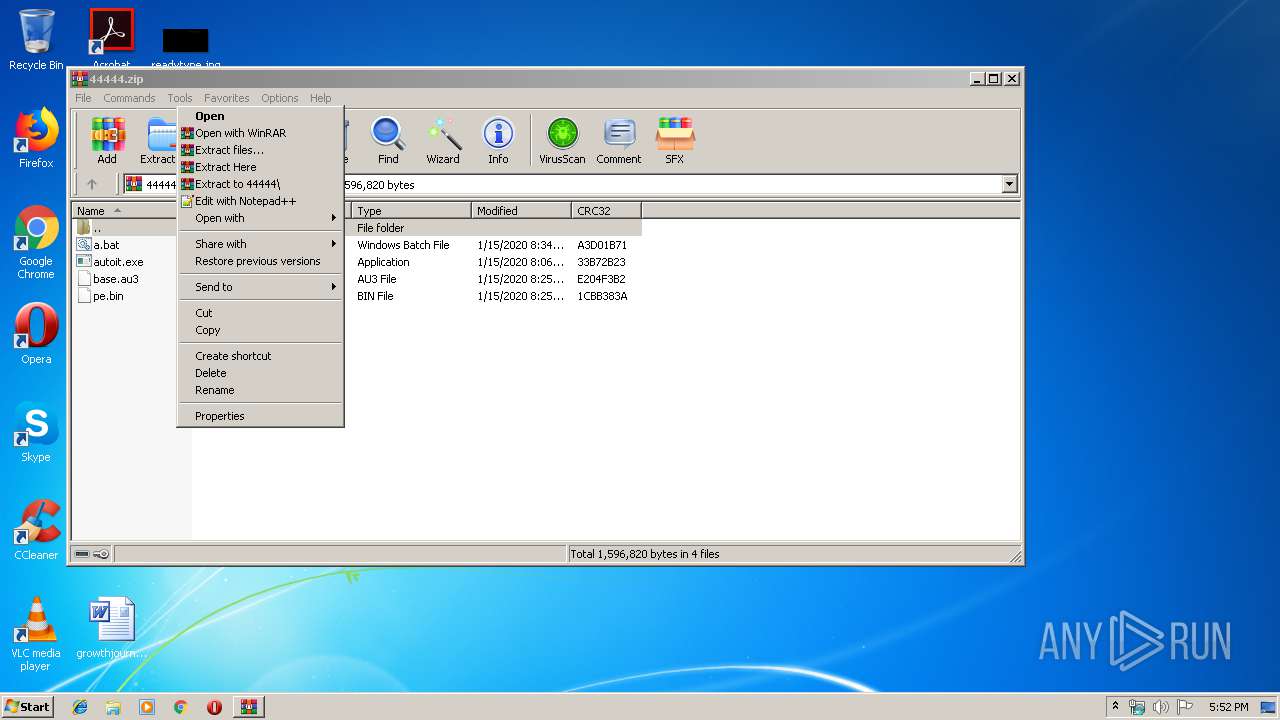
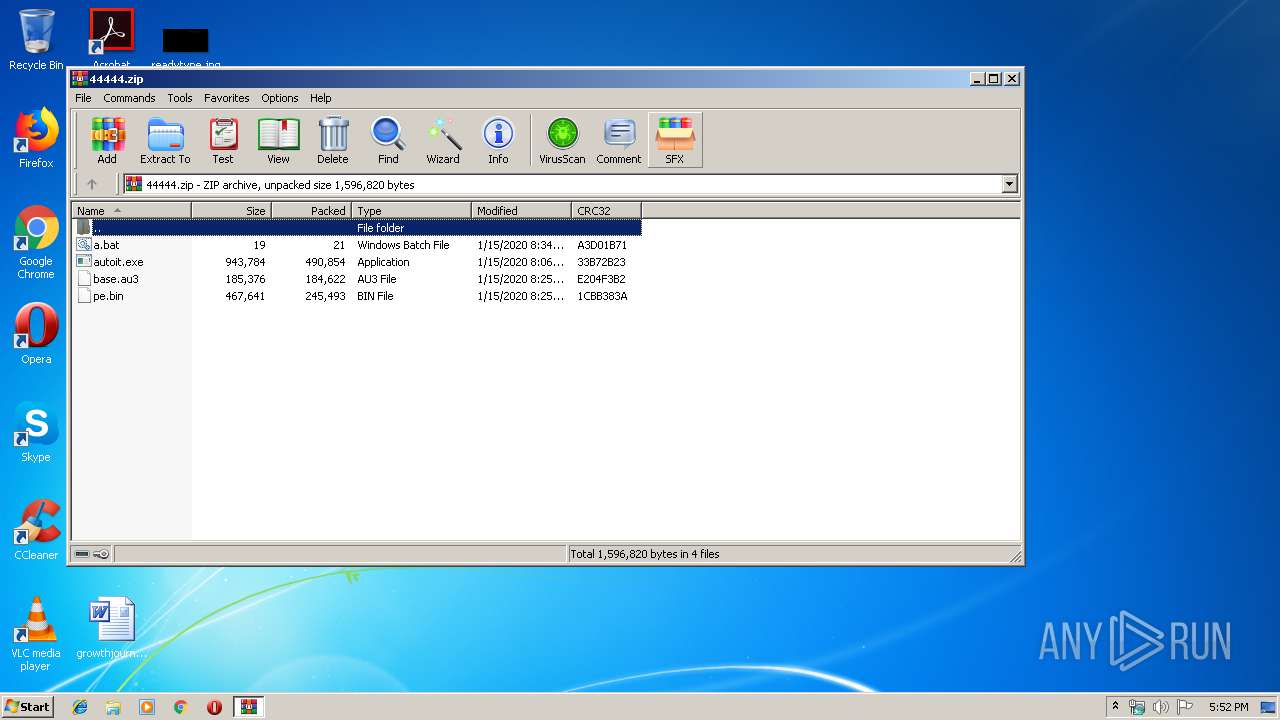
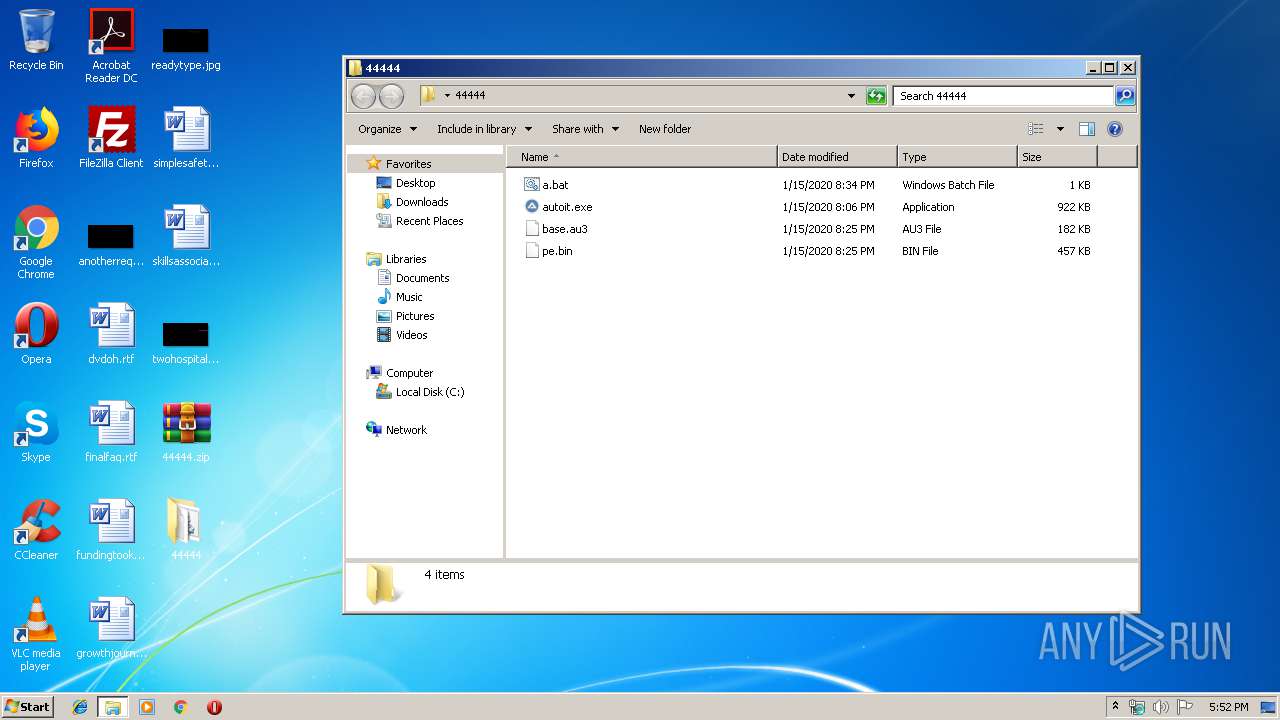
| File name: | 44444.zip |
| Full analysis: | https://app.any.run/tasks/1105143d-beee-4c12-a731-0c2b61722aca |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2020, 17:52:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 38F2EFBE3BDCB7B5D87267155648177B |
| SHA1: | 9E9019712667DFD520A28AEDB8575528858A231D |
| SHA256: | D70DEEFF61F817A3BDDD3B1714274A58FF5DACB3A3C90D713AEC2E2CD033AAE0 |
| SSDEEP: | 24576:L1+1ATdd3BmATWZEk0ToWa3+sc0tgOpaN3x+34Y:xdd3BmXuo98OE4J |
MALICIOUS
Application was dropped or rewritten from another process
- autoit.exe (PID: 2844)
Connects to CnC server
- notepad.exe (PID: 2500)
Changes the autorun value in the registry
- notepad.exe (PID: 2500)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2728)
- notepad.exe (PID: 2500)
Drop AutoIt3 executable file
- notepad.exe (PID: 2500)
- WinRAR.exe (PID: 2728)
Creates files in the program directory
- notepad.exe (PID: 2500)
INFO
Manual execution by user
- WinRAR.exe (PID: 2728)
- cmd.exe (PID: 2488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:01:15 14:25:18 |
| ZipCRC: | 0x1cbb383a |
| ZipCompressedSize: | 245493 |
| ZipUncompressedSize: | 467641 |
| ZipFileName: | pe.bin |
Total processes
41
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
