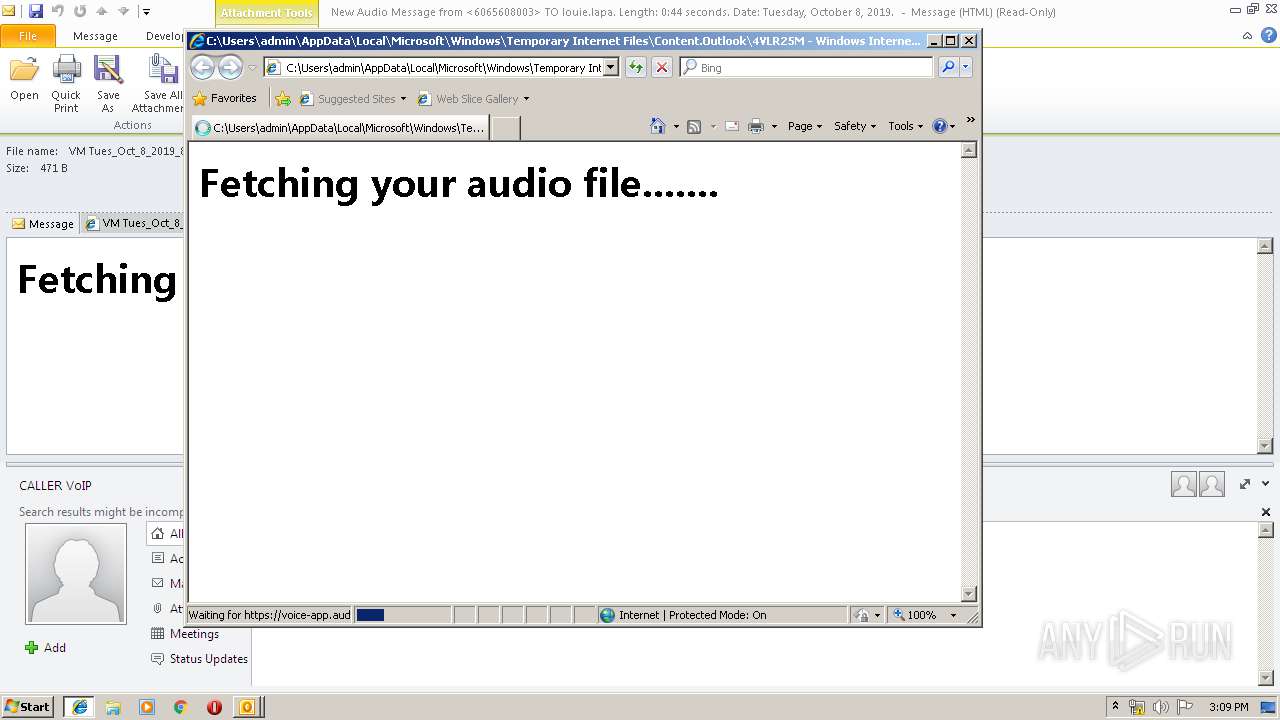
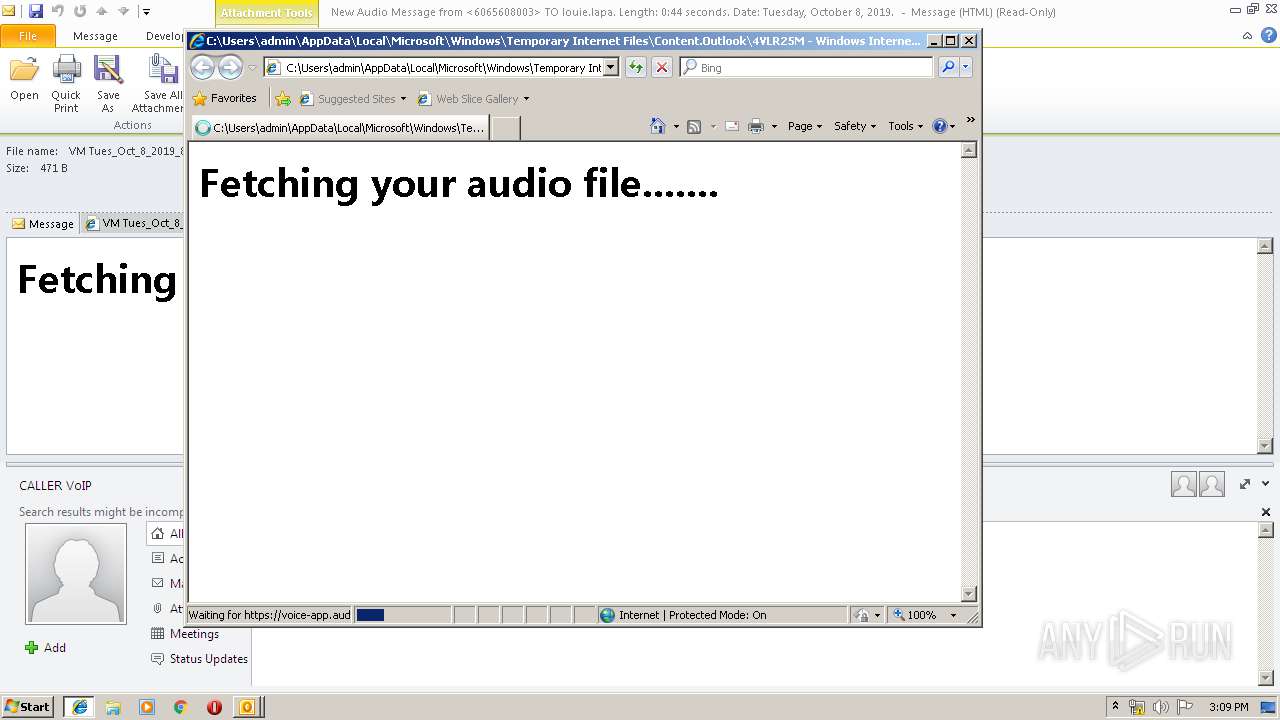
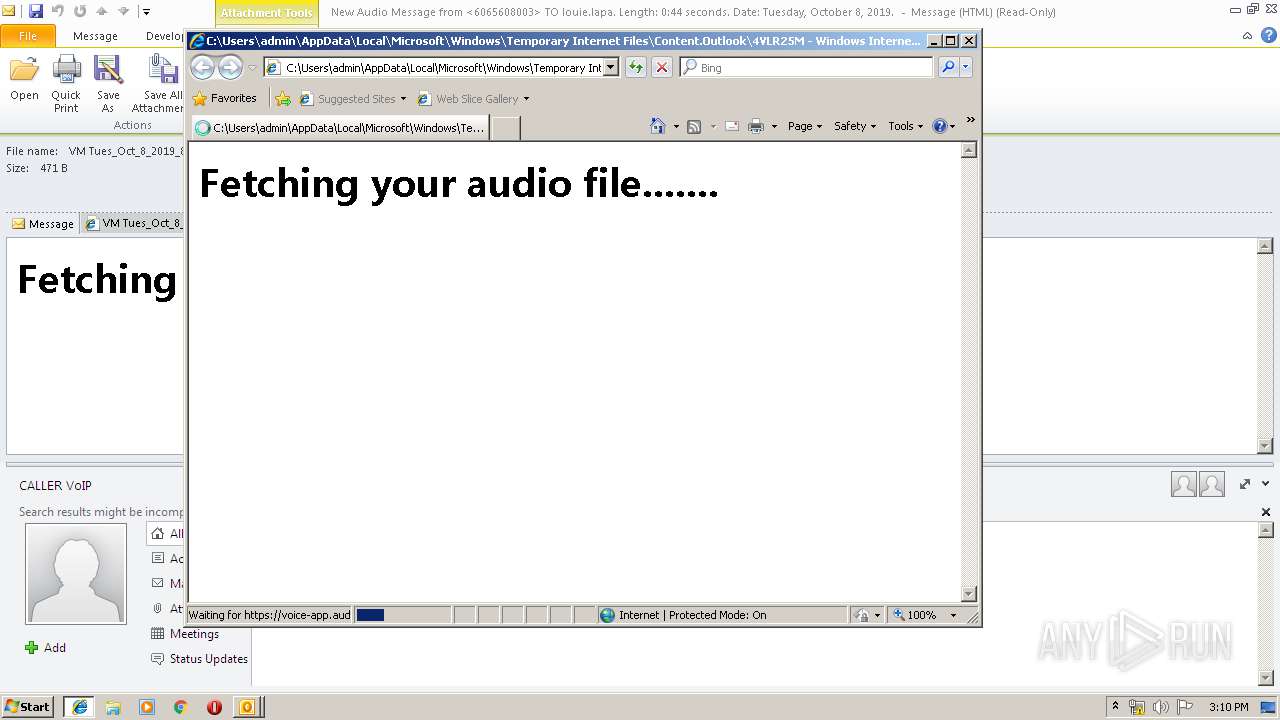
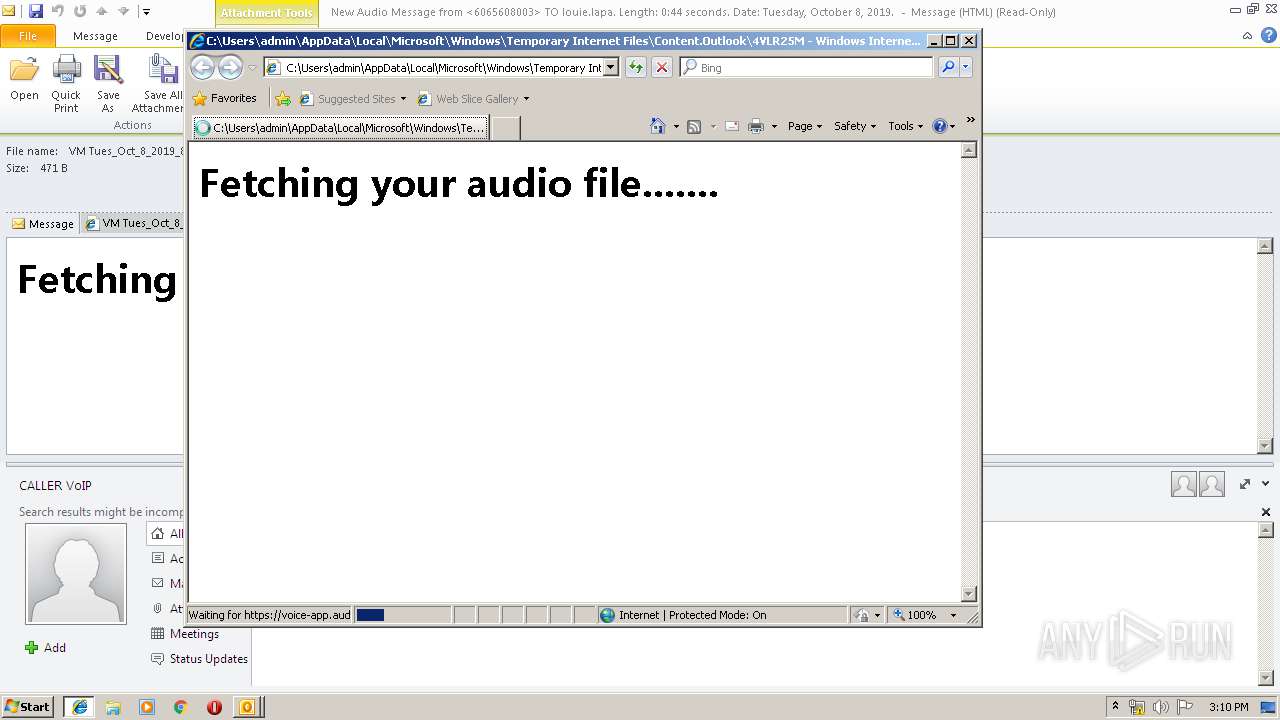
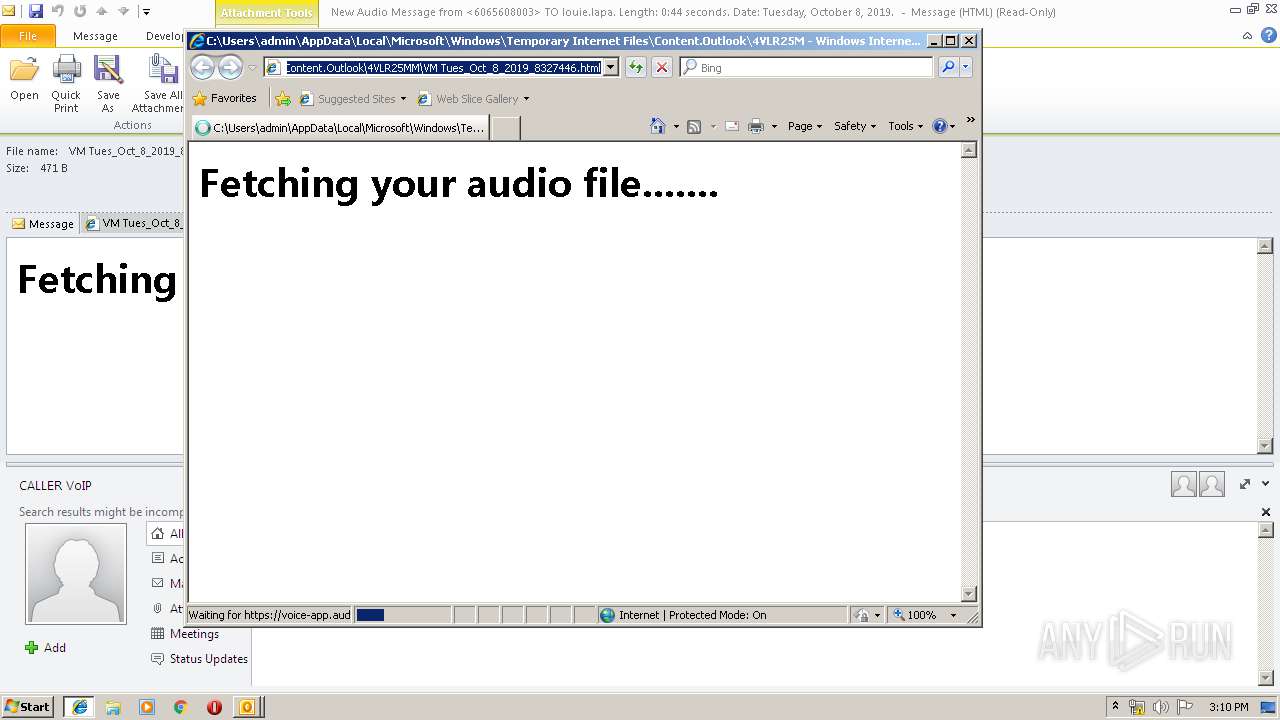
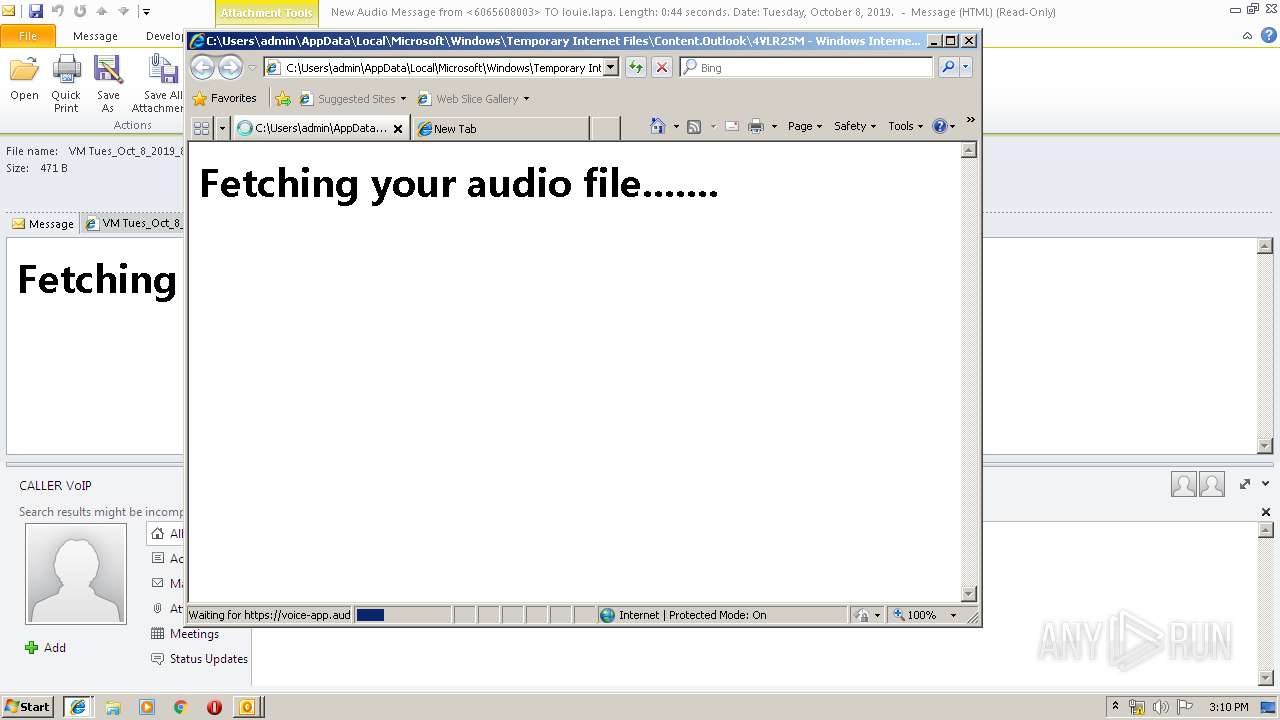
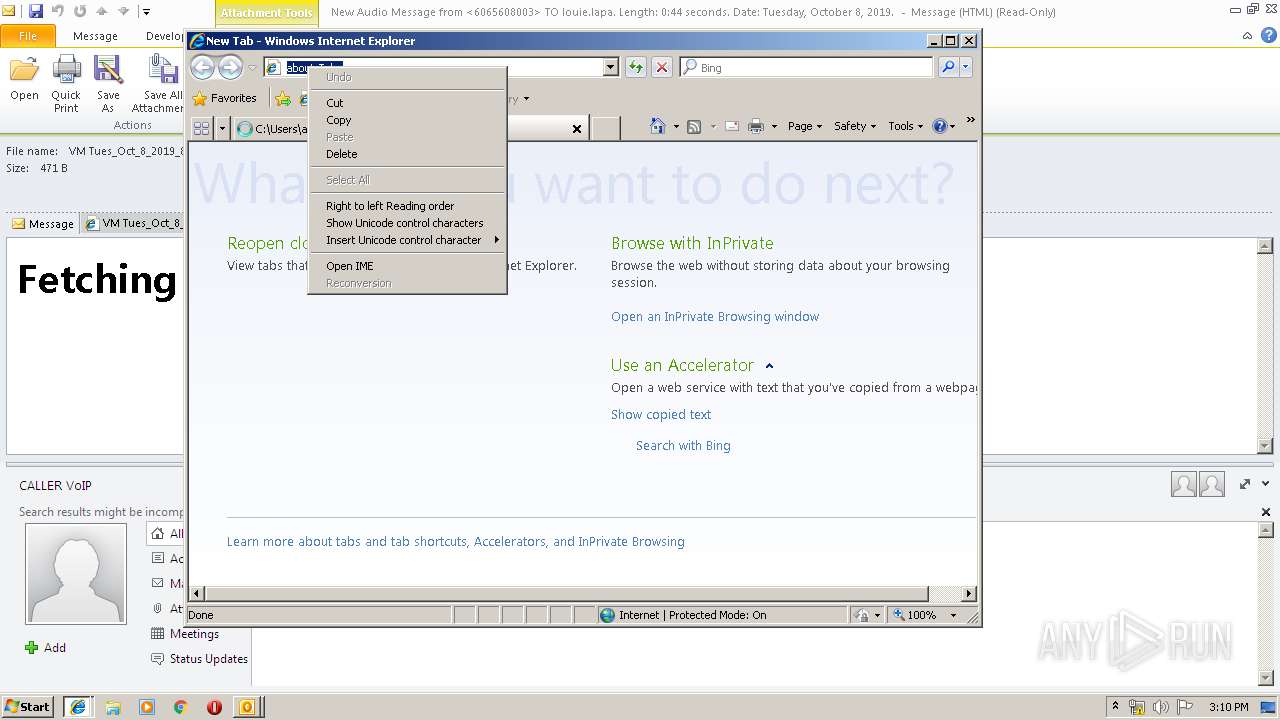
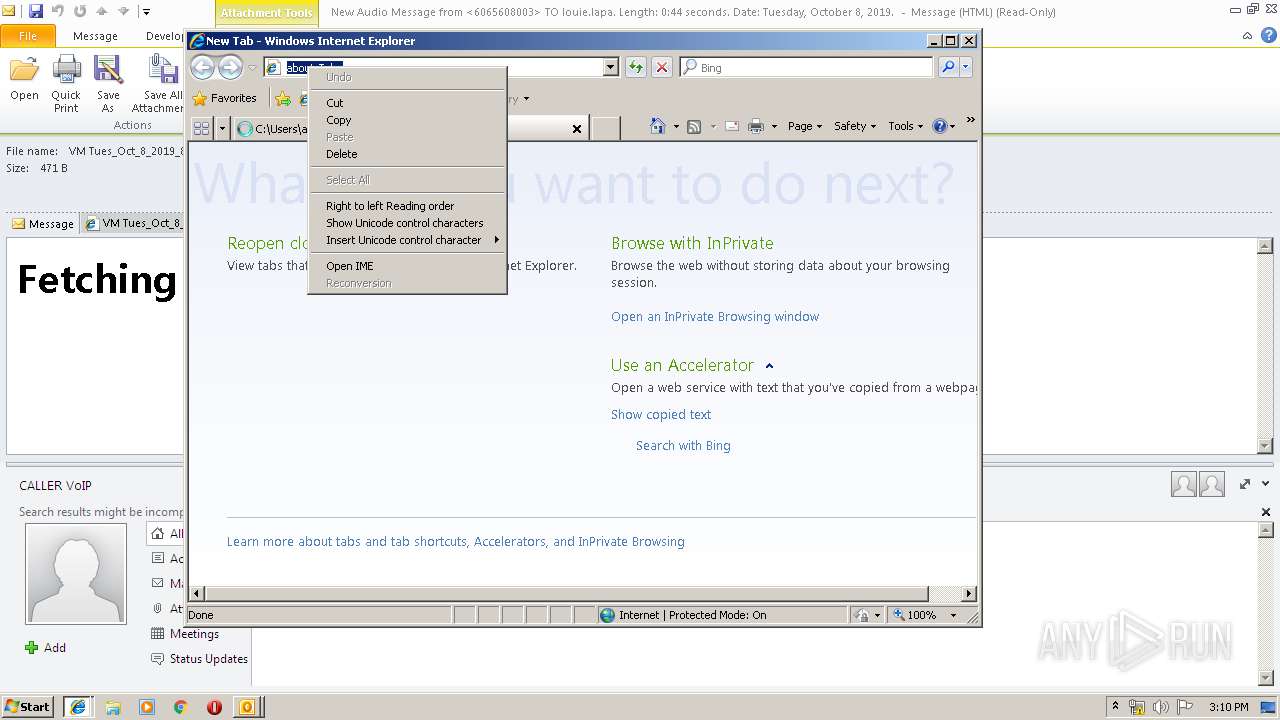
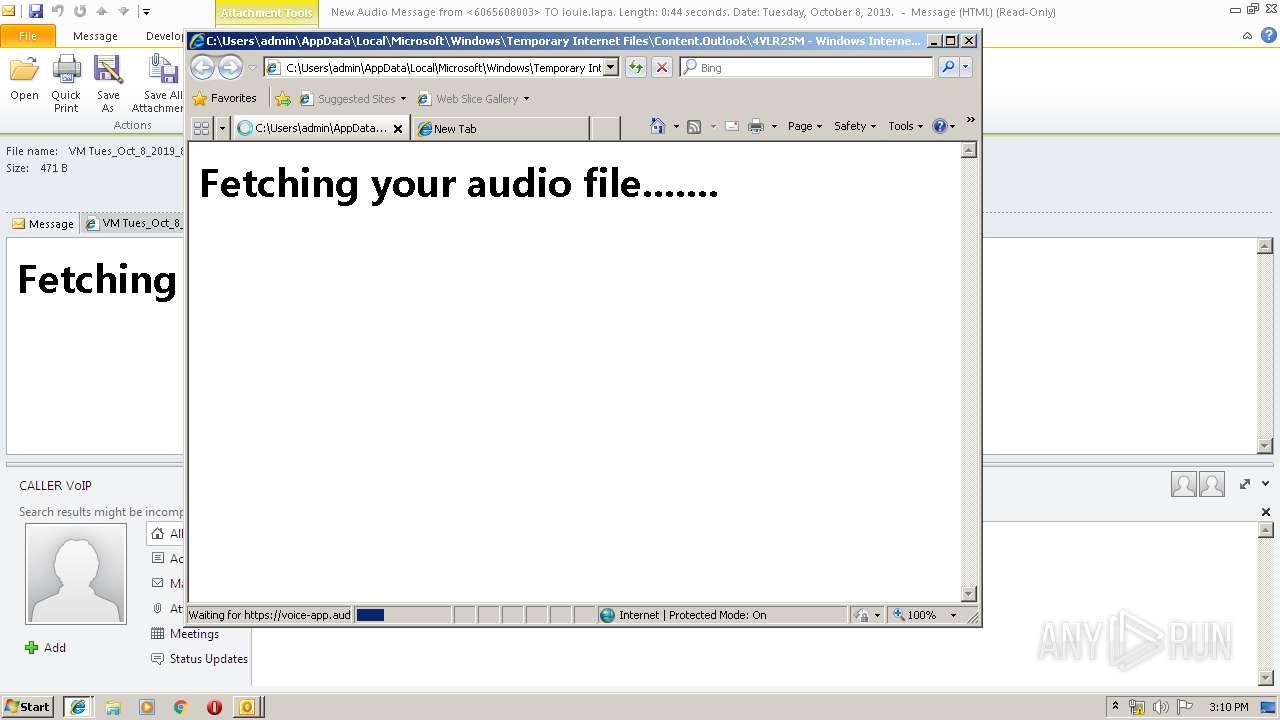
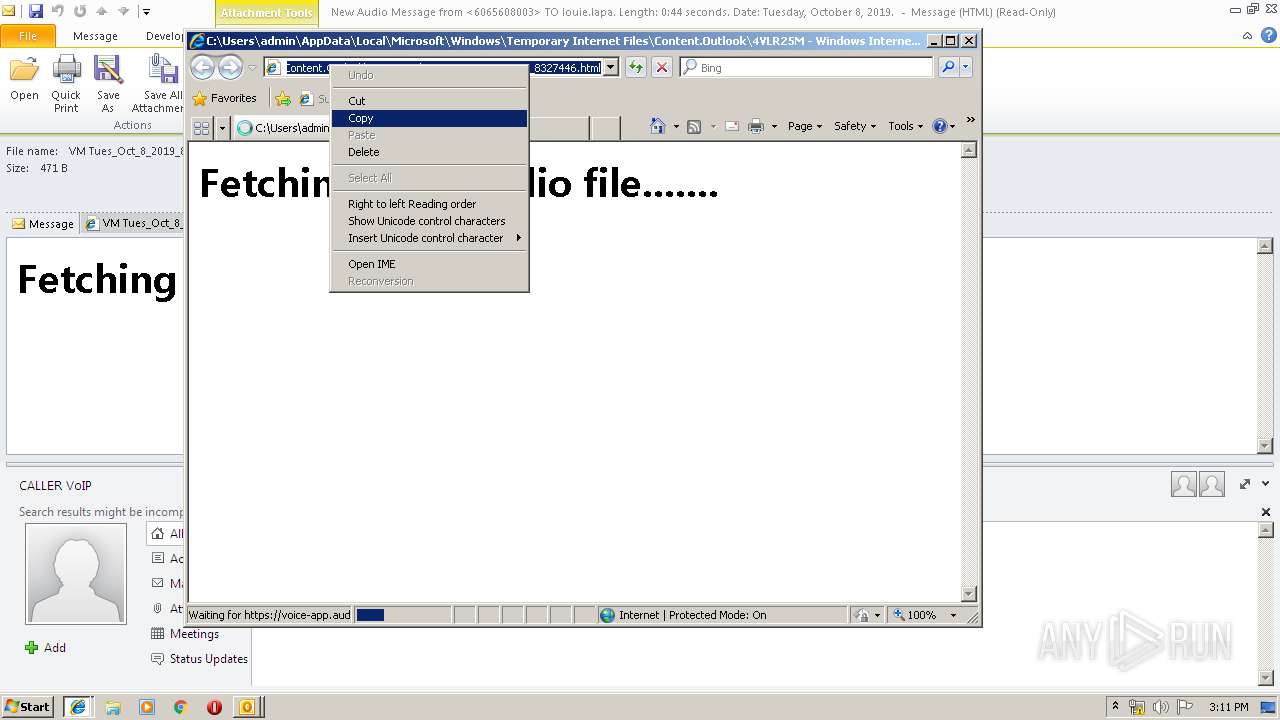
| File name: | New Audio Message from 6065608003 TO louie.lapa. Length 0 44 seconds. Date Tuesday, October 8, 2019. .eml |
| Full analysis: | https://app.any.run/tasks/4244760d-14cc-433a-aac2-3e0009f1cbc2 |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2019, 14:05:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 6E045AEAFC7D9A23E574903BA3EE3069 |
| SHA1: | 8E8AC80469A53031B24B6C9116EBBD2B3706ED61 |
| SHA256: | D71ECD06BD292178577E8D0DB2261B2118EE2EA7AEE5A4FA31258B17346D1C47 |
| SSDEEP: | 384:wGtrFc7vtdsqPxitRFchpAbtEDToC9A7cnfxBLbubfINa:bUV6qPMc6K1ucnpJbW2a |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 2960)
Executed via COM
- prevhost.exe (PID: 3676)
Reads internet explorer settings
- prevhost.exe (PID: 3676)
- OUTLOOK.EXE (PID: 2960)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2960)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2960)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2960)
Changes internet zones settings
- iexplore.exe (PID: 2824)
Application launched itself
- iexplore.exe (PID: 2824)
Reads Internet Cache Settings
- iexplore.exe (PID: 3596)
- iexplore.exe (PID: 3328)
Reads internet explorer settings
- iexplore.exe (PID: 3596)
- iexplore.exe (PID: 3328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
40
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2824 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\4VLR25MM\VM Tues_Oct_8_2019_8327446.html | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2960 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\9f8e1448-f3ea-4485-aec2-57a02ff34c20.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3328 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2824 CREDAT:6403 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3596 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2824 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3676 | C:\Windows\system32\prevhost.exe {F8B8412B-DEA3-4130-B36C-5E8BE73106AC} -Embedding | C:\Windows\system32\prevhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Preview Handler Surrogate Host Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 578
Read events
2 054
Write events
503
Delete events
21
Modification events
| (PID) Process: | (2960) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2960) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2960) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | <b< |
Value: 3C623C00900B0000010000000000000000000000 | |||
| (PID) Process: | (2960) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 900B000076AF1DB7AA7ED50100000000 | |||
| (PID) Process: | (2960) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (2960) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220250880 | |||
| (PID) Process: | (2960) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (2960) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (2960) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (2960) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1330184213 | |||
Executable files
0
Suspicious files
0
Text files
40
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR4E3C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\4VLR25MM\VM Tues_Oct_8_2019_8327446 (2).html\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019092020190921\index.dat | — | |
MD5:— | SHA256:— | |||
| 2960 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_6CFDA9698DE68041BC5D1E3875CAB2BC.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 2960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
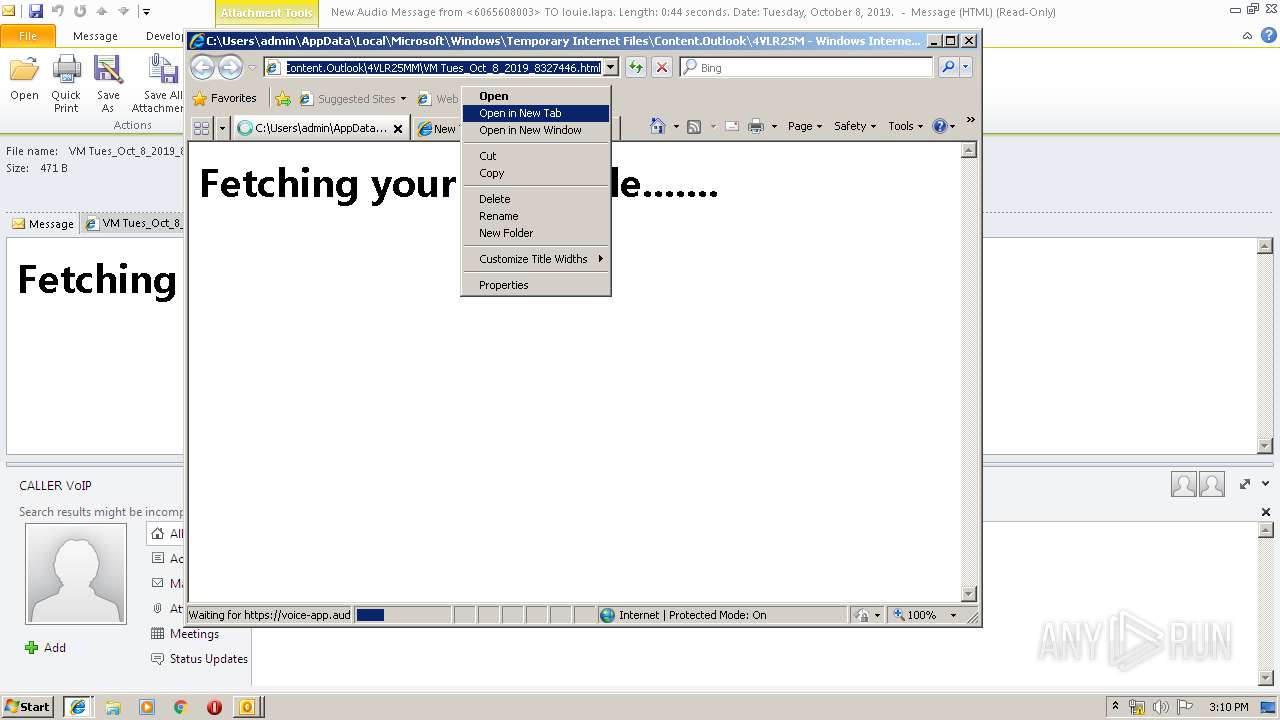
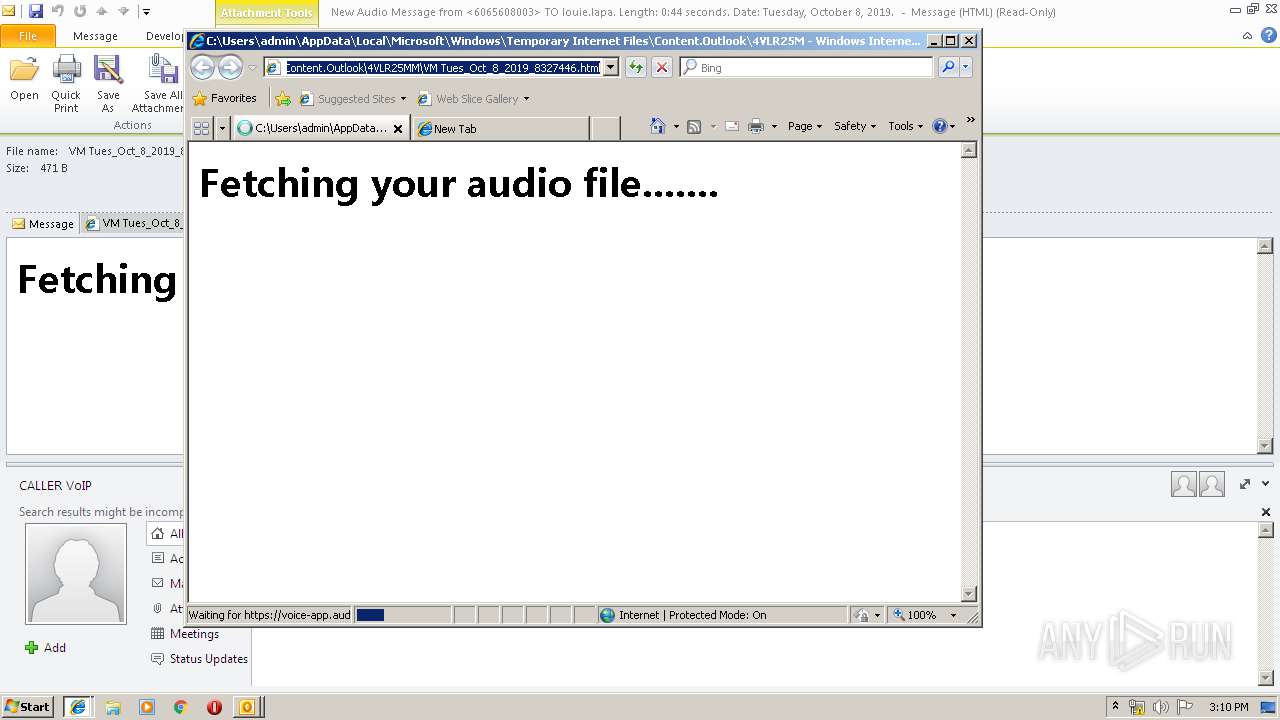
| 2960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\4VLR25MM\VM Tues_Oct_8_2019_8327446.html | html | |
MD5:— | SHA256:— | |||
| 3676 | prevhost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\wbk8EF0.tmp | html | |
MD5:— | SHA256:— | |||