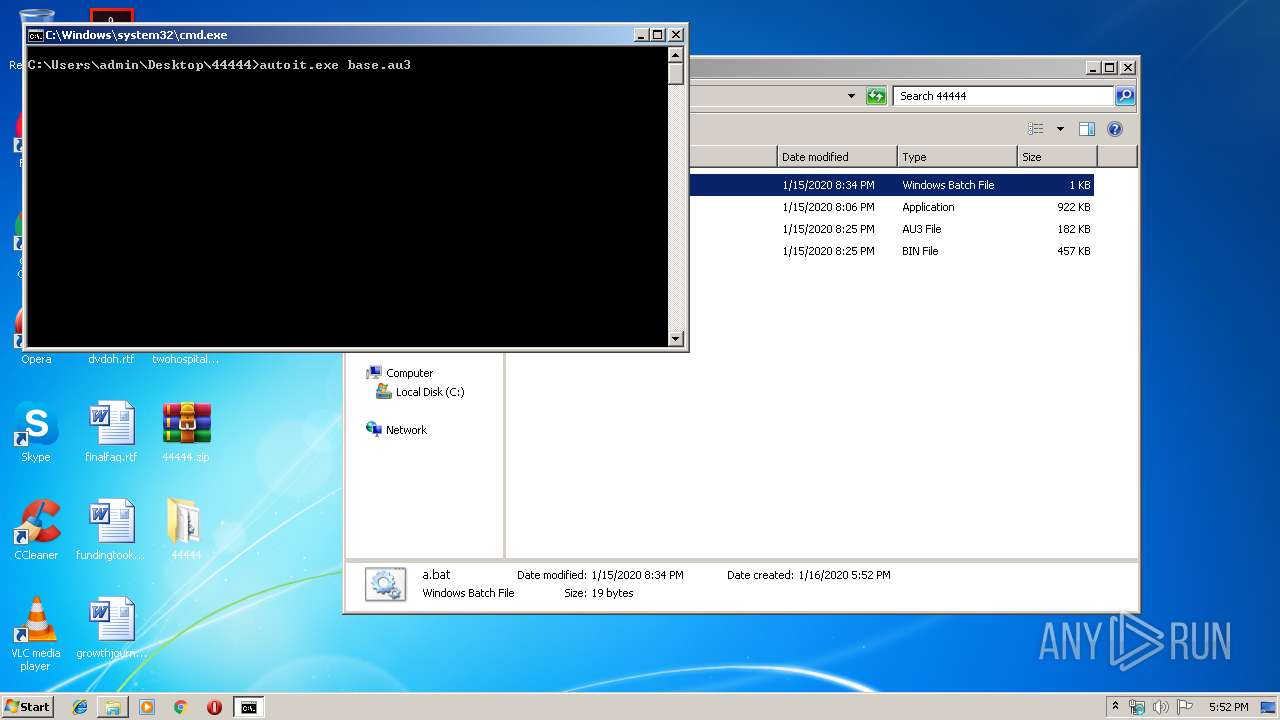
| 2488 | cmd /c ""C:\Users\admin\Desktop\44444\a.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2500 | "C:\Windows\system32\notepad.exe" | C:\Windows\system32\notepad.exe | autoit.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2600 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\44444.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2728 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\44444.zip" C:\Users\admin\Desktop\44444\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2844 | autoit.exe base.au3 | C:\Users\admin\Desktop\44444\autoit.exe | — | cmd.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 1 Modules
| |||||||||||||||
Total events
1 413
Read events
354
Write events
1 059
Delete events
0
Modification events
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\44444.zip | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
2
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2500 | notepad.exe | C:\ProgramData\Intel\Wireless\95f8f9e\109207d\4c82613 | — | |
MD5:— | SHA256:— | |||
| 2728 | WinRAR.exe | C:\Users\admin\Desktop\44444\base.au3 | binary | |
MD5:— | SHA256:— | |||
| 2500 | notepad.exe | C:\ProgramData\Intel\Wireless\95f8f9e\pe.bin | text | |
MD5:— | SHA256:— | |||
| 2500 | notepad.exe | C:\ProgramData\Intel\Wireless\95f8f9e\83328d7.au3 | binary | |
MD5:— | SHA256:— | |||
| 2500 | notepad.exe | C:\ProgramData\Intel\Wireless\95f8f9e\109207d\87a6e29 | text | |
MD5:— | SHA256:— | |||
| 2728 | WinRAR.exe | C:\Users\admin\Desktop\44444\pe.bin | text | |
MD5:— | SHA256:— | |||
| 2728 | WinRAR.exe | C:\Users\admin\Desktop\44444\a.bat | text | |
MD5:— | SHA256:— | |||
| 2500 | notepad.exe | C:\ProgramData\Intel\Wireless\95f8f9e\109207d\16-01-2020.log | text | |
MD5:— | SHA256:— | |||
| 2728 | WinRAR.exe | C:\Users\admin\Desktop\44444\autoit.exe | executable | |
MD5:3F58A517F1F4796225137E7659AD2ADB | SHA256:1DA298CAB4D537B0B7B5DABF09BFF6A212B9E45731E0CC772F99026005FB9E48 | |||
| 2500 | notepad.exe | C:\ProgramData\Intel\Wireless\95f8f9e\bbedecj.exe | executable | |
MD5:3F58A517F1F4796225137E7659AD2ADB | SHA256:1DA298CAB4D537B0B7B5DABF09BFF6A212B9E45731E0CC772F99026005FB9E48 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
11
DNS requests
18
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2500 | notepad.exe | POST | 200 | 83.171.237.231:9993 | http://0.le4net00.net:9993/ | unknown | text | 488 b | malicious |
2500 | notepad.exe | POST | 200 | 83.171.237.231:9993 | http://0.le4net00.net:9993/ | unknown | text | 2 b | malicious |
2500 | notepad.exe | POST | 200 | 51.77.85.131:80 | http://124.red-79-152-243.dynamicip.fina-tdl.io/s/cpux86.bin | GB | text | 1.78 Mb | suspicious |