| 3596 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019100920191010\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
5
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2960 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2824 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
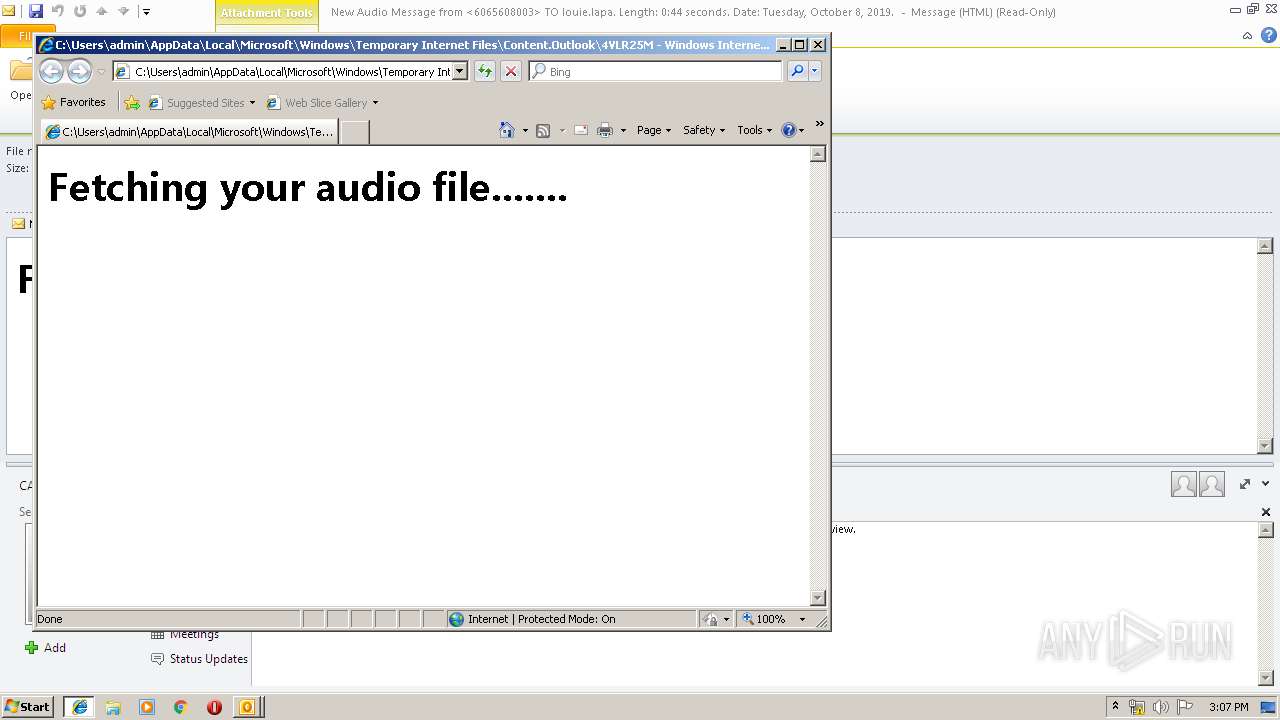
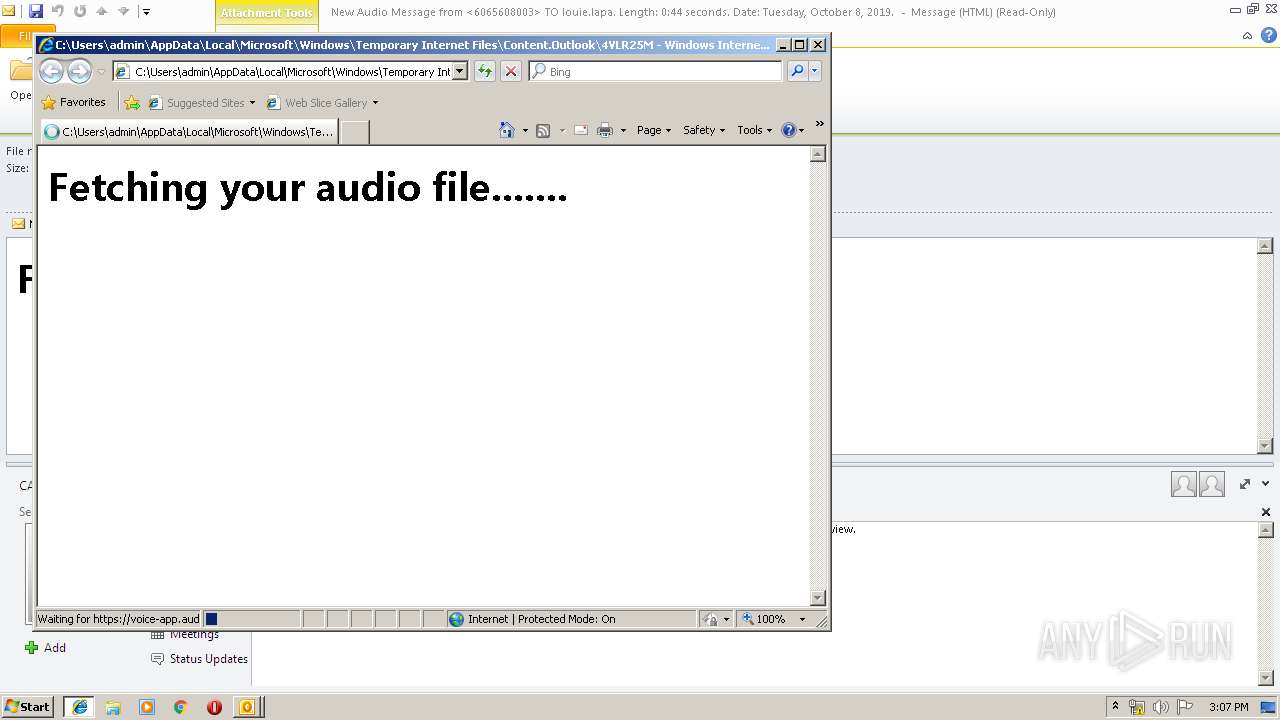
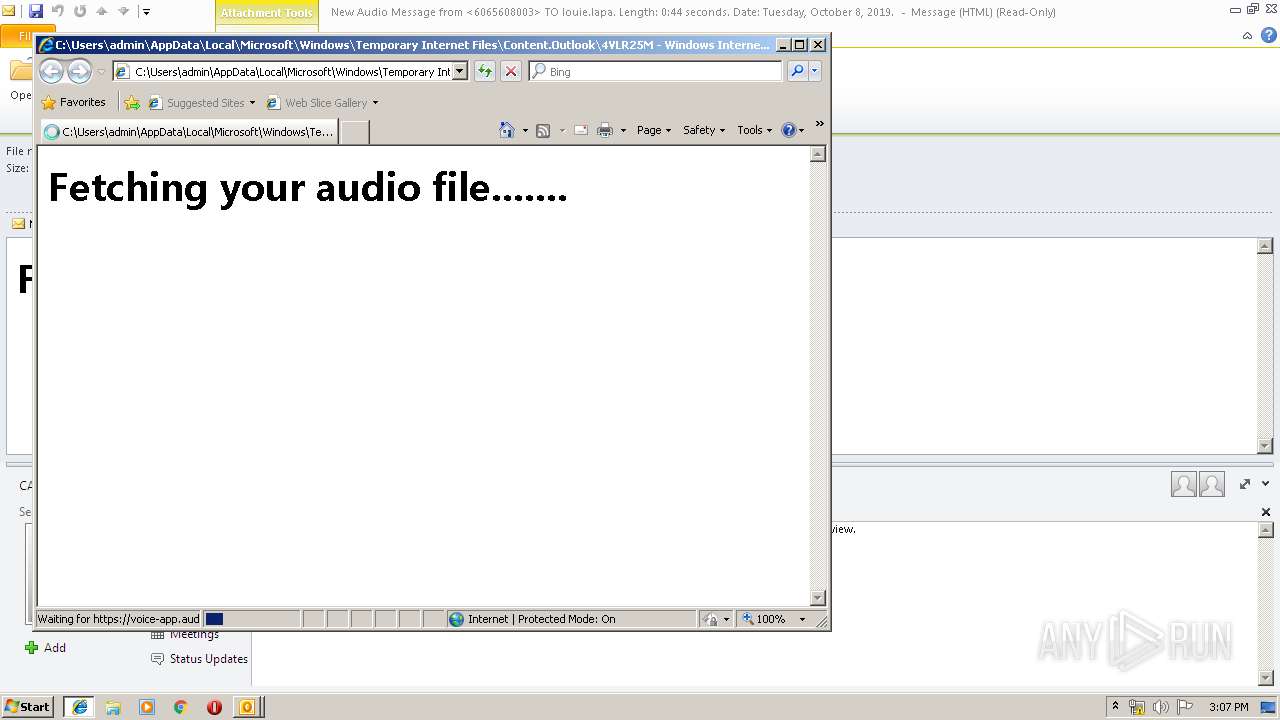
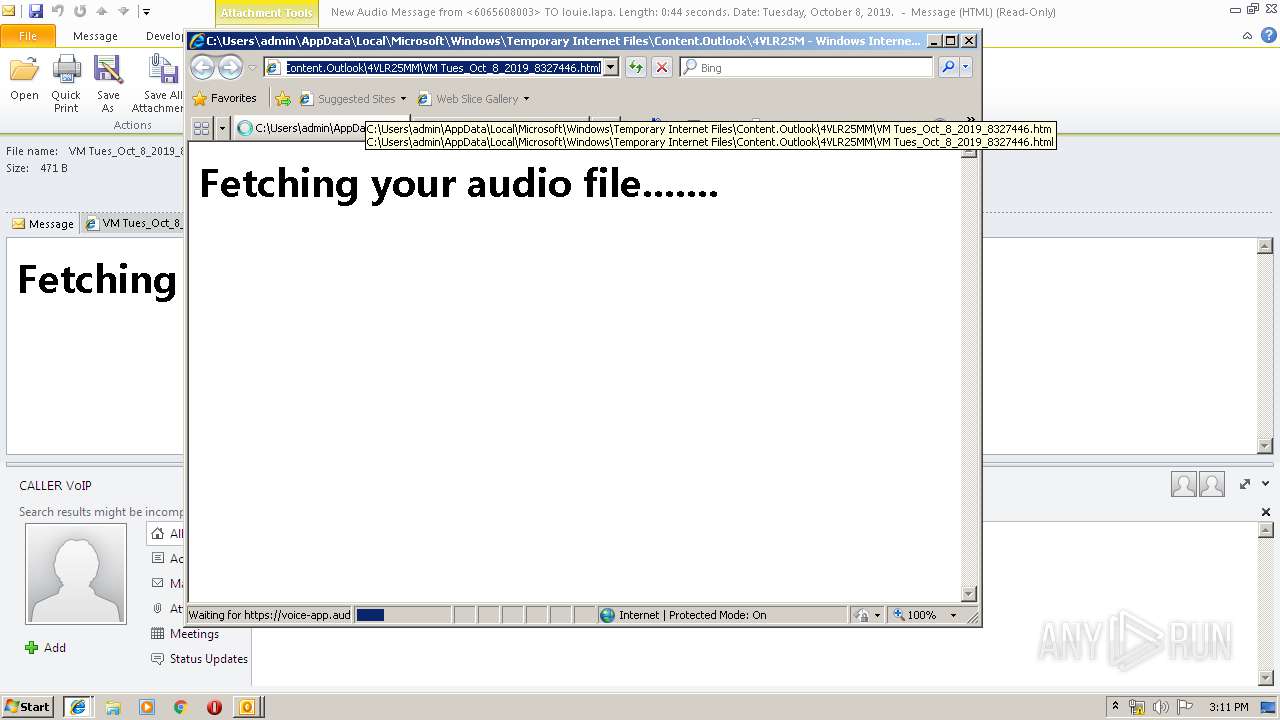
3596 | iexplore.exe | 96.8.118.121:443 | voice-app.audioservice.club | ColoCrossing | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
www.bing.com |
| whitelisted |
voice-app.audioservice.club |
| malicious |