2500 | notepad.exe | POST | 200 | 83.171.237.231:9993 | http://0.le4net00.net:9993/ | unknown | text | 2 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2500 | notepad.exe | 51.77.85.131:80 | 124.red-79-152-243.dynamicip.fina-tdl.io | — | GB | suspicious |
2500 | notepad.exe | 185.185.27.75:2424 | 0.weathdata.nu | Hetzner Online GmbH | DE | malicious |
2500 | notepad.exe | 83.171.237.231:9993 | 0.le4net00.net | — | — | malicious |
2500 | notepad.exe | 83.171.237.231:2424 | 0.le4net00.net | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
0.le4net00.net |
| malicious |
compute.deutschlandaws.com |
| unknown |
deploy.static.blazingtechnologies.io |
| unknown |
as202248.net |
| unknown |
124.red-79-152-243.dynamicip.fina-tdl.io |
| suspicious |
vlan27.as09.uk.es.x46o7.io |
| unknown |
google-ic-211564-bac-b7.c.bacb7c.to |
| unknown |
ae-12-3104.bar1.madrid1.lev3l0.net |
| malicious |
server-13-224-114-187.mad50.r.telcel.io |
| malicious |
google-ic-314668-mad-b1.c.in3tia.to |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2500 | notepad.exe | A Network Trojan was detected | MALWARE [PTsecurity] W32.HfsVibisi.E172 checkin |
2500 | notepad.exe | A Network Trojan was detected | MALWARE [PTsecurity] W32.HfsVibisi.E172 checkin |
2500 | notepad.exe | A Network Trojan was detected | MALWARE [PTsecurity] W32.HfsVibisi.E172 checkin |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